What is Pluggable Authentication Module in Linux?
The Pluggable Authentication Module (PAM) in Linux is a dynamic and flexible authentication framework that allows administrators to configure and control the authentication process for various applications and services on a Linux system. PAM provides a standardized interface for authentication, enabling system administrators to define authentication policies and rules that suit their specific security requirements.
At its core, Pluggable Authentication Module Linux operates as a set of shared libraries, offering a modular architecture for handling user authentication. Upon a user's attempt to access a service or application, PAM intervenes to verify the user's identity and either grants or denies access, depending on the defined authentication policies.
The primary goal of PAM is to separate the authentication mechanism from the applications that need authentication, making it easier to manage and customize the authentication process across the entire system. In this manner, PAM enhances security by allowing the implementation of changes to authentication policies without requiring alterations to the applications themselves.
PAM allows system administrators to configure various authentication methods, such as traditional password-based authentication, smart card authentication, fingerprint recognition, or even two-factor authentication. These authentication methods can be combined or customized to create a robust and layered security approach, ensuring that only legitimate users can access the system resources.
In summary, Pluggable Authentication Module in Linux provides a powerful and flexible framework for managing authentication in a modular and centralized manner. It empowers system administrators to enforce security policies tailored to their specific needs, enhancing the overall security posture of Linux systems. By decoupling the authentication process from applications, PAM ensures a standardized and efficient approach to user authentication, contributing to a more secure and manageable computing environment.
Advantages of PAM
Let's explore the key advantages of the Pluggable Authentication Module and understand how it contributes to creating a more robust and secure computing environment.
- Modular Architecture: PAM's modular design allows for easy integration of multiple authentication methods and policies. Administrators can choose from authentication modules, enabling a tailored and layered security approach.
- Centralized Management: PAM provides a centralized location for managing authentication policies. It simplifies the administration process by enabling system-wide application of changes without requiring modifications to individual applications.
- Enhanced Security: PAM minimizes the risk of security vulnerabilities by separating authentication from applications. Swift implementation of system-wide authentication updates further bolsters system security.
- Flexibility and Customization: PAM grants administrators the freedom to tailor the authentication process to meet precise security requirements. They can combine various authentication methods or create new ones to fit the organization's needs.
- Support for Two-Factor Authentication: PAM supports two-factor authentication, adding an extra layer of security to user logins. It significantly reduces the risk of unauthorized access.
- Adaptability to New Technologies: PAM's design facilitates seamless integration of emerging authentication technologies. It remains adaptable to future advancements, ensuring continued robustness in the face of evolving security threats.
- Compatibility with Multiple Applications: PAM's standardized interface makes it compatible with applications and services. This cross-compatibility streamlines the authentication process across the system.
- Auditability and Accountability: PAM enables the logging of authentication activities, creating an audit trail for security analysis and compliance purposes. It enhances accountability and aids in detecting potential security breaches.
In conclusion, the Pluggable Authentication Module in Linux offers numerous advantages that contribute to a more secure and manageable authentication process.
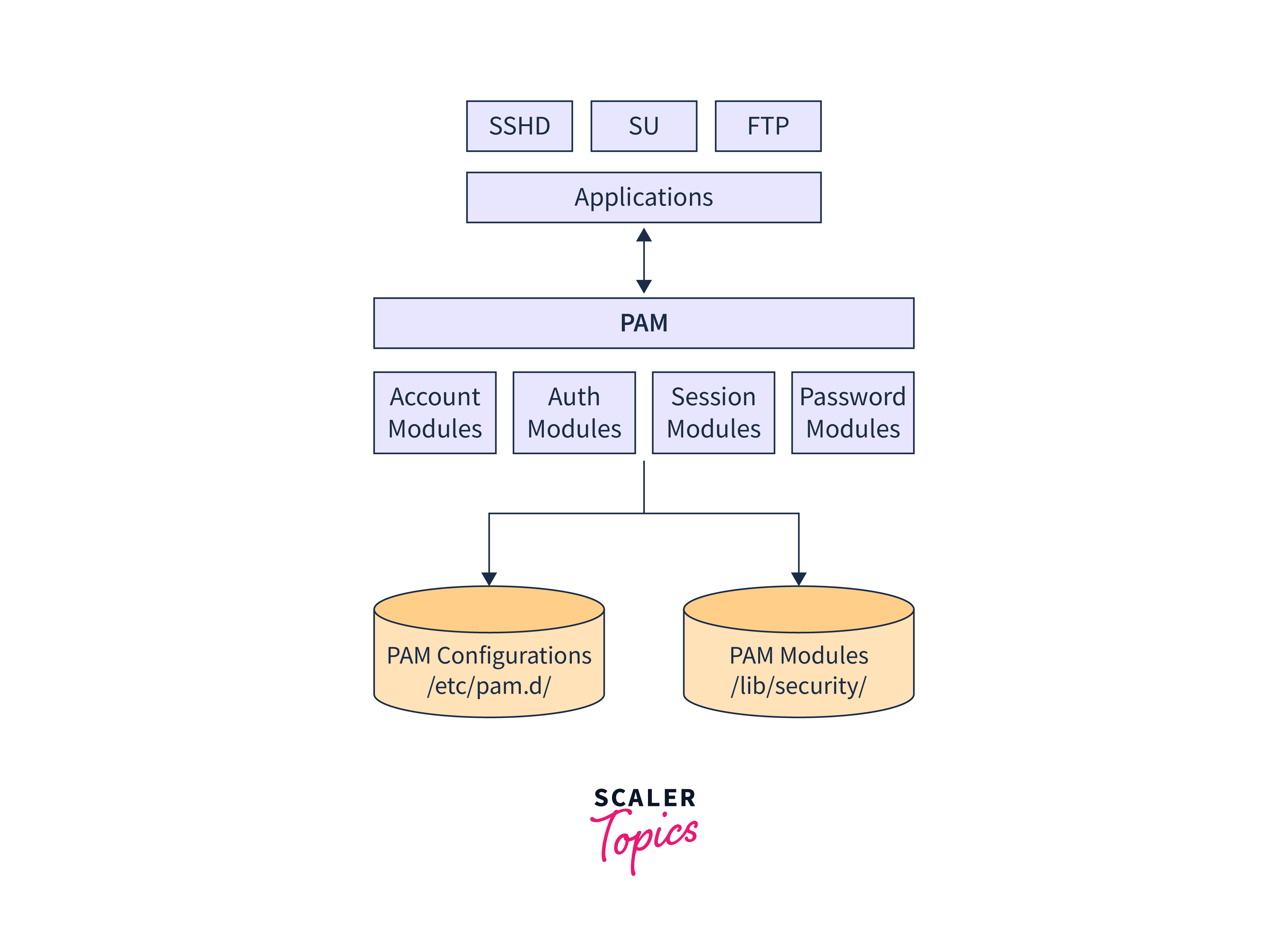
Components of Pluggable Authentication Module Linux
The Pluggable Authentication Module Linux comprises several key components provide a flexible and robust authentication framework. Each plays a vital role in the authentication process, contributing to the overall security and manageability of the system.
-
Authentication Modules At the PAM's core lies a collection of authentication modules, each responsible for handling a specific authentication method. These modules can range from traditional password-based authentication to more advanced methods like biometric authentication, smart card authentication, or two-factor authentication. Administrators can select and configure the appropriate modules to create a tailored authentication scheme that meets their security requirements.
-
Configuration Files PAM utilizes configuration files in the /etc/pam.d/ directory to define the authentication rules and policies for individual services and applications. Each application has it's dedicated configuration file, allowing administrators to customize the authentication process independently for different services. This separation of configurations ensures fine-grained control over authentication policies.
-
PAM Library The PAM library, represented by the libpam module, acts as the interface between the application and the authentication modules. When an application invokes the PAM library, it triggers the authentication process, which then calls upon the specified authentication modules based on the configuration. The PAM library handles the communication between the application and the modules seamlessly.
-
PAM-Aware Applications For PAM to function effectively, applications must be PAM-aware. PAM-aware applications integrate the PAM library calls within their authentication routines, allowing PAM to intervene during the authentication process. Thankfully, most modern Linux applications are PAM-aware, guaranteeing compatibility with PAM.
-
PAM Conversations PAM conversations facilitate communication between the PAM library and the user during authentication. This interaction can involve prompting the user for credentials or displaying relevant messages during authentication. PAM conversations provides a user-friendly experience while maintaining security.
-
PAM Configuration Directives Within the configuration files, administrators can utilize PAM configuration directives to control the behaviour of the authentication modules. These directives determine how PAM should respond in different situations, such as authentication success, failure, or error conditions. This fine-grained control enables administrators to customize the authentication process extensively.
In conclusion, the various components of Pluggable Authentication Module Linux work together harmoniously to deliver a versatile and secure authentication framework.
Conclusion
In conclusion, Pluggable Authentication Module Linux is a powerful and adaptable authentication framework offering a standardized interface for managing authentication processes across diverse applications and services.
Here are the key takeaways from the article:
- PAM's modular architecture allows administrators to integrate multiple authentication methods, creating a tailored and layered security approach.
- Centralized management of authentication policies simplifies administration and facilitates swift system-wide updates without modifying individual applications.
- The separation of authentication from applications minimizes security vulnerabilities, enhancing the system's security.
- PAM provides flexibility and customization options, empowering administrators to adapt the authentication process to specific security requirements.
- Support for two-factor authentication adds an extra layer of security to user logins, mitigating the risk of unauthorized access.
- PAM remains adaptable to emerging authentication technologies, ensuring compatibility with future advancements.
- Its standardized interface enables cross-compatibility with various applications, streamlining the authentication process across the system.
- Logging of authentication activities creates an audit trail for security analysis and compliance purposes, enhancing accountability and security monitoring.
Overall, Pluggable Authentication Module Linux is an indispensable tool for system administrators, empowering them to enforce robust security policies while ensuring a seamless and user-friendly authentication experience for legitimate users.
