Two Phase Locking Protocol

Locking in a database management system is used for handling transactions in databases. The two-phase locking protocol ensures serializable conflict schedules. A schedule is called conflict serializable if it can be transformed into a serial schedule by swapping non-conflicting operations.
Two-Phase Locking
Before understanding the two phases of Locking, let's understand the types of locks used in transaction control.
- Shared Lock: Data can only be read when a shared lock is applied. Data cannot be written. It is denoted as lock-S
- Exclusive lock: Data can be read as well as written when an exclusive lock is applied. It is denoted as lock-X
Now, let's understand the two phases of locking.
The two phases of Locking are :
- Growing Phase: In the growing phase, the transaction only obtains the lock. The transaction can not release the lock in the growing phase. Only when the data changes are committed the transaction starts the Shrinking phase.
- Shrinking Phase: Neither locks are obtained nor they are released in this phase. When all the data changes are stored, only then the locks are released.
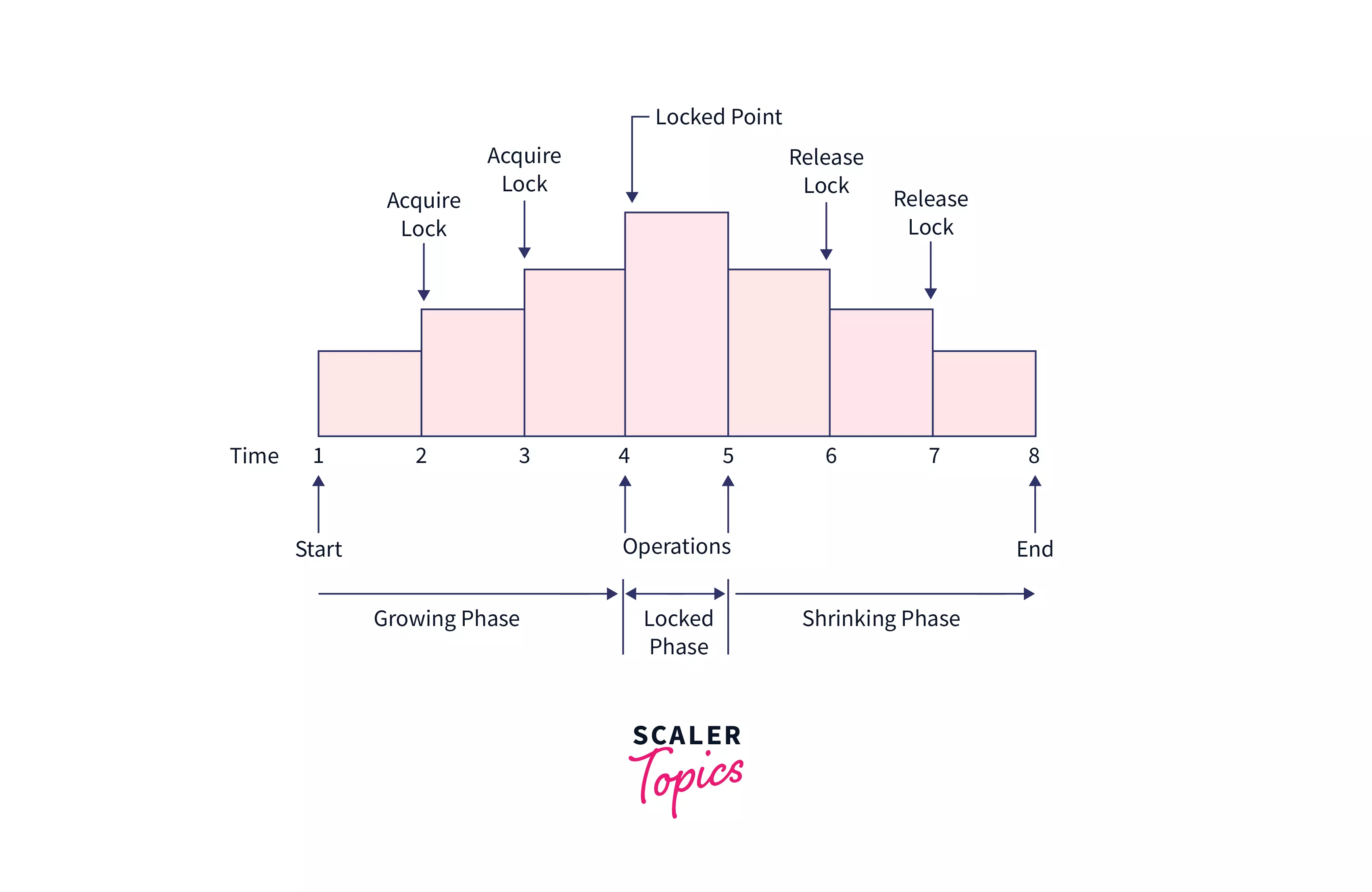
In the above figure, we can see that in the growing phase, all the locks are obtained till the point when all the locks needed by the transactions are acquired. This pint is called Lock-Point. After the lock point, the transaction enters the Shrinking phase.
Two-Phase Locking Types
Two-phase Locking is further classified into three types :
-
Strict two-phase locking protocol :
- The transaction can release the shared lock after the lock point.
- The transaction can not release any exclusive lock until the transaction is committed.
- In strict two-phase locking protocol, if one transaction rollback then the other transaction should also have to roll back. The transactions are dependent on each other. This is called Cascading schedule.
-
Rigorous two-phase locking protocol :
- The transaction cannot release either of the locks, i.e., neither shared lock nor exclusive lock.
- Serializability is guaranteed in a Rigorous two-phase locking protocol.
- Deadlock is not guaranteed in the rigorous two-phase locking protocol.
-
Conservative two-phase locking protocol :
- The transaction must lock all the data items it requires in the transaction before the transaction begins.
- If any of the data items are not available for locking before execution of the lock, then no data items are locked.
- The read-and-write data items need to be known before the transaction begins. This is not possible normally.
- Conservative two-phase locking protocol is deadlock-free.
- Conservative two-phase locking protocol does not ensure a strict schedule.
Cascading Roll Back in 2PL
Let's understand cascading rollback in 2Pl with the help of an example :
Cascading rollback means if one transaction rollback then other transactions dependent on it should also roll back.
| S no. | T1 | T2 | T3 |
|---|---|---|---|
| 1 | Lock-X(R1) | ||
| 2 | Read(R1) | ||
| 3 | Write(R1) | ||
| 4 | Lock-S(R2) LP | ||
| 5 | Read(R2) | ||
| 6 | Unlock-R1,Unlock-R2 | ||
| 7 | Lock-X(R1) LP | ||
| 8 | Read(R1) | ||
| 9 | Write(R1) | ||
| 10 | Unlock-R1 | ||
| 11 | Lock-S(R1) LP | ||
| 12 | Read-R1 |
Because of Write(R1) in T1 and after that, Read(R1) in T2 and Read(R1) in T3, there is a dirty read which means the data written by transaction T1 is being read by transaction T2 and T3. So if T1 Rollback, T2 and T3 also have to rollback, causing cascading Rollback. So cascading Rollback is possible in a two-phase locking protocol.
In the above transaction, LP denotes Lock Point.
Before the lock point in all three transactions, T1, T2, and T3, there is a growing phase in transactions, respectively, and after LP, the shrinking phase starts.
Deadlock in 2PL
Let's understand deadlock in a two-phase locking protocol with the help of an example.
| S.no | T1 | T2 |
|---|---|---|
| 1 | Lock-X(R1) | Lock-X(R2) |
| 2 | Read(R1) | Read(R2) |
| 3 | Lock-X(R2) | Lock-X(R1) |
- In the above transaction in step 3, T1 cannot execute the exclusive lock in R2 as the Exclusive lock is already obtained by transaction T2 in step 1.
- Also, in step 3, the Exclusive lock on R1 cannot be executed by T2 as T1 has already applied the Exclusive lock on R1.
So, if we draw a wait-for graph, we can see that T1 waits for T2 and T2 waits for T1, which creates conflict, and the waiting time never ends, which leads to a deadlock.
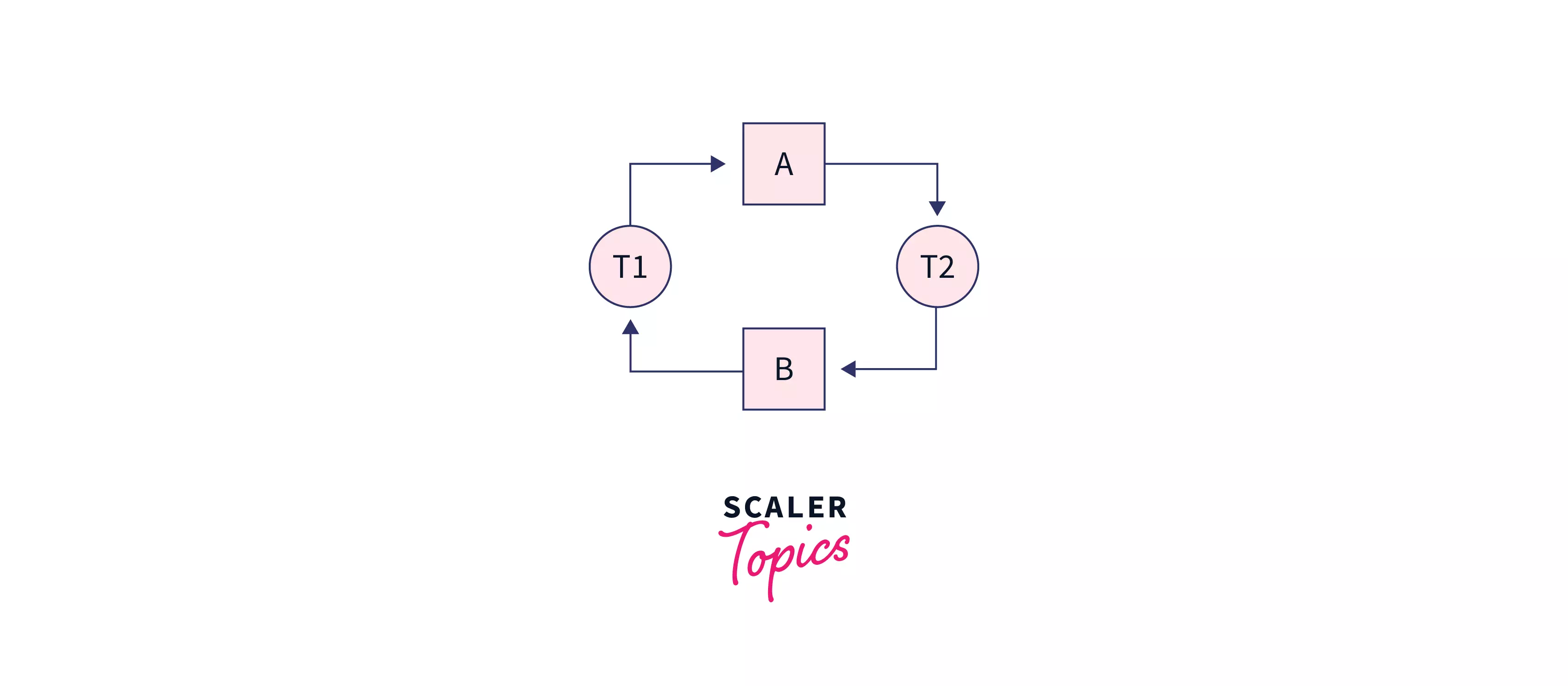
Hence, deadlock is possible in a two-phase locking protocol.
Conclusion
- Locking is used to handle concurrent transactions in databases
- Growing and shrinking phases are two phases of 2PL.
- Locks are only obtained in the growing phase.
- Locks are neither obtained nor released in the shrinking phase.
- Cascading rollback is possible in a two-phase locking protocol
- Deadlock is also possible in a two-phase locking protocol.
