What is Reverse-Engineering in Software Engineering?
Overview
Reverse engineering in software engineering involves dissecting and analyzing existing software to understand its functionality, structure, and design. It aids in comprehending legacy systems, identifying vulnerabilities, and creating compatible alternatives. This process often involves decompilation, disassembly, and code analysis, allowing developers to extract valuable insights and recreate source code. Reverse engineering plays a pivotal role in software maintenance, system migration, and security auditing. However, its ethical and legal implications, particularly in terms of intellectual property, should be carefully considered and respected during the exploration of proprietary software.
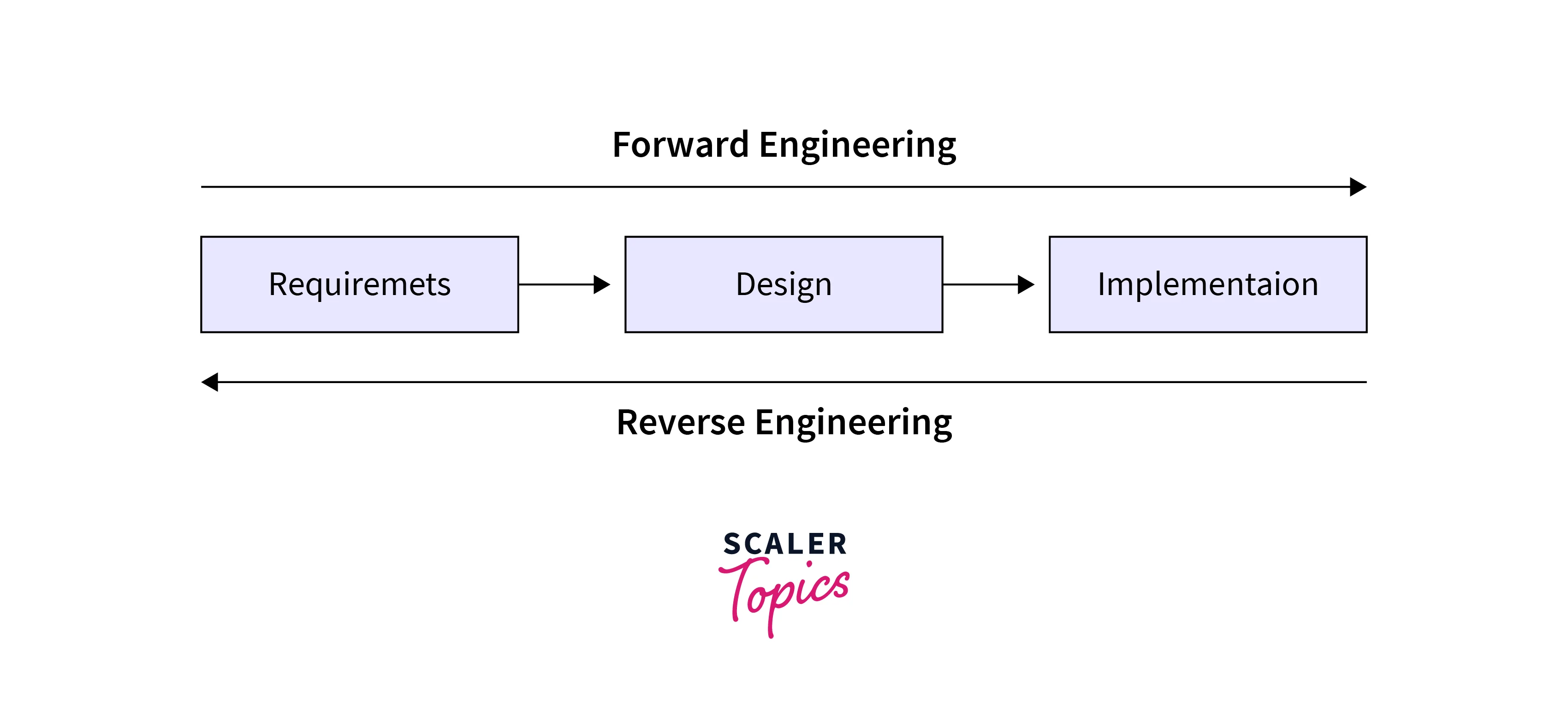
Introduction to Reverse Engineering in Software Engineering
Reverse engineering in software involves dissecting existing software to understand its inner workings. It serves purposes like understanding legacy systems and finding vulnerabilities. Techniques like decompilation and code analysis are used. It has benefits for software maintenance but raises ethical and legal questions, especially with proprietary software and intellectual property rights.
Impact of Reverse Engineering on Various Industries
- Software Security:
Reverse engineering helps identify vulnerabilities and weaknesses in software, enabling security experts to patch them before exploitation, thus enhancing overall cybersecurity. - Digital Forensics:
In cases of cybercrimes or incidents, reverse engineering aids investigators in analyzing malicious code and tracing digital footprints, contributing to efficient and accurate digital forensic analysis. - Competitive Analysis:
Businesses leverage reverse engineering to dissect competitors' products, enabling insights into design, features, and technologies, aiding strategic decision-making and fostering innovation.
Reverse Engineering Goals
Reverse engineering is the process of deconstructing and analyzing a product or system to understand its design, functionality, and underlying mechanisms. The goals of reverse engineering can vary based on the specific context and objectives, but here are some common goals:
- Understanding Functionality:
- Gain insights into how a product or system works.
- Identify the components and their interactions.
- Uncover hidden features or capabilities.
- Compatibility and Interoperability:
- Modify or adapt existing products to work with new hardware or software.
- Ensure compatibility with different platforms, systems, or formats.
- Bug Analysis and Debugging:
- Identify and analyze software bugs or vulnerabilities.
- Debug and fix issues in proprietary software without access to the source code.
- Product Improvement:
- Enhance or optimize the performance of a product.
- Identify areas for improvement in terms of speed, efficiency, or user experience.
- Security Assessment:
- Identify potential security vulnerabilities or weaknesses.
- Assess the efficacy of the implemented security measures.
- Design Documentation:
- Create documentation for systems with incomplete or missing documentation.
- Generate technical documentation for legacy systems.
- Intellectual Property Protection:
- Detect unauthorized use or reproduction of proprietary technology.
- Determine if intellectual property rights are being violated.
- Competitor Analysis:
- Analyze and understand the design choices of competitors' products.
- Extract information about their technological advancements.
- Recovery of Lost Data:
- Retrieve data from damaged or corrupted files or devices.
- Extract data from legacy formats or systems.
- Learning and Education:
- Use reverse engineering as a learning tool to understand complex systems.
- Gain insights into different programming languages, architectures, and methodologies.
- Legacy System Migration:
- Migrate old systems to modern platforms or architectures.
- Preserve functionality while updating underlying technologies.
- Customization and Modification:
- Customize products for specific use cases or preferences.
- Modify software to add new features or remove unwanted ones.
- Hardware Analysis:
- Understand the internal workings of hardware devices.
- Replicate or adapt hardware components for specific purposes.
- Resource Optimization:
- Identify unnecessary resource consumption in software or hardware.
- Optimize resource usage for better performance or efficiency.
- Legal and Regulatory Compliance:
- Verify that products meet industry standards and regulations.
- Ensure compliance with legal requirements for interoperability.
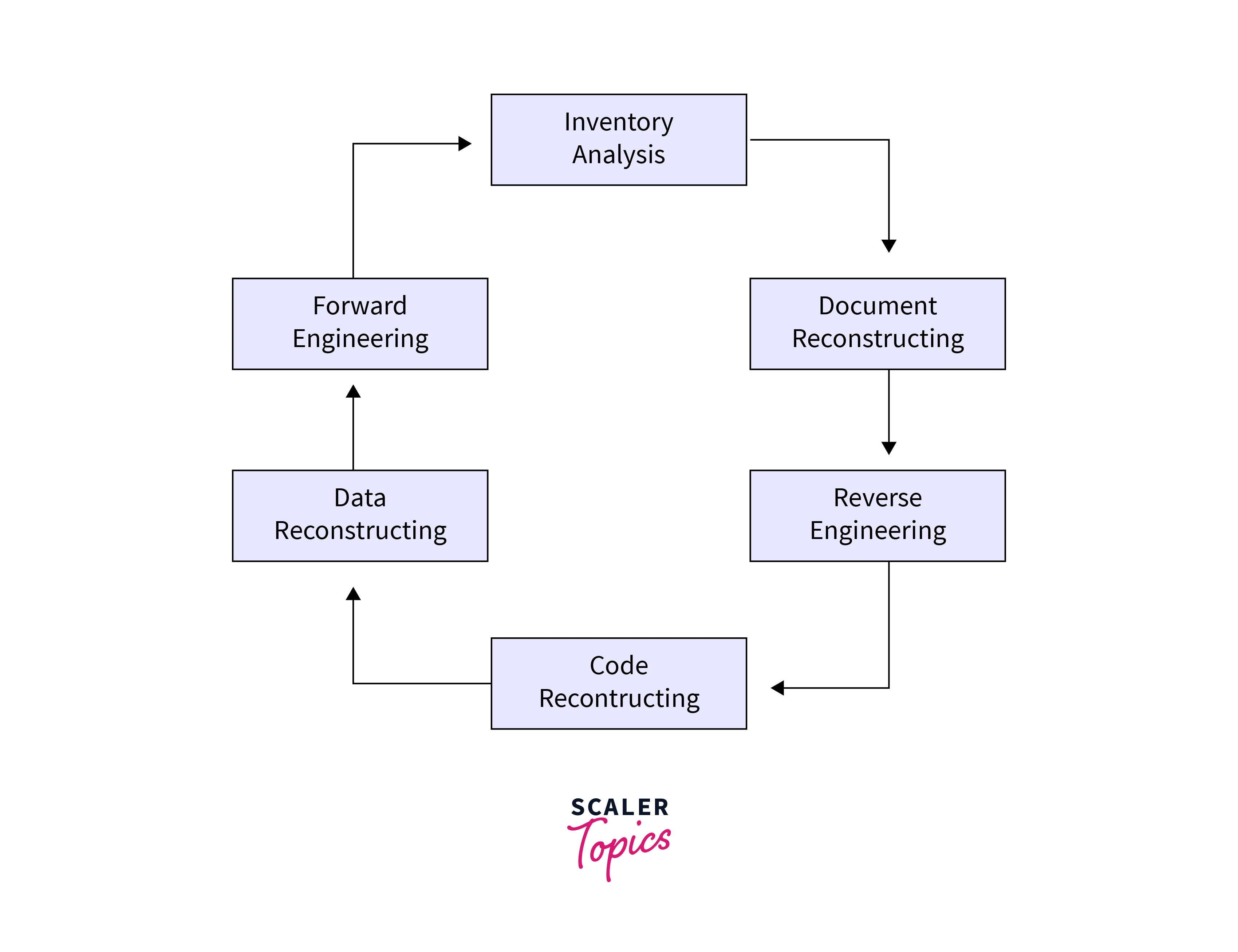
Steps of Software Reverse Engineering
- Initial Analysis:
Understand the software's purpose, platform, and structure. - Decompile/Disassemble:
Convert executable code back into a more human-readable form. - Code Analysis:
Study the decompiled code to comprehend functionality and algorithms. - Identify Components:
Isolate modules, functions, and data structures. - Control Flow Analysis:
Trace program execution paths to discern logic and behavior. - Data Flow Analysis:
Track data manipulation to understand input/output relationships. - Reconstruction:
Rebuild higher-level abstractions for better comprehension. - Dynamic Analysis:
Execute the software in a controlled environment to observe runtime behaviour. - API and Library Identification:
Determine external libraries and APIs used. - Vulnerability Discovery:
Identify security weaknesses, bugs, or exploits. - Documentation: Create documentation describing the software's inner workings.
- Modification/Enhancement:
Make changes to the software, if necessary. - Testing:
Verify modified software's functionality and stability. - Legal and Ethical Considerations:
Ensure compliance with software licensing and ethical guidelines.
Reverse Engineering Tools
Reverse engineering, if performed manually, can be extremely time-consuming and labour-intensive. Therefore, it is crucial to have automated tools that support this process. Below are some examples of such tools:
- CIAO and CIA:
These tools serve as graphical navigators for software and web repositories, providing a collection of tools for reverse engineering. - Rigi:
Rigi is a visual tool designed for enhancing software comprehension and understanding. - Bunch:
This tool focuses on software clustering and modularization, aiding in the organization of complex codebases. - GEN++:
An application generator that facilitates the creation of analysis tools specifically for the C++ programming language. - PBS:
The Software Bookshelf tools are utilized for extracting and visualizing program architectures, aiding in architectural analysis.
By utilizing these tools, the process of reverse engineering can be significantly streamlined and made more efficient.
Advantages of Reverse Engineering
- Understanding and Documentation:
Reverse engineering allows for a deeper understanding of how a product, software, or system works, which can aid in creating comprehensive documentation and improving future designs. - Innovation and Improvement:
By dissecting existing products, engineers can identify areas for improvement and innovation, leading to the development of enhanced versions or entirely new products. - Interoperability:
Reverse engineering can help decipher proprietary file formats and protocols, enabling better integration and compatibility with other systems and software. - Legacy System Maintenance:
When original design documentation is unavailable, reverse engineering becomes essential for maintaining and updating legacy systems, extending their lifespan. - Competitive Analysis:
Reverse engineering competitors' products can provide insights into their strengths and weaknesses, guiding strategic decisions and market positioning. - Troubleshooting and Debugging:
Reverse engineering aids in diagnosing and fixing issues, especially when dealing with complex systems where the original source code or design is not accessible.
Limitations of Reverse Engineering
- Legal and Ethical Concerns:
Reverse engineering can often raise legal and ethical dilemmas, especially when it involves copyrighted or patented materials. Unauthorized reverse engineering may infringe on intellectual property rights. - Resource Intensive:
The process of reverse engineering can be time-consuming and resource-intensive. It requires skilled professionals, specialized tools, and a significant investment of time and effort. - Incomplete Information:
Reverse engineering may not always yield a complete and accurate representation of the original design or system. Some details may be missed or misinterpreted during the process. - Loss of Optimization:
The original design might have been optimized for specific performance metrics, which may not be fully understood during reverse engineering. Altering the design without proper knowledge could lead to suboptimal results. - Outdated Technology:
In some cases, the technology or methods used for reverse engineering might not be up-to-date, leading to limitations in accuracy and efficiency. - Risk of Intellectual Property Theft:
Engaging in reverse engineering could potentially expose sensitive design information to competitors, leading to the risk of intellectual property theft and compromising a company's competitive advantage.
Challenges in Reverse Engineering
- Outdated Programming Languages:
- Lack of modern support and tools.
- Difficulty in finding skilled developers.
- Lack of Documentation:
- Inadequate or outdated documentation.
- Unclear system functionality and design.
- System Dependencies and Integration:
- Complex interconnections with other systems.
- Disruptions during analysis and changes.
Addressing the Challenges in Reverse Engineering
- Outdated Programming Languages:
- Consider migration to modern languages.
- Use emulators or interfaces for integration.
- Wrap legacy code with modern interfaces.
- Lack of Documentation:
- Utilize reverse engineering tools.
- Conduct thorough code analysis.
- Engage with past users and stakeholders.
- System Dependencies and Integration:
- Map out dependencies and data flow.
- Isolate and modularize components.
- Use stubs or mocks for external services.
- Implement automated testing.
- Skill and Knowledge Gap:
- Cross-train existing team members.
- Hire experts with relevant expertise.
- Foster collaboration and consult external experts.
Conclusion
- Reverse engineering provides valuable insights into existing software systems, allowing developers to understand complex codebases and their functionality.
- It is crucial for maintaining and updating legacy systems, enabling developers to make informed decisions about enhancements or bug fixes.
- Reverse engineering aids in understanding proprietary or closed systems, facilitating integration with other software and platforms.
- It plays a vital role in identifying vulnerabilities and security flaws in software, enabling proactive mitigation and enhancing overall cybersecurity.
- Reverse engineering assists in analyzing competitor software to understand their features and functionalities, aiding in market positioning and innovation.
- By examining existing code, developers can identify performance bottlenecks and areas for optimization, leading to more efficient software.
- Reverse engineering helps in generating accurate documentation for software that lacks proper documentation, aiding in future maintenance and development efforts.
- It serves as an educational tool for software engineers to learn from well-implemented solutions and programming techniques in existing software projects.
