AWS Secrets Manager
Overview
AWS Secrets Manager is an AWS offering that protects the secrets needed to access our applications, services, and IT resources. It allows a customer to replace hardcoded credentials in their code with an API call to Secrets Manager to retrieve the secret programmatically. Because the secret is no longer included inside the plain text, it cannot be compromised by someone studying it.
What is AWS Secrets Manager?
The customer stated that managing secrets is very important, but there are some difficult use cases, such as an application that uses secrets but does not want to write plain text secrets in the source code, the customer wanted to rotate their secrets regularly to meet compliance needs (or) to improve security, and the customer also wanted to control who is doing what with the secrets.
When it comes to rotation, people frequently create manual (or) programmatic processes that call for them to take applications offline, update secrets, and then redeploy applications to work with these new secrets. Customers discovered that people have very limited visibility, so once they share a password over email, they do not have any way to ensure its security. While there are solutions available, they are either too complex or too expensive, especially when you consider the cost of the infrastructure and the people required to ensure that your secrets management is highly available and can scale to make any spiky load.
So to solve all these problems, AWS Secrets Manager enables the customers to rotate, manage and retrieve database credentials to meet compliance needs and improve security, API keys, and other secrets throughout their lifecycle.
The AWS Secrets Manager is designed for IT administrators who need a safe and scalable way to store and manage secrets. Secrets Manager allows security managers in charge of fulfilling regulatory and compliance standards to monitor and cycle secrets without affecting applications. Secrets from AWS Secrets Manager can be retrieved programmatically by developers who desire to replace hardcoded secrets in their apps.
AWS Secrets Manager Concepts
Before we go any further, let's take a quick look at the major concepts we'll be using later.
-
Secret: A secret is made up of secret information, secret value, and metadata. A secret value can be either a text (or) binary value. JSON text string with key/value pairs used to store several string values in a single secret.
-
Rotation: It is the procedure of renewing a secret regularly to make it more difficult to gain access to the credentials. You can set up an automatic rotation for your secrets in Secrets Manager.
-
Version: The secret manager generates new copies of the secret whenever the user rotates (or) changes the secret value, which is known as the version. AWS Secret Manager provides various labels to indicate the different versions:
- AWSCURRENT: tells about the currently active version.
- AWSPENDING: tells about upcoming version after rotation.
- AWSPREVIOUS: tells about the last version.
Features Of AWS Secrets Manager
Secure Storage: AWS provides security to secrets by using AWS Secrets Manager which uses encryption and decryption tools in AWS Key Management Services for storing the keys. Users can also use AWS Identity and Access Management (IAM), tag-based policies, and resource-based restrictions for secure storage of secrets.
Automatic secret rotation: You can set up an automatic rotation for your secrets in Secrets Manager. When Secrets Manager rotates a secret, the credentials in both the secret and the database or service are updated. Secrets Manager natively supports rotating credentials for Amazon RDS, Amazon DynamoDB, and Amazon Redshift clusters. Secrets Manager may be extended to rotate other secrets using Lambda functions.
Replication of Secrets: You can use AWS Secrets Manager to automatically duplicate secrets across various AWS Regions to fulfill your specific disaster recovery and cross-regional redundancy needs. Secrets Manager will securely build regional read replicas by reducing the need to maintain a sophisticated solution for this capability.
Programmatic Retrieval of Secrets: You can use the AWS Secrets Manager GUI, AWS SDK, AWS CLI, or AWS CloudFormation to store and retrieve secrets. To retrieve secrets, replace plain-text secrets in your apps with code that uses the Secrets Manager APIs to bring in those secrets programmatically. Secrets Manager includes code samples for calling Secrets Manager APIs, which may also be found on the Secrets Manager Resources page.
Audit and monitor of use: AWS Secrets Manager integrates with logging, monitoring, and messaging services to allow you to audit and monitor secrets. For example, after enabling AWS CloudTrail for an AWS region, the user can check AWS CloudTrail logs for secret updation information. Similarly, you can enable Amazon CloudWatch to receive notifications when secrets are inactive for an extended length of time.
Compliance: AWS Secrets Manager provides tools for handling various secrets-related workloads, for example, defense security, federal authorization, payment card data information, and other sensitive information.
Benefits
Secrets should be rotated regularly: AWS Secrets Manager assists you in meeting your security and compliance needs by allowing you to rotate secrets safely without requiring code deployments. Secrets Manager includes built-in support for Amazon RDS, Amazon Redshift, and Amazon DocumentDB and automatically rotates these database credentials on your behalf.
Fine-grained policies to manage access: Secrets Manager allows you to control secret access with fine-grained AWS Identity and Access Management (IAM) policies and resource-based policies. Users can, for example, design a policy that allows developers to obtain specific secrets only when they are utilized in the development environment.
Cost Savings: Pricing for Secrets Manager is as per usage. Secret Manager charges based on both the number of secrets maintained there and the frequency of Secrets Manager API requests. By using Secrets Manager, you can create a highly accessible secrets management service without having to make an initial investment (or) pay for ongoing infrastructure maintenance.
Centrally secure and audit secrets: Secrets Manager allows you to help safeguard secrets by encrypting them using encryption keys managed by AWS Key Management Service (AWS KMS). Centralized auditing also connects with AWS' logging and monitoring services.
Secrets replication through many areas: AWS Secrets Manager makes it simple to duplicate secrets across various AWS regions to support multi-region applications and disaster recovery situations. The user does not need to duplicate and manage secrets across different AWS regions due to the multi-region support of Secrets Manager. It allows them to easily access and read secrets wherever they are needed.
AWS Secrets Manager Pricing
AWS Secrets Manager charges users based on the number of secrets and the number of API calls made. There are no hidden charges (or) long-term commitments. You simply pay for consumption, with no expenditures associated with the infrastructure, license, or employees necessary to guarantee that your secrets are consistently and widely available.
- TRIAL PERIOD OF 30 DAYS
AWS Secrets Manager is available for free for a 30-day trial period. During the 30-day free trial, you may rotate, manage, and recover secrets. When you save your first secret, your free trial begins.
- PER MONTH PER SECRET
$0.40 per month per secret A replica secret is considered a separate secret and will be charged $0.40 per replica each month. The charge is prorated for secrets held for less than a month (based on the number of hours.)
- PER TEN THOUSAND API CALLS $0.05 for every 10,000 API requests.
What Secrets Can I Manage In AWS Secrets Manager?
AWS Secrets Manager allows users to save a JSON document that lets them handle any text blurb of 64 KB or less. AWS Secrets Manager can manage these secrets:
- AWS credentials – AWS IAM AWS user's security-related credentials are stored in AWS Identity and Access Management.
- Encryption keys – AWS KMS Encrypting keys are generally stored in the AWS Key Management service.
- SSH keys – Amazon EC2 Instance Connect Secure Shell (SSH) keys are access credentials that are used in SSH protocol and stored in AWS Elastic Compute Cloud instance connect.
- Private keys and certificates – AWS Certificate Manager Private keys and Certificates are stored in AWS Certificate Manager.
- Database credentials – Secrets Manager Various database credentials are stored in AWS Secrets Manager.
- Application credentials – Secrets Manager Application-related credentials are also stored in AWS Secrets Manager.
- OAuth tokens – Secrets Manager OAuth tokens which are used to make requests to the resource server are also stored in AWS Secrets Manager.
- Application Programming Interface (API) keys – Secrets Manager Application Programming Interface (API) keys are also stored in AWS Secret Manager.
What Secrets Can I Rotate With AWS Secrets Manager?
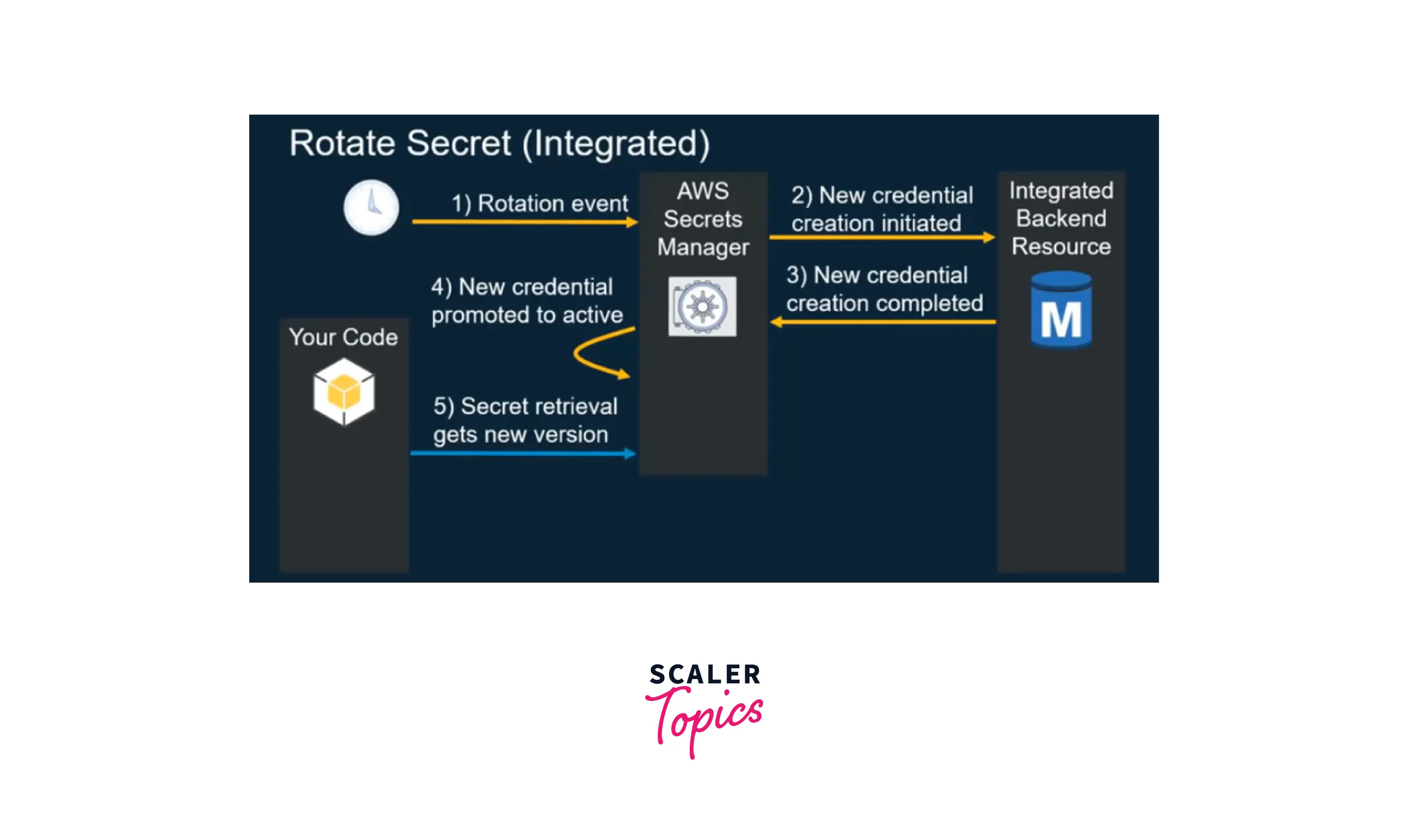
Credentials for AWS RDS, Amazon DynamoDB, and AWS Redshift may be rotated natively. Secrets Manager can be extended to rotate other secrets, such as Oracle database credentials hosted on EC2 (or) OAuth refresh tokens by changing AWS Lambda functions accessible in the Secrets Manager documentation. The below image demonstrates how rotation works in AWS Secret Manager:
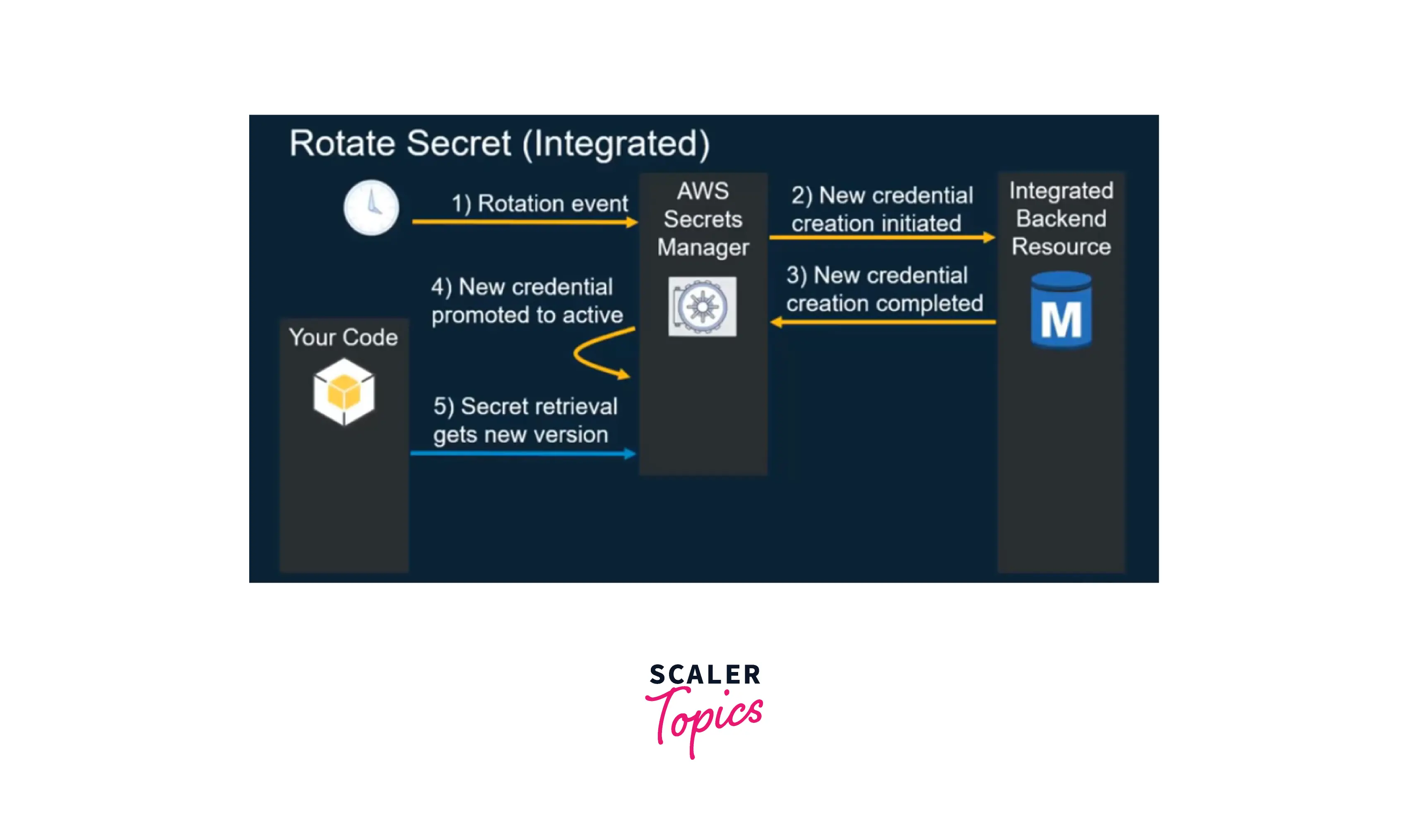
When you configure the secrets manager to rotate a secret on your behalf, the secret manager creates a lambda function in the same VPC as the resource and then uses the lambda function to trigger rotations. So when it comes time to execute the rotation, the lambda function triggers the secrets manager to create a new secret, store this new secret within the resource, and update the value that is stored within the secrets manager. As a result, when an application attempts to retrieve the secrets manager, it will get the updated value throughout the entire process. Secrets managers use labels to manage the various versions of the secrets. This enables the secrets manager to know which version is active and should be passed along to applications. Applications do not have to worry about managing the multiple versions of the secrets, they always get the active version of the secrets which they can use to connect to the resource.
How Can My Application Use These Secrets?
To start, create an AWS Identity and Access Management (IAM) policy that grants your app access to specific secrets. Then, in the source code of the application, replace plain-text secrets with code that allows you to obtain these secrets programmatically using the Secrets Manager APIs.
In this example, the application needs access to a database and requires database credentials from the secret manager to make this access happen. If the application is running on an EC2 instance, you can use the IAM role to provide access to secrets from the secrets manager. The application authenticates and authorizes access by presenting the AWS credentials to the secret manager. The secret manager decrypts the secrets and sends them securely to your application. Your application can then use this secret and if you have configured the secrets manager to rotate the secrets automatically secrets, the secrets manager will execute this rotation transparently.
Get Started With AWS Secrets Manager
Follow these steps to secure your secrets and credentials using AWS Secrets Manager:
- Find out what your secrets are and where they are used in your apps.
- Navigate to the Secrets Manager interface after signing in to the AWS Management Console using your AWS credentials.
- Upload the secrets using the Secrets Manager console.
- You can also develop a script to upload many secrets at the same time.
- If additional users (or) apps require access to the secret, create an IAM policy to provide access.
- Update all the applications which use these secrets to obtain secrets through Secrets Manager.
- If the secret is used, select automatic rotation using the AWS Secrets Manager console.
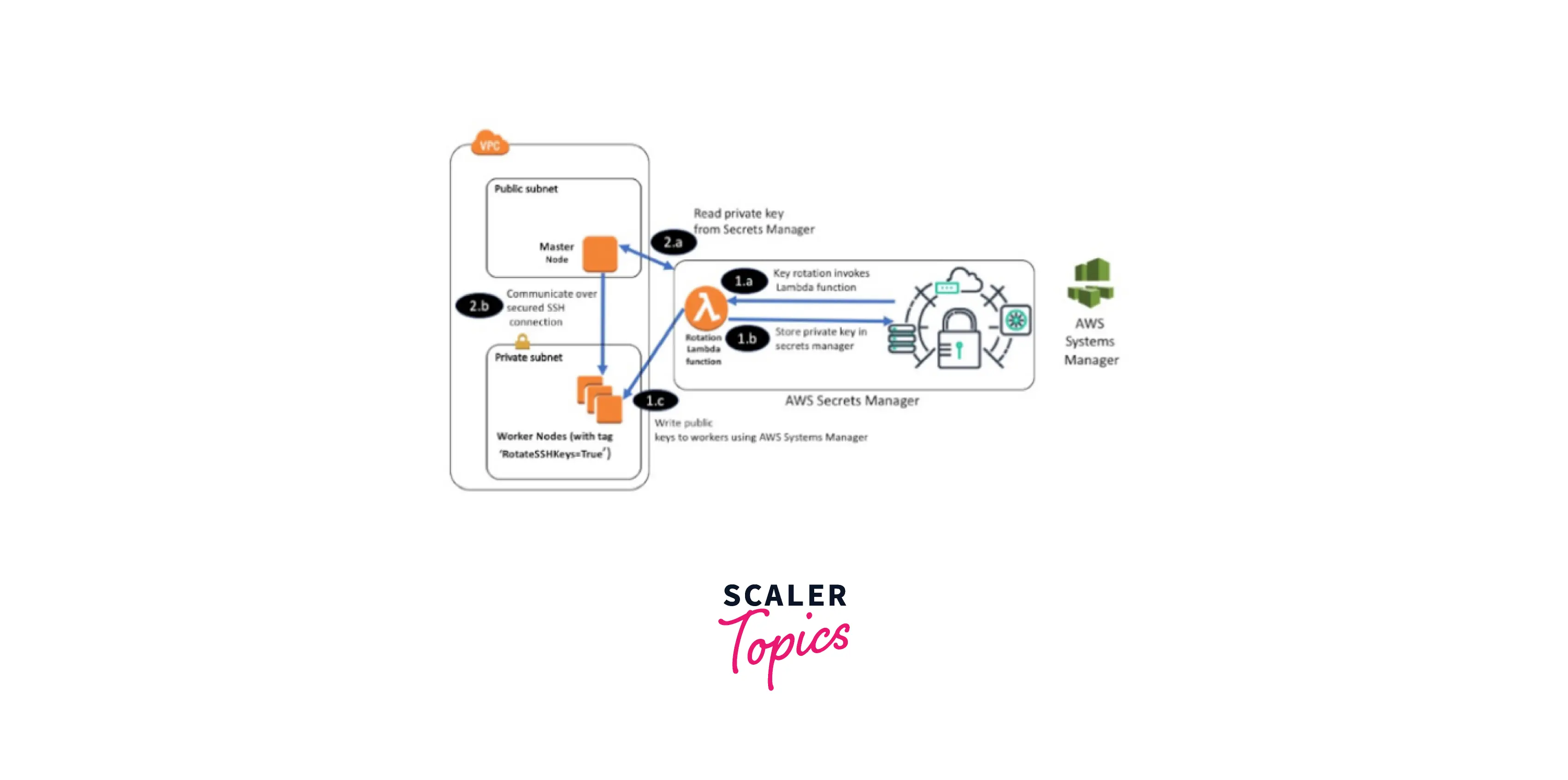
The following steps can be understood using this flow diagram:
In What Regions is AWS Secrets Manager Available?
AWS Secrets Manager provides its services in the following regions namely:
| us-east-2 | us-east-1 | us-west-1 | us-west-2 | me-central-1 |
| ap-east-1 | ap-southeast-3 | ap-south-1 | ap-northeast-3 | ap-northeast-2 |
| ap-southeast-2 | ap-northeast-1 | ca-central-1 | eu-central-1 | eu-west-1 |
| eu-west-3 | eu-north-1 | me-south-1 | sa-east-1 | us-gov-east-1 |
| eu-south-1 | af-south-1 | ap_southeast-1 | eu-west-2 | us-gov-west-1 |
As the AWS regions list is updated daily so these are regions that are currently supporting AWS Secrets Manager.
Conclusion
-
AWS Secrets Manager allows an application to replace plain text secrets in the source code with an API call to Secrets Manager to retrieve the secret programmatically.
-
AWS Secrets Manager maintains unique secrets per region, per environment per account with multi-region replication support that increases application availability and disaster recovery.
-
Users should rotate secrets regularly, which is super easy with just a few clicks.
-
AWS Secrets Manager provides fine-grained IAM policies, tag-based access control, and resource-based policies to control permission to secrets.
-
AWS Secrets Manager does not charge the user for versioning of secret (or) for using encryption keys.
-
AWS Secrets Manager creates a highly accessible secrets management service without having to make an initial investment (or) pay for ongoing infrastructure maintenance. Pricing for AWS Secrets Manager is as per the usage of the customers.
