Deadlock Detection and Recovery in Operating System
Overview
Deadlock occurs when multiple processes are unable to proceed because each one is waiting for a resource held by another. Deadlock detection in OS is a vital strategy to identify such scenarios in an operating system. This process involves periodically examining resource allocation graphs or utilizing various algorithms to identify circular wait conditions. Once detected, recovery methods can be employed, like terminating processes, preempting resources, or rolling back certain operations to break the deadlock. For an in-depth understanding, explore this article by Scaler Topics on Deadlock in operating systems.
What is Deadlock Detection and Recovery in OS?
Deadlock detection and recovery in OS are crucial steps to identify and fix deadlock situations. Deadlocks occur when multiple processes are stuck, each needing resources held by others. This creates a deadlock where no progress can be made.
The strategies for managing deadlock detection and recovery encompass:
Prevention:
This proactive approach involves implementing systematic measures to prevent deadlocks from materializing. The operating system strives to ensure a secure system state that inherently eliminates the possibility of deadlocks. This objective is achieved through sophisticated resource allocation algorithms such as the Banker's Algorithm, which strategically grants resources to processes to avoid potential deadlocks by design. Please refer to this article by Scaler Topics to learn more about Deadlock Prevention in Operating System (OS).
Deadlock Detection and Recovery in OS:
In scenarios where preventive measures are insufficient and deadlocks occur, the operating system needs to adeptly detect and resolve these issues. Deadlock detection algorithms, like the Wait-For Graph algorithm, play a pivotal role in pinpointing the precise processes and resources entangled in deadlock conditions. Following detection, recovery algorithms, exemplified by the Rollback and Abort techniques, step in to address the deadlock. These recovery algorithms systematically release resources held by specific processes involved in the deadlock, effectively dismantling the deadlock state. By doing so, the system reclaims its operability, allowing processes to resume their execution and the system to continue its progress.
How is Deadlock Prevention Different from Deadlock Detection and Recovery in OS?
| Aspect | Deadlock Prevention in OS | Deadlock Detection and Recovery in OS |
|---|---|---|
| Objective | Prevent deadlocks from occurring. | Allow deadlocks to occur, then detect and recover from them. |
| Resource Allocation | Requires careful resource allocation to avoid circular wait, hold and wait, no preemption, and mutual exclusion conditions. | Resources are allocated without stringent conditions; processes may request resources as needed. |
| Complexity | Typically more complex to implement, as it requires stricter allocation policies and resource management. | Less complex to implement, as it focuses on detecting and resolving deadlocks after they occur. |
| Performance Impact | Can affect system performance due to resource allocation constraints and potential delays in acquiring resources. | Detection adds some overhead, and recovery may involve terminating processes, which can impact system performance. |
| Resource Utilization | May lead to underutilization of resources since processes might not get all the resources they need. | Strives to maximize resource utilization, potentially at the cost of increased risk of deadlocks. |
| Process Blocking | Processes may be blocked from starting due to resource unavailability, leading to possible delays. | Processes may be allowed to start even if they can't acquire all resources, but they might later face deadlock situations. |
| Preemption | Generally involves resource preemption, which can be complex and might lead to inefficiencies. | Preemption of resources is not necessary in most cases, allowing for smoother process execution. |
| Proactive vs. Reactive | Proactively prevents deadlocks before they occur by imposing constraints on resource allocation. | Reactively detects deadlocks once they happen and takes actions to resolve them. |
| System Responsiveness | Can improve system responsiveness by reducing the chances of deadlocks and the need for recovery. | May require system downtime or process termination for recovery, impacting overall responsiveness. |
| Compatibility | May not be suitable for all systems or applications, especially those with dynamic resource needs. | Suitable for a wide range of systems and applications since it handles deadlocks reactively. |
Deadlock Detection
Deadlock detection in OS is a critical concept in computer science and operating systems that deals with the potential problem of deadlocks in concurrent systems. A deadlock occurs when two or more processes are unable to proceed with their execution because each process is waiting for a resource that is held by another process within the same system. This situation results in a standstill where no process can make progress, effectively halting the system's functionality.
Causes of Deadlocks:
- Mutual Exclusion:
At least one resource must be held in a non-sharable mode. This means that only one process can use the resource at a time. - Hold and Wait:
A process must be holding at least one resource and waiting to acquire additional resources at the same time. - No Preemption:
Resources cannot be forcibly taken away from a process; they can only be released voluntarily. - Circular Wait:
A circular chain of two or more processes exists, where each process is waiting for a resource held by the next process in the chain.
Deadlock Detection in OS Strategies:
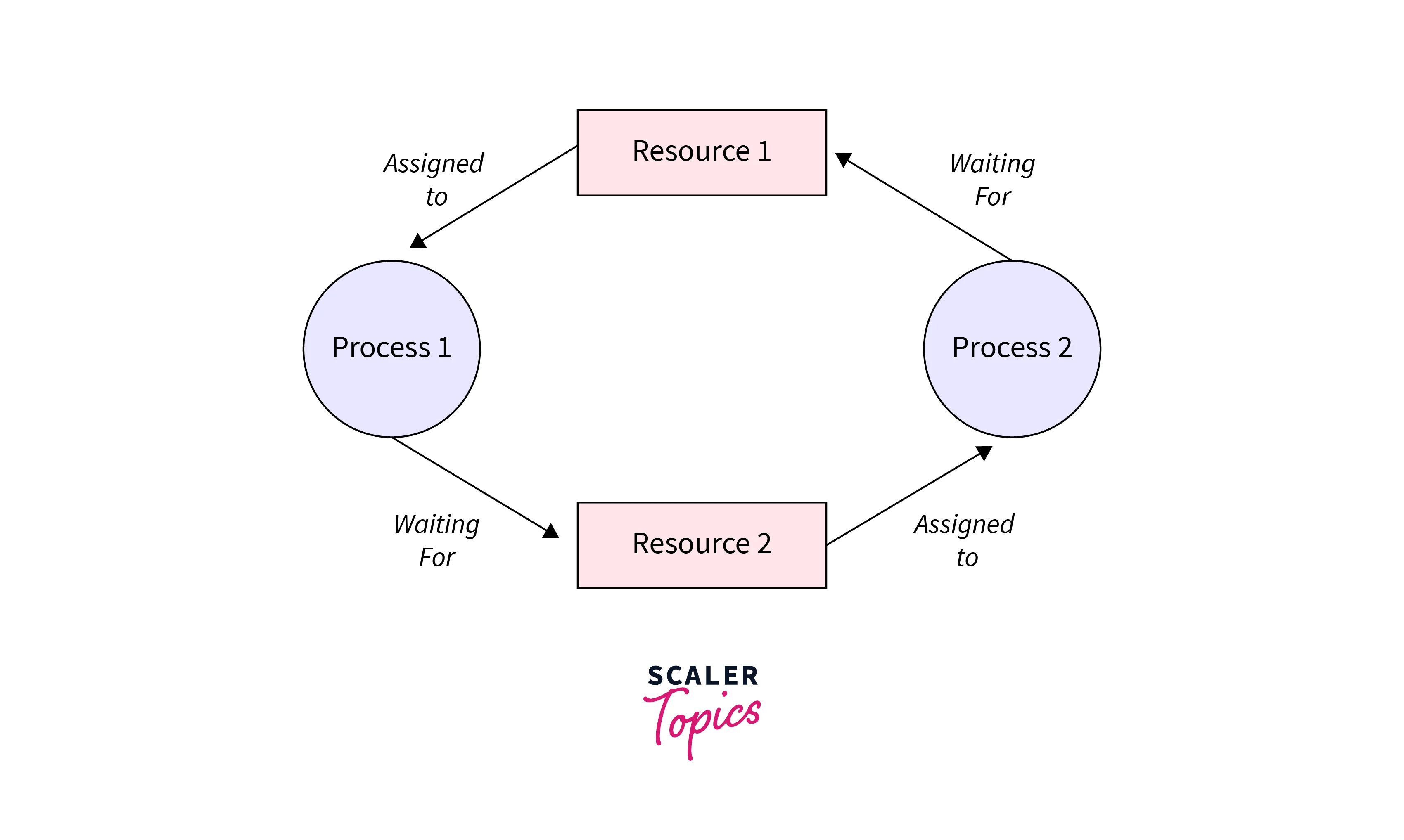
- Resource Allocation Graph:
This method represents the resources and processes as nodes in a graph, with edges representing resource requests and allocations. Deadlocks can be detected by identifying cycles in the graph. - Wait-Die and Wound-Wait Schemes:
These schemes are used in resource management systems where older processes can preempt resources from younger processes (Wound-Wait) or vice versa (Wait-Die). These strategies help to prevent potential deadlocks. - Banker's Algorithm:
This algorithm is used to determine if a resource allocation will lead to a safe state, where a safe state ensures that all processes can complete their execution without getting stuck in a deadlock. - Timeout Mechanisms:
Processes are given a certain time limit to complete their execution. If they fail to complete within the time limit, their allocated resources are released, preventing potential deadlocks. - Periodic Checking:
In this approach, the system periodically checks for potential deadlocks by analyzing the state of resources and processes. If a deadlock is detected, appropriate actions are taken.
Advantages of Deadlock Detection in OS:
- Prevents Hangs:
Detects and resolves deadlocks, preventing system freezes. - Optimizes Allocation:
Identifies inefficient resource usage and reallocates for efficiency. - Dynamic Allocation:
Responds to real-time demands, improving responsiveness. - Minimizes Impact:
Reduces disruptions, enhancing user experience. - Predictable Behavior:
Enables better management and predictability. - Monitors Health:
Provides insights, aids performance optimization. - Reclaims Resources:
Frees locked resources, increasing availability.
Limitations of Deadlock Detection:
- Detection Overhead:
Adds computational burden due to continuous monitoring. - Delayed Resolution:
Only responds after deadlock occurs, not preventing it. - Resource Usage:
Consumes additional system resources for monitoring. - Complexity:
Requires careful design and tuning, adding complexity. - Potential False Positives:
Can detect non-deadlock situations as deadlocks.
Deadlock Recovery
Deadlock recovery is a process in computer science and operating systems that aims to resolve or mitigate the effects of a deadlock after it has been detected. Deadlocks are situations where multiple processes are stuck and unable to proceed because each process is waiting for a resource held by another process. Recovery strategies are designed to break this deadlock and allow the system to continue functioning.
Recovery Strategies:
- Process Termination:
One way to recover from a deadlock is to terminate one or more of the processes involved in the deadlock. By releasing the resources held by these terminated processes, the remaining processes may be able to continue executing. However, this approach should be used cautiously, as terminating processes could lead to loss of data or incomplete transactions. - Resource Preemption:
Resources can be forcibly taken away from one or more processes and allocated to the waiting processes. This approach can break the circular wait condition and allow the system to proceed. However, resource preemption can be complex and needs careful consideration to avoid disrupting the execution of processes. - Process Rollback:
In situations where processes have checkpoints or states saved at various intervals, a process can be rolled back to a previously saved state. This means that the process will release all the resources acquired after the saved state, which can then be allocated to other waiting processes. Rollback, though, can be resource-intensive and may not be feasible for all types of applications. - Wait-Die and Wound-Wait Schemes:
As mentioned in the Deadlock Detection in OS section, these schemes can also be used for recovery. Older processes can preempt resources from younger processes (Wound-Wait), or younger processes can be terminated if they try to access resources held by older processes (Wait-Die). - Kill the Deadlock:
In some cases, it might be possible to identify a specific process that is causing the deadlock and terminate it. This is typically a last resort option, as it directly terminates a process without any complex recovery mechanisms.
Advantages of Deadlock Recovery:
- Resumes Processes:
Terminates deadlock-involved processes, allowing others to continue. - Reclaims Resources:
Releases resources, improving allocation. - Minimizes Downtime:
Swiftly resolves deadlocks, reducing system downtime. - User Transparent:
Shields users from deadlock complexities. - Ensures Stability:
Prevents prolonged hangs, enhances system stability. - Optimizes Utilization:
Redistributes resources for efficient use. - Automated Resolution:
Swift, automated recovery from deadlocks. - Boosts Fault Tolerance:
Contributes to system reliability and fault tolerance.
Limitations of Deadlock Recovery:
- Process Termination:
May terminate processes, affecting user tasks. - Resource Waste:
Terminated processes release resources, causing waste. - User Impact:
Interruption to users due to process termination. - Unfairness:
Selecting processes to terminate may seem arbitrary. - Automated Risks:
Automated recovery decisions might not be optimal.
FAQs
Q. How does deadlock detection work?
A. Deadlock detection involves periodically analyzing the resource allocation graph to identify if any cycles (deadlock situations) exist among processes.
Q. What is the aim of deadlock recovery?
A. Deadlock recovery aims to resolve the deadlock once detected. This can involve techniques like process termination, resource preemption, or killing processes to break the deadlock.
Q. Is deadlock recovery always a viable solution?
A. Deadlock recovery can have downsides, such as potential loss of data or increased system complexity. It's often considered a last resort, with prevention strategies being preferable to avoid deadlocks altogether.
Conclusion
- Deadlocks can severely impact system stability and resource utilization, necessitating robust strategies for detection and recovery in operating systems.
- Various deadlock detection algorithms, like resource allocation graphs and bankers' algorithm, help identify potential deadlock situations by analyzing resource allocation and request patterns.
- Deadlock detection minimizes resource wastage by allowing the system to take timely action, releasing resources held by one or more processes stuck in a deadlock.
- Recovery techniques involve terminating processes, releasing resources, and subsequently allowing waiting processes to proceed, ensuring system continuation and freeing up locked resources.
- Deadlock detection incurs computational overhead, potentially affecting system performance, but it's crucial to maintain system integrity and prevent prolonged resource blockage.
- While detection and recovery are essential, combining them with prevention strategies like resource allocation policies and process prioritization is key to minimizing the occurrence of deadlocks in the first place.
