AWS ARN (Amazon Resource Name)
Overview
AWS resources are uniquely identified by their Amazon Resource Names (ARNs). When a resource needs to be specified clearly throughout all of AWS, such as in IAM policies, Amazon Relational Database Service (Amazon RDS) tags, and API calls, we require an ARN. They serve as a singular, account-wide identity for any service.
What is an Amazon Resource Name (AWS ARN)?
Amazon Resource Name is referred to as an ARN. It is a resource's special identification that you create in AWS. To put it another way, everything you create in AWS normally has an ARN attached to it.
An ARN will be assigned to an S3 Bucket, for instance, when it is created.
arn:aws:s3:::bucket_name/key_name
Similarly, let's say you are creating an EC2 instance.
arn:aws:ec2:region:account-id:instance/instance_id
As a general rule, whenever you create a resource on AWS using the "create" button, an ARN identifier will be generated and linked to the AWS resource that you created.
The image below shows the ARN for a role called "deploy-role" that was created.

Why Is AWS ARN Important?
- Concerning IAM policies, ARNs are crucial. If you adhere to the accepted security best practices for IAM roles and policies, you will eventually use ARNs.
- They are employed in IAM rules to provide resources with granular access restrictions. One illustration is allowing a specific IAM user only to access particular EC2 instances.
- It can make API requests and automate script references to other resources.
- We frequently need to link up AWS resources. For instance, if we wanted to subscribe an SNS topic to a Lambda function, we would need to give AWS our ARN to specify the Lambda function we wanted.
AWS ARN Format
Most of the time, you can create the ARN URL using the structure mentioned below:
arn:aws:service:region:account-id:resource-id arn:aws:service:region:account-id:resource-type/resource-id arn:aws:service:region:account-id:resource-type:resource-id
The following is an example of an ARN:
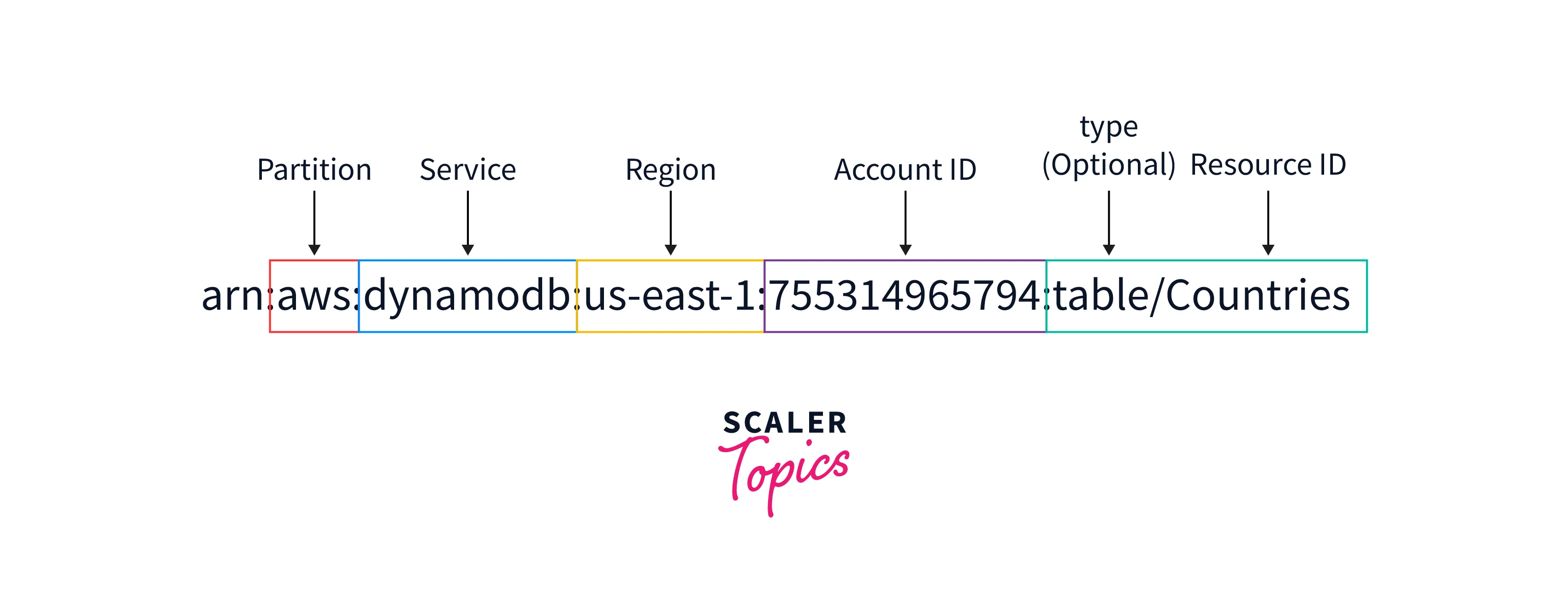
- Partition: The partition is a collection of AWS regions. This component can have three values: aws, aws-cn, or aws-us-gov. Only ARNs that employ the AWS value will ever be seen or used by 99% of you.
- Service: The service identifies the service that this ARN refers to. Your service identifier will be dynamodb, for instance, if you build a DynamoDB table. You get the concept.
- Region: The region is the area where produced the resource. AWS has numerous parts spread out all over the world. Keep in mind that the help you make has a specific geographic scope. To put it another way, a DynamoDB table created in us-east-1 only exists and not in any other regions. The resource itself is housed in the region's related data center.
- Account id: Every AWS customer has an account id. A 12-digit number that uniquely identifies your account is called an account id.
- Resource Type: The resource type is an optional field. It could be there or not, depending on the resource you generate. The example above shows that it is our DynamoDB database's value table. The ARN is for a service subresource, which is why (a table). This isn't present in all ARNs and only makes sense in specific situations.
- Resource id: The resource id identifies the resource at the lowest level. It stands for the name of our DynamoDB table, "Countries," in the example above.
AWS ARN Paths
- Paths can be included in resource ARNs. For instance, the resource identifier in Amazon S3 is an object name that can have slashes (/) to create a path.
arn:aws:s3:::bucket_name/key_name - The asterisk (*), a wildcard character, can be used in paths. For example: arn:aws:s3:::bucket_name/*, indicates ALL the objects/keys inside the s3 bucket.
- IAM group names and user names can also contain paths. If you're designing an IAM policy, for instance, you may use a wildcard to define all IAM users who have the path "program_7911" as follows: arn:aws:iam::123456789012:user/Development/program_7911/*
- This useful feature makes granting permissions simpler. We may use routes and wildcards (in this case, the *) to signify all rather than having to construct numerous policies for various items.
How to Find Your ARN?
- The ARN is accessible for some services via the resource's information page. The below images show how simple it is to get and copy the ARN for S3.
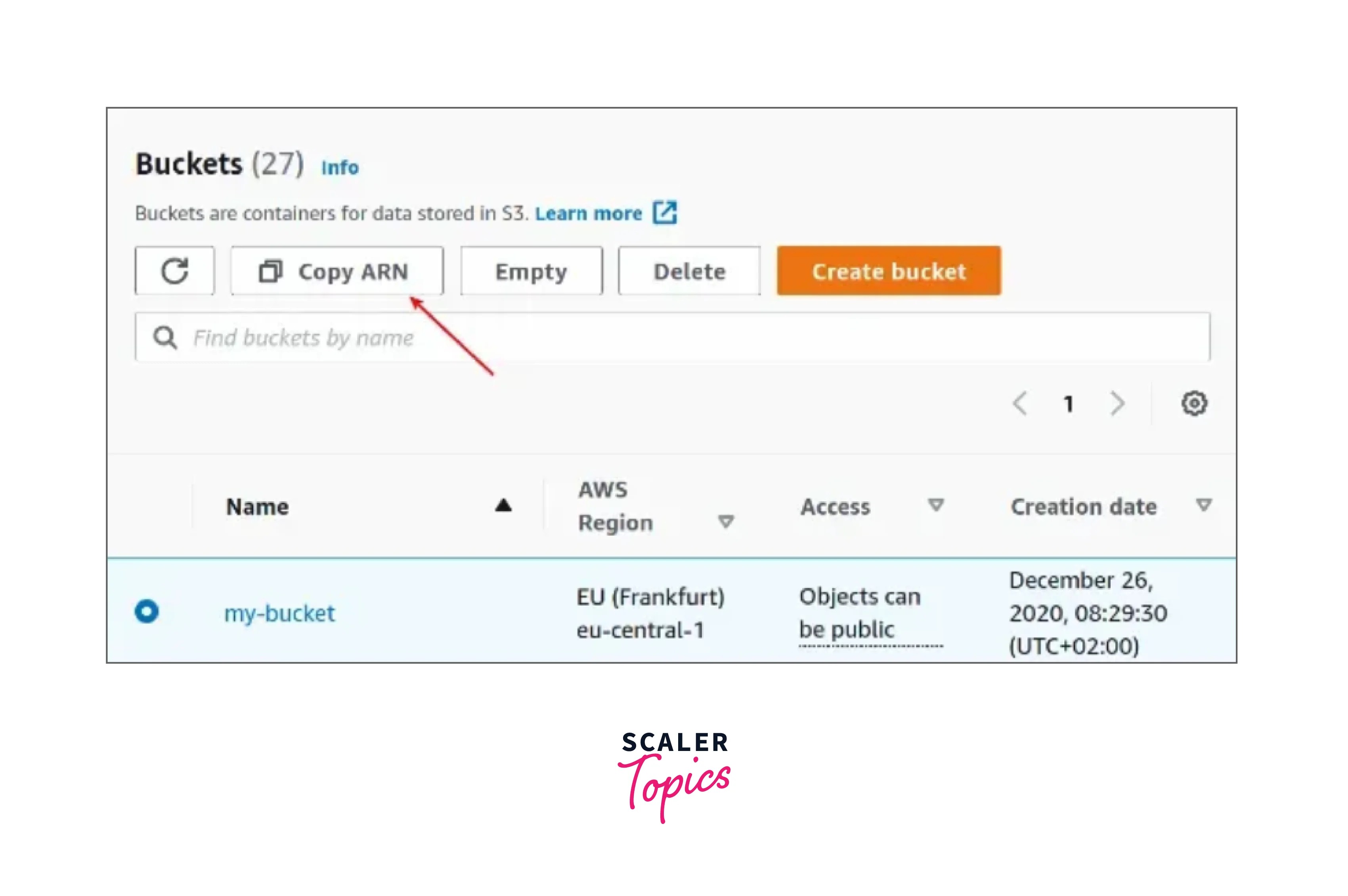
-
If you are trying to get the ARN of different AWS resources, Wizard can assist you. To do this, click "Create Policy" under the "Policies" tab in the IAM Management Console (https://console.aws.amazon.com/iam/)
-
After the above step, select the AWS Service for which you want the resource ARN, Now choose "All Actions" from the actions tab.
-
Let's say you want to do this for AWS EC2, Choose "All EC2 actions" from the Actions panel.
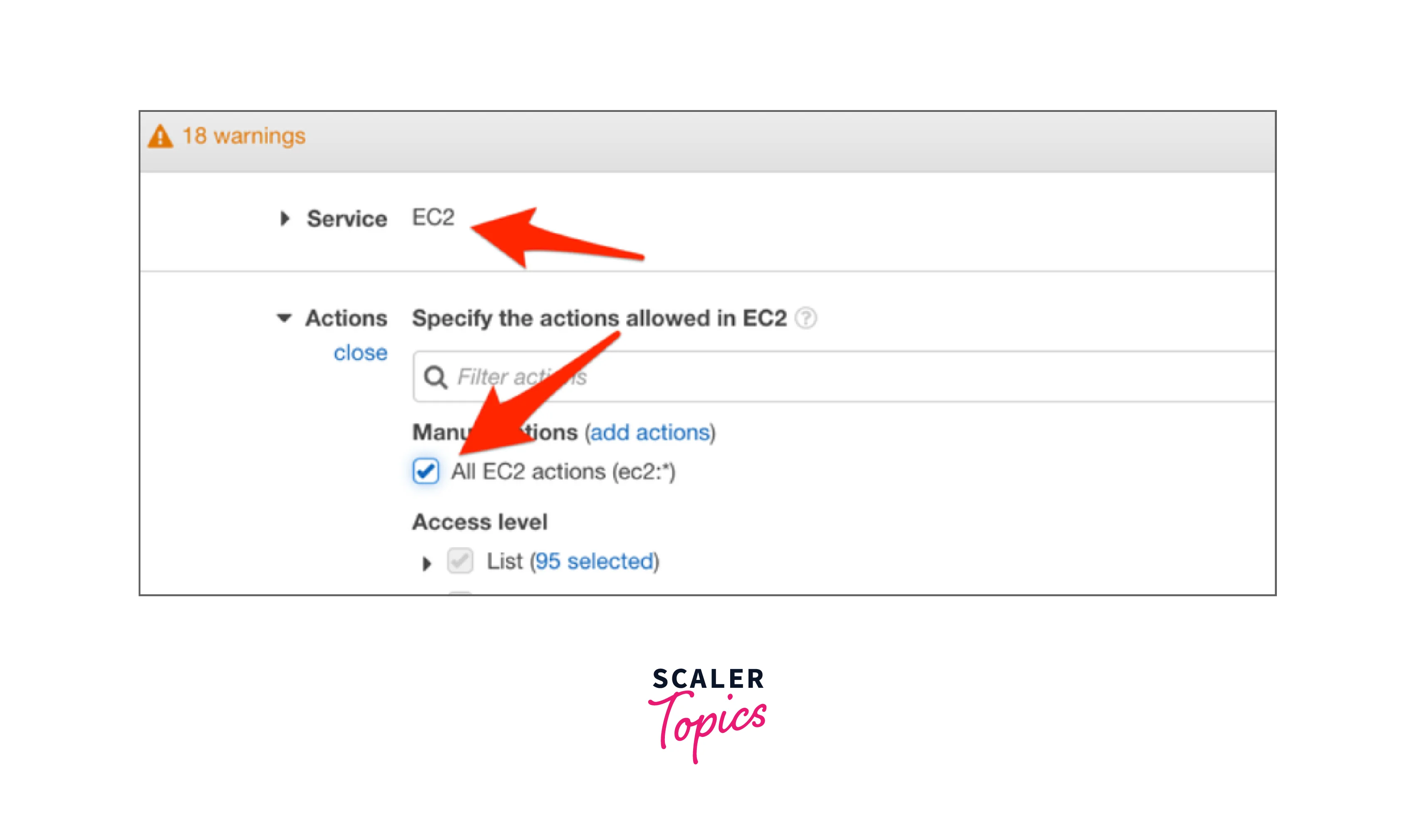
- In the resources tab, you may see a list of all potential resources with ARNs under the resources page. Choose "Add ARN" under the network interface: if you wish to create the ARN of a specific network interface.
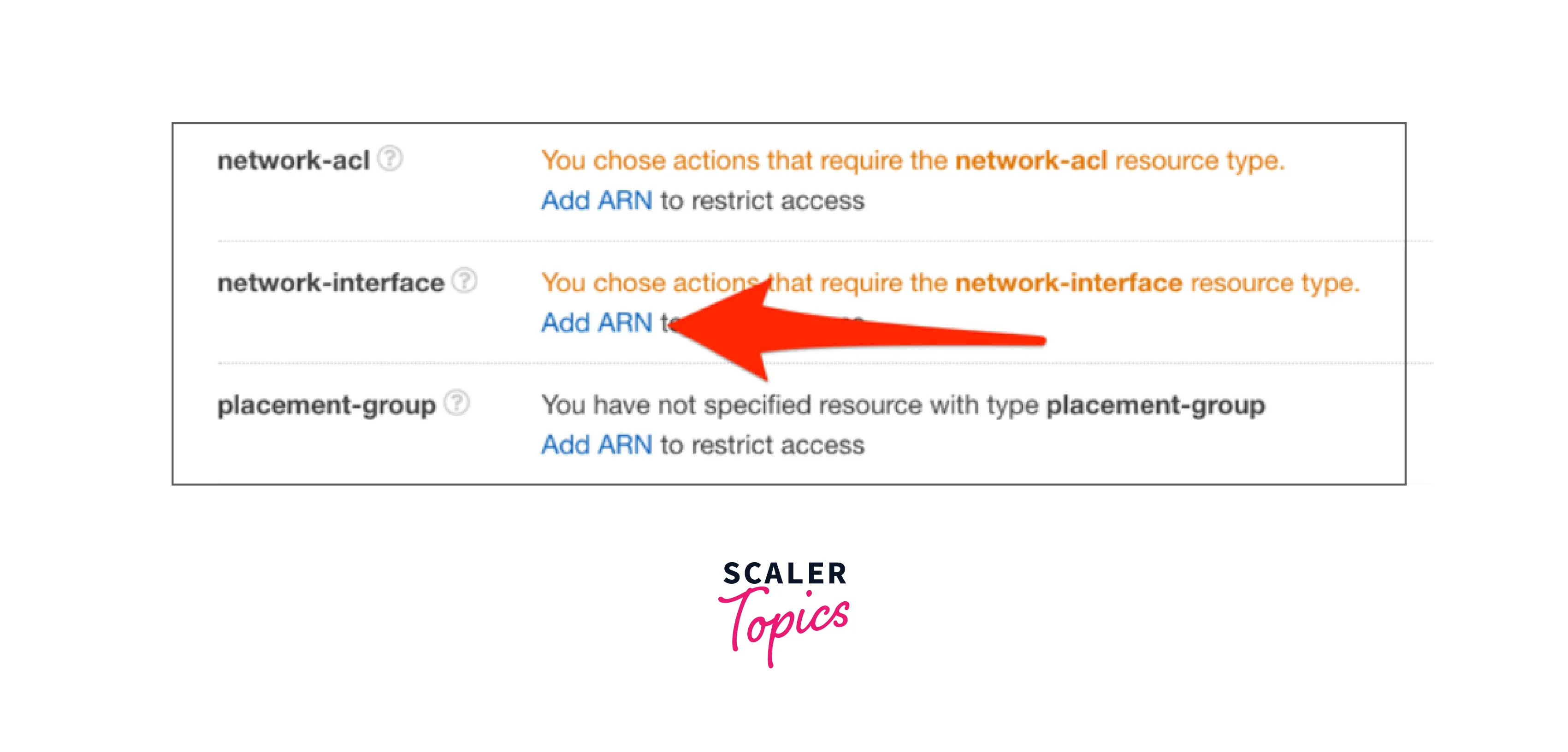
- Now the resource's region and general ID must be chosen. The "Network Interfaces" page in the EC2 console allows you to view the network interface ID.Select the region and general ID from the list in the EC2 console's "Network Interfaces" tab.
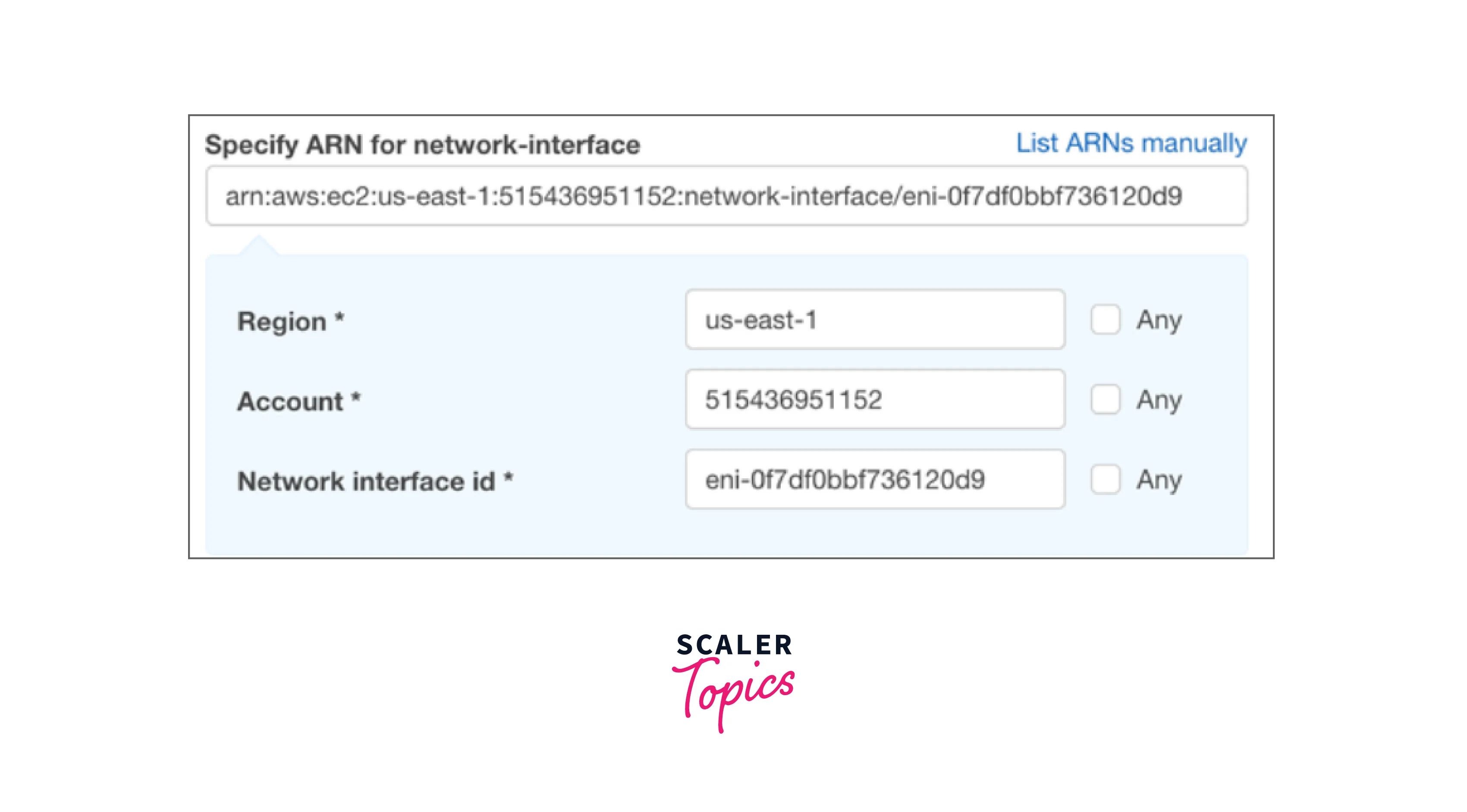
- Once the information is entered, the ARN should be generated for you. Once you're done, you can leave the wizard because you don't want to save the policy.
More ARN Examples
It's crucial to keep in mind that ARNs have a similar structure but can differ somewhat based on the AWS service. Here are a few illustrations of how ARNs appear in various AWS services.
-
Lambda Function: arn:aws:lambda:us-west-1:999999999999:function: hello . Here 999999999999 is an imaginary AWS account and hello is the name of the function.
-
S3 Bucket: arn:aws:s3:::my-bucket my-bucket is the name of the S3 bucket.
-
SNS Topic: arn:aws:sns:us-east-1:999999999999:DemoSNSTopic
-
SNS Topic Subscription: arn:aws:sns:us-west-1:999999999999:DemoSNSTopic:61e425ce-627e-a32e-9a2e-6253c3ec2
-
Cloudwatch Alarm: arn:aws:cloudwatch:us-east-1:999999999999:alarm:alarm-name
-
IAM User: arn:aws:iam::799114967794:user/user-name
These are fictitious AWS ARNs, so you have a clearer idea of how they look.
How to Get the ARNs of AWS Resources?
-
ARNs for different resources in AWS are different and it can be hard for a person to find them. Therefore, here is a link to the AWS docs for information on the ARN syntax of different AWS resources https://docs.aws.amazon.com/service-authorization/latest/reference/reference_policies_actions-resources-contextkeys.html.
-
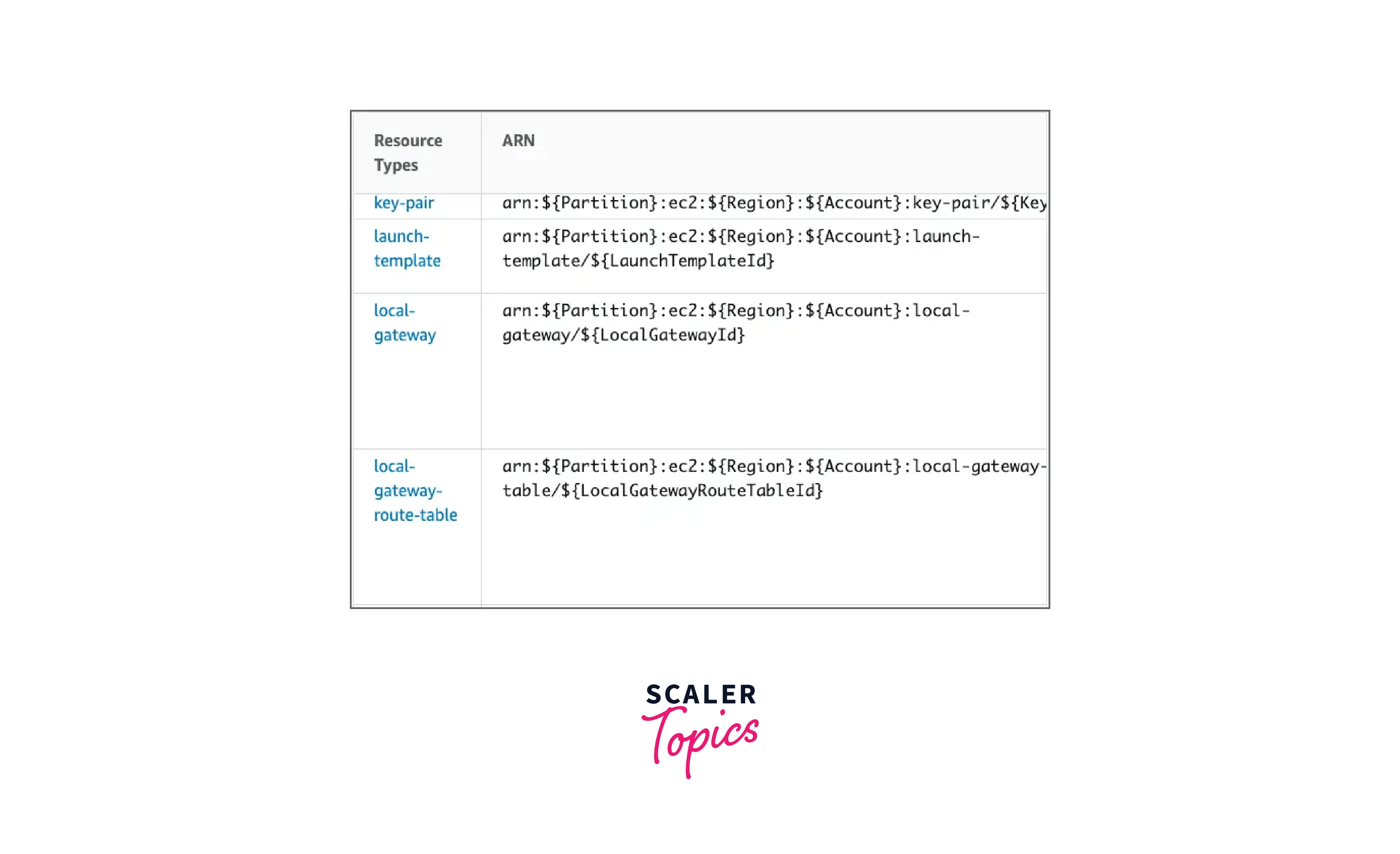
You may discover the references for all the sub-resource types for ec2 on the AWS page, for instance, by selecting the ec2 resource from the list and scrolling down to the "Resource Types Defined by Amazon EC2" section, as shown below.
- Utilizing the AWS policy generator is another option.
- When you choose a policy resource in the policy generator, the arn proposal is immediately displayed, as seen below.

ARN Wildcards
-
ARN specifications support wildcards.
-
Consider a scenario where you want an IAM policy that grants access to every object in a single bucket. You can use a wildcard arn for this like the one below. arn:aws:s3:::my-data-bucket/*
-
The use of a wildcard arn in an IAM policy is demonstrated here. This policy permits all S3 bucket activities.
Getting ARN from AWS CLI
-
The CLI allows you to obtain the ARNs of particular resources.
-
You may obtain the ARN via the CLI for all IAM roles, policies, and users by describing it.
-
Here is an illustration of how to land a role. aws iam get-role --role-name EMR_DefaultRole
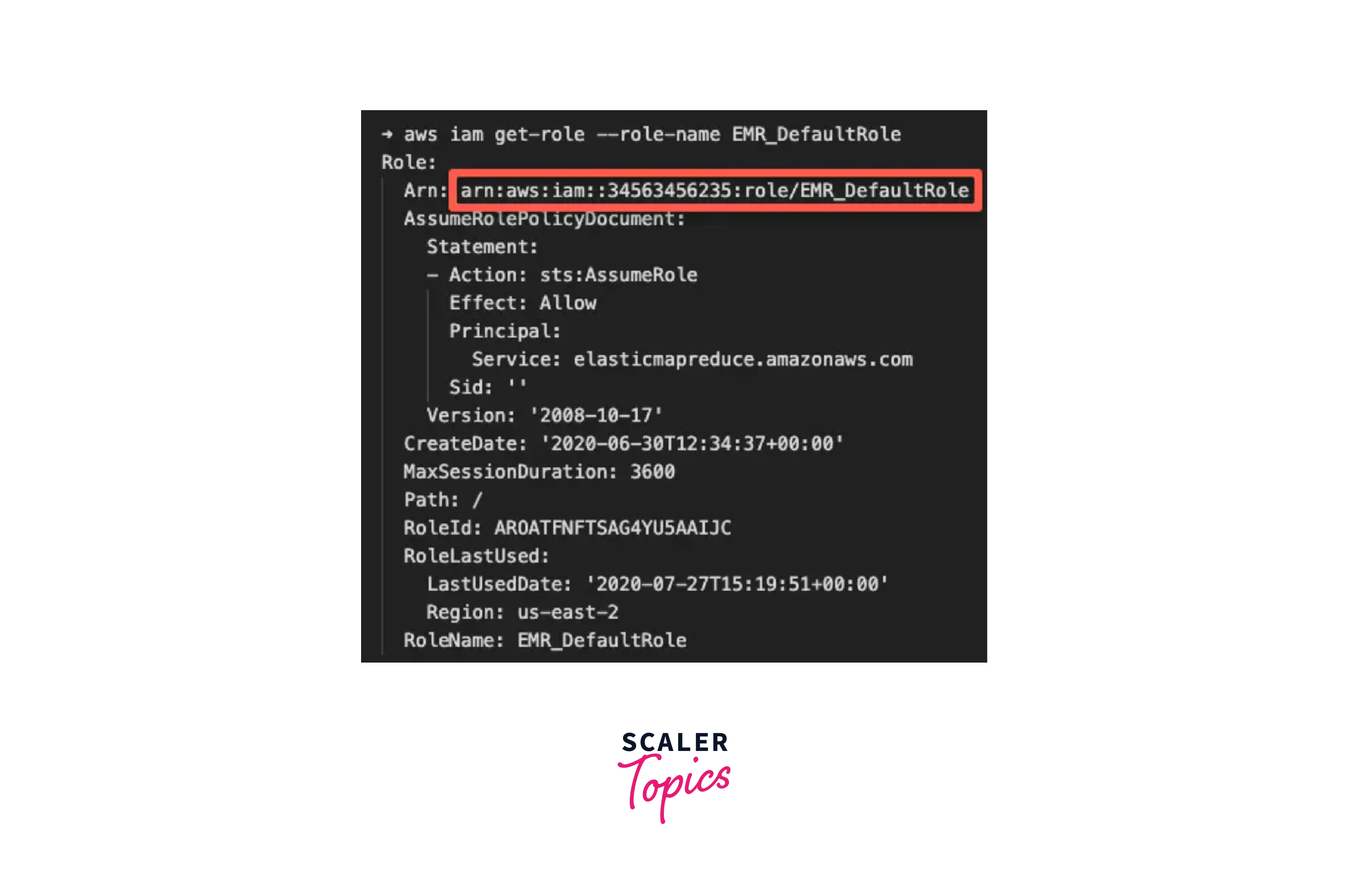
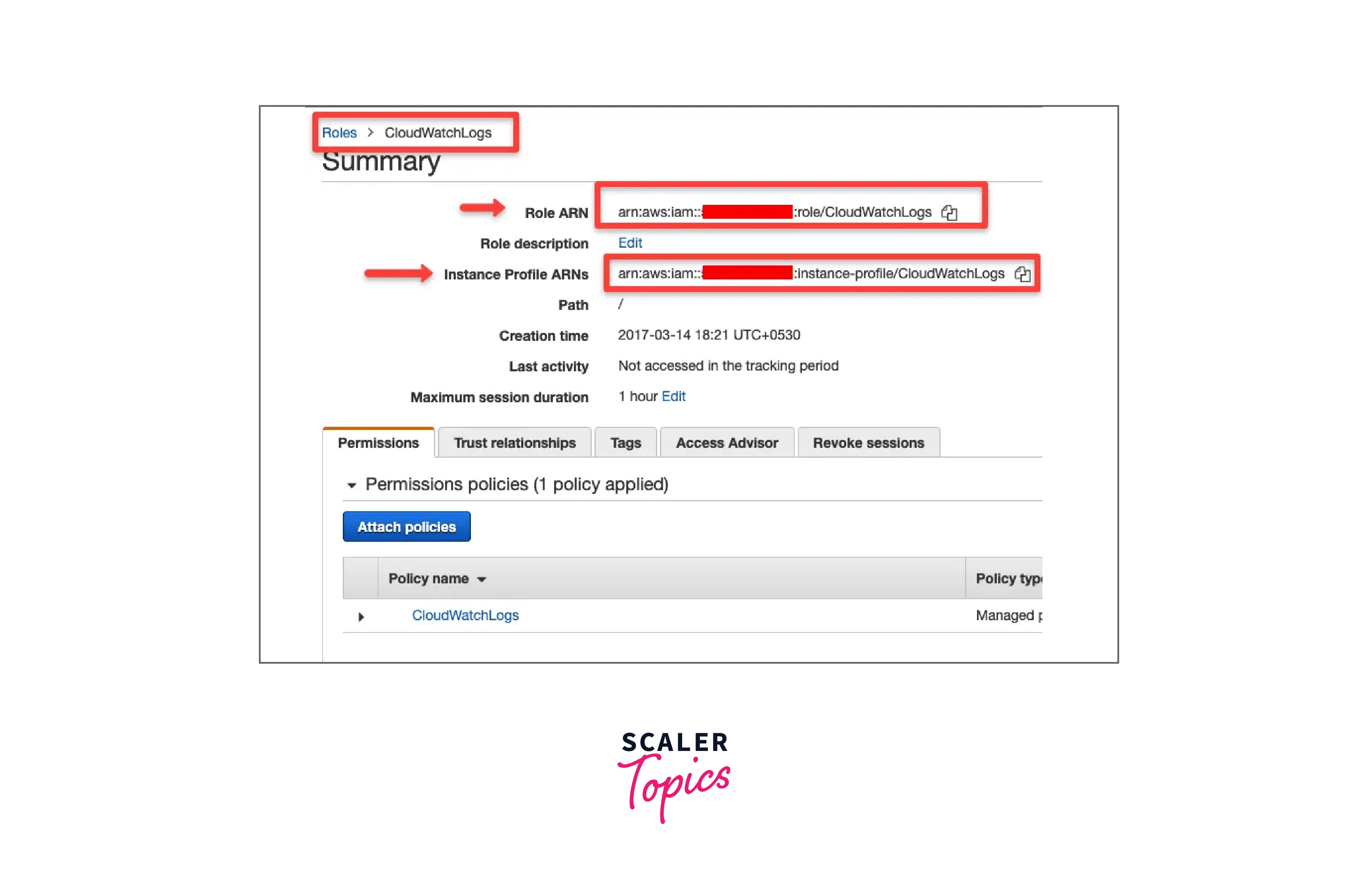
Getting ARN from AWS Console
- The AWS console allows you to access the ARN of IAM resources directly.
Getting ARN as Output in Cloudformation
-
If you're using Cloudformation, you can use the function to get the resource ARN in the output. Fn::GetAtt
-
Here is an example of a Lambda function's arn obtained using syntax.
Getting ARNs of Principal
- When creating an S3 bucket policy, SNS topic, VPC endpoint, and SQS policy, you must enter a principal parameter.
- The trusted source identified as the "Principal" in the policy to grant or restrict access to the resource is specified as an ARN.
- For instance, you might name the user arn as Principal in the policy if you just wanted a particular user to access an S3 bucket.
- The primary option is displayed below if you generate these policies using a policy generator.
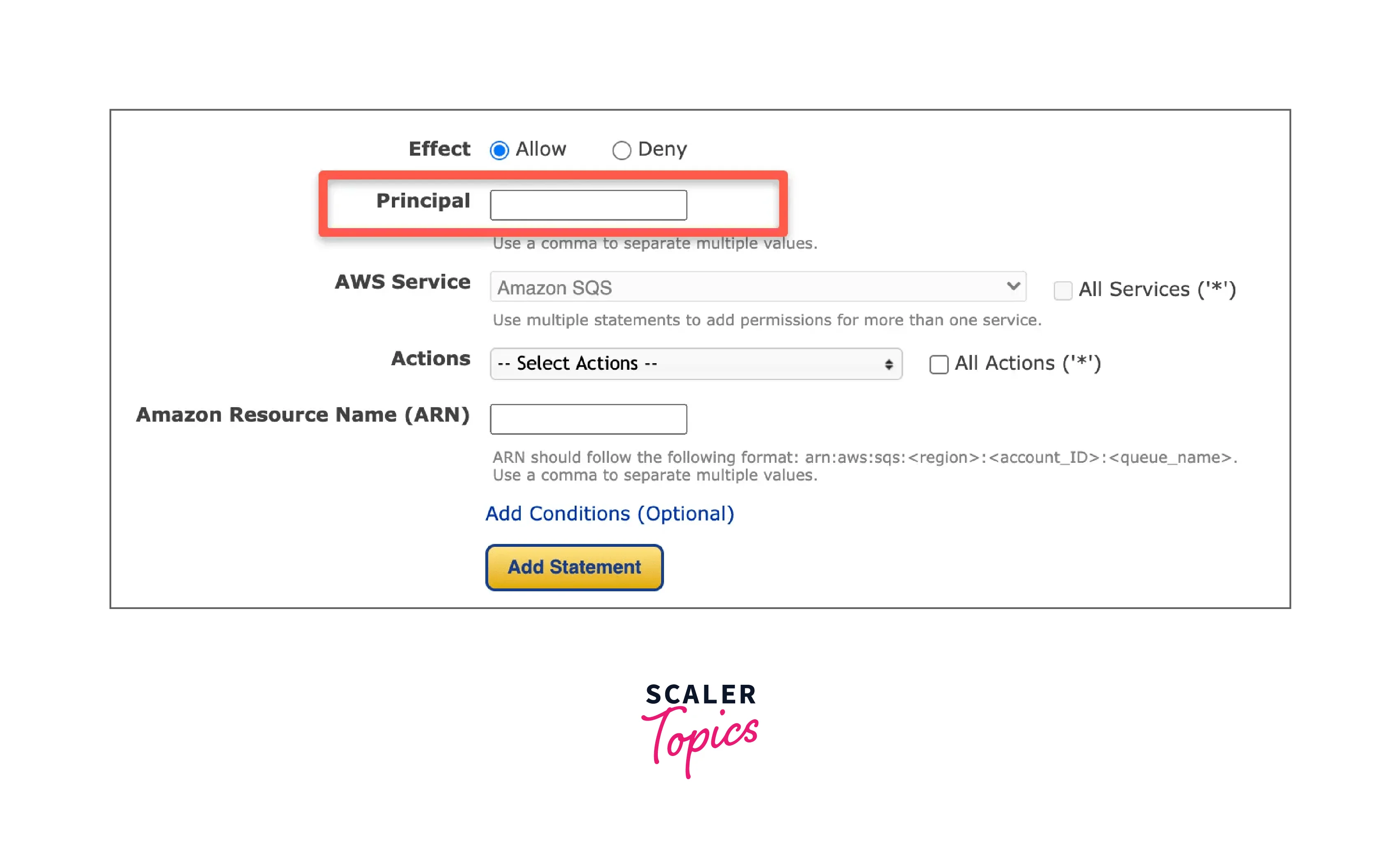
As the Principal, you first specify the user, account, and role of ARN.
Conclusion
- This article taught us that ARNs, or Amazon Resource Names, are distinct strings that designate an AWS resource or collection of AWS resources via a path. You'll encounter them throughout AWS, so it's critical to comprehend what they are and how they operate.
- After being created, ARNs cannot be changed. They are often found on the AWS resource's home page or in the "Additional Settings" sections. And the significance of it in several other AWS services.
- We also looked at various AWS ARN examples.
- We talked about subjects like how to get the ARNs of AWS resources, ARN wildcards, an ARN from the AWS CLI, an ARN from the AWS Console, and an ARN from the AWS Console ARN as output in Cloudformation, and how to get ARNs of principal.
