S3 Object Lock
Overview
Write-once-read-many (WORM) model objects can be stored using S3 Object Lock in AWS. Object locks can prevent items from being removed or overwritten for a set period or indefinitely. Use S3 Object Lock to add a layer of defense against object changes and deletion or to comply with regulatory requirements that call for WORM storage.
What is S3 Object Lock?
S3 Object Lock in AWS is an Amazon S3 feature that enables individuals and organizations to store files in a highly secure, unchangeable manner. It is employed when enterprises must demonstrate that data has not been altered or destroyed after being written, and it is based on the write once, read many (WORM) approaches (WORM).
When they need to prove Compliance or when they need an unalterable, permanent copy of the data for auditing or record-keeping, many businesses rely on S3 Object Lock and WORM.
Ways to Manage Object Retention
Retention Period
- An object version is protected for a specific amount of time during a retention period. When you specify a retention period for an object version, Amazon S3 adds a timestamp to the metadata of the object version to show when the retention period ends.
- Unless you also put a legal hold on the object version, the object version can be overwritten or deleted after the retention term has passed.
- When you explicitly apply a retention term to an object version, you give it a Retain Until Date. The object version is protected by Amazon S3 until the retention time has passed and is stored with the Retain Until Date setting in its metadata.
- The Retain Until Date for the object version is determined when you add an object to the bucket by multiplying the given period by the date of the object version's creation. The metadata for the object version contains the Retain Until Date. The object version is then secured as though a lock with that retention duration had been set on it voluntarily.
Legal Holds
- You can legally hold an object version using Object Lock. A legal hold stops an object version from being replaced or deleted, similar to a retention period. A legal hold, on the other hand, has no related retention time and is in place until it is lifted. Any user with the s3:PutObjectLegalHold permission may freely add and remove legal holds from objects.
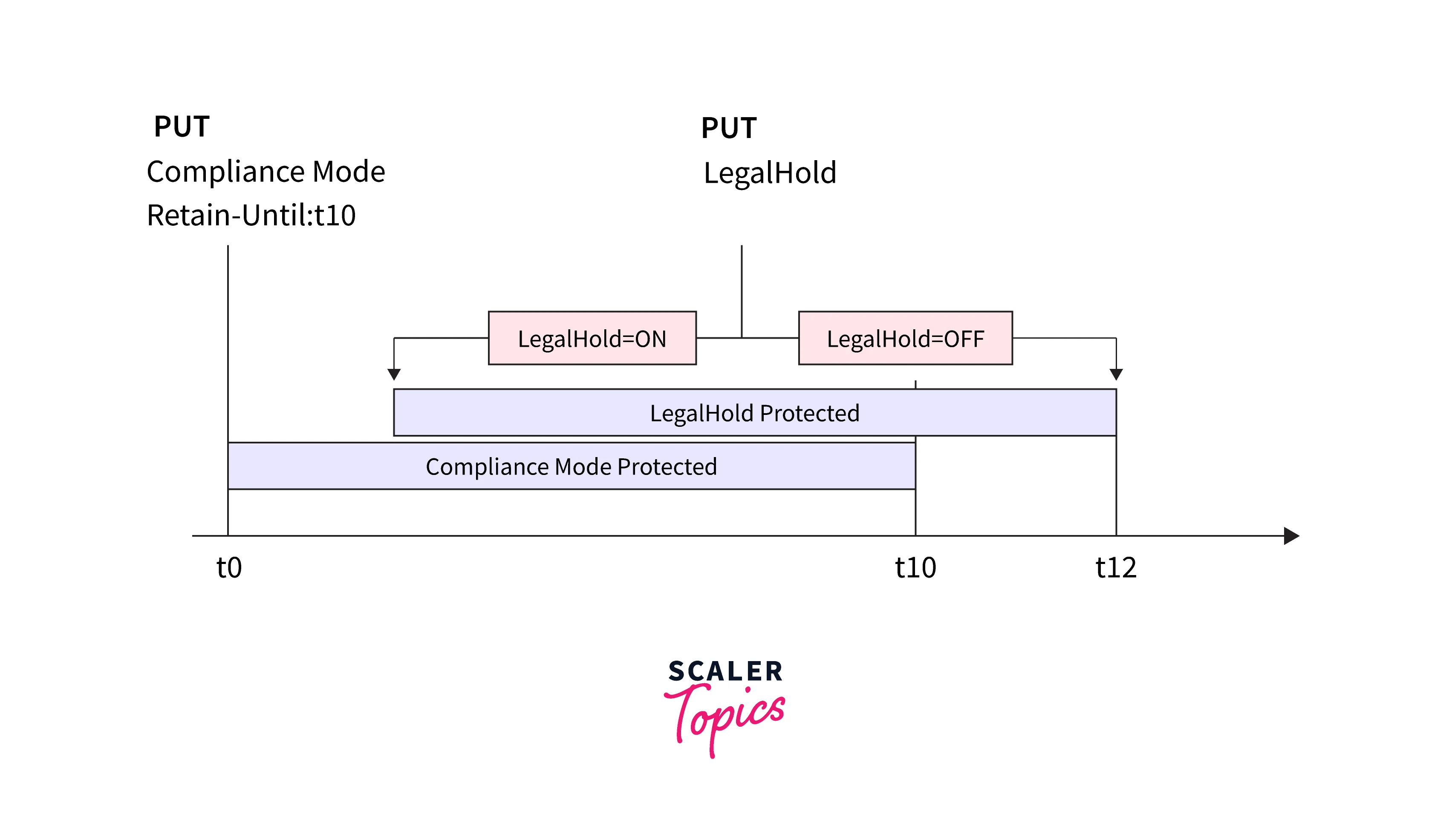
- Retention times have no bearing on legal holds. You can set and delete legal holds regardless of whether the specified object version has a configured retention period as long as the bucket containing the item has Object Lock enabled. The retention mode and retention term for an object version is unaffected by placing a legal hold on it.
How does S3 Object Lock Works?
S3 Object Lock is a component of the object storage method for storing massive amounts of often unstructured data. Unlike fixed-sized block storage or file hierarchy storage systems, object storage organizes material into buckets of various sizes. These additional approaches are not covered by it.
The specifics of how S3 Object Lock functions are complex and have several facets. The steps will be broken down into the parts below.
S3 Object Lock Functionality
- Compared to block storage and file hierarchy storage systems, which we all use on our desktop computers, object storage is less commonly understood (which has been an enterprise storage standard for a while).
- S3 object lock functionality focuses on preventing tampering with objects for a predetermined amount of time (Retention) or indefinitely until you release the lock (legal hold).
- The most straightforward place to implement Object Lock is at the bucket level since with object storage, data is organized into buckets with shared metadata. Users can construct buckets with Object Lock enabled for the entire bucket in S3 environments that support it.
- Then, users can specify the bucket's retention options. According to client agreements or audit regulations, a financial services company can, for instance, specify a retention period of seven years. The data cannot be removed, rewritten, or altered for seven years after the Object Lock is set up. The information may be erased or replaced once the retention period has passed.
- Business users occasionally prefer that particular things not have an expiration date attached to them. Setting a legal hold, which has an indefinite retention term, prevents the item from being removed or overwritten until the customer specifically releases the hold.
S3 Object Lock Protection Mode
There are two Protection Modes for S3 Object Lock.
- Compliance: This is the stricter mode, designed to comply with regulations. Even for the root account, deletions of WORM-protected items are not permitted. Retention settings cannot be relaxed once in Compliance mode; in particular, the retention time duration cannot be shortened and the mode cannot be altered.
- Governance: This is primarily meant to safeguard data against security flaws like accidental deletion, stolen credentials, or rogue actors, especially those who carry out ransomware attacks. It is possible to define a "privileged" delete type that allows the deletion of WORM-protected objects. The protection mode may be elevated to Compliance to modify the retention configuration.
| Governance Mode | Compliance Mode |
|---|---|
| Enforces a legal hold's or retention period's general guidelines | Stricter mode compared to governance |
| Specific users with special authority have the power to temporarily override or modify retention settings. | Data cannot be altered or removed by anyone, not even the root user. |
| For storage that doesn't need to comply, this option is ideal. | Nobody, not even the root user, can change the retention settings. |
| The user must wait until the retention parameters have passed. | |
| Ideal for settings where companies store data that must regularly be monitored for compliance. |
Configuring S3 Object Lock Using the Console
You must first enable a bucket to use S3 Object Lock before you can lock any items in it. When you create a bucket, you turn on Object Lock. You can lock objects in a bucket after you enable object lock for that bucket. You cannot disable or suspend versioning for a bucket that has Object Lock enabled when it is created.
To Enable Object Lock Legal Hold
- Open the Amazon S3 console via https://console.aws.amazon.com/s3/ after logging into the AWS Management Console.
- Select the desired bucket's name from the list of buckets.
- Select the name of the object you wish to enable or disable legal hold for from the Objects list.
- Your object's properties are shown in the Object overview when it first opens.
- Select Edit from the Object Lock legal hold menu.
- Select if Legal hold is enabled or disabled.
- Select Save changes.
To Edit Object Lock Retention Settings
- Select the name of the object whose Object Lock retention settings you want to change from the Objects list.
- Your object's properties are shown in the Object overview when it first opens.
- Select Edit from the Object Lock retention menu.
- Select whether to enable or disable, from Retention.
- Select Governance mode or Compliance mode under Retention mode.
- Enter the day that the object is no longer protected by the selected retention method in the Retain till date box.
- Select Save changes.
Managing S3 Object Lock
You may configure and examine lock information, establish retention limits, manage deletes and lifecycles, and more using the AWS CLI, AWS SDKs, and Amazon S3 REST APIs.
Viewing the Lock Information for an Object
- Using the GET Object or HEAD Object commands, you can check the object lock state of an Amazon S3 object version. For the supplied object version, the retention mode is returned by both commands., Retain Until Date, and the legal-hold status.
- You need to have the s3:GetObjectRetention permission to see the retention mode and duration for an object version. You need to have the s3:GetObjectLegalHold permission to see the legal hold status of an object version. The request is successful if you GET or HEAD an object version but lack the rights to inspect its lock status. It does not, however, return data that you are not authorized to read.
- Request the Object Lock settings for the bucket to view its default retention configuration, if it has one. You need to have the s3:GetBucketObjectLockConfiguration access to accomplish this.
Bypassing Governance Mode
If you have the s3:BypassGovernanceRetention permission, you can conduct operations on object versions that are locked in governance mode as if they were unprotected. These actions include uninstalling an object lock by installing a new lock with no parameters, deleting an object version, or reducing the retention time.
You must expressly state in your request that you want to circumvent the governance mode. To accomplish this, add the x-am-bypass-governance-retention: true header to your request or, for requests made through the AWS CLI or AWS SDKs, use the corresponding option. If you have the authorization necessary to circumvent governance mode, the AWS Management Console automatically adds this header to requests made through the console.
Configuring Events and Notifications
Using Amazon S3 Event Notifications, AWS CloudTrail can track who has access to and modifies your S3 Object Lock settings and data. You may also use Amazon CloudWatch to generate alerts depending on this data.
Setting Retention Limits
Using a bucket policy, you can limit the minimum and maximum retention times for a bucket. The s3:object-lock-remaining-retention-days condition key is used to accomplish this. 100 years is the maximum retention duration.
A bucket policy using S3 can be shown in the example below: To set a maximum retention time of ten days, use the object-lock-remaining-retention-days condition key.
Managing Delete Markers and Object Lifecycles
Although a secured object version cannot be removed, you can still mark it for removal. An object or its object versions are not deleted when a delete marker is placed on the object. However, it causes Amazon S3 to act as though the object has been removed in the majority of situations.
On protected objects, object lifecycle management customizations, such as adding delete marks, continue to work properly. Protected object versions are nevertheless protected from deletion or replacement by a lifetime configuration.
Using S3 Object Lock With Replication
By using S3 Object Lock with Replication, you may automatically and asynchronously copy locked items and associated retention metadata between S3 buckets in the same or separate AWS Regions. The objects in a source bucket are replicated to a destination bucket when replication is used.
Option 1: Activate S3 Object Lock First
- Activate Object Lock on the target bucket, or both the source and the target buckets.
- Establish replication between the source and destination buckets.
Option 2: Establish The Replication First
- Replication between the source and destination buckets should be configured.
- Activate Object Lock on either the source or the target buckets, but not both.
When using one of the aforementioned options, you must either enable Object Lock when creating the bucket or get in touch with AWS Support if you're using an existing bucket. To ensure that replication is configured properly, this is necessary.
Why Should S3 Object Lock be Used?
For the majority of enterprises, using S3 Object Lock is a wise decision. Consider these justifications:
- Defend Files from Unintentional Destruction: Neither purposefully nor mistakenly, it is impossible to delete any files or objects that are in object lock.
- Protect Sensitive Files from Tampering: Even if compliance is not a concern, some files still need to be safe and impenetrable. For instance, object locks will ensure the integrity of any files that might be used as evidence or as part of an audit.
- Show Compliance: Compliance-level object locks are used as evidence of compliance in sectors where observation is essential (such as the medical, financial, etc.).
- Protection Against Ransomware: Threat actors' ransomware threats are essentially pointless if they cannot physically delete your files.
How Does Object Lock Work Against Ransomware?
An effective defence against ransomware assaults is S3 Object Lock. Take into account these six ways that S3 Object Lock might shield your company from this danger.
Compatible With Extra Storage Services for Increased Security
Seagate Lyve Cloud object storage as a service is compatible with S3 Object Lock, an AWS-specific implementation that is also compatible with other storage providers. You'll have more protection in disaster recovery and ransomware scenarios if you diversify your data across several platforms.
Object Lock Protected Data Cannot Be Changed
Threat actors cannot threaten to alter or destroy the data because it is protected by S3 Object Lock and cannot be modified. Even if they get in, the only harm they can do is acquire the knowledge and perhaps spread it.
WORM Creates Added Security
Data protected by S3 Object Lock cannot be altered, overwritten, destroyed, or harmed in any other way because of the WORM concept. The classic air-gap idea, in which actual backup tapes were removed from the premises so they couldn't be accessed or corrupted, is analogous to the WORM capabilities of Linear Tape Open (LTO) tapes.
That idea is transformed into a digital format by WORM. Companies can retrieve data saved in the WORM paradigm and restart, regardless of how devastating an attack is.
No Access by Unauthorized Users to Data
Another issue that many organizations worry about is internal dangers, whether they are deliberate or unintended. Data tampering is not feasible without particular authorization (in governance mode) or at all, regardless of whether the unauthorized user is a member of your organization or an external danger (in compliance mode).
Replaces Tapes and Retrieves Data
By distributing immutable data over the cloud, S3 Object Lock makes LTO tape and air-gapped backups obsolete. Costly tape solutions are no longer required because the cloud handles data storage and retrieval.
Increases the Protection of Your Enterprise Disaster Recovery Plan
S3 Object Lock is a cushion for your company's disaster recovery plan, not a replacement for it. Giving you an additional layer of unchangeable object storage gives you a backup site in case your disaster recovery plan needs to be implemented.
Comparing S3 Object Lock to Legacy Compliance
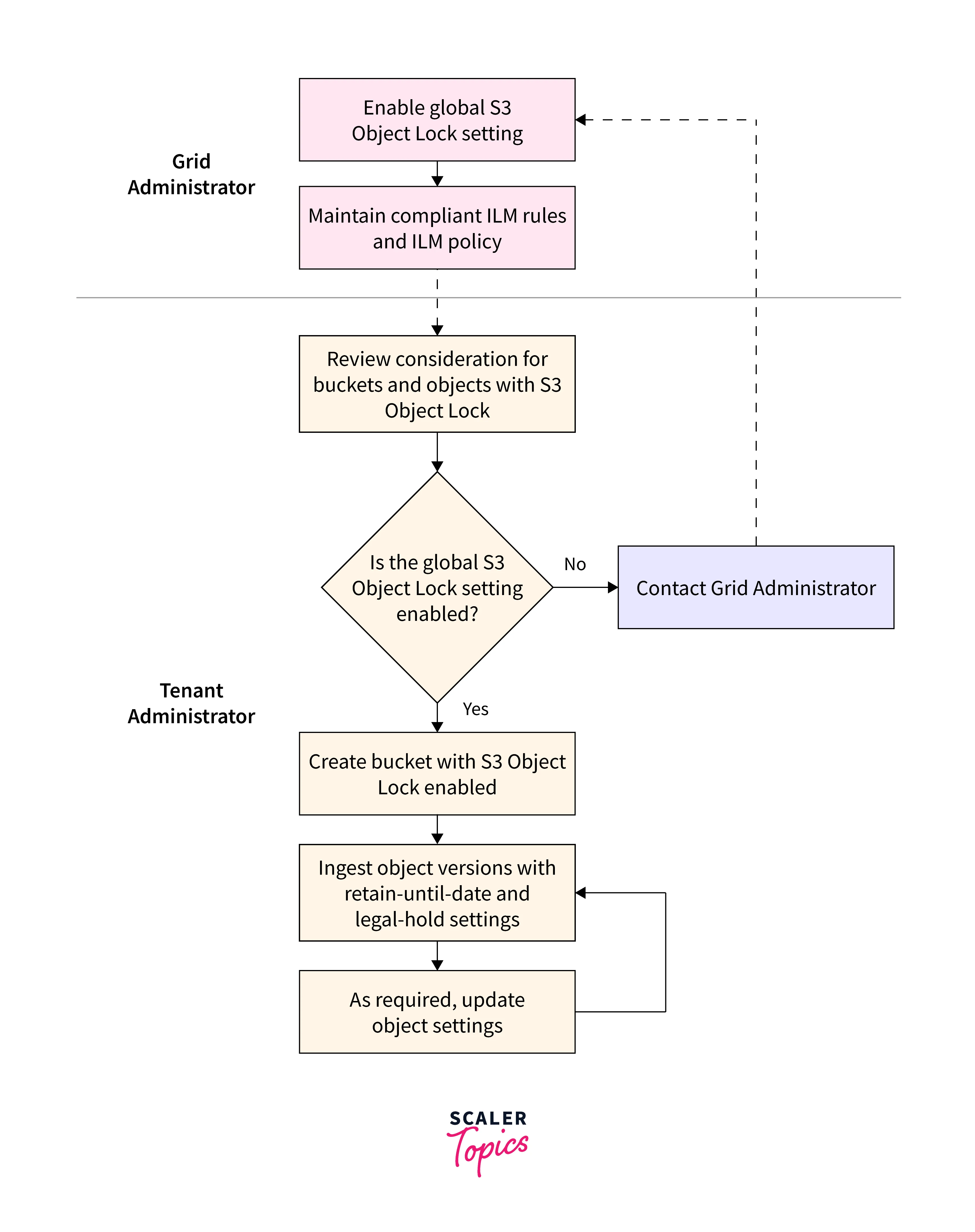
The Compliance function included in prior StorageGRID versions has been replaced by the S3 Object Lock. The proprietary StorageGRID Compliance feature, now referred to as "legacy Compliance," is deprecated because the S3 Object Lock feature complies with Amazon S3 criteria.
The global S3 Object Lock setting was activated automatically if the global Compliance setting had previously been enabled. Tenant users can no longer create new buckets with Compliance enabled. Tenant users can still utilize and maintain any existing historical Compliant buckets, including carrying out the following operations as needed.
- Adding fresh items to a bucket that already has legacy Compliance enabled.
- Increasing the bucket's retention time with legacy Compliance enabled.
- Altering the legacy Compliance enabled auto-delete setting for an active bucket.
- Putting a legal hold on a bucket that is already in use and has legacy Compliance enabled.
- Lifting a judicial ban.
| S3 Object Lock (New) | Compliance (Legacy) | |
|---|---|---|
| How is the feature made available worldwide? | From the Grid Manager, select CONFIGURATION > System > S3 Object Lock. | No longer backed. The S3 Object Lock setting is active in StorageGRID 11.6 if you previously used a version of the software to enable the global Compliance setting. StorageGRID can still be used to control the settings of already existing compliant buckets, but not for the creation of new compliance buckets. |
| For a bucket, how is the feature enabled? | When making a new bucket with the Tenant Manager, Tenant Management API, or S3 REST API, users must enable S3 Object Lock. | Users can still add new objects to already-existing Compliant buckets even when new bucket creation is no longer permitted when Compliance is enabled. |
| Does bucket versioning work? | Yes. Versioning of the bucket is necessary and is initiated when S3 Object Lock is enabled for the bucket. | No. Bucket versioning is not supported by the old Compliance feature. |
| What controls object retention? | Each object version has a retain-until date that users can choose. | Users are required to specify a bucket-wide retention duration. All of the items in the bucket are subject to the retention period. |
| Can a bucket's retention and legal hold default settings be changed? | Yes. For object versions without their retention settings defined after intake, StorageGRID buckets with S3 Object Lock enabled may apply a default retention term. | Yes |
| Can the retention period be adjusted? | An object version's retain-until date can be extended but never lowered. | Although it can never be shortened, the bucket's retention period can be extended. |
| Where is the legal hold managed? | Any object version in the bucket can have a lawful hold put on it or lifted. | All of the items in the bucket are subject to a legal hold that has been imposed on them. |
| When is the object deletable? | An object version can be deleted after the retain-until-date is reached, assuming the object is not under legal hold. | The version of the object may be deleted after the retain-until date has elapsed if it is not the subject of a legal hold. |
| Is bucket lifecycle configuration supported? | Yes | No |
Conclusion
- In this article, We learned about S3 Object Locks. Write-once-read-many (WORM) model objects can be stored using S3 Object Lock. For a set period or indefinitely, object lock can assist in preventing items from being removed or overwritten.
- Two retention options are provided by S3 Object Lock. These are namely Governance mode and Compliance Mode.
- Use the Compliance mode only if you never want any user, including the root user, to have access to your AWS account.
- An object version is protected for a specific amount of time during a retention period.
- You can formally halt an object version using Object Lock. A legal hold stops an object version from being replaced or deleted, similar to a retention period.
- You must enable Object Lock on a bucket to use it. Additionally, you have the option of configuring a default retention setting and time frame for newly added objects to the bucket.
- An effective defence against ransomware assaults is S3 Object Lock.
