S3 Data Encryption
Overview
Amazon S3 is a storage service where customers can store their data. AWS KMS is the key management service that is used to manage the cryptographic keys key management service that is used to manage cryptographic keys. In the S3 bucket, data is stored in the form of objects. To protect the objects in transit and at rest, we are using S3 data encryption in AWS. Customers can choose between server-side encryption and client-side encryption in AWS while storing data in Amazon S3.
What is S3 Data Encryption?
Amazon S3 is the AWS Managed Storage Service, which is publicly available for all AWS customers across the globe. Customers can store their files in the form of objects in the S3. The data or files stored in S3 include sensitive and mission-critical data. To protect the data in transit and the data at rest, AWS allows customers to use S3 data encryption in aws while upload and download their data. By default, objects uploaded are not encrypted. Once the customer has enabled the default encryption, all the data or files uploaded to S3 will be encrypted using AWS SSE-S3 or AWS SSE-KMS.
AWS S3 Data Encryption Types
Server-Side Encryption
When we upload or send files to the Amazon S3 bucket, Amazon S3 will encrypt the files or objects and then save them in the bucket. In the Amazon S3 backend, the data is essentially encrypted and saved on disk in its data center. Whenever we send a request to download the files or objects, Amazon S3 will decrypt the files and return them to us.
Use Amazon S3-Managed Keys (SSE-S3)
- Amazon S3-managed keys, or Amazon SSE-S3, are using AES 256-bit encryption, which is considered one of the strongest block ciphers.
- In SSE S3, there are two keys involved to protect the object or files uploaded in the bucket.
- The first key, otherwise known as a unique key, will be used for encrypting each object in the bucket.
- A second key, otherwise known as the root key, is used to encrypt the unique key and rotate the key regularly.
- Unless specific encryption is specified while uploading, it is applied by default to all objects.
- There is no charge for using this encryption.
Use CMK (Customer Master Key) in AWS KMS (SSE-KMS)
- AWS KMS is abbreviated as Key Management Service.
- Customers can use the existing AWS KMS key or create a new KMS key by using the AWS KMS console or AWS CLI.
- The KMS key is managed by AWS. It is a regional service.
- Those keys can be used to encrypt and decrypt the objects in the S3 bucket.
- In KMS Key, customers have control over who can use that KMS key. Without the proper KMS Key permission, any unauthorized access will be denied.
- Additionally, using CloudTrail logs, customers can find out who accessed the SSE-KMS key and when it was accessed.
- There is an additional charge that will be incurred for using this service.
Use a Customer Provided Encryption Key (SSE-C)
- In SSE-C, the key will be provided by the customer, and Amazon S3 will do the encryption for the object in the S3 bucket.
- When a customer uploads an object, S3 encrypts it with the encryption key provided by the customer and deletes the key from S3 memory.
- When a customer downloads the object, S3 will verify the key by matching it with the salted hash value and return the response.
- If a customer-provided encryption key is mismatched, the data will be lost and cannot be recovered.
- There are no charges for using SSE-C
Client-Side Encryption
Client-side encryption will occur from the customer or client side. Customers encrypt the data or files using their key and upload the data to Amazon S3. Once they download the object, they will use their key to decrypt the files. Here, the data will be encrypted on the customer side and stored in S3.
Use a Customer Provided Master Key
- Here, the key will be managed by the customer. So the encryption and decryption will also be taken care of by the customer. S3 will store the object. The object can be further encrypted by server-side encryption.
- If the key is lost, the data will not be recovered.
Use a CMK (Customer Master Key) Stored in AWS KMS
- AWS KMS Customer Master Key will be used to encrypt and decrypt the data locally before uploading and downloading the object from the bucket. Amazon S3 will not do the cryptography work. AWS KMS does.
Object Upload
- First, the client will send a request to AWS KMS for a new symmetric key using the KMS Key ID, which can be used to encrypt the object in the bucket.
- AWS KMS returns with two data keys that are unique and randomly generated.
- A Plaintext
- Cipher Blob
A plaintext data key will be used by the client to encrypt the object.
The cipher blob will be uploaded to the S3 object as metadata.
Object Download
- When the customer downloads the object, the client will download the encrypted object from the Amazon S3 object.
- The S3 object contains a cipher blob key as metadata. The client will send that data key to AWS KMS to retrieve the plaintext data key.
- Once it gets the plaintext, it will use it to decrypt the downloaded object.
Setting Up Amazon S3 Encryption
Encrypt an Object in Amazon S3
Requirement: S3 bucket with object
1. Go to the object available in the S3 bucket and click the Object Action button.
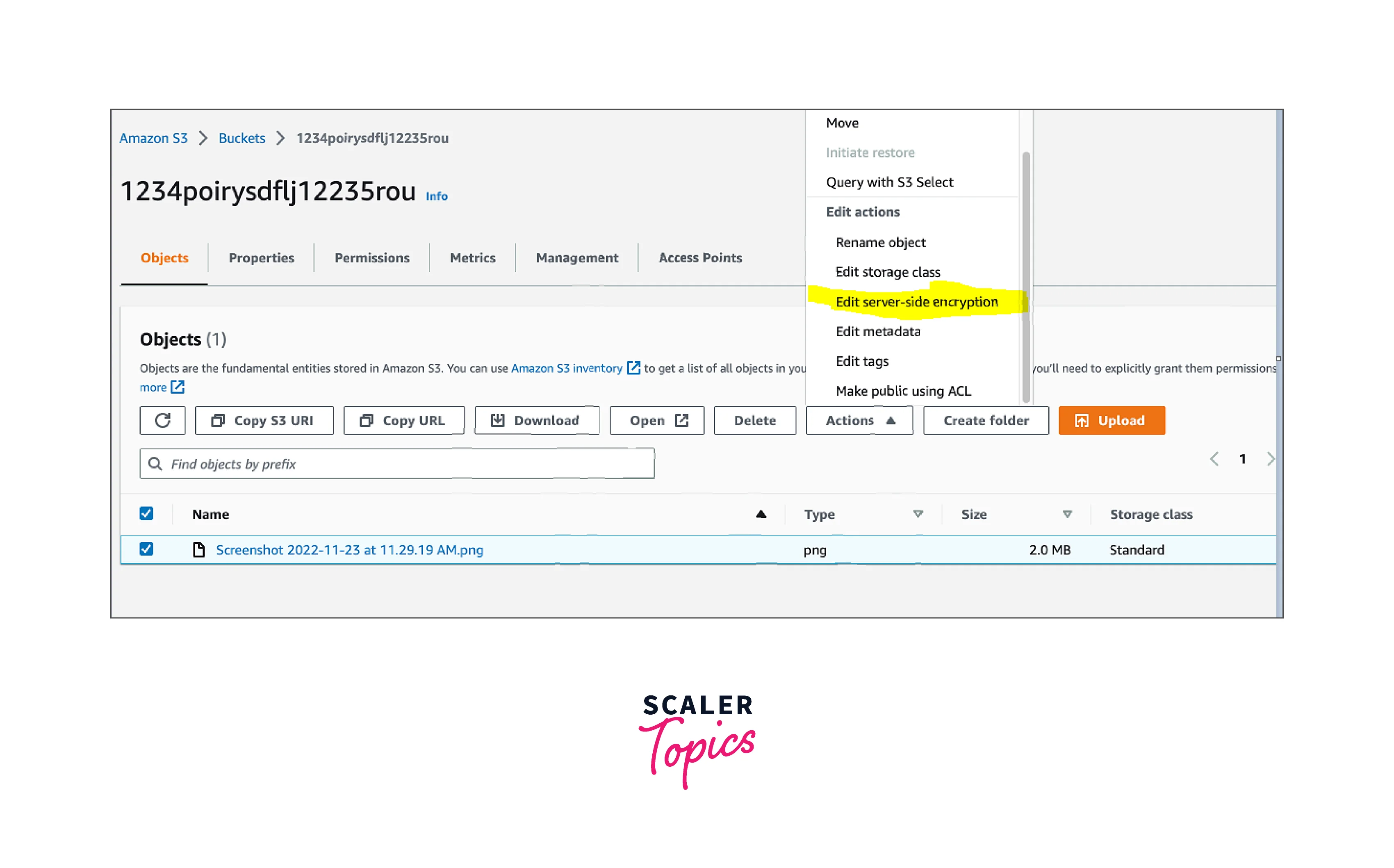
2. In the action menu, we could see "Edit the server-side encryption" and click it.
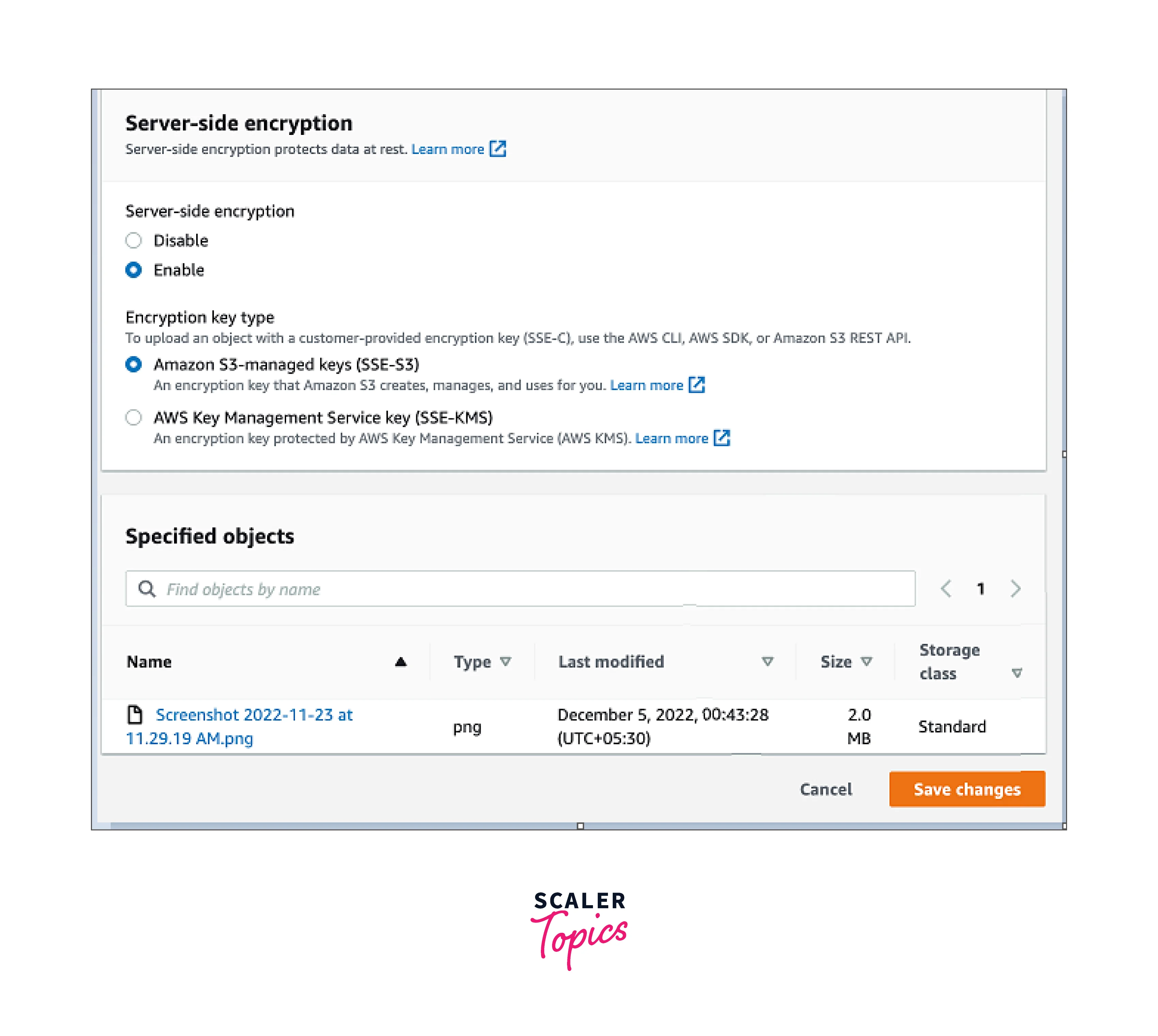
3. It will show us the option to choose the AWS SSE-S3 or AWS SSE-KMS. Choose AWS SSE-S3 and click save.
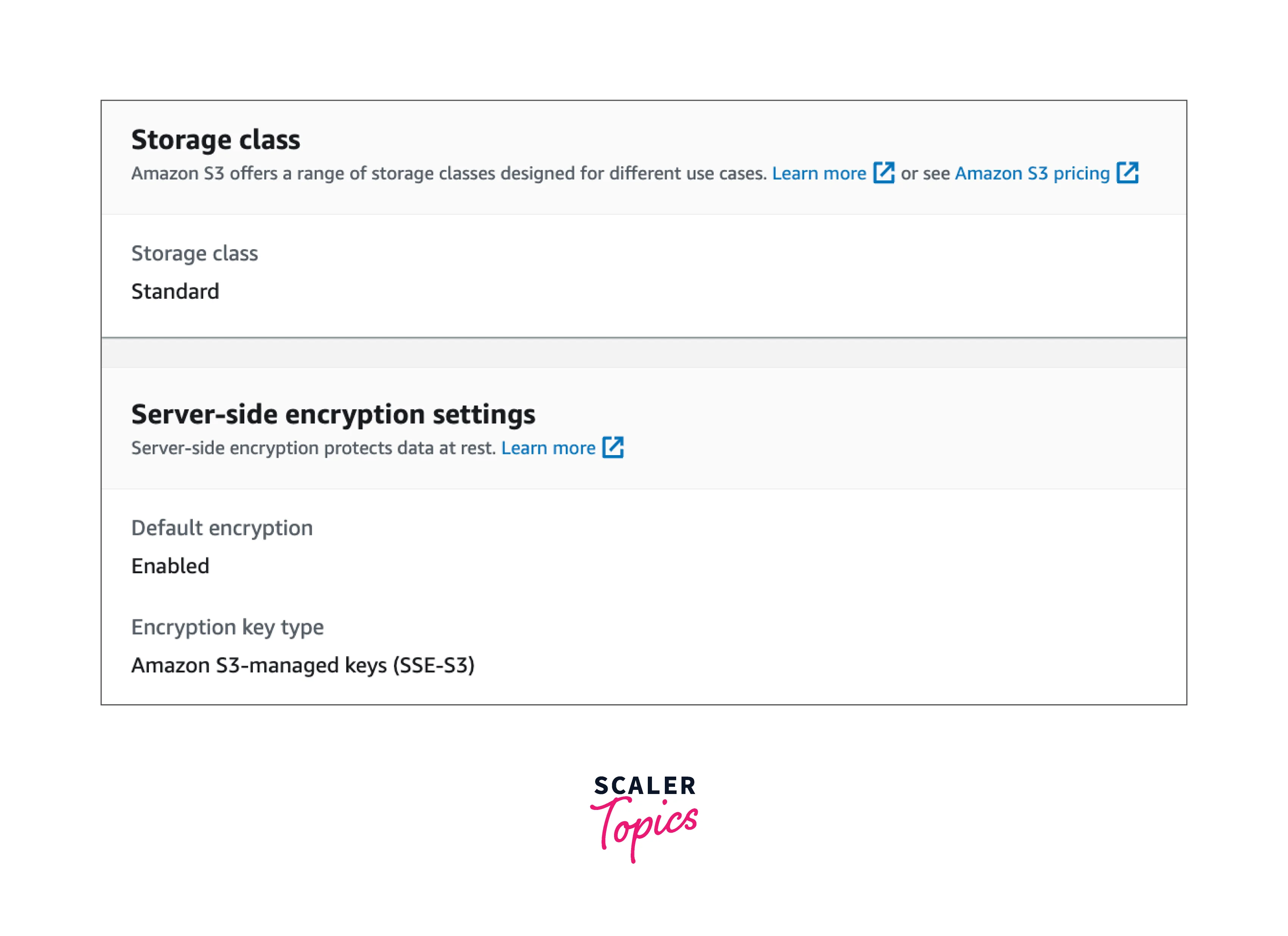
4. We can now see that the object is encrypted with an AWS SSE-S3 key that uses AES-256-bit encryption.
Encrypt an Amazon S3 Bucket
1. Go to the AWS Management Console and choose the S3 service, then select any one of the available S3 buckets.
2. Select properties in the bucket settings and scroll down to find the encryption option.
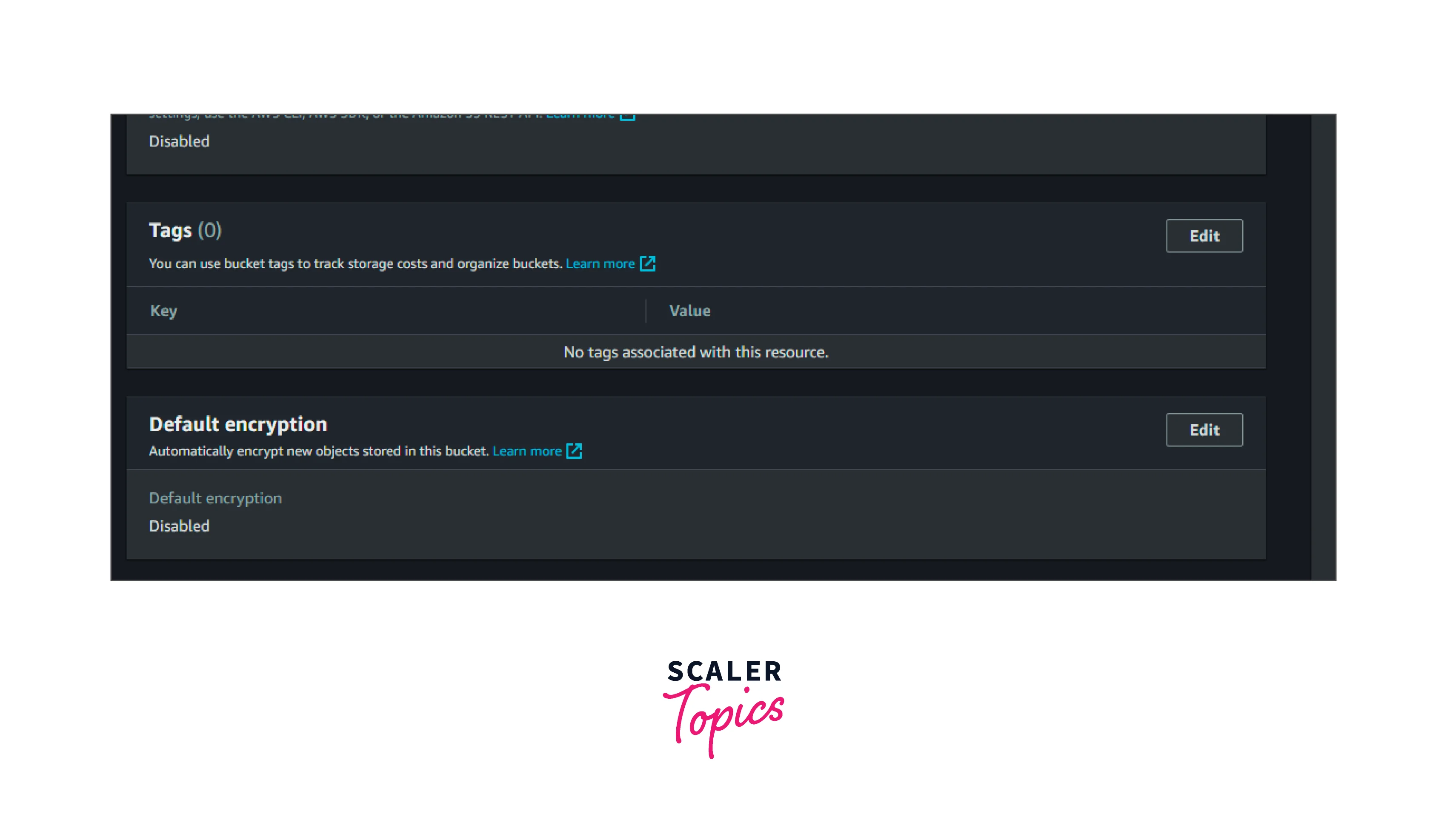
3. Select the edit button and enable the encryption.
4. It will ask us to choose either AWS SSE-S3 or AWS SSE-KMS. Choose AWS SSE-S3 and save it.
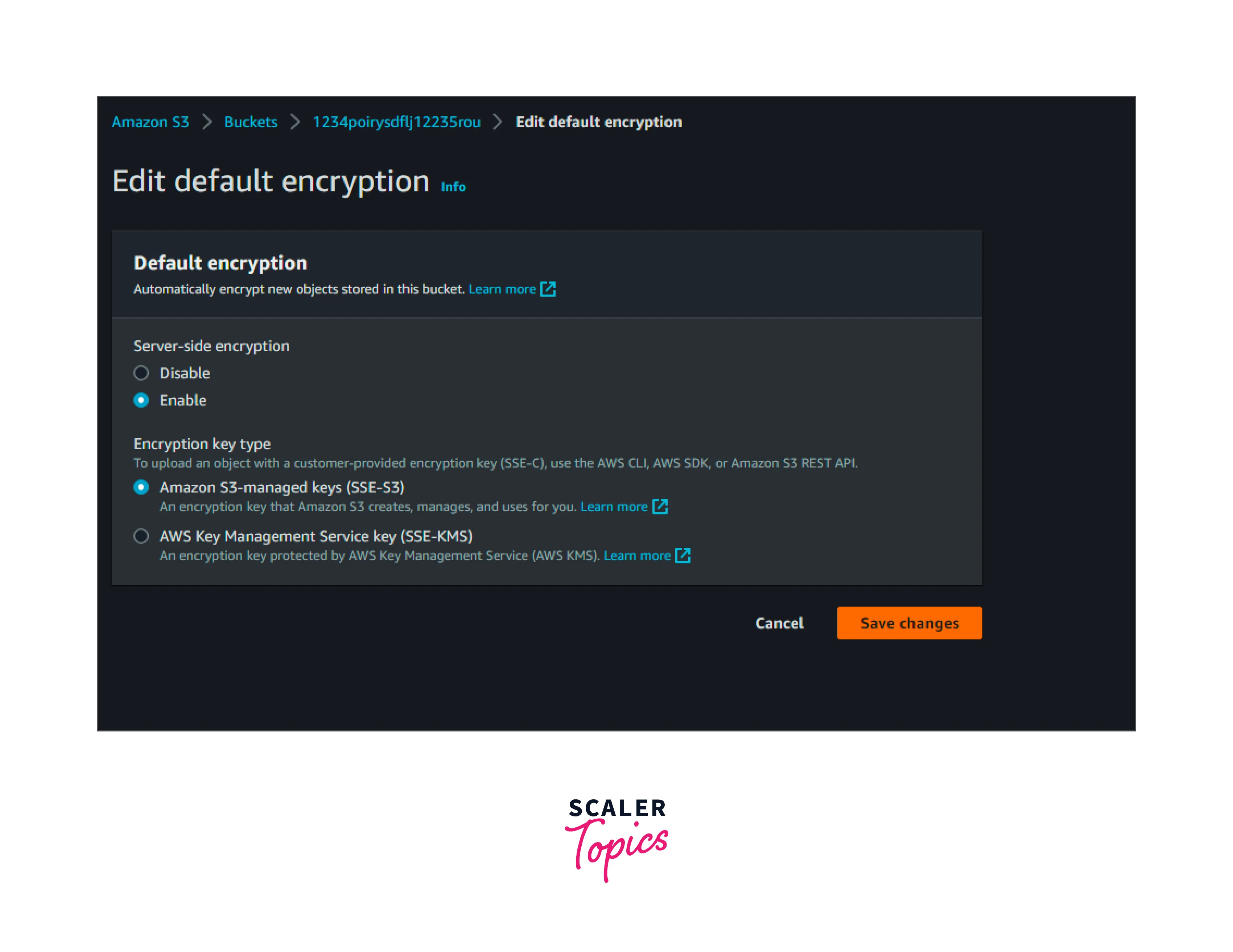
5. Now the bucket is encrypted. All the objects uploaded to that bucket will be encrypted using the AWS SSE-S3 key, which is AES 256-bit encryption.
Conclusion
- Amazon S3 objects are encrypted and stored by default encryption setting in the bucket properties.
- Customers can choose the options available for encryption based on their use case.
- AWS-managed keys are highly available, managed by AWS itself, and rotated regularly.
- Some encryption methods provided by AWS are available free of charge. AWS also allows customers to use their keys to encrypt their data for compliance with regulatory standards.
- Encrypting the data adds another layer of security to the customer's business and reduces the risk of a data breach.
