AWS Internet Gateway
Overview
Understanding networking in AWS is crucial for sustaining Internet access while protecting sensitive servers and applications. Because there are components with similar names, it might be challenging to recall the differences and know how to use them. It can be quite distinct from traditional networks. Internet Gateways, NAT Gateways, and NAT Instances are three services that are frequently misunderstood. In this article, we will be learning about the AWS Internet Gateway.
What is an AWS Internet Gateway?
Communication between your VPC and the Internet is made possible via an internet gateway, a component of your VPC that is horizontally distributed, robust, and highly available. It supports both IPv4 and IPv6 communication. There are no bandwidth limitations or threats to the availability of your network traffic. AWS Internet Gateway lets a resource in your public subnets that has a public IPv4 or IPv6 address connect to the Internet. Resources on the internet can link to resources in your subnet using the accessible IPv4 or IPv6 address. For example, the AWS internet gateway enables you to access an EC2 instance on AWS using your local PC.
AWS Internet Gateway conceptually connects an AWS VPC to the Internet. It doesn't exist. Each VPC has a single Internet Gateway. If a VPC does not have an Internet Gateway, the resources cannot be accessible from the Internet. However, to connect to the Internet, resources inside of your VPC need an Internet Gateway.

How to Enable Internet Access from a VPC?
Enable Internet Access
You need to take the following steps to grant instances in a subnet in a VPC access to or from the internet using an AWS Internet Gateway.
- Make an `AWS Internet Gateway and join it to your VPC.
- Add a route that directs internet traffic to the internet gateway to the routing table for your subnet.
- Make that every instance on your network has either a public IPv4 address or an IPv6 address.
- Make that the required internet traffic may pass to and from your instance using your protection group rules and network access control lists.
Public and Private Subnets
- If a subnet is connected to a routing table with a route to an internet gateway, it is referred to as a public subnet.
- An AWS Internet Gateway cannot be reached by a private subnet even though it is connected to a routing table.
- In the routing table of your public subnet, you can add a route for the internet gateway to any addresses that are implicitly unknown to the routing table (0.0.0.0/0 for IPv4 or::/0 for IPv6).
- Alternatively, you can restrict the scope of the route to a smaller group of IP addresses, such as the public IPv4 addresses of your company's AWS externally accessible endpoints or the Elastic IP addresses of additional Amazon EC2 instances outside your VPC.
IP Addresses and NAT
-
For IPv4 internet connections, your instance requires a public IPv4 address. Either provide your instances Elastic IP addresses or configure your VPC so that it automatically allocates public IPv4 addresses to them.
-
Your instance only has access to the private (internal) IP address space defined within the VPC and subnet. The reply address field is logically set by the internet gateway to the public IPv4 address or elastic IP address of your instance rather than its private IP address when communication leaves your VPC network and goes to the internet.
-
To support IPv6 communication over the internet, your VPC and subnet must both have an associated IPv6 CIDR block and your instance must be assigned an IPv6 address from the subnet's range. IPv6 addresses are, by default made public because they are universally unique.
-
The graphic below depicts the availability zone A public subnet. There is a route in this subnet's route table that points all IPv4 traffic to the AWS Internet Gateway.
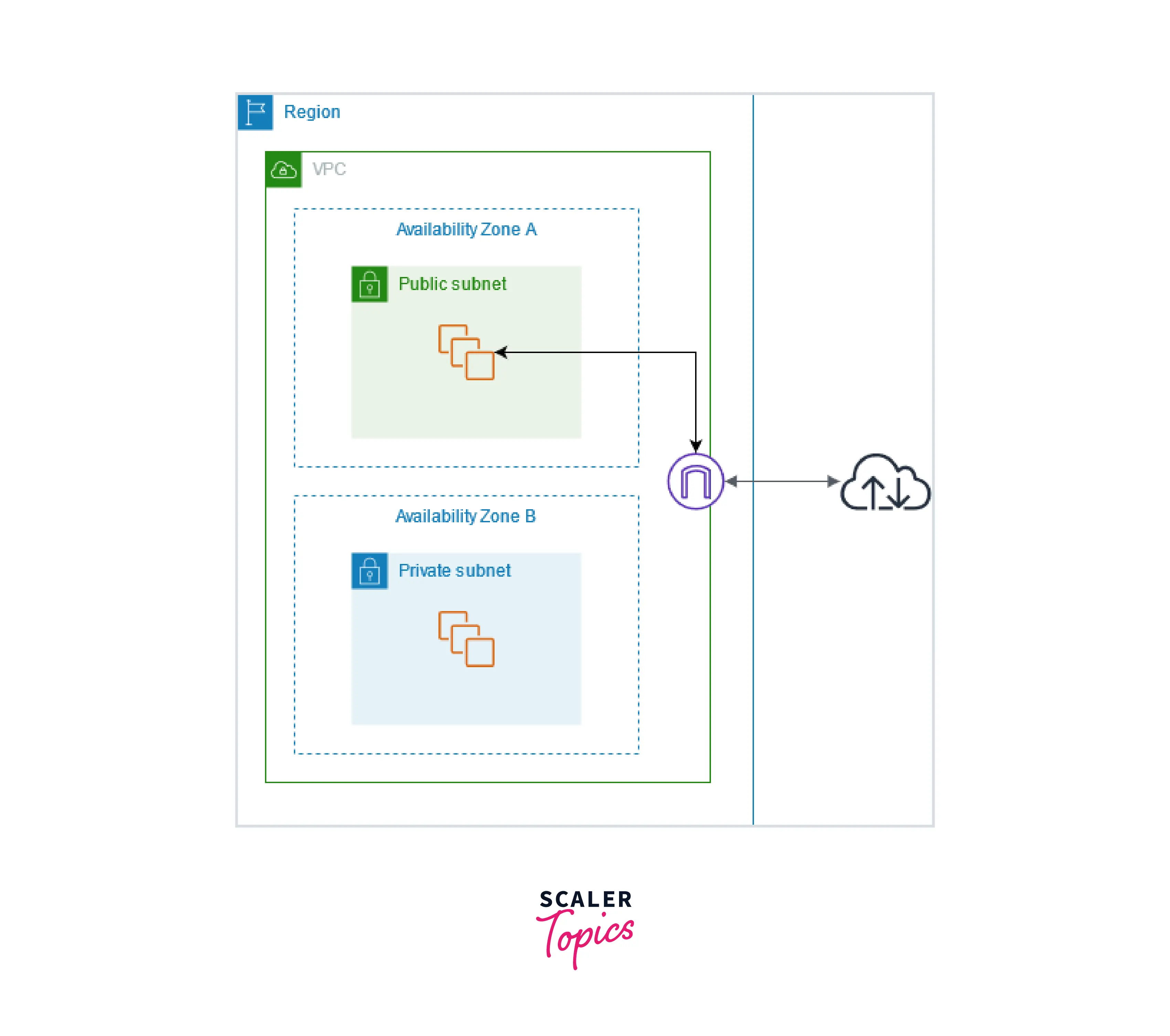
-
The instances on the public subnet require public IP addresses or elastic IP addresses to be able to communicate with the internet through the internet gateway. For instance, the subnet of availability zone B is private since the routing table does not contain a route to the internet gateway. Instances on the private subnet cannot access the internet through the internet gateway even though they have public IP addresses.
Internet Access for Default and Nondefault VPCs
The components needed for internet connection over IPv4 or IPv6 are automatically included with your VPC, as shown in the following table.
| Component | Default VPC | Nondefault VPC |
|---|---|---|
| Internet gateway | Yes | No |
| Route table with route to internet gateway for IPv4 traffic (0.0.0.0/0) | Yes | No |
| Route table with route to internet gateway for IPv6 traffic (::/0) | No | No |
| Public IPv4 address automatically assigned to instance launched into subnet | Yes (default subnet) | No (nondefault subnet) |
| IPv6 address automatically assigned to instance launched into subnet | No (default subnet) | No (nondefault subnet) |
- See Default VPCs for further details on default VPCs. See Create a VPC for additional details on setting up a VPC.
- See IP addressing for additional details on IP addressing in your VPC and managing how instances are given public IPv4 or IPv6 addresses.
- You must configure the routing and security you desire for the new subnet when you add it to your VPC.
Getting Started with Enabling Internet Access from a Subnet in a VPC
Create A Subnet
To Expand Your VPC by a Subnet
- Navigate to this to access the Amazon VPC console.
- Select Create subnet under Subnets from the navigation pane.
- Specify the subnet details as needed:.
- Name Tag: You can optionally give your subnet a name. By doing this, you produce a tag with the key Name and the Value you specify.
- VPC: Decide the VPC you want to create the subnet for.
- Availability Zone: You can choose to select the Availability Zone or Local Zone where your subnet will be located, or you can leave it at the default No Preference and let AWS pick one for you.
- IPv4 CIDR Block: Give your network an IPv4 CIDR block, such as 10.0.1.0/24. Please refer to IPv4 VPC CIDR blocks for further details.
- CIDR Block for IPv6 :(Optional) Select Specify a custom IPv6 CIDR if an IPv6 CIDR block has been linked to your VPC. Set the subnet's hexadecimal pair value, or leave it at the default.
- Select Create.
Create and Attach an Internet Gateway in AWS Internet Gateway
Connect Your Internet Gateway to Your VPC Once it has been created.
To Build a Web Gateway and Connect it to your VPC
- Navigate to this to access the Amazon VPC console.
- Select Internet gateways from the navigation pane, and then select Create internet gateway.
- Add or remove a tag if you choose.
[Add a tag] Choose to Add tag and do the following:
- Put the key name in the Key field.
- Enter the key value as Value.
- Select Create internet gateway.
- Choose Actions, Attach to VPC after selecting the newly established internet gateway.
Create A Custom Route Table
To Create a Custom Route Table
- Navigate to the Amazon VPC console at this
- Select Create route table from the Route Tables menu in the navigation pane.
- You can optionally give your route table a name in the Create route table dialogue box. Next, Select your VPC and click Create route table.
- Choose the newly constructed custom route table. The tabs for working with its routes, affiliations, and route propagation are displayed in the details pane.
- Select Edit routes, Add a route, and then add the aforementioned routes as appropriate on the Routes page. When you are finished, select Save changes.
- Enter 0.0.0.0/0 in the Destination box and choose the internet gateway ID from the Target list for IPv4 traffic.
- Enter::/0 in the Destination box and choose the internet gateway ID from the Target list for IPv6 traffic.
- Select the checkbox for the subnet on the Subnet associations tab, then select Edit subnet associations, followed by Save associations.
Create a Security Group for Internet Access
To Create a Security Group and Associate it with an Instance
- Navigate to Amazon EC2 console at this
- Select Security Groups from the navigation pane, and then select Create security group.
- Enter a name and description for the security group.
- Choose your VPC under the VPC menu.
- Select Add Rule under Inbound Rules, then fill out the necessary details. Choose HTTP or HTTPS from Type, for instance, and enter 0.0.0.0/0 for IPv4 traffic or::/0 for IPv6 traffic as the Source.
- Select Create security group.
- Instances should be selected from the navigation pane.
- Choose Actions, Security, and then Change Security Groups after selecting the instance.
- Choose to Add a security group after selecting an existing security group for Associated security groups. Select Delete to remove a security group that is already connected. Select Save once you're done making adjustments.
Assign an Elastic IP Address to an Instance in AWS Internet Gateway
To allocate an Elastic IP address and assign it to an instance through the console
- Navigate to this to access the Amazon VPC console.
- Select Elastic IPs from the navigation pane.
- Pick and Allocate a new address.
- Select Allocate.
- Choose Actions, then Associate address after selecting the Elastic IP address from the list.
- Select either the instance ID or the network interface ID** after selecting Instance or Network interface. Choose Associate after choosing the private IP address you want to pair the elastic IP address with.
Detach an Internet Gateway from Your VPC
To Detach an AWS Internet Gateway
- Navigate to this to access the Amazon VPC console.
- Select the Elastic IP address by selecting Elastic IPs from the navigation pane.
- Select Disassociate address under Actions. Select the Dissociate address option.
- Internet gateways can be selected from the navigation pane.
- Select the internet gateway, then click on Detach from VPC under Actions.
- Select Detach internet gateway from the Detach from VPC dialogue box.
Delete an Internet Gateway in AWS Internet Gateway
To Delete an Internet Gateway
- Visit the Amazon VPC console at this.
- The navigation pane allows for the selection of Internet gateways.
- After choosing the internet gateway, select Actions, And delete internet gateway.
- In the Delete Internet Gateway dialogue box, type delete and ch tooose Delete Internet Gateway.
Difference between Internet Gateway and NAT Gateway
| AWS Internet Gateway | NAT Gateway |
|---|---|
| The horizontally scaled, redundant, and highly available VPC component known as the Internet Gateway (IGW) enables es communication between your VPC and the internet. | NAT Gateway (NGW) is a managed Network Address Translation (NAT) service. |
| Resources (like EC2 instances) on public subnets can connect to the internet thanks to `Internet GatewaSimilarlyilar to this, resources on the internet can us by e the public to connect to resources on your subnet. | Similar to Internet Gateway (IGW), NAT Gateway performs a similar function, but it only allows connections to be established in one direction: instances on a private subnet can connect to services outside your VPC, but external services cannot initiate connections with those instances. |
| IPv4 and IPv6 traffic are supported by Internet Gateway. | NAT gateways are supported for IPv4 or IPv6 traffic. |
| Your network traffic is not subject to availability concerns or bandwidth restrictions as a result of Internet Gateway. | Each NAT gateway is developed and installed with redundancy in a distinct Availability Zone. |
| A VPC can only have one Internet Gateway connected to it. | A public NAT gateway can only have one Elastic IP address associated with it. |
| Internet Gateway is not Availability Zone specific. | Establish a NAT gateway in each availability zone to create an architecture that is independent of the availability zone. |
| Having an internet gateway in your account is free of charge. | Each hour that your NAT gateway is operational and each gigabyte of data it processes are billed to you. |
Conclusion
- In this article we first learned what is an AWS Internet Gateway and also went through its different features
- We also learned about enabling internet access from a VPC and also the concepts associated with it like public and private subnets and IP and NAT Addresses.
- We also went through a detailed explanation for getting started with enabling internet access from a subnet in a VPC which involved Creating a subnet, Creating and attaching an internet gateway, Creating a custom `route table', Creating a security group for internet access, Assigning an Elastic IP address to an instance, Detaching an internet gateway from your VPC and Deleting an internet gateway.
- In the end, we learned about the difference between AWS Internet Gateway and NAT Gateway.
