Amazon Inspector
Overview
Amazon Inspector is a service that performs automatic security assessments and compliance with AWS-hosted applications. AWS Inspector assesses applications for exposure, vulnerabilities, and deviations from best practices. After performing an assessment, AWS Inspector produces a detailed list of security findings prioritized by the level of severity.
What is Amazon Inspector?
Your AWS workloads are continuously scanned for vulnerabilities by AWS Inspector, a vulnerability assessment and management tool. AWS Inspector scans AWS Elastic Container Registry (AWS ECR) container images and AWS EC2 instances for software flaws and unintentional network exposure.
Amazon Inspector security evaluations assist you in checking for unexpected network access and vulnerabilities on your Amazon EC2 instances. Amazon Inspector assessments are provided to you in the form of preconfigured rule packages that are mapped to standard security best practices and vulnerability descriptions.
When a network issue or software vulnerability is found, AWS Inspector generates a finding. A vulnerability finding describes the vulnerability, specifies the resource it affects, rates its severity, and provides recommendations for a fix. With the help of the AWS Inspector dashboard, you may examine account discovery information in various ways, or you can use other AWS services to see and analyze your findings.
Features of AWS Inspector
-
Amazon EC2 and container workload vulnerability management AWS Inspector is a multi-resource vulnerability management solution that works with Amazon Elastic Compute Cloud (EC2) and container workloads. It discovers many vulnerabilities, including software flaws and inadvertent network exposure, that may be exploited to compromise workloads, repurpose resources for nefarious use, or exfiltrate data.
-
Easy one-click activation and integration with AWS Organizations You may launch AWS Inspector across several accounts with a single click in the AWS Inspector panel or a single API request. You may designate an Inspector Delegated Administrator (DA) account to your organization, which can start and configure all member accounts and combine all findings.
-
Automated vulnerability discovery and ongoing vulnerability scanning When launched, AWS Inspector instantly detects all EC2 instances and container images marked for scanning in Amazon Elastic Container Registry (ECR) and then begins scanning them for software vulnerabilities and accidental network exposure. When new common vulnerabilities and exposures (CVE) are announced or changes in the workloads, such as installing new software in an EC2 instance, all workloads are constantly rescanned.
-
Risk score for findings assigned by the Inspector By connecting CVE information with environmental parameters such as network reachability results and exploitability data, AWS Inspector creates a highly contextualized Inspector risk assessment for each discovery. This allows the findings to be prioritized and emphasizes the essential findings and vulnerable resources. The Inspector score calculation (and factors influencing the score) can be viewed in the Inspector Score tab within the Findings Details side panel.
-
Comprehensive coverage monitoring To help you prevent coverage gaps, AWS Inspector provides an aggregated, nearly real-time picture of the environment coverage throughout an organization. In addition to EC2 instances, ECR repositories, and container images currently being scanned by AWS Inspector, it also gives analytics and comprehensive information on accounts that use AWS Inspector. AWS Inspector also identifies resources that aren't being closely watched and offers instructions on how to add them.
-
Integrated and enabled with AWS Organizations with one simple click. With a single click in the AWS Inspector dashboard or one API request, start AWS Inspector across many accounts. You may designate an Inspector Delegated Administrator (DA) account for your company in AWS Inspector. This account will be able to start and configure all member accounts and aggregate all findings.
-
Automated vulnerability finding and ongoing vulnerability scanning When AWS Inspector is launched, it instantly begins scanning all recognized EC2 instances and Amazon Elastic Container Registry (ECR) container images for software vulnerabilities and accidental network exposure. Every time a new common vulnerability and exposure (CVE) is released or a workload changes, such as when new software is installed on an EC2 instance, all workloads are routinely rescanned.
How AWS Inspector Works
Before you enable AWS Inspector, take note of the following:
The regional service is AWS Inspector. Every configuration process you finish in this guide needs to be repeated in every Region you wish to use AWS Inspector to monitor.
-
You can activate either EC2 scanning, ECR container image scanning, or both using AWS Inspector. You may manage the scanning kinds using the AWS Inspector APIs or the account administration page in the console.
-
The Amazon EC2 Systems Manager (SSM) agent must be installed and active for AWS Inspector to give common vulnerabilities and exposures (CVE) information for your Amazon EC2 instances. Many Amazon EC2 instances already have this agent installed; however, you might need to explicitly enable it. All your Amazon EC2 instances are checked for network reachability problems regardless of the SSM agent state. See Scanning Amazon EC2 instances for further details on setting scans for Amazon EC2.
-
AWSServiceRoleForAmazonInspector2 is a service-linked role created for your account worldwide when you enable AWS Inspector for the first time in any Region. This role contains the trust policies and permissions that enable AWS Inspector to gather information about software packages and examine VPC configurations to produce vulnerability findings.
-
AWS Inspector performs and produces a results report with recommendations for safeguarding the AWS environment. You must install the AWS Inspector agent for it to work properly and define the EC2 instances you wish to examine before you can use it. Additionally, you can set up periodic inspections for your EC2 instances, which may last between 15 minutes and 12 hours and repeat every certain number of days.
-
To find security or compliance concerns, all necessary data is gathered and compared with the pre-installed security rule packages.
Enabling AWS Inspector in AWS Cloud
Enabling AWS Inspector in your account is the first step toward utilizing it. Any enabled scan type of AWS Inspector immediately looks for and inspects all available resources.
You must designate a delegated administrator for AWS Inspector if you wish to administer AWS Inspector for several accounts inside your company using a centralized administrator account. To find out how to make AWS Inspector available in your workplace, select one of the following alternatives.
Environment for Standalone Accounts:
- Go to https://console.aws.amazon.com/inspector/v2/home to access the AWS Inspector console.
- Decide on Getting Started.
- In a solo account, all scan kinds are automatically enabled when you enable AWS Inspector. You may manage the enabled scan kinds using the AWS Inspector APIs or the account administration page in the console. After being turned on, AWS Inspector immediately locates and starts scanning all permissible resources. Review the following scan type information to see which resources are eligible by default.
View AWS Inspector findings
In the AWS Inspector console or by using the API, you may examine the results for your environment. Additionally, all results are sent to AWS Security Hub and Amazon EventBridge (if enabled). Container image discoveries are also sent to Amazon ECR.
The AWS Inspector interface provides a variety of ways to examine your results. The Findings table allows you to explore the specifics of certain discoveries, while the AWS Inspector dashboard provides a high-level summary of threats to your environment.
Using the Findings table and dashboard, you investigate a finding's specifics in this stage.
In the AWS Inspector interface, click on your environment to examine specific findings:
-
Go to https://console.aws.amazon.com/inspector/v2/home to access the AWS Inspector console.
-
Click Dashboard in the navigation bar. Any link you choose on the dashboard will take you to a page in the AWS Inspector interface with further information on the selected item.
-
Choose Findings in the navigation pane.
-
The All findings tab, which shows all EC2 instances and ECR container image results for your environment, will be displayed by default.
-
To access the details pane for a specific finding, select its name from the Title column of the Findings list. There is a Finding details tab for each finding. The following are some ways that you can interact with the Finding details tab:
-
Follow the link in the "Vulnerability Details" section to view the documentation for further information about the vulnerability.
-
To access the service console for the impacted resource and conduct more research on your resource, click the Resource ID link in the Resource Affected section.
-
The Inspector Score Breakdown page for discoveries of the category "package vulnerability" also explains how the AWS Inspector score was determined for that discovery. See Finding types in AWS Inspector for further information on how to locate types.
Rules and Packages
-
Your assessment targets (groups of AWS resources) may be examined using AWS Inspector for potential security flaws and vulnerabilities.
-
AWS Inspector compares the security configuration and behavior of the assessment targets to a set of security rule packages. A rule is a security check that AWS Inspector runs during the assessment run in the context of AWS Inspector.
-
You may request assessments from AWS Inspector in the form of pre-built rule packages aligned with well-known security best practices and vulnerability descriptions.
The following rules packages may be used in any combination during an AWS Inspector assessment:
-
Network Assessments
- Network Reachability The Network Reachability package's rules examine your network setups to identify any security holes in your EC2 instances. The conclusions that AWS Inspector produces also include recommendations for limiting insecure access.
-
Host Assessments
- Common risks and vulnerabilities The rules in this package assist in determining if the EC2 instances that make up your assessment targets are vulnerable to common threats (CVEs).
- Standard from the CIS The CIS Security Benchmarks program offers well-defined, objective, consensus-based industry best practices to assist enterprises in evaluating and enhancing their security.
- Ideal security procedures for AWS Inspector Use the AWS Inspector rules to check if your systems are set up safely.
AWS Inspector Agent Installation
Installing an AWS Inspector agent that permits access to your Amazon EC2 instances and the apps running on them is required before you can use AWS Inspector and the host assessments/rules package.
The AWS System Manager Run Command should be able to automatically install this agent if you simply follow the instructions in the AWS Inspector dashboard. Simply click "Get started" to begin, then follow the instructions.
Here are some simple instructions for installing an AWS Inspector agent manually on various OS systems if you must.
Linux installation of the AWS Inspector agent on an Amazon EC2 instance
To set up the agent on a Linux EC2 instance:
-
Login or establish a connection to the EC2 instance running the Linux operating system where the AWS Inspector agent will be installed.
-
Use the command line to get the agent installation script: Install Linux using wget https://inspector-agent.amazonaws.com/latest
-
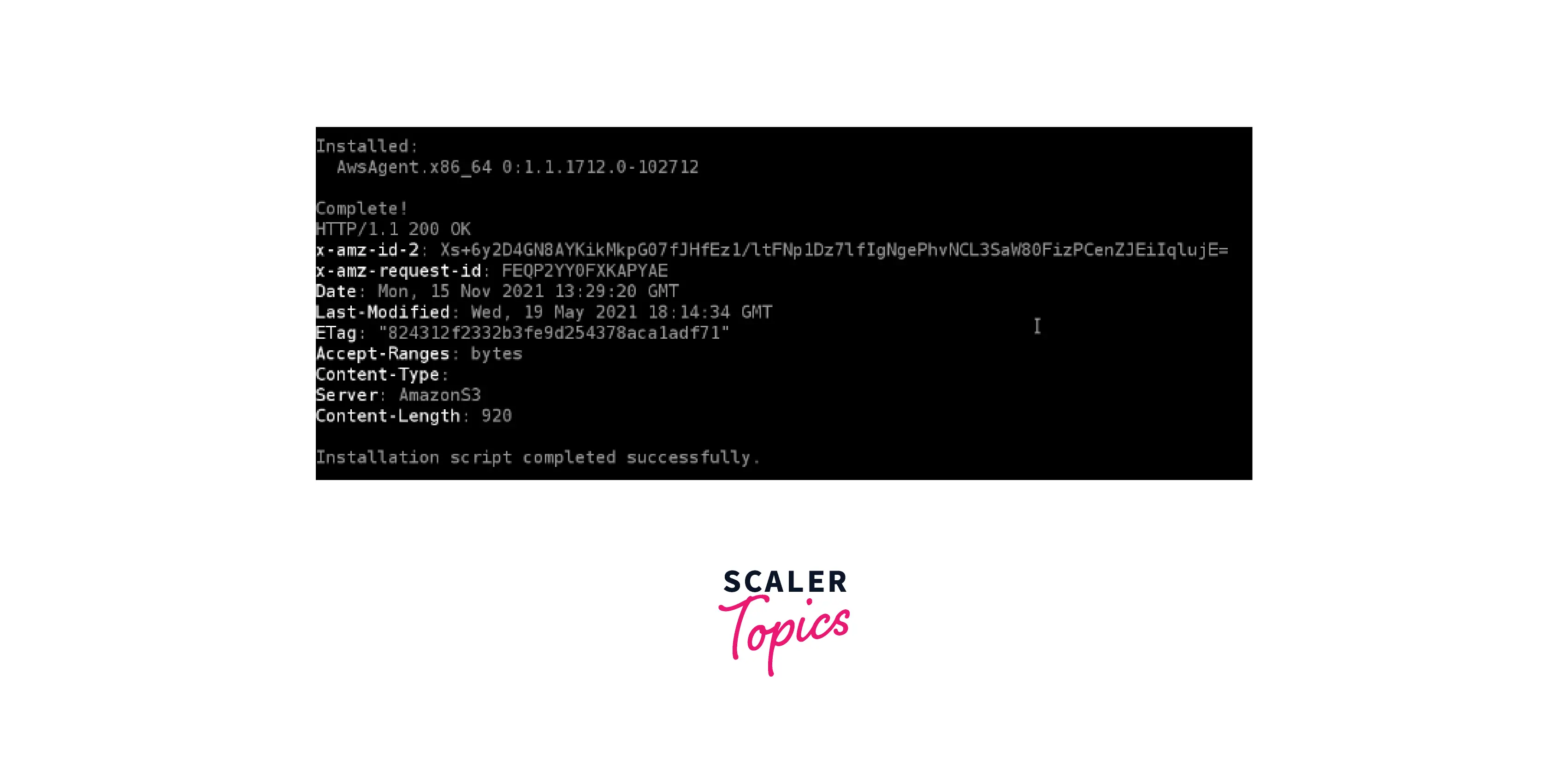
Run sudo bash install to set up the agent.
-
The console should display the confirmation.
Getting Started
To get started with AWS inspector, first of all, users have to access AWS Management Console live on their account. Search for amazon inspector in the search bar provided at the top, and clicking it will take the user to the dashboard of AWS Inspector.
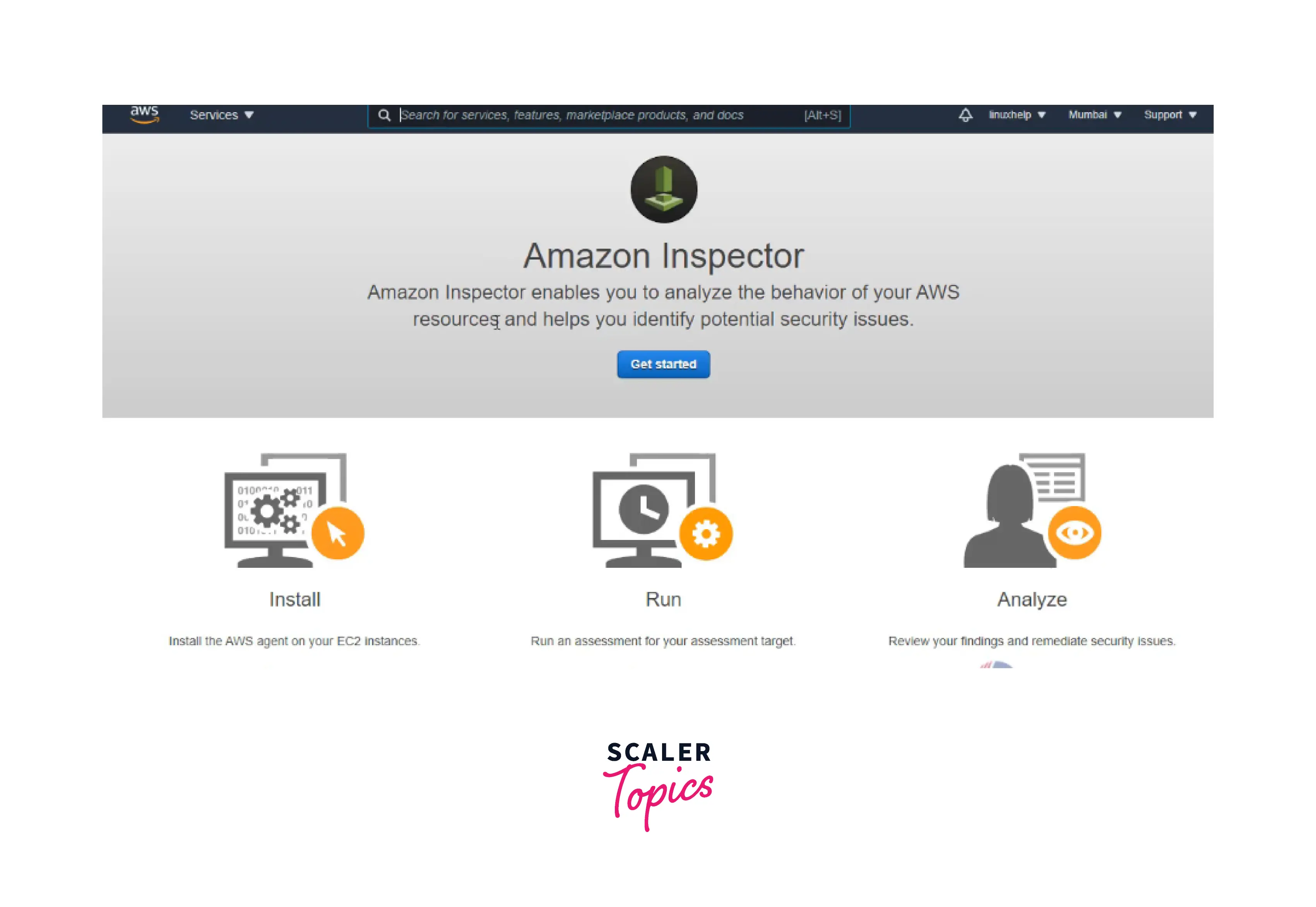
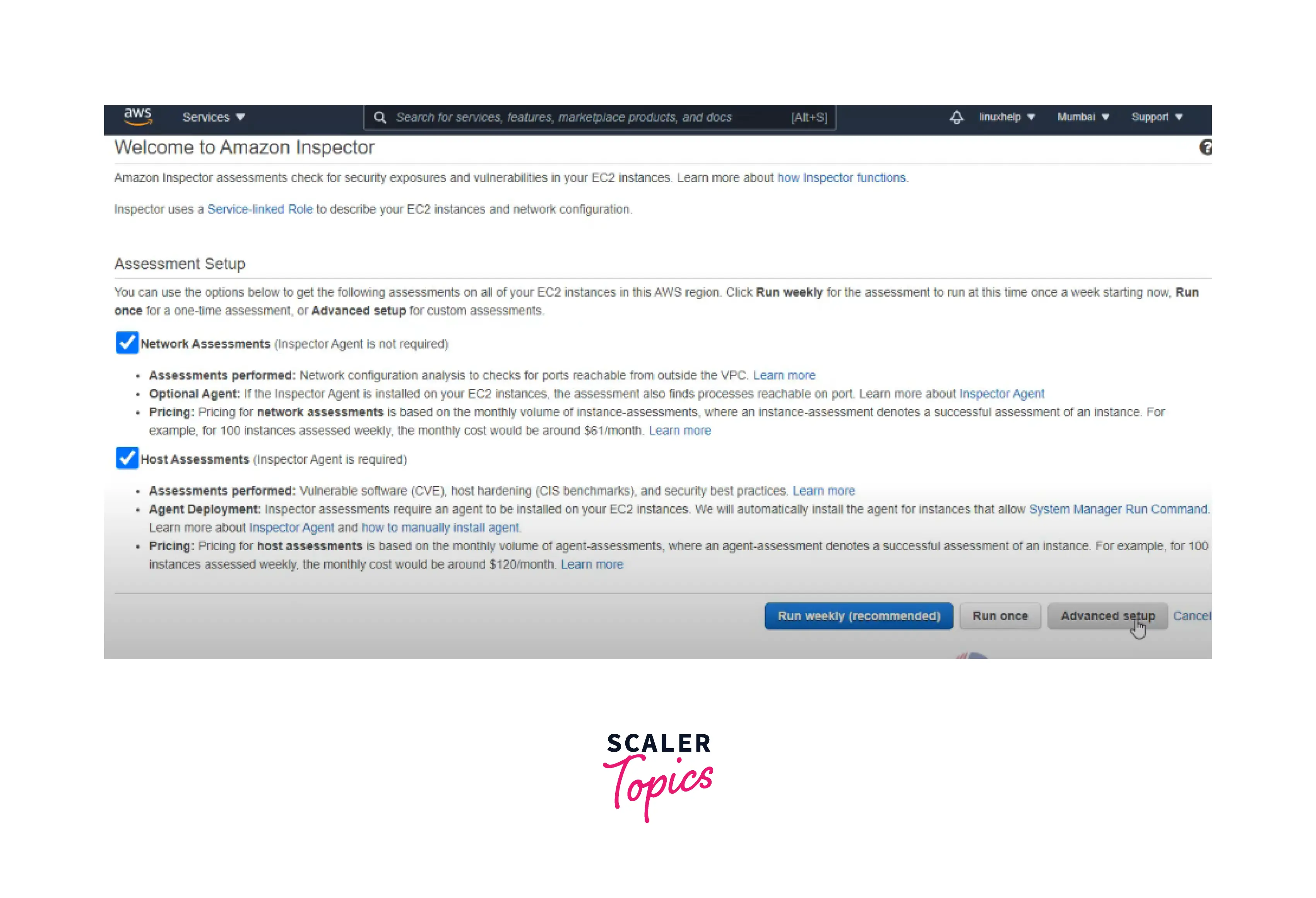
Now click on the "Get Started" button and then click on the advanced setup button in the right below a corner.
Here you can define your assessment target, but before this, you have to create an EC2 instance for the Amazon Inspector. For this, go to the EC2 instance in the search bar and click on the Launch instances button, as shown below.
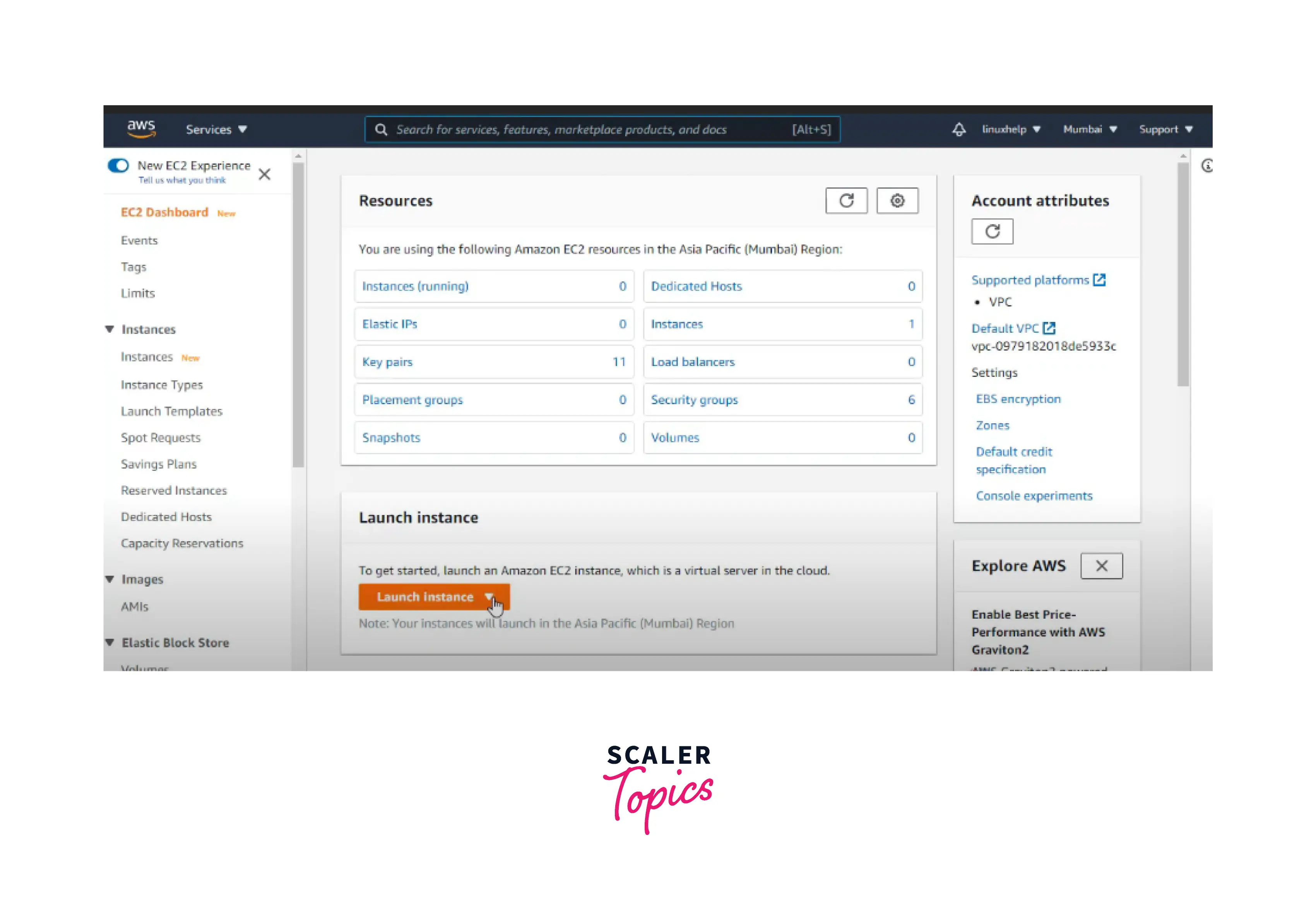
Now you can simply create the EC2 instances by following these steps:
Step1: Choose an Amazon Machine Image.
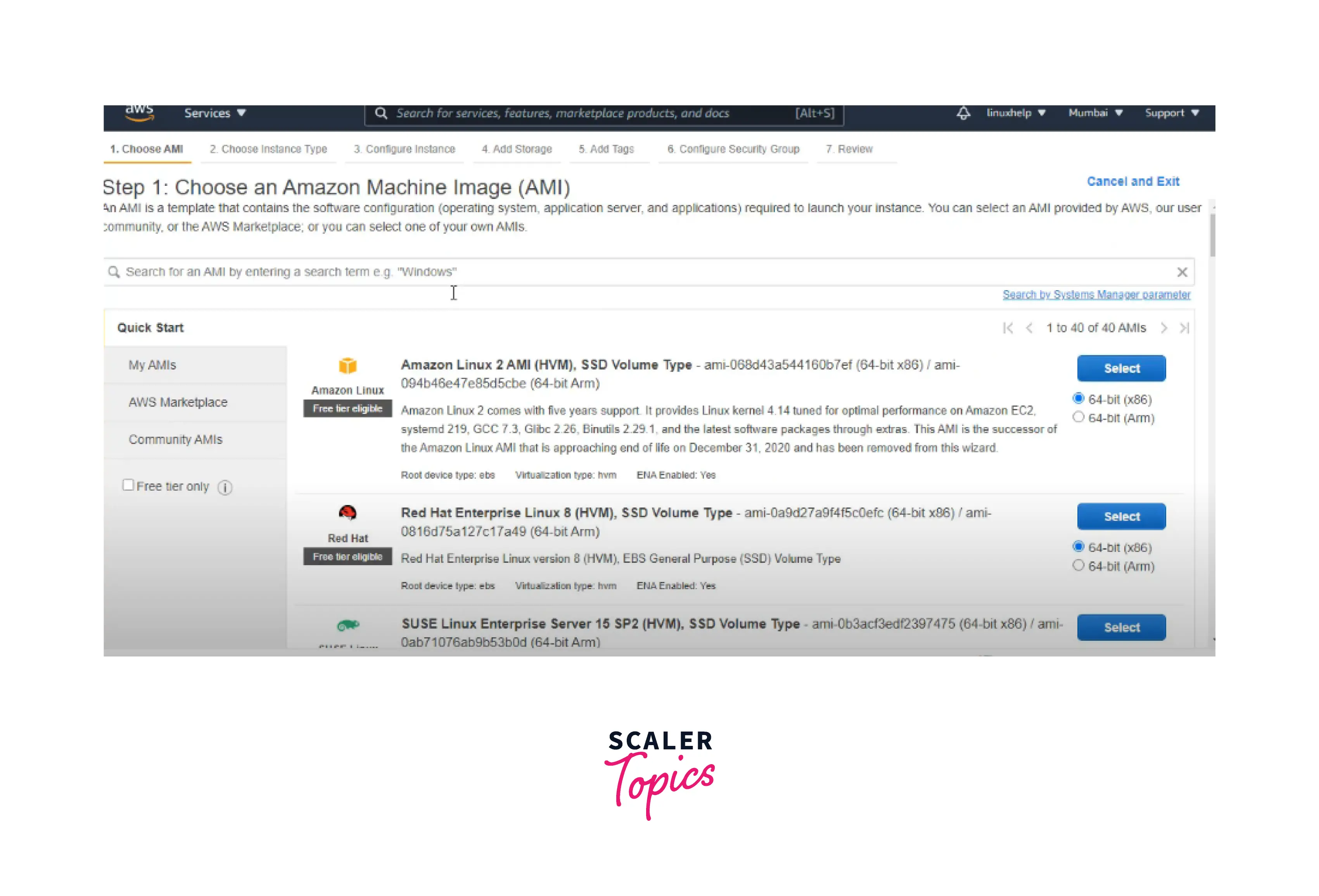
Step2: Choose an instance type.
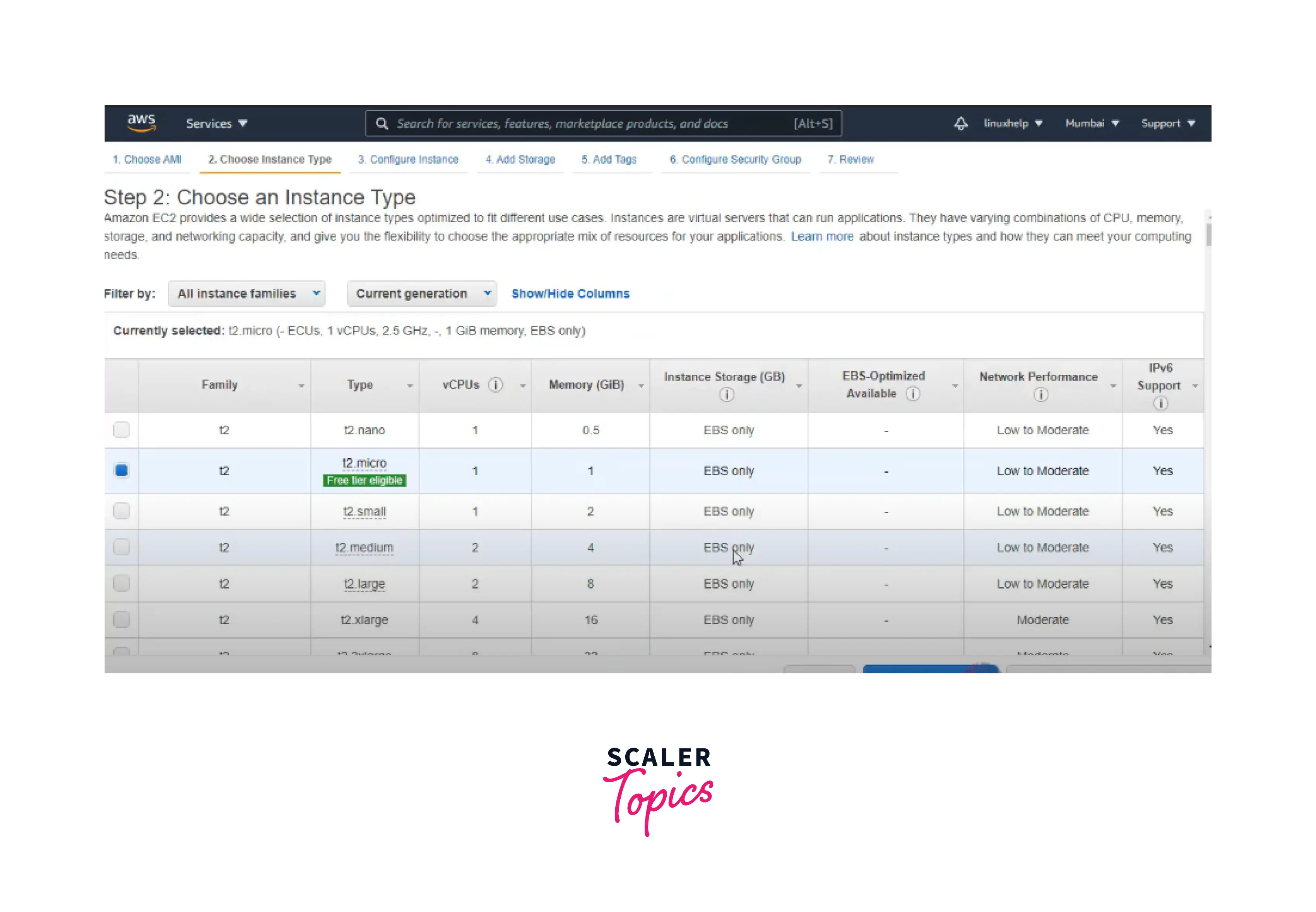
Step3: Configure the instance details.
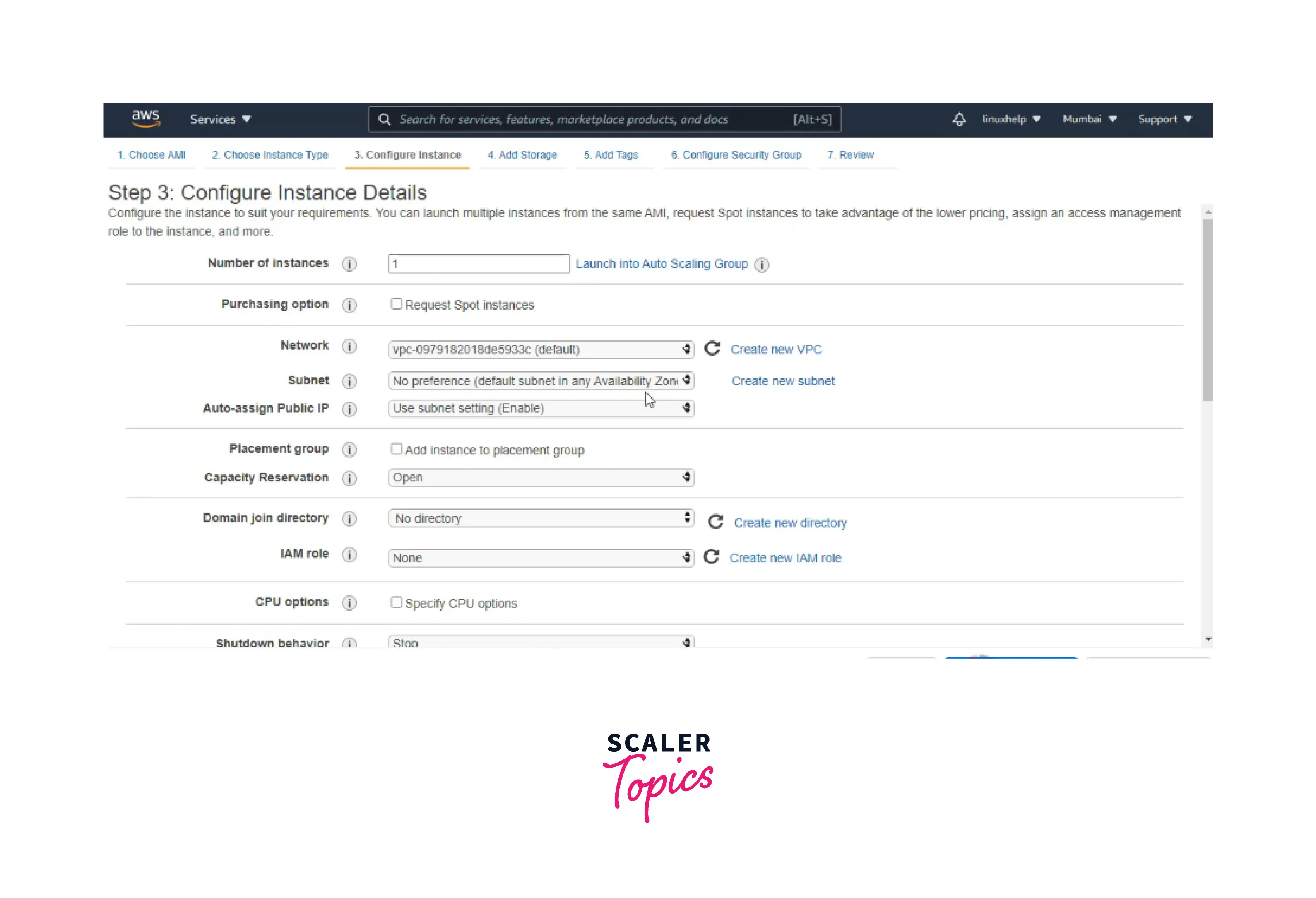
Step4: Add Storage.
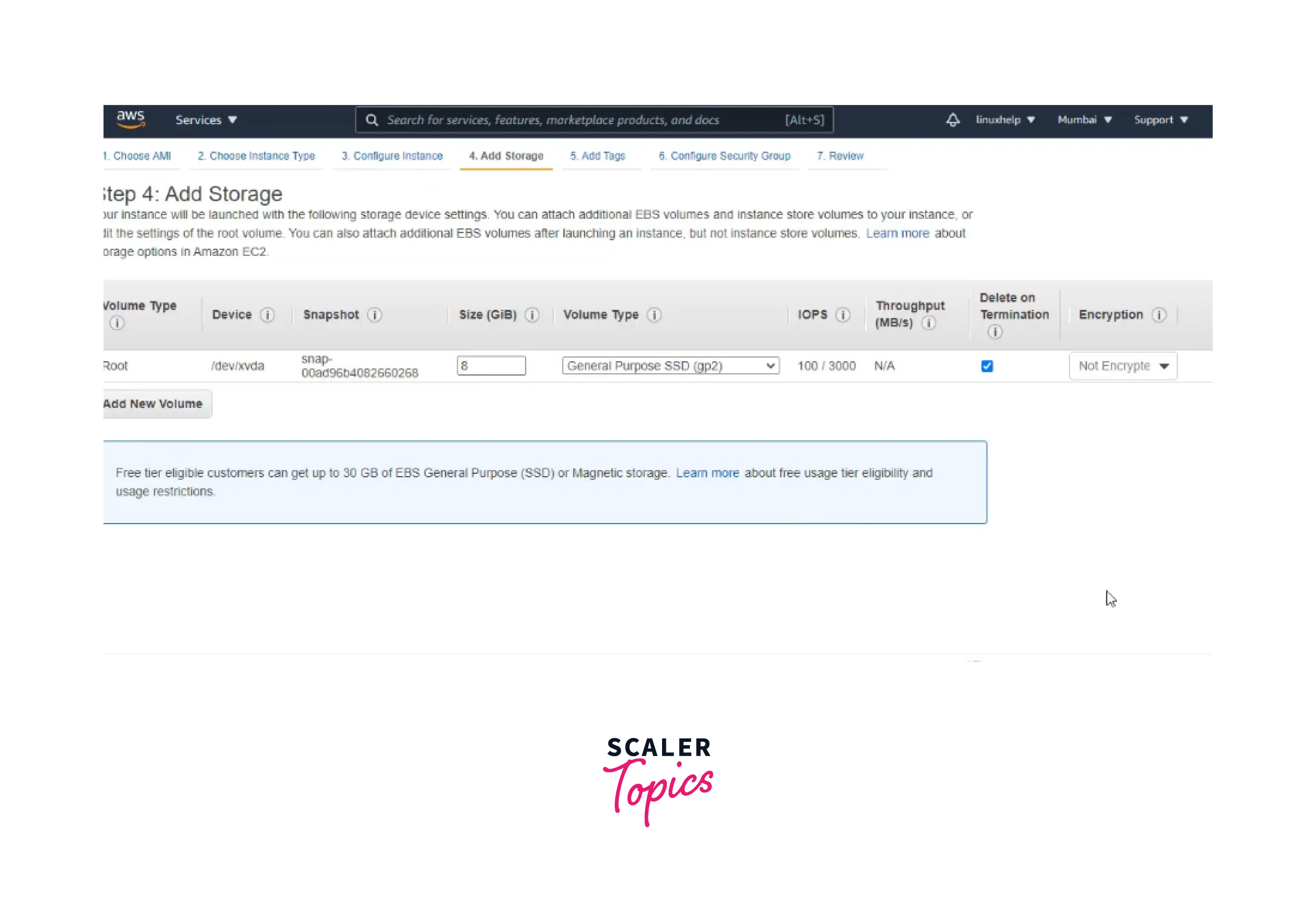
Step5: Add tags and Configure the security group with custom TCP with port number 21.
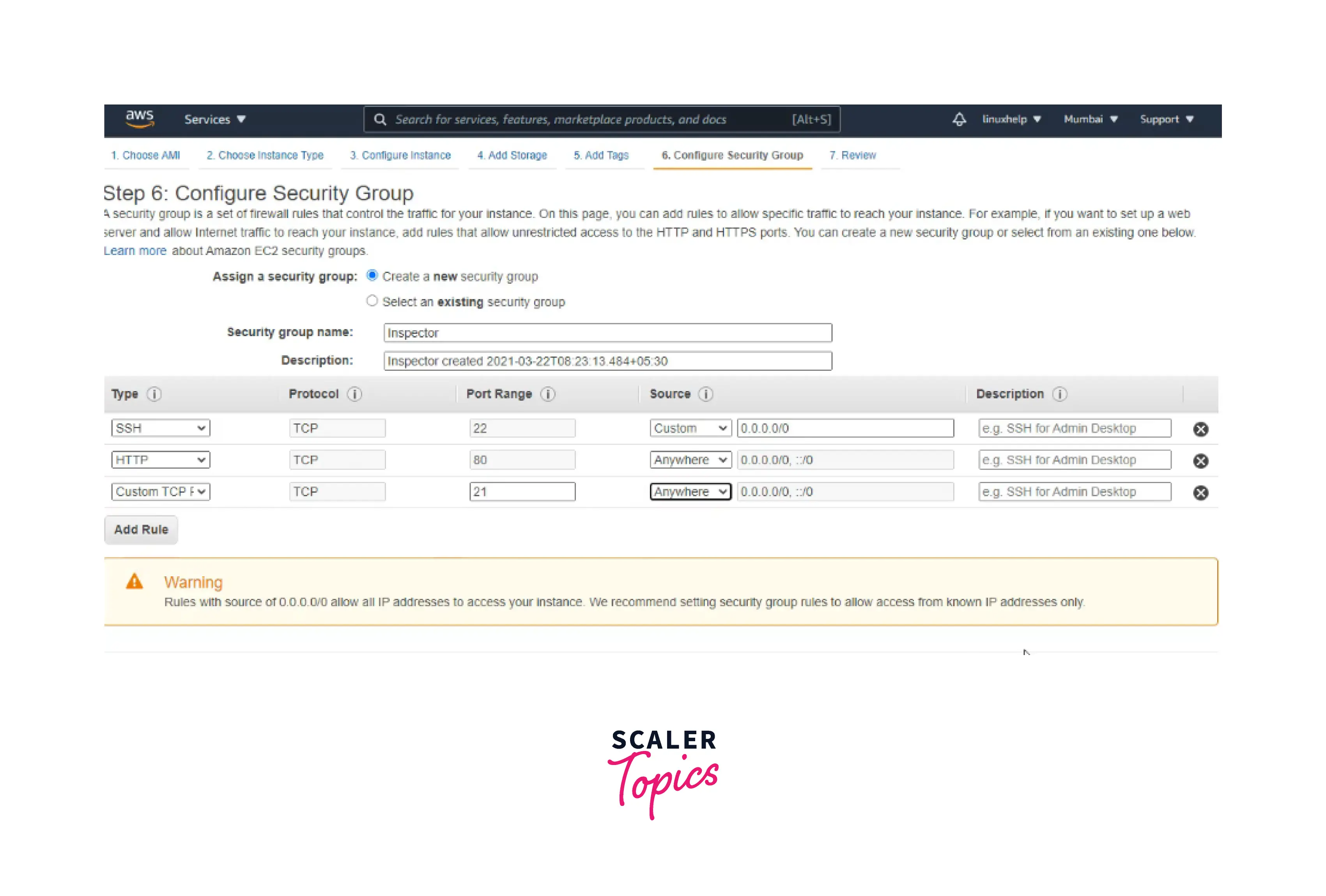
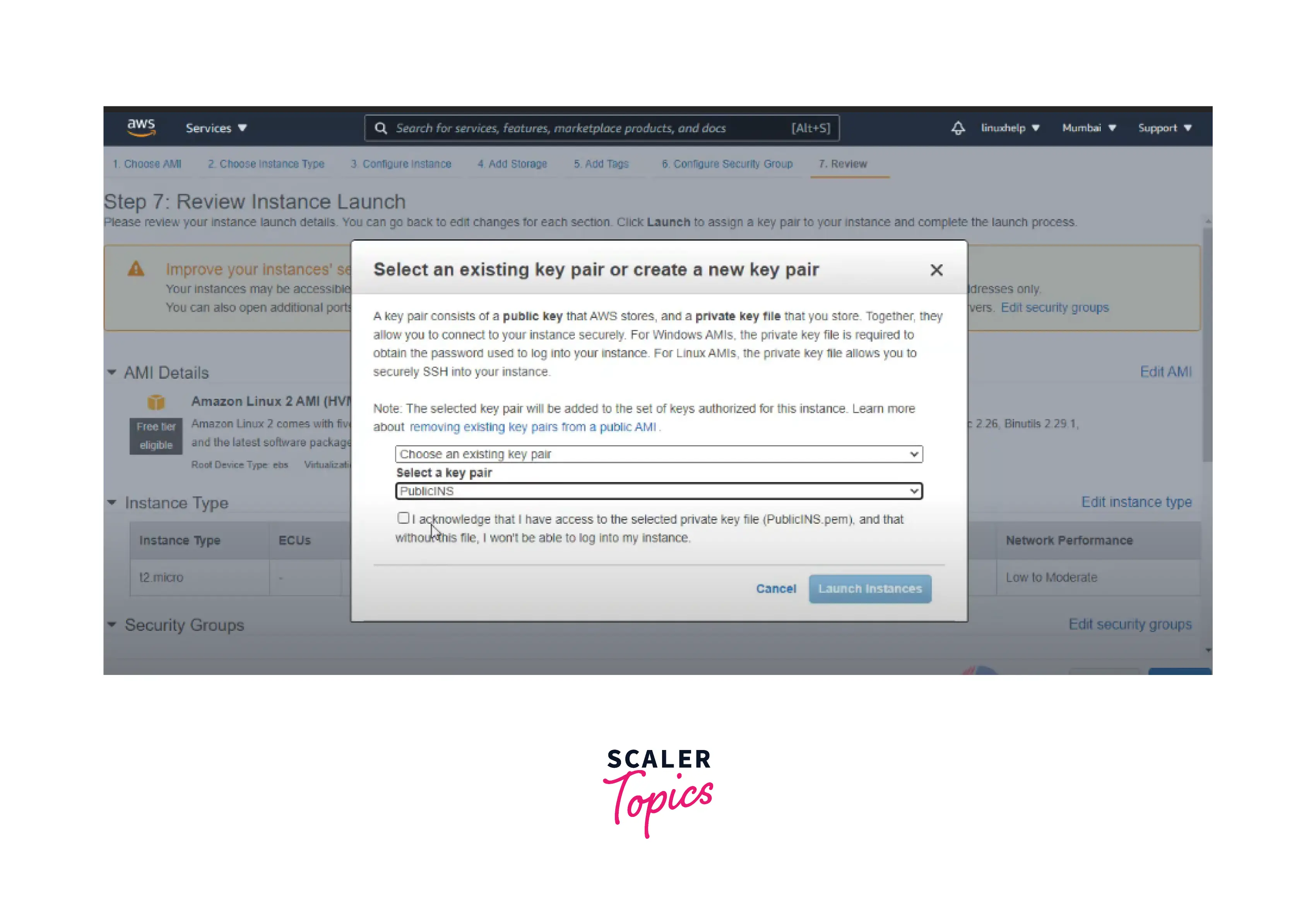
Step6: Finally, Review the instance launch.
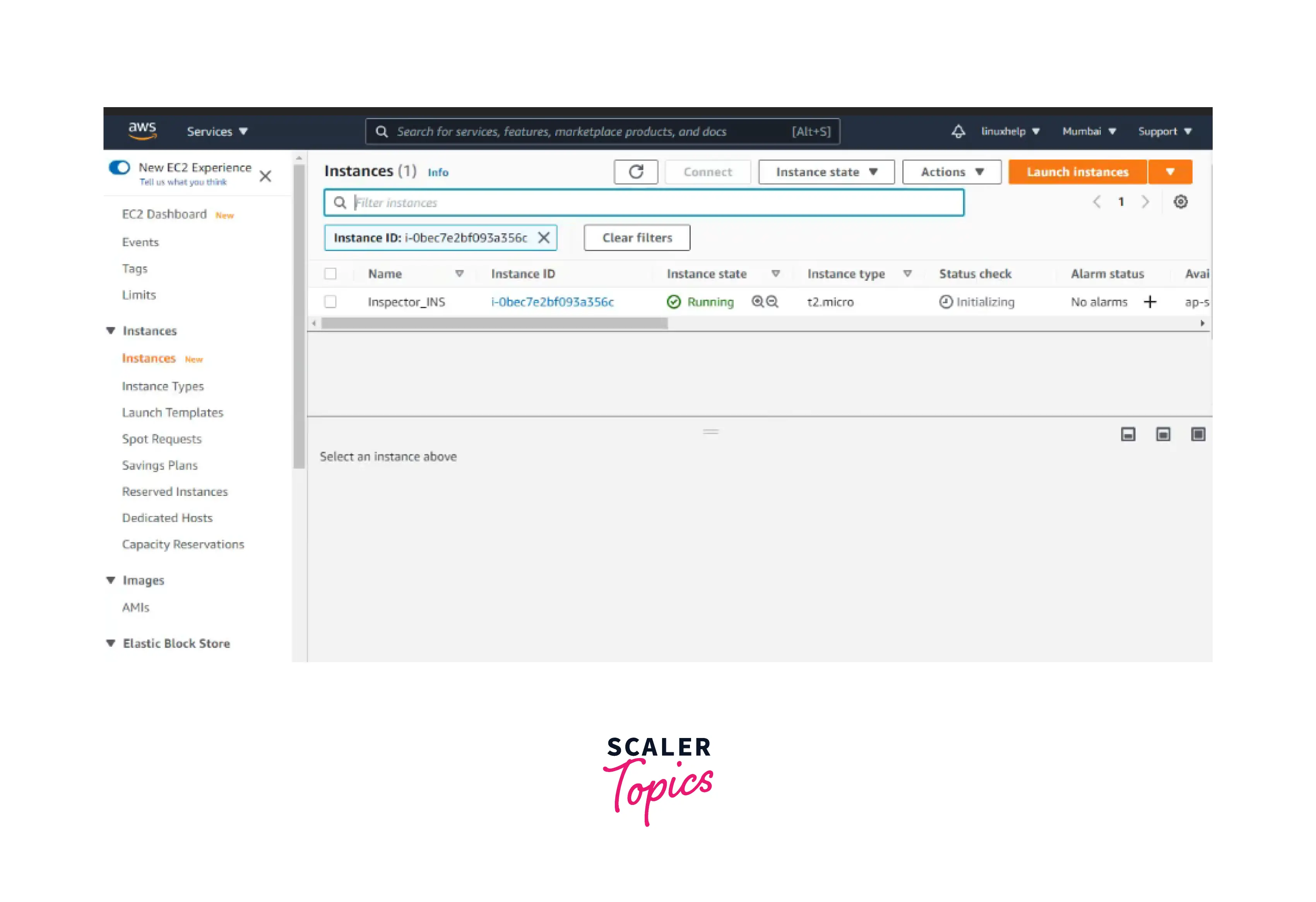
Now you can see the running instance in the below image.
Now, after successfully creating the EC2 instance, come back to the Amazon Inspector Console.
Step 1: You can define the assessment's target and provide the name.
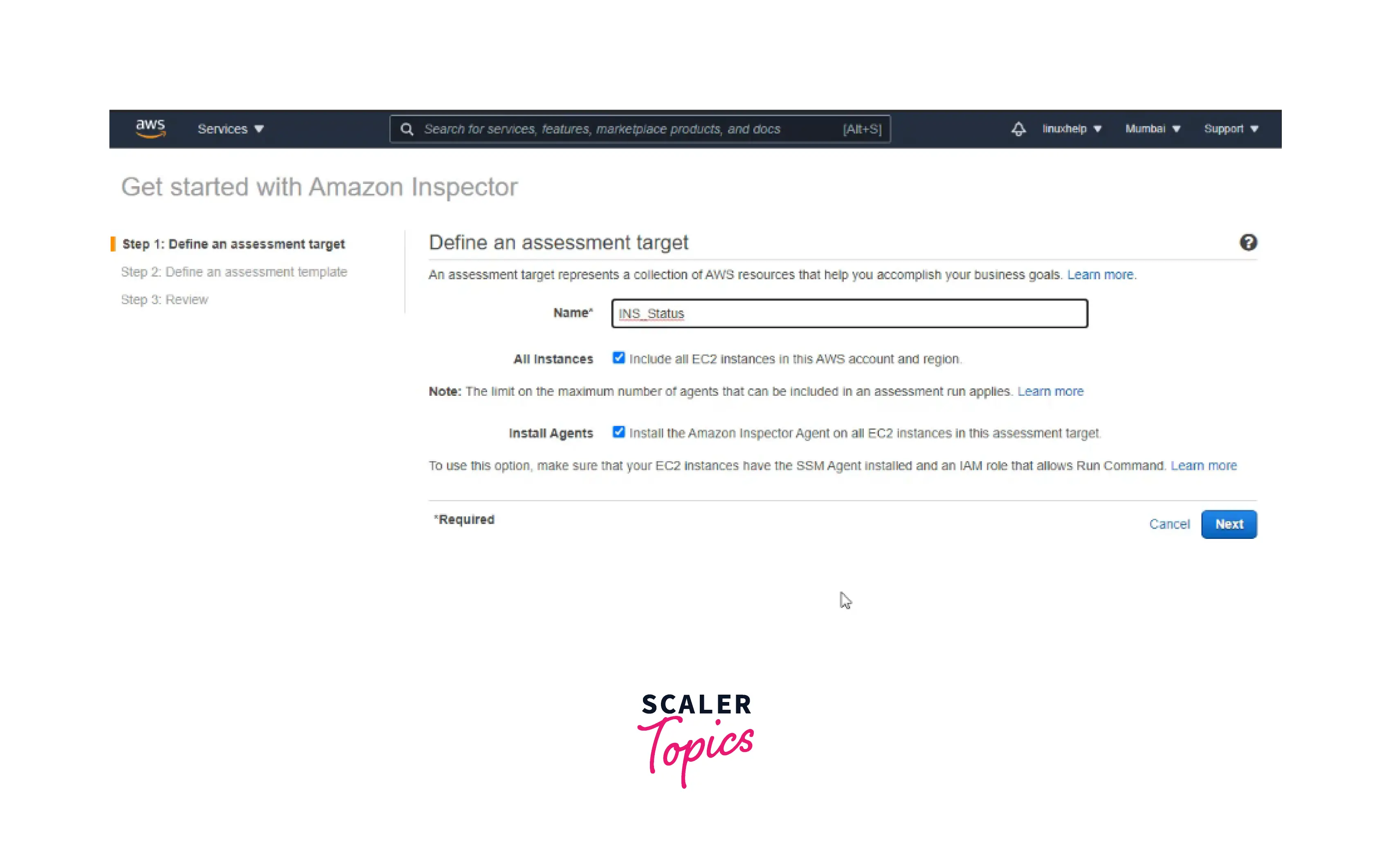
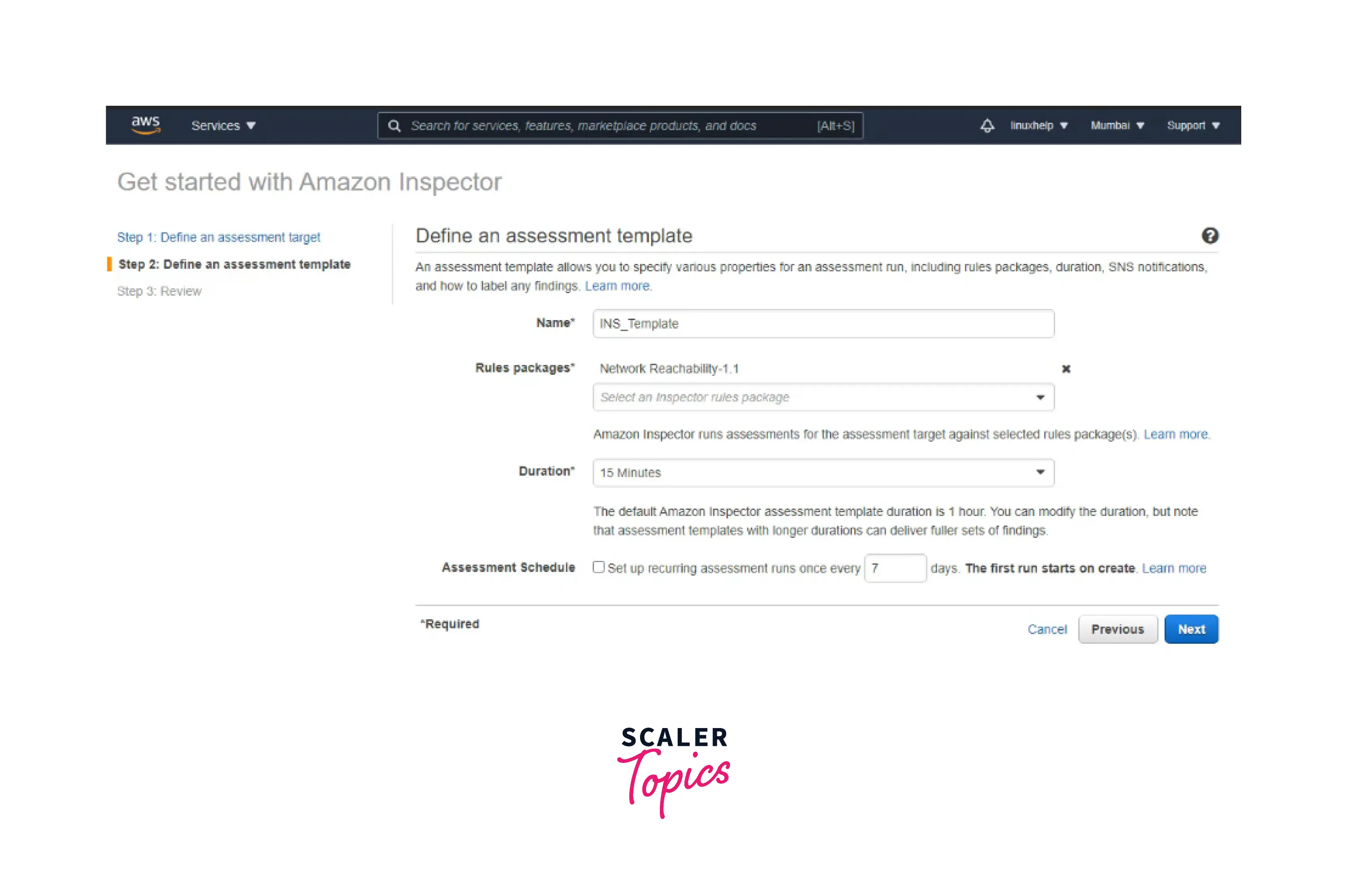
Step 2: Now, you can define the assessment template where you can specify the name, rule packages, duration(minimum is 15 minutes), and assessment schedule. Click on Next.
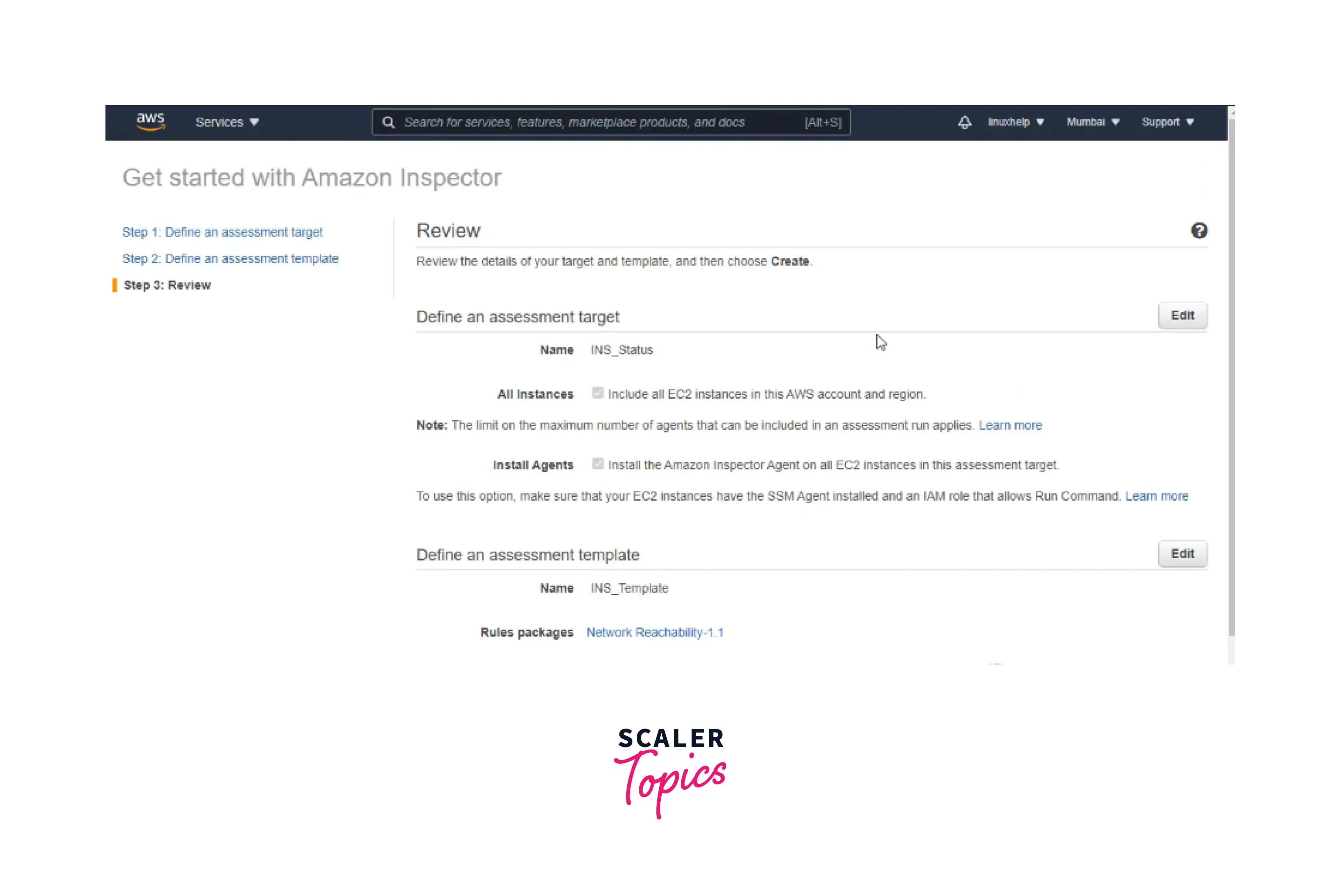
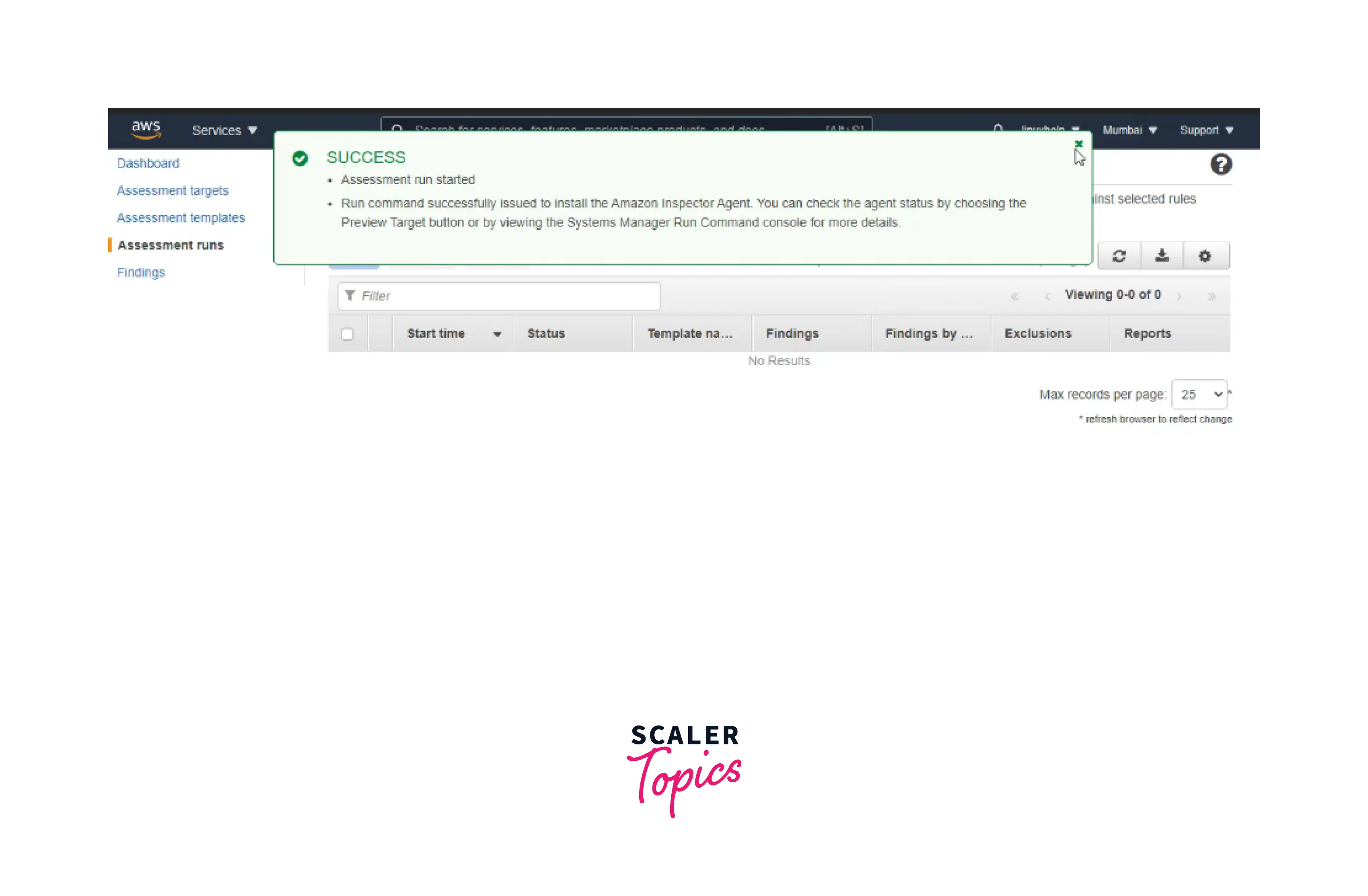
Step 3: Now, you can review the whole assessment specification, and you are done. A success message pops up, as shown below.
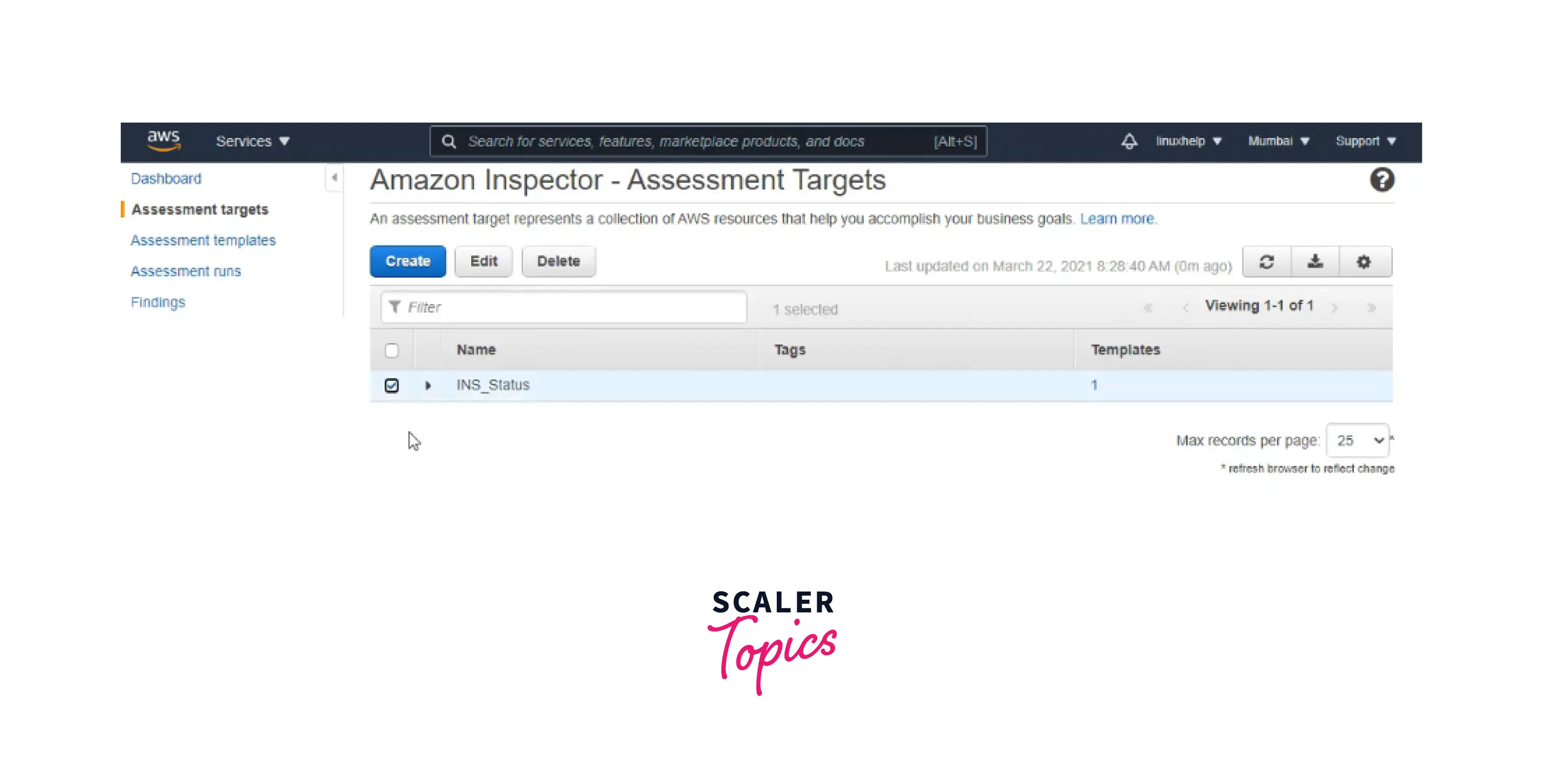
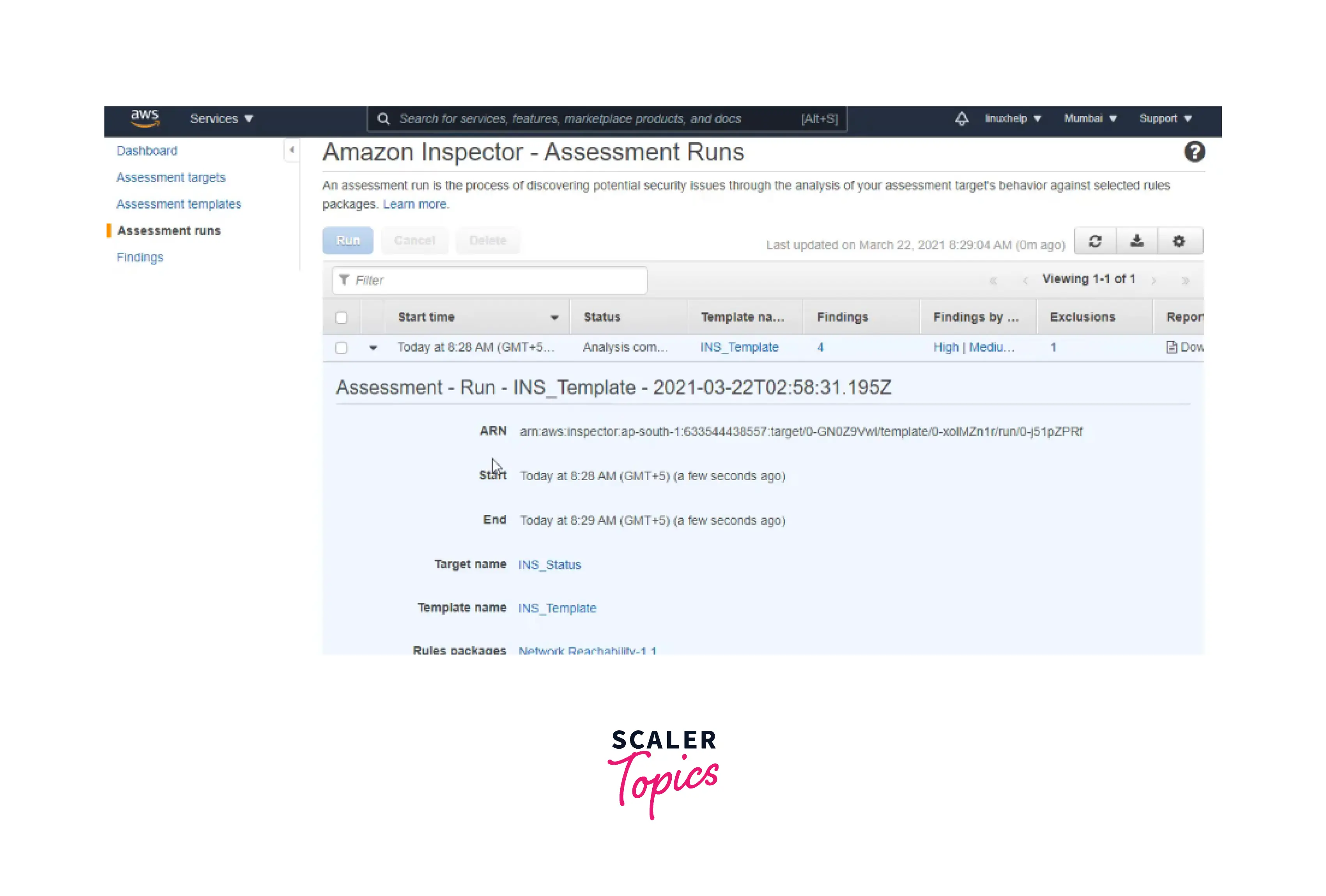
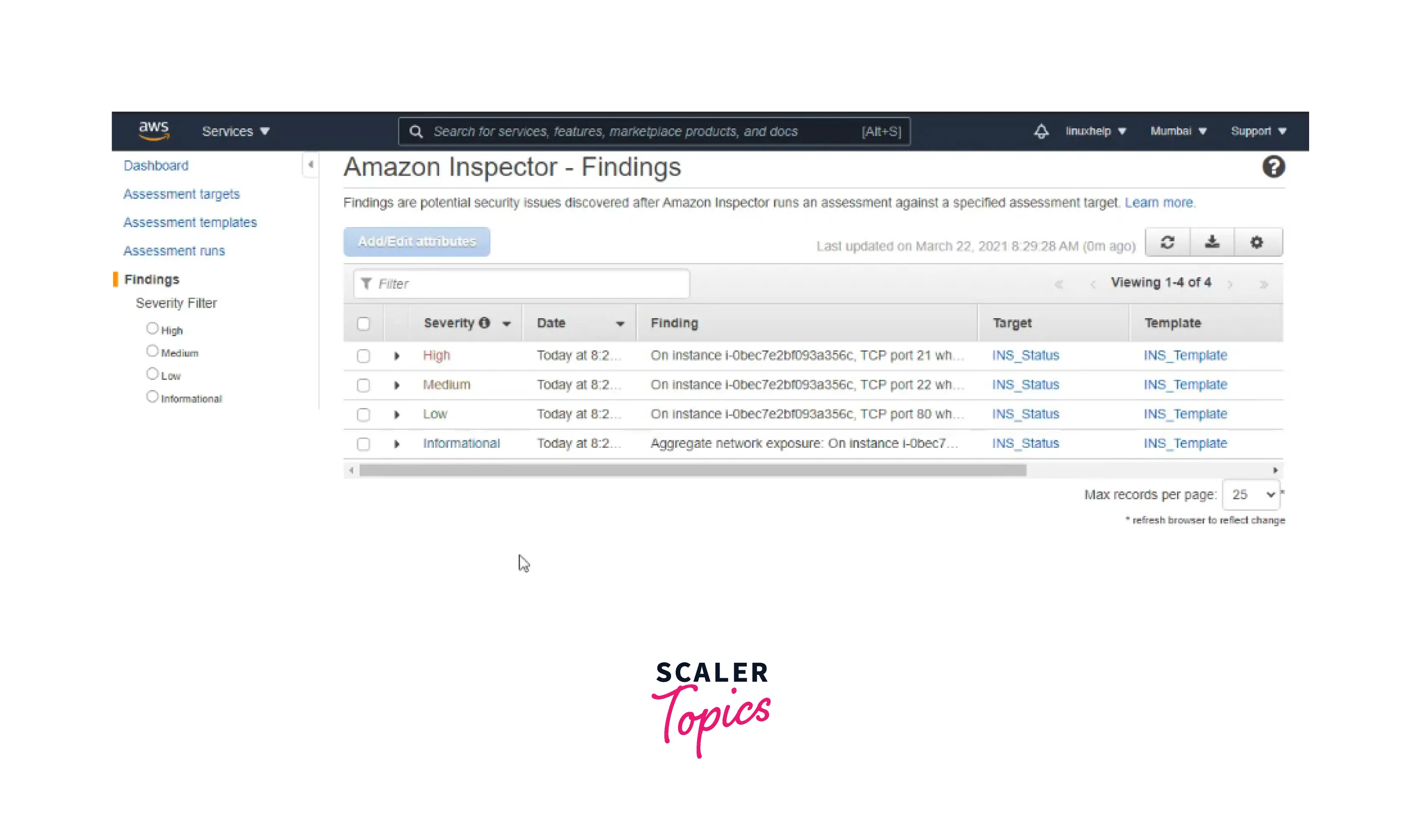
Now you can see the assessment targets, templates, runs, and findings using AWS Inspector, as shown below.
AWS Inspector pricing
-
Amazon EC2 instances being scanned and the total number of container pictures first scanned when sent to Amazon Elastic Container Registry (ECR) and rescanned during a month are combined to estimate monthly charges.
-
Amazon EC2 instance scans: Every EC2 instance is routinely checked for unwanted network exposure and software flaws. The total monthly cost is calculated based on the average * number of EC2 instances evaluated each month. Intermittently running instances are charged depending on the overall time used throughout a month.
-
Amazon ECR container image scans: Each container image set for AWS Inspector scanning and submitted to Amazon ECR is examined for software vulnerabilities.
With AWS Inspector, there are no minimum costs and no long-term obligations, and you simply pay for your use.
Free Trial:
-
All new AWS Inspector accounts are entitled to a 15-day free trial to test the service and determine its value. The trial includes free ongoing scanning of all qualifying Amazon Elastic Compute Cloud (EC2) instances and container images published to the Amazon Elastic Container Registry (ECR).
-
Additionally, you may examine projected spending in the AWS Inspector dashboard and totaled spending for the entire firm in the main AWS Inspector administrator account. Before making a choice, you may learn more about and calculate the cost of utilizing AWS Inspector to automatically and continuously scan your whole organization's Amazon EC2 and ECR infrastructure for vulnerabilities.
Benefits of AWS Inspector
-
Find Vulnerabilities Quickly Automatically uncover vulnerabilities and swiftly route those discoveries to the proper teams so they can act right away.
-
Put Patch Remediation first Create context-based risk assessments using the most recent information on common vulnerabilities and exposures (CVE) and variables like network accessibility to help you identify and prioritize risky resources.
-
Meet the Requirements for Compliance AWS Inspector scans support NIST Cybersecurity Framework(NIST CSF), Payment Card Industry Data Security Standard(PCI DSS), and other regulations' compliance needs and best practices.
-
Earlier Zero-Day Vulnerabilities Identification Utilize over 50 sources of vulnerability intelligence to speed up MTTR and assist in quickly identifying zero-day vulnerabilities.
AWS Inspector vs. Amazon GuardDuty
The services AWS Inspector and Amazon GuardDuty provide help to make your AWS environment more secure.
-
AWS Inspector exclusively examines Amazon EC2 and offers security assessments of your AWS environment. You must install the AWS Inspector agent to perform a wider range of security tests. While AWS CloudTrail logs, DNS logs, and other sources are used to monitor odd account behavior, Amazon GuardDuty assists with evaluating the whole AWS account and may be easily configured.
-
Amazon GuardDuty assists with analyzing the totality of your AWS accounts for potential threats, while AWS Inspector offers security analyses of the settings and configurations of your apps.
-
It's important to remember that when we refer to "applications" in Inspector, we currently only mean EC2 and ECR. Installing an agent will enable it to assess more configurations. On the other side, GuardDuty will continuously watch over your "AWS accounts, workloads, and data stored in Amazon S3" and let you know when a potential threat is found. If a "security finding" is found, automatic preventative actions may also be implemented.
Conclusion
-
With Amazon EC2 and AWS ECR container workloads, AWS Inspector provides a multi-resource vulnerability management tool. It identifies a variety of weaknesses that might be used to corrupt workloads, repurpose resources for malicious purposes, (or) exfiltrate data, such as software bugs and unintentional network exposure.
-
AWS Inspector delivers an aggregated, near real-time image of an organization's environment coverage to help you avoid coverage gaps.
-
AWS Inspector may provide assessments in the form of pre-built rule packages matched with well-known security best practices and vulnerability descriptions.
-
All new AWS Inspector accounts are eligible for a 15-day free trial to evaluate the service's value. The trial provides continual free scanning of all qualified AWS (EC2) instances and container images in the AWS cloud (ECR).
-
To help you discover and prioritize problematic resources, create context-based risk assessments utilizing the most recent information on common vulnerabilities and exposures (CVE) and characteristics such as network accessibility.
