Encryption and Decryption
Overview
In the realm of modern technology, the terms "encryption" and "decryption" are omnipresent, and they form the bedrock of secure communication and data protection. In this comprehensive exploration of encryption and decryption, we will delve into the fundamentals, techniques, and key concepts that underpin this critical aspect of information security.
Encryption and decryption are essential processes for ensuring the confidentiality and integrity of sensitive information in digital communication. Encryption involves transforming plaintext data into an unreadable format, known as ciphertext, using an encryption algorithm and a secret key. Decryption, on the other hand, is the reverse process; it converts ciphertext back into plaintext using a decryption algorithm and the same secret key.
Shared Key and Public Key Encryption
Shared Key Encryption
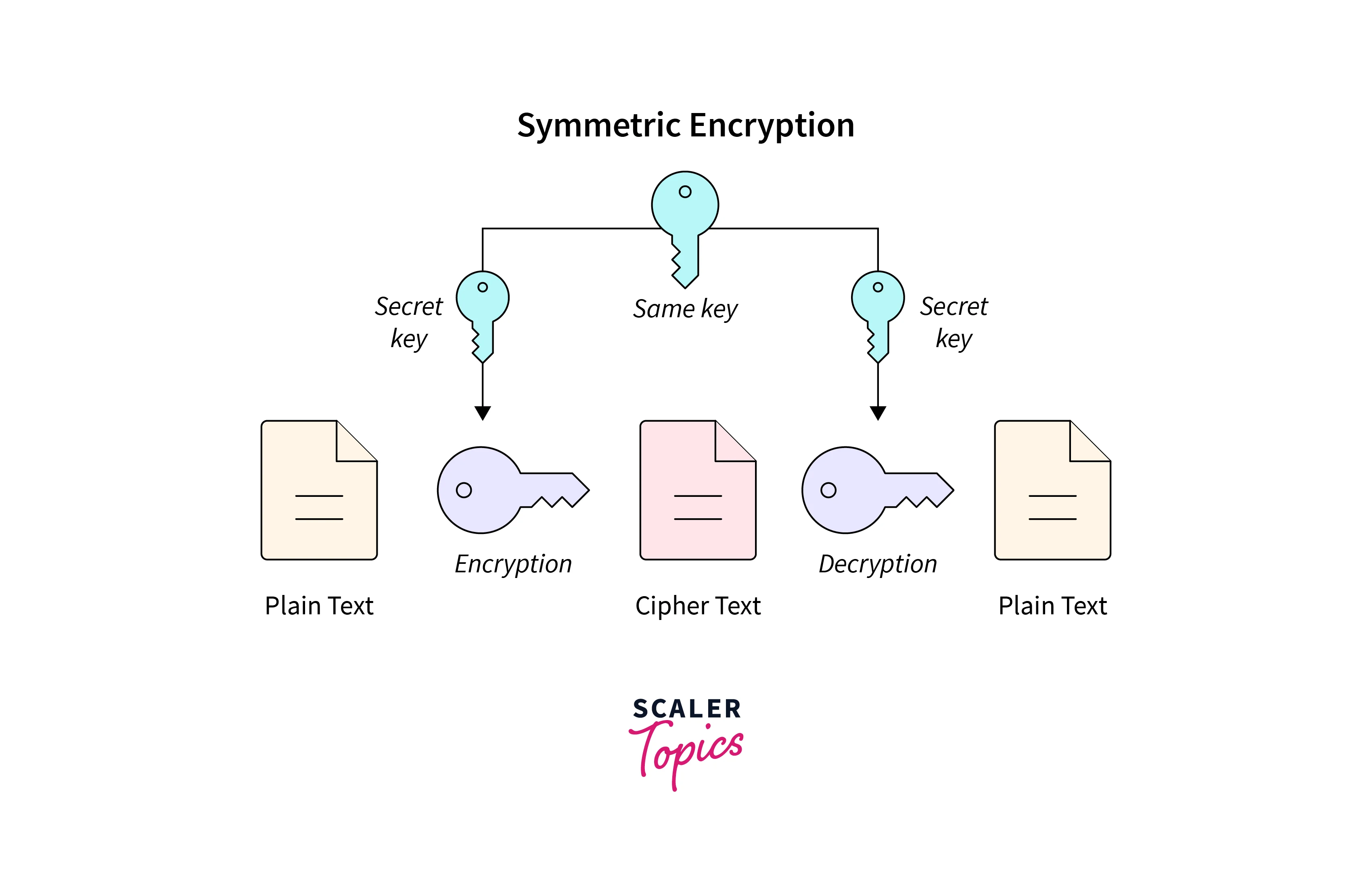
Shared key encryption, also known as symmetric encryption, employs a single secret key to both encrypt and decrypt data. This key is shared between the sender and the receiver. The most significant advantage of shared key encryption is its efficiency, as it is generally faster than public key encryption.
To illustrate this process, imagine two parties, Alice and Bob, who wish to communicate securely over an insecure channel. They both possess the same secret key. When Alice wants to send a message to Bob, she uses this shared key to encrypt the message, creating ciphertext. Upon receiving the ciphertext, Bob employs the same key to decrypt it, revealing the original message.
However, shared key encryption has a critical limitation - key distribution. For Alice and Bob to communicate securely, they must securely share the key beforehand. This can be challenging, especially in large networks or over the internet.
Public Key Encryption
Public key encryption, also known as asymmetric encryption, uses a pair of keys: a public key for encryption and a private key for decryption. These keys are mathematically related but cannot be derived from one another. This provides a powerful advantage - anyone can use the public key to encrypt a message, but only the holder of the private key can decrypt it.
In our scenario, Alice and Bob each have a pair of public and private keys. Alice shares her public key with anyone who wants to send her an encrypted message. When Bob wants to send an encrypted message to Alice, he uses her public key to encrypt it. Only Alice, who holds the corresponding private key, can decrypt and read the message.
Public key encryption elegantly addresses the key distribution problem of shared key encryption. However, it tends to be slower due to the complexity of the encryption and decryption processes.
Diffie-Hellman Key Exchange
The Diffie-Hellman Key Exchange, named after its inventors Whitfield Diffie and Martin Hellman, is a pivotal protocol that enables two parties to securely exchange cryptographic keys over an untrusted network. This exchange occurs without actually sharing the secret key. This shared secret can then be used to establish secure communication channels, ensuring the confidentiality and integrity of data exchanged between the parties.
The Diffie-Hellman protocol operates on the mathematical principles of modular exponentiation. Two parties, Alice and Bob, agree on two publicly known numbers, a prime number 'p' and a primitive root 'g' modulo 'p'. Each party also privately selects their secret exponent - Alice chooses 'a', and Bob selects 'b'.
They then compute the following:
- Alice computes A = g^a mod p.
- Bob computes B = g^b mod p.
Alice and Bob exchange 'A' and 'B' with each other. Using their respective secret exponents and the values received from the other party, they can independently compute the shared secret key:
- Alice computes s = B^a mod p.
- Bob computes s = A^b mod p.
Remarkably, both parties now possess the same secret keys 's', which they can use for shared key encryption. Even if an eavesdropper intercepts 'A' and 'B', deriving 'a' or 'b' from these values is computationally infeasible, ensuring the security of the key exchange.
Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) is a property of cryptographic systems that guarantees that the compromise of a single encryption key will not compromise past or future communications. In essence, it provides a higher level of security by ensuring that even if an attacker gains access to the encryption keys, they cannot decrypt past or future communications.
PFS is particularly crucial in scenarios where long-term keys are used, such as with public key infrastructure (PKI) and secure messaging applications. By continually generating new session keys for each communication session, PFS ensures that past communications remain confidential, even if the session keys are compromised. This property is essential for protecting sensitive information and maintaining the security of encrypted communications in various secure communication protocols.
Implementing Perfect Forward Secrecy requires careful key management and the use of specific cryptographic protocols. When two parties want to establish a secure communication channel, they generate temporary session keys that are discarded after the session ends. This prevents attackers from retroactively decrypting previously intercepted traffic even if they later acquire the private keys. Widely used in secure messaging apps, PFS adds an extra layer of protection to sensitive data and addresses the vulnerabilities associated with relying solely on static, long-term encryption keys.
Encryption Algorithms
Here is a table summarizing some common encryption algorithms used in the field of encryption and decryption:
| Encryption Algorithm | Key Type | Example Use Case |
|---|---|---|
| AES (Advanced Encryption Standard) | Shared Key | Secure file storage and transmission |
| RSA (Rivest-Shamir-Adleman) | Public Key | Secure email communication |
| DES (Data Encryption Standard) | Shared Key | Legacy encryption for data protection |
| ECC (Elliptic Curve Cryptography) | Public Key | Efficient encryption for IoT devices |
| Blowfish | Shared Key | Secure network communication |
1. AES (Advanced Encryption Standard):
AES, also known as Rijndael, is one of the most widely used symmetric encryption algorithms. It operates on blocks of data and supports key lengths of 128, 192, or 256 bits. AES is known for its security, efficiency, and speed, making it suitable for various applications, including secure communication and data encryption.
2. RSA (Rivest-Shamir-Adleman):
RSA is a widely used public key encryption algorithm that relies on the mathematical properties of large prime numbers. It uses a pair of keys: a public key for encryption and a private key for decryption. RSA is commonly used for secure email communication, digital signatures, and key exchange protocols like SSL/TLS.
3. DES (Data Encryption Standard):
DES was one of the earliest encryption standards. It uses a 56-bit key to encrypt data in 64-bit blocks. While it was widely used in the past, DES is considered relatively weak by today's standards due to its short key length. Triple DES (3DES) is a variant that applies DES encryption three times in succession for improved security.
4. ECC (Elliptic Curve Cryptography):
ECC is a public key cryptography system that relies on the algebraic structure of elliptic curves over finite fields. It offers strong security with shorter key lengths compared to traditional RSA encryption. ECC is particularly popular in resource-constrained environments, such as IoT devices.
5. Blowfish:
Blowfish is a shared key encryption algorithm in which the user-provided encryption key is expanded into an array of subkeys using a key expansion algorithm. This process creates a series of subkeys used in subsequent encryption and decryption. Blowfish generates a large number of subkeys, each 32 bits long, from the original encryption key. Blowfish is considered secure and has undergone extensive cryptanalysis without significant vulnerabilities discovered. It offers flexibility with variable key lengths (32 to 448 bits) to cater to different security needs.
Difference between Encryption and Decryption
Here's a table highlighting the key differences between encryption and decryption:
| Aspect | Encryption | Decryption |
|---|---|---|
| Purpose | Converts plaintext into ciphertext for security | Converts ciphertext back into plaintext |
| Process | Uses encryption algorithm and secret key | Uses decryption algorithm and the same secret key |
| Keys | In shared key, a single key is used | In public key, a public-private key pair is used |
| Efficiency | Generally faster (especially in shared key) | Slower due to complexity (public key) |
| Key Distribution | Requires secure sharing of the secret key | No need for key sharing, uses recipient's public key |
| Security | Vulnerable if the secret key is compromised | Secure as long as the private key remains secret |
SKIP Certificates
SKIP (Simple Key Management for Internet Protocols) Certificates are a critical component of securing Internet communication. They are used to establish trust between entities in a network and ensure the authenticity of data transmission. These are digital credentials that authenticate network entities and enable secure communication in an SKIP deployment. They are issued by trusted CAs, contain key information, and are essential for establishing trust, ensuring data security, and preventing unauthorized access in networked environments.
SKIP certificates come in two types - signed and unsigned.
Signed
Signed SKIP Certificates are digitally signed by a trusted certificate authority (CA). These certificates provide a robust mechanism for authenticating the identity of network entities. When a certificate is signed by a CA, it attests that the public key within the certificate indeed belongs to the entity claimed in the certificate. This prevents malicious actors from impersonating trusted entities.
Unsigned
Unsigned SKIP Certificates lack the CA's digital signature but still serve a purpose. They are useful in scenarios where a centralized authority is not available or practical. While unsigned certificates may not provide the same level of trust as signed certificates, they can still be used to establish secure communication between peers in a network.
Certificate Discovery
Certificate discovery is the process of locating and validating certificates in a network. This is crucial for ensuring secure communication, especially when dealing with signed SKIP certificates. Certificate discovery mechanisms enable parties to verify the authenticity of the certificates presented by other entities. It plays a pivotal role in the establishment of trust and security within a networked environment. It involves the process of identifying, locating, and validating digital certificates, which are essential for ensuring secure communication, particularly when dealing with signed SKIP certificates.
Methods of Certificate Discovery:
- Certificate Authorities (CAs):
Many networks and systems rely on trusted Certificate Authorities to issue and manage digital certificates. Certificate discovery often involves querying CA repositories or directories to obtain the necessary certificates. CAs are responsible for verifying the identity of certificate holders before issuing certificates, adding a layer of trust. - Online Certificate Status Protocol (OCSP):
OCSP is a protocol used to check the validity and status of digital certificates in real time. When entities want to verify the validity of a certificate, they can send an OCSP request to the certificate issuer's OCSP responder, which provides a signed response indicating whether the certificate is still valid. - Certificate Revocation Lists (CRLs):
CRLs are periodically updated lists maintained by CAs that contain information about revoked certificates. Certificate discovery may involve checking these lists to ensure that a certificate has not been revoked before trusting it. - Local Certificate Stores:
In some cases, certificates are stored locally on devices or systems. Certificate discovery involves searching these local repositories for the required certificates. This approach is often used when entities within a closed network need to communicate securely. - LDAP Directories:
Lightweight Directory Access Protocol (LDAP) directories are commonly used to store and retrieve digital certificates. Entities can search LDAP directories to discover and validate certificates. - Certificate Discovery Protocols:
Some network protocols and applications incorporate certificate discovery as an inherent part of their operation. For example, in the context of email encryption, the S/MIME (Secure/Multipurpose Internet Mail Extensions) protocol uses certificate discovery to find and validate public keys for email recipients.
Certificate Chain Validation:
In addition to discovering certificates, the process often includes certificate chain validation. This ensures that a presented certificate is part of a valid certificate chain, starting from a trusted root certificate. Each certificate in the chain is validated, including checking for revocation status, to establish trust.
In conclusion, certificate discovery is a critical component of secure communication and trust establishment within networks. By locating and validating certificates, entities can verify the authenticity of their communication partners and protect against impersonation and unauthorized access, especially when dealing with signed certificates like those used in SKIP (Simple Key Management for Internet Protocols) and other security protocols.
Name Space Identifiers
Name Space Identifiers (NSIs) are used in SKIP to uniquely identify network entities. These identifiers ensure that the correct entity is being communicated with, further enhancing the security of data transmission. Here's an explanation of NSIs and their significance:
1. Unique Identifiers:
NSIs serve as unique identifiers for various entities in a SKIP network. These entities can include devices, users, or services that participate in secure communications within the network.
2. Preventing Ambiguity:
In a network where multiple entities may have similar or identical names or addresses, NSIs help avoid ambiguity. By assigning unique NSIs to each entity, SKIP ensures that there is no confusion when identifying and communicating with specific network participants.
3. Enhanced Security:
NSIs contribute to the security of SKIP communications by making it difficult for attackers to impersonate or intercept messages intended for a specific entity. Since NSIs are unique and specific, it becomes challenging for malicious actors to manipulate or misuse them.
4. Namespace Management:
SKIP relies on a namespace management mechanism to assign and maintain NSIs. This mechanism ensures that NSIs are distributed and managed securely within the network.
5. Flexibility:
NSIs can take various forms, such as alphanumeric strings or numerical identifiers, depending on the namespace management policy in place. This flexibility allows organizations to adapt NSIs to their specific needs and naming conventions.
6. Mapping to Public Keys:
In many cases, NSIs are associated with the public keys of the entities they represent. This association facilitates secure communication and allows parties to verify the authenticity of the public key associated with a specific NSI.
7. Scalability:
NSIs are designed to scale with the size and complexity of the network. As the network expands and more entities join, new NSIs can be assigned to maintain uniqueness.
8. Namespace Hierarchies:
SKIP may employ namespace hierarchies to organize NSIs in a structured manner. This hierarchical approach can make it easier to manage and route communications within the network.
9. Trust and Verification:
NSIs can be used as a basis for trust and verification. When a network entity presents its NSI along with its associated public key, other entities can use this information to validate the entity's identity and authenticity.
In summary, Name Space Identifiers (NSIs) are essential components of the SKIP protocol suite, providing unique and secure identification for entities within a network. They contribute to the prevention of ambiguity, enhance security, and facilitate the trust and verification processes in secure communications. By assigning and managing NSIs effectively, SKIP helps ensure the integrity and authenticity of network participants, making it a valuable tool for securing Internet communications.
SKIP Tunnels
SKIP Tunnels are a mechanism used to establish secure communication channels within a network. They provide a means to encapsulate and protect data as it traverses the internet or other potentially insecure channels. These tunnels help ensure the confidentiality and integrity of data as it moves between network nodes. They offer several features that enhance security, including:
Centralized Decryption
SKIP Tunnels can be configured to allow centralized decryption of traffic. Centralized decryption allows for the decryption of encrypted data at a specific central point within a network. This is useful for network monitoring and security analysis, as it enables authorized entities to inspect encrypted traffic for potential threats. It simplifies the monitoring and analysis of network traffic, making it easier to identify security issues.
Topology Hiding
SKIP Tunnels can hide the network topology, making it difficult for external entities to gain insights into the structure of the network. This adds a layer of security by preventing attackers from mapping the network. Topology hiding can be achieved through various means, such as using private IP address ranges, network address translation (NAT), or employing encryption within the network. By hiding the network topology, it becomes more challenging for attackers to map the network, making it less vulnerable to attacks that rely on knowledge of the network layout.
Prevention of Packet Fragmentation
In some cases, attackers may attempt to exploit packet fragmentation to compromise security. SKIP Tunnels can be configured to prevent packet fragmentation, thwarting such attacks. Prevention of packet fragmentation is a network security practice aimed at thwarting attacks that take advantage of packet fragmentation in the network. Prevention methods may include setting maximum packet size limits, enforcing strict packet size constraints, or configuring network devices to discard fragmented packets.
Preventing packet fragmentation helps maintain the integrity and security of network traffic by closing potential security loopholes. It reduces the risk of attacks that rely on manipulating fragmented packets, such as buffer overflow attacks or evasion techniques.
Conclusion
- Encryption and decryption are fundamental processes for securing digital communication.
- Shared key encryption uses a single secret key for both encryption and decryption, while public key encryption uses a pair of keys - public and private.
- The Diffie-Hellman Key Exchange is critical for securely sharing encryption keys over an untrusted network.
- Perfect Forward Secrecy ensures that past and future communications remain confidential even if encryption keys are compromised.
- Encryption algorithms like AES, RSA, and ECC serve various use cases.
- SKIP Certificates, both signed and unsigned, are vital for authenticating entities in a network.
- Certificate discovery, namespace identifiers, and SKIP tunnels enhance the security of network communication.
