Collision Avoidance in Wireless Networks
Overview
In computer networking, a collision happens when multiple devices attempt to transfer data via a commonly shared circuit. In a common circuit, various devices may listen at the same time, but only one device at a time is allowed to transmit data. This requires that all other devices listen to the transmission. Many devices are connected to one single shared stream of transmission. Thus collisions are likely to occur.
Collision Avoidance in Wireless Networking
Wireless technologies, unlike their wired counterparts, are mostly half duplex, meaning a wireless device may talk as well as listen, but can not do both things simultaneously. For instance, R.F. (Radio Frequency) becomes difficult to be used as a shared medium, since in any RF region containing several wireless devices, only one of the devices is allowed to talk at a time. Since a single device can be a transmitter at a time, one slow device may slow down the entire wireless traffic in that region, and may also introduce collisions.
Wireless media are shared spaces, leading to collisions if multiple devices attempt to communicate at the same time. However, in the case of wired technologies, we do have certain methods of collision avoidance and detection, for example, C.S.M.A./C.D. (Carrier Sense Multiple Access/Collision Detection), packet retransmission, etc. However, in the case of wireless technologies, we do not have the means of collision detection and/or packet retransmission, since there is no method of detecting a collision in the air.
Matter of fact, wireless networks are supposed to ensure with certainty that there occur no collisions, due to which only a single device in the RF region may transmit at a time. 802.11 W.L.A.N.s (Wireless Local Area Networks) have methods of doing so, such as CSMA/CA, R.T.S./C.T.S. (Request To Send/Clear To Send), etc. Wireless nodes utilize CSMA/CA. Though often it is required to control the air.
Mechanisms of collision avoidance in RTS/CTS are enabled on hidden endpoints. Hidden endpoints are those nodes that are not in the range of other nodes. A transfer from a wireless node, apart from its data payload, includes an announcement that it is transmitting, as well as an expression of the duration of time for which it needs the air. If nodes X and Y are distant, they may not be able to listen to each other's announcements. If A can not listen to the transmissions of B, both X and Y will infer that the air is free, and if they transfer at the same time collisions will occur. To resolve this issue, RTS/CTS was developed.
Carrier Sense Multiple Access with Collision Avoidance
CSMA/CD is a M.A.C. (Media Access Control) protocol used in LAN. It utilizes the early technology of ethernet to avoid collisions before they occur. CSMA/CD checks the common shared channel if it's busy or not, and defers transfers while the channel is busy. CSMA/CD senses collisions by checking for transmissions from other stations. Once a collision is detected, the station halts transmitting, sending a jam signal. It then waits for an arbitrary amount of time before beginning to retransmit.
CSMA/CA appropriately organizes the data transmissions by regulating the communication over a computer network with a common medium of transfer. CSMA/CA keeps checking for any transmissions from the other stations (nodes) in the channel (shared medium). It starts transmitting once the channel is free of any transmissions. The moment a collision is detected by a station, the transmission is halted and a jam signal is sent by the station, which then waits a certain time duration before it retransmits.
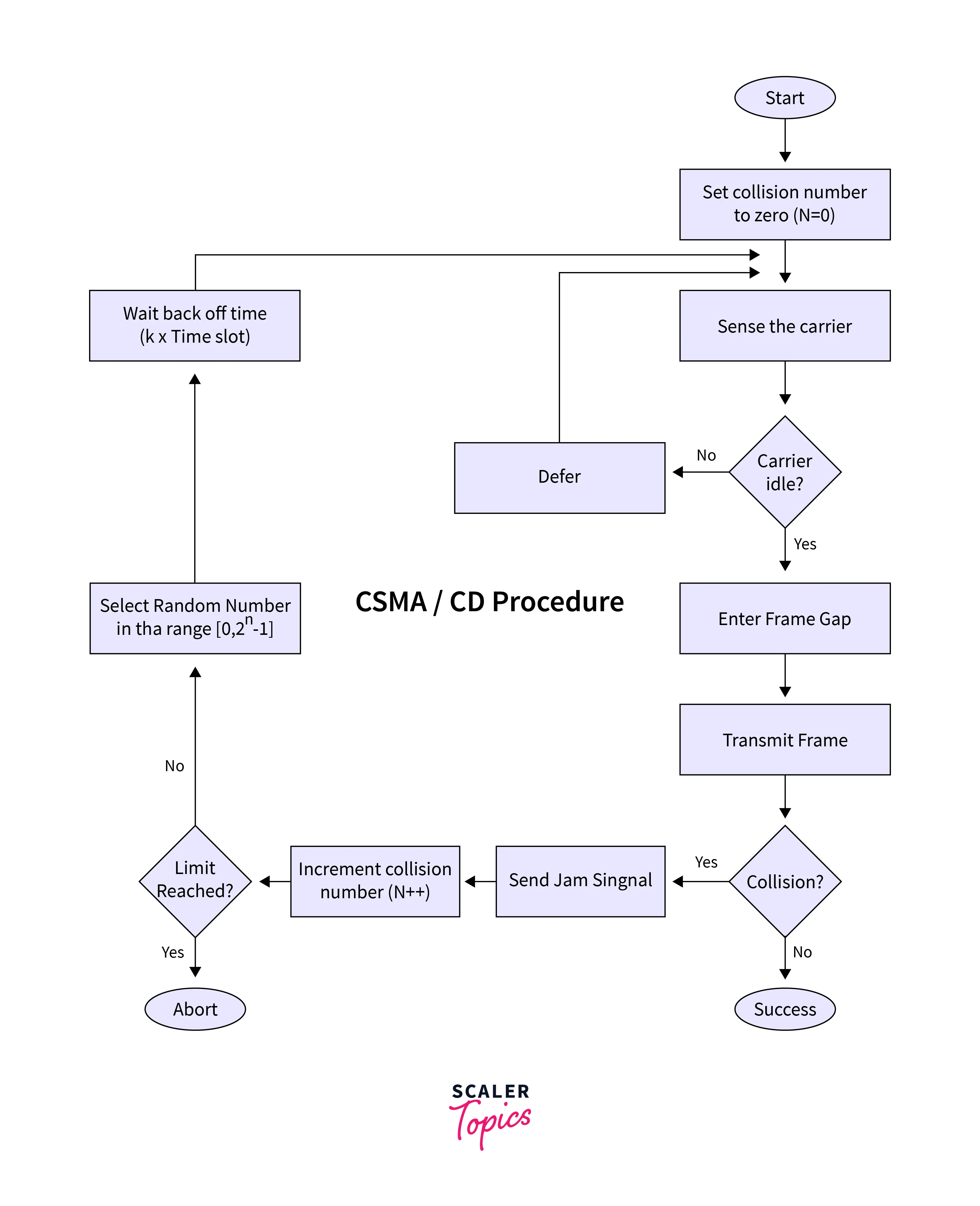
CSMA/CA operates in one of the following four ways:
1. 1-persistent
This is an aggressive algorithm. The shared channel is checked first, and if the channel is found to be free, the data is delivered right away. Otherwise, the station must wait while continually sensing the channel to be cleared. The moment that happens the station must immediately broadcast the frame.
2. Non-Persistent
Before sending the data, the station first checks if the channel is free. If so, the node sends the data immediately. However, if the channel is busy, the station needs to wait for an arbitrary duration of time (not necessarily continuous). Once the station learns that the channel is clear, it transmits the frames.
3. P-Persistent
It is a mix of the Non-Persistent and the 1-Persistent modes. In P-persistent mode, every station assesses the channel. If any station finds the channel to be free, it sends a frame containing a probability ‘p’. In case the data is not transmitted, the frame restarts with the following time slot after having waited for a ‘q’ random period, where:
4. O-Persistent
A supervisory station allocates to each station an order of transmission. Stations wait for their time slot as per their assigned transmission sequence when the transfer medium is clear.
CSMA/CA vs CSMA/CD
| Key | CSMA/CA | CSMA/CD |
|---|---|---|
| Effectiveness | Effective before a collision occurs. | Effective after a collision has occurred. |
| Network Type | Usually used in wireless type networks. | Mostly used in wired kind networks. |
| Recovery Time | Reduces the probability of a collision occurring. | Minimizes the recovery time. |
| Conflict Management | First announces its intention of sending the data. Once an acknowledgment arrives, the transmitter transfers the data. | In case of a conflict occurring during transmission, the data frames are retransmitted. |
| IEEE Standard | Comes under the IEEE 802.11 standard. | Comes under the IEEE 802.3 standard. |
| Efficiency | Relatively less efficient. | Relatively more efficient. |
Working of CSMA/CA
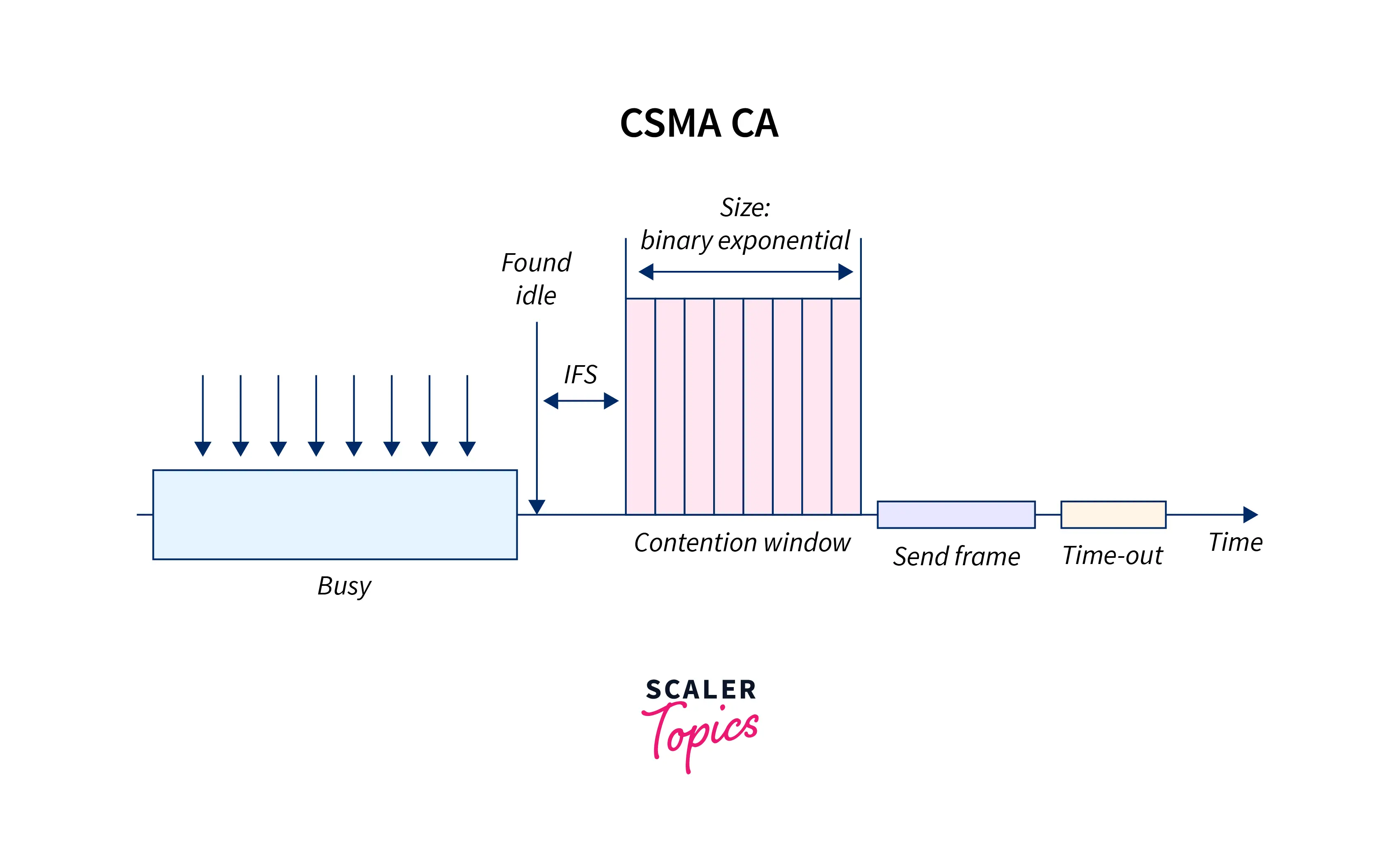
CSMA/CA avoids collisions using the following 3 core techniques:
1. Interframe Space
The station does not immediately transmit on finding the channel to be clear. Rather, it waits for a certain fixed amount of time referred to as I.F.S. (Interframe Space). The reason is that there is a possibility of transmissions having been started from the very same distant station, and the signal from that station has not yet reached the other stations.
Hence, the aim of using IFS time is to enable this transmitted signal to reach the other stations. After the IFS time, if the channel stays idle, the station may send. But it must still wait for a time duration equivalent to the contention time. The priority of a frame or a station can also be defined using the IFS variable.
2. Contention Window
The contention window is a duration of time divided into slots/segments. Any station ready to transmit picks as its wait time, a random number of segments. This number of slots in the contention window alters as per the binary exponential back-off strategy, meaning that the initial value set is 1, doubling every time the station can’t detect a free channel after the IFS time.
In a contention window, the station is required to check the channel at the end of every time slot. If the channel is found to be busy by the station, the process need not be restarted. The station just halts the timer and resumes it once the channel is determined to be cleared.
3. Acknowledgments
Even after having taken so many precautions, there still exists a chance of collisions occurring and destroying the data. The time-out timer as well as the positive acknowledgment may help ensure that the receiver receives the frame.
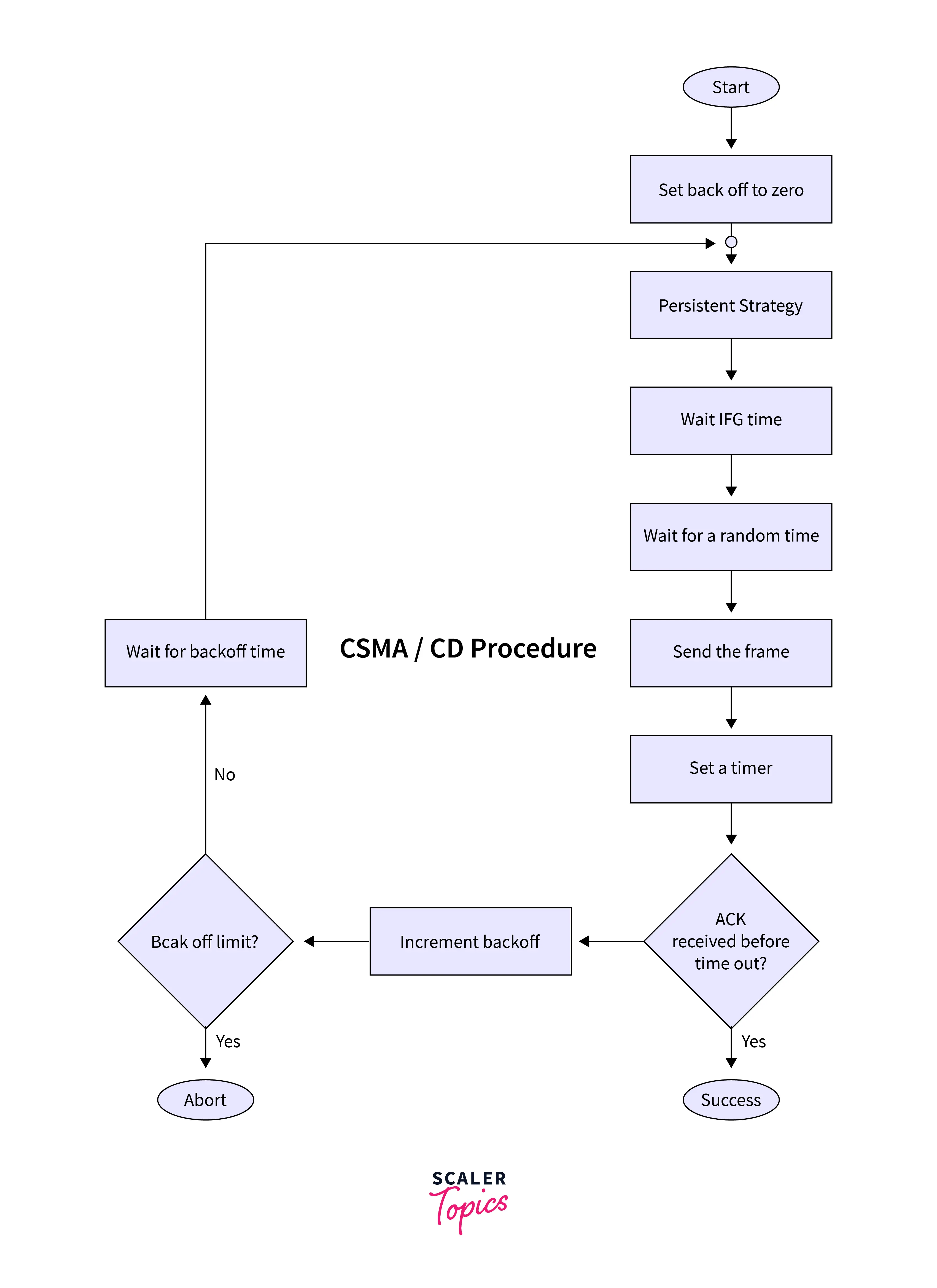
Advantages of Using CSMA/CA
- CSMA/CA aids in preventing data collisions.
- Using the RTS/CTS extension, CSMA/CA avoids data traffic that is unnecessary.
- Hidden node collision is avoided using CSMA/CA.
- CSMA/CA controls the packets and sends them to whoever the receiver wishes to transmit to.
- Larger the data volume, the smaller the probability of a collision occurring.
Disadvantages of Using CSMA/CA
- CSMA/CA does not suit large-scale networks.
- There is a distance limit of 2.5 km, beyond which collision cannot be detected.
- Certain nodes can not be assigned priorities.
- The larger the number of devices, the poorer the performance.
Conclusion
- A collision happens when multiple devices attempt to transfer data via a commonly shared circuit, in which various devices may listen at the same time, but only one device at a time is allowed to transmit data.
- Wireless technologies, unlike their wired counterparts, are mostly half duplex, meaning a wireless device may talk as well as listen, but can not do both things simultaneously.
- CSMA/CD is a MAC protocol used in LAN and utilizes the early technology of ethernet to avoid collisions before they occur.
- CSMA/CA avoids collisions using the following 3 core techniques: interframe space, contention window, and acknowledgment.
- CSMA/CA operates in one of the following 4 modes: 1-persistent, non-persistent, p-persistent, and o-persistent.
