IAM Users in AWS
Overview
An AWS Identity and Access Management (IAM) user is an entity that you create in AWS to represent the person or application that uses it to interact with AWS. A user in AWS consists of a name and credentials. An IAM user with administrator permissions is not the same thing as the AWS account root user. In AWS, a user is defined by their name and credentials. IAM Users' primary function is to allow users to log in to the AWS Management Console and submit requests to the AWS services.
Introduction to IAM Users
You create an entity in AWS called an IAM user. The IAM user represents the individual or entity interacting with AWS through the IAM user. Giving people the ability to log in to the AWS Management Console for interactive chores and to send programmatic queries to AWS services using the API or CLI is one of the main uses for IAM users. In AWS, a user is made up of a name, a password for the AWS Management Console, and maybe two access keys for the API or CLI.
When you establish an IAM user, you can either directly attach policies to the user or add the policies to a user group that already has the relevant authorization policies attached (this is preferable). Additionally, you can duplicate an existing IAM user's permissions, which adds the new user immediately to the same user groups and policies.
How Does AWS Identify an IAM User?
IAM creates the following ways to recognise a user when you create one:
- A user's friendly name is the name you gave them when you created them, like Richard or Anaya. You may find these names in the AWS Management Console.
- A user's Amazon Resource Name (ARN). When you need to identify a user specifically across all of AWS, you utilise the ARN. A user could be designated as a Principal in an IAM policy for an Amazon S3 bucket, for instance, by using an ARN. An IAM user's ARN might resemble the following: arn:aws:iam::account-ID-without-hyphens:user/Richard
- A unique identifier for the user. This ID is returned only when you use the API, Tools for Windows PowerShell or AWS CLI to create the user; you do not see this ID in the console.
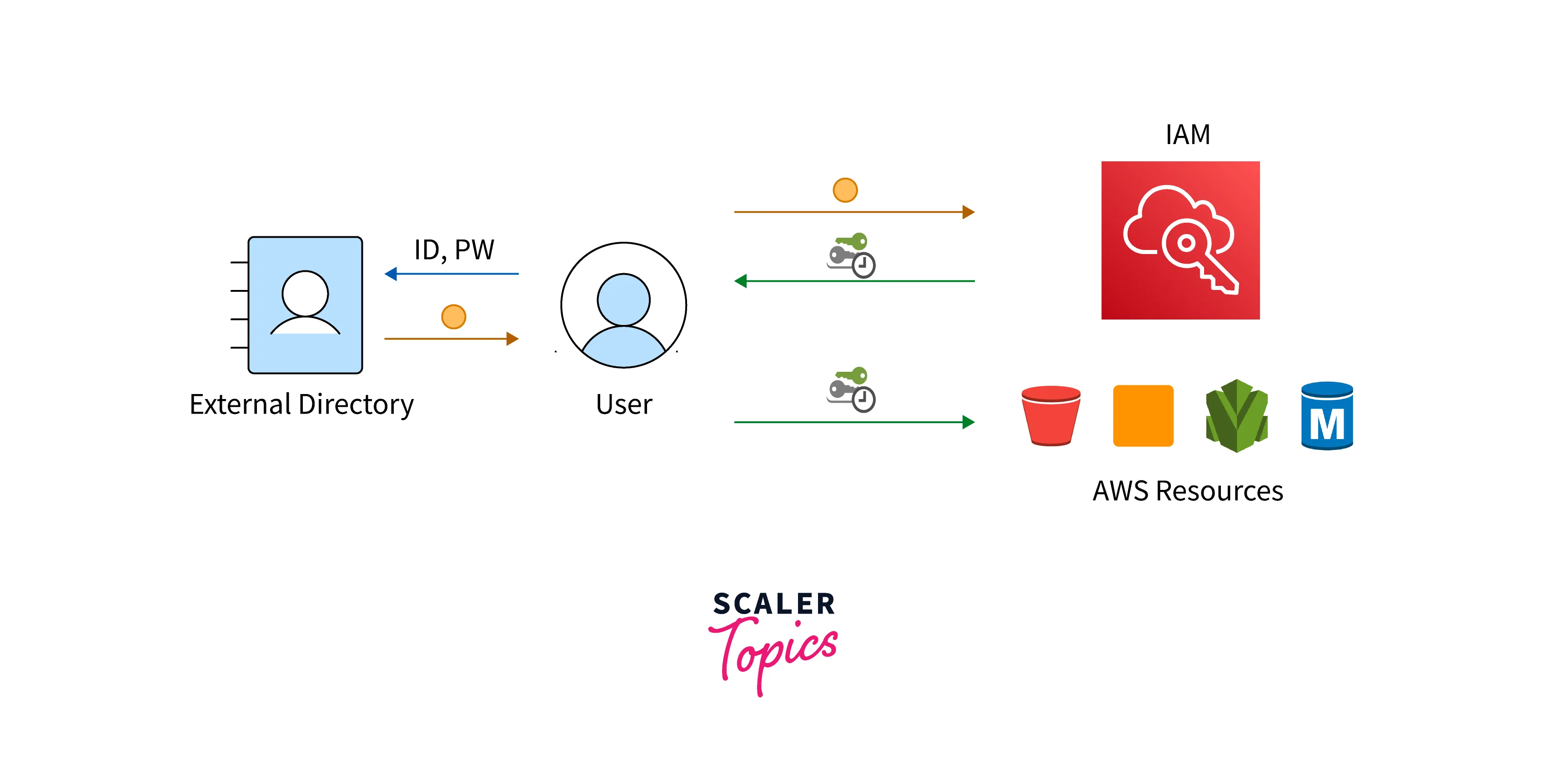
Users and Credentials
The user credentials, there are various ways to access AWS:
- Console Password: A secret password that the user enters to log in to interactive sessions, such as the AWS Management Console. When a user's password (console access) is disabled, they are unable to access the AWS Management Console with their username and password. It does not alter their access rights or stop them from logging in to the console using a false identity.
- Access Keys: A pair consisting of a secret access key and an access key ID. Two can be given to a user at once. These can be used to contact AWS programmatically. The AWS CLI, Tools for Windows PowerShell, AWS API, and the AWS Console mobile application continue to work and permit access if the user has active access keys.
- SSH Keys for Use with CodeCommit: A CodeCommit authentication public key that is an SSH public key in the OpenSSH format.
- Server Certificates: You can authenticate with some AWS services using SSL/TLS certificates. It is advised you deploy, manage, and provision your server certificates using AWS Certificate Manager (ACM). Use IAM only if you have to handle HTTPS connections in a region where ACM is incompatible.
You can select the appropriate credentials for your IAM user. You must at the very least select to add a console password or access keys when you use the AWS Management Console to establish a user. New IAM users created with the AWS CLI or AWS API come without any credentials by default. Based on the requirements of your user, you must build the right kind of credentials for an IAM user.
Utilize the following choices to manage passwords, access keys, and MFA gadgets:
- In Command of Your IAM users' Credentials: The passwords that allow access to the AWS Management Console should be created and updated. Create a password policy to impose a required level of complexity. Give users the option to alter their passwords.
- For your IAM Users, Manage Access Keys: To gain access to the resources in your account programmatically, create and update access keys.
- Enabling multi-factor authentication (MFA) for the user will increase the security of their login credentials. Users are required to submit two forms of identity while using MFA: They first give the credentials associated with their user identity (a password or access key). Additionally, they offer a transient numeric code that is produced by a hardware device or an app on a smartphone or tablet.
- For your Account, Download a Credential Report: A report of all IAM users in your account, along with the status of each of their different credentials, such as passwords, access keys, and MFA devices, may be generated and downloaded. The credential report for passwords and access keys displays the time since the last use of the password or access key.
Users and Permissions
A brand-new IAM user is created with no permissions and cannot do anything. The user is not permitted to use any AWS resources or carry out any AWS operations. The ability to individually provide permissions to each user is a benefit of having individual IAM users. You might grant certain users administrative rights so they can manage other IAM users and administer your AWS resources. However, in the majority of situations, you want to restrict a user's access to only the tasks (AWS actions or operations) and resources required for the job. Consider Sam, the name of the user. You can set a password for the IAM user Sam when you create it. Additionally, you grant the IAM user access so that he can start a particular Amazon EC2 instance and read (GET) data from a table in an Amazon RDS database. A permissions limit can also be added for your users. An advanced feature called a permissions boundary enables you to utilize AWS-managed policies to set a maximum number of permissions that an identity-based policy can provide to a user or role.
Users and Accounts
Only one AWS account is connected to each IAM user. Users are not required to keep a payment method on file with AWS because they are established within your AWS account. Your account will be charged for any AWS services used by users under your account. IAM resources in an AWS account have a restricted number and size.
Users as Service Accounts
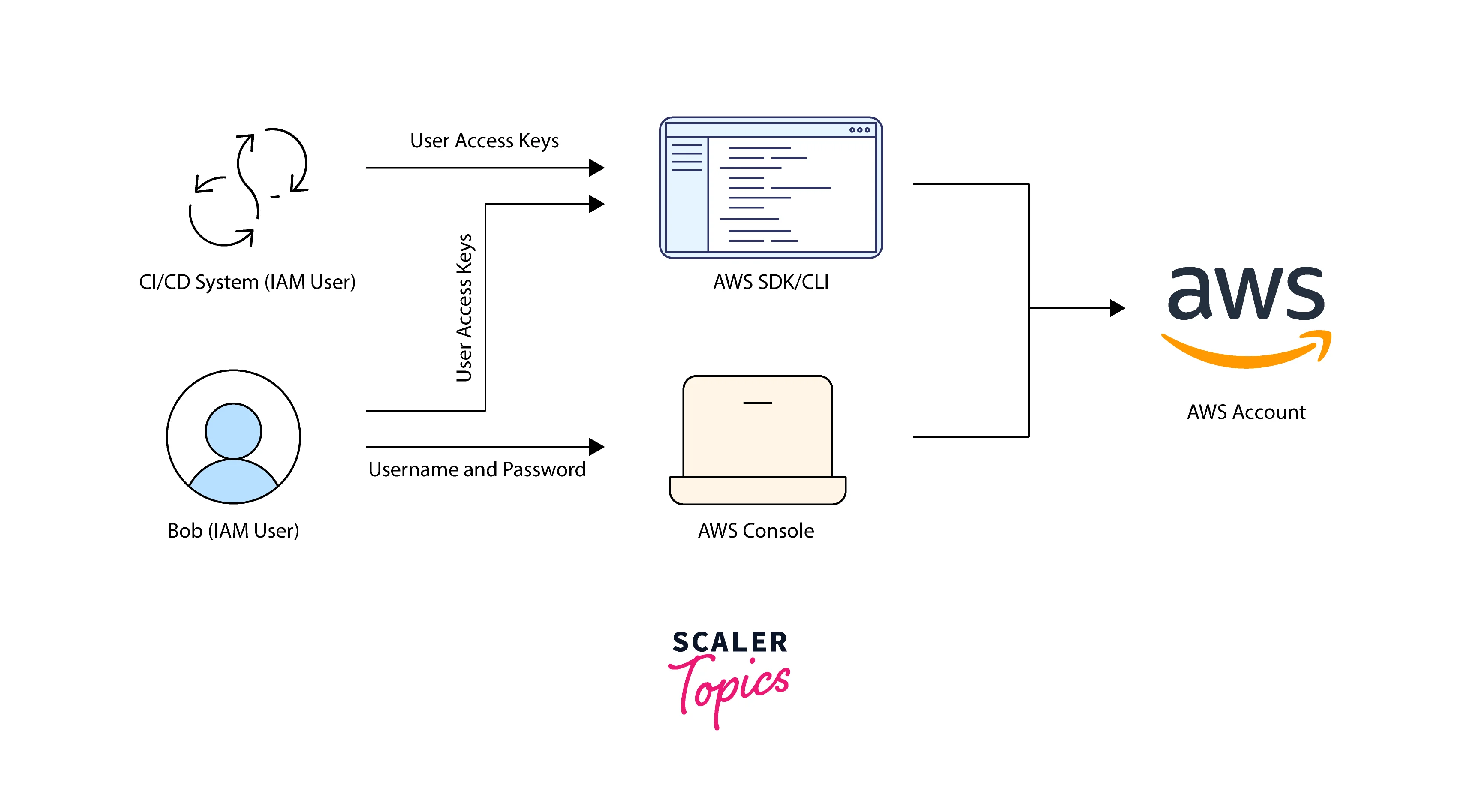
A resource in IAM with related credentials and permissions is known as an IAM user. A person or program that utilizes its credentials to submit requests to AWS might be represented as an IAM user. The term "service account" is frequently used to describe this. Only incorporate access keys directly into your application code if you use an IAM user's long-term credentials. You do not need to store access keys in code using the AWS Command Line Interface and the AWS SDKs.
Creating an IAM User in AWS
Creating IAM Users (Console)
To Create One or More IAM Users (console)
- Open the IAM console by logging into the AWS Management Console at https://console.aws.amazon.com/iam/
- Select Users from the navigation pane, then select Add users.
- Enter the new user's user name. This is the AWS sign-in name. Select Add another user and enter each additional user's user name if you want to add more than one user. At one moment, you can add up to 10 users.
- Choose the kind of access that this group of users will be granted. You have the option of choosing programmatic access, AWS Management Console access, or both.
- If the users need access to the AWS CLI, the API, or the Tools for Windows PowerShell, choose Programmatic access. Each new user receives an access key as a result. On the Final page, you may view or download the access keys.
- If the users need access to the AWS Management Console, choose AWS Management Console access. Each new user receives a password.
- For Console password, the following things need to be done:
- Autogenerated Password: A randomly generated password that complies with the account password policy is given to each user. On the Final page, you may view or download the passwords.
- Custom Password: You enter a password that is assigned to each user.
- Select Next: Permissions.
- Indicate the permissions you want to give this group of new users on the Set permissions page. Select one of the three possibilities listed below:
- Add User to Group: Select this option if you wish to add the users to a group or groups with existing rights. IAM shows a list of the groups in your account and any policies they have associated with them. Choose to Create a group to start a new group, or pick one or more already existing groups.
- Copy Permissions From Existing User: Select this option if you want to transfer to new users all of an existing user's group memberships, associated managed policies, embedded inline policies, and any existing permissions boundaries. IAM lists all of the users associated with your account. Choose the option whose permissions best meet the requirements of your new users.
- Attach Existing Policies Directly: To get a list of the AWS-managed and customer-controlled policies in your account, select this option. Choose the policies you want to apply to the new users or click Create a policy to open a new tab and start a brand-new policy from scratch. See step 4 of the procedure for creating IAM policies for further details. Close that tab after creating the policy, then switch back to your original tab to add the new user to the policy.
- Select Next: Tags.
- To view every one of the choices you've made so far, select Next: Review. Select Create user when you are ready to move on.
Creating IAM Users (AWS CLI)
To Create an IAM User (AWS CLI)
- Create a user. aws iam create user
- Include the user in a group or groups. Policies that allow the user the necessary permissions must be attached to the groups you define. aws iam add-user-to-group
Creating IAM Users (AWS API)
To Create an IAM User from the (AWS API)
- Create a user CreateUser
- Add the user to one or more groups. Policies that allow the user the necessary permissions should be attached to the groups you define. AddUserToGroup
Deleting an IAM User
Deleting an IAM User (Console)
To Delete an IAM User(Console)
- Open the IAM console at https://console.aws.amazon.com/iam/ after signing into the AWS Management Console.
- User needs to be selected from the navigation pane.
- To delete a user, tick the box next to its name in the user group list. By kind, rights, and user group name, you can filter the list of user groups using the search box.
- Select Delete.
- Enter the name of the user and select Delete in the confirmation box if you only want to delete one user group. To delete multiple user groups, enter the desired number of user groups, followed by the desired user group, and then select Delete.
Deleting an IAM User (AWS CLI)
To Delete an IAM User Group (AWS CLI)
- Remove all users from the user group. aws iam get-user(to obtain the user's list)
- Delete every inline policy that is a part of the user. aws iam list-policies (to obtain a list of the inline policies for the user) and aws iam delete-policy(the user's inline policies to be removed)
- Delete the user. aws iam delete
Deleting an IAM User Group (AWS API)
To Delete an IAM User Group (AWS API)
- Remove all users from the user group GetGroup (to retrieve the list of users in the user group), RemoveUserFromGroup(to remove a user from the user group).
- Remove all embedded inline policies from the user group. ListGroupPolicies and DeleteGroupPolicy are two commands that can be used to view and remove a user group's inline policies, respectively.
- All management policies related to the user group should be disconnected. ListAttachedGroupPolicies (to acquire a list of the managed policies associated with the user group) and DetachGroupPolicy(to get a list of the managed policies attached to the user group).
- Delete the user group. DeleteGroup
Conclusion
- The IAM user represents the individual or entity interacting with AWS through the IAM user.
- When we create a user, IAM creates two ways to identify that user. Firstly it friendly name is given to each user and secondly, a unique identifier for the user is also provided.
- There are various ways to access AWS like Access Keys, Console Passwords, and Server credentials.
- Using Server Credentials is a more efficient method and provides more security than all other methods.
- Creating / Deleting IAM User with the console using AWS CLI and AWS API.
