Subnets in AWS
Overview
You may divide your resources into logical network segments by creating numerous Subnets in AWS. As a result, you might have separate Subnets for web infrastructure, application servers, and database instances. It is simpler to implement a greater level of security with this type of subnet separation. You may keep your infrastructure's administration simple by logically grouping related resources.
What are Subnets in AWS
Does your house have one room? Your home includes several rooms since each one has a distinct function, such as a kitchen, living room, dining room, etc. Consider them to be subnets. Instead of having one enormous area where you can cook, clean, and sleep, which would quickly become quite disconnected, the space in your home, your CIDR block, has been divided into smaller, more manageable, purpose-specific spaces.

Subnet Basics
The term subnet describes an IP address range in your VPC. AWS resources, like EC2 instances, may be started in a certain subnet. The IPv4 CIDR block, which is a subset of the VPC CIDR block, is specified when you construct a subnet.
Each subnet cannot span more than one Availability Zone and must be located fully inside that zone. Your applications can be safeguarded against the failure of a single Availability Zone by running instances in several zones.
In a Local Zone, an AWS infrastructure deployment that moves computing, storage, databases, and other selected services closer to your end customers, you can choose to add subnets. Your end users can execute programs requiring single-digit millisecond latencies in a Local Zone.
Subnet Types
Subnets are classified as public, private, or VPN-only depending on how your VPC is configured:
- Public subnet: Through an internet gateway or an egress-only internet gateway, the subnet traffic is sent to the public internet. See Connect to the internet using an Internet Gateway for further details.
- Private subnet: Traffic from the subnet cannot pass via an internet gateway or an egress-only internet gateway to access the public internet. A NAT device is necessary for internet access to other users.
- VPN-only subnet: Via a virtual private gateway, the subnet traffic is sent to a Site-to-Site VPN connection. Through an Internet gateway, subnet traffic cannot access the general Internet.
Depending on how the VPC is set up, you must give the IP addresses of a subnet when creating one:
- The subnet only has an IPv4 CIDR block; there is no IPv6 CIDR block. An IPv4-only subnet's resources must use IPv4 for communication.
- Dual Stack: The subnet has a CIDR block for IPv4 and a CIDR block for IPv6. Both an IPv4 CIDR block and an IPv6 CIDR block must exist in the VPC. A dual-stack subnet's resources support IPv4 and IPv6 communication.
- The subnet only has an IPv6 CIDR block; there is no IPv4 CIDR block. IPv6 CIDR block must be present in the VPC. An IPv6-only subnet requires IPv6 communication between resources.
The internal IPv4 address range of the subnet is always private, regardless of the kind of subnet, we do not disclose the address block to the internet.
Subnet Settings
Each subnet has a changeable characteristic that controls whether network interfaces built there receive public IPv4 addresses and, if necessary, IPv6 addresses. When you launch an instance on that subnet, the principal network interface (eth0) is also generated for the instance. You can alter this parameter for a given instance at launch, regardless of the subnet characteristic. The following subnet parameters are modifiable once the subnet has been created.
- You can specify the auto-assign IP settings so that each new network interface in this subnet will automatically request a public IPv4 or IPv6 address.
- Setting for Resource-based Names (RBN): enables you to control how DNS A and AAAA record inquiries are handled as well as the hostname type for EC2 instances in this subnet.
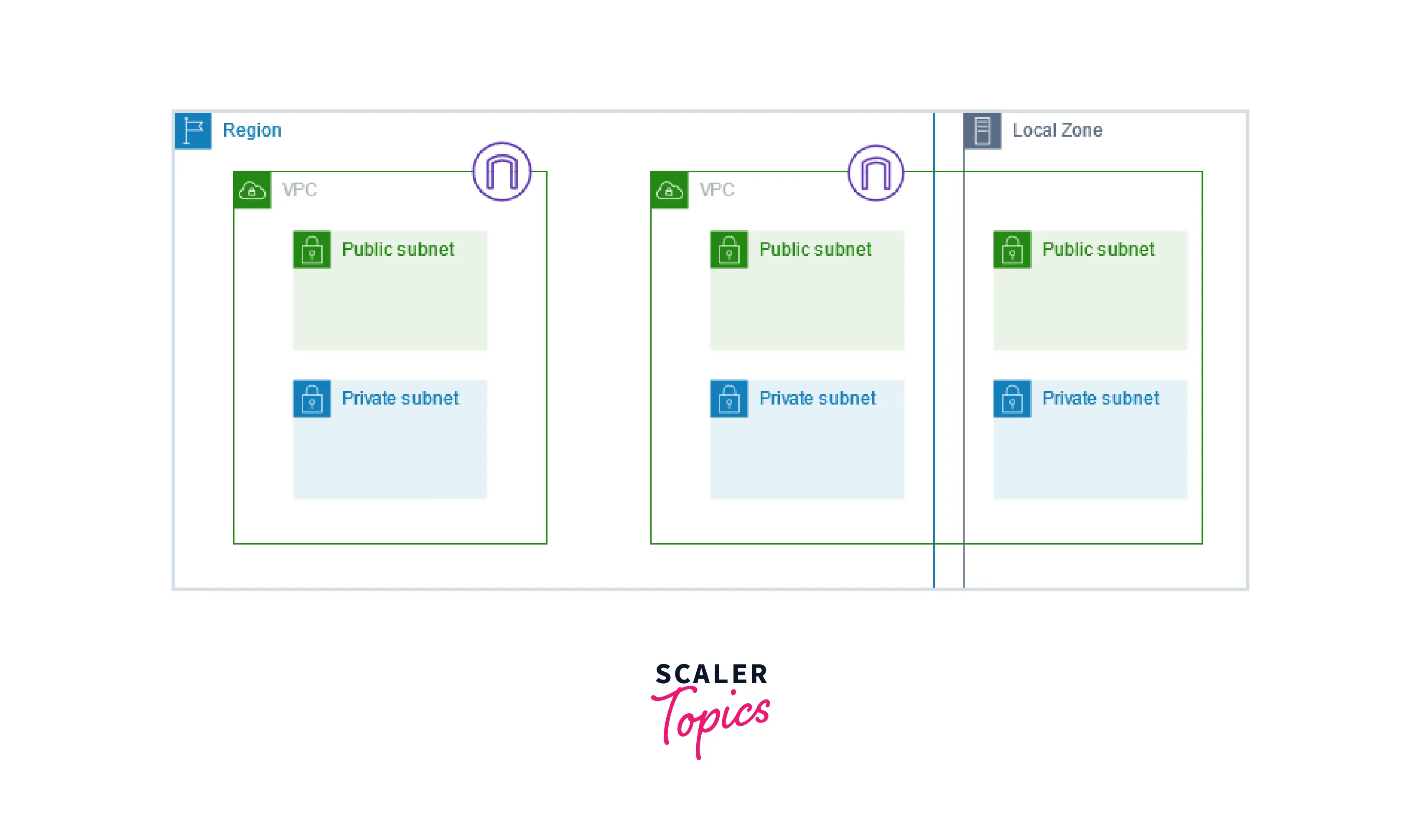
Subnet Diagram
Two VPCs in a Region are depicted in the diagram below. There is an internet gateway, public and private subnets, and a VPC for each. The VPC includes a Local Zone as well.
Subnet Sizing
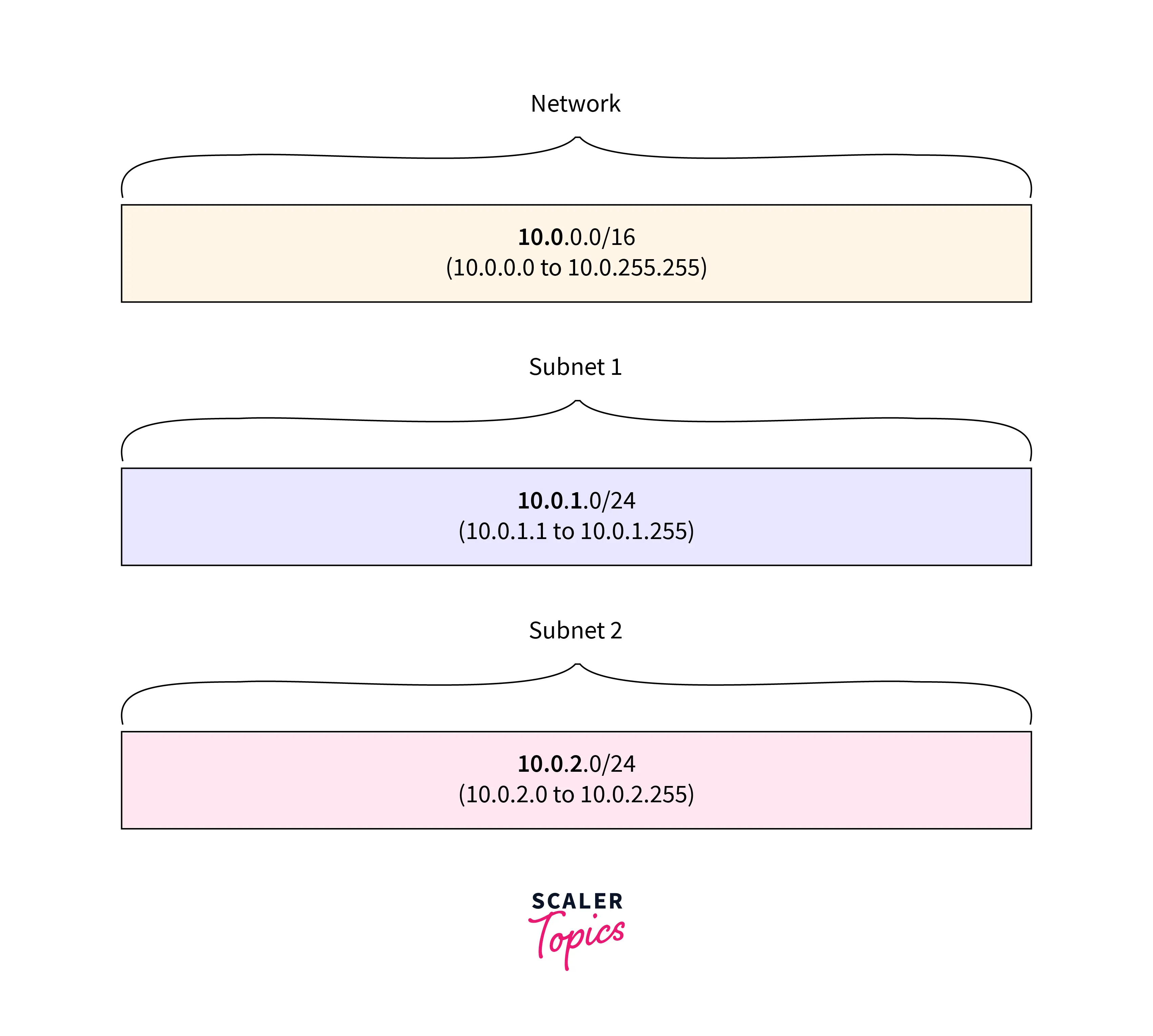
The CIDR block of a subnet within a VPC may match the VPC's CIDR block exactly or it may be a subset of the VPC's CIDR block for a single subnet (to create multiple subnets in the VPC). The range of the permitted block size is from a /28 netmask to a /16 netmask. The CIDR blocks of the subnets cannot cross over if more than one subnet is created in a VPC.
It allows 256 IP addresses, for instance, if you build a VPC with the CIDR block 10.0.0.0/24. This CIDR block may be divided into two subnets, each of which can accommodate 128 IP addresses. For addresses 10.0.0.0 - 10.0.0.127, one subnet uses CIDR block 10.0.0.0/25, while the other uses CIDR block 10.0.0.128/25. (for addresses 10.0.0.128 - 10.0.0.255).
The creation and calculation of IPv4 subnet CIDR blocks can be aided by online tools. By looking up phrases like subnet calculator or CIDR calculator, you might locate tools that are suitable for your needs. You can get assistance from your network engineering team in choosing the CIDR blocks that should be used for your subnets.
You cannot utilize or assign the first four IP addresses and the final IP address in each subnet CIDR block to a resource, such as an EC2 instance. The following five IP addresses, for instance, are reserved in a subnet with the CIDR block 10.0.0.0/24:
- Network address 10.0.0.0.
- AWS has reserved 10.0.0.1 for the VPC router.
- AWS has reserved 10.0.0.2. The base of the VPC network range plus two is the DNS server's IP address. The principal CIDR of a VPC that has several CIDR blocks contains the IP address of the DNS server. For all CIDR blocks in the VPC, we additionally reserve the base of each subnet range plus two. Check out the Amazon DNS server for further details.
- 10.0.0.3: An AWS reservation for future usage.
- Network broadcast address: 10.0.0.255. Since broadcasting is not supported in a VPC, we reserve this address. The CIDR block is automatically changed to its canonical form if you create a subnet using a command-line tool or the Amazon EC2 API. For instance, if you enter 100.68.0.18/18 for the CIDR block, we generate a 100.68.0.0/18 CIDR block.
IPv6 Subnet Sizing
You can associate an IPv6 CIDR block with an existing subnet in your VPC or when you build a new subnet if you've already done so with your VPC. The IPv6 CIDR block of a subnet has a fixed prefix length of /64.
You may use online calculators and creation tools, such as IPv6 Address Planner, to compute and generate IPv6 subnet CIDR blocks. Search for phrases like IPv6 subnet calculator or IPv6 CIDR calculator to locate further resources that meet your needs. You may also get assistance from your network engineering team in choosing the IPv6 CIDR blocks that should be used for your subnets. You cannot use or assign an EC2 instance with the first four IPv6 addresses and the final IPv6 address in each subnet CIDR block. A subnet with the CIDR block 2001:db8: 1234:1a00/64, for instance, has the following five IP addresses reserved:
Subnet Routing
Each VPC by default has one route table that is already set up with a local route. The local route is only applicable to the subnet that has been configured for the whole VPC. Your local route would be specified as 172.16.0.0/16, for instance, if your VPC was configured with an address space of 172.16.0.0/16. This enables seamless communication between all resources generated within the VPC without the need for extra setup. The local route cannot be removed from your route table, and it always appears by default when a new route table is built inside a VPC.
Route tables are given to certain subnets within a VPC. All of the subnets in a VPC would be allocated to the single route table that was constructed. In a VPC, you have the option of creating more than one route table or just sticking with the default one.
Subnet Security
Security groups and network ACLs are two capabilities offered by AWS that you may utilize to improve security in your VPC. Network ACLs manage inbound and outbound traffic for your subnets, whereas security groups manage inbound and outbound traffic for your instances. Security groups may often satisfy your needs, but if you want an extra layer of protection for your VPC, you can also employ network ACLs.
Each subnet is required to have a network ACL by design. Each subnet you build is immediately connected to the VPC's default network ACL. Both the association and the default network ACL's content are revocable.
To record the traffic that goes to and from the network interfaces in your VPC or subnet, you may build a flow log on that network. On a specific network interface, a flow log can also be produced.
Creating, Viewing, and Deleting Your Subnets
Creating A Subnet
You must choose an IPv4 CIDR block for the subnet from your VPC's range to add it to your network. The Availability Zone in which you wish the subnet to live might be specified. The same Availability Zone can house numerous subnets.
Conditions
- If there is an IPv6 CIDR block connected to the VPC, you can optionally provide one for a subnet.
- You should be aware of the following if you construct an IPv6-only network. When an EC2 instance is started on a subnet that only supports IPv6, it only obtains an IPv6 address. Any instances that you start in an IPv6-only subnet must be Nitro System instances.
- You must activate the Zone in order to construct the subnet in a Local Zone or Wavelength Zone.

STEPS TO CREATE A SUBNET
- Open the Amazon VPC console at here to add a subnet to your VPC.
- Select Subnets from the navigation pane.
- Select Create subnet.
- Choose the VPC for the subnet as the VPC ID.
- Enter the name of your subnet under the Subnet name. By doing this, you produce a tag with the key Name and the value you provide.(Optional)
- You can select a Zone for your subnet's availability zone, or you can leave the setting at the default No Preference and let AWS pick one for you.
- Select IPv6-only if the network should only use IPv6. This option is only accessible if the VPC is linked to a particular IPv6 CIDR block. If you select this option, the subnet cannot be linked to an IPv4 CIDR block.
- Enter the IPv4 CIDR block for your subnet under the IPv4 CIDR block. 10.0.1.0/24, as an example. Detailed information is available at VPC size for IPv4. This choice is not accessible if IPv6-only was selected.
- Select Custom IPv6 CIDR and enter the hexadecimal pair value for the IPv6 CIDR block (for example, 00). Only if the VPC has an associated IPv6 CIDR block is this option available.
- Select Create subnet.
Configurations options
A subnet may be set up as follows after creation:
- Configure routing: The traffic may then be routed to a gateway connected to the VPC, such as an internet gateway, using a custom route table that you can construct. See Configure route tables for further details.
- Change the way IP addresses are handled. If instances are launched in the subnet, you can specify whether they get a public IPv4 address, an IPv6 address, or both. See Subnet settings for further details.
- Change the parameters for resource-based names (RBN). See Amazon EC2 instance hostname types for further details.
- Create or change the ACLs on your network. See Control traffic to subnets with network ACLs for additional details.
- Join other accounts on the subnet. See Share a subnet for additional details.
Viewing A subnet
- Navigate here to access the Amazon VPC console.
- Select Subnets from the navigation pane.
- To access the detail page, either choose the subnet's checkbox or its ID.
- For a global view of your subnets, go here to access the Amazon EC2 Global View console.
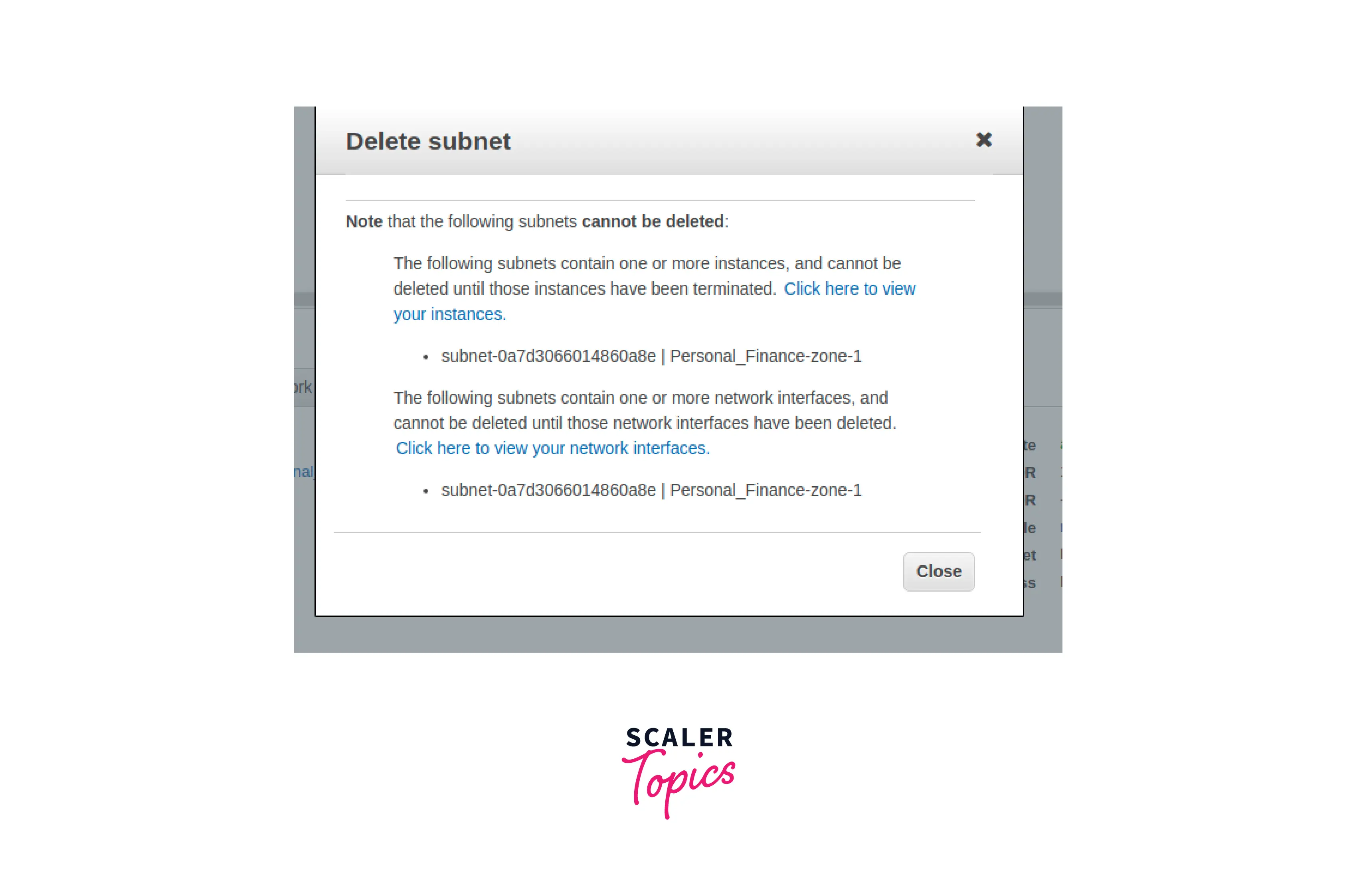
Deleting A subset
- Navigate here to access the Amazon VPC console.
- Select Subnets from the navigation pane.
- To access the detail page, either choose the subnet's checkbox or its ID.
- For a global view of your subnets go here to access the Amazon EC2 Global View console.
Conclusion
- The term subnet describes an IP address range in your VPC. Subnets may be connected to AWS services like EC2 instances and RDS DB instances.
- To organize instances into groups according to your operational and security needs, you may construct subnets.
- Depending on how your VPC is set up, subnets might be public, private, or VPN-only.
- A modifiable property of each subnet determines whether network connections created there are assigned public IPv4 addresses and if required, IPv6 addresses.
- The CIDR block of a subnet within a VPC may match the VPC's CIDR block exactly, or it may be a subset of the VPC's CIDR block (to create multiple subnets in the VPC).
- You can associate an IPv6 CIDR block with an existing subnet in your VPC or when you build a new subnet if you've already done so with your VPC.
