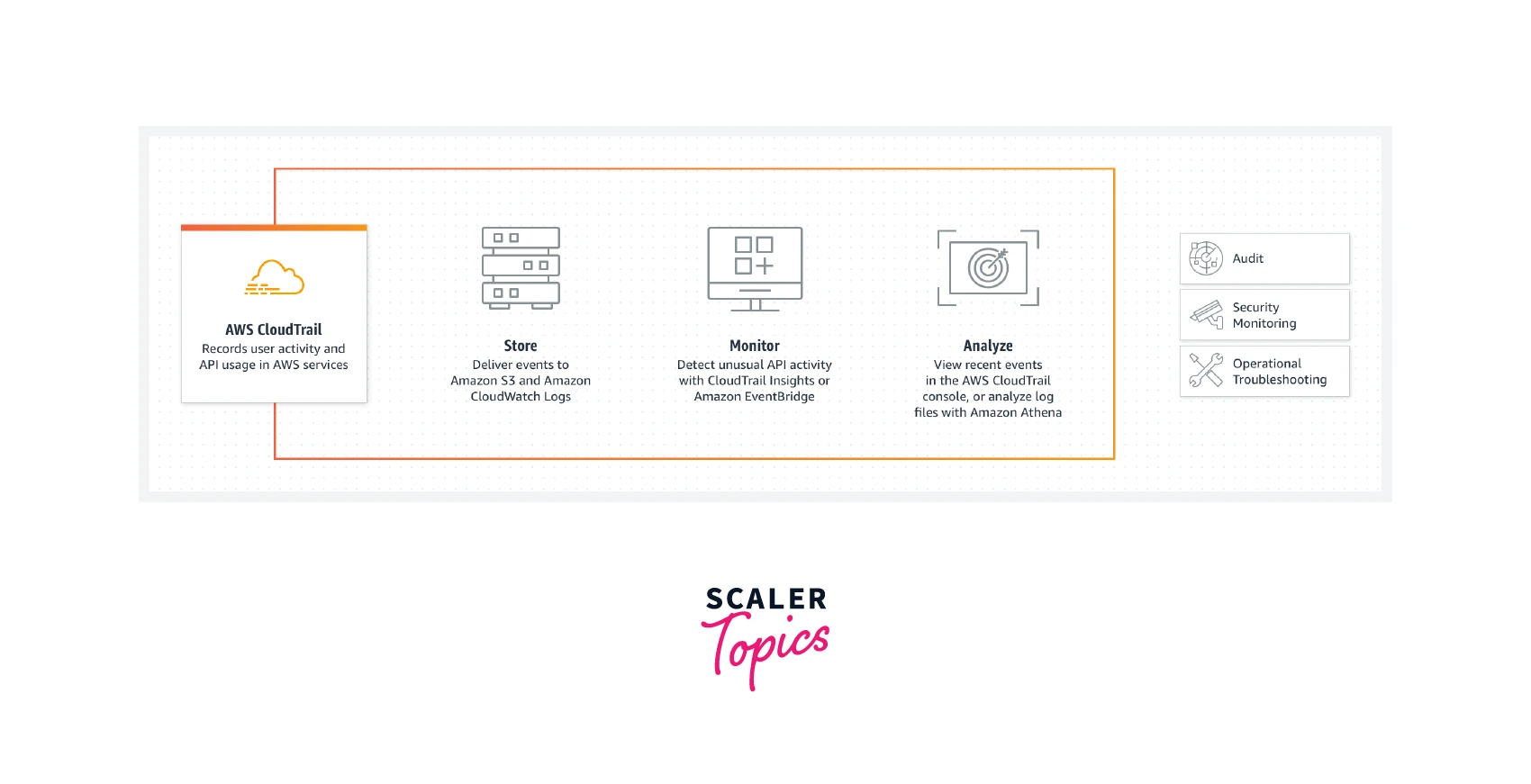
AWS CloudTrail
Overview
What motivates your desire to operate one of the services included in the AWS Console's Management Tools category? CloudTrail in AWS aids your AWS account's governance, compliance, and operational audits. Events in AWS CloudTrail are entries made by a user, role, or AWS service. The AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs are just a few examples of the events that may occur. A CloudTrail event gets created each time something happens in your AWS account.
What is AWS CloudTrail and Why do We Need it?
Let's use an example to comprehend the concept of CloudTrail. Imagine you are a detective who has been given a case to investigate. You start following the "trails" of all the suspects to discover the offender. CloudTrail similarly performs its work in the world of AWS.
The primary purpose of the service, CloudTrail, is to keep track of all AWS API queries that are performed. These API queries may come from programmatic requests performed by a user using an SDK, the AWS command line interface, the AWS administration panel, or even another AWS service.
For instance, when auto-scaling launches or shuts down an instance, an API request is automatically sent. CloudTrail has a complete log of all these API queries.
When an API call is made, AWS CloudTrail records the request as an event, logs the event in a file, and then stores the log file on S3. A new event is represented by each API call in the log file. With each incident, CloudTrail also logs and transmits additional identifying details. For instance, the caller's name, the moment the request was made, and the originating IP address.
AWS CloudTrail Features
Amazon CloudTrail includes a lot of capabilities you would expect from a monitoring and governance solution. These features consist of:
-
Since AWS CloudTrail is "Always On," you can access data going back 90 days.
-
Event history will let you view all modifications.
-
multi-regional arrangement.
-
Verification of log file integrity and encryption.
-
CloudTrail Insights, management events, and data events.
Benefits
-
Security Troubleshooting and Analysis By periodically recording an extensive history of modifications made to the AWS account, AWS CloudTrail will enable the user to identify and troubleshoot security and operational issues.
-
Simplified Compliance By automatically capturing and keeping event logs for activities created periodically in the AWS account, AWS CloudTrail can change the compliance audits. Searching through the log data is made simple by integration with Amazon CloudWatch Logs. Additionally, it aids in identifying occurrences that are out of compliance and speeds up incident investigations and auditor request responses.
-
Visibility of resource and user activities By capturing AWS Management Console events and API requests, Amazon CloudTrail improves insight into user and resource activity.
-
Automation of security The user can utilize Amazon CloudTrail to automatically react to the account for the protection of Amazon resources. The user will be able to specific processes that run once the events that might result in security vulnerabilities are discovered, thanks to the integration of Amazon CloudWatch Events.
Use cases
- Auditing work: Monitor, archive, and check the integrity of occurrences. Easily create audit reports that are needed for compliance with both internal and external regulations.
- Keep track of security incidents: Utilize the Who, What, and When details in CloudTrail Events to spot unwanted access. Respond with automated processes and rules-based EventBridge notifications.
- Investigate operational problems: Utilize machine learning (ML) models to continuously monitor API usage history to notice unexpected behavior in your AWS accounts and identify its fundamental cause.
How does CloudTrail Work?
- Account activity occurs, providing the user with fundamental knowledge about Cloudtrail. The action is seen by and saved as a Cloudtrail event by AWS Cloudtrail.
- With the aid of Cloudtrail history, the user may examine and download Cloudtrail activities.
- The user can configure Cloudtrail and provide a storage Amazon S3 bucket.
- The Cloudtrail log is provided to both the CloudWatch logs and the CloudWatch events in addition to the Amazon S3 bucket.
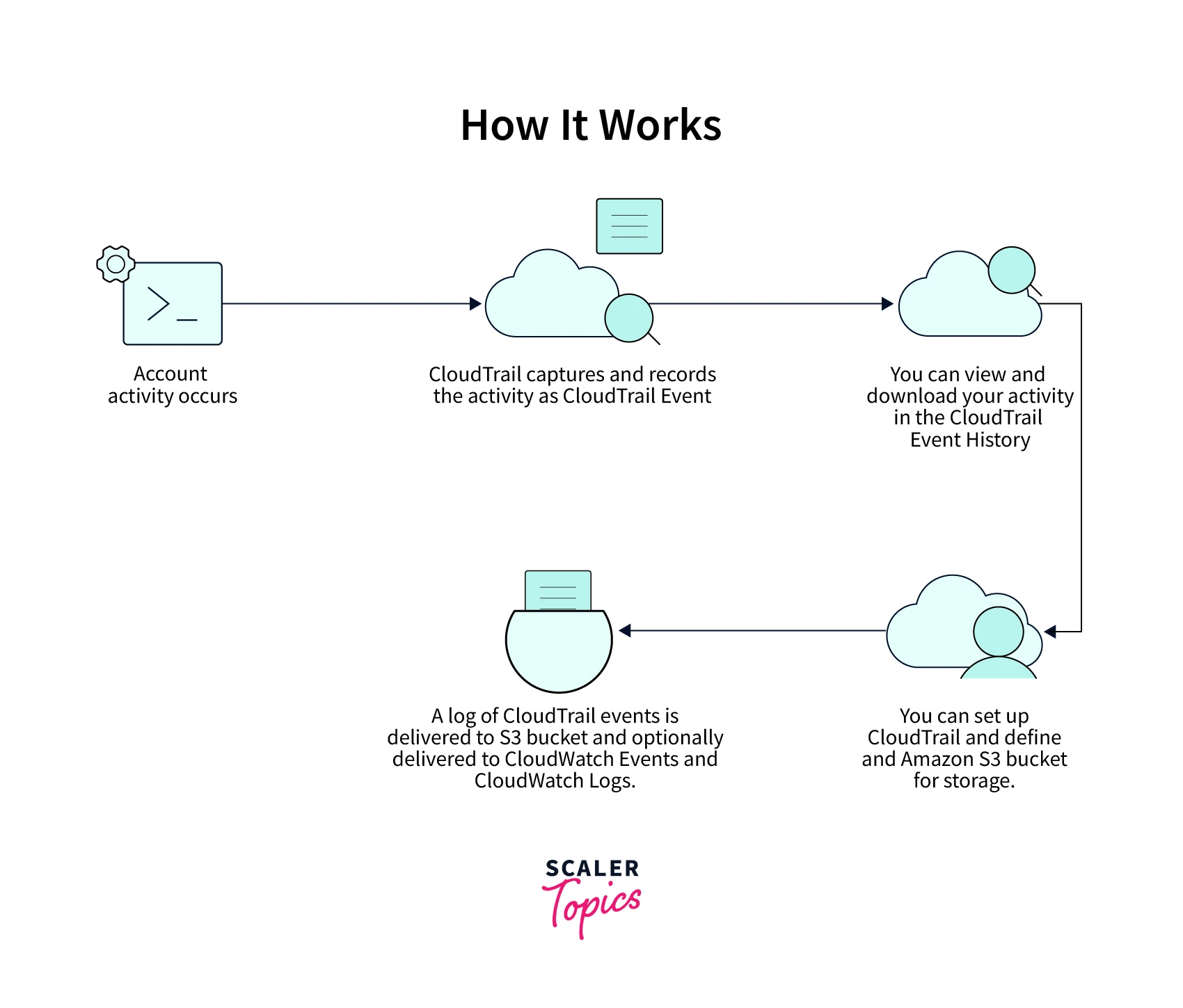
CloudTrail Workflow
View the AWS Account Event History
The CloudTrail console or the AWS CLI may be used to examine and search through the previous 90 days' worth of events that CloudTrail has logged.
Download Events
For your AWS account, you may download a CSV or JSON file containing up to the previous 90 days' worth of CloudTrail events.
Build a Trail
CloudTrail may send log files to your Amazon S3 bucket by using a trail. When you make a trail in the console, it automatically applies to every region. Events from every region in the AWS partition are logged by the trail, which then sends the log files to the S3 bucket you choose.
Create and Subscribe to an Amazon SNS Topic
To get notifications when log files are delivered to your bucket, subscribe to a subject. You may get notifications from Amazon SNS in a variety of ways, including programmatically using Amazon Simple Queue Service.
View Your Log Files
Log files may be retrieved via Amazon S3.
Control User Permissions
To control which users may create, configure, or remove trails, start and stop recording, and access buckets that contain log files, utilize AWS Identity and Access Management (IAM).
Observe Occurrences with CloudWatch Logs
It's possible to set up your trail so that it sends events to CloudWatch Logs. Then, you can utilize CloudWatch Logs to keep an eye on certain API requests and account events.
Data events and log management
Set up your trails to record all management and data events, read-only events, or write-only events.
CloudTrail Concepts
Events
The documentation of a transaction in an AWS account. This activity may involve a move made by a user, role, or service that CloudTrail can watch.
Types
- Management events You are logged in by default. Management events, also known as control plane operations, give information on management operations made on resources in your AWS account.
- Data events Data events sometimes referred to as data plane operations give information on resource activities carried out on or in a resource. Data events frequently include enormous volumes of activity.
- Insight events Not logged in by default. Observable behavior in your AWS account is captured by insights events. When you enable Insights events, CloudTrail will find suspicious behavior and report it to S3. The pertinent data that insights events give, such as the linked API, incident time, and statistics, enable you to comprehend unexpected behavior and take appropriate action. Only when CloudTrail notices changes in your account's API usage that significantly deviate from the account's regular usage patterns are insights events recorded.
Events are transmitted to any trail that includes global services and are reported as occurring in the US East (N. Virginia) Region, for global services like IAM, STS, CloudFront, and Route 53.
The following attributes: Event name, User name, Resource name, Event Source, Event ID, and Resource type may be used to filter logs in addition to the Time range.
Trails
To track, examine, and react to changes in your AWS resources, create a CloudTrail path. Types
- A trail that spans all regions is created by CloudTrail, which logs events across all regions and sends the CloudTrail event log files to a particular S3 bucket. This is the default choice when you create a trail in the CloudTrail console.
- One-regional trail: CloudTrail only captures the events in the region you designate. This is the default choice when you create a trail using the AWS CLI or the CloudTrail API.
In an organization established using AWS Organizations, you may make an organization trail that will record all occurrences for all AWS accounts. The management account has to be set up with organization trails. CloudTrail event log files are by default encrypted using server-side encryption over Amazon S3. You can alternatively decide to use an AWS Key Management Service key to encrypt your log files. You can set up S3 lifecycle rules to automatically archive or destroy log files, and you may retain your log files in your S3 bucket for as long as you choose. You may set up Amazon SNS notifications to receive alerts when log files are sent and verified. Log files are published by CloudTrail every five minutes or so.
AWS CloudTrail Log Files
Your CloudTrail files can be used for more complicated activities.
- Make several pathways in each area.
- Sending CloudWatch Logs to the CloudTrail log files allows for monitoring.
- Exchange log files among accounts.
- Java applications for log processing may be created using the AWS CloudTrail Processing Library.
- Verify that your log files, which CloudTrail delivered to you, have not been altered.
When an event takes place in your account, CloudTrail checks to see if it conforms to the parameters for your trails. Your Amazon S3 bucket and Amazon CloudWatch Logs log group receive only events that correspond to your trail settings. Multiple trails can be set up differently so that they only process and record the events you specify. For instance, one trail might record management and read-only data events, delivering all read-only events to a single S3 bucket. A different trail can record just management and write-only data events, delivering all write-only events to a different S3 bucket.
Alternatively, you may set up your trails such that one trail logs and sends all management events to a single S3 bucket, while another trail logs and sends all data events to a different S3 bucket.
Enabling/Disabling Trails
By adjusting the button in the trail's property screen's upper right corner, we may activate or disable an existing trail.
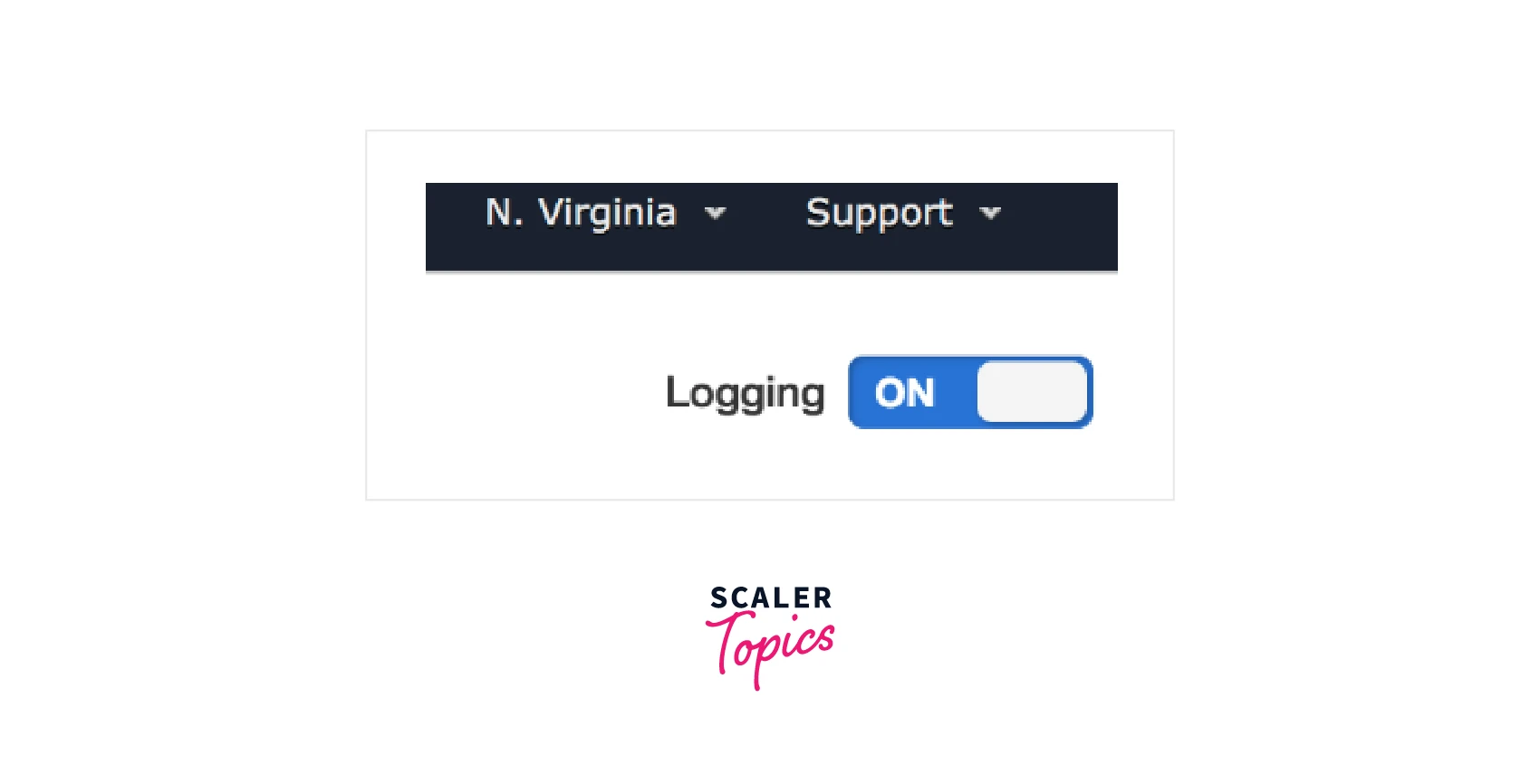
If you have many trails running in your account and are unsure which one your log management monitoring platform is using, you might need to do this. You may check after selectively disabling each trace.
Sending AWS CloudTrails to CloudWatch
Amazon CloudWatch is a foundational service of the AWS platform, similar to CloudTrail. Simply said, any AWS account can be thought of as having CloudWatch as its eyes and ears. CloudWatch provides a range of capabilities for monitoring other account resources, delivering alerts depending on resource state, scheduling Lambda functions and other processes, and hosting log files from various AWS services and resources, whereas CloudTrail tracks and records API calls made to objects.
CloudWatch can be used in the following situations:
- Billing notifications for AWS
- Notifications for EC2 auto-scaling
- RDS instance performance monitoring dashboards
- Lambda function or data pipeline CloudWatch events
- Log groups and streams for various resource types in CloudWatch (e.g. VPC flow logs)
Events from CloudTrail may be published to CloudWatch Logs. This strategy enables CloudTrail to use CloudWatch functionalities like:
- Searching through logs is simple.
- Sending notifications for logged events
- Creating dashboards and metric filters from recorded events
Two conditions must be met to submit a trail to CloudWatch:
- A log stream and a CloudWatch log group
- An IAM role and its policy that grants CloudTrail access to CloudWatch
After the trail has been constructed, the option to send CloudTrail events to CloudWatch Logs becomes accessible. The trail has to be modified thereafter to use CloudWatch. We are updating and setting up our Trail1 to submit its logs to CloudWatch in the image below.

Click the “Configure” button:
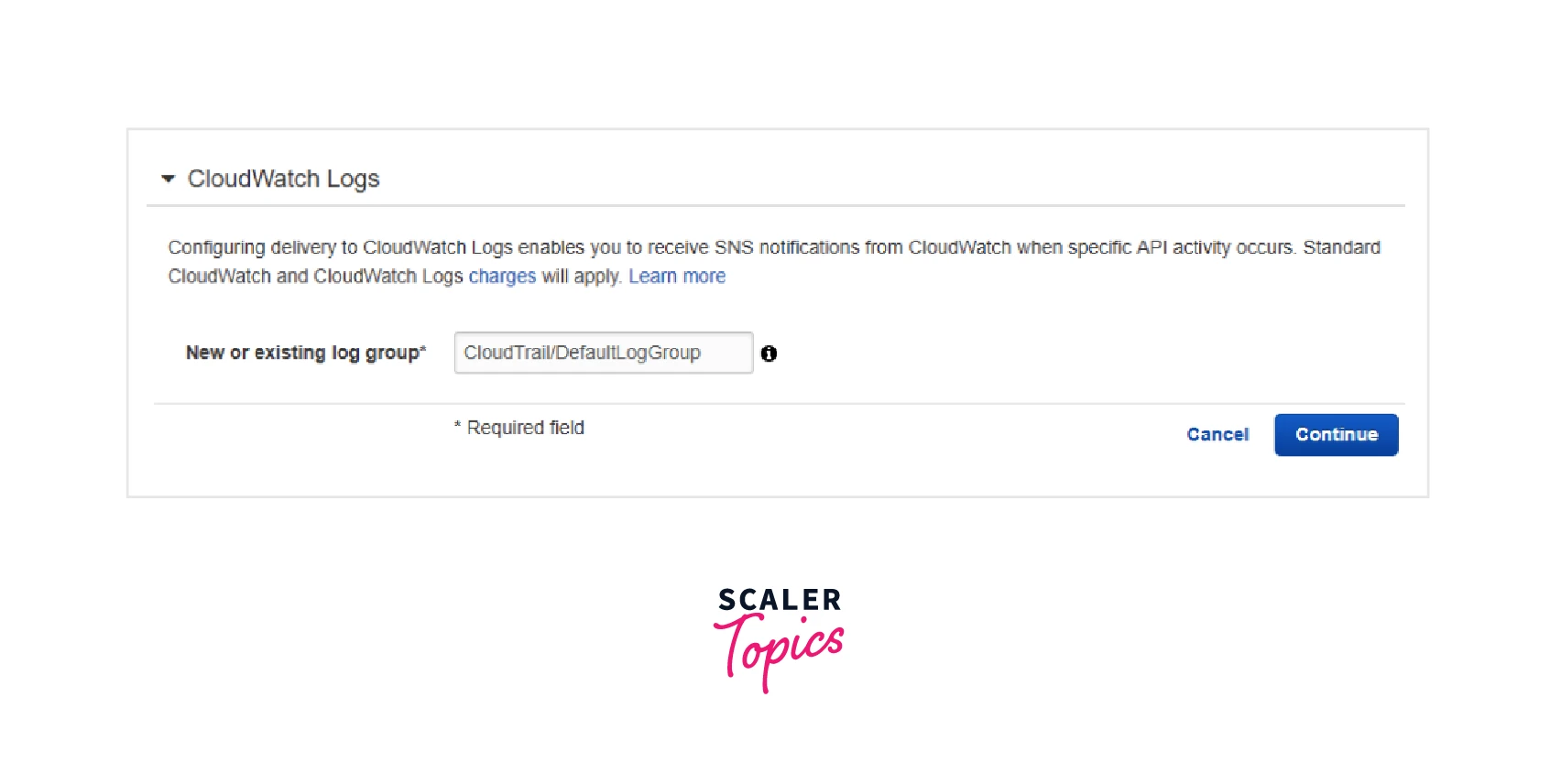
The log group and log stream names where the events will be broadcast must be known to CloudWatch. The proposed default log group ("CloudTrail") is an option, or we may define a different log group. A log stream will be included in this log group for each trail that has been set up to submit its logs to CloudWatch.
The wizard then requests the IAM role to utilize when we click "Continue" as follows:
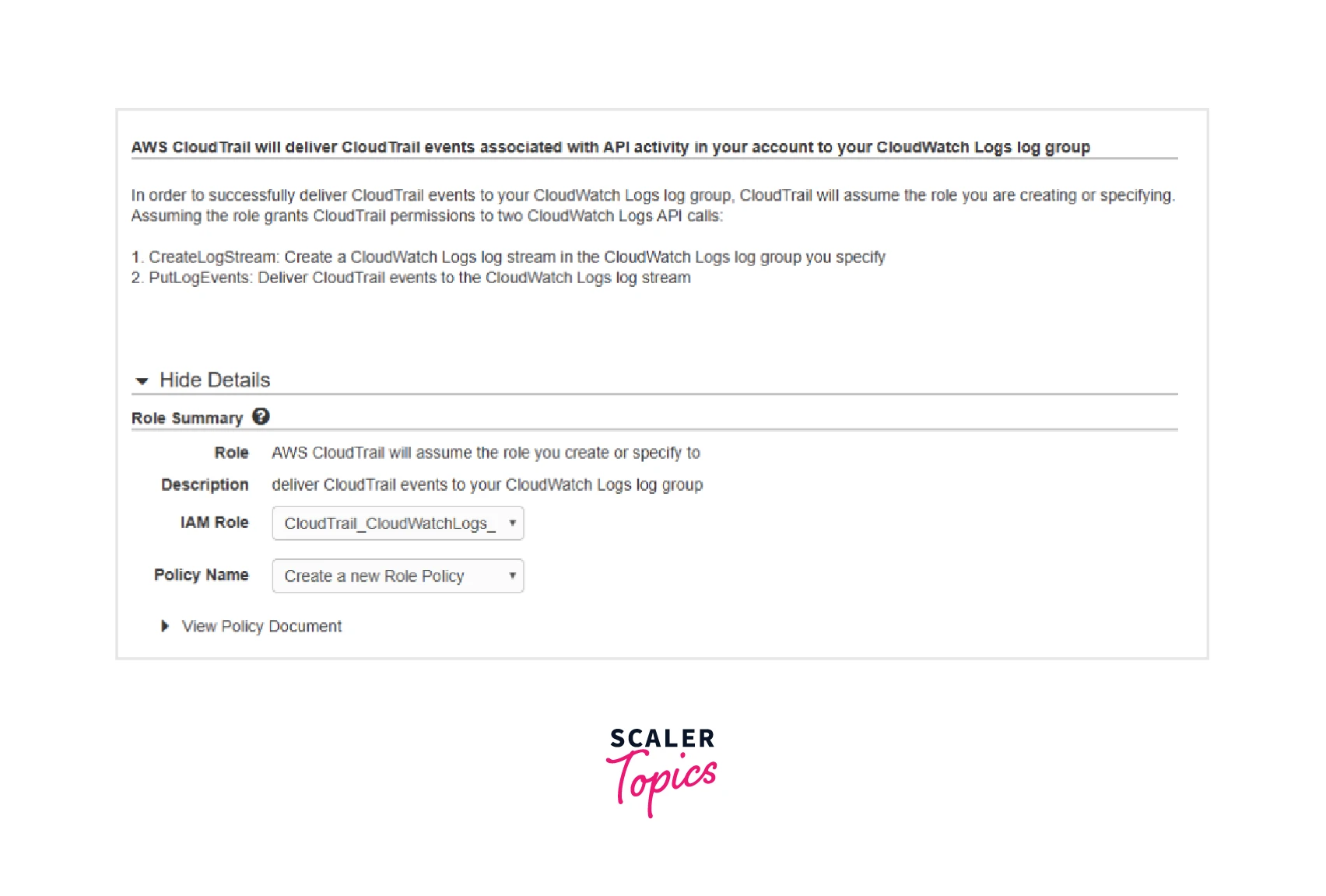
Once more, we have the option of specifying our unique role and policy or letting the wizard construct them for us. "CloudTrail CloudWatchLogs Role" will be the role's default name. This role's IAM policy will provide CloudTrail access to CloudWatch Logs with the "CreateLogStream" and "PutLogEvents" permissions.
We may save the modifications after defining the IAM role and policy.
We can then navigate to the log group to observe that the trail's log stream has been established:
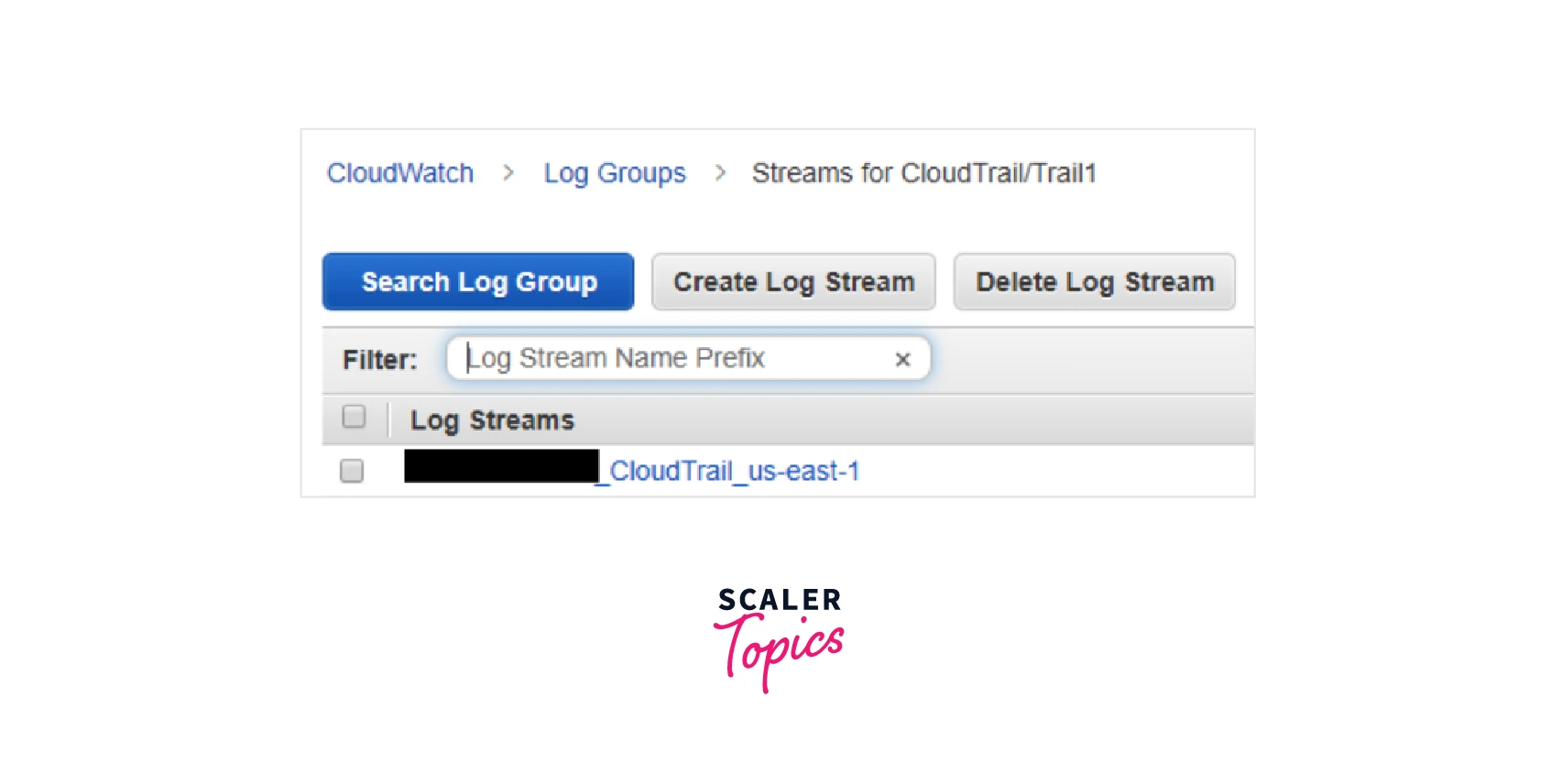
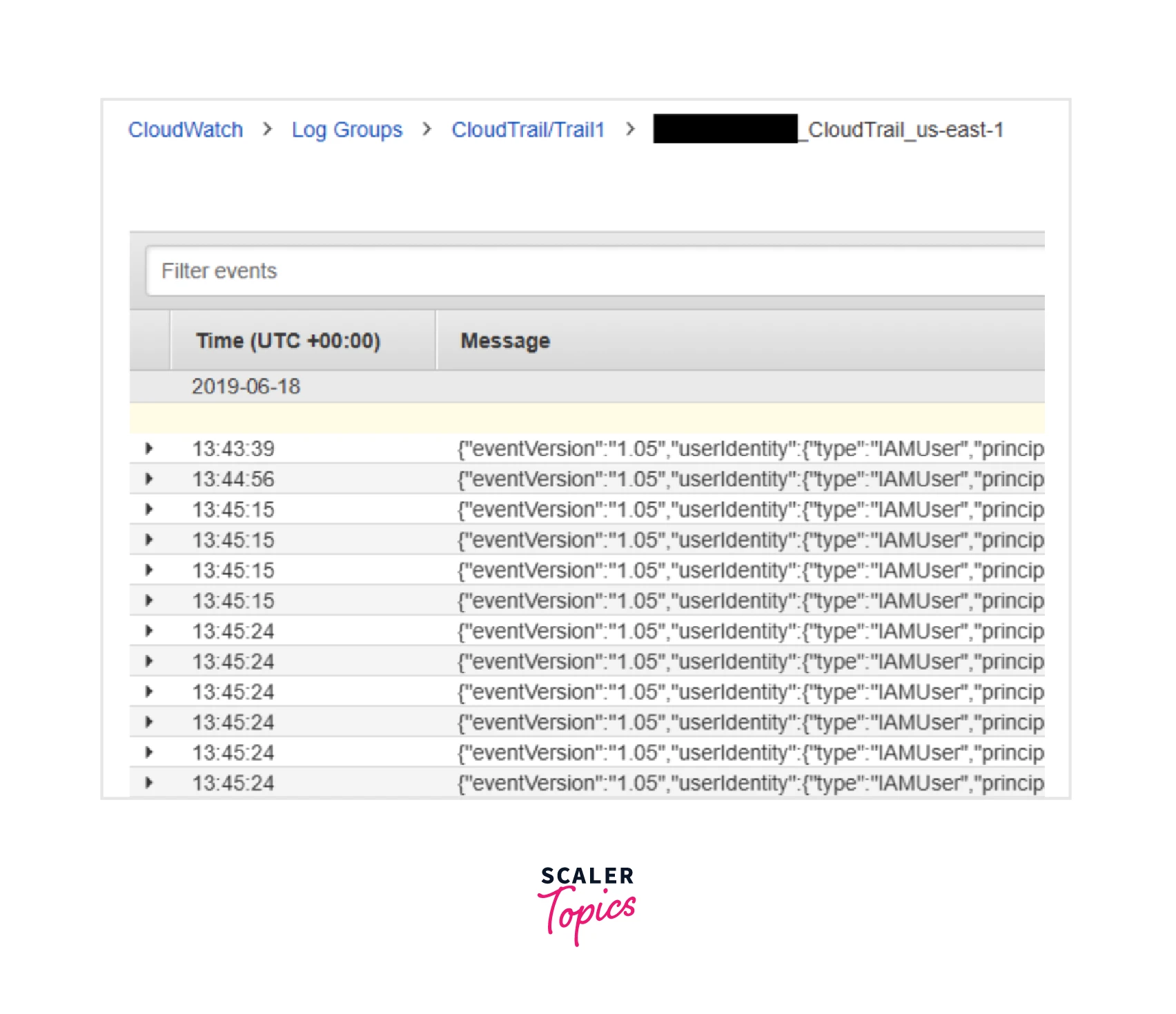
The log stream's naming scheme is as follows: <account_id>_CloudTrail_<region> Inside the log stream, we can view the log events:
Amazon CloudTrail Pricing
- Management events are offered for free for the first time in each location. There are fees for additional copies of management events.
- Only the Lambda functions, DynamoDB tables, and S3 buckets you designate are recorded and charged for data events.
- Since CloudTrail sends logs to an S3 bucket, S3 fees depending on consumption apply after a trail is set up.
AWS Free Tier
Event history By default, AWS CloudTrail records management events for all AWS services and is free to use. Using the CloudTrail console or the CloudTrail lookup-events API, you may see, search, and download the most recent 90-day history of the control plane activity associated with your account at no extra charge.
Lake For 30 days, CloudTrail Lake is free to test for new clients. The whole feature set will be available to you throughout this period. You will be subject to the following restrictions during the 30-day free trial period:
- up to 5 GB of data ingestion
- 5 GB of data may be scanned
- Save data without paying more.
Your free trial ends after 30 days or if you've used up all of your free use, whichever occurs first. You can continue using AWS CloudTrail Lake after your free trial has ended at the regular pay-as-you-go service fees outlined in the Paid Tier section.
Trails By generating trails, you may send one copy of your ongoing management events for free to your Amazon S3 bucket.
Paid Tier
Lake You pay a single price for both storage and ingestion with AWS CloudTrail Lake. Your data can be kept for up to seven years. Select the data you want to analyze, and pay as you go.
Trails Pay exactly what you really use. No minimum payment is necessary. Using trails, you may transmit extra copies of events, including data events. Charges for Amazon S3 are necessary and are not included in the given price.
The events provided using trails made in member accounts are charged as additional copies if the management account has an organization trail that sends management events.
Insights Choose which event to study for CloudTrail Insights, and pay as you go. In your trails, you may activate CloudTrail Insights events.
You can visit the following website to learn more about costs:Amazon Cloudtrail
Conclusion
- CloudTrail is an extremely effective tool in your never-ending quest to improve your security solution. Every API call performed inside your environment may be recorded, enabling superior auditing and, in turn, compliance with certain governance requirements.
- The setup is simple. Once the system is up and operating, the logs may be a useful source of data for governance audits and forensic investigations.
- Different teams and departments can utilize CloudTrail for various use cases thanks to the flexibility to build numerous Trails.
- Additionally, we discovered that CloudTrail records all API calls made within your environment and in any locations where this is set up to happen. A relevant Event is created with corresponding metadata for each API call that is recorded and stored in a Log file.
