AWS KMS ( Key Management Service)
Overview
AWS Key Management Service (KMS) provides centralized management of the cryptographic keys required to secure your data. The service is connected with several AWS services, making it simple to encrypt data stored in these services and manage access to the keys used to decode it.
What is AWS Key Management Service (AWS KMS), and Why do We Need It?
AWS KMS is used for the encryption of data. The AWS KMS's primary function is to control and store these encrypted keys. Encryption of data is essential for sensitive information that unapproved customers should not access. Encryption of data both at rest and when it's being sent.
Client-Side and Server-Side Encryption are the primary strategies for implementing Encryption at rest.
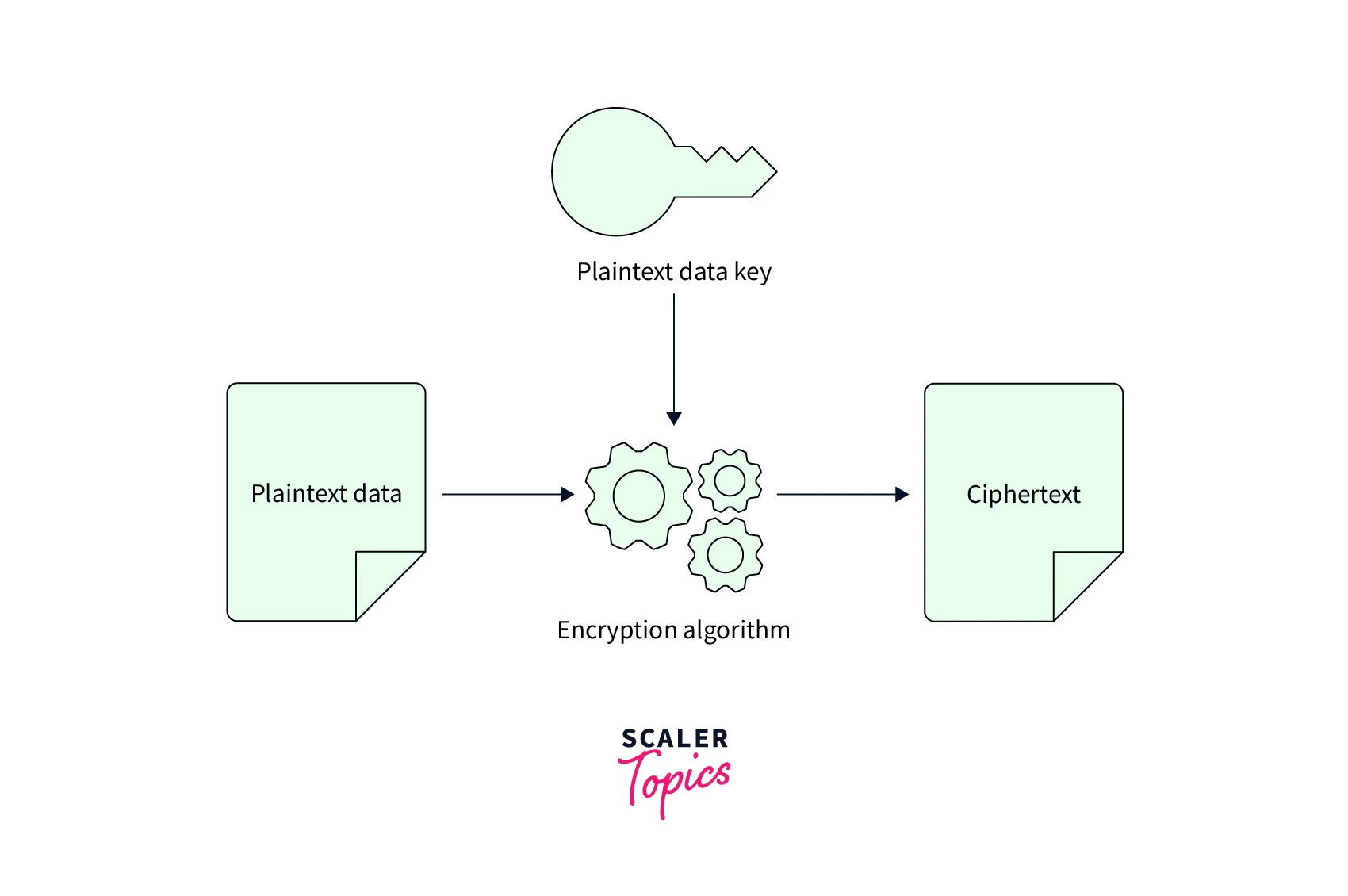
Encryption on the Client Side:
It allows you to encrypt data on your computer before sending it to a server (or) backend services, such as AWS Simple Storage Service, AWS Elastic Block Store, AWS Redshift, etc. In a nutshell, this encryption allows you to handle your keys while encrypting your data.
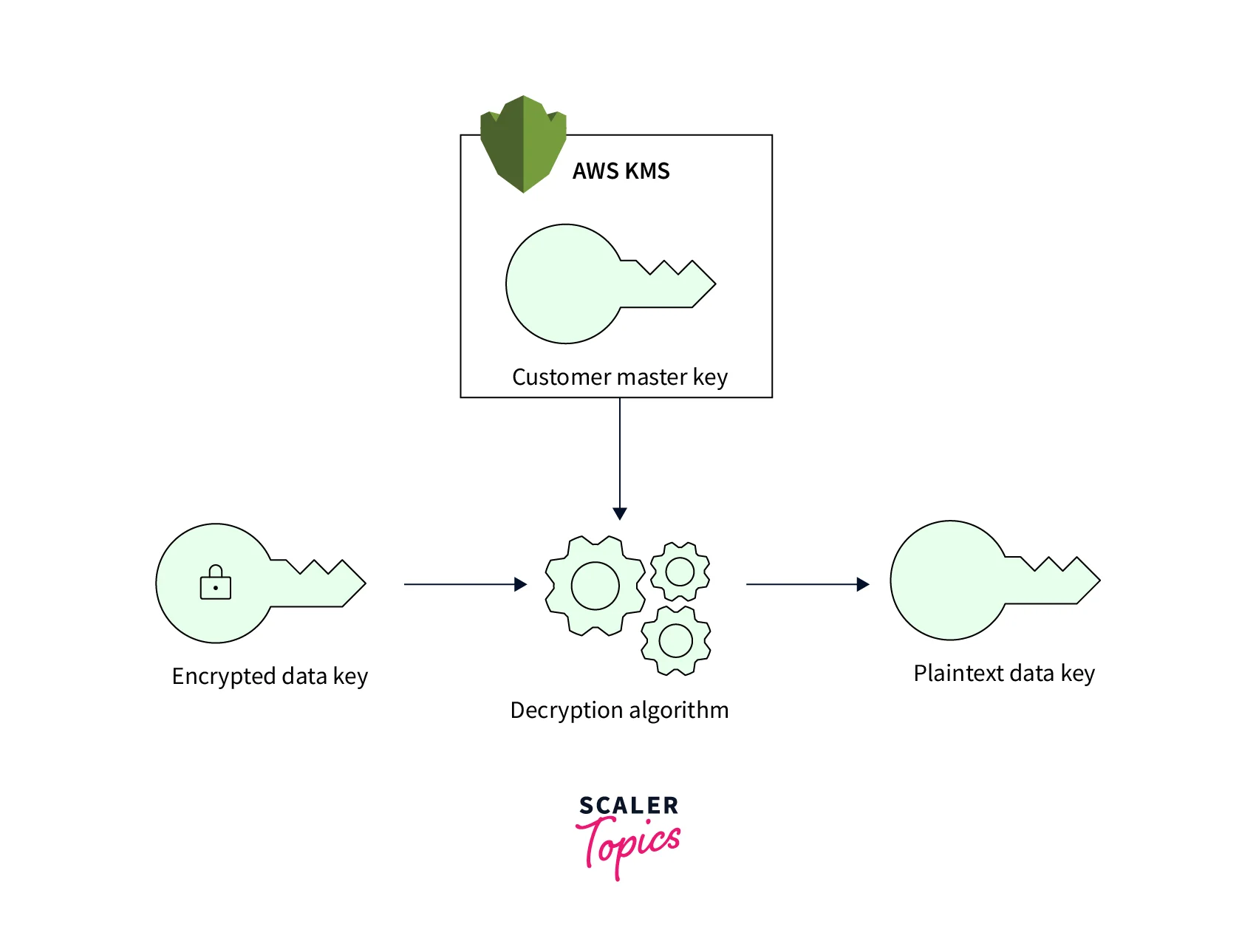
Encryption on the Server Side:
AWS encrypts and maintains the keys for the user, whereas users allow backend applications to encrypt and handle the keys on their behalf.
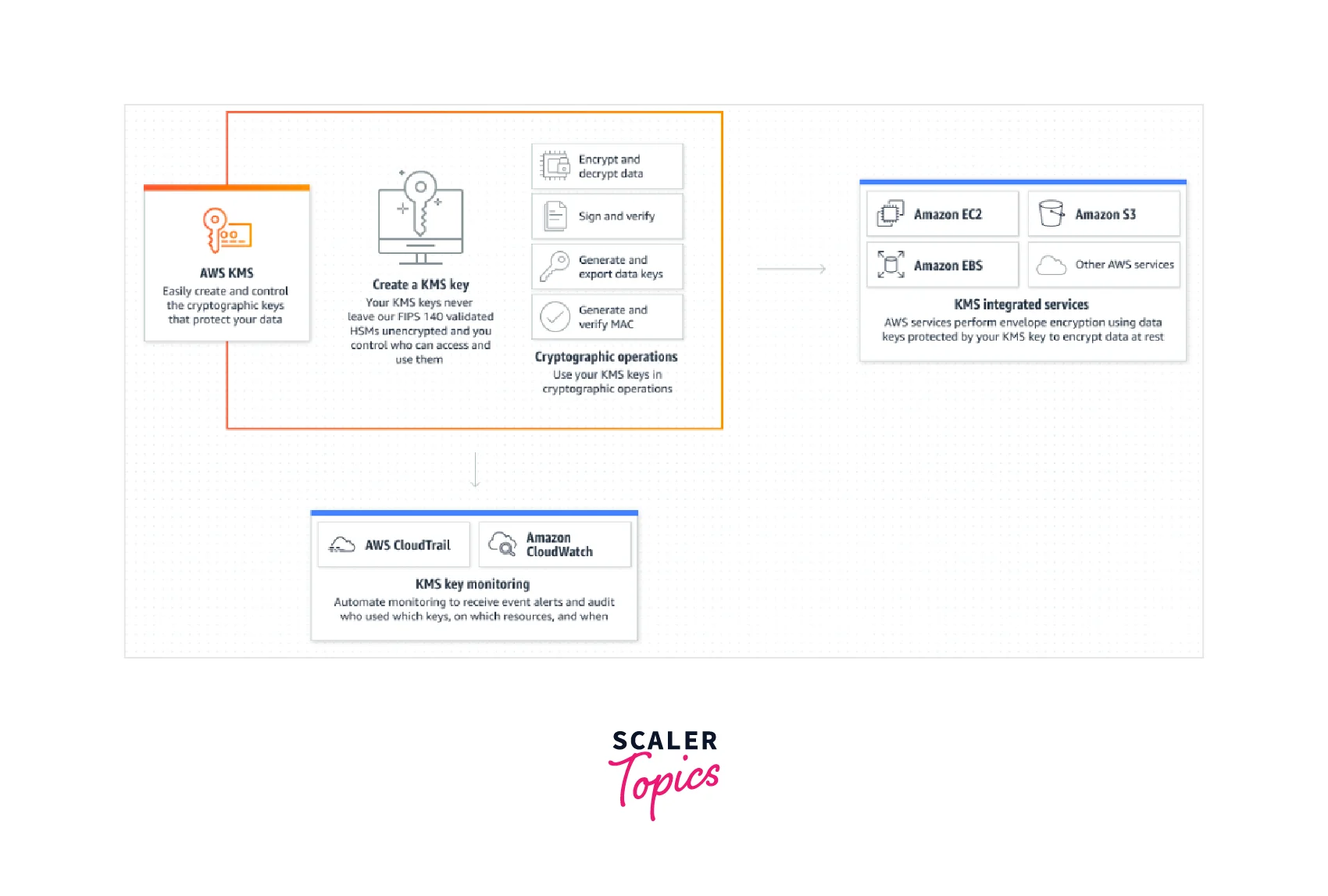
Features of AWS KMS
-
Centralized Key Management: AWS KMS gives you centralized management over your keys' lifespan and permissions. You can create new keys whenever you choose, and you can separate the users from the managers of keys.
-
Integration of AWS Services: AWS KMS interfaces with AWS services to encrypt data in transit or to enable signing and verification using an AWS KMS key. Integrated AWS services employ envelope encryption to safeguard data at rest, where a data key is used to encrypt data and is encrypted under a KMS key stored in AWS KMS. In your AWS account, you may generate two types of KMS key resources: When required, an AWS-managed KMS key can be generated automatically. You may list or inventory AWS Governed KMS keys in AWS CloudTrail and obtain a record of their use, but permissions for the resource are managed by the AWS service for which it was established. A customer-controlled KMS key allows you complete control over the key's rights and lifetime.
-
Capabilities in Auditing: If you enable AWS CloudTrail for your AWS account, each request to AWS KMS is logged in a log file and transmitted to the Amazon S3 bucket you chose when you enabled AWS CloudTrail.
-
Scalability, durability, and High Availability: The AWS KMS service is completely managed. The service automatically adjusts to suit your demands as your use of Encryption develops. It allows you to manage and utilize thousands of KMS keys in your account at any time.
-
Secure : AWS KMS employs Hardware Security Modules (HSMs) that have been certified under FIPS 140-2 or are validated to produce and safeguard keys. Your keys are only used within these devices and should never be left unencrypted. The plaintext keys are not written to disk and are always utilized in the HSMs' volatile memory for the duration required to conduct the specified cryptographic operation. This is true whether you ask AWS KMS to create keys on your behalf, import them into the service, or use the custom key store capability to produce keys in an AWS CloudHSM cluster. Keys generated by the AWS KMS service are never transferred outside of the AWS area in which they were generated and may only be used in that region.
-
HMAC : Hash-Based Message Authentication Codes (HMACs) may be generated and verified using KMS's FIPS 140-2 approved hardware security modules (HSMs). HMACs are a type of cryptographic building block that uses secret key material within a hash function to generate a unique keyed message authentication code.
-
Custom Key Store: AWS KMS allows you to establish your key store using your control HSMs. An AWS CloudHSM cluster backs up each custom key store. AWS KMS produces and stores non-extractable key material for the KMS key in your own managed AWS CloudHSM cluster. When you utilize a KMS key in a custom key store, the cryptographic operations are handled by the cluster's HSMs. This functionality combines AWS KMS's ease and extensive integration with the additional control of an AWS CloudHSM cluster in your AWS account. AWS KMS offers complete console and API support for developing, deploying, and maintaining bespoke key stores. You may use the KMS keys in your custom key store just like any other KMS key.
-
Asymmetric Keys: AWS KMS allows you to create and use asymmetric KMS keys and data key pairs. A KMS key can be designated for usage as a signing key pair or an encryption key pair. Inside Hardware Security Modules (HSMs), key pair creation and asymmetric cryptographic operations using these KMS keys are carried out.
Advantages of AWS KMS
-
Completely managed: You define permissions to use keys to govern access to your encrypted data, while AWS KMS enforces your permissions and manages your keys' durability and security.
-
Encryption of information: You may use KMS-protected data encryption keys to encrypt locally within your apps, thanks to the integration of AWS KMS and the AWS Encryption SDK. Using simple APIs, you may also include Encryption and critical management into your apps, regardless of where they run.
-
Centralized key management: It offers a solo point and regularly sets policies for use with your apps and AWS services. You may quickly generate, rotate, remove, and manage critical permissions using the AWS CLI, SDK, or management console.
-
Manage AWS services encryption: AWS KMS is integrated with other services to make it easier to use your keys to encrypt data across all of your AWS workloads. You decide what amount of access control you require, including the ability to exchange encrypted resources between accounts and services.
-
Sign data digitally: AWS KMS allows you to perform digital signature operations using asymmetric key pairs to ensure the integrity of your data. Recipients of digitally signed data can validate the signatures regardless of whether they have an AWS account.
-
Low price: AWS KMS requires no commitment and no upfront fees. You pay US $1 per month to keep any key you make. AWS-managed keys generated by AWS services on your behalf are free to keep. Whenever users use or manage keys beyond the free tier, you are charged per request.
-
Compliance : To simplify your compliance requirements, the assurance and quality controls in AWS KMS have received certification under several compliance schemes. Your keys can be kept in single-tenant Hardware Security Modules (HSMs) in instances of AWS CloudHSM that you manage using AWS KMS.
-
Internal auditing: AWS CloudTrail and KMS are connected to record all API calls, including key management activities and usage. You can control risk, adhere to compliance standards, and do forensic analysis with API request logging.
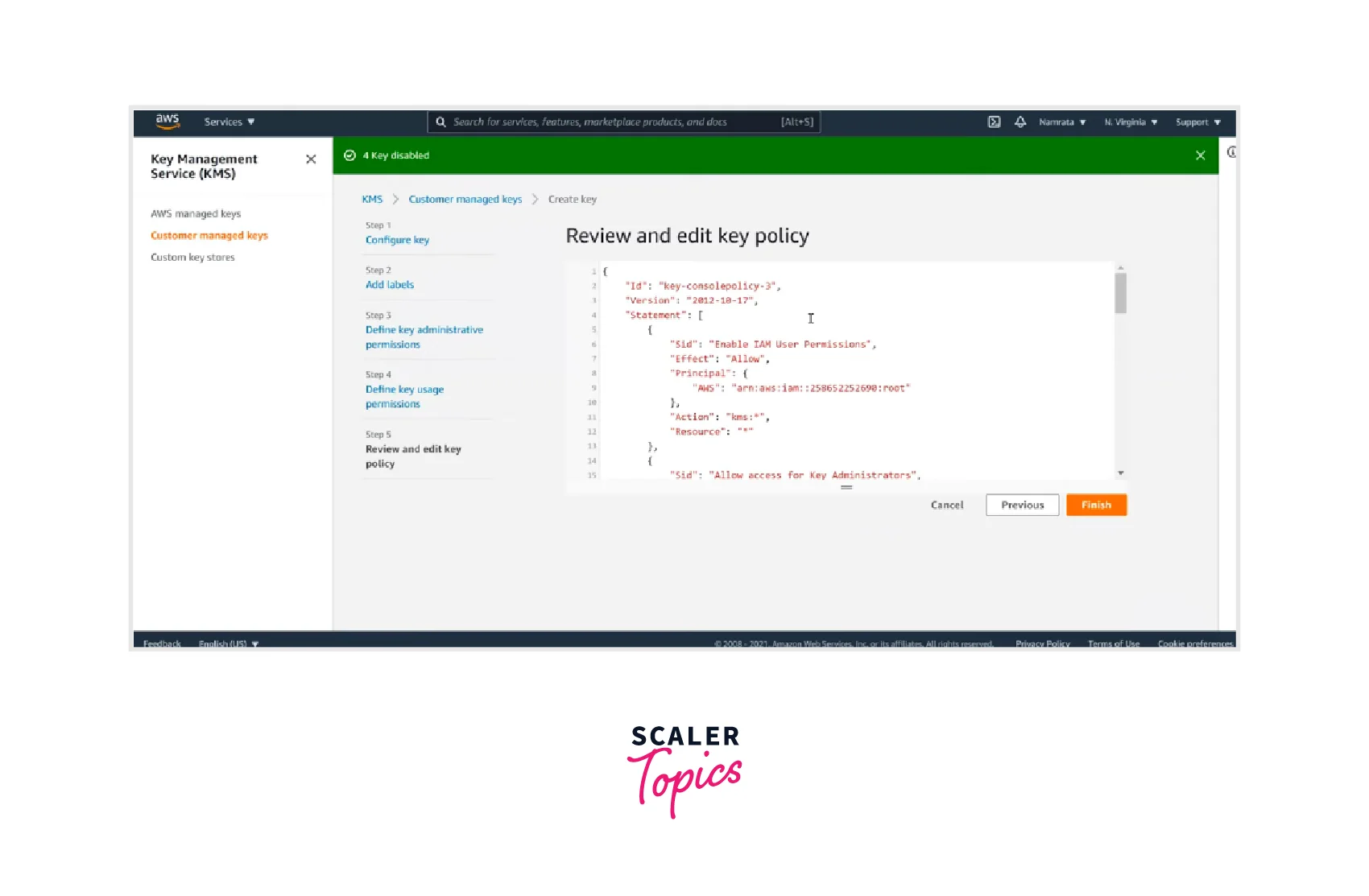
Steps to Create Keys Using AWS KMS
- Login to the AWS account and open KMS Console from AWS Management Console. Click on "Create Key."
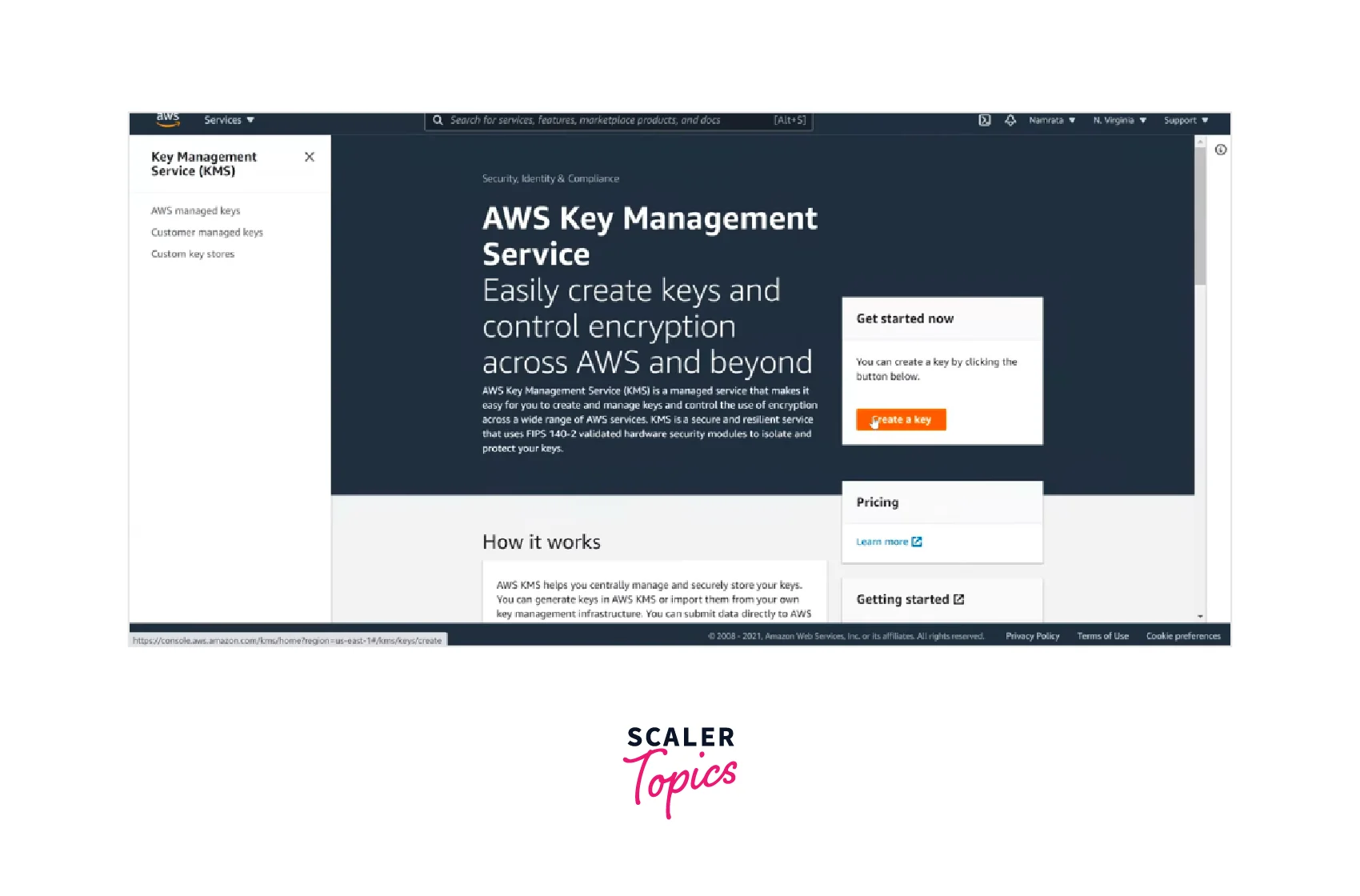
- Now, you can configure the key by selecting the key type, key usage, etc., and clicking Next.
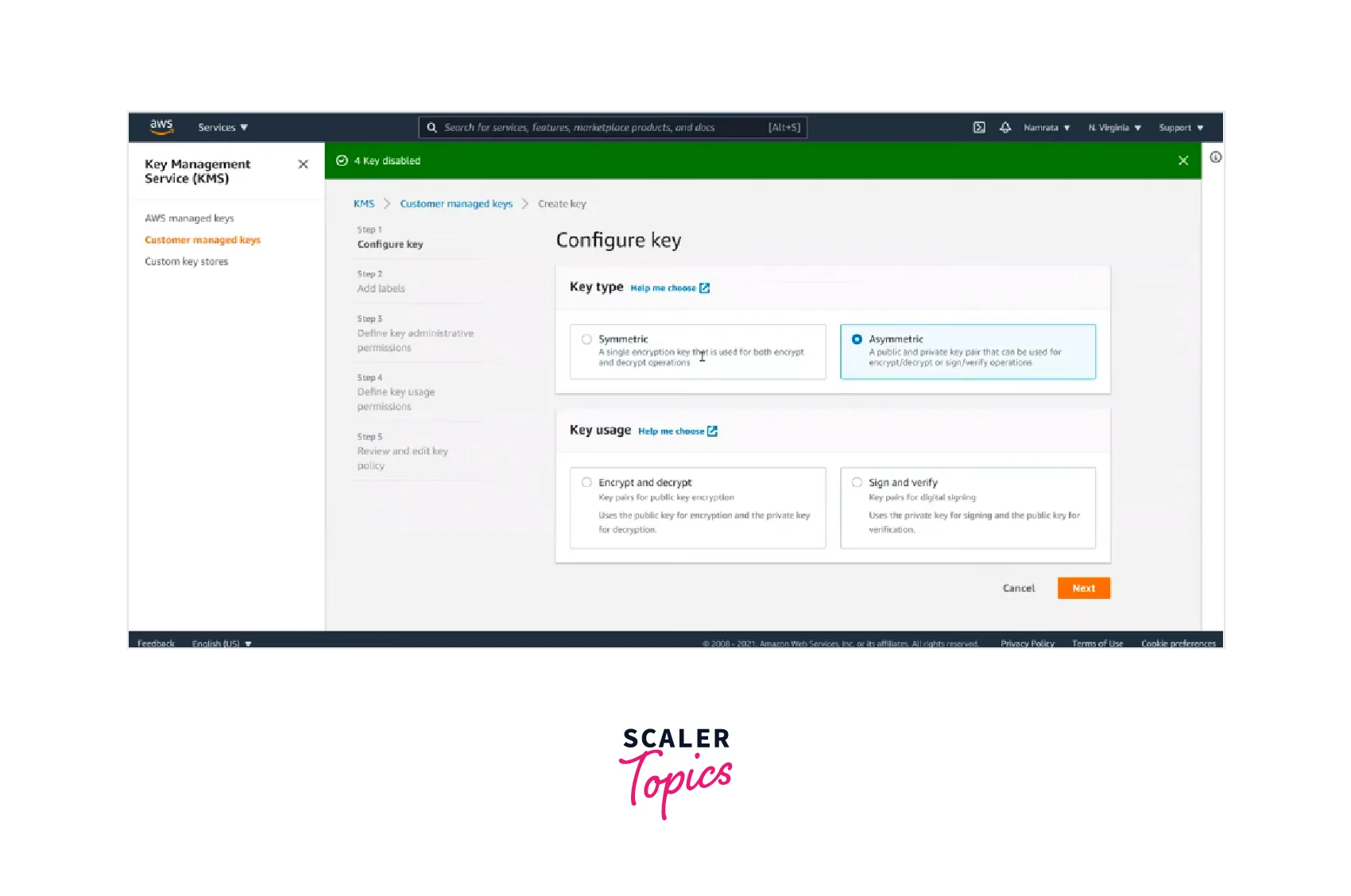
- Add labels by entering the alias name and description and can also specify the optional tags. Click on Next.
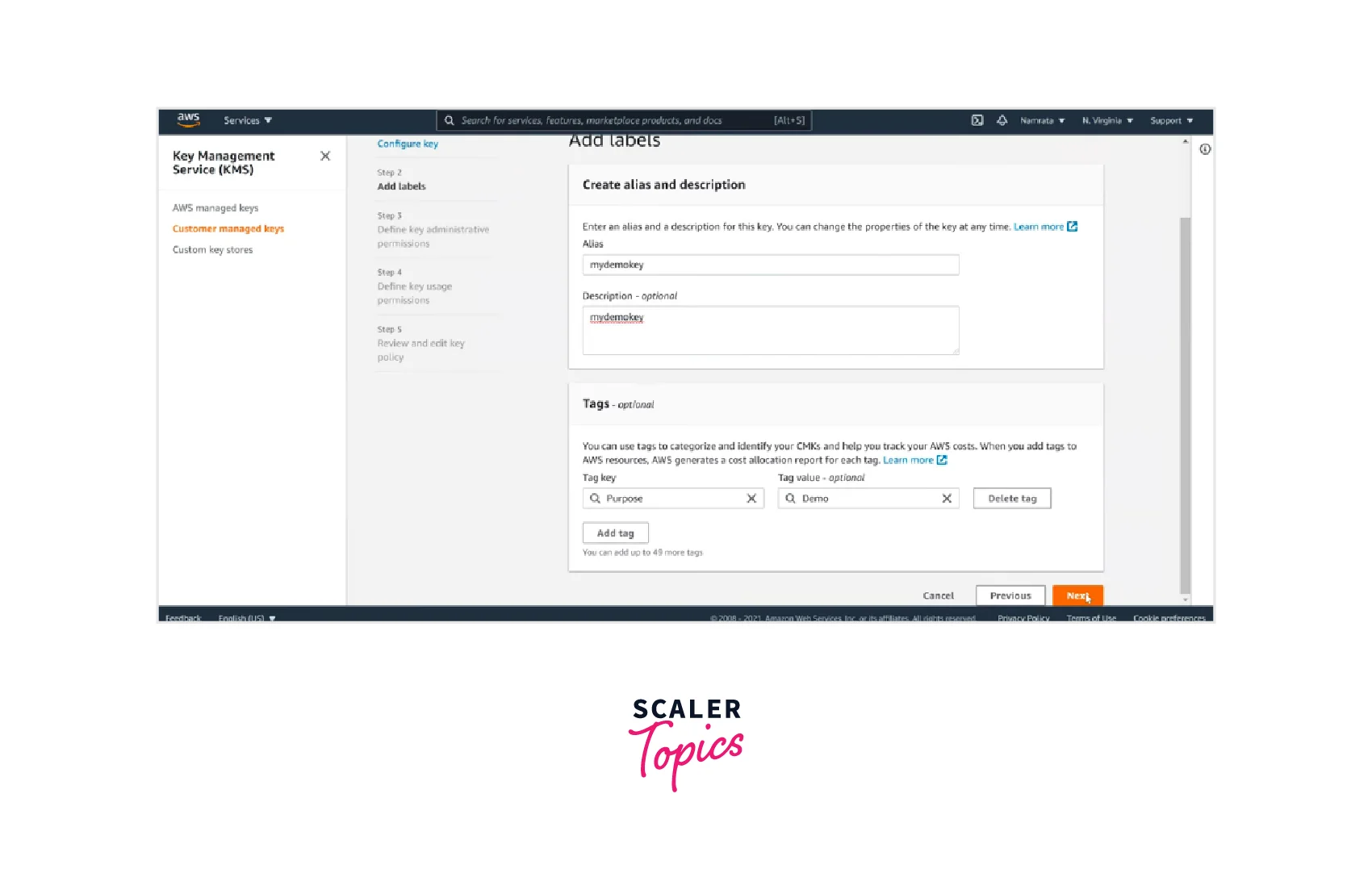
- Now define the key administrative permissions from the available options and click Next.
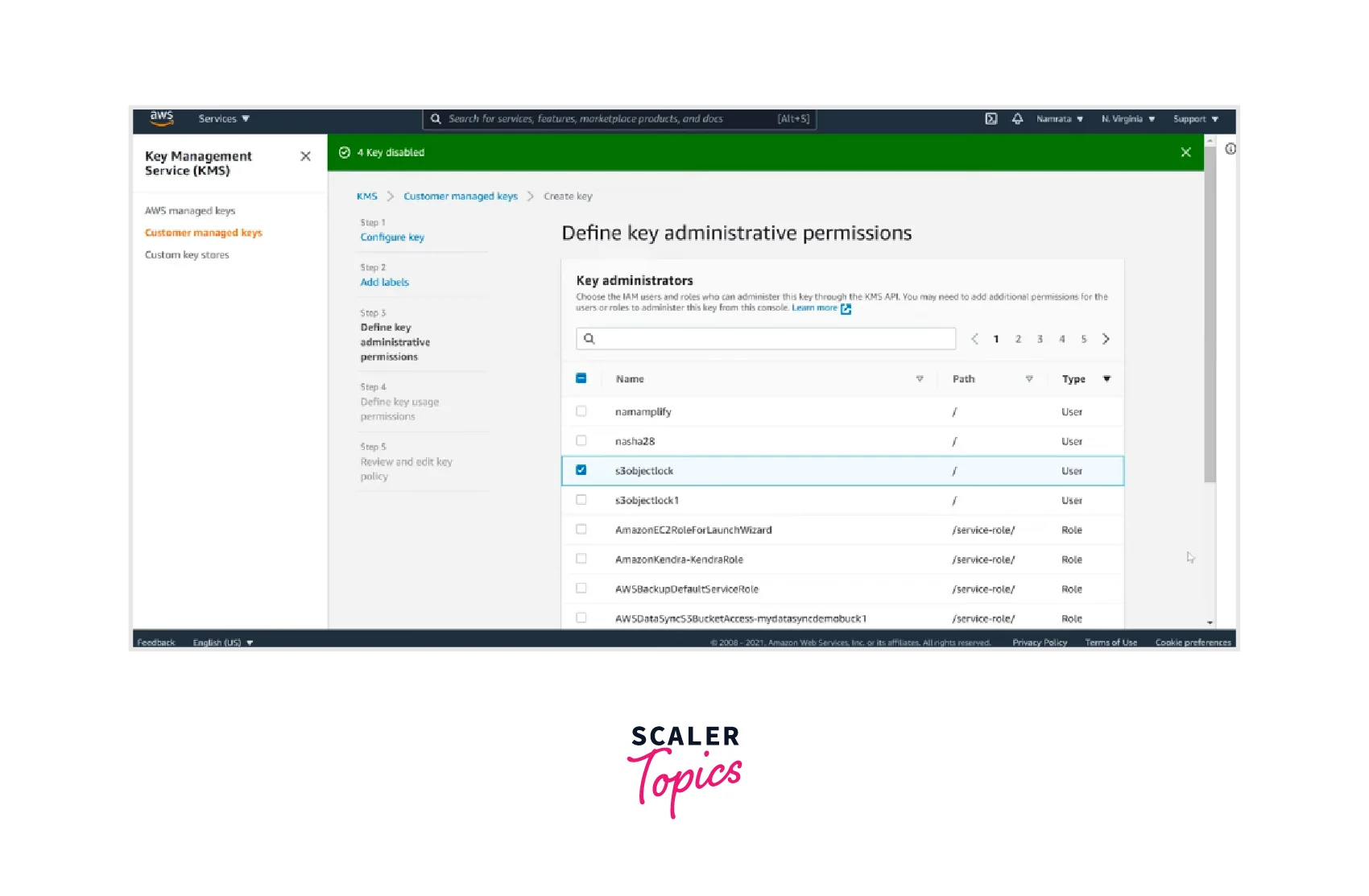
- Now define the key usage permissions from the available options and click Next.
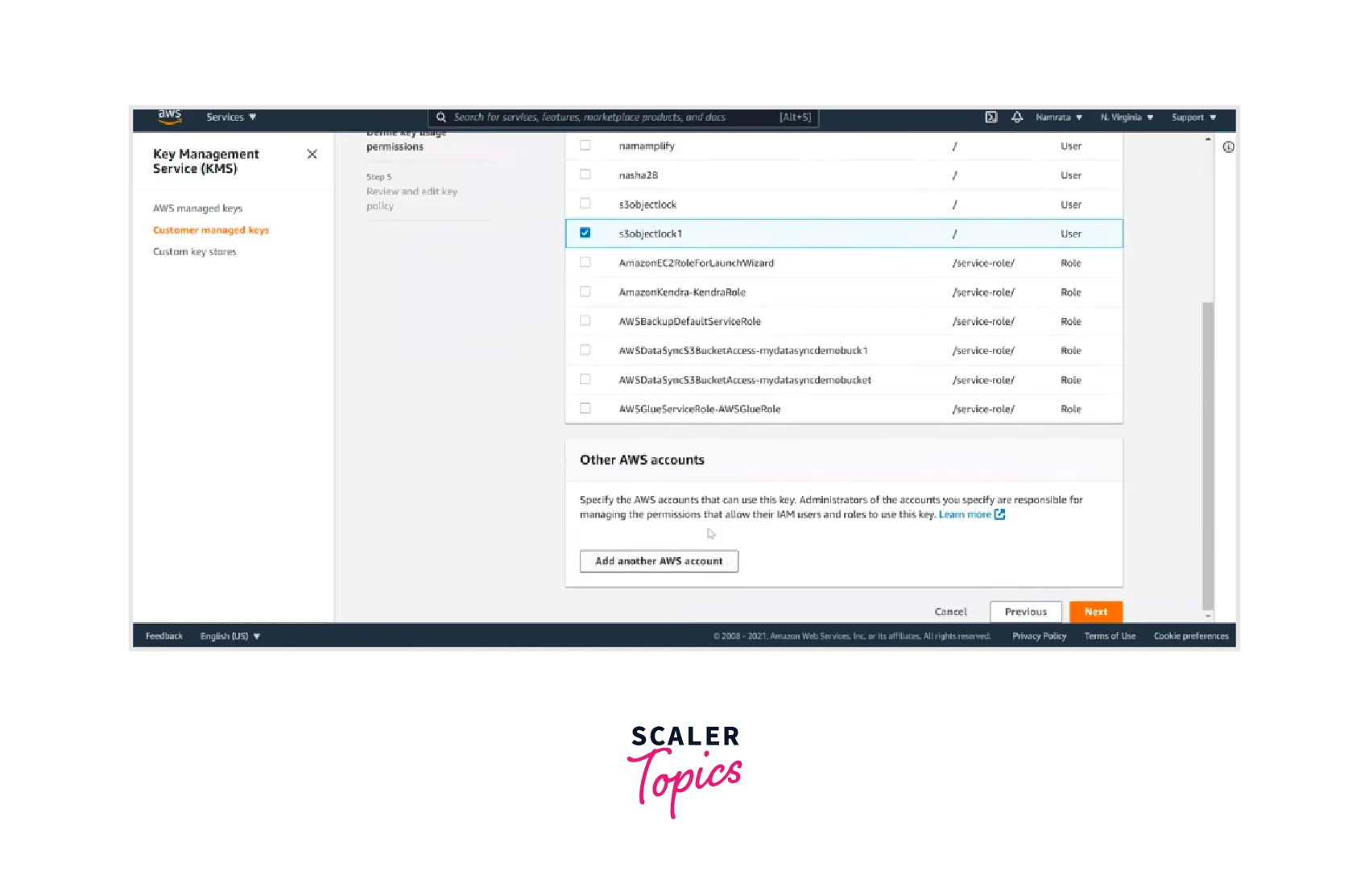
- Now, Review and edit the key policy and click on Finish.
AWS Managed Key Vs. Customer Managed Keys
| AWS Managed Key | Customer Managed Key |
|---|---|
| 1. These keys are generated by AWS services for their encrypted resource requirement. | 1. The Customer explicitly creates these keys to encrypt data. |
| 2. These keys are identified by AWS services name, e.g., AWS/SQS, AWS/DynamoDB, AWS/S3, etc. | 2. Customer-managed keys can be given any alias name and related description. |
| 3. Customers do not have direct control over the AWS-managed keys. | 3. Customers have complete direct control over these keys. |
| 4. These keys can't be deleted once created. | 4. The Customer can remove, activate (or) disable these keys. |
| 5. These keys are automatically rotated every three years. | 5. These keys are automatically or manually rotated once a year. |
| 6. AWS manages all related policies for the Customer. | 6. Each key Customer defines the access control and usage policy, and grants permissions for their usage. |
Conclusion
-
AWS Key Management Service (KMS) provides centralized management of the cryptographic keys required to secure data.
-
AWS KMS provides two types of keys: AWS Managed and Customer Managed Keys.
-
AWS KMS manages both Client-Side Encryption and Server-Side Encryption for implementing Encryption at rest.
-
Customers are charged per request when they use (or) manage keys beyond the free tier.
-
AWS KMS connects with other AWS services to encrypt data in transit or to enable signing and verification using an AWS KMS key.
-
AWS CloudTrail and KMS are connected to record all API calls which allows users to control risk, adhere to compliance standards, and forensic analysis with API request logging.
