AWS Cloud HSM
Overview
AWS CloudHSM is a Hardware Security Module (HSM) service hosted in the cloud that allows you to execute cryptographic operations and host encryption keys. With contractual, severe corporate, and regulatory compliance standards, it provides consumers with additional data protection. It allows you to produce and utilize encryption keys on AWS Cloud.
What is AWS Cloud HSM?
AWS Cloud HSM delivers hardware security modules in the AWS Cloud. A hardware security module (HSM) is a computational device that handles cryptographic operations and provides secured storage space for cryptographic keys.
- When you utilize an HSM from AWS CloudHSM, you may execute the following cryptographic tasks:
- Create, store, import, export, and manage cryptographic keys, including symmetric and asymmetric key pairs.
- Encrypt and decrypt data with symmetric and asymmetric algorithms.
- Use cryptographic hash functions to construct message digests and hash-based message authentication codes (HMACs).
- Cryptographically sign data (including code signing) and validate signatures.
- Produce cryptographically safe random data
How Does It Work?
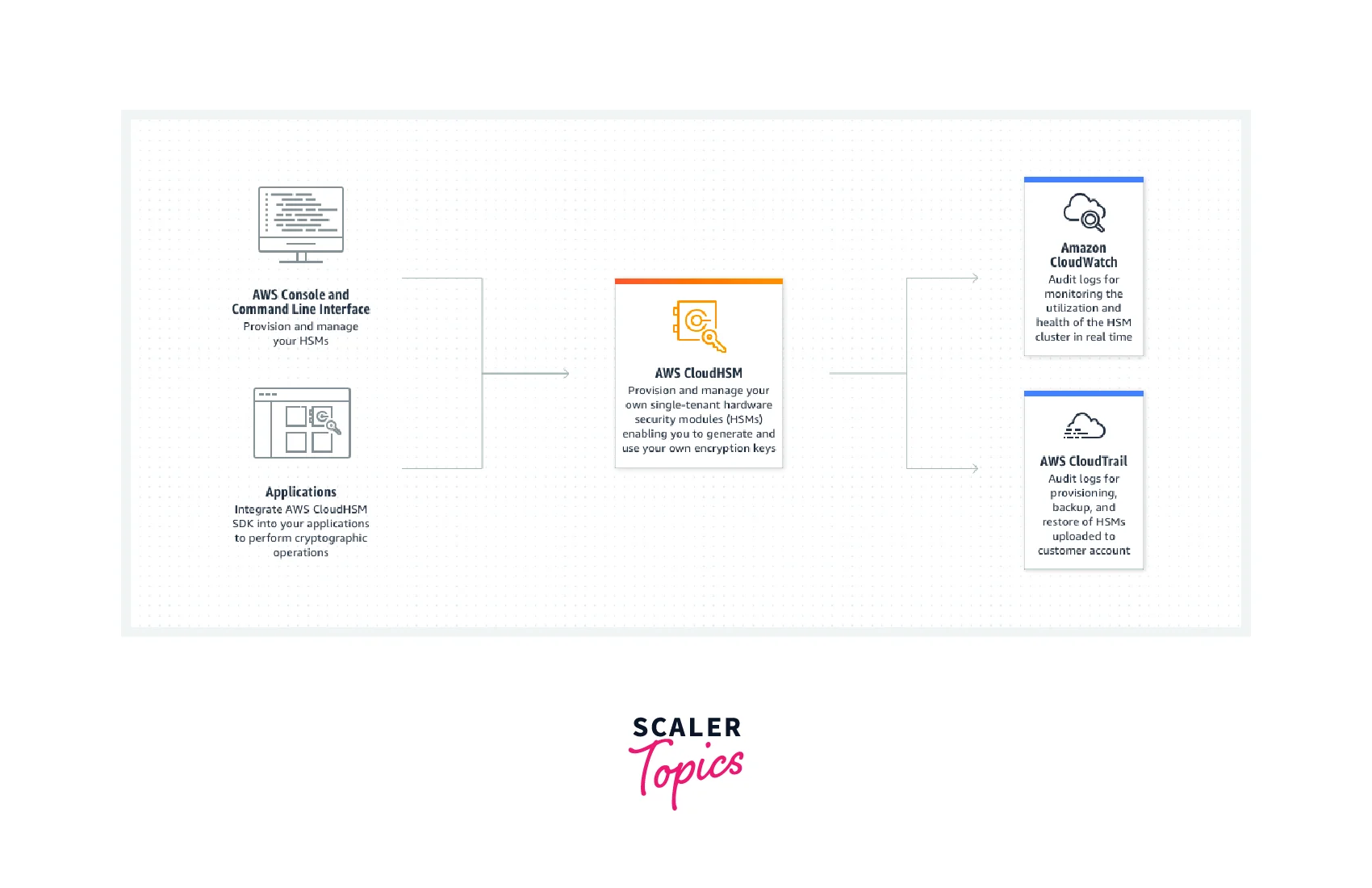
- To use the AWS CloudHSM service, you must first construct a CloudHSM cluster. These clusters feature numerous HSMs that span various Availability Zones within a region. In a cluster, the HSMs are automatically synchronized and load-balanced.
- Each HSM functions as a network resource in an Amazon VPC. Furthermore, you will have single-tenant access to each HSM within an Amazon VPC (Virtual Private Cloud).
- Because AWS CloudHSM operates on Amazon VPC, you may use typical VPC security rules to govern HSM access.
- AWS CloudHSM API or CLI may add and delete HSMs from a cluster with a single call. A CloudHSM cluster can be set up on EC2 instances once created.
- Users may therefore utilize HSM with apps running on Amazon EC2 instances. HSMs can connect to applications via mutually authorized SSL channels established by HSM client software.
- As a result, network latency is minimized in the connection since HSMs are positioned near EC2 instances in Amazon Data Centers.
- AWS CloudHSM is completely protected to preserve encryption keys and includes a tamper detection system. As a result, after three unsuccessful tries to access an HSM partition using admin credentials, the appliance erases its partitions.
When To Use AWS CloudHSM?
AWS CloudHSM is a service that allows you to create and manage cloud-based hardware security modules. A hardware security module (HSM) is a type of security device used to produce and store cryptographic keys.
When Should I Use It?
When you want to control the HSMs that create and store your encryption keys, use AWS CloudHSM. AWS CloudHSM allows you to establish and administer HSMs, create users, and define their rights. You also generate the symmetric and asymmetric key pairs used by the HSM.
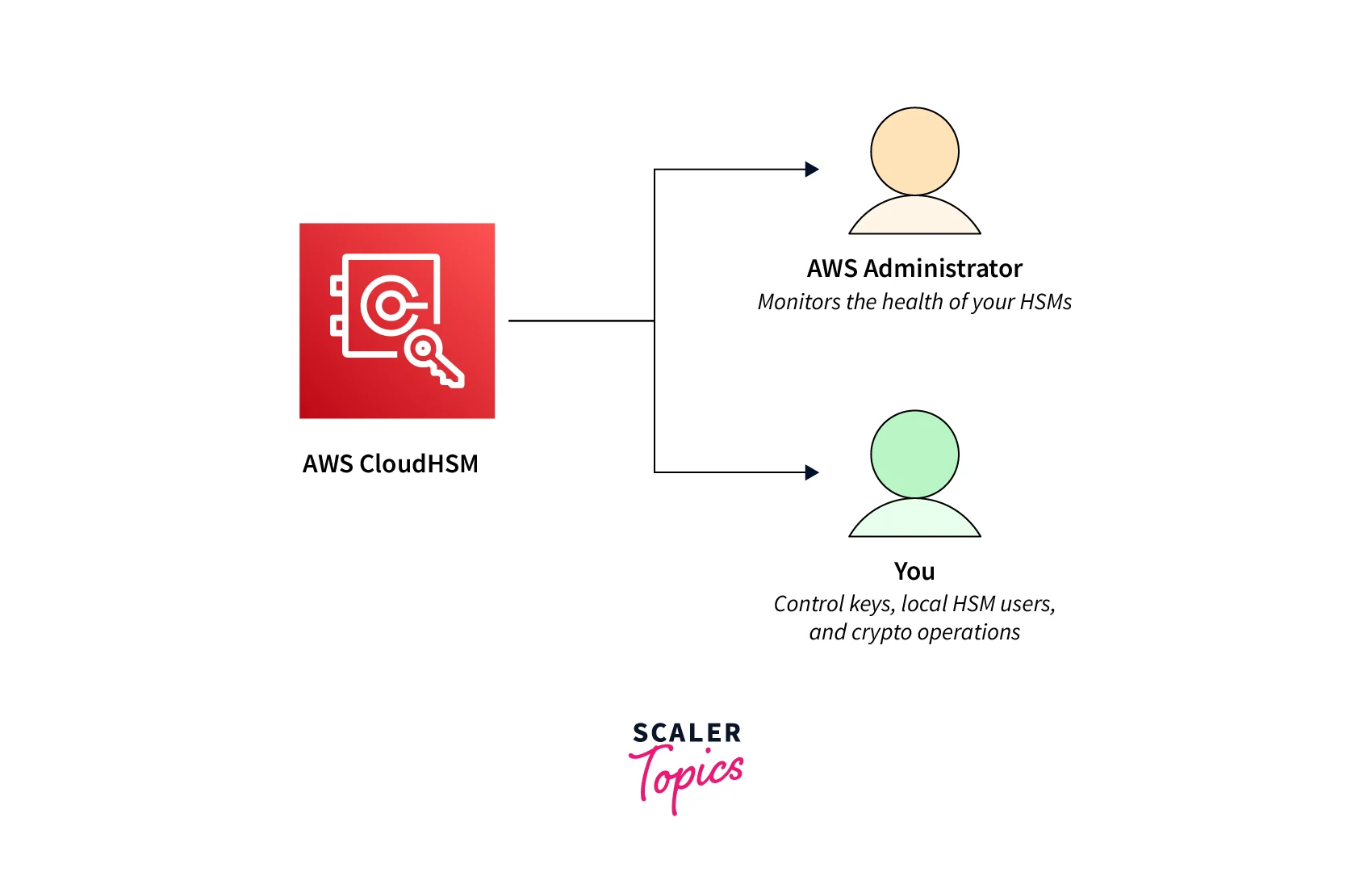
Separation of duties and role-based access control is inherent in the design of CloudHSM. AWS has a limited credential to the HSM that permits us to monitor and maintain the health and availability of the HSM, take encrypted backups, and to extract and publish audit logs to your CloudWatch Logs AWS has no access to any keys or data inside your CloudHSM cluster and cannot perform any operations other than those allowed for an HSM appliance user.
When Should I Use Something Different?
Try AWS Key Management Service if you need to safeguard your encryption keys in a service supported by FIPS-validated HSMs but do not need to administer the HSM.
NIST considers non-validated encryption to provide no protection for information or data—in effect, the data would be regarded as unprotected plaintext. FIPS 140-2 or FIPS 140-3 are applicable if the agency stipulates that the information or data be cryptographically safeguarded. In other words, if cryptography is required, it must be validated. If the cryptographic module is revoked, it is no longer possible to utilize it.
CloudHSM complements existing data protection solutions and allows you to protect your encryption keys within HSMs that are designed and validated to government standards for secure key management.
CloudHSM allows you to securely generate, store, and manage cryptographic keys used for data encryption in a way that keys are accessible only to you.
A Hardware Security Module (HSM) provides secure key storage and cryptographic operations within a tamper-resistant hardware device.
HSMs are designed to securely store cryptographic key material and use the key material without exposing it outside the cryptographic boundary of the hardware.
You can use the CloudHSM service to support a variety of use cases and applications, such as database encryption, Digital Rights Management (DRM), Public Key Infrastructure (PKI), authentication and authorization, document signing, and transaction processing.
AWS Cloud HSM Concepts
AWS CloudHSM Clusters
In a cluster, AWS CloudHSM delivers hardware security modules (HSMs). A cluster is a group of independent HSMs kept in sync by AWS CloudHSM. Consider a cluster to be one logical HSM. When you conduct a task or operation on one of the HSMs in a cluster, the other HSMs in the cluster are automatically updated.
You may build a cluster with 1 to 28 HSMs. You can arrange the HSMs in an AWS Region in separate Availability Zones. Increasing the number of HSMs in a cluster improves performance. Redundancy and high availability are provided by distributing clusters across Availability Zones.
Individual HSMs might be challenging to integrate into a synchronized, redundant, highly available cluster, but AWS CloudHSM handles some of the undifferentiated hard liftings for you. You can add and delete HSMs from a cluster while AWS CloudHSM keeps them linked and in sync.
Cluster Architecture
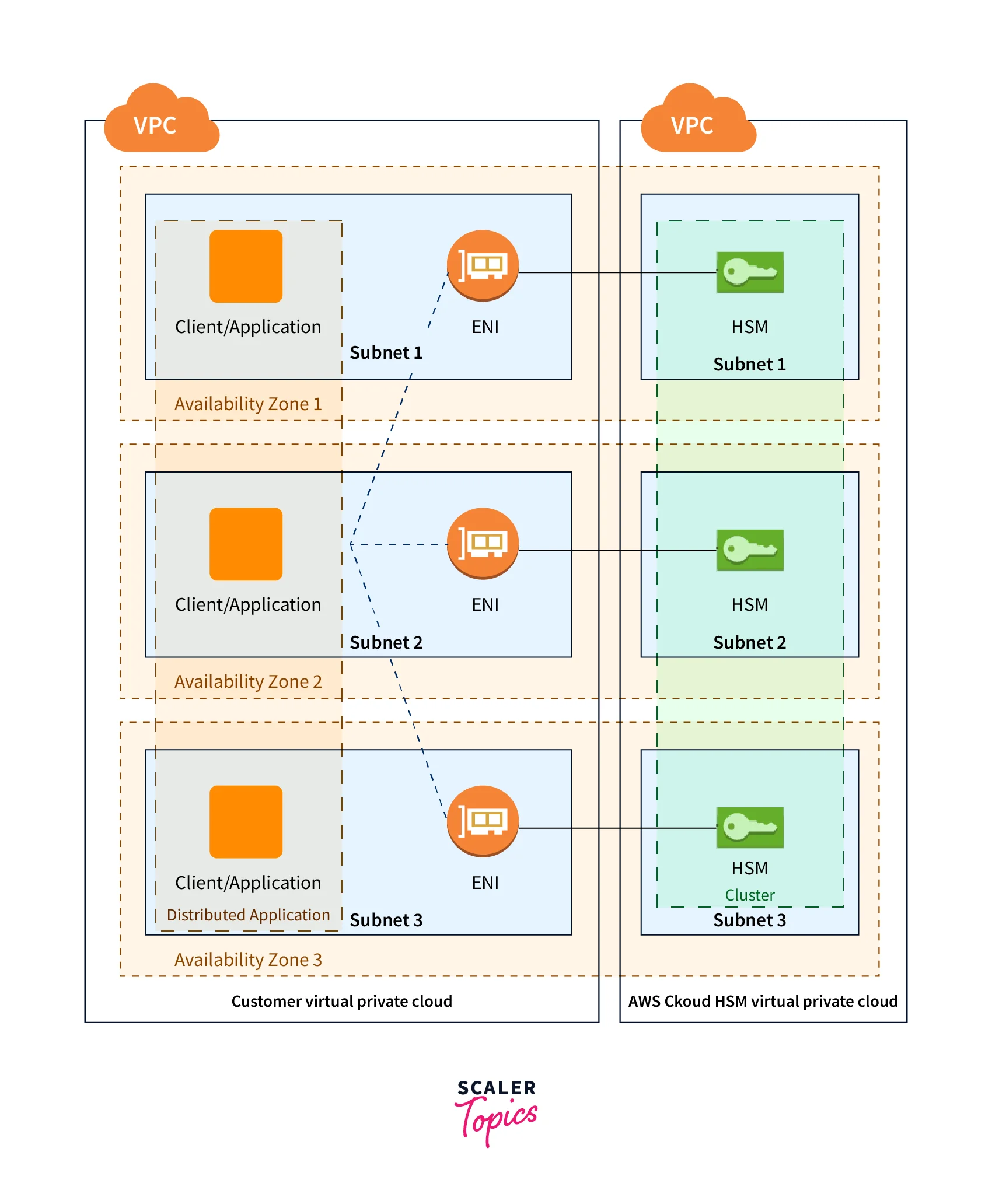
When constructing a cluster, specify an Amazon Virtual Private Cloud (VPC) and one or more subnets in that VPC from your AWS account. We recommend that you build one subnet in each AWS Region's Availability Zone (AZ).
When you create an HSM, you have to specify the cluster and Availability Zone. By distributing the HSMs over many Availability Zones, you gain redundancy and high availability if one Availability Zone fails.
When you create an HSM, AWS CloudHSM creates an elastic network interface (ENI) in your AWS account's specified subnet. The elastic network interface is used to communicate with the HSM. The HSM is housed in a separate VPC under an AWS account controlled by AWS CloudHSM. The HSM and its associated network interface are in the same Availability Zone.
The AWS CloudHSM client software is required to interface with the HSMs in a cluster. Typically, the client is installed on Amazon EC2 instances, known as client instances, located in the same VPC as the HSM ENIs, as indicated in the image below. However, this is not strictly essential; you may install the client on any capable computer that can connect to the HSM ENIs. Through their ENIs, the client connects with the individual HSMs in your cluster.
- A collection of individual HSMs.
- Other HSMs are automatically kept up to date when you perform a task on one HSM in a cluster.
- You can create a cluster that has 1 to 28 HSM and place the HSMs in different AZs in a region.
- Cluster provides higher performance as you add more HSMs.
- When you add a new HSM to a cluster:
- AWS CloudHSM backup all the keys, users, and policies on an existing HSM.
- Restores the backup onto the new HSM to keep HSMs in sync.
- Supports cluster load balancing.
The diagram below depicts an AWS CloudHSM cluster of three HSMs, each in a distinct Availability Zone inside the VPC.
Backups
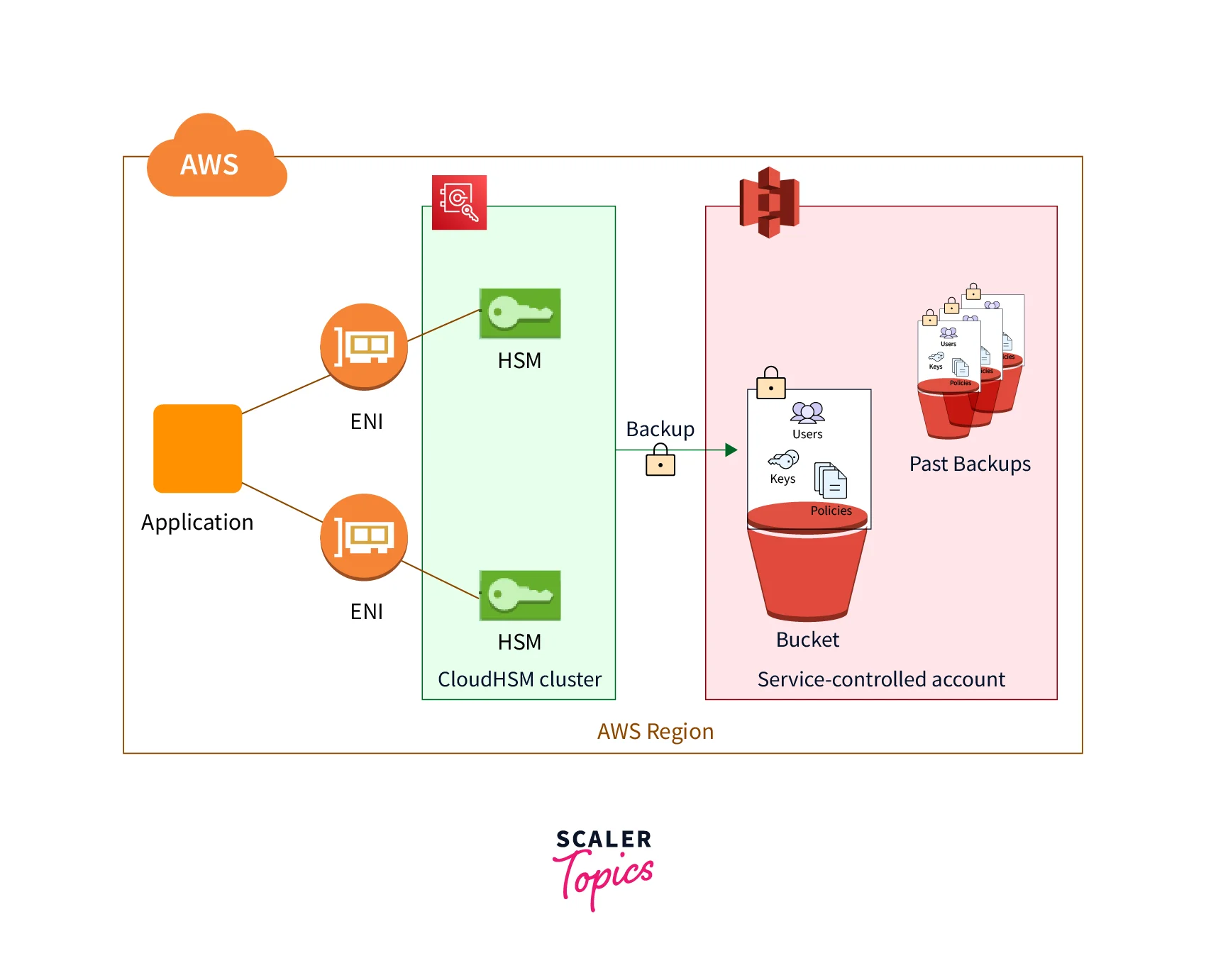
AWS CloudHSM performs regular backups of the cluster's users, keys, and rules. Backups are stored in the same region as your cluster in a service-controlled Amazon S3 bucket. The above diagram depicts your backups' link to the cluster. Backups are safe, long-lasting, and updated regularly.
Security of Backups
When AWS CloudHSM backs up data from the HSM, the HSM encrypts all data before transmitting it to AWS CloudHSM. The data is never sent out of the HSM unencrypted.
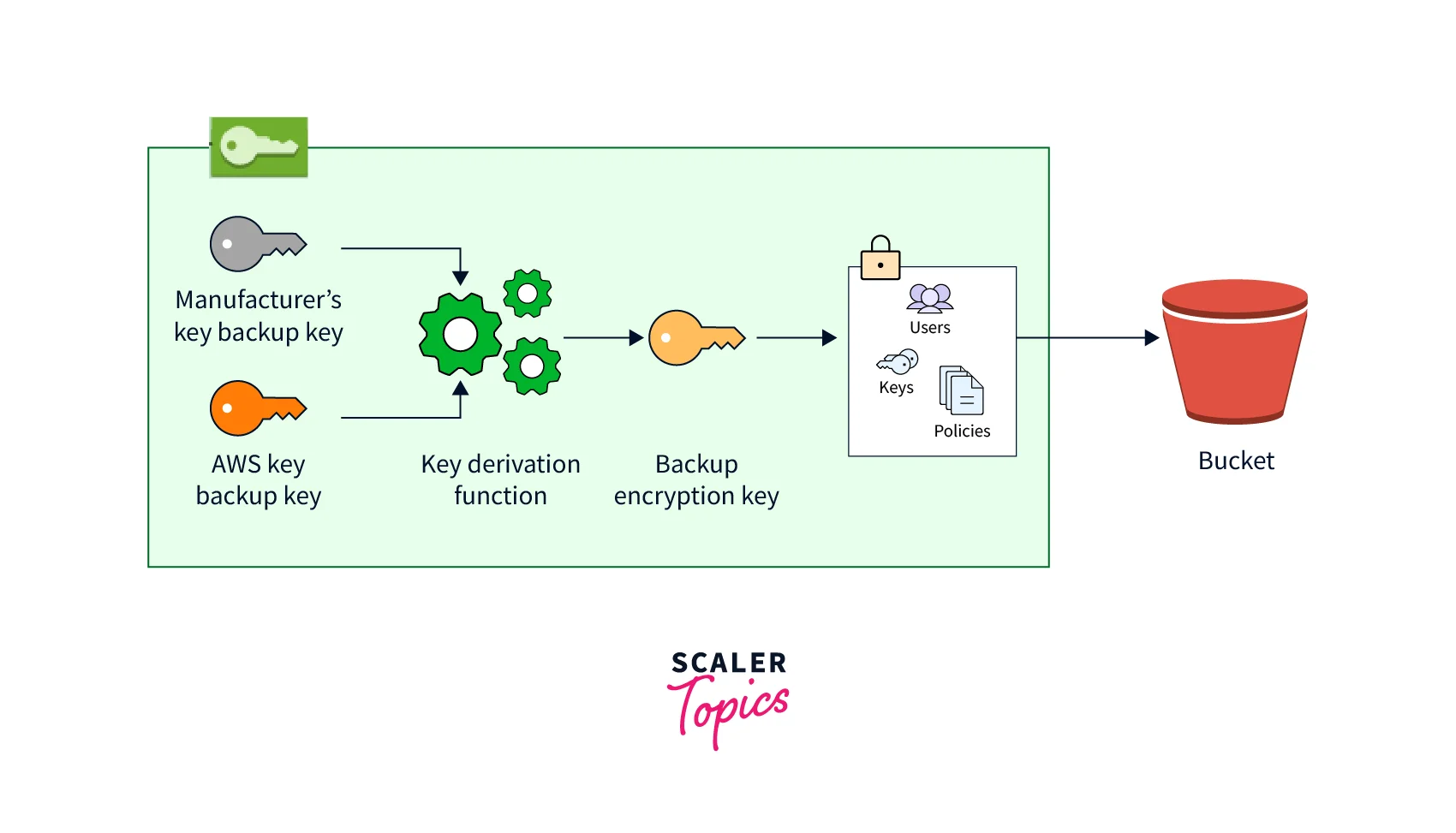
The HSM encrypts its data using an ephemeral encryption key known as the ephemeral backup key (EBK). When AWS CloudHSM does a backup, the EBK is an AES 256-bit encryption key produced within the HSM. The HSM creates the EBK, which is then used to encrypt the HSM's data using a FIPS-approved AES key wrapping approach that adheres to NIST special publication 800-38F. The HSM then sends the encrypted data to AWS CloudHSM. An encrypted duplicate of the EBK is included in the encrypted data.
The HSM encrypts the EBK using another encryption key known as the persistent backup key (PBK). The PBK also functions as an AES 256-bit encryption key. The HSM generates the PBK using a FIPS-approved key derivation function (KDF) in counter mode, by NIST special publication 800-108. This KDF's inputs include the following:
The hardware manufacturer permanently embeds a manufacturer key backup key (MKBK) in the HSM hardware.
When AWS CloudHSM first configures the HSM, it securely installs an AWS key backup key (AKBK).
The following diagram summarizes the encryption procedures. The backup encryption key is a representation of both the persistent backup key (PBK) and the ephemeral backup key (EBK).
AWS CloudHSM can only restore backups to AWS-owned HSMs manufactured by the same manufacturer. Because each backup retains all of the original HSM's users, keys, and settings, the restored HSM has the same safeguards and access restrictions as the original. All other data on the HSM that existed before the restored data overwrite the restoration.
A backup is made up entirely of encrypted data. Before storing a backup in Amazon S3, the service encrypts it with AWS Key Management Service (AWS KMS).
Backups Durability
AWS CloudHSM maintains cluster backups in an Amazon S3 bucket managed by the service. Backups have the same durability level as any item saved in Amazon S3: 99.999999999%.
HSM Users
Unlike other AWS services and resources, you do not require AWS Identity and Access Management (IAM) users or IAM rules to access resources within your cluster. Instead, with AWS CloudHSM, you employ HSM users directly on the hardware security module (HSM).
Each HSM user is authenticated by the HSM using credentials that you specify and maintain. Each HSM user has a type that governs the actions that may be performed on the HSM as that user.
- HSM users differ from IAM users.
- A CloudHSM Management Utility (CMU) is required to create and manage users on HSM
- An HSM user has a type that specifies which actions they may carry out on HSM.
- Precrypto officer (PRECO) - a temporary user on the cluster's initial HSM.
- The crypto officer (CO | PCO) manages users and provides two-factor authentication.
- A crypto user (CU) is someone who manages keys and executes cryptographic operations.
- The appliance user (AU) is in charge of cloning and synchronization.
- Quorum authentication is supported.
Keys
- In CloudHSM, only a CU can create a key.
- To manage keys on HSM, you may use the following:
- Library for PKCS #11
- JCE supplier
- CNG and KSP suppliers
- key mgmt util
- To synchronize keys between clusters, use the sync key command in CMU.
CLI Tools
- CloudHSM Management Software (CMU)
- The cloudhsm mgmt utility assists COs in managing users in HSMs.
- It also includes a command that enables CUs to share keys and get and set key properties.
- Utility for Key Management (KMU)
- CUs can manage keys on HSMs using a key mgmt util.
- CloudHSM resources can be tagged.
AWS CloudHSM Client SDK
The AWS CloudHSM Client SDK contains tools for integrating your apps with your cluster's HSM and performing HSM administration activities. This program includes a Public Key Cryptography Standards #11 (PKCS #11) implementation, which provides a standard for interacting with hardware devices that store cryptographic information and execute cryptographic tasks.
The Client SDK also provides software for offloading cryptographic activities to the HSM from a different platform or language-based programs, such as Java applications, Linux applications that utilize OpenSSL, or Microsoft Windows CNG and KSP providers that employ a restricted set of instructions.
AWS CloudHSM Quotas
Quotas, formerly known as limitations, are the values allotted to AWS resources. The AWS CloudHSM resource quotas below apply to your AWS Region and AWS account. AWS's default quota is the first value used, and these numbers are mentioned in the table below. An adjustable quota can be set higher than the default quota.
Features of AWS Cloud HSM
- Security
Manage your keys on FIPS-compliant hardware safeguarded by customer-owned, single-tenant HSM instances operating in your Virtual Private Cloud (VPC). The AWS CloudHSM is designed with a separation of tasks and role-based access control in mind. AWS monitors your HSMs' health and network availability; you manage the HSMs and create and use your encryption keys.
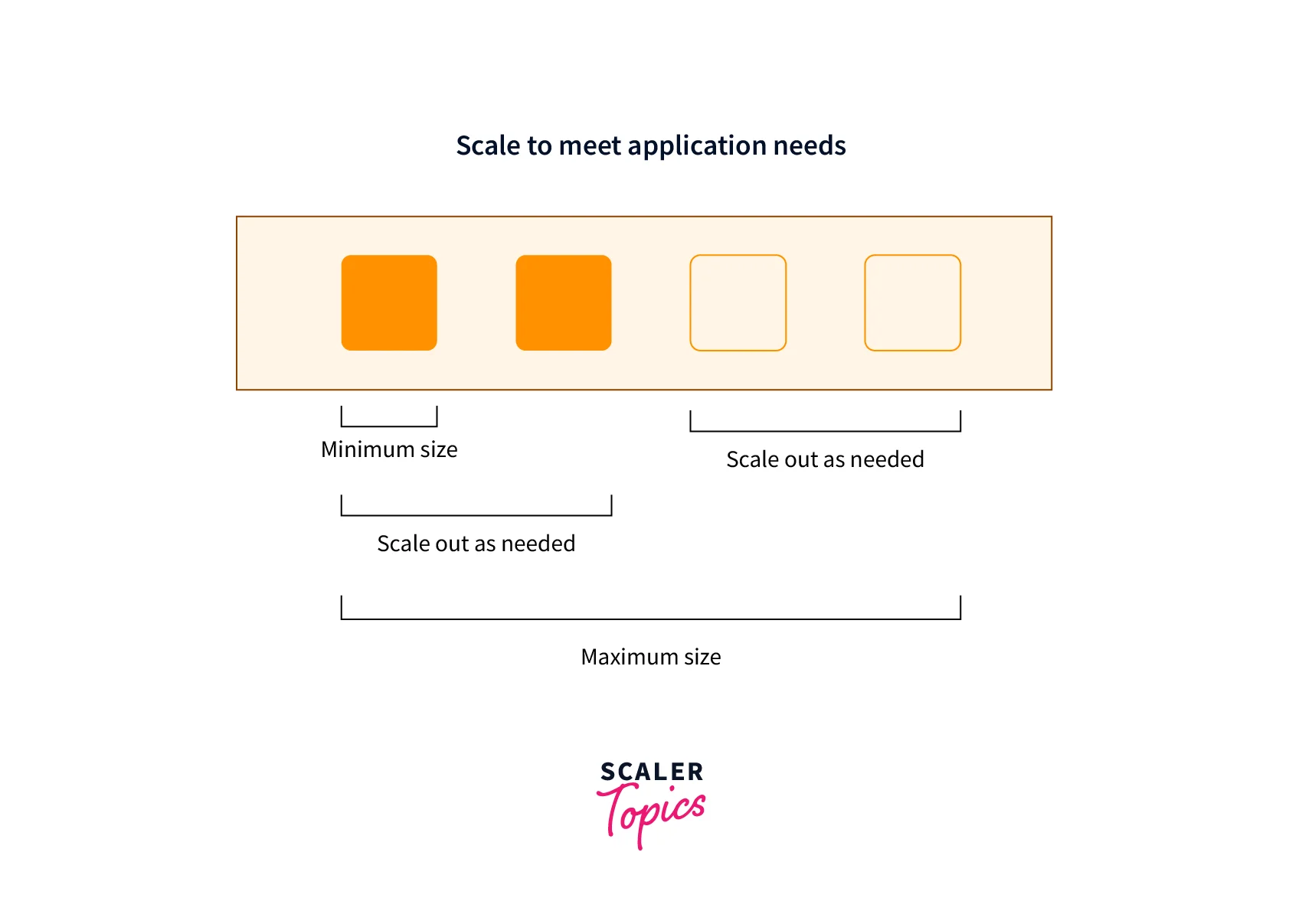
- Performance
Meet your applications' performance objectives via elasticity, adding or eliminating HSM instances while maintaining latency and reliability targets.
- Compliance Compliance with security and privacy requirements such as PCI, GDPR, HIPAA, and FedRAMP must be demonstrated.
- Availability Automatically load balance requests & securely duplicate keys among your cluster's HSM instances, enhancing key durability and capacity.
- Flexibility Deploy an open solution that supports diverse cryptographic methods using industry standards, including PKCS#11, JCE, OpenSSL, and CNG/KSP.
AWS Cloud HSM Use Cases
A hardware security module (HSM) in AWS CloudHSM can assist you in achieving a range of objectives.
- Offload Web Server SSL/TLS Processing Secure Sockets Layer (SSL) or Transport Layer Security (TLS) can be used by web servers and their clients (web browsers). These protocols validate the web server's identity and provide a secure connection to send and receive webpages or other data over the internet. This is frequently referred to as HTTPS. The web server employs a public-private key pair and an SSL/TLS public key certificate to create an HTTPS session with each client. This procedure requires significant computing on the web server's part, but you may offload some of it to the HSMs in your AWS CloudHSM cluster. SSL acceleration is another term for this. Offloading lessens the computational strain on your web server while also adding security by keeping the server's private key in HSMs.
- Protect an Issuing Certificate Authority's (CA) Private Keys A certificate authority (CA) is a trustworthy institution that provides digital certificates in public key infrastructure (PKI). These digital certificates use cryptography and digital signatures to link a public key to an identity (a person or organization). To run a CA, you must safeguard the private key that signs the certificates issued by your CA. You can keep the private key in your AWS CloudHSM cluster's HSM and use it to execute cryptographic signature operations.
- Transparent Data Encryption (TDE) Should be Enabled for Oracle Databases Transparent Data Encryption (TDE) is a feature in some versions of Oracle's database software. The database program encrypts data before saving it on disk via TDE. A table or tablespace key encrypts data in the database's table columns or tablespaces. The TDE master encryption key is used to encrypt these keys. The TDE master encryption key can be stored in the HSMs of your AWS CloudHSM cluster for further protection.
AWS Cloud HSM Pricing
You pay by the hour using AWS CloudHSM, with no long-term obligations or upfront fees.
Region: US East (Ohio) Total hourly price per HSM -----------------$1.45
Each CloudHSM Classic instance you launch will incur a $5,000.00 upfront price in each location. After that, you will be charged an hourly rate for each hour until you discontinue the HSM. The below shows the hourly pricing by region.
Region: US East (Ohio) Hourly price per HSM ----------------------$1.88 CloudHSM Classic is closed to new customers.
Unless otherwise specified, the charges are exclusive of relevant taxes and levies, including VAT and sales tax. Customers with a Japanese billing address must pay Japanese Consumption Tax while using AWS.
Monthly bills are delivered. Because each month has a varied number of days, the amount on your statement will fluctuate monthly.
Each half-hour consumed will be invoiced as a full hour. Amazon retains the right to charge $.02 per GB for network data transfers into and out of a CloudHSM instance that exceeds 5000 GB per month.
For more information about pricing you can follow the link.
Getting Started with AWS Cloud HSM
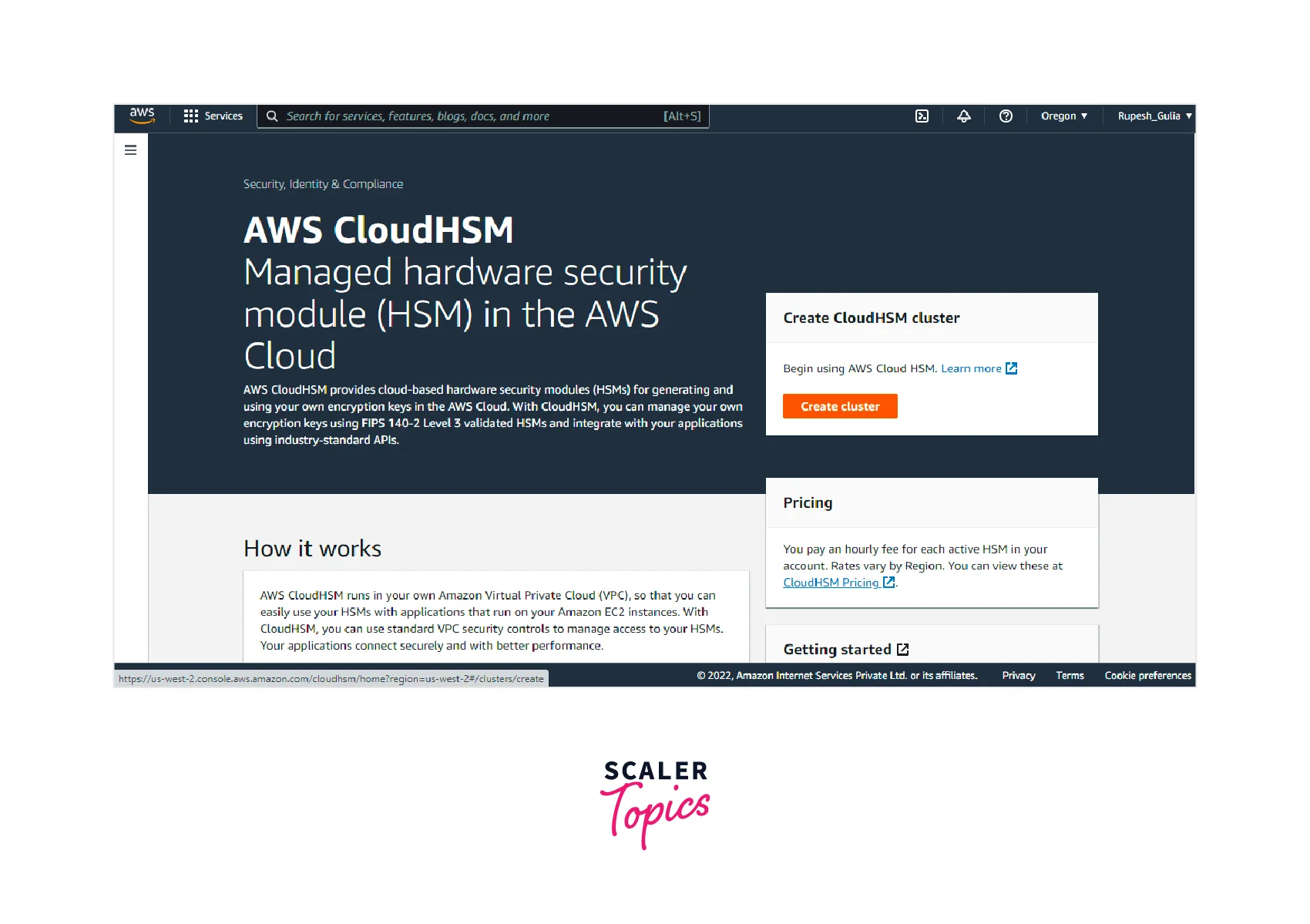
- First, open AWS CloudHSM from the AWS management console to get started. Now, click on the create cluster button, as shown below, to create a cluster.
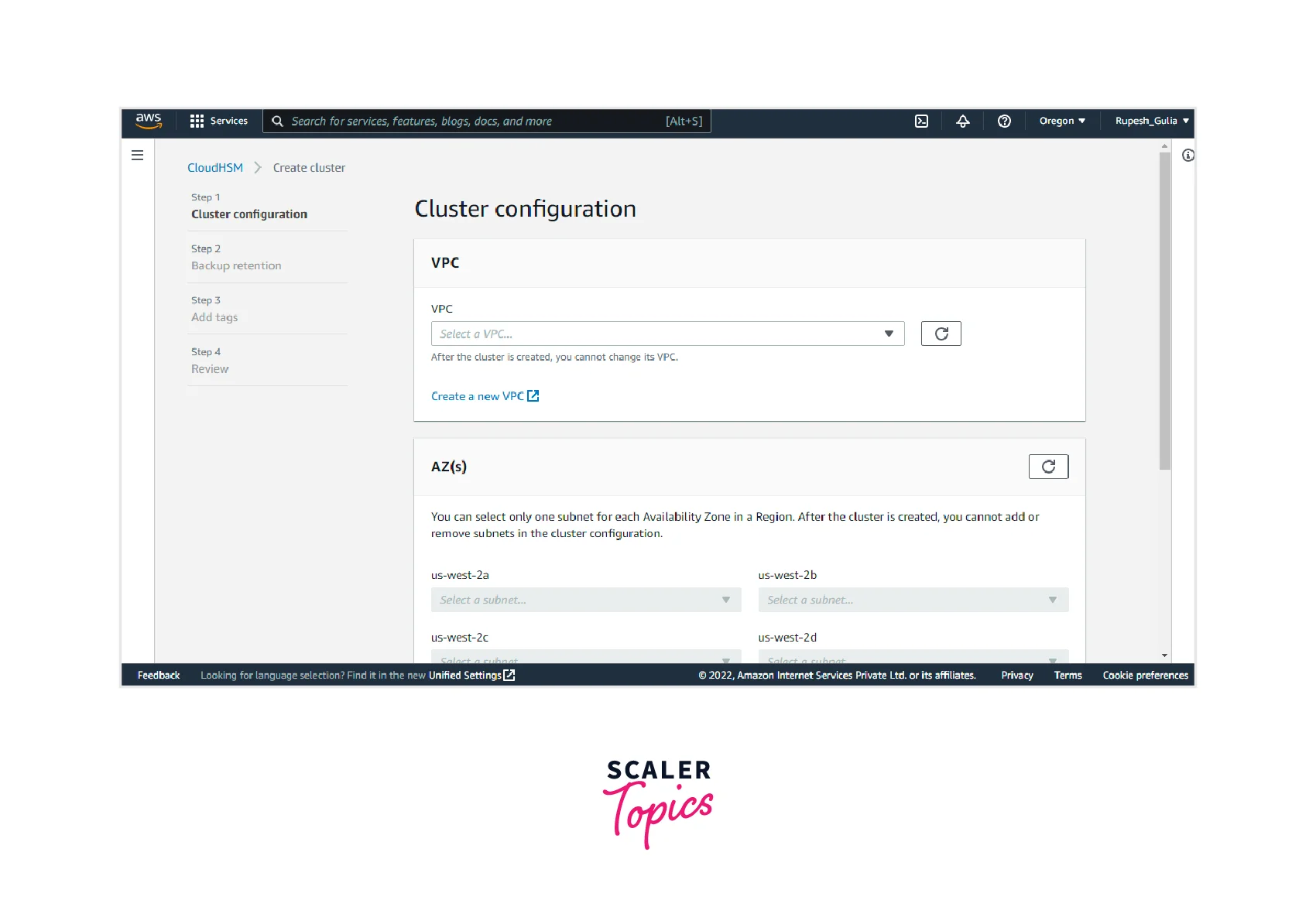
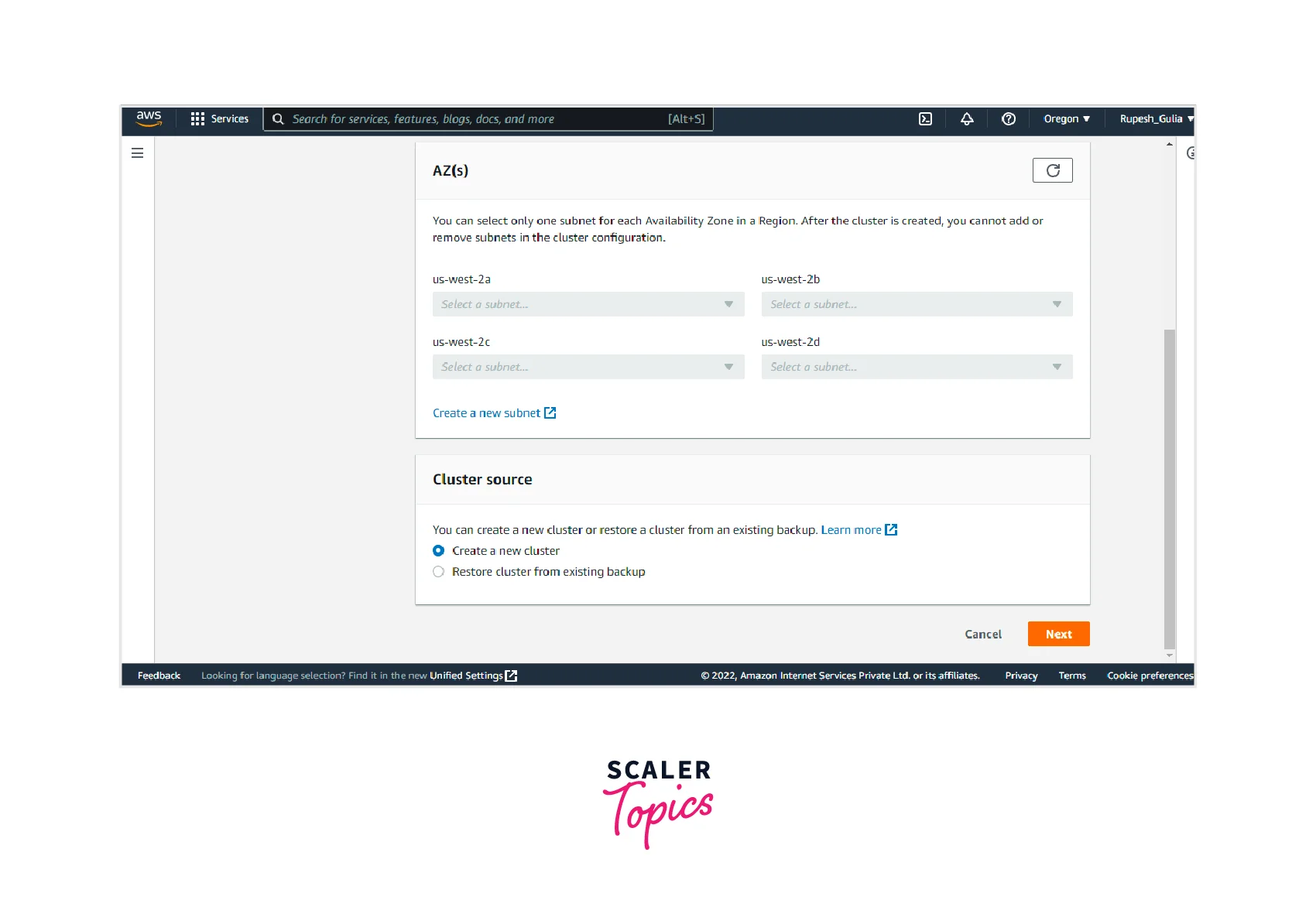
- Step 1: Now, you have to provide the VPC. Here we have selected the default VPC. Then you can provide the subnets from the various AZ. After that, you can specify the cluster source(new (or) existing). Click on the Next button.
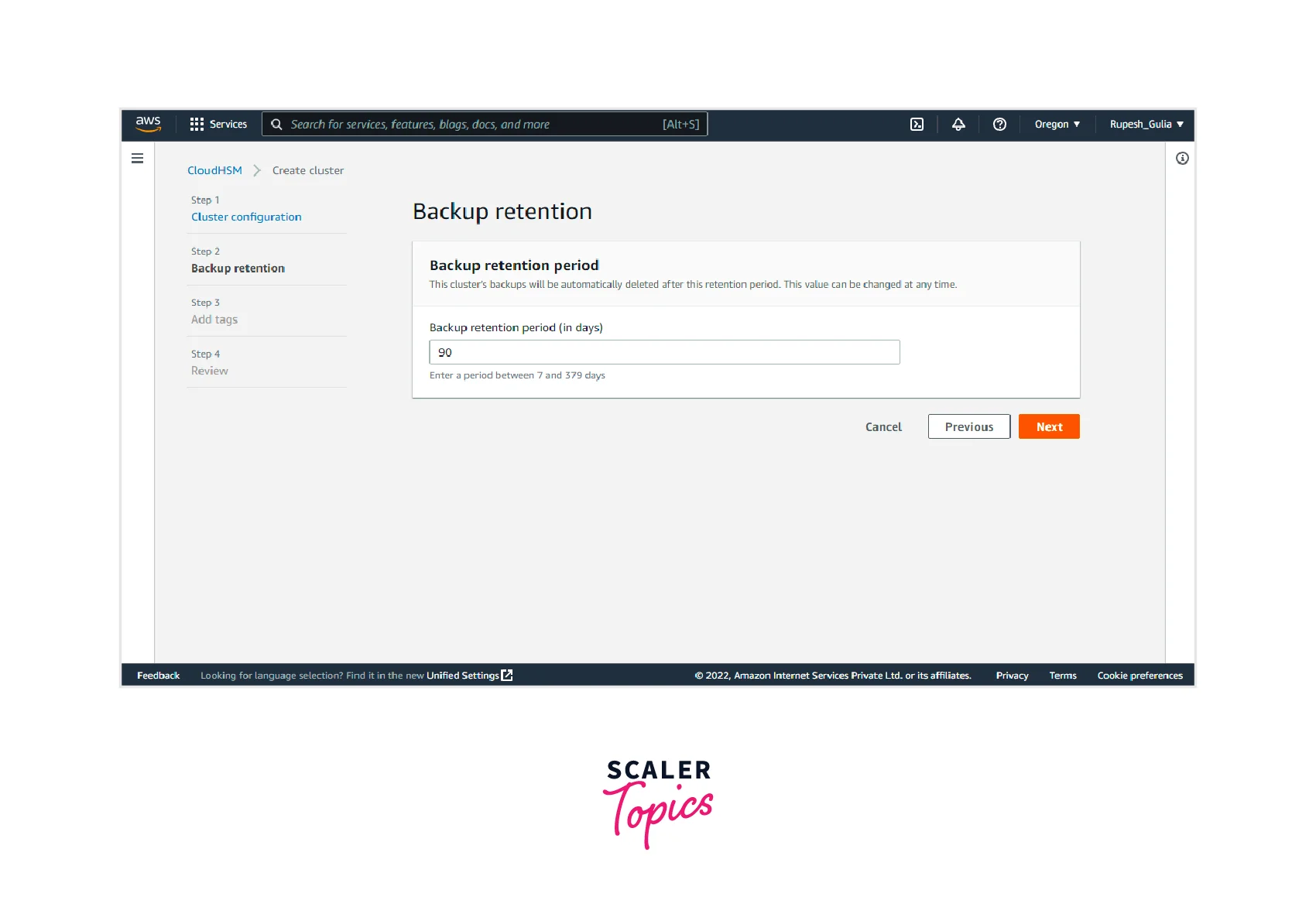
- Step 2: Next step is to specify the Backup retention period, after which the cluster’s backups will be automatically deleted, which can be changed at any time. Then click on Next.
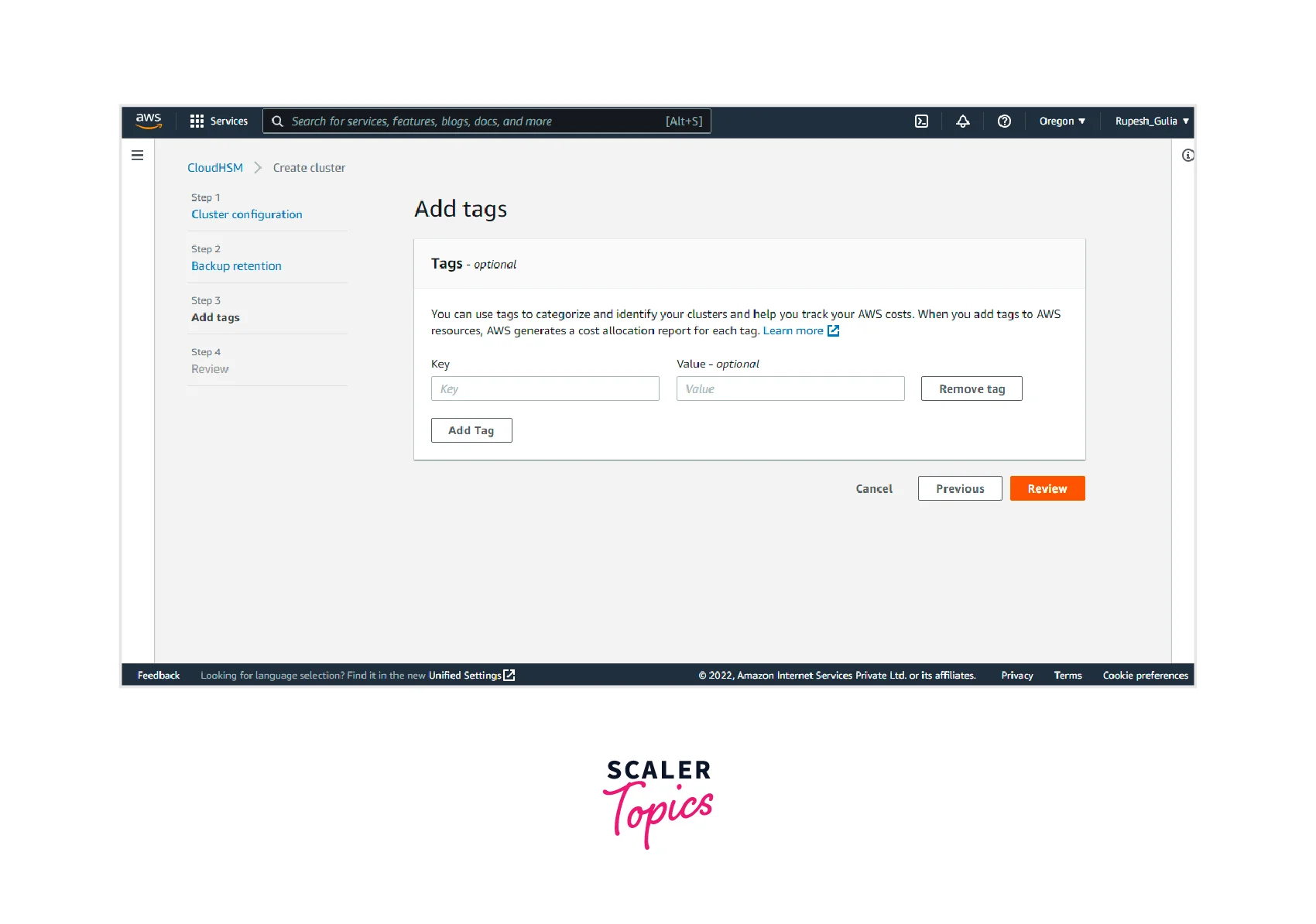
- Step 3: Now, you can add any tags if needed (as it is optional), which you can use to categorize and identify your clusters and help track your AWS costs. Click on the "REVIEW" button.
- Step 3: Now, you can review all your cluster specifications and click on the "Create Cluster" button.
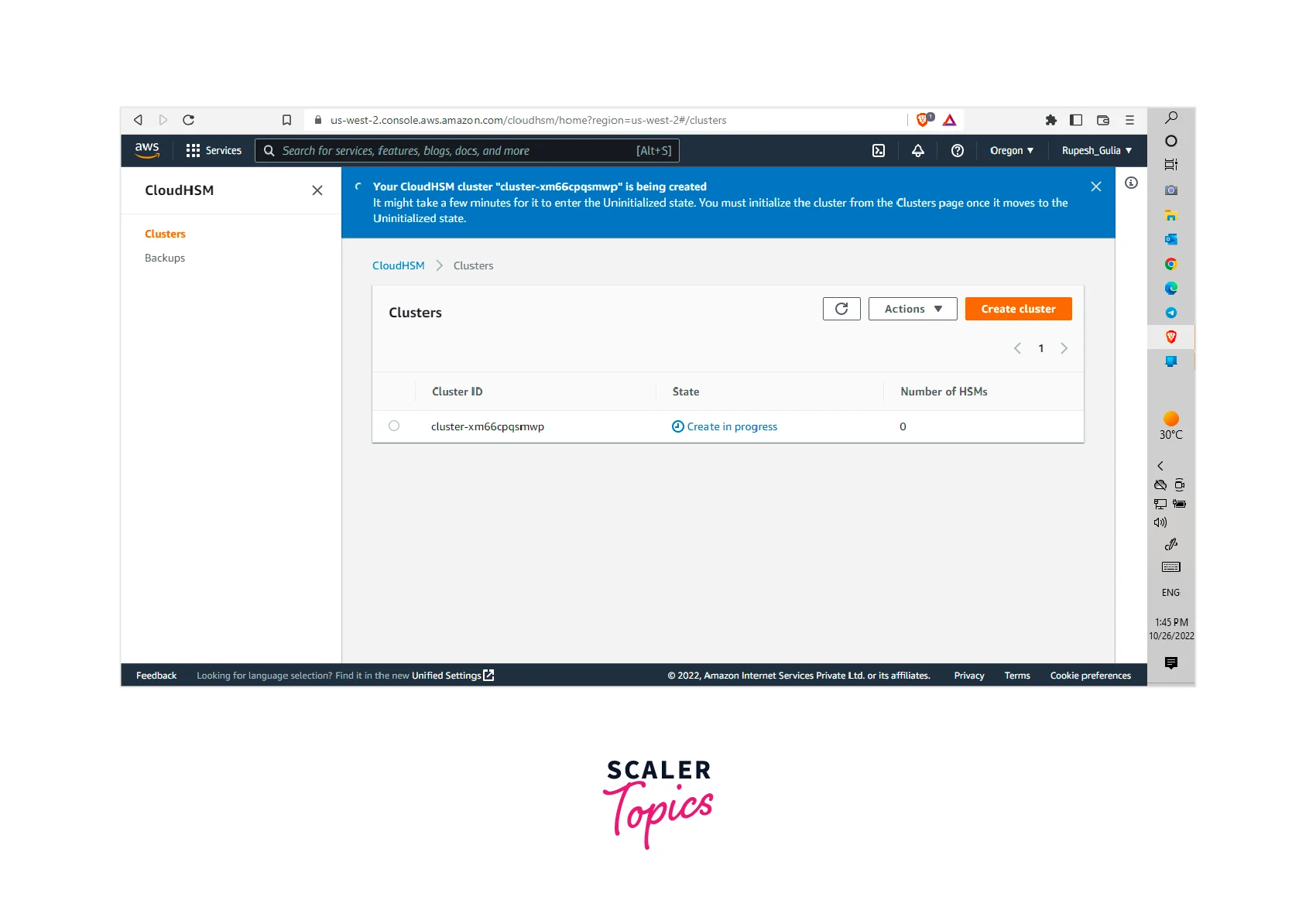
- Step 4: Finally, your cluster will be created.
CloudHSM vs AWS KMS
| Cloud HSM | AWS KMS |
|---|---|
| 1. CloudHSM provides you with a single-tenant multi-Availability Zone cluster that is exclusive to you. | 1. AWS KMS is multitenant; nevertheless, it employs HSMs, dispersed among customer accounts, so it is not unique to you. |
| 2. In HSM the customer has control over accessing of the keys. Instead, you retain control of your access keys, AWS does not have access to your keys. | 2. In AWS KMS the keys are controlled by the user and AWS. |
| 3. As a result, because it is a managed service, you do not have access to the AWS-managed component of CloudHSM. | 3. This service is Managed (automatically) by AWS. |
| 4. CloudHSM operates within a VPC in your account. | 4. AWS KMS operates within Amazon Web Services. |
| 5. AWS CloudHSM can be integrated with a small set of services (Redshift, Oracle RDS etc.) | 5. Most services from AWS are fully integrated. |
| 6. AWS CloudHSM has Level 3 FIPS 140-2 Compliance available. | 6. AWS KMS has Level 2 overall (Level 3 in some areas) FIPS 140-2 Compliance available. |
| 7. AWS CloudHSM has access and authentication policy of Quorom-based K of N. | 7. It has mainly AWS IAM Policy. |
Conclusion
- AWS CloudHSM assists with encryption and cryptographic procedures. It offers single-tenant access to each HSM within an Amazon VPC and includes tamper resistance, security, and managed service features.
- AWS CloudHSM includes key concepts namely Clusters, Backups, HSM Users, Keys, CLI tools, etc.
- AWS CloudHSM charges an hourly fee until the termination, which ranges from 1 USD to 3 USD, depending on the location selected.
- CloudHSM allows you to securely generate, store, and manage cryptographic keys used for data encryption in a way that keys are accessible only by you.
- Unlike other AWS services, you do not need AWS IAM users to access resources within your cluster. Instead, you directly utilize HSM users on the hardware security module (HSM).
- You can set up and manage HSMs using AWS CloudHSM, create users, and specify their permissions. The HSM's symmetric and asymmetric key pairs are also produced by you.
