Difference between Active Attack and Passive Attack
Overview
In the field of cybersecurity, threats to digital systems and sensitive data are a constant concern. Two primary categories of attacks that hackers employ to compromise security are active and passive attacks. Understanding the differences between active and passive attacks is crucial for effective defense strategies. This article dives into the distinctive characteristics of active and passive attacks, providing insightful examples and a comprehensive comparison.
Active Attacks
Active attacks involve direct interaction with the target system, where the attacker actively manipulates or alters data, disrupts services, or gains unauthorized access. These attacks are often characterized by their aggressive and intrusive nature, as the attacker actively seeks to compromise the integrity, confidentiality, or availability of the target.
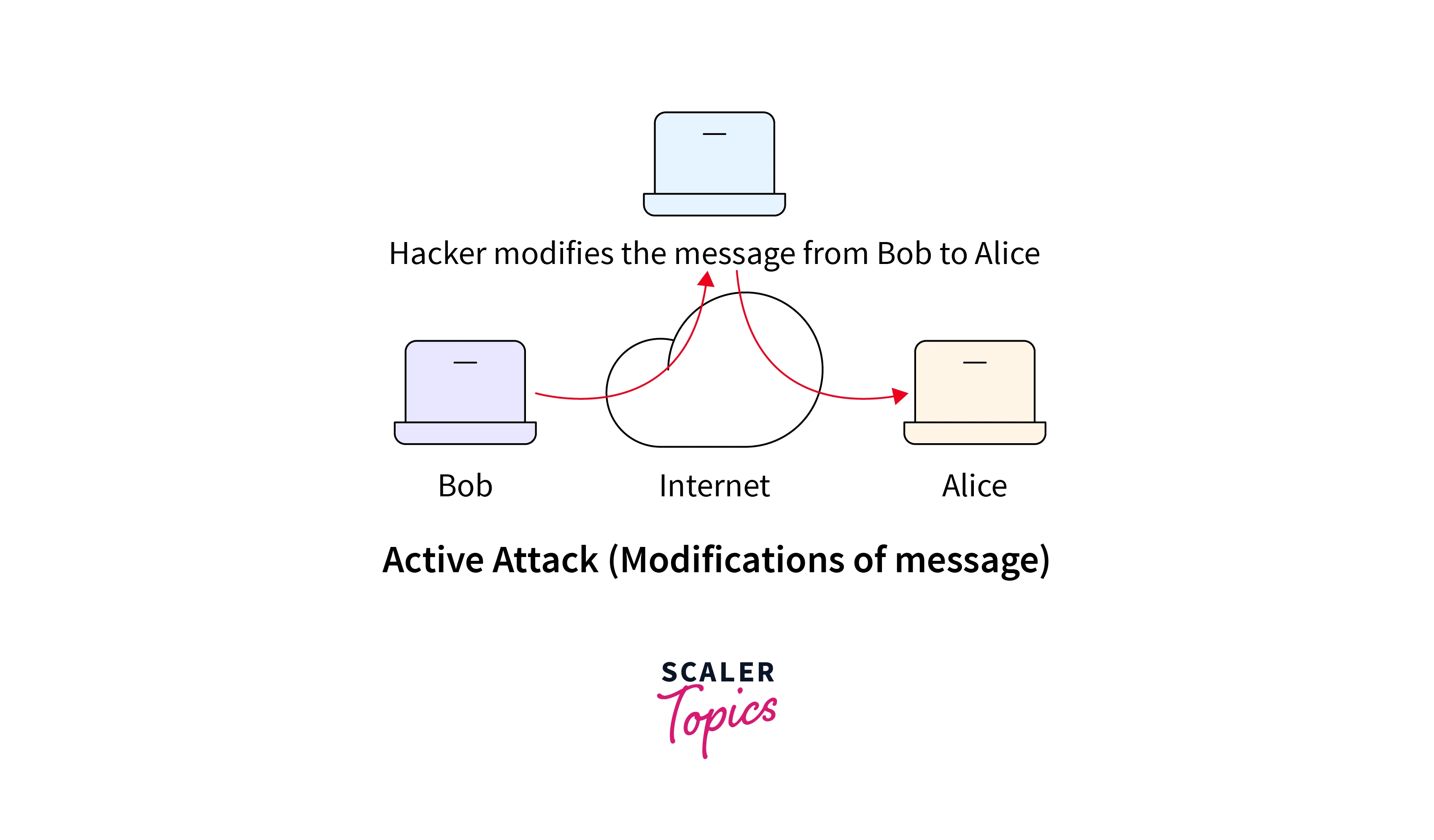
The following are some examples of active attacks:
Malware Injection
Malware injection is a prevalent form of active attack where an attacker inserts malicious software (malware) into a target system. One of the most common delivery methods for malware is through email attachments. For instance, a hacker might craft an email that appears legitimate, encouraging the recipient to open an attached file. Unbeknownst to the victim, the attachment contains malware that exploits vulnerabilities in the system. Once opened, the malware could take various forms, such as viruses, worms, or Trojan horses.
Imagine a scenario where an employee receives an email appearing to be from a co-worker containing a seemingly innocent document attachment. Upon opening the attachment, malware is executed, allowing the attacker to gain control over the victim's device. The attacker can then steal sensitive data, monitor activities, or even use the compromised device to launch further attacks.
Denial of Service (DoS) Attack
A Denial of Service (DoS) attack aims to disrupt the normal functioning of a system, network, or service by overwhelming it with a flood of requests. Attackers achieve this by utilizing a large number of devices, often forming a botnet, to send an excessive volume of requests simultaneously. As a result, the targeted system becomes inundated and unable to respond to legitimate user requests.
Imagine a popular e-commerce website during a flash sale event. An attacker orchestrates a DoS attack, sending an overwhelming number of requests to the website's servers. The servers become so burdened that they are unable to process genuine customer requests, causing the website to slow down or become completely inaccessible. This impacts customer experience and potentially leads to revenue loss for the business.
Man-in-the-Middle (MitM) Attack
A Man-in-the-Middle (MitM) attack is a sophisticated technique where an attacker intercepts and monitors communication between two parties without their knowledge. The attacker positions themselves between the communicating parties and can capture, alter, or even inject malicious content into the communication stream.
Consider a person using public Wi-Fi in a coffee shop to access their online banking account. An attacker, also connected to the same network, uses MitM techniques to intercept the data traffic between the user's device and the bank's server. The attacker can collect sensitive information such as login credentials and account numbers. Additionally, they can manipulate the data exchanged, making the victim believe they are interacting directly with the bank's website.
Passive Attacks
In contrast to active attacks, passive attacks are more covert and involve eavesdropping or monitoring the target system's data and communication without directly altering or interrupting it. These attacks aim to gather sensitive information, such as passwords, credit card numbers, or confidential business data, without the victim's awareness.
The following are some examples of passive attacks:
Packet Sniffing
Packet sniffing is a passive attack where an attacker intercepts and monitors data packets being transmitted between devices on a network. Attackers achieve this by using specialized tools that can capture and analyze the content of these packets. This attack is particularly effective on unsecured or poorly encrypted networks.
Consider an individual using a public Wi-Fi network at an airport. An attacker on the same network, equipped with packet sniffing tools, can capture data packets transmitted between the user's device and various websites. If the websites do not use encryption (HTTPS), the attacker can gain access to unencrypted data, including login credentials, personal messages, and browsing history. This exposes the user to risks of identity theft, account compromise, and privacy breaches.
Eavesdropping
Eavesdropping is a passive attack that involves intercepting and listening in on conversations or communication channels to gather sensitive information. Attackers may target phone calls, email exchanges, or any other form of communication to gain valuable insights or confidential data.
Imagine a corporate setting where company executives are discussing strategic plans over a phone call. An attacker who gains access to the communication channel can eavesdrop on the conversation and obtain insider information about the company's future initiatives. This information could be exploited for financial gain, market manipulation, or competitive advantage.
Passive Password Attacks
Passive password attacks involve the accumulation of password information from various sources, such as leaked databases or data breaches. Attackers gather passwords exposed in security breaches and compile them into lists for future use. They then attempt to use these compromised passwords to gain unauthorized access to user accounts on different platforms.
Consider a scenario where a popular social media platform experiences a data breach, exposing millions of user account credentials. Attackers can obtain these leaked passwords and attempt to use them on various websites and services, exploiting users who reuse passwords across platforms. This passive attack leverages poor password practices and highlights the importance of using unique, strong passwords for each account.
Difference between Active and Passive Attacks
| Aspect | Active Attack | Passive Attack |
|---|---|---|
| Nature | Intrusive and aggressive, involves direct interaction | Covert and non-intrusive, involves eavesdropping and monitoring |
| Objective | Data manipulation, disruption, unauthorized access | Data gathering, information interception |
| Interaction | Directly alters data or services | Monitors data and communication, no direct alteration of data |
| Examples | Malware injection, DoS attacks, MitM attacks | Packet sniffing, eavesdropping, passive password attacks |
| Visibility to Victim | Often noticeable due to disruptions or anomalies | Often goes unnoticed unless analyzed |
| Targeted Area | Integrity, confidentiality, and availability of data and services | Confidentiality of information, such as passwords and sensitive data |
| Impact | Immediate and potentially disruptive, can lead to system crashes, data loss, or unauthorized access | Gradual accumulation of information, potential unauthorized access to accounts or sensitive data |
| Detection | More likely to be detected due to active interference and anomalies | Detection can be challenging since the attacker doesn't actively alter data or disrupt services |
| Prevention Measures | Firewalls, intrusion detection systems, access controls | Encryption, strong authentication mechanisms, secure network protocols, monitoring for unusual activities |
| Mitigation Focus | Preventing unauthorized access, limiting damage | Securing data in transit, implementing robust authentication |
| Examples Continued | Ransomware attacks encrypt files and demand payment, phishing attacks trick users into revealing information, brute-force attacks guess passwords, social engineering manipulates users | Cryptojacking covertly uses victim's computing power for cryptocurrency mining, data breaches steal sensitive information, sniffing and intercepting login credentials, passive reconnaissance for future attacks, insider threats monitoring internal communication for illicit activity |
| Response | Immediate response required to mitigate damage, isolate affected systems | Requires proactive measures to prevent data exposure, constant monitoring of network traffic |
Conclusion
- In the ever-evolving cybersecurity landscape, distinguishing between active and passive attacks is paramount.
- While active attacks involve direct interference and manipulation, passive attacks are subtler and primarily focus on covert data interception.
- Organizations and individuals must implement robust security measures to effectively counter both types of attacks.
- Utilizing encryption, strong access controls, and network monitoring can play a significant role in safeguarding against these threats.
