AWS Nitro System
Overview
The next generation of EC2 instances is built on the AWS Nitro System, which helps AWS to innovate more quickly, further lower prices for customers, and provide extra features like better security and additional instance kinds. The infrastructure for virtualization has been fundamentally reimagined by AWS. In the past, hypervisors were used to virtualize the CPU, storage, and networking while safeguarding the actual hardware and BIOS and offering a wide range of management tools.
Introduction to AWS Nitro
What is AWS Nitro Enclaves and How Does It Work?
-
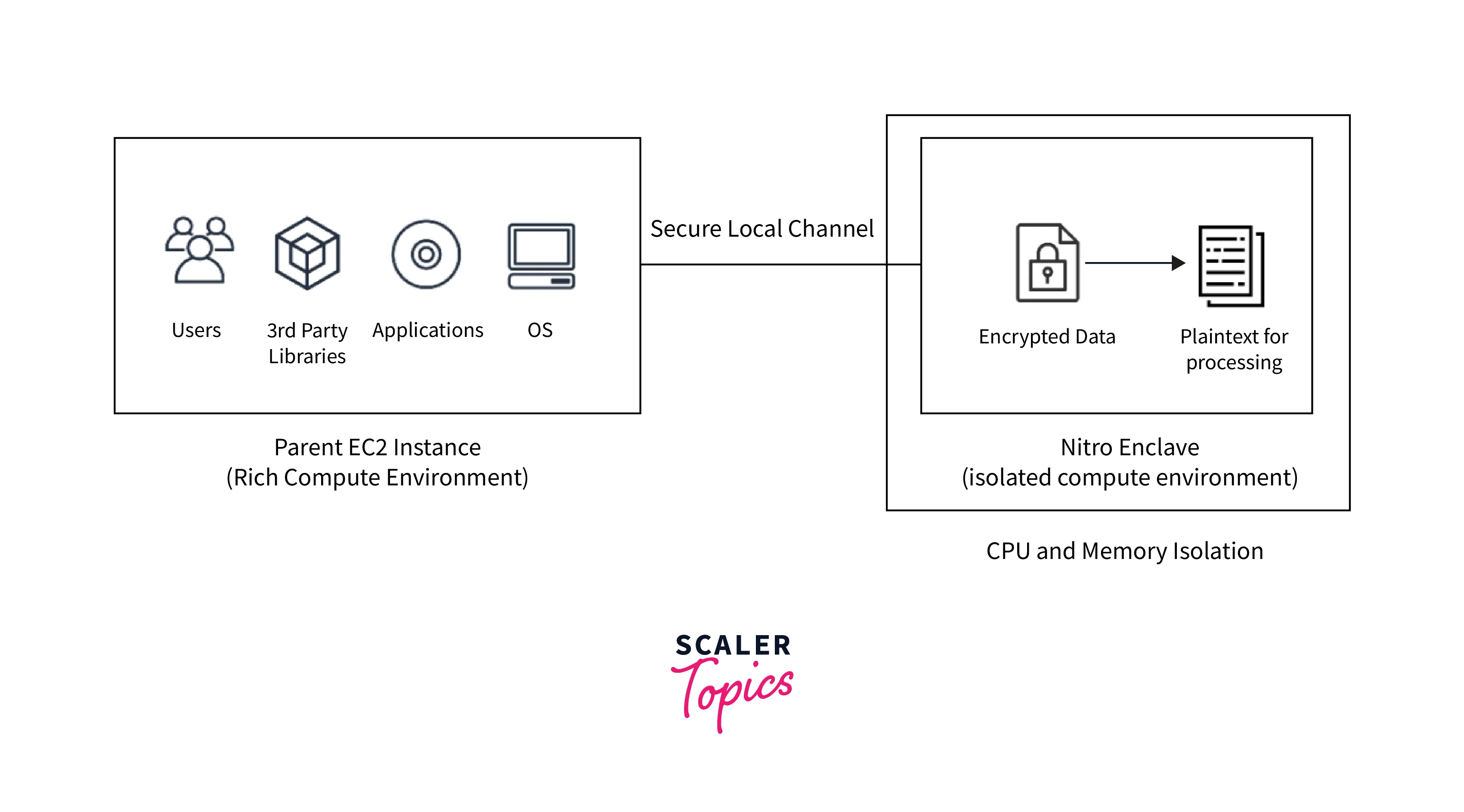
AWS Nitro Enclaves is a feature of Amazon EC2 that allows you to construct isolated execution environments, known as enclaves, using Amazon EC2 instances. Enclaves are virtual computers that are isolated, hardened, and severely limited.
-
They only offer secure local socket communication with their parent instance. They lack permanent storage, interactive access, and external networking capabilities.
-
Users cannot SSH into an enclave, and the data and programs inside the enclave cannot be accessible by the parent instance's processes, apps, or users (root or admin).
-
Nitro Enclaves also has an attestation capability, which allows you to confirm the identification of an enclave and guarantee that only permitted code is executed inside of it.
-
Nitro Enclaves is connected with AWS Key Management Service, which offers built-in attestation support and allows you to prepare and secure sensitive information for execution inside enclaves. Nitro Enclaves can be used in conjunction with the other key management systems.
Concepts
Enclave
Enclaves are virtual machines that have their kernel, memory, and CPUs. It is formed by dividing memory and virtual CPUs from the AWS Nitro-based parent instance. There is no external network access and also no persistent storage in an enclave. The separated vCPUs and memory of the enclave cannot be accessible by the parent instance's process, apps, kernel, or users.
Enclave Identification
AWS enclave IDs are unique identifiers. It contains the parent instance ID as well as a unique identification for each enclave established by the instance. An enclave generated by a parent instance with the ID f-4535567890abcdef0, for example, may have the enclave ID f-4535567890abcdef0-enc9876543210fghih.
Parent Instance
The Amazon EC2 instance that is utilized to assign CPU cores and storage to the enclaves is known as the parent instance. The enclave receives the resources for the length of its existence. The only instance that really can interact through its enclave is the parent instance.
Image File Enclave
When an enclave is launched, an Enclaves Image File (.eif) contains a Linux OS, library, and any enclave programs.
AWS Nitro Enclaves Command Line Interface (CLI)
The AWS Nitro CLI is used for creating, managing, and terminating enclaves. On the parent instance, the Nitro CLI should be deployed and utilized.
AWS Nitro Enclaves Software Development Kit
It is an open-source framework that can be used to create enclave apps or to upgrade existing ones to operate in an enclave. Additionally, the SDKs interface with AWS KMS and have built-in functionality for cryptographic attestation as well as other cryptographic processes.
Cryptographic Certification
The process by which an enclave proves its identity and builds confidence with an external service is known as cryptographic attestation. The elements in an enclave's attest documentation can be utilized as a requirement for an external party's permission decision.
Attestation Report
The Nitro Hypervisor creates and signs an attestation document. It comprises enclave information such as PCRs, a cryptographic sequence number, and other data that you can create. It could be used by any external system to validate an enclave's identity and build confidence.
Configuration Registers for Platforms
PCR is the enclave-specific cryptographic measure. Some PCRs have generated automatically when an enclave is formed and can be used to ensure that no modifications have already been introduced to the enclaves since it has been formed. You may also construct extra PCRs manually to guarantee that the enclave is operating on the instance that you intend it to operate on.
KMS Proxy
An enclave uses the KMS proxy to connect to AWS KMS via the parent instance's architecture. The proxy is included in Nitro CLI and executes on the parent instances. If you utilize AWS KMS as the key management service and use the Nitro Enclaves SDK to conduct AWS KMS operations the proxy is necessary.
The Vsock Socket
A parent instance and an enclave can communicate locally using a channel called a vsock. When interacting with outside services, an enclave can only do so over this communication channel. A context identifier (CID), which you can provide when starting an enclave, determines the vsock address of an enclave. The parent instance always employs CID 3.
Vsock uses POSIX socket APIs such as join, listening, and accept when running on Linux. The Winsock2 API is the default Windows sockets API used by the Vsock on Windows.
Key Features of AWS Nitro
-
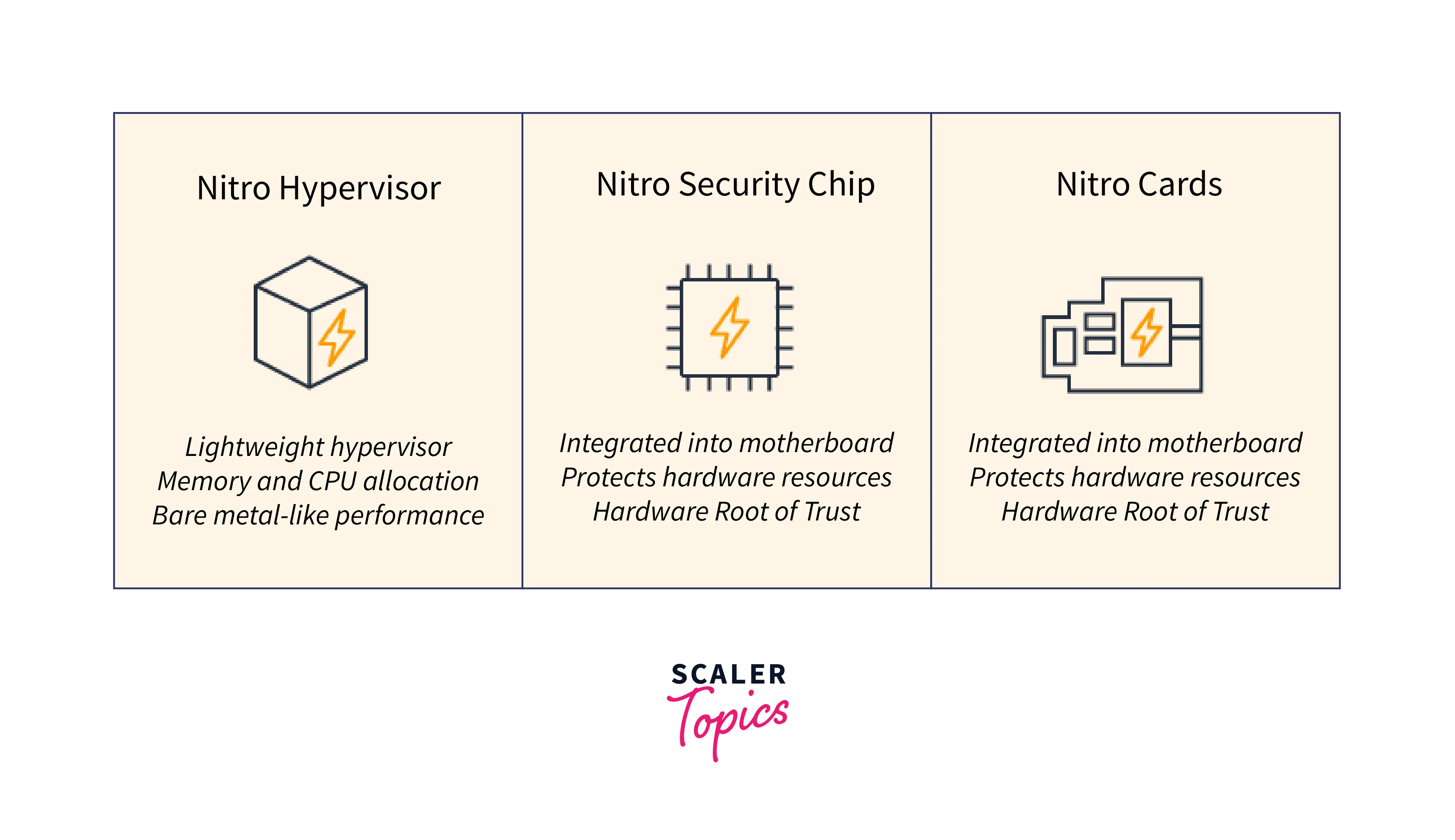
AWS Nitro Cards: A set of cards called the Nitro Cards offloads and speeds IO for various operations, thereby boosting system performance. The Nitro Card for VPC, the Nitro Card for EBS, the Nitro Card for Instance Storage, the Nitro Card Controller, and the Nitro Security Chip are important cards.
-
Nitro Security Chip: Due to the virtualization and security operations being offloaded to specialized hardware and software, the Nitro Security Chip allows the most secure cloud platform with the smallest attack surface. The danger of human mistake and manipulation is further eliminated by a closed-down security paradigm that forbids any administrative access, even that of Amazon workers.
-
AWS Nitro Hypervisor: Performance from the Nitro Hypervisor is the same as that of bare metal and it is a lightweight hypervisor that controls memory and CPU allocation.
-
Nitro Enclaves on AWS: AWS Nitro Enclaves lets users build isolated computing environments within their Amazon EC2 instances to further protect and safely manage sensitive information including PII, medical, banking, and IP rights information. Nitro Enclaves employ the very same Nitro Hypervisor functionality as EC2 instances to enable CPU and memory separation.
- NitroTPM: NitroTPM is a secure and compliant feature that allows customers to employ TPM-dependent apps and operating system features in the EC2 instances. It adheres to the TPM 2.0 standard, making it simple to move existing on-premises applications that rely on TPM functionality to EC2. NitroTPM uses the AWS Nitro System to offer a safe cryptographic offload, allowing EC2 instances to produce, store, and utilize keys despite getting access to identical keys. NitroTPM may also give cryptographic verification of the integrity of your instances using TPM attestation protocols.
AWS Nitro Use Cases
-
Keeping Private Keys Safe: Customers may now isolate and utilize private keys (e.g., SSL/TLS) in an enclave while keeping those keys hidden from users, apps, and libraries on the parent instance. Usually, these private keys are saved in plain text on the EC2 instance.
-
AWS ACM for Nitro Enclaves: AWS ACM for Nitro Enclaves is a program that enables the usage of public and personal SSL/TLS certifications with web servers and applications operating on EC2 instances on Amazon using AWS Nitro Enclaves.
-
Tokenization:: Tokenization is the process of converting extremely sensitive data, including credit card information or medical information, into a token. Customers can execute the application that performs this conversion within an enclave using Nitro Enclaves. Data that has been encrypted can be transferred to the enclaves, in which it is unencrypted and processed. Throughout this procedure, the parent AWS EC2 instances will be unable to see or retrieve the sensitive data.
-
Computation by Many Parties: Customers may build up multi-party computation using Nitro Enclaves' cryptographic attestation feature, where numerous entities can participate and analyze sensitive information without having to reveal or exchange the actual data with each party. To ensure the separation of roles, inter computations may also be performed within the same company.
Three Parts of AWS Nitro
Nitro Cards
These cards, of which there are four types of Nitro cards, are used to conduct specialized activities on the underlying host.
We have the following:
- VPC Networking Nitro Card
- EBS Nitro Card
- Instance Storage Nitro Card
- Nitro Card Controller
Let's start the discussion with the first nitro card which is the VPC networking nitro card.
The EBS Nitro Card is required to block storage afterward. An NVMe controller was used in the development of the EBS services, allowing your virtual instances to communicate with the data-storing layer. The AWS EC2 instances communicate well with the NVMe controller via a PCIe bus, which offers fast data transfer rates and minimal latency.
This card was created and constructed specifically to manage traffic related to VPC Networking requests. It employs an Elastic Network Adapter (ENA) card to provide better networking capabilities and has driver support for all of the major operating systems supplied by AWS to assure compatibility with your instance selection.
This Nitro card is also in charge of the VPC data plane, which is the component that handles networking requests and lets your instances communicate with other instances in your VPC. As a consequence, the data plane of the VPC Nitro card handles any requests the host gets about network encapsulation, security groups, routing, and network limitation, which helps to retain the same consistent performance experience.
Nitro Security Chip
Because virtualization and security operations are offloaded to dedicated hardware and software, the Nitro Security Chip allows the most secure cloud platform with the smallest attack surface. Furthermore, a tightly controlled security architecture forbids any administrative access, even that of Amazon workers, removing the risk of human mistakes and sabotage.
Nitro Hypervisor
The Nitro Hypervisor is a lightweight hypervisor that controls memory and CPU allocation while providing performance comparable to bare metal.
Nitro Enclaves?-Getting Started
The lesson that follows will lead you through the fundamentals of using AWS Nitro Enclaves. It demonstrates how to start an enclave-enabled parent instance, create an enclave image file, check that an enclave is functioning, and terminate an enclave when it is no longer required.
The Hello Enclaves example application is used throughout the lesson.
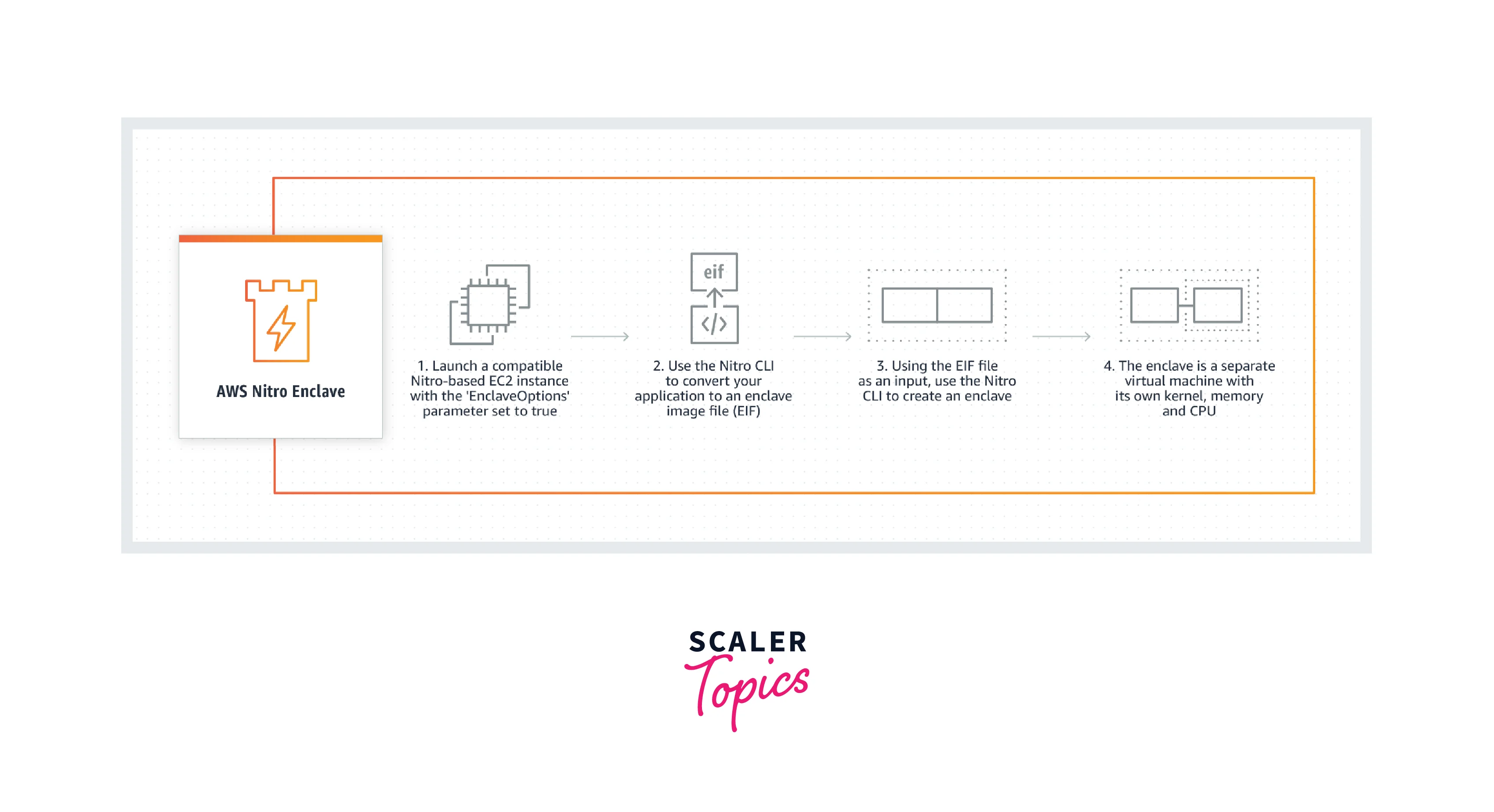
Step 1: Get the enclave-enabled parent instance ready
Launch the parent instance that will be used to construct the enclave and configure it to execute Nitro Enclaves.
To set up the Parent Instance
- Use the run-instances command to start the instance and specify the —enclave-options parameter to true. You must additionally specify a Windows or Linux AMI as well as a supported instance type.
—image-id ami id —count 1 —instance-type supported instance type —key-name your key pair —enclave-options 'Enabled=true' $ aws ec2 run instances
-
Establish a connection to the parent instance.
- Join your Linux instance
- Join your Windows instance
-
On the parent instance, install the AWS Nitro Enclaves CLI.
-
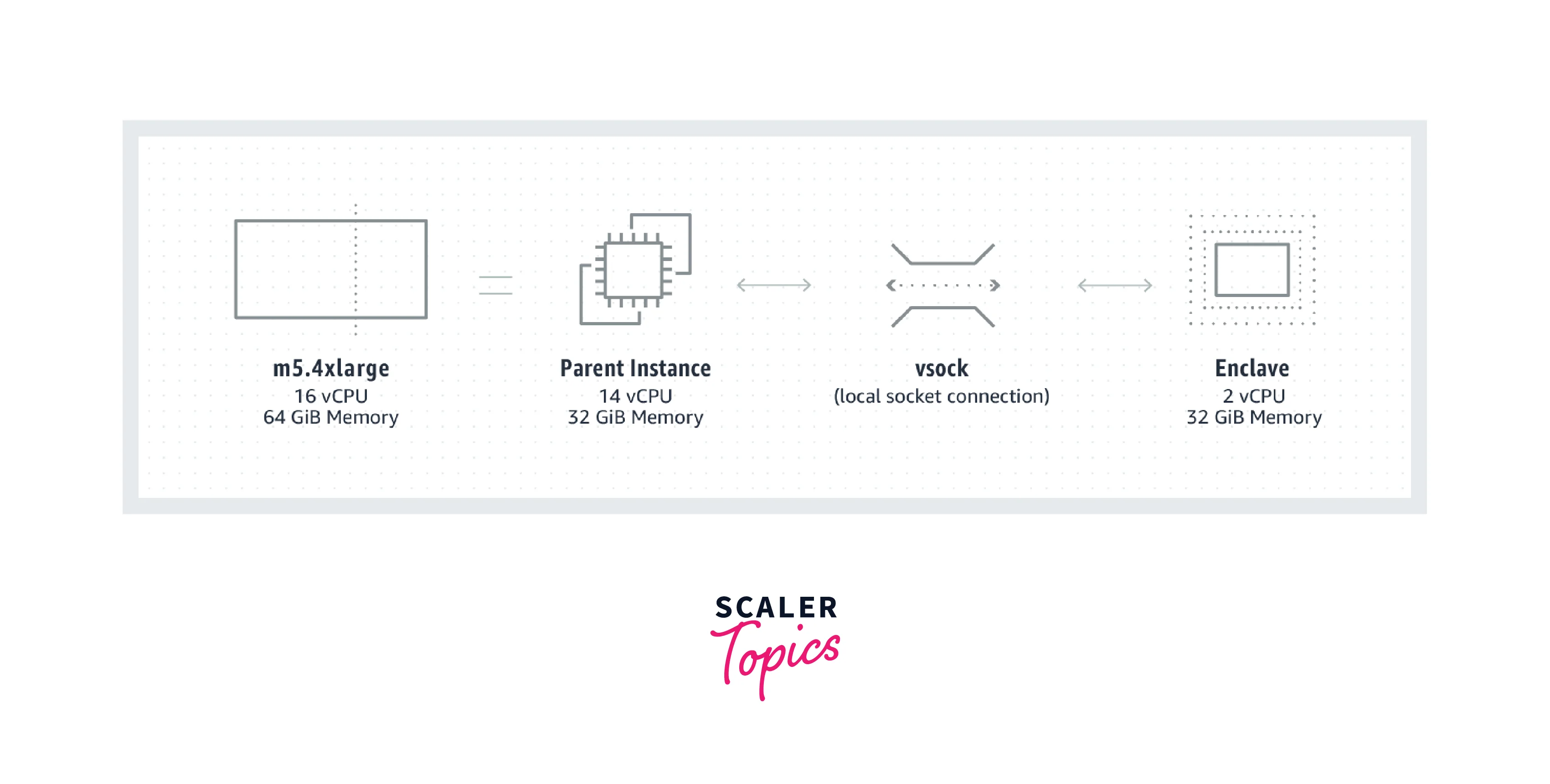
If you are using a Linux parent instance, you must allocate RAM and vCPUs ahead of time. You must preallocate at least 2 vCPUs and 512 MiB of RAM for this tutorial. See Installing the Nitro Enclaves CLI on Linux for additional details.
-
For information on installing the Nitro Enclaves CLI on Windows, see Installing the Nitro Enclaves CLI on Windows.
Create the enclave image file
- Create a Docker image based on the application. The command below creates a Docker image named hello with the tag latest.
$ docker build nitro enclaves/examples/hello -t hello
- Execute the following command to ensure that the Docker image was successfully constructed.
docker image ls
- Use the nitro-cli build-enclave command to convert the Docker image to an enclave image file. The command below creates an enclave image file called hello.eif.
$ nitro-cli build-enclave hello:latest —docker-uri hello.eif —output-file hello.eif
Output
The hello.eif enclave image file is now complete. It is worth noting that the command output contains three hashes: PCR0, PCR1, and PCR2. These hashes are measures of the enclave image and boot process that may be utilized during the attestation procedure. This lesson will not employ the attestation procedure.
Step 3: Run the enclave
You may now launch the enclave using the hello.eif enclave image file. In this lesson, you will use the hello.eif enclave image file to launch an enclave with two vCPUs and 512 MiB of RAM. In addition, you will establish the enclave in debug mode.
Use the nitro-cli run-enclave command to get started. Include the —debug-mode option and provide the vCPUs, RAM, and location to the enclave image file.
$ nitro-cli run-enclave --cpu-count 2 --memory 512 --enclave-cid 16 --eif-path hello.eif --debug-mode
Output
The enclave is currently running. In this example output, the enclave has the ID i-05f6ed443aEXAMPLE-enc1735f6ed443aEXAMPLE and the EnclaveCID value of 16. The local socket (vsock) that connects the parent instances and the enclaves acts the same as an IP address when using the EnclaveCID.
Step 4: Validate the enclave
You may have used the AWS nitro-cli describe-enclaves operation to ensure that the enclave is operational.
$ nitro-cli describe-enclaves
The command returns information about the enclave, such as the enclave ID, number of vCPUs, memory size, and condition. The enclave is in the RUNNING state in this situation.
Furthermore, because you constructed the enclave in debug mode, you may inspect the enclave's read-only console output using the nitro-cli console command.
$ nitro-cli console --enclave-id i-05f6ed443aEXAMPLE-enc1735f6ed443aEXAMPLE
Output
The Hello Enclave program is meant to display Hello from the enclave side! to the terminal every 5 seconds in this scenario.
Step 5: Terminate the enclave
You can terminate the enclave with the nitro-cli terminate-enclave command if you no longer need it.
$ nitro-cli terminate-enclave --enclave-id i-05f6ed443aEXAMPLE-enc1735f6ed443aEXAMPLE
Output
Benefits of AWS Nitro
-
Rapider Innovation: The Nitro System is a comprehensive set of building pieces that can be combined in a variety of ways, allowing us to develop and provide EC2 instance types with an ever-expanding assortment of compute, storage, memory, and networking options.
-
Improved Security: The Nitro System delivers better security by monitoring, protecting, and verifying the instance hardware and firmware in real time. The attack surface is reduced by offloading virtualization resources to specialized hardware and software.
-
Improved Performance and Cost: The Nitro System allocates nearly all of the host hardware's compute and memory resources to your instances, resulting in improved overall performance. Furthermore, specialized Nitro Cards offer high-speed networking, EBS, and I/O acceleration.
-
Previous Generation Instances are Supported: AWS Nitro System allows earlier generation EC2 instances to extend the service life beyond the average lifetime of the underlying hardware. The AWS Nitro System delivers current hardware and software components for EC2 instances, allowing clients to keep their workloads operating on the instance families that they were created on.
-
Extra Isolation and Security: Enclaves are totally isolated, fortified, and highly limited virtual computers. They do not have permanent storage, interactive access, or external networking. A secure local channel is used to communicate between your instance and your enclave.
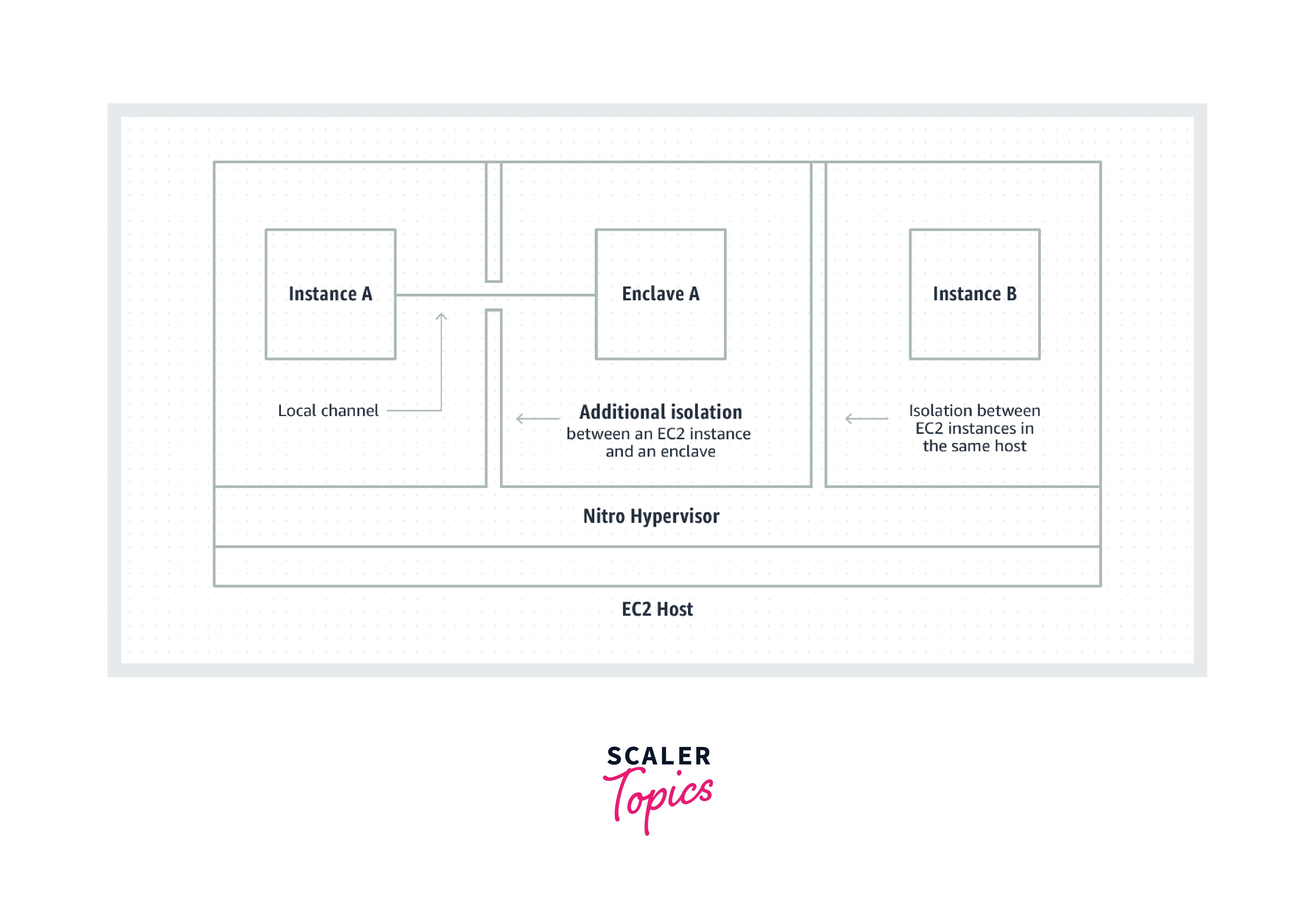
-
Isolation Using the Nitro Enclaves: Nitro Enclaves extends the Nitro Hypervisor's proven isolation to further isolate the enclave's CPU and memory from users, apps, and libraries on the parent instance. These characteristics serve to segregate the enclave and your program, reducing the attack surface area dramatically.
-
Attestation By Cryptography: Attestation allows you to validate the identity of the enclave and ensure that only authorized code is executing in your enclave. The Nitro Hypervisor performs the attestation process, which results in a signed attestation document that the enclave can use to authenticate its identity to another party or service.
-
Flexible: Nitro Enclaves are adaptable. Enclaves may be built using various CPU core and memory configurations. This assures that you have enough resources to execute the same memory or compute-intensive applications that you were previously running on your EC2 instances.
Performance Comparison: Nitro Hypervisor vs. Bare Metal
We tested four workloads: the Weather Research and Forecasting (WRF) Model (for weather forecasting), OpenFOAM (for computational fluid dynamics), GROMACS (for molecular dynamics), and High-Performance Linpack (for high performance) (synthetic matrix solver). These were chosen to demonstrate applications with various features. We execute the program on a scale of 16 instances (576 cores) in each scenario, utilizing AWS ParallelCluster and FSx for Lustre as the shared filesystem.
Weather Research and Forecasting Model (WRF):
With over 48,000 registered users from over 160 countries, WRF is one of the most frequently used numerical weather prediction (NWP) models. The CONUS 2.5km benchmark scenario was used for this investigation (version for WRF v4). This task, like other weather models, will have high I/O parts to both read initial conditions and create output. The rate of simulation is employed as a performance statistic, and it is based on the entire wall-clock time, which includes both I/O and computation time.
GROMACS:
GROMACS is a molecular dynamics (MD) simulation software for proteins, lipids, and nucleic acids. We used the benchRIB input set from the Max Planck Institute for Biophysical Chemistry for this assessment. The performance figure used in comparisons is the 'ns/day' measure generated by GROMACS at the end of a run.
OpenFOAM:
OpenFOAM is a free and open-source computational fluid dynamics software suite. We utilize a scaled-up (15 million cells) version of the 4 million cell motorcycle scenario from the standard OpenFOAM v2012 lesson set for this. The comparative performance statistic is based on the total time for all iterations and is translated to iterations per hour.
HPL (High-Performance Linpack):
HPL is a software application that uses a double-precision floating point to solve a dense linear system. It serves as the foundation for the Top 500 list, which rates the "fastest supercomputers in the world." Although this is not a finished application, it has been included for completeness. The optimized HPL implementation offered by Intel in the OpenAPI package was utilized for these runs. The GigaFLOPs provided at the end of the run are the performance metrics used for comparison.
Conclusion
-
The Nitro System handles critical network, server, security, firmware patching, and monitoring duties, freeing up the underlying server for customer use. This gives EC2 instances access to all cores; none must be allocated for storage or network I/O.
-
Over the last few years, the Nitro System has powered all EC2 Instance types. Nitro Card I/O Acceleration, Nitro Security Chip, and Nitro Hypervisor are the three key components.
-
Some server types have multiple Nitro System cards that implement the AWS Nitro System's five main features, namely Nitro Card for VPC, Nitro Card for EBS, Nitro Card, for Instance, Storage, Nitro Card Controller, and Nitro Security Chip.
-
The Nitro System also enables the usage of a very basic, lightweight hypervisor that is nearly always idle, allowing us to safely handle bare metal instance types.
