S3 Presigned URLs
Overview
By default, all S3 objects are private. Only the object owner has permission to access them. However, the object owner can optionally share objects with others by creating a pre-signed URL, using their security credentials, to grant time-limited permission to download the objects. When you create a prespre-signed for your object, you must provide your security credentials and then specify a bucket name, an object key, an HTTP method (GET to download the object), and an expiration date and time. The presigned URLs are valid only for the specified duration. If you created an apre-signedd URL using a temporary token, then the URL expires when the token expires, even if the URL was created with a later expiration time.
What are Pre-Signed S3 URLs and Why Use Them?
By default, all objects and buckets are private. You can, however, use a presigned URL to opportunistically share things or permit your users or customers to upload objects to buckets without using their AWS security credentials or permissions. To create a URL that can be used to access your Amazon S3 buckets, utilize pre signed URLs. You link a pre-signed URL to a particular action when you generate it. You can distribute the URL so that anyone with access can carry out the activity as if they were the ones who signed the document originally. When the URL hits its expiration date, it will cease to function. An URL that enables you to grant momentary access to S3 objects is known as a pre-signed URL.
With these URLs, you can limit the permissions, operations, and expiration time easily.
- Permission: A pre-signed document has the author's consent. The URL will immediately acquire all the rights that the user or service has over the S3 bucket regardless of whether the creator is an IAM user or an AWS Service.
- Operations: You can specify the operations as read, write, or update when you create the URL. You can do this to restrict read and write access to the appropriate users.
- Expiration Time: Similar to operations, when you create a URL you may specify when it will expire. However, the URL will also expire automatically if the creators' credentials have already expired.
- Resources: You can specify the bucket name when you create the URL.
You might want to use them in one of two typical use cases:
- Simple, infrequent exchange of personal files.
- Frequent, automated access to a file in an application to view or upload.
How Do S3 Signed URLs Work?
- Signed URLs operate by signing a command, in this case, the S3 getObject command, with the bucket and object key as inputs. Other operations may also be signed; for instance, PUT enables the uploading of new objects.
- The Access key is visible in the URL, while the Secret key is only utilized to produce the Signature portion. The access/secret key pair is different from a username/password in this sense.
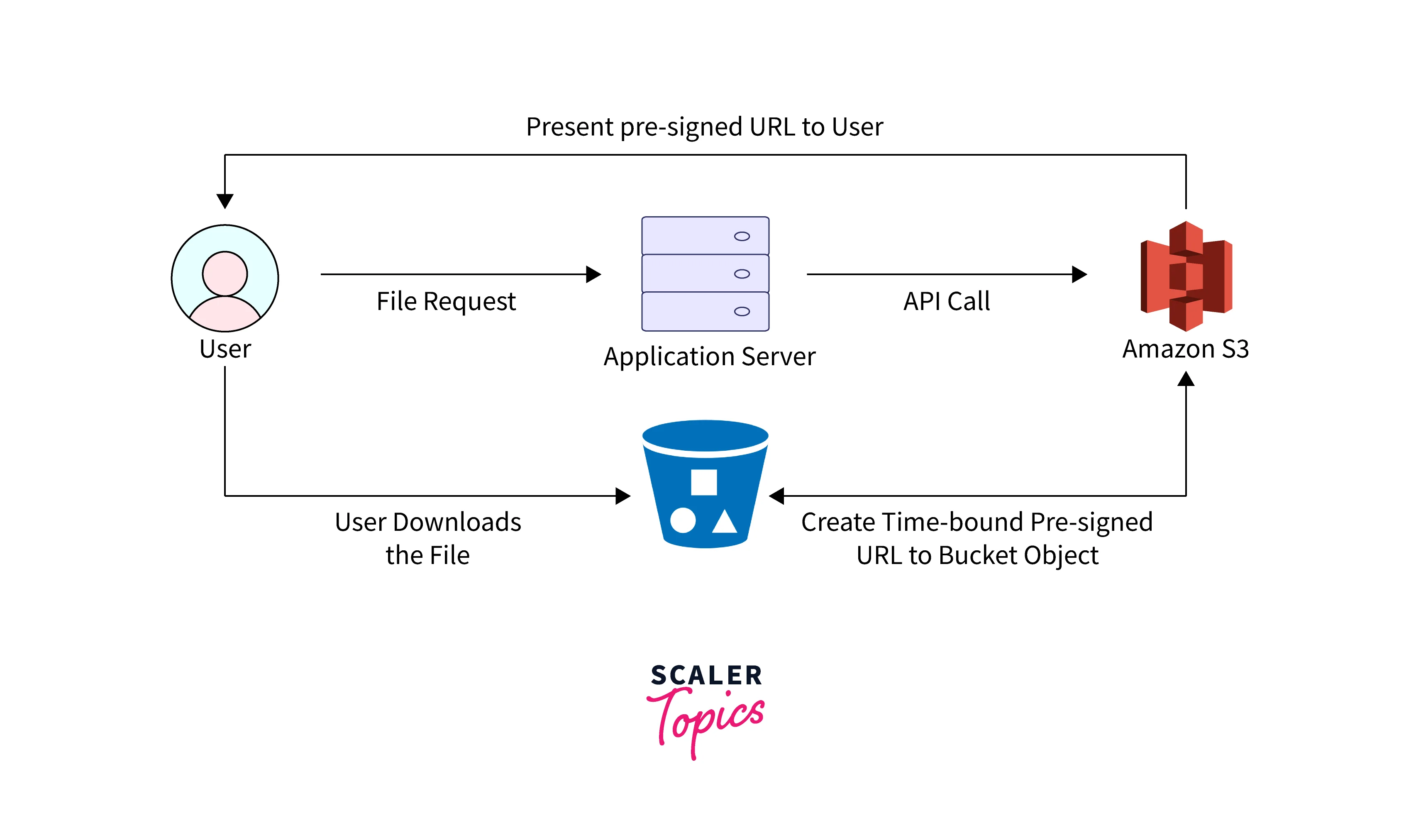
- Although it sends the request as the signer user, the signed URL does not grant access to the object in the S3 bucket on its own. It functions exactly as though the signer had issued it.
- Therefore, the pre-signed URL S3 is only functional if the signer user has access to the action (getObject) and the resource (bucket + key); as a result, the signed URL ceases to function if the permission is later revoked. However, if the permission is then granted again, it will start to function once more.
- In other words, there is no guarantee that the signed URL will function even after it expires. Everything is based on the signer user's rights.
Who Can Create a presigned URL?
A pre-signed URL can be created by anyone with legitimate security credentials. However, for someone to properly access an object, the pre-signed URL must be produced by a person who isaauthorized to carry out the operation on which it is based. You can generate a presigned URL S3 using the credentials listed below:
- IAM Instance Profile: Redeemable for six hours.
- AWS Security Token Service: When signed with persistent credentials, such as the credentials of the root user of an AWS account or an IAM user, the token is valid for up to 36 hours.
- IAM User: While using AWS Signature Version 4, valid for up to 7 days.
IAM user credentials (access and secret keys) must first be assigned to the SDK you're using to establish a pre-signed URL S3 valid for up to 7 days. Then, employ AWS Signature Version 4 to create a pre-signed URL.
Limitingpresignedd URL Capabilities
- The permissions of the user who established an S3 pre-signed URL determine its capabilities.
- Presigned URLs are essentially bearer token that allows access to those who have them. Therefore, we advise you to give them the proper protection.
- You can create AWS Identity and Access Management (IAM) policies that demand a specific network path if you want to limit the use of pre-signed URLs and allS3access to that network path. You can specify these policies on the Amazon S3 bucket, the IAM principal making the call, or both.
- Using those credentials requires the user to send requests from the designated network due to a network-path limitation on the principal. Only requests coming from the designated network are allowed access to the bucket due to a limitation. Recognize that these limitations don't just apply in cases where a pre signed S3 URL is used.
- Depending on the kind of endpoint, you employ a different IAM global condition. Use was: SourceIp if you are connecting to Amazon S3's public endpoint. Use aws: SourceVpc or aws: SourceVpce if your VPC endpoint for Amazon S3 is any of these.
- The principal is required by the following IAM policy statement to only access AWS from the designated network range. With the implementation of this policy statement, all access must come from that range. This applies to everyone utilizing a pre signed S3 URL, too.
When does S3 Check the Expiry Time and Date of a presigned URL?
At the moment of the HTTP request, Amazon S3 checks the signed URL's expiration date and time. For instance, if a client starts downloading a sizable file right before the expiration time, the download must finish even if the expiration time elapses while it is being processed. The download will not succeed if the connection fails and the client tries to resume it after the expiration period has passed.
Generating a presigned URL to Share an Object
Via Use of the S3 Console
These procedures can be used to create a presigned S3 URL for an object using the AWS Management Console.
To Create a presigned URL Through the AWS Management Console
- Open the Amazon S3 console via https://console.aws.amazon.com/s3/ after logging into the AWS Management Console.
- Select the name of the bucket containing the object for which you want an S3 pre-signed URL from the Bucket List.
- Choose the object you wish to establish an apre-signedd URL for from the Objects list.
- Share with an S3 pre-signed URL can be selected from the Actions menu.
- Indicate how long the S3 pre-signed URL should remain active.
- Choose Createpre signedd URL.
- The URL is automatically transferred to your clipboard when a confirmation window displays. If you need to copy the presigned S3 URL once more, you will see a button to do so.
Via Use of the AWS CLI
See presign in the AWS CLI Command Reference to learn how to create an S3 pre-signed URL to share an item.
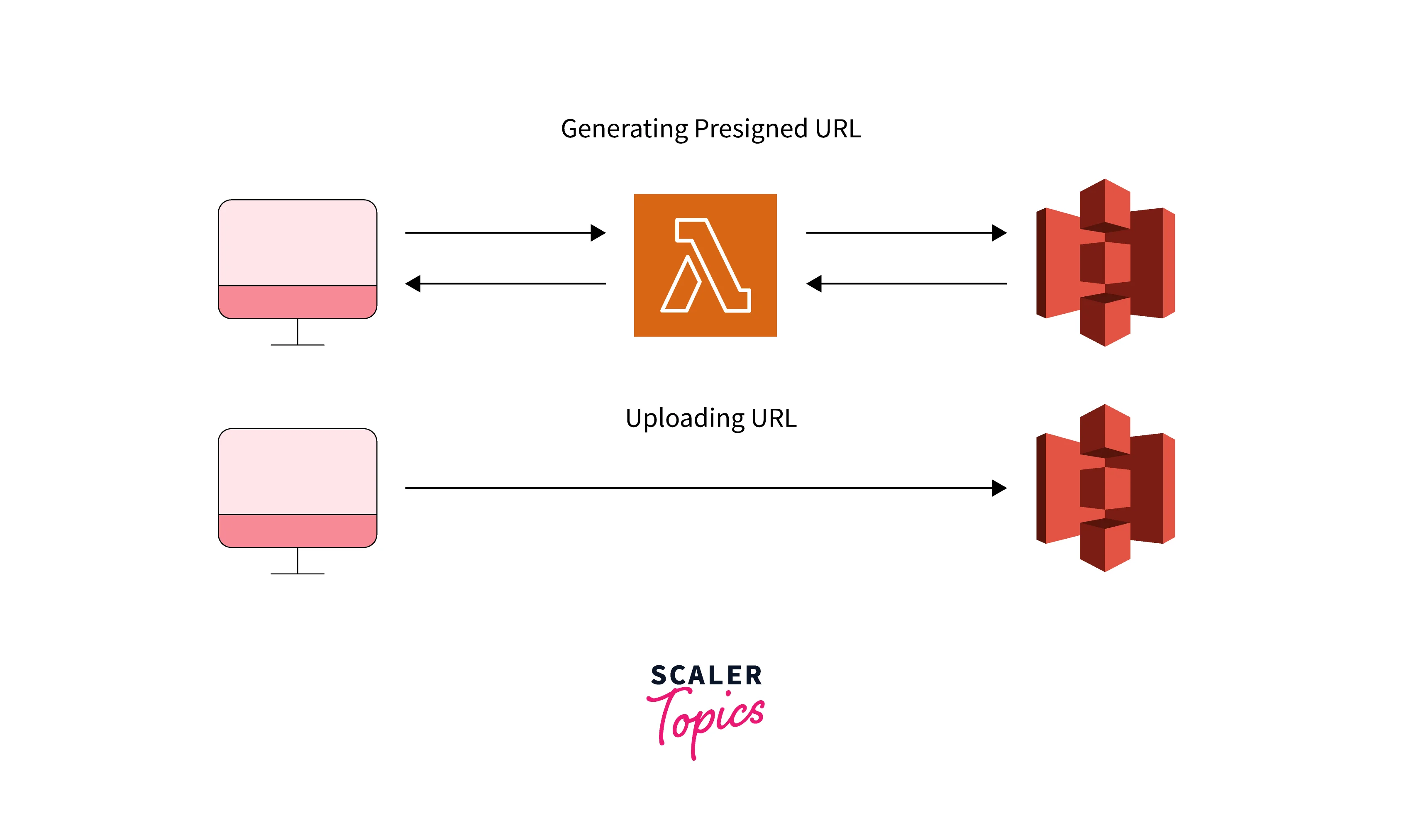
Generating apresignedd URL to Upload an Object
To learn more about how to create an S3pre-signedd URL to upload an item, click on the provided link.
Generating a S3 presigned URL to Delete an Object
For more information about using S3 pre-signed URLs to delete an object, follow this provided link.
Use Cases of S3 Presigned URLs
Sharing Files Using S3 URLs
Consider allowing a friend to download a video file that you have stored in your S3 bucket or sharing a private presentation with a business colleague. In both scenarios, you may create an Amazon S3 URL in CloudBerry Explorer and share it with the recipient to grant them temporary access.
There are a few distinct methods for ad-hoc, one-off generation of these URLs, including:
- AWS Tools for Powershell usage.
- Via means of the AWS CLI.
- CloudBerry Explorer is used.
Generating a Pre-Signed S3 URL with AWS Tools for Powershell
The Get-S3PreSignedURL cmdlet can be used to create a pre-signed URL in Powershell if you are using the AWS Tools for Powershell.
Get-S3PreSignedURL -Bucket cloudberry-examples -Key presentation.ppt -Expires 2022-11-25
The URL will be returned by the cmdlet, which you can copy and use as necessary.
Generating a Pre-Signed S3 URL With the AWS CLI
The command for a Windows computer is:
"C:\Program Files\Amazon\AWSCLI\aws.exe" s3 pre sign s3://cloudberry-examples/presentation.ppt
Using S3 URLs in Your Application Code for Temporary, Automated Access
Using Python and Boto3, Create a URL to Read an Object from Your Application Code
As was already discussed, you could want to grant a user of your application temporary read access to an S3 object. You can see how to implement it in your application code in the piece of code below.
To interface with S3, we first import the boto3 library and build a client. The GetObject API call on the object we specify is then enabled by a URL we create:
A user might be given temporary access and be emailed this URL to view in their browser.
Using Python and Boto3 to Create a URL for an Object Upload in Your Application Code
It is possible to build a pre-signed URL for POST requests. This could be useful for allowing users to upload large files with restricted access right from the browser.
Say you want to enable users to upload files to my cloudberry-examples bucket with the key name uploads/image.jpg. The generate pre-signed post method is used to create the Amazon S3 URL and provide it to the client in the example below. You can even impose constraints on the request, such as a 1 MB file size limit:
A URL property and a fields property with a collection of key-value pairs are both included in the response. The file must be submitted with the fields' key-value pairs as part of a multipart/form-data request.
Conclusion
- In this article, we learned about S3 Presigned URLs. Pre-signed URLs provide short-term access to a private object in your S3 bucket. They work by appending an AWS Access Key, expiration time, and Sigv4 signature as query parameters to the S3 object.
- We also covered two use cases of S3 pre-signed URLs. First, we looked at how pre signed URLs make sharing private files simple. Secondly, it explained how we could access or view files in an application using pre-signed URLs.
- This article also explained how to get started using pre-signed URLs using AWS CLI and AWS Console. It further explained how we could generate S3-presigned URLs to share, delete and upload files.
- Ultimately, we learned how to limit the capabilities of S3 Presigned URLs.
