Context-based Access Control
Overview
Context Based Access Control abbreviated as CBAC is part of the Cisco IOS and this functions as an application and stateful firewall and filtering of traffic is performed by it at the different OSI model layers. Traffic Filtering, Traffic Examine, Intrusion Prevention, and alert and audit traits are done by the CBAC.
Introduction
Context Based Access Control abbreviated as CBAC is part of the Cisco IOS and this functions as an application and stateful firewall filtering of traffic is performed by it at the network layer(IP protocols and addresses), Transport layer(UDP and sessions, ports), Session layer(conversation state) and the application layer( particular application protocols). Access-list is abbreviated as ACL and it is a list that defines a set of 8 rules for network traffic control and network attack reduction.
Context-based access control (CBAC) is one of the firewall software features that filters the packets of TCP and UDP intelligently. It performs filtering based on the application layer protocol session information.
What CBAC (Context Based Access Control) Can Do?
Context Based Access Control provides us with the functionality of network protection on various levels with the help of the following functions:
- Intelligent filtering is not provided by CBAC for all the protocols.
- CBAC works for the specified protocols.
- If the protocol is not specified by you for CBAC then how to filter the protocol is decided based on the existing access lists.
- No temporary openings are created for the protocols whose CBAC inspection is not specified.
Traffic Filtering
Only those replies are permitted by CBAC that are in the state table. Traffic originated from the trusted network and the firewall was filtered by it. It has the potential of filtering the traffic intelligently up to layer 7.
Traffic Inspection
Tracking of Information of TCP/UDP needed for the more thorough inspection of packet payload is done by Context Based Access Control.
Alerts and Audit Trails
Information related to the established connections, source and destination IP addresses, and amount of data sent is recorded by the Context Based Access Control mechanism of the router.
Intrusion Prevention
Connection establishment speed is monitored by CBAC for the identification of the attacks such as TCP syn attacks, and DOS attacks. Based on information collected from the monitoring CBAC has the potential of connection dropping or reestablishment for responding to malicious packets.
How CBAC?
CBAC works similarly to the reflexive Access list but the only difference is that in addition the state table is also maintained by it for maintaining the sessions in the memory. When the device within the network initiates the session then in the state table a dynamic entry is put and outgoing (outbound) traffic is permitted to pass through the router(firewall based on the IoS). With the help of this dynamic entry, outbound traffic replies can be passed from the router because there is a traffic entry that is initiated within the network. CBAC mechanism of the firewall based on the IoS allows to achieve this as on the access list temporary holes are opened by it so that it allows the reply packets.
CBAC Configuration
Refer to the below image for the configuration of the CBAC
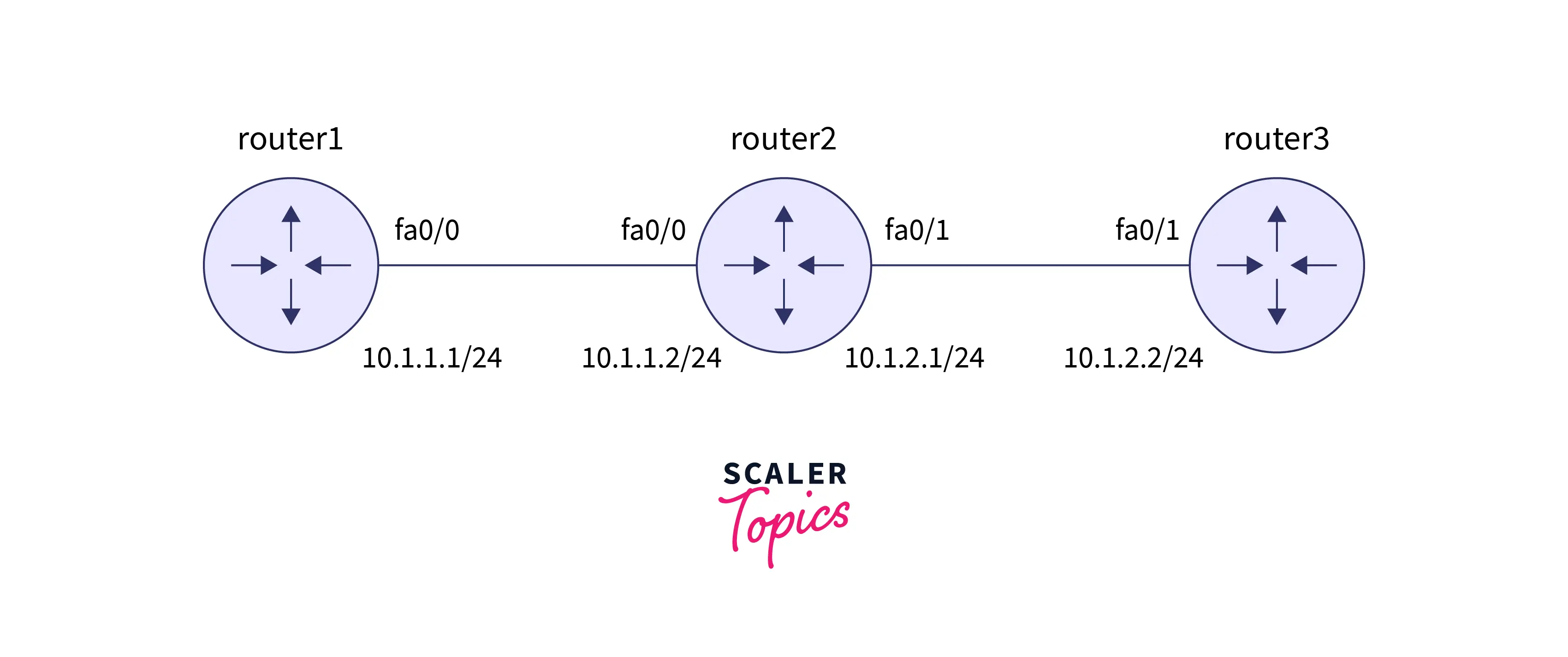
The name of the three routers are given below:
- router1 has 10.1.1.1/24 IP address on the port fa0/0
- router2 has a 10.1.1.2/24 IP address on port fa0/0 and it has a 10.1.2.1/24 IP address on port fa0/1.
- router3 has 10.1.2.2/24 IP address.
Firstly, all the routers get their routes using the Enhanced Interior Gateway Routing Protocol (EIGRP) and this helps the routers ping each other.
Then, we will consider router3 as an SSH server and router2 is the router on which Context Based Access Control performs its operations and it only allows traffic that is checked by router2.
First, we perform router1 EIGRP configuration:
After that, we perform router2 EIGRP configuration so that router2 can reach other networks:
Then, we perform router3 EIGRP configuration.
After it, we perform router3 ssh configuration.
After all this, on router2 we are going to create an Access list. This will not accept any traffic except EIGRP as it makes it possible to reach all the routers in the networks.
Then, perform it to the interface.
As we applied access-list on router1 so it cannot ssh router3 and this access list will not accept any other packet except EIGRP. So now for the inspection of the ssh traffic, we perform the configuration of the CBAC on router2. CBAC operating on the IoS router inspected traffic is allowed only.
The above-given first command !cbac is to enable the feature cbac and for inspection of ssh traffic, we use the second command.
So, now inspection is applied to the interface:
As firstly the router2 inspected the packet of ssh while leaving the outbound interface i.e. fa0/1. So now router1 can ssh the router3.
Verification can be commanded by the following command:
Limitations of CBAC
- Due to the need for detailed protocols and knowledge of how operations are performed, understanding CBAC can be difficult.
- Traffic derived from itself(the router at which we have performed configuration of CBAC) is not inspected by the mechanism of the Context Based Access Control.
- It does not inspect encrypted packets like IPsec.
Conclusion
- Contex Based Access Control abbreviated as CBAC is part of the Cisco IOS and this functions as an application and stateful firewall and filtering of traffic is performed by it at the different OSI model layers.
- Traffic Filtering, Traffic Examine, Intrusion Prevention, and alert and audit traits are done by the CBAC.
- CBAC works similarly to the reflexive Access-list but the only difference is that in addition the state table is also maintained by it.
- In the configuration of the CBAC, initially all the routers get their routes using the Enhanced Interior Gateway Routing Protocol (EIGRP) and this helps the routers ping each other.
- Due to the need for detailed protocols and knowledge of how operations are performed, understanding CBAC can be difficult.
