Security Groups Vs NACL
Overview
When you create your networking stack on AWS, you have access to several inherent critical protections. It can be tricky to handle such a broad range of services and capabilities, and it can be not very clear to know which tools to employ in every situation. The Network Access Control List (NACL) and The Security Group are the two primary security elements that can be misunderstood while using VPC networking. The use cases for each of these security characteristics vary noticeably when you compare a Security Group to an NACL in AWS, even though they are often quite similar. To control inbound and outbound traffic, security groups and NACL in AWS both function as virtual firewalls.
What Are The Security Groups?
A stateful firewall called a Security Group can be connected to instances. To an instance or instances, a security group in AWS performs a firewall function. In both inbound and outbound rules, the Security Group will always contain an implicit denial that is concealed. Therefore, in Security Groups, we can only expressly allow something and not refuse it.
Advantages
- You should start with security groups in AWS because they are the simplest and most fundamental component of security.
- Security Groups in AWS are connected at the ENI (Elastic Network Interface) level and assessed against the resource's physical host before being approved.
- You can assess a source or destination using the prefix list or another resource's security group. Using this, you can filter traffic to particular resources instead of everything in a Classless Inter-Domain Routing(CIDR) range.
- Additionally, security groups in AWS are stateful, so if traffic can go in one direction, it can also flow backward.
- Security Groups considerably minimize the susceptibility of your EC2 instances to network-based risks by limiting precisely which endpoints your Virtual Machines(VMs) are allowed to communicate with.
Disadvantages
- In a region, we can have up to 10,000 security groups (the default is 2500). You must submit a service request if you want to raise the limit.
- For a certain Security Group, 60 inbound rules and 60 outbound rules are permissible.
- Each elastic network interface can support 16 security groups (ENI). The standard is 5.
What is a Network Access Control List?
Because NACLs are stateless firewalls that operate at the subnet level, they serve as a firewall for the entire subnet or subnets. An NACL's default setting permits all inbound and outbound traffic. In contrast to Security Groups, NACLs need us to explicitly state in the Inbound and Outbound Rules what to deny. In NACL, there is no Implicit Deny.
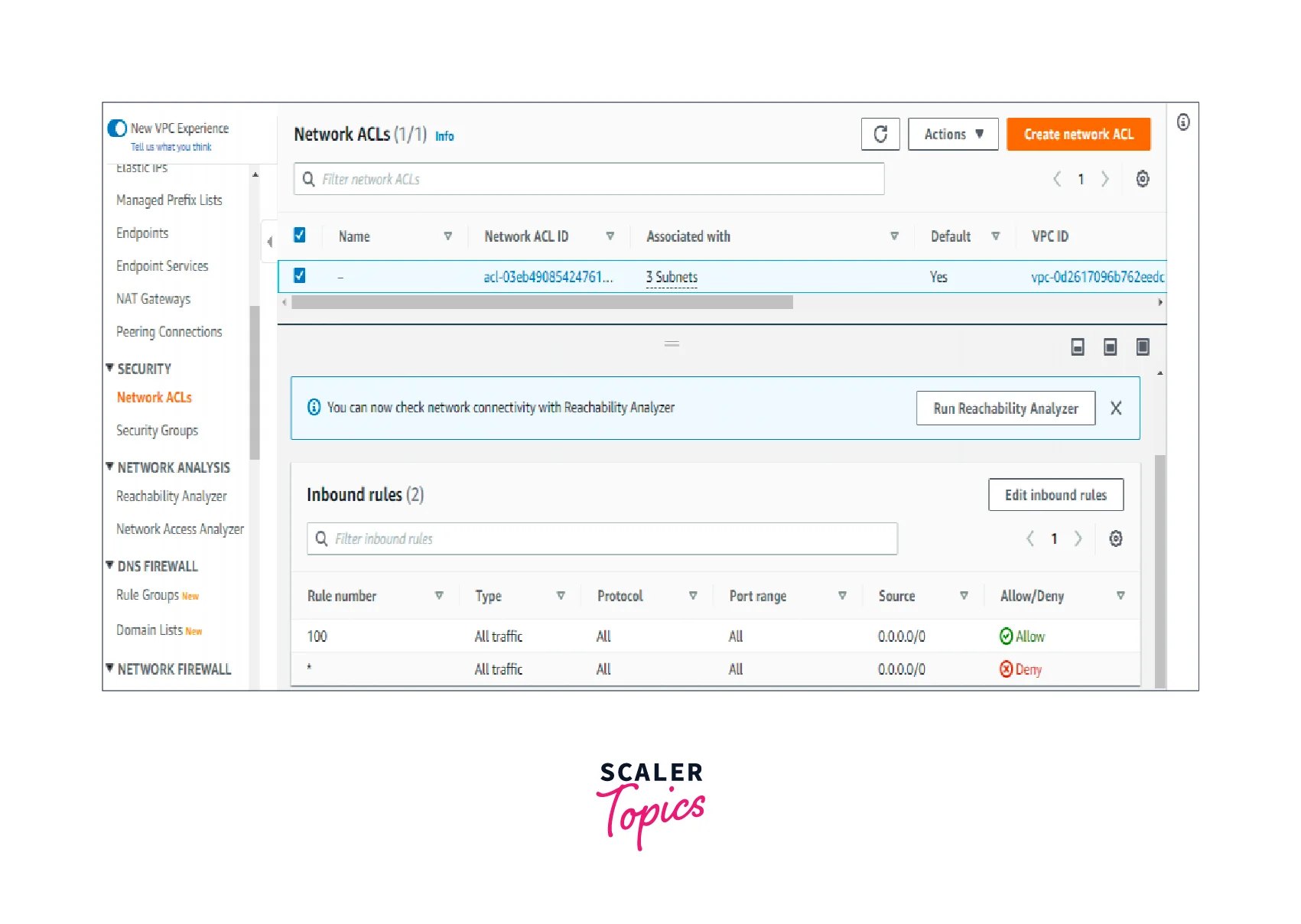
Advantages
- Improved server protection for internet use.
- More restrictions on entrance points for access.
- Enhanced access and communication between internal networks.
- Permissions for users and groups can be controlled more precisely.
- Improved security against spoofing and denial-of-service assaults.
- Enhanced network manageability and performance.
Limitations
- A single NACL in AWS may include a maximum of 20 rules.
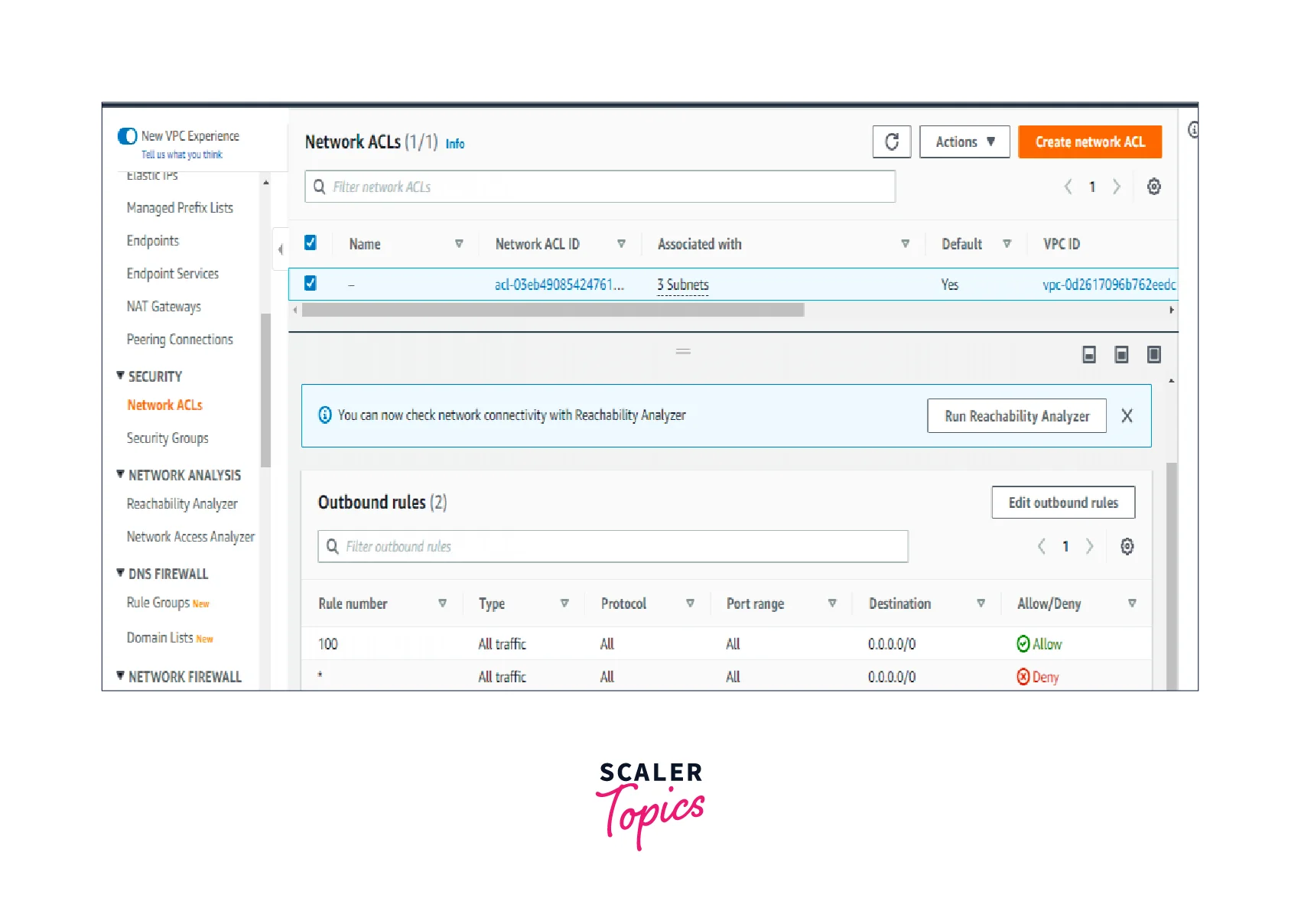
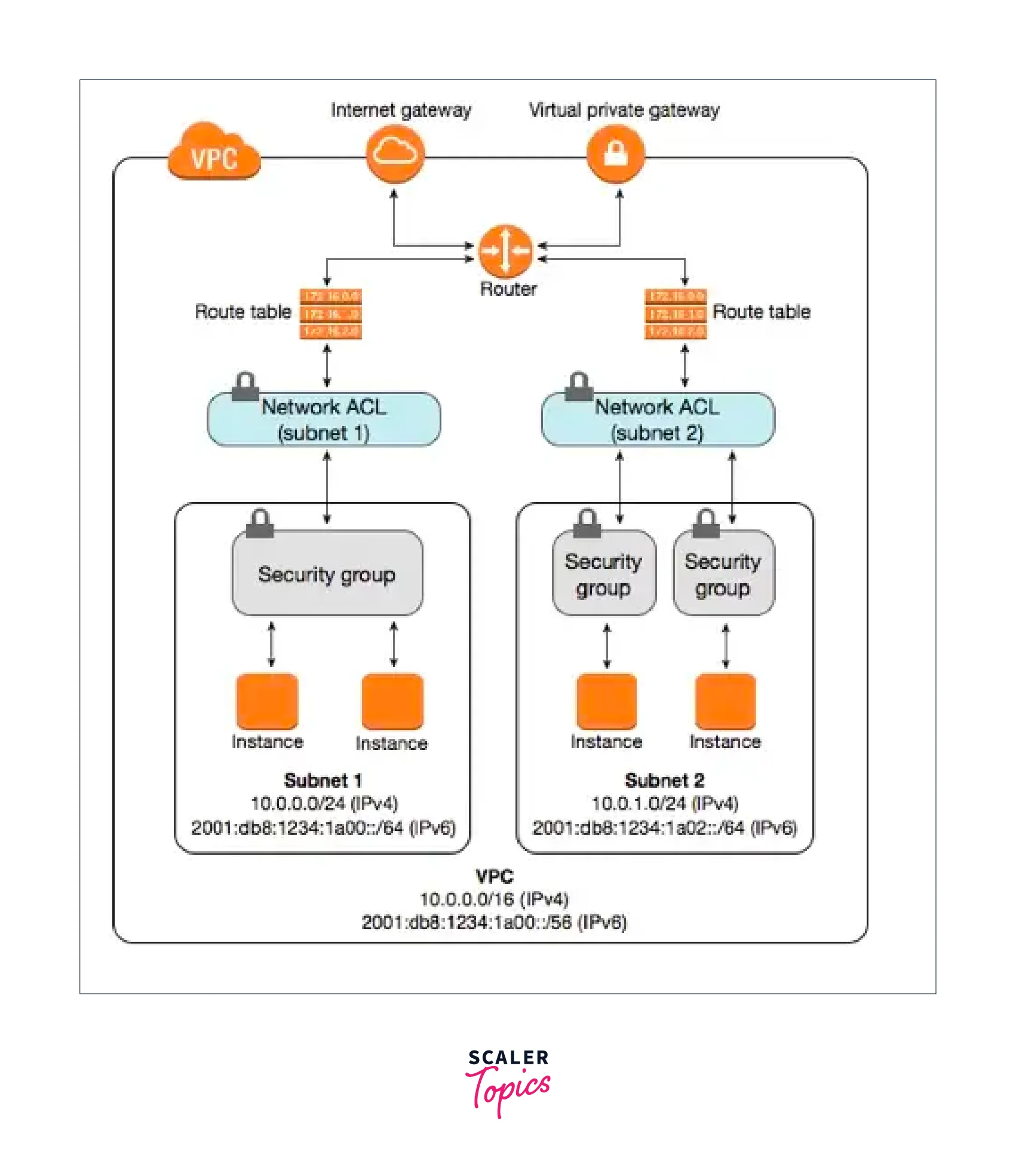
Detailed Difference Between Security Groups Vs NACL
Rules Supported
Security group only accepts allow rules (by default all rules are denied). You cannot, for instance, prevent a certain IP address from creating a connection.
Allow and deny rules are supported by NACL. You might expressly forbid a specific IP address from establishing a connection using refuse rules. Disallow connections from the IP address 132.205.52.12 to EC2 Instances.
Type of States
Security Groups in AWS are stateful. This means that any modifications made to an incoming rule will also be made to the outgoing rule. For instance, the outgoing port 80 will immediately be opened if you permit an incoming port 80.
NACL in AWS is stateless. This indicates that any modifications made to an incoming rule won't affect the outgoing rule. For instance, you would have to follow the rule for outgoing traffic if you allowed incoming traffic on port 80.
Association
NACLs in AWS are linked to the subnet, whereas security groups are linked to an instance.
Because network ACLs are applicable at the subnet level, each instance in the subnet that has a related NACL will abide by its restrictions. Security groups are an exception to this rule; security groups must be expressly allocated to an instance.
This indicates that the rule is applied to all instances inside the subnet group. With a Security group, you need to manually assign a security group to each instance.
Positions Among Defense Layers
For inbound/ingress traffic, Network ACL serves as the first layer of defense while Security groups serve as the second layer.
Security group serves as the first layer of security, while Network ACL serves as the second line of defense for outgoing and egress traffic.
Others
Unlike instances, which can have many security groups, subnets can only have one NACL in AWS.
CIDR, IP, and security group destinations are permitted by security group rules.
NACLs in AWS only permit CIDR as a destination.
Conclusion
- The virtual shields or defenders of EC2 instances are security groups in AWS. By default, all inbound traffic is prohibited while all outbound traffic from the instance is allowed unless specifically allowed.
- A virtual firewall for subnets called Network Access Control List regulates subnets' inbound and outbound traffic. A Default NACL will be connected with the VPC after it is created and w, permittingnbound, and Outbound Traffic.
- Security groups in AWS serve as the first layer of security, while NACLs in AWS serve as the second line of defense
- Unlike instances, which can have many security groups, subnets can only have one NACL.
- A security group's rules are all applied, unlike Network ACL where rules are handled in the order they appear (the rule with the lower number is processed first).
