VPC Peering
Overview
A networking connection known as a VPC peering link allows you to transport traffic between two VPCs using private IP addresses. You can use VPC peering to deploy cloud resources in a user-defined virtual network. VPCs allow communication between instances just as if they were on the same network. These resources allow for the more secure transport of data.
What is VPC Peering, and How Does It Work?
VPC peering is a method of connecting two or more virtual private clouds (VPCs). A VPC peering connection is defined as "a networking link between two VPCs that enables traffic to be sent using private IPv4 (or) IPv6 addresses." Instances in VPC can communicate with each other as if they were on the same network once joined through a VPC peering connection.
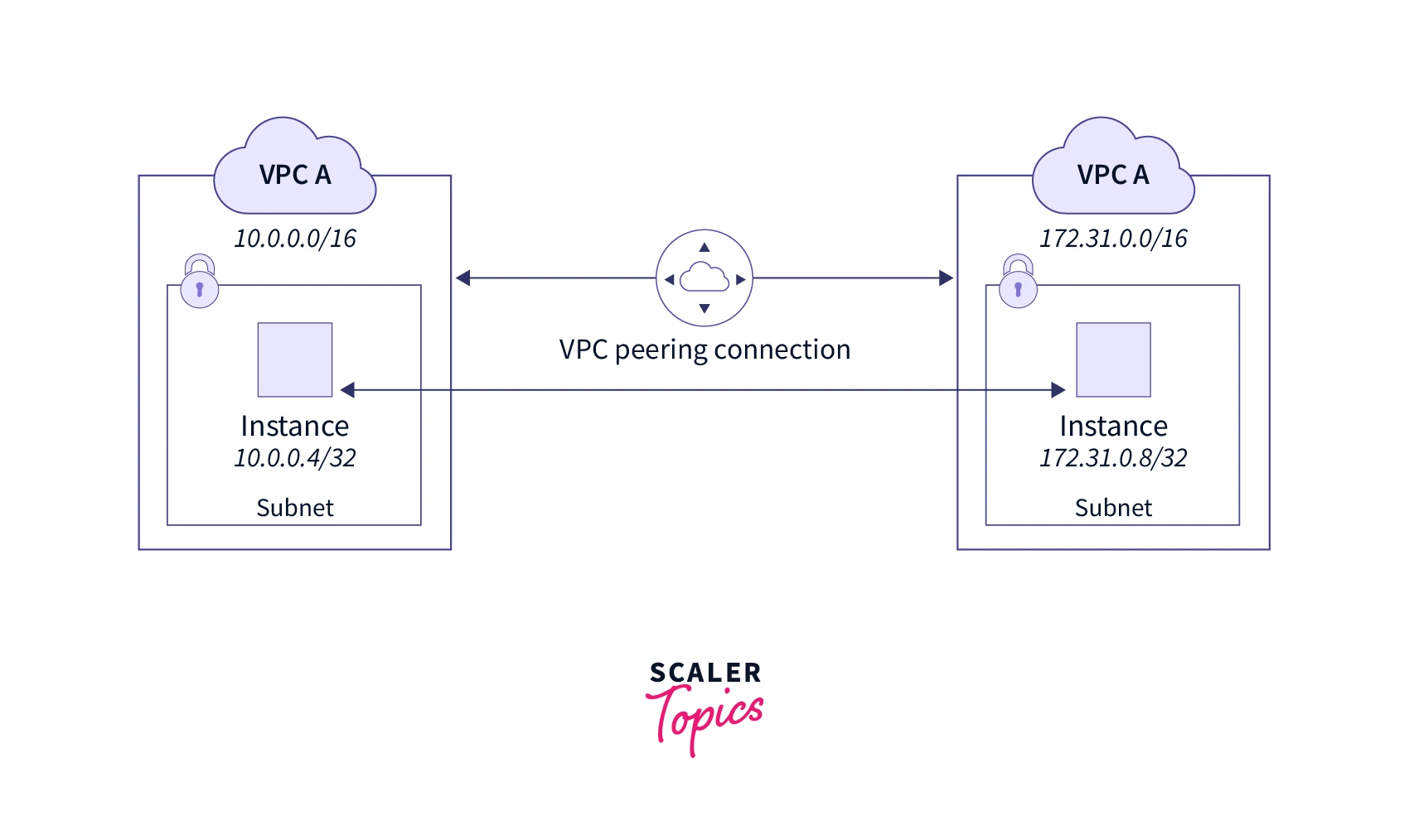
AWS creates a VPC peering connection using the current architecture of a VPC; it is neither a gateway nor a VPN connection, and it does not require any additional physical hardware. In communication, there is no single point of failure (or) bandwidth limitation.
You must perform the following to establish a VPC peering connection:
- The owner of the requester VPC asks the owner of the accepter VPC to create a VPC peering connection. You (or) another AWS account can control the accepter VPC, but it cannot have a CIDR block that is identical to the CIDR block of the requester VPC.
- The accepter VPC's owner approves the VPC peering connection request to initiate the VPC peering connection.
- The owner of each VPC in the VPC peering connection must manually add a route pointing to the IP address range of the other VPC to one (or) more of their VPC route tables in order to permit traffic between VPCs using private IP addresses.
- To make sure that traffic to and from the peer VPC is not restricted, update the security group rules related to your instance as necessary. You can utilize a security group from the peer VPC as a source (or) destination in your security group rules if both VPCs are in the same region.
- When utilizing the default VPC peering connection parameters, a public DNS hostname is used by EC2 instances to the instance's public IP address. To change this behavior, enable DNS hostname resolution for your VPC connection. After DNS hostname resolution is enabled, if instances on either side of the VPC peering connection address one another using a public DNS hostname, the hostname resolves to the instance's private IP address.
Key Properties of VPC Peering
- A VPC peering connection helps you to increase data flow speed. If you possess several AWS accounts, for example, you can peer the VPCs across numerous accounts to build a file-sharing network. A VPC peering connection is used to allow other VPCs to access resources in one of your VPCs.
- Peering links were established between VPCs in various AWS Regions (also called inter-Region VPC peering). This enables VPC resources such as EC2 instances, Amazon RDS databases, and Lambda functions running in multiple AWS Regions to interact, utilizing private IP addresses without needing gateways, VPN connections, or other network equipment.
- The traffic is still contained within the private IP space. There is no single failure or bandwidth bottleneck point in all inter-region traffic.
- Traffic is routed through the global AWS backbone rather than the public internet, reducing dangers such as typical vulnerabilities and distributed denial-of-service (DDoS) assaults.
- Inter-Region VPC Peering is a simple and cost-effective technique to share resources or replicate data for regional redundancy.
Restrictions of VPC Peering
Take note of the following constraints and requirements while creating a VPC peering connection with another VPC:
- A VPC peering connection between VPCs with equal (or) overlapping IPv4 (or) IPv6 CIDR (Classless Inter-Domain Routing) blocks cannot be established. Amazon always allocates a unique IPv6 CIDR block to your VPC. You cannot establish a peering connection if your IPv6 CIDR blocks are unique, but your IPv4 blocks are not.
- You are limited to a certain amount of active and pending VPC peering connections per VPC.
- VPC peering does not allow transitive peering relationships. Your VPC does not have access to other VPCs with which the peer VPC may be peered via a VPC peering connection. VPC peering connections built exclusively inside your AWS account are included. Unsupported VPC peering settings provide further information about unsupported peering partnerships.
- Unicast reverse path forwarding is not supported in VPC peering connections.
- You can allow resources on either side of a VPC peering connection to communicate over IPv6; however, IPv6 is not widely used.
- Although it is not automatically possible, resources on either side of a VPC peering connection can interact via IPv6. An IPv6 CIDR block must be assigned to each VPC, IPv6 communication must be enabled for the VPC instances, and routes that route IPv6 traffic intended for the peer VPC to the VPC peering connection must be added to your route tables.
- Any tags you make for your VPC peering connection are only valid in the account or area where they are created.
- Private DNS hostnames for that VPC cannot be resolved to private IP addresses if the IPv4 CIDR block of that VPC in a VPC peering connection falls outside the IPv4 address ranges established by RFC 1918. You can activate the DNS resolution capability for the VPC peering connection to resolve private DNS hostnames to private IP addresses.
- A peer VPC's Amazon DNS server cannot be accessed or queried.
Additional constraints applied to an inter-region VPC peering connection:
- A security group rule that refers to a peer VPC security group cannot be created.
- You cannot enable communication with a peer VPC for an EC2-Classic instance attached to a VPC using ClassicLink.
- The Maximum Transmission Unit (MTU) via the Regions VPC peering connection is 1500 bytes. For inter-Region VPC peering connections, jumbo frames (MTUs up to 9001 bytes) are not supported. However, they are supported for VPC peering connections within the same region.
- Even though the IPv4 CIDR for the VPC falls inside the private IPv4 address ranges described by Remote Function Call(RFC), you must enable DNS resolution support for the VPC peering connection to resolve private DNS hostnames of the peered VPC to private IP addresses.
Getting Started with VPC Peering
Create a VPC Peering Connection with Another VPC in Your Account
The user must execute activities like creating and accepting the VPC peering connection in order to establish the connection. This requires the user to have the necessary VPC IDs. Connections may be established in the same Region (or) another.
To establish a peering relationship with a VPC inside the same region:
- Navigate here to access the Amazon VPC console.
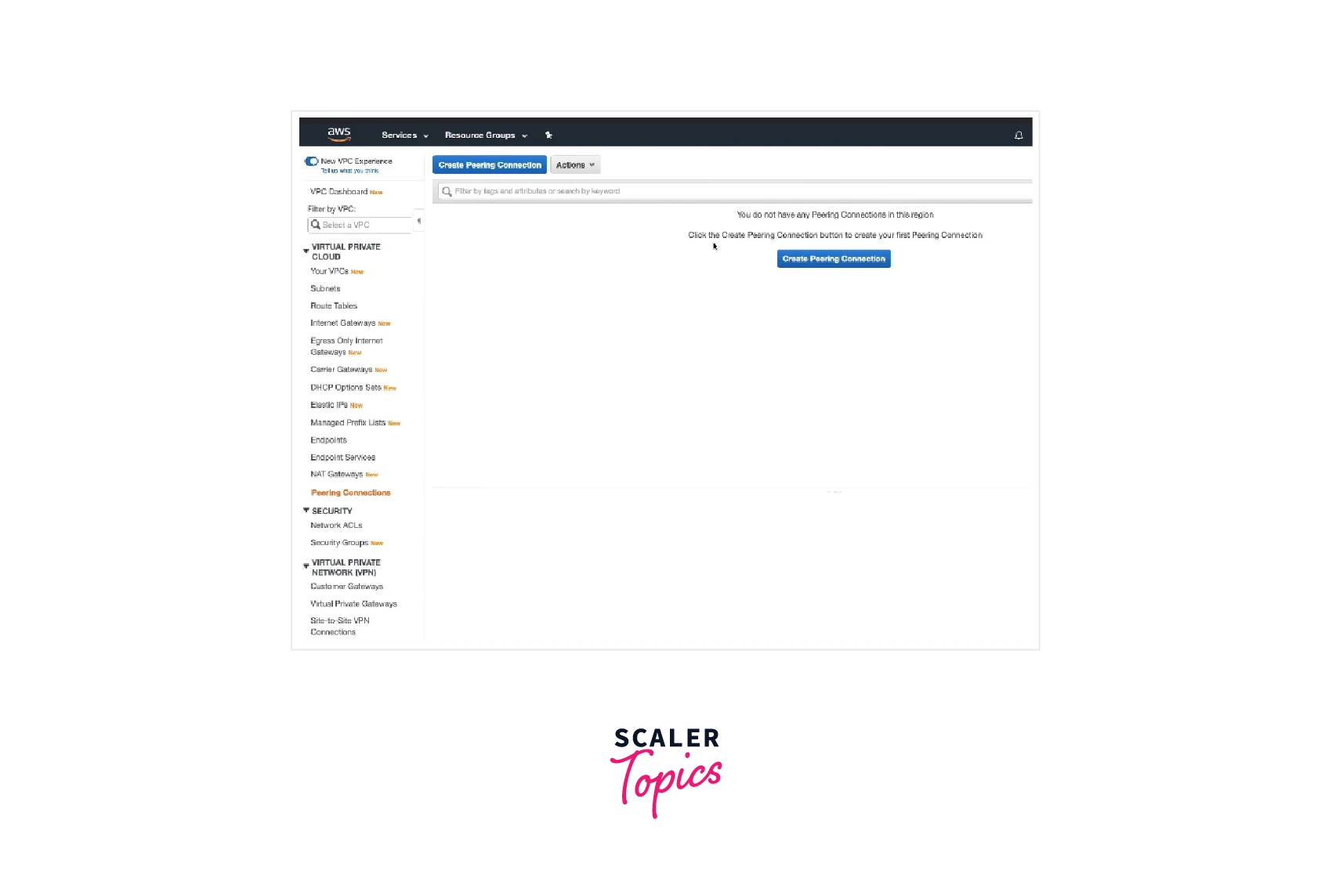
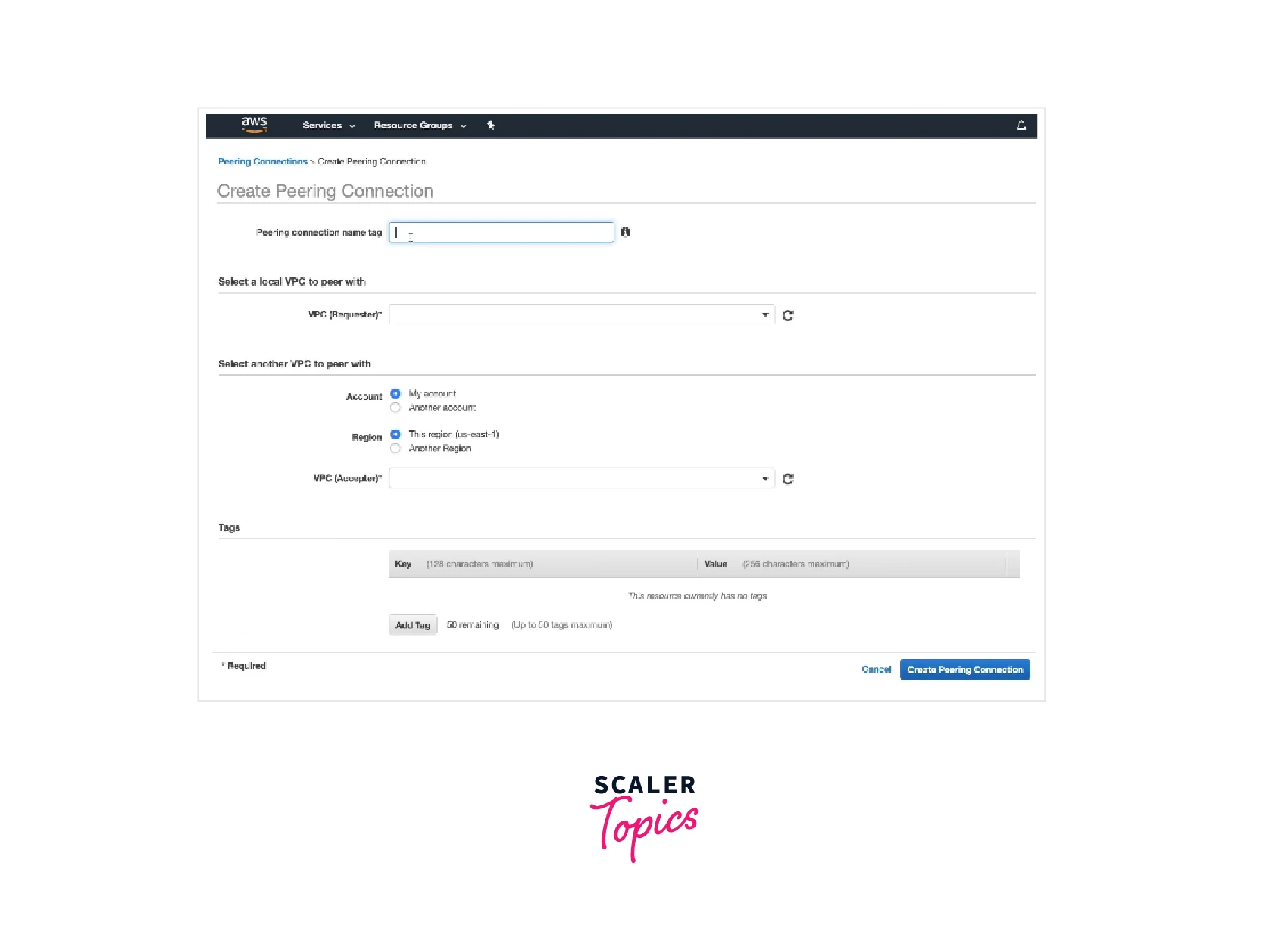
- Select Peering Connections, and Create Peering Connection from the navigation bar.
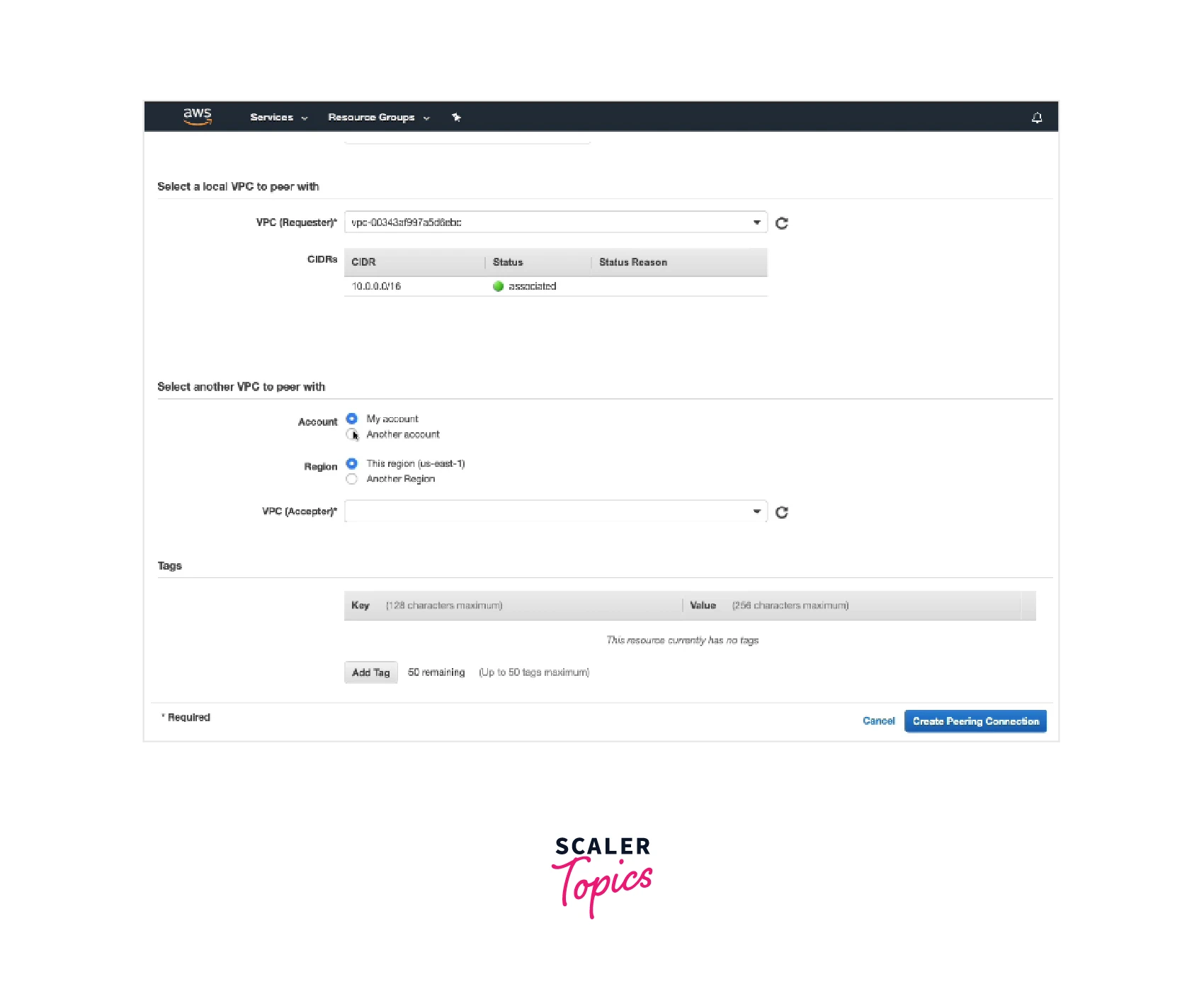
- After configuring the following details, select Create Peering Connection.
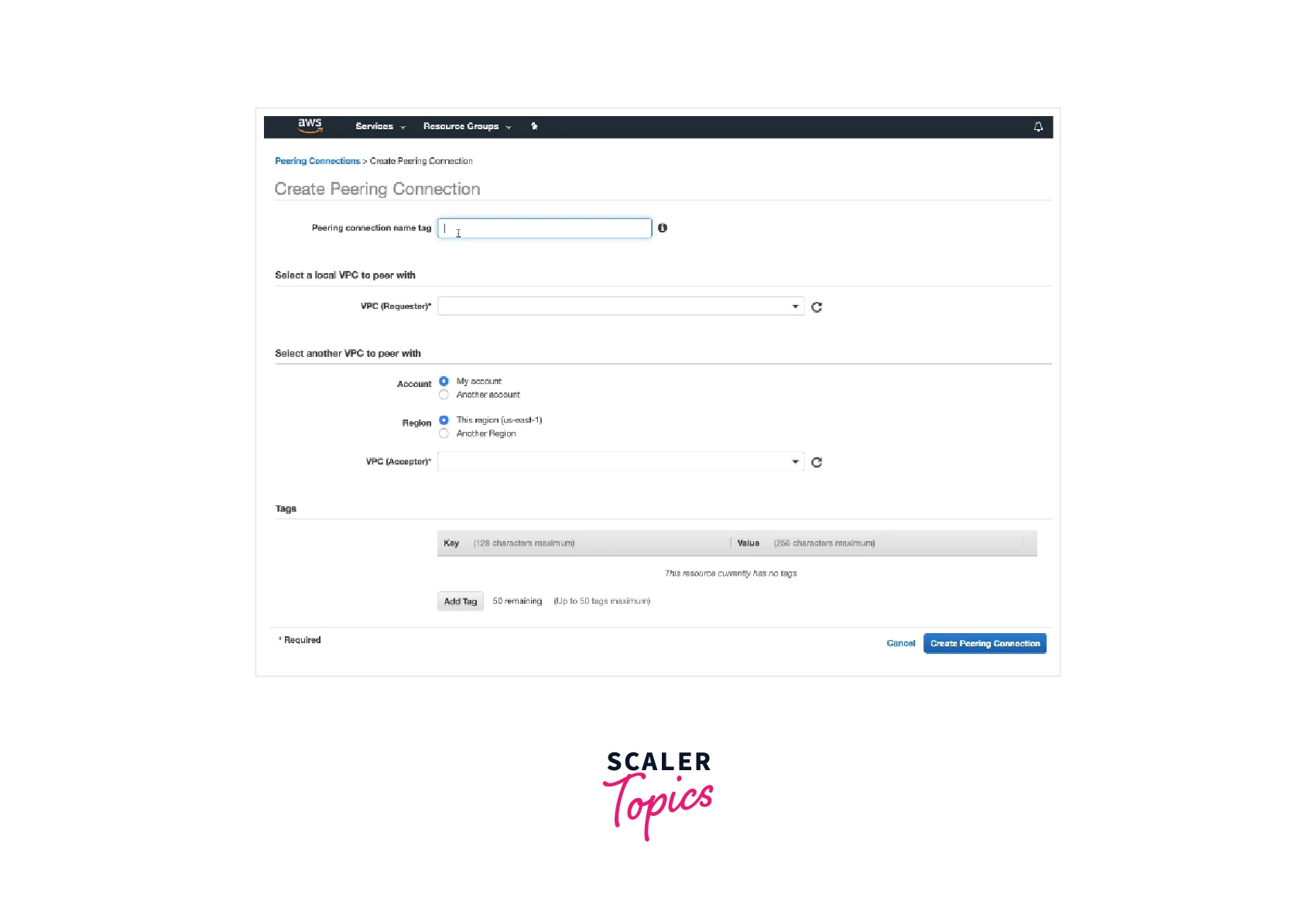
- Select OK in the confirmation dialog box.
- Select the newly formed VPC peering connection, then click Accept Request under Actions.
- Choose Yes, Accept in the confirmation popup box. Choosing to Modify my route tables now will take you to the route tables page; selecting Close will take you back to the first confirmation box.
To establish a VPC peering link with another Region's VPC:
- Go to here to launch the Amazon VPC console.
- Select Peering Connections, and Create Peering Connection from the navigation bar.
- After configuring the following details, select Create Peering Connection.
- Select OK in the confirmation box.
- Choose the region of the accepter VPC in the Region selection.
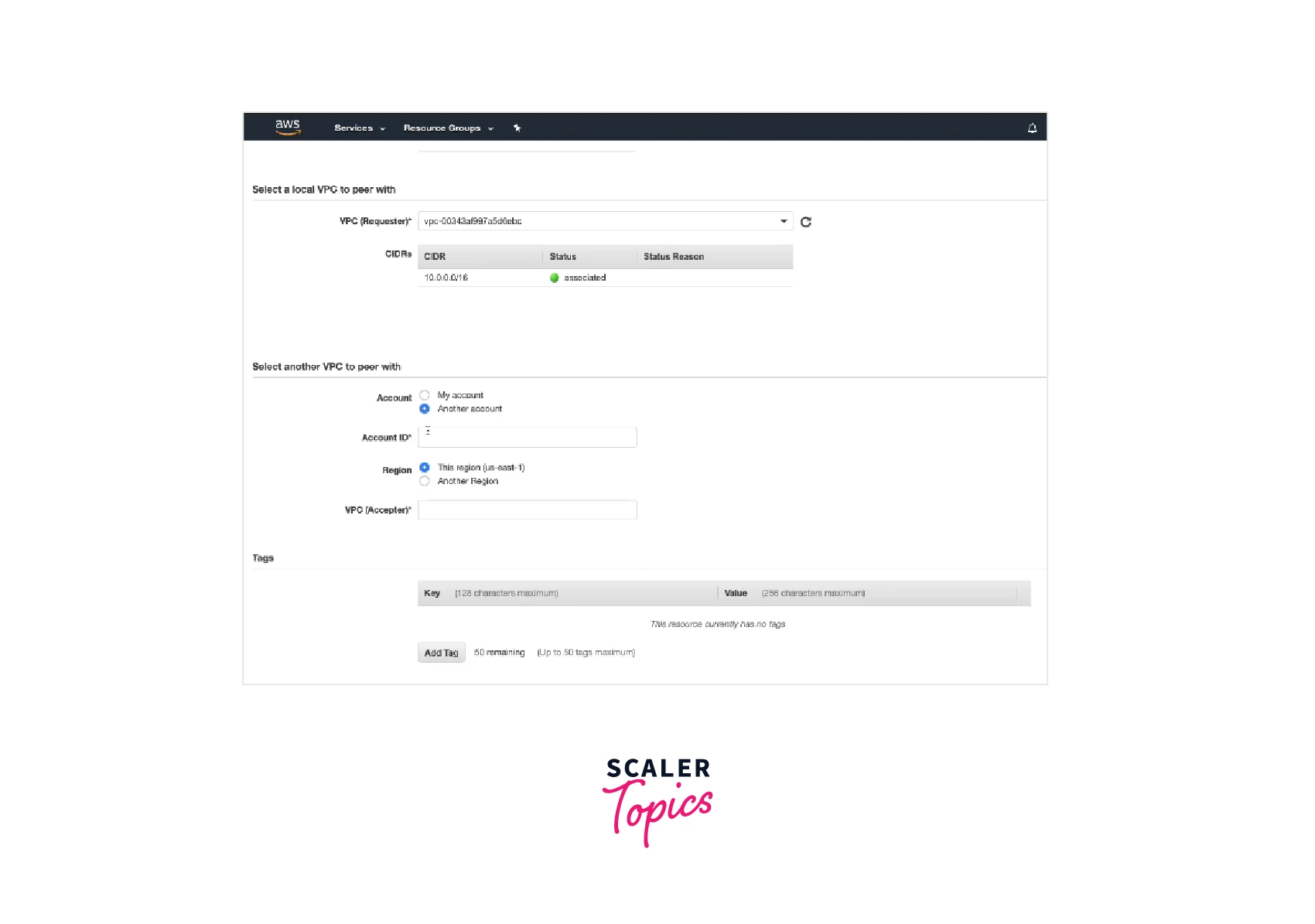
- Pick Peering Connections from the navigation window. Choose Actions, Accept Request, and then choose the VPC peering connection you just made.
- Select Yes, Accept in the confirmation dialog box. Choosing to Modify my route tables now will take you to the route tables page; selecting Close will take you back to the first confirmation box.
Create a VPC peering Connection with a VPC in Another AWS Account
The user must execute activities like creating and accepting the VPC peering connection in order to establish the connection. This requires the user to have the necessary VPC IDs and AWS account numbers. Connections may be established in the same Region (or) another.
To establish a peering relationship with a VPC inside the same region:
- Go here to launch the Amazon VPC console.
- Select Peering Connections, and Create Peering Connection from the navigation bar.
- After configuring the following information, select Create Peering Connection.
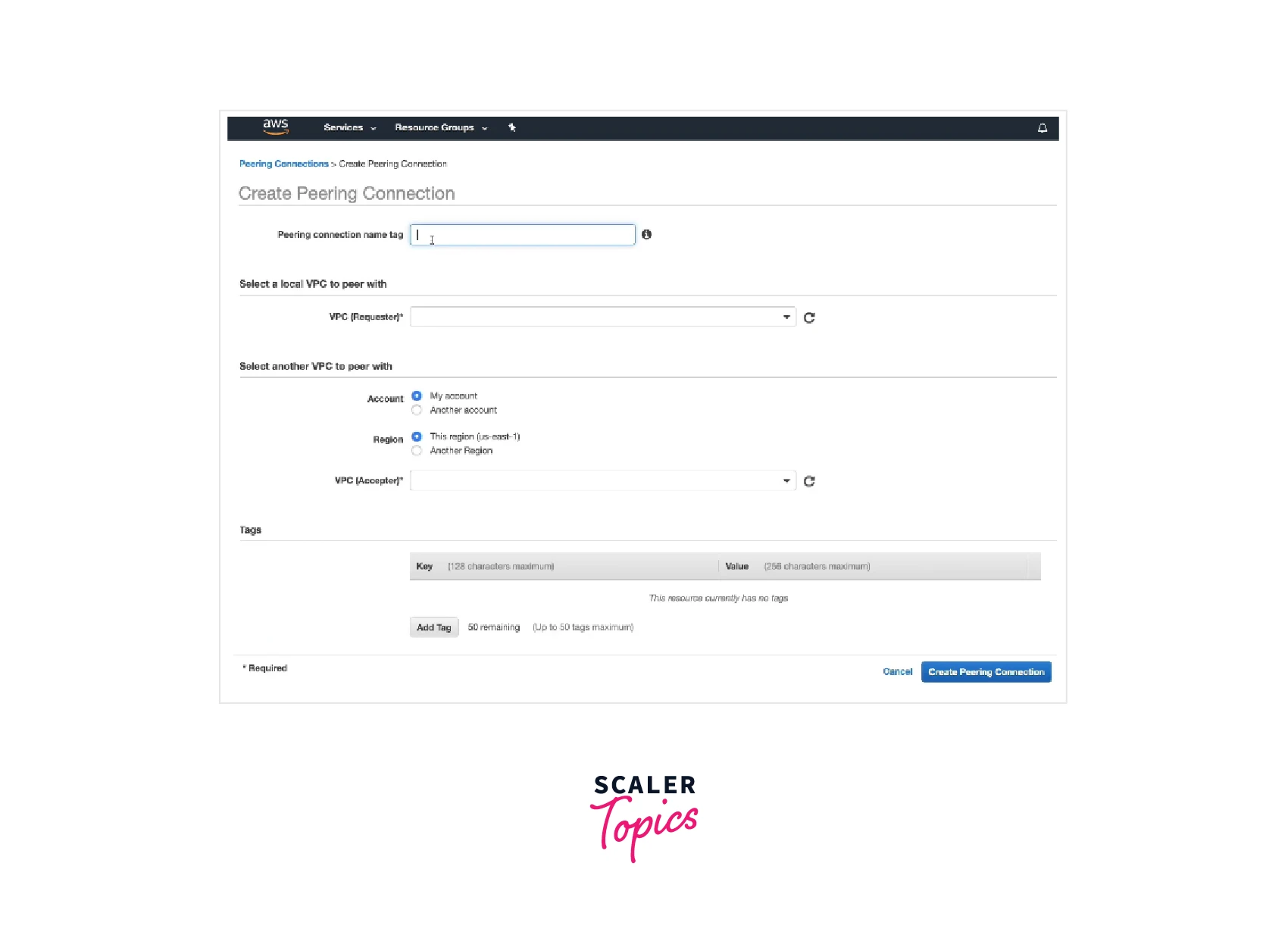
- Select OK in the confirmation box.
To establish a VPC peering link with another Region's VPC:
- Go here to launch the Amazon VPC console.
- Select Peering Connections, and Create Peering Connection from the navigation bar.
- After configuring the following details, select Create Peering Connection.
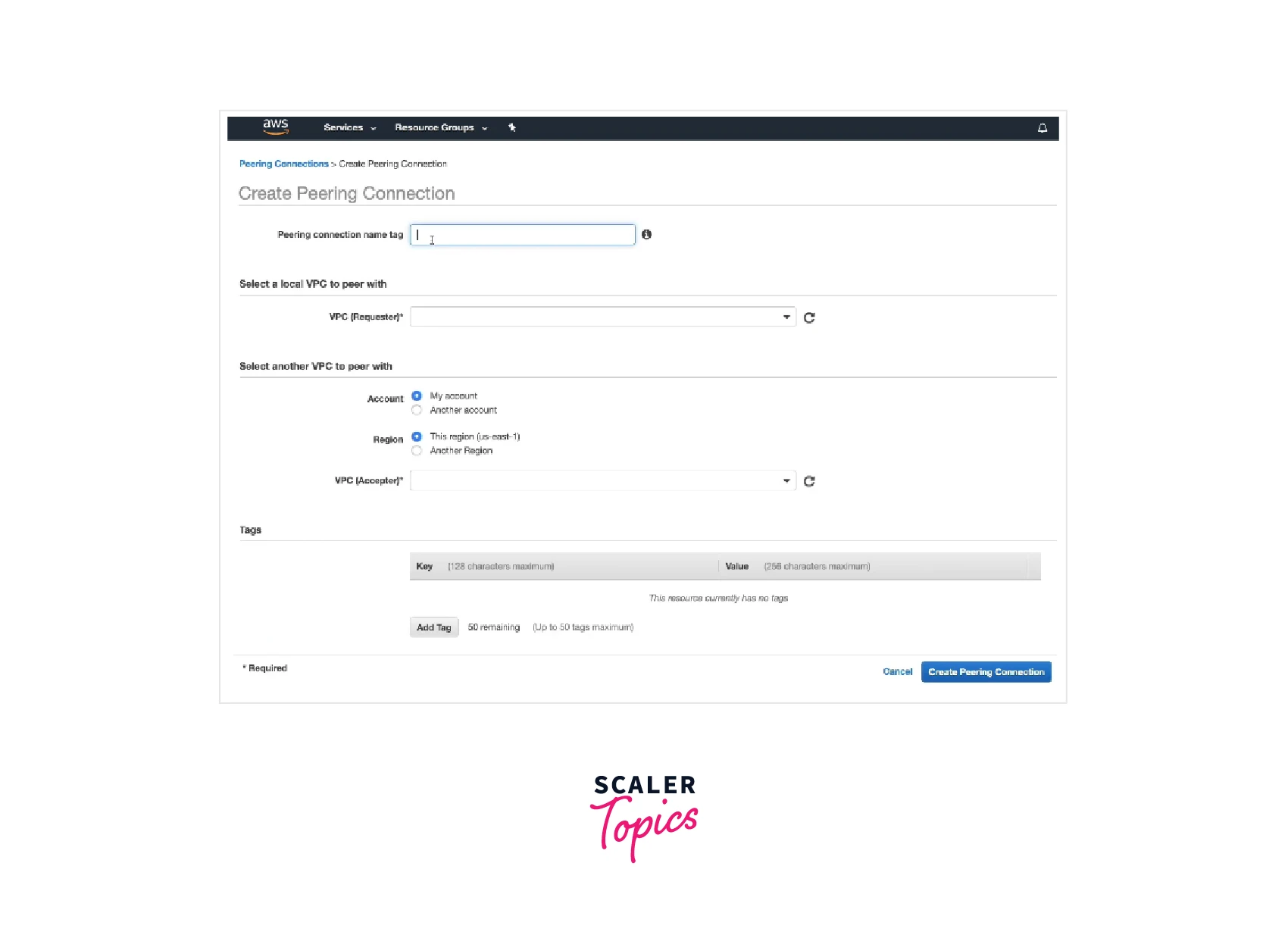
- Select OK in the confirmation box.
Benefits of Using VPC Peering
- Increase security. VPC peering improves security by providing private communication between two or more VPC networks, isolating traffic from the public Internet. Because your traffic never leaves your cloud provider's network, you eliminate an entire class of threats for your stack.
- Reduce network expenses. VPC peering saves you money on network transport while also improving network latency. Because peering traffic does not leave your cloud provider's network, public IP latency is reduced. Furthermore, because peer networks interact using internal IP addresses, transmitting data through the cloud provider's network is less expensive than over the public Internet.
- Increase the flexibility of services that do not require an Internet connection. When your instances don't need a public IP address, (or) a network address translation (NAT) set up to the public Internet, you should utilize VPC peering. This may be advantageous for backend services if users want to prevent unnecessary traffic from their instances to the public Internet.
- Reduced Network Usage Charges: VPC peering can assist minimize your cloud data costs since public cloud providers frequently charge lower rates for data moved within VPC peering connections compared to data carried through public internet connections.
- Limited Access AWS VPC Peering enables traffic to always remain on the AWS global network and never cross the open internet. Additionally, it decreases risk vectors like widespread exploits and DDoS attacks.
VPC Peering and Network Observability
- While VPC peering can improve contemporary network performance and security, it also complicates network topologies.
- Organizations must take measures to control this complexity through network observability to prevent problems with VPC peering setups from impairing network availability (or) performance.
- Within VPC peering, various issues might develop, and it can be challenging to identify the exact cause of a problem. Traffic flow issues might result from manually defined routes; for instance, a network service deterioration in one cloud provider could raise latency for all VPCs that are peering with that provider's VPCs.
- To complicate matters further, cloud providers give users little capabilities to track and regulate the performance of VPC peering connections.
- Each cloud provider is only concerned with assisting clients in managing the performance of network resources running within its cloud. AWS tools, for example, will not assist you in troubleshooting issues with a peer VPC operating in Azure. AWS only monitors the performance of VPCs that are hosted on AWS.
- It implies that your responsibility is to recognize and handle any possible problems that may develop if your team configures VPC peering. By absorbing network telemetry data from various sources, correlating it, and contextualizing it, network observability systems enable you to accomplish this and provide answers to queries about the status of your VPCs.
Conclusion
- AWS creates a VPC peering connection using the current architecture of a VPC; it is neither a gateway nor a VPN connection, and it does not require any additional physical hardware.
- A VPC peering connection helps the user to increase data flow speed. If users possess several AWS accounts then they can peer the VPCs across numerous accounts to build a file-sharing network.
- AWS VPC peering increases security and flexibility for services that do not require Internet access.
- AWS VPC peering has several advantages, including the ability to be horizontally scaled, the encryption of inter-regional communication, high availability, and the absence of any bandwidth limitations.
- VPC peering saves you money on network transport while also improving network latency. Because peering traffic does not leave your cloud provider's network, public IP latency is reduced.
