AWS Cognito
Overview
Amazon Cognito is an authentication and user management solution that can be incorporated into your online or mobile apps. The backend resources of your app may be accessed through AWS or any service behind Amazon API Gateway with the help of Amazon Cognito, which also offers temporary security credentials.
In addition to social identity providers like Facebook, Twitter, Amazon, Google, and Apple, you may also connect your identity provider.
What is AWS Cognito, and What is It Used for?
For a successful sign-in, web apps typically require a valid username and password combination. More methods are now included in modern authentication routines to guarantee user authentication. This holds while utilizing AWS due to the capabilities and functionalities made available by AWS Cognito. The Amazon Cognito service is made to offer APIs and technology for crucial user management functions, including user repository management, authentication, and authorization, with a variety of operations for your online and mobile apps.

Features of Amazon Cognito
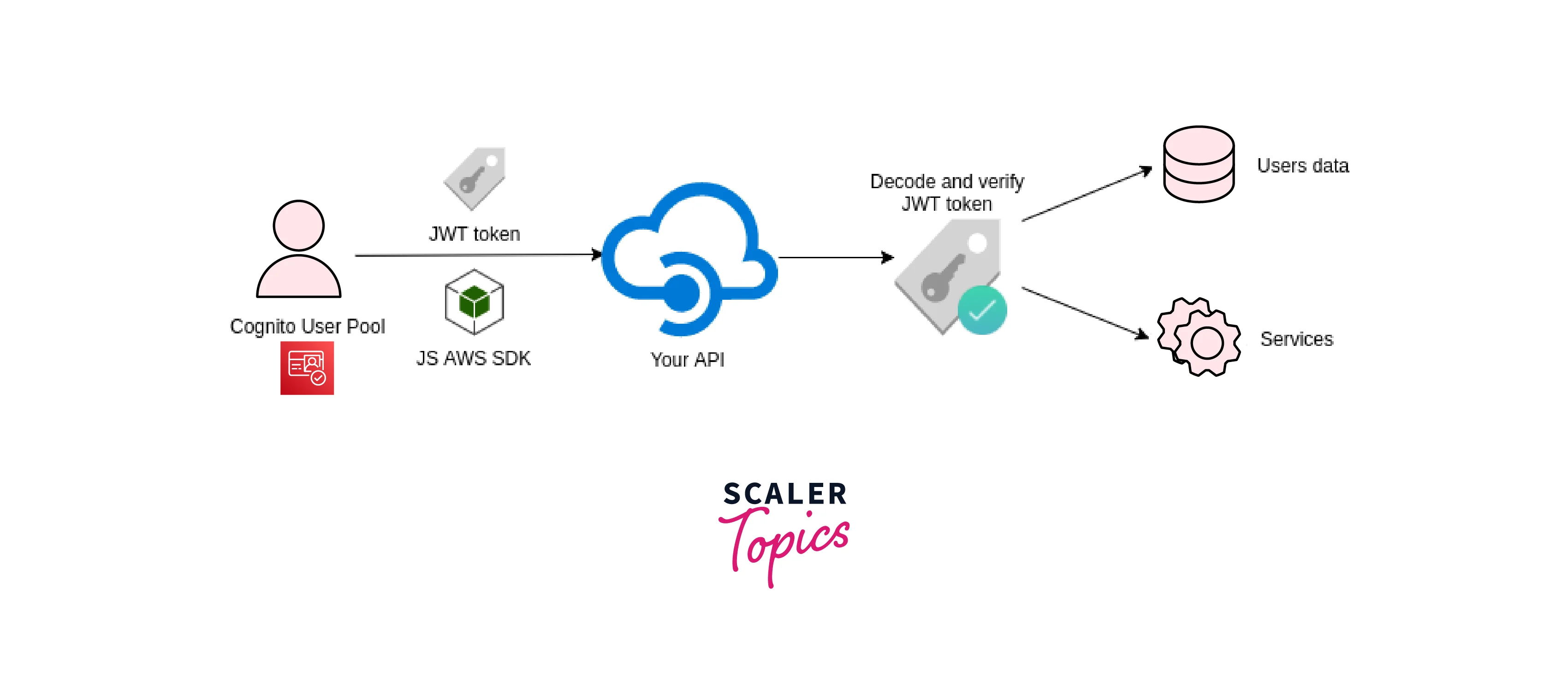
User Pools
In Amazon Cognito, a user pool is a user directory. With a user pool, your users may share resources with a third-party authenticator or sign in to your online or mobile app using Amazon Cognito. All users in the user pool have a directory profile that you can access through a Software Development Kit, regardless of whether they sign in directly or through a third party.
User pools offer you:
- Registration and login for services.
- There is a built-in, editable online user interface for user sign-in.
- Social login with Google, and Facebook, Sign in using Apple, Amazon, Security Assertion Markup Language, and OIDC identity providers as well as your user pool.
- Management of user-profiles and user directories.
- Account security features, including phone and email verification, checks for compromised credentials, account takeover prevention, and multi-factor authentication (MFA).
Identity Pools
Your customers can get temporary AWS access to AWS services like Amazon S3 and DynamoDB by using an identity pool. Identity pools allow for both anonymous guest users and the usage of the following entities for user authentication:
- Amazon Cognito user pools
- Social login with Google, Facebook, Apple, and Amazon.
- Providers of OpenID Connect (OIDC).
- Identity providers for Security Assertion Markup Language.
- Identity verified by developers.
How Does Amazon Cognito Authentication Work?
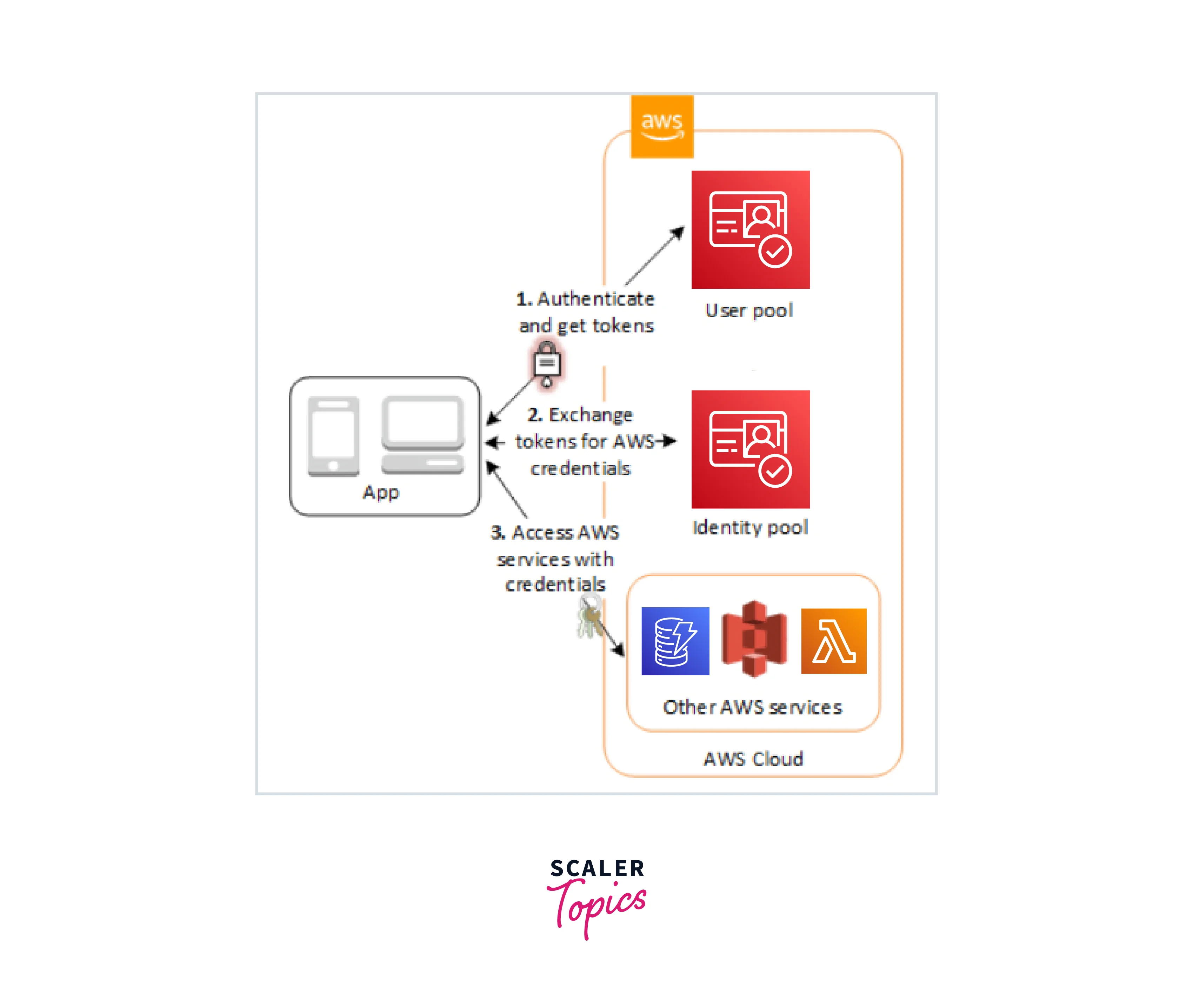
To bootstrap their credentials, a user authenticating with Amazon Cognito will go through the following three steps:
- GetId
- GetOpenIdToken
- AssumeRoleWithWebIdentity
GetId
- The first call required to create a new identity in Cognito is the GetId API request.
- Enabling unauthenticated "guest" access in your apps is one of Cognito's most outstanding features. Users can use the GetId API to request a new identity ID if this functionality is enabled in their identity pool.
- Users can give tokens (OAuth or OpenID Connect) that identify them in those providers once you've set up your application to enable a public login provider (Facebook, Google+, and log in with Amazon). Cognito will either establish a new authenticated identity or return the identity currently connected to that specific login when used in a call to GetId.
GetOpenIdToken
- We call the GetOpenIdToken API call once we've obtained an identity ID. This may be the initial call we make throughout an app session if we have a cached identification ID.
- If our identity is not authenticated, all that is required to obtain a token for it is the identity ID.
- We must send at least one valid token for a login already connected to a verified identity if we have one. If any of the tokens handed in during the GetOpenIdToken call fail the validation described before, the entire ring will fail. The identity ID is included in the response from the GetOpenIdToken function as well.
AssumeRoleWithWebIdentity
Once we obtain an OpenID Connect token, we can use the Security Token Service AssumeRoleWithWebIdentity API call to exchange it for temporary AWS credentials. The only difference between this call and one where we directly log in to Facebook, Google+, or Amazon is that we pass a Cognito token rather than one from one of the other public providers.
Common Use Cases
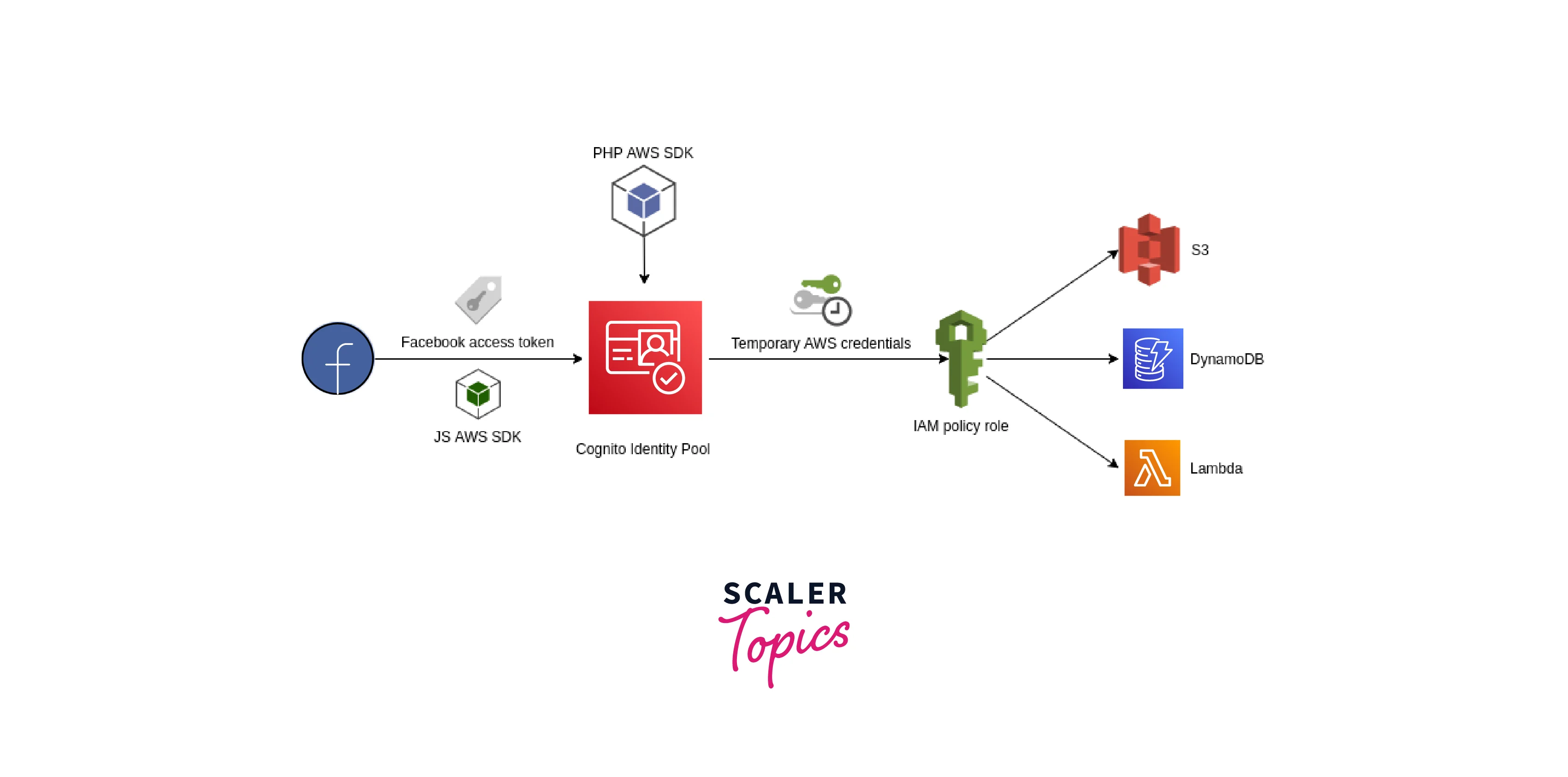
- Make it possible for your users to log in using a user pool.
- Your web or mobile app will get user pool tokens from Amazon Cognito following a successful user pool sign-in. These tokens can be used to manage user access to server-side resources.
- Utilize a User Pool to access resources via API Gateway and Lambda. Users can access resources such as Lambda functions or your API by using the tokens API Gateway verifies following a successful user pool login.
- Give your users identity pool access so they may use AWS services. The identity pool provides temporary AWS credentials in return, which you may use to log into other AWS services.
- With the help of tokens obtained after a successful Amazon Cognito authentication, provide your users access to AWS AppSync resources (from a user pool or an identity pool).
- AWS Amplify, a framework for creating online and mobile apps with AWS services, and Amazon Cognito are frequently combined.
Synchronizing User Data with AWS Cognito Sync
Using Amazon Cognito, you may store user information in datasets that comprise key-value pairs. This information is linked by Amazon Cognito to identity in your identity pool so that your app may access it from many devices and logins. Use the synchronize method to sync this data between an end user's devices and the Amazon Cognito service. A dataset can only be one megabyte (MB) in size. Up to 20 datasets can be linked to an identity.
The identity data is created in a local cache by the Amazon Cognito Sync client. Your program interacts with this local cache to read and write keys. Because of this communication, all changes you make to the device are immediately visible even when you are offline. When the synchronize method is used, changes from the service are retrieved to the device, and any local modifications are sent to the service. At this point, other devices can synchronize with the changes.
Amazon Cognito Security and Data Protection
You can safeguard links to your apps' user accounts using Amazon Cognito's increased security features. These cutting-edge security features include protection against the use of stolen credentials and customized vulnerability-based vulnerability verification.
To safeguard the identity of your users, you may add multi-factor authentication (MFA) to a user pool. Your user pool can utilize MFA to provide a second authentication factor in addition to the user name and password. To sign in to your users, you can use either SMS text messages or time-based one-time passwords (TOTP). Additionally, adaptive authentication's risk-based paradigm allows you to foresee the potential need for additional authentication factors. Advanced security features for the user pool include adaptive authentication and safeguards against stolen credentials.
Amazon Cognito Pricing
- Suppose you use Cognito Identity to create a User Pool. In that case, you are only charged depending on the number of monthly active users (MAUs). If a user performs an identification activity, such as a sign-up, sign-in, token refresh, or password change throughout a calendar month, they are regarded as MAUs.
- For users that log in directly to Cognito User Pools or through social identity providers, the Cognito Your User Pool functionality includes a free tier of 50,000 MAUs; for users federated through Security Assertion Markup Language 2.0-based identity providers, the free level is 50 MAUs.
- There is an extra charge when you enable enhanced security features for Amazon Cognito.
Conclusion
- We spoke about AWS Cognito in this article and discovered that it is an authentication and user management tool.
- The user pool, a user directory that is used to share resources with a third-party authenticator, and identity pool, which provides you temporary access, were also highlighted as aspects of Amazon Cognito.
- After discussing the three primary parts of the Amazon Cognito authentication process—GetId, GetOpenIdToken, and AssumeRoleWithWebIdentity—which is how authentication works—we looked at a few real-world use scenarios.
- We spoke about utilizing key-value pairs to synchronize user data using AWS Cognito Sync and about using multi-factor authentication and time-based one-time passwords to protect user data while using Amazon Cognito.
- Finally, we spoke about the cost of Amazon Cognito and the variables that affect it.
