AWS Certificate Manager
Overview
AWS offers the AWS Certificate Manager as a service that can help the user with provisioning and managing(renewal and deployment-related work) the SSL/TLS certificates integrated with AWS services and AWS Certificate Manager integrated resources. With AWS certificate manager, all the hassle and time-taking manual process of buying, uploading, and keeping track of the expiration date and eventually renewing the SSL/TLS certificates along with deployment-related tasks for these certificates are taken care of within a few clicks of requesting the certificate via the AWS Certificate Manager.
SSL/TLS Certificates
Let us briefly discuss what an SSL/TLS certificate is and why it is important.
An SSL certificate is like an ID card or a badge that proves someone is who they say they are. SSL certificates are stored and displayed on the Web by a website’s or application’s server.
The Secure Socket Layer(widely known as SSL) is a standard security certificate that helps to enable an encrypted link( all data that travel through this link is private and integral) between a web browser and a web server. Similarly, Transport Layer Security (widely known as TLS) is used for encryption to protect the data and information in transit.
The below diagram shows why we need the SSL/TLS certificate for safe transactions.
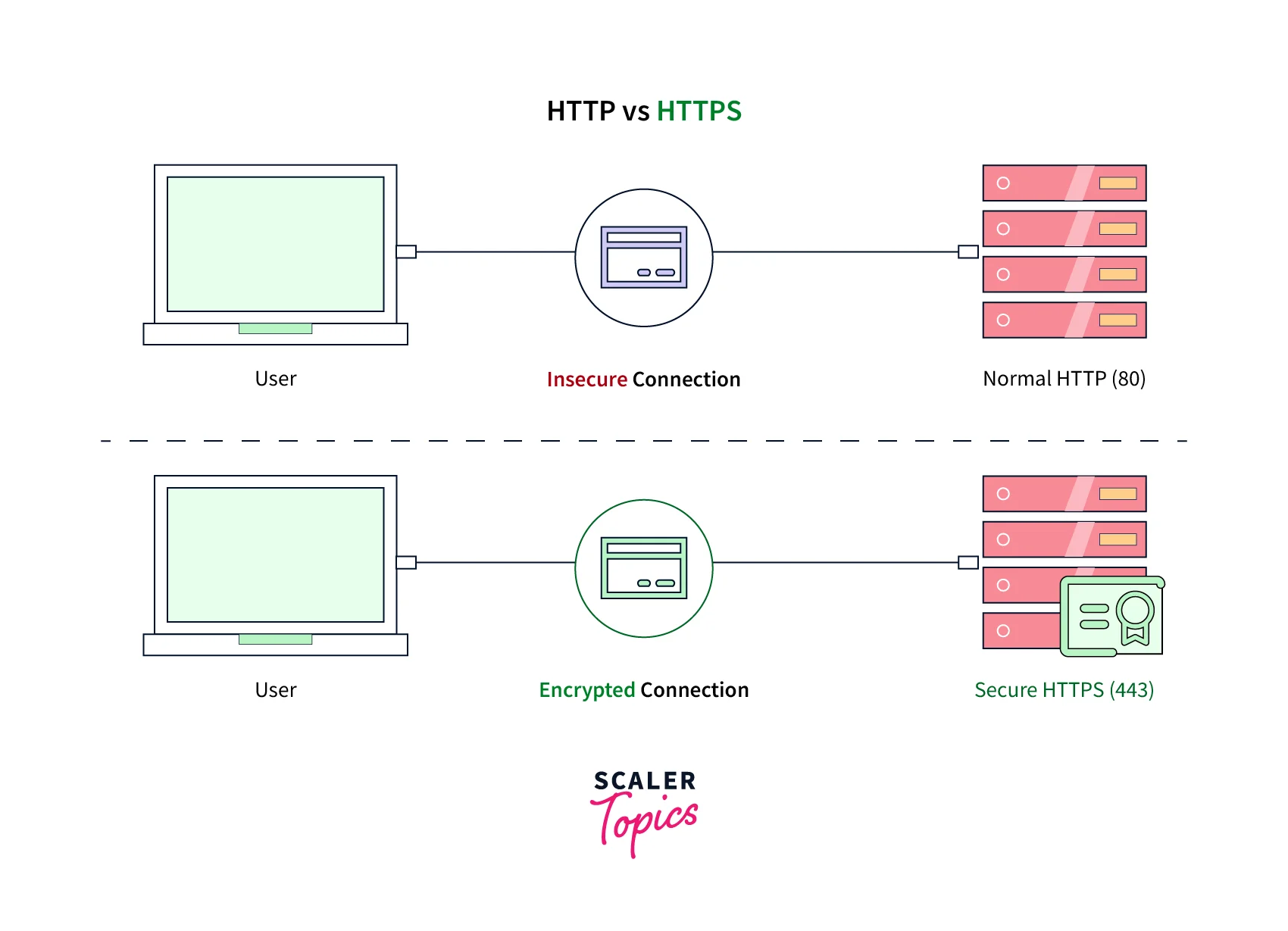
You might find SSL/TLS being interchangeably used but to clarify TLS is an improved version of SSL. The SSL or TLS is important to be integrated when your sensitive data is in transit. For example, websites that judiciously use SSL/TLS certificates are PCI-DSS(Payment Card Industry Data Security Standard), FedRAMP, and HIPAA(Health Insurance Portability and Accountability Act).
The below diagram depicts the working of SSL/TLS in brief:
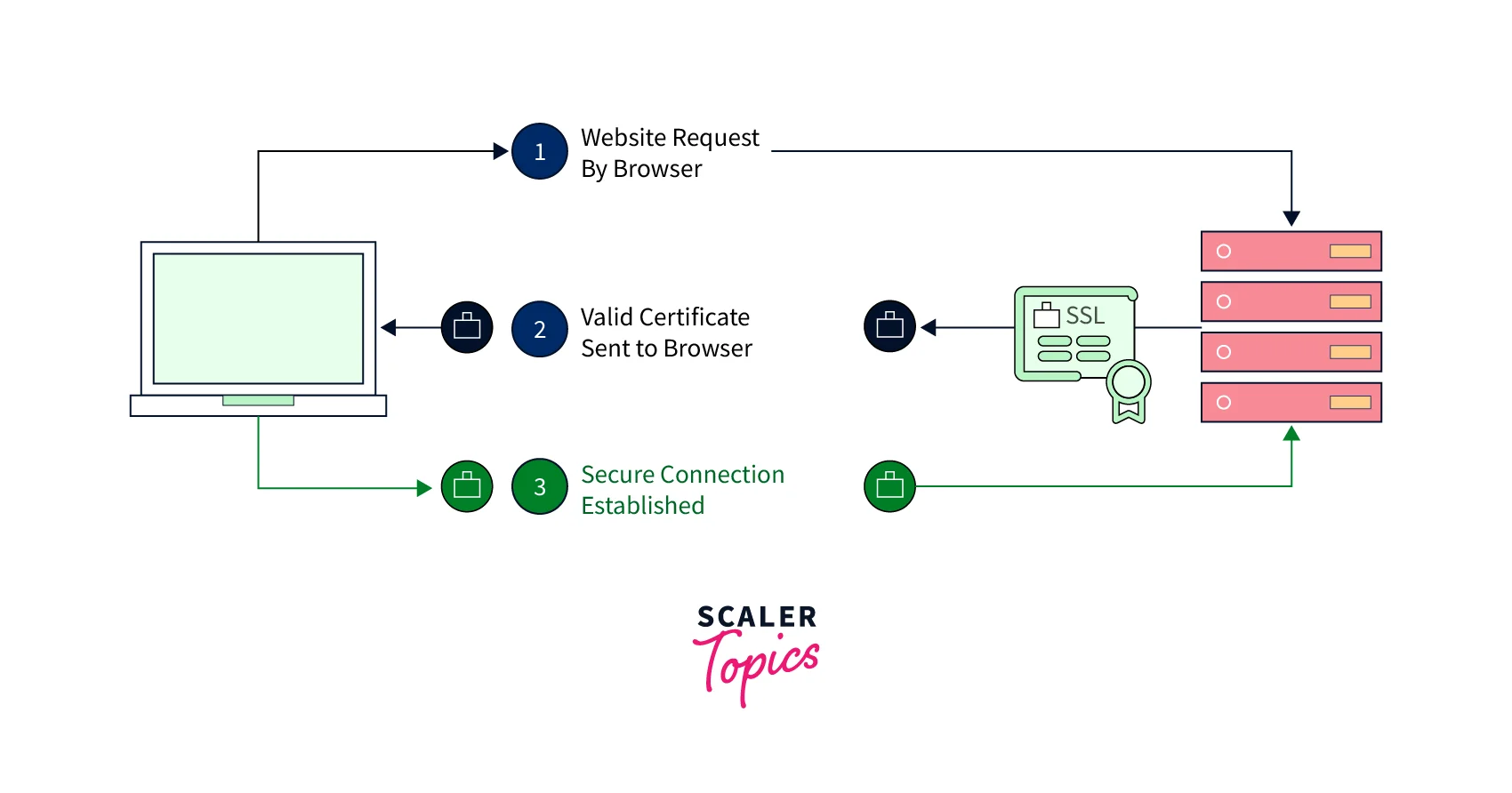
- When a server tries to establish a connection with the website, the server requests the web server to identify itself.
- As a validation of its identity, the web server then sends a copy of its SSL certificate to the server.
- The server then validates the information from the SSL/TLS certificate. Once it finds it trustworthy, it sends back a validated message to the web server.
- Finally, the web server sends a digitally signed acknowledgment to acknowledge the start of an SSL-encrypted session between them. This network creation between the servers is encrypted so that the data in transit is protected.
What is AWS Certificate Manager and How Does it Work?
Sometimes it might get difficult to provision and manage certificates for the service that you are using daily. Renewal and deployment of these certificates become additional work that must be taken care of, and if the certificate got expired then it is a hassle to issue the certificate over again.
Well, worry not. AWS understands your pain points and therefore offers its popular service called AWS Certificate Manager. AWS Certificate Manager is an AWS service that can help with provisioning and managing(renewal and deployment-related work) of the SSL/TLS certificates that are integrated with AWS services and AWS Certificate Manager integrated resources. AWS certificate manager takes away the hassle and the time taken in the manual process of buying, uploading, and keeping track of the expiration date and eventually renewing the SSL/TLS certificates along with deployment-related tasks for these certificates.
With AWS Certificate Manager, the users can easily provision, manage, renew, and automate the deployment of the public Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates that are ACM-integrated AWS services, or internally connected resources. Having an SSL/TLS certificate attached to your AWS service is important for security purposes as this ensures security across the network communications and establishment of the identity of the websites over the resources running on private networks as well as the internet.
The below diagram shows how AWS Certificate Manager can help ease the process related to SSL/TLS certificate provisioning and management:
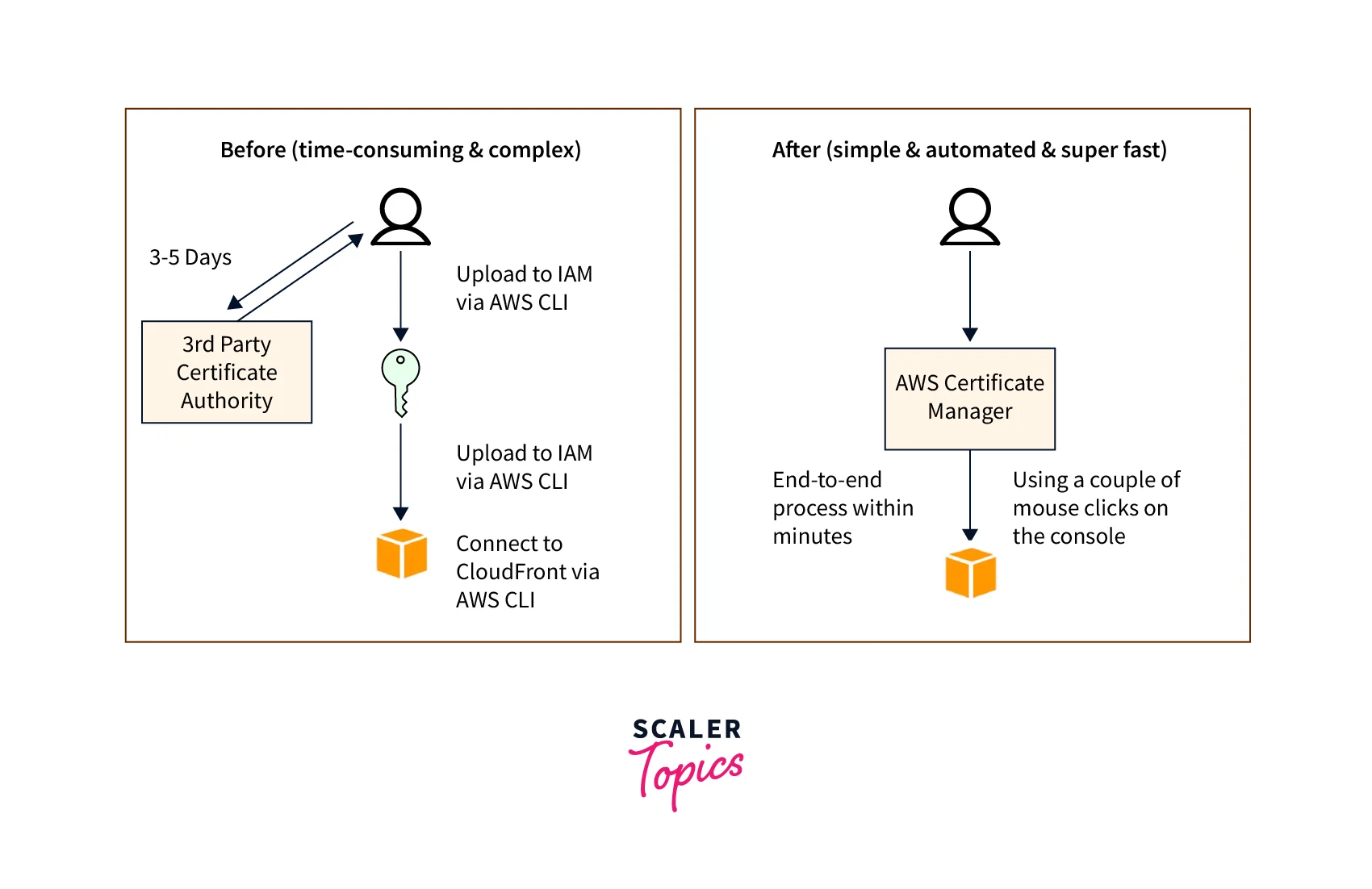
AWS Certificate Manager makes it easy to request a certificate within a few clicks, and deploy it on ACM-integrated AWS resources, like Elastic Load Balancers, and APIs on API Gateway along with renewal this certificate is taken care of. When it comes to provisioning any public certificates through the AWS Certificate Manager for usage with ACM-integrated services is also charged zero fees.
How It Works
The below diagram shows the detailed working of the AWS Certificate Manager where you can see all the types of certificates like public certificates, private certificates as well as import certificates from thrust third-party service providers. All these certificates are cross-checked and provisioned via the AWS certificate Manager that provisions and manages them with the ACM-integrated AWS resources like Elastic Load Balancer, AWS CloudFront, AWS API Gateway, or AWS Clodwatch as shown. With the AWS Certificate Manager (ACM) we can provision, manage, renew, and deploy any public, import, or private SSL/TLS certificates for users that are linked with AWS services, ACM-integrated AWS resources, or any internally connected resources. The time-consuming manual process of buying, uploading, deploying, and renewal of these SSL/TLS certificates is taken care of by the AWS certificate manager.
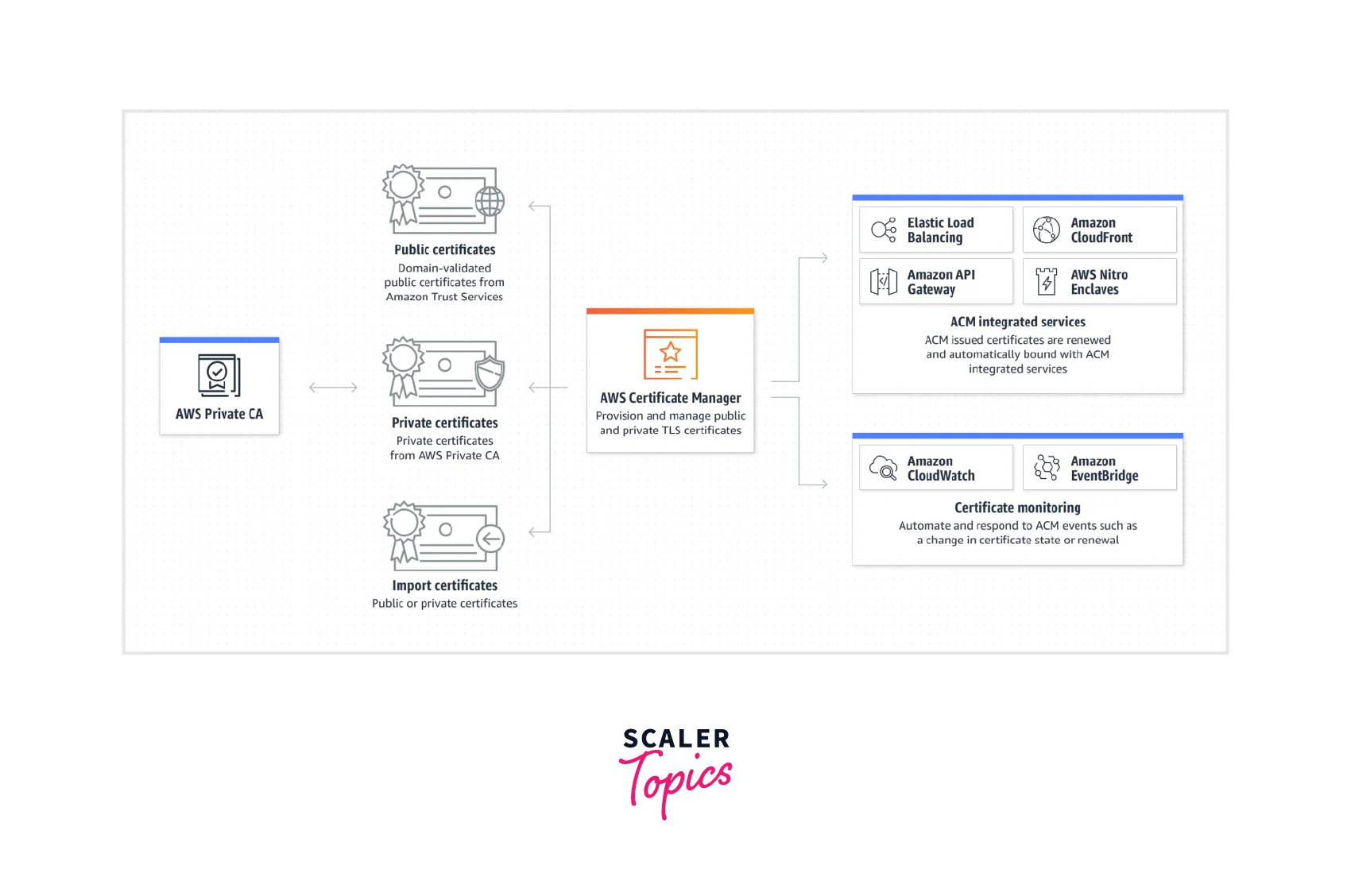
AWS Certificate Manager Concepts
Before we proceed to explore the AWS Certificate Manager service and its features, use cases, and more. Let us quickly visit some of the important key concepts listed below that shall help us understand the AWS Certificate Manager better.
- The private key cannot be downloaded for an ACM Certificate.
- The ACM Certificate are X.509 version. It offers three certificates of this version that are valid for 13 months.
- Adding, Modifying, or Removing any domain names from an existing AWS Certificate Manager Certificate is restricted. For doing so, you must raise a request to issue a new certificate that contains the revised list of domain names.
- By default, all the public certificates are trusted by the applications and browsers, whereas it is recommended that an administrator explicitly validate and configure the applications to trust the private certificates to avoid any misuse.
- No interchanging of any ACM certificates is allowed between any two AWS services. You need to first remove the certificate association to delete the certificate that is already in use.
- Always keep in mind to validate that you either own or have control of all of the domains that are determined in the request made for requesting an ACM certificate.
- At least one fully qualified domain name (FQDN) is mandatory needed, to be included for each ACM Certificate whereas additional names are also appreciated.
- Wildcard names such as *.test.com are allowed while creating your ACM Certificate to protect the various websites under the same domain or subdomains.
- AWS Certificate manager creates an AWS-managed customer master key (CMK) in AWS KMS(Key Management System), the first time when you either import or request a certificate in an AWS region. This unique CMK is an alias as aws/acm for each AWS account and every AWS region. This is required for encrypting the certificate’s private key.
For more information related to the concepts, please visit the Link from AWS documentation.
Features of AWS Certificate Manager
A few key features offered by AWS Certificate Manager are listed below:
Secure Key Management
By provisioning the SSL/TLS certificates, we make sure that the private keys are well protected, stored, and managed. This strong encryption along with accurate key management is the best practice offered by AWS Certificate Manager.
Ability to Import Third-Party Certificates
If you want to provision any external third-party service provider certificate with your AWS resources at no extra cost, you can do so with the AWS Certificate Manager. It is easy to use the AWS Certificate Manager for importing certificates issued by third-party Certificate Authorities (CAs) and quickly deploy them with ACM-integrated AWS resources like Elastic Load Balancers or Amazon API Gateway. The expiration date and replacement of the imported certificates are also possible once the expiration date of the certificate is near. You can also request a free certificate from AWS Certificate Manager, and assign it the task of handling future renewals.
Capability to Manage the Certificates Centrally on The Aws Resource Cloud
With AWS Certificate Manager it is easier and quicker to centrally manage the SSL/TLS certificates provisioned by AWS Certificate Manager for any AWS resource Region. This capability to manage the certificate can happen within a few clicks from the AWS Management Console, AWS CLI, or the AWS Certificate Manager APIs. You also get the ability to audit the usage of each of the certificates from the logs generated by the AWS CloudTrail.
Integrated with Other Aws Resource Cloud Services
You can easily provision the SSL/TLS certificate and deploy these with any ACM-integrated AWS resource like Elastic Load Balancer or API in Amazon API Gateway. For public email-validated certificates, you can also use the AWS Certificate Manager as it works well with AWS Elastic Beanstalk and AWS CloudFormation to effectively manage the public certificates.
Types of Certificates for Use with AWS Certificate Manager
There are four types of Certificates for Use with AWS Certificate Manager:
- Public certificates
- Private certificates
- Imported certificates
- CA certificates
Let us discuss each one of them in brief.
Public Certificates
The Public certificates are the ones that are managed (renewed and deployed) by the AWS Certificate Manager which is only used with ACM-integrated services.
Private Certificates The Private certificates are created as well as managed by the AWS Certificate Manager Private CA in three different ways:
- You delegate the management to ACM where the ACM manages its renewal and deployment with ACM-integrated services.
- You export the certificate and the ACM Private CA automatically takes care of the renewal by sending a notification to Amazon CloudWatch once completed. The renewed certificates and private keys can be downloaded by writing a client-side code and then you can easily take care of its deployment. With ACM, we get the capability to export private certificates and integrate them with containers, IoT devices, EC2 instances, and servers residing on-premises.
- Lastly, you allow the ACM Private CA to offer the flexibility for creating the private keys, generating a certificate signing request (CSR), and issuing private certificates from the ACM Private CA where all the management (renewal and deployment ) is in your hands.
Imported Certificates
ACM allows you to import certificates from a trusted third-party service provider via the AWS Management Console, or AWS CLI. You are held responsible for the management (renewal and deployment before they expire ) of the imported certificates.
CA Certificates
With the ACM private CA(Certificate Authority), you can generate and issue CA certificates which are quite helpful for identifying the private certificate authorities. the CA administrators can create a private CA hierarchy with this CA certificate for stronger security and restrict the access controls for even the most-trusted root CA as per requirement.
AWS Certificate Manager Use Cases
A few of the popular use cases of AWS Certificate Manager are set below:
Securing and Protecting Your Website
AWS Certificate Manager provides an easy way to make it easier to provide the SSL/TLS protocol, you can secure and encrypt the sensitive data in transit in addition to authenticating the use of SSL/TLS certificates for enabling secure connections between the browsers and your website.
Improved Uptime
All the challenges related to maintaining SSL/TLS certificates, like certificate renewals, are managed with AWS Certificate Manager without the hassle to track the expiration dates and so on.
Helps to Meet the Compliance Requirements
AWS Certificate Manager helps the organization meet regulatory and compliance requirements with its easy enabling of the SSL/TLS for securing and encryption of data in transit.
AWS Certificate Manager Pricing
The pricing structure of the AWS certificate Manager is quite simple. All the Public SSL/TLS certificates that you provision via the AWS Certificate Manager are charged free of cost whereas you only pay for the AWS resources that are created to keep your application running.
You only get charged for each of the active ACM Private CA per month pro-rated. The AWS Certificate Manager Private CA offers its users to pay monthly for the service and private certificates that they create. These prices go down per certificate as the number of private certificates increases.
Getting Started with AWS Certificate Manager
So far we learned the concepts around AWS Certificate Manager, now let us get started with AWS Certificate Manager, and with the basic six steps, we can easily request an SSL/TLS Certificate through the AWS Certificate Manager.
Let's get started!!!
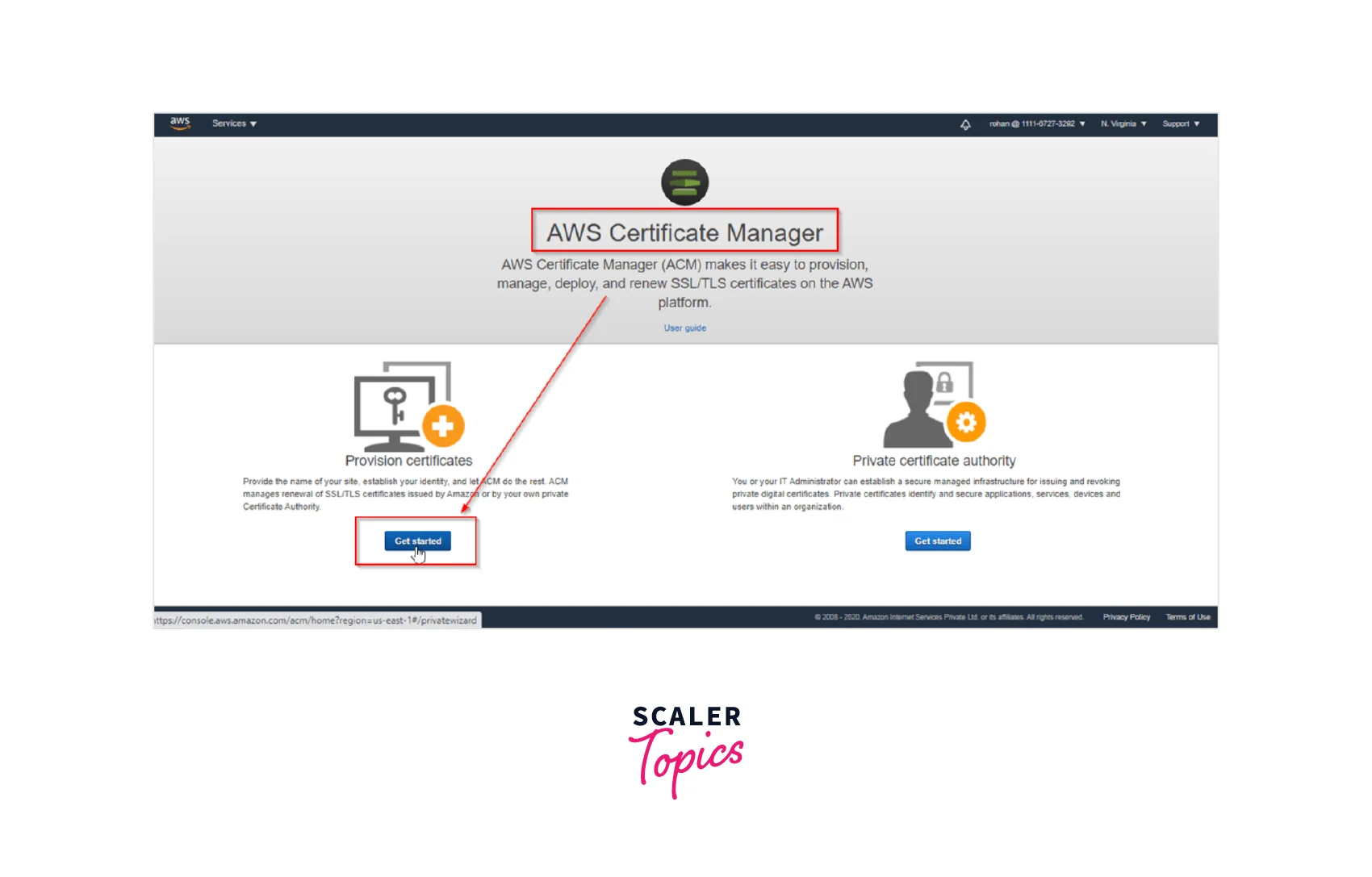
Step 1: As shown below, the first step starts with Provisioning Certificates. Navigate to the ACM console by signing in to the AWS Management Console. Select Get started to request the required certificate.
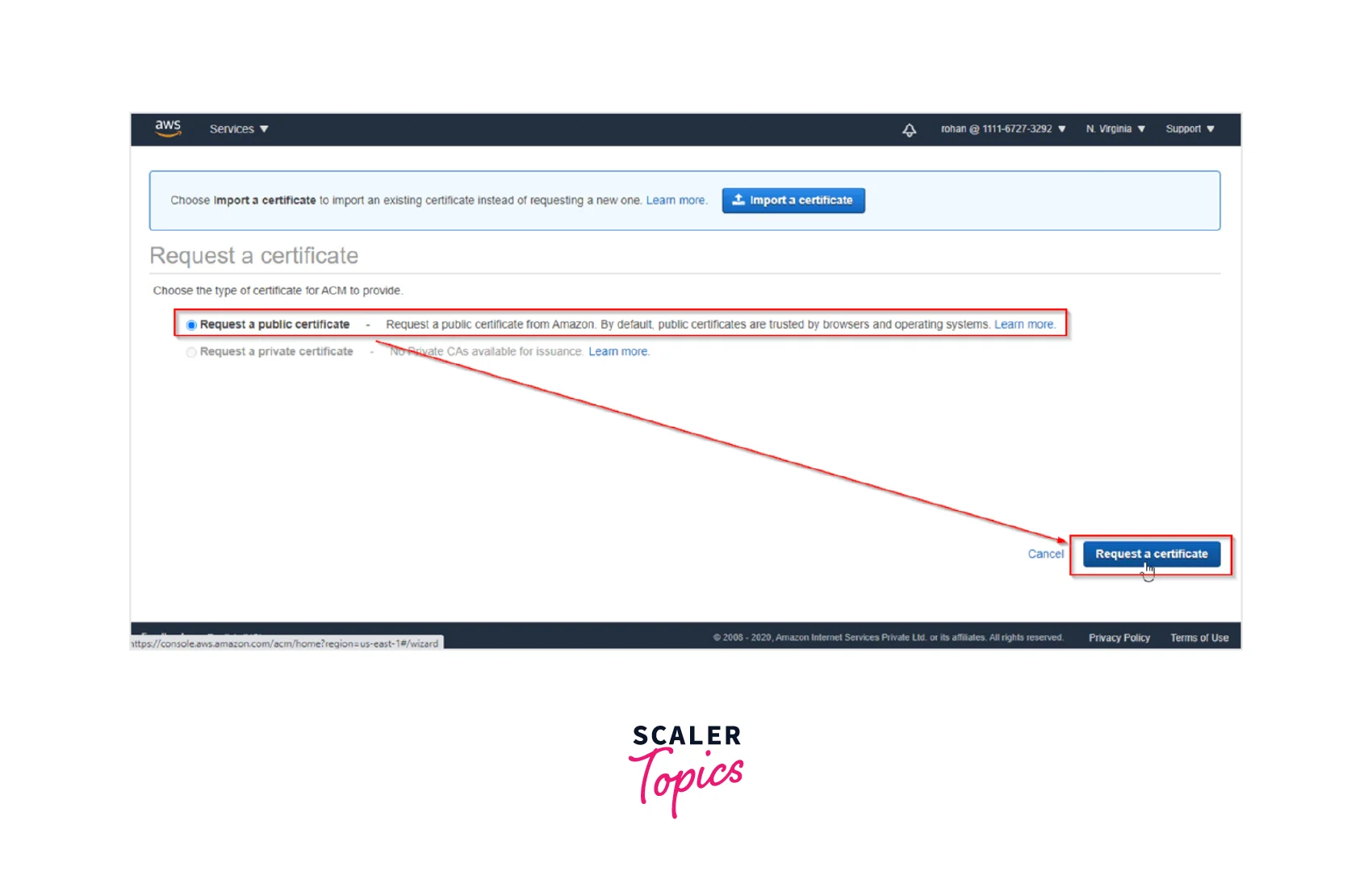
Step 2: Second step is to Request a New Certificate by choosing the Request a certificate button on the right bottom corner as shown below.
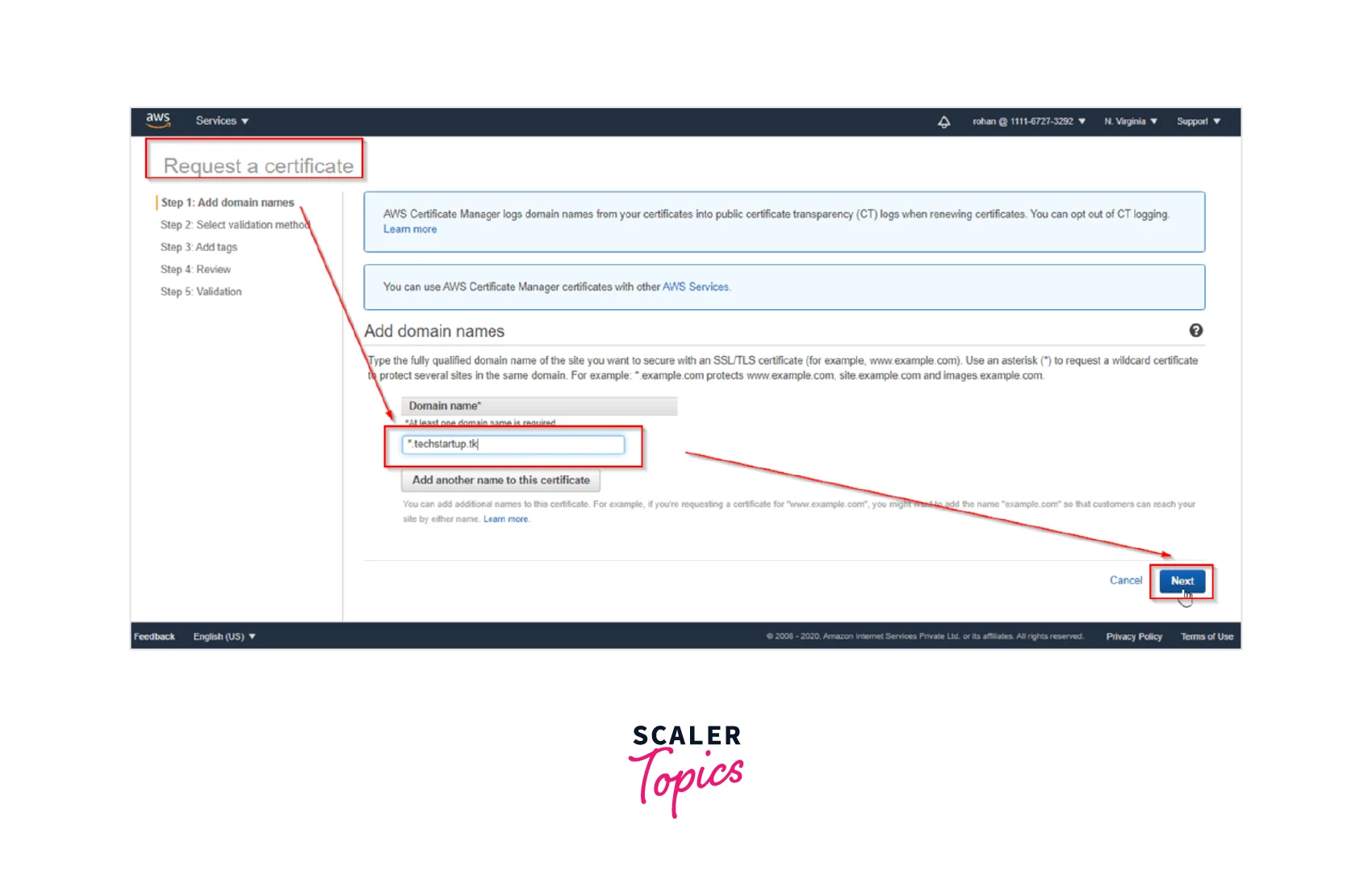
Step 3: Next we Provide the Domain Names to the certificate that we requested as seen below. Keep a check to positively add a wildcard before the domain name.
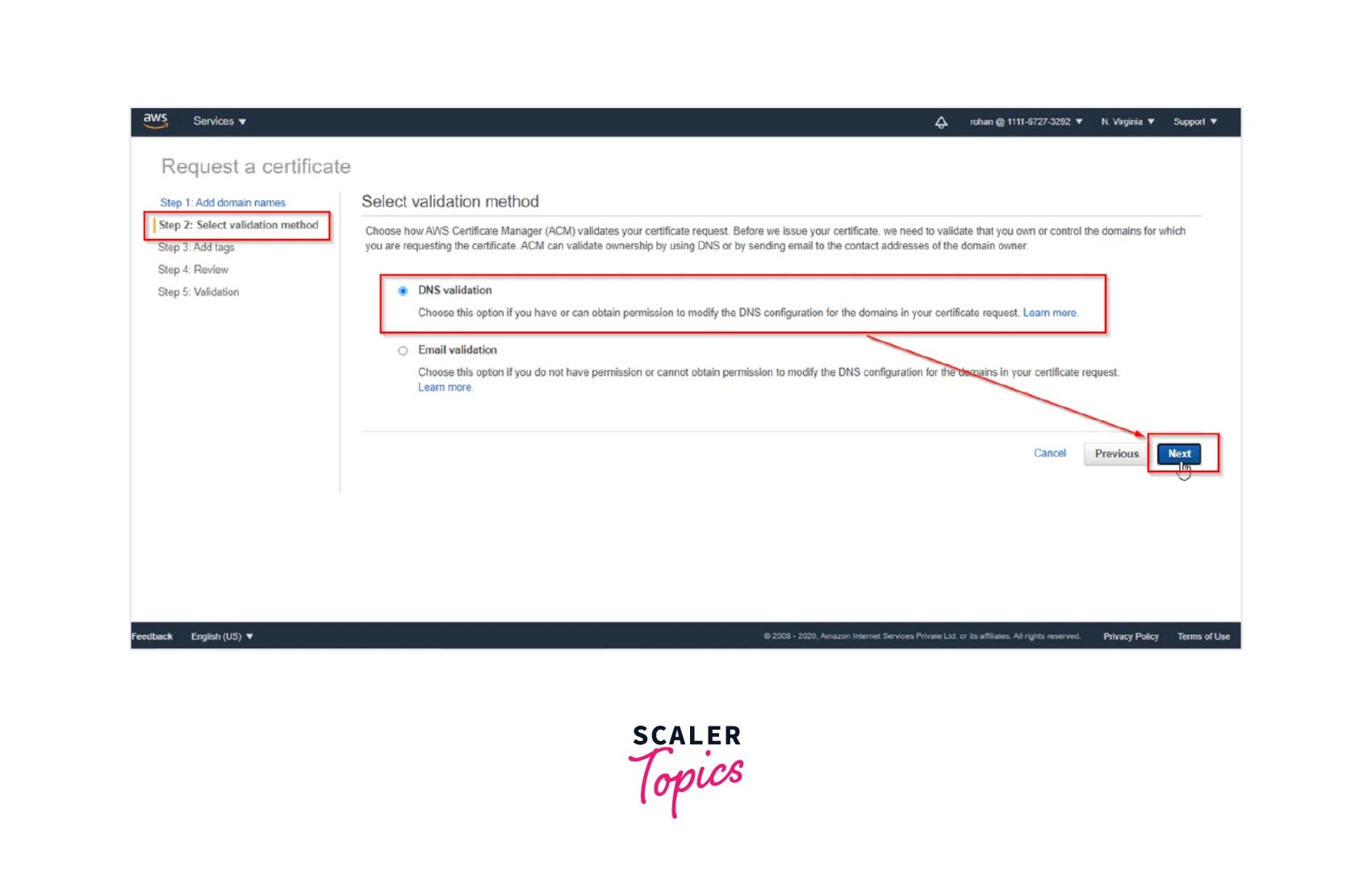
Step 4: Moving forward we need to Choose the appropriate Validation Method of the two options as shown below. We have two options: 'DNS Validation' and 'Email Validation'. We will select the DNS validation option, where we can specify the CNAME record for our DNS configuration. This shall help to establish control of the domain name. Now, select the DNS validation button and move to the next page by clicking Next.
Step 5: Next we Create a Record in Route53 by clicking on the Create a record in Route53 button which shall automatically create a CNAME record for us in the Route53 hosted zone as can be seen below.
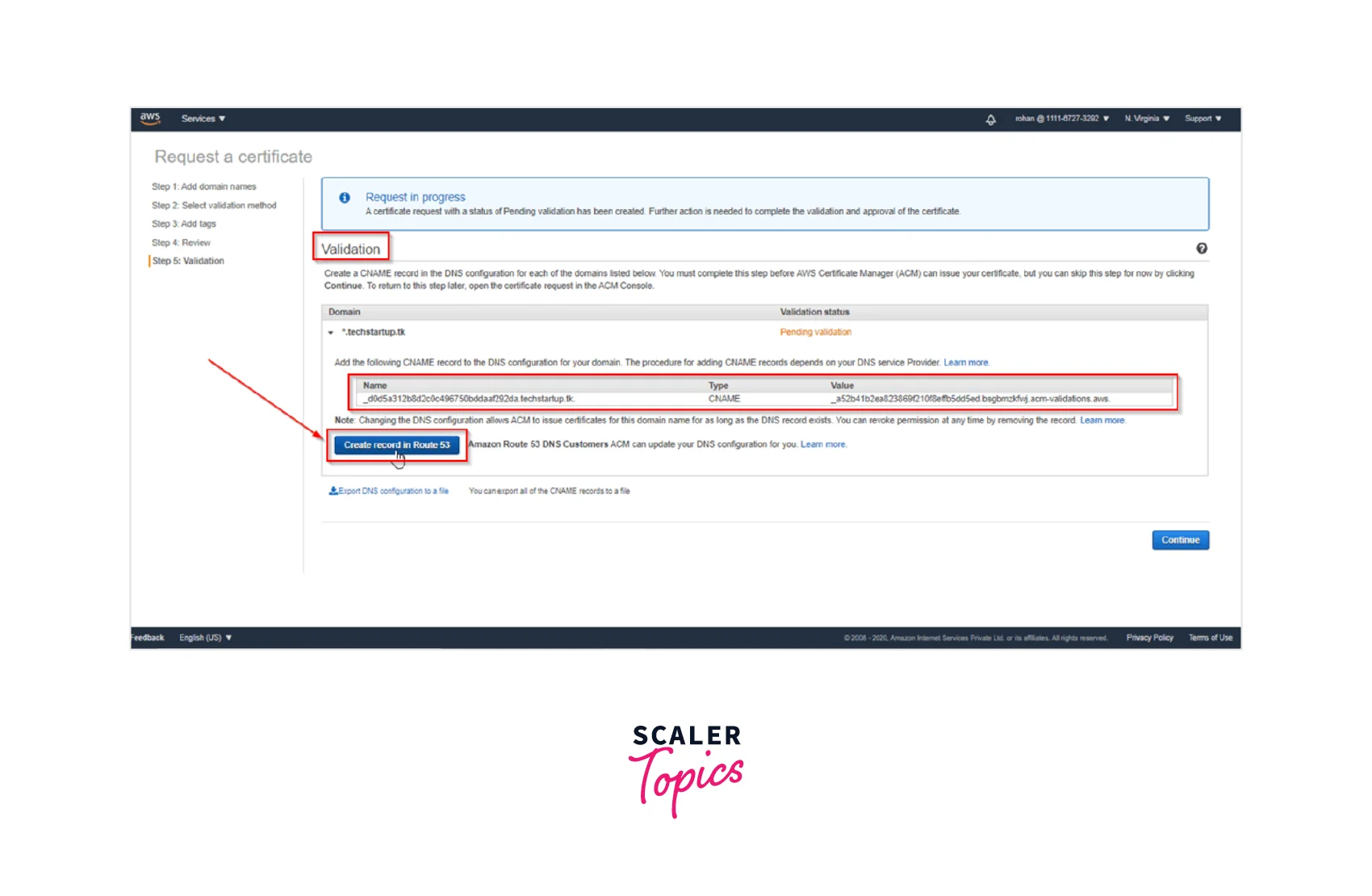
Step 6: Finally, we have the Certificate Issued to us. Once we Refresh and the validation is completed, we shall see the status of the certificate will change to issued as seen below.
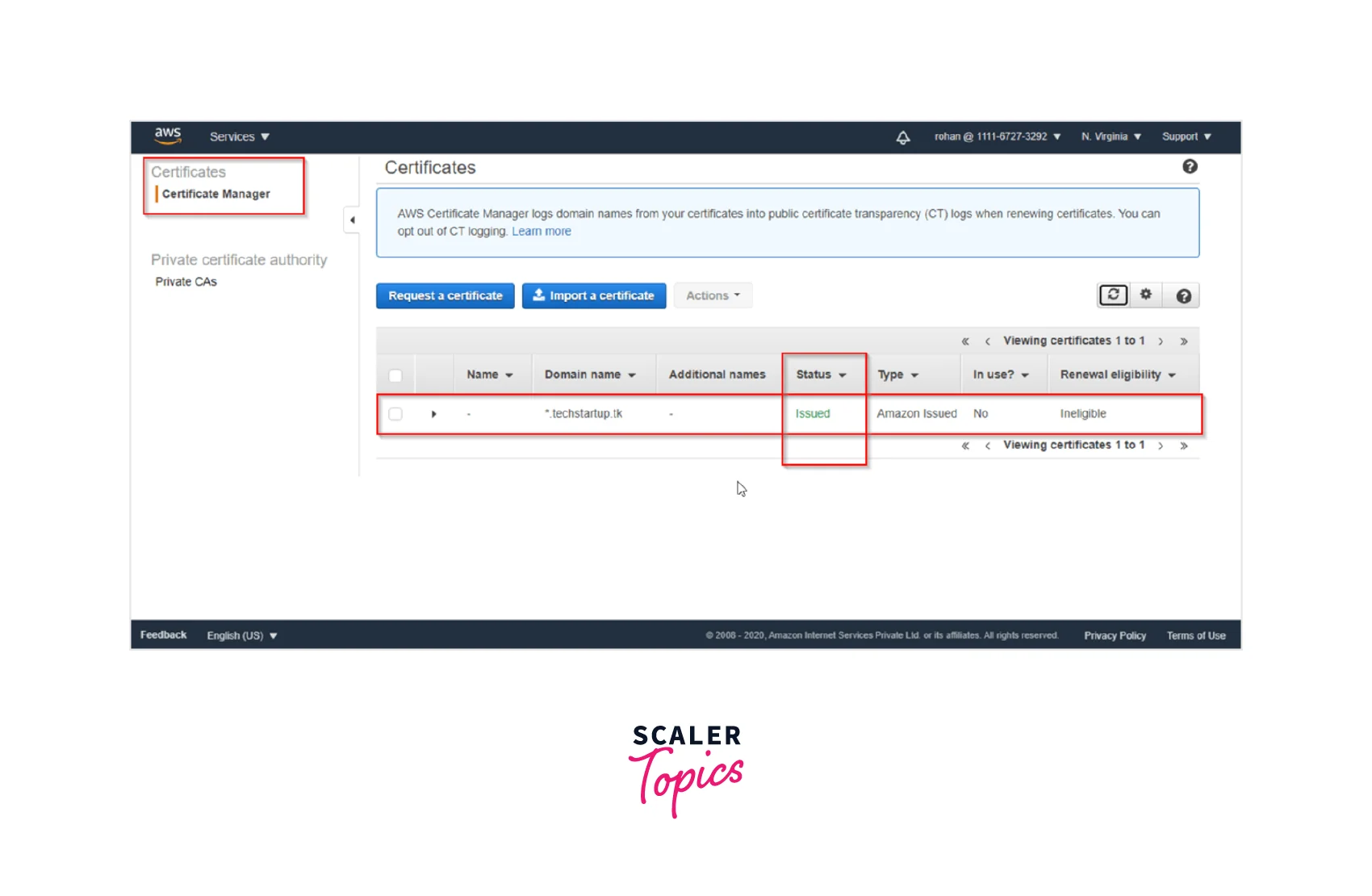
Voila!!! You have successfully created and issued your first ever 'SSL/TLS Certificate' that shall be used to attach with the ACM integrated services.
Importing Certificates into AWS Certificate Manager
We can import any external certificate (issued by a trusted third-party service provider) into the ACM via either the AWS console or the AWS CLI. Non-AWS issuers are not allowed to import the certificate yet.
Importing the Private Certificate via The AWS Console:
Step 1: Login to the ACM console via the link. For first-time users of ACM, you shall see the AWS Certificate Manager headline where you need to select the Get started option as shown below.
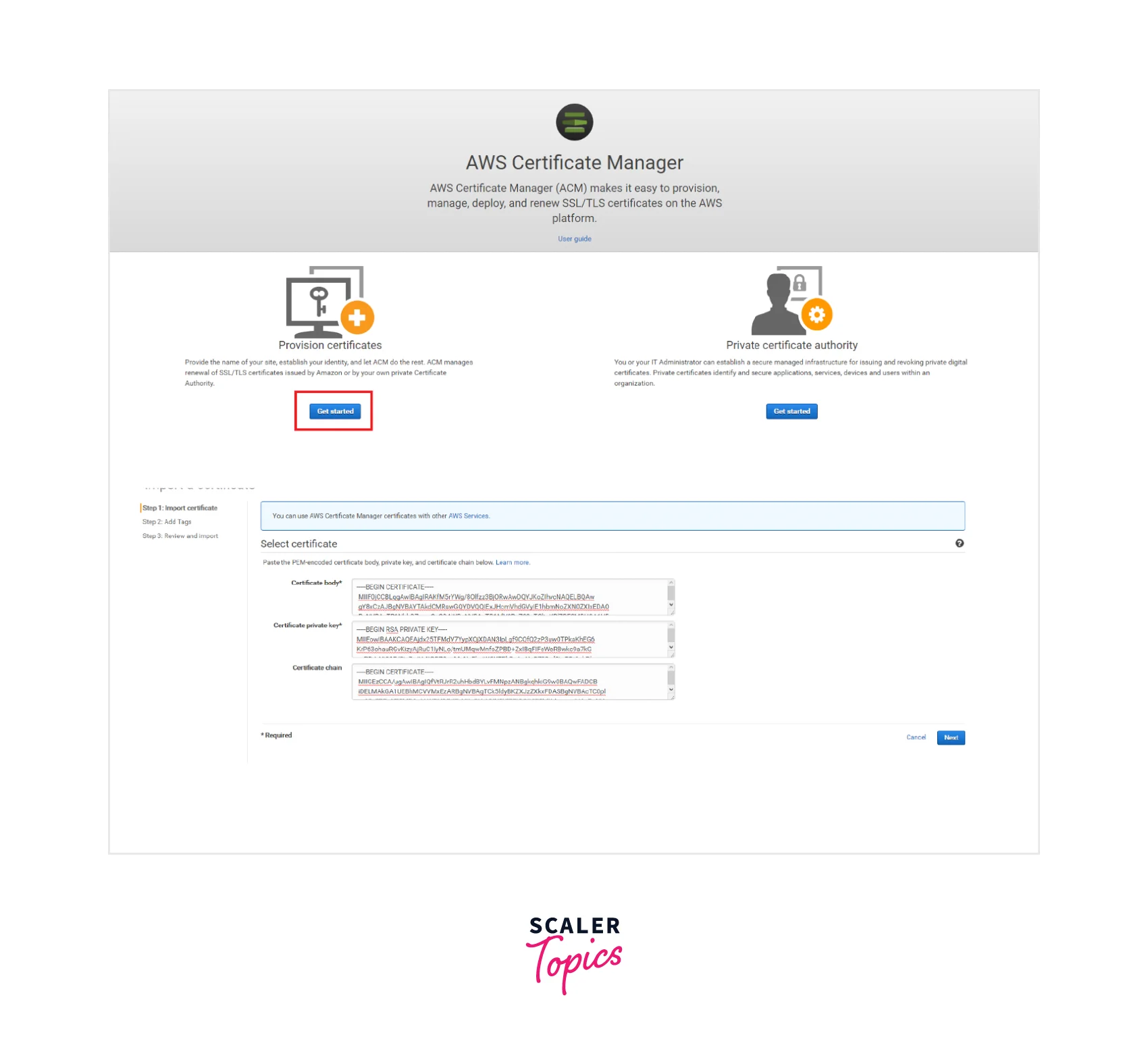
Step 2: Now, select the Import a certificate option as shown below where you can perform any of the below methods:
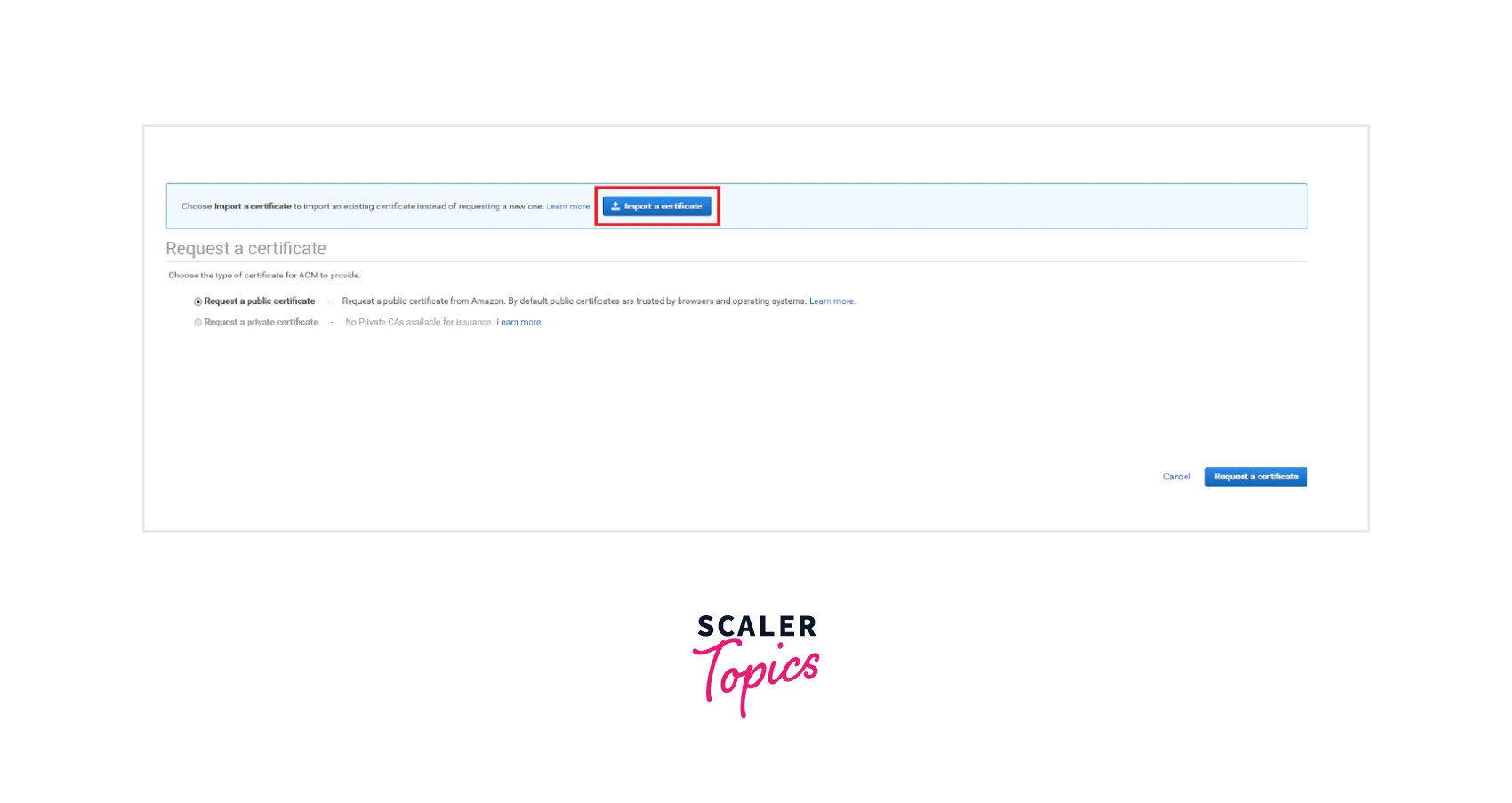
- You need to paste the PEM-encoded certificate for importing the Certificate body. This must begin with -----BEGIN CERTIFICATE----- and end with -----END CERTIFICATE-----
- You need to paste the certificate's PEM-encoded, the unencrypted private key for importing the Certificate private key This must begin with -----BEGIN PRIVATE KEY----- and end with -----END PRIVATE KEY-----.
- To import a Certificate chain, you should paste the PEM-encoded certificate chain which is an Optional suggestion

Step 3: You need to now Review and Import by cross-checking the metadata shown about the certificate to make sure it's the same that you wanted to import.
The fields to check are mentioned below:
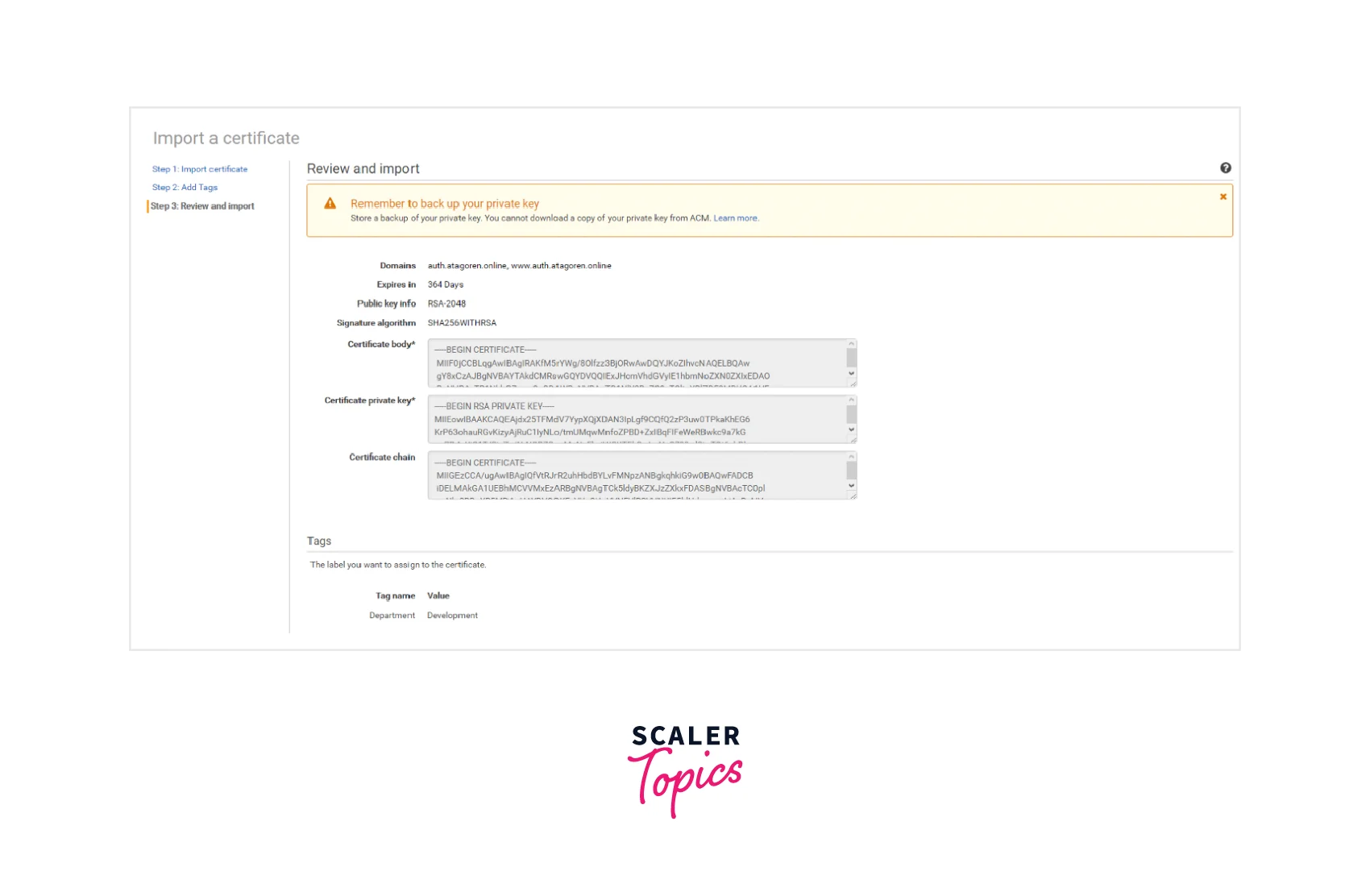
- Domains — Fully qualified domain names (FQDN) which are successfully authenticated by the certificate are listed here.
- Expires in — Shows the number of days until which the certificate is active.
- Public key info — Shows the key pair generated using the cryptographic algorithm used.
- Signature algorithm — Shows the certificate's signature created using the cryptographic algorithm.
- Can be used with — All the ACM integrated services that are well supported by the certificates that you want to import are aggregated under this as a list.
Step 3: Once all the fields are validated, select the IMPORT option to import the certificate into the AWS Certfatcte Manager.
Importing the Private Certificate via Cli:
Suppose you want to import a certificate via the CLI, where The PEM-encoded certificate is stored in the Certificate.pem file. The PEM-encoded certificate chain is stored in the CertificateChain.pem file. The PEM-encoded, unencrypted private key is stored in the PrivateKey.pem file.
The below shall be used to import the certificate:
Once successful, it shall return the Amazon Resource Name (ARN) of the imported certificate.
For more information related to the import certificates, please visit link from AWS documentation.
Exporting Certificates
We can export a certificate for usage in your private PKI (public key infrastructure) environment that is, issued by AWS Private CA. Here, the file we are exporting could include, a certificate, the encrypted private key, or even the certificate chain.
Note: It advised to never export a publicly trusted ACM certificate or even its private key. Also, the exported file must always be securely stored.
Let us discuss how we can Export Certificates via the AWS console or CLI:
Exporting the private certificate via the AWS console:
Step 1: Select the AWS Certificate Manager by logging into the AWS console via the link. Choose the certificate that needs to be exported which can be done by selecting the Export (for private certificates only) button on the Actions menu.
Step 2: Type the passphrase and confirm the private key.
Quick Note: It is recommended to use any ASCII character except #, $, or %. while creating the passphrase.
Step 3: Select the Generate PEM Encoding option.
Step 4: Now either you can copy the certificate, encrypted key, or the certificate chain which can either be added to the memory or exported as a file by selecting the Export button.
Step 5: Lastly, complete exporting the certificate by selecting the Done button.
Exporting the Private Certificate via The AWS CLI:
By calling the export-certificate command we can easily export a private certificate along with a private key. Also, at the time of running the command, you will have to assign a passphrase.
Note: It is recommended to use a file editor to strong the passphrase in a file and then pass this file in the space of the passphrase as a security practice. This help to keep your passphrase secure and save it from not getting stored in the command history which eventually help to secure the passphrase form from getting leaked to others.
The below commands are used on CLI to apply the PEM formatting.
[Windows]
[Linux]
Output
Below is the output for the above commands. The output is represented as a base64-encoded, PEM-format certificate, that contains the certificate chain as well as the encrypted private key.
You can also output all as a file, by simply appending the > redirector as shown below:
For more information related to the export certificates, please visit link from AWS documentation.
Benefits of AWS Certificate Manager
Below are the listed benefits that AWS Certificate Manager offers are:
- Renewal Process of The Certificate Is Managed:
With Amazon Certificate Manager, you don't need to worry about the renewal process of the certificates. The renewal process is completely managed in ACM (as it can automate renewal and deployment of these) which is used with ACM-integrated services, like API Gateway and Elastic Load Balancing.
- Public certificates are free for ACM-integrated services No additional fee is charged for provisioning any public SSL/TLS certificates which you shall be implemented with ACM-integrated services, like API Gateway and Elastic Load Balancing. With Amazon Certificate Manager, you only pay for the AWS resources that you would create for keeping your application running.
- Easy to issue certificates: All the time-taking along with the error-prone steps are skipped with AWS Certificate Manager for any SSL/TLS certificate issuing. Within a few clicks, we can easily request any trusted SSL/TLS certificate from AWS. Also, the deployment of the certificates to enable SSL/TLS for your website is taken care of. All the hassle of generating a key pair or the certificate signing request (CSR), submitting a CSR to a Certificate Authority, and even uploading and installation of the certificate is removed efficiently.
Conclusion
- AWS Certificate Manager is an AWS service that can help with provisioning and managing(renewal and deployment-related work) of the SSL/TLS certificates that are integrated with AWS services and AWS Certificate Manager integrated resources.
- All the Public SSL/TLS certificates that you provision via the AWS Certificate Manager are charged free of cost whereas you only pay for the AWS resources that are created to keep your application running.
- All the challenges related to maintaining SSL/TLS certificates, like certificate renewals, are managed with AWS Certificate Manager without the hassle to track the expiration dates and so on.
