What is Checksum?
Overview
We are here with one of the techniques used in data transmission for detecting an error. The name of that error detection algorithm is Checksum. It is essential to perform error detection in data transmission.
The Checksum is an error detection technique that detects an error in a transmitted message by appending redundant bits in the message. So this article comprehensively provides all the information on the checksum error detection technique.
What is Checksum Error Detection?
- Checksum is used for error detection.
- Checksum is the redundant bits that are attached with actual data.
- Sometimes, a Checksum is also considered as a hash sum or hash value.
- On the sender’s side, this method uses a checksum generator to generate a Checksum. On the receiving end, a checksum checker is used to validate whether the correct data is received.
- Checksum is an error detection algorithm that can be applied to any length message.
- Checksum provides information to the receiver about the transmission to ensure that the full range of data is delivered successfully.
Note :
The Checksum is an error detection algorithm that appends redundant bits in a message for error detection and can work on any message length.
Types of Checksum Algorithms
Many cryptographic hash functions are used by programmers to generate checksum values.
Some of them are given below with a brief introduction:
-
SHA-0 :
SHA-0 was the first hash function of this type, but it was withdrawn briefly in . -
SHA-1 :
SHA-1 is a hash function that is not considered a secure hash function as of . -
SHA-2 (224, 256, 384, 512) :
This includes some changes from its previous version, SHA-1. The SHA-2 family consists of a total of six hash functions with hash values that are 224, 256, 384, or 512 bits. -
MD5 :
MD5 is a hash function that generates a checksum value, but it is not required for each file to have a unique number. So MD5 is open to vulnerabilities if the hacker swaps the file with a checksum value.
Error Detection by Checksum
The Checksum is generated at the sender end, and on the receiver end, the Checksum is validated.
Refer to the image below to see the error detection process of Checksum.
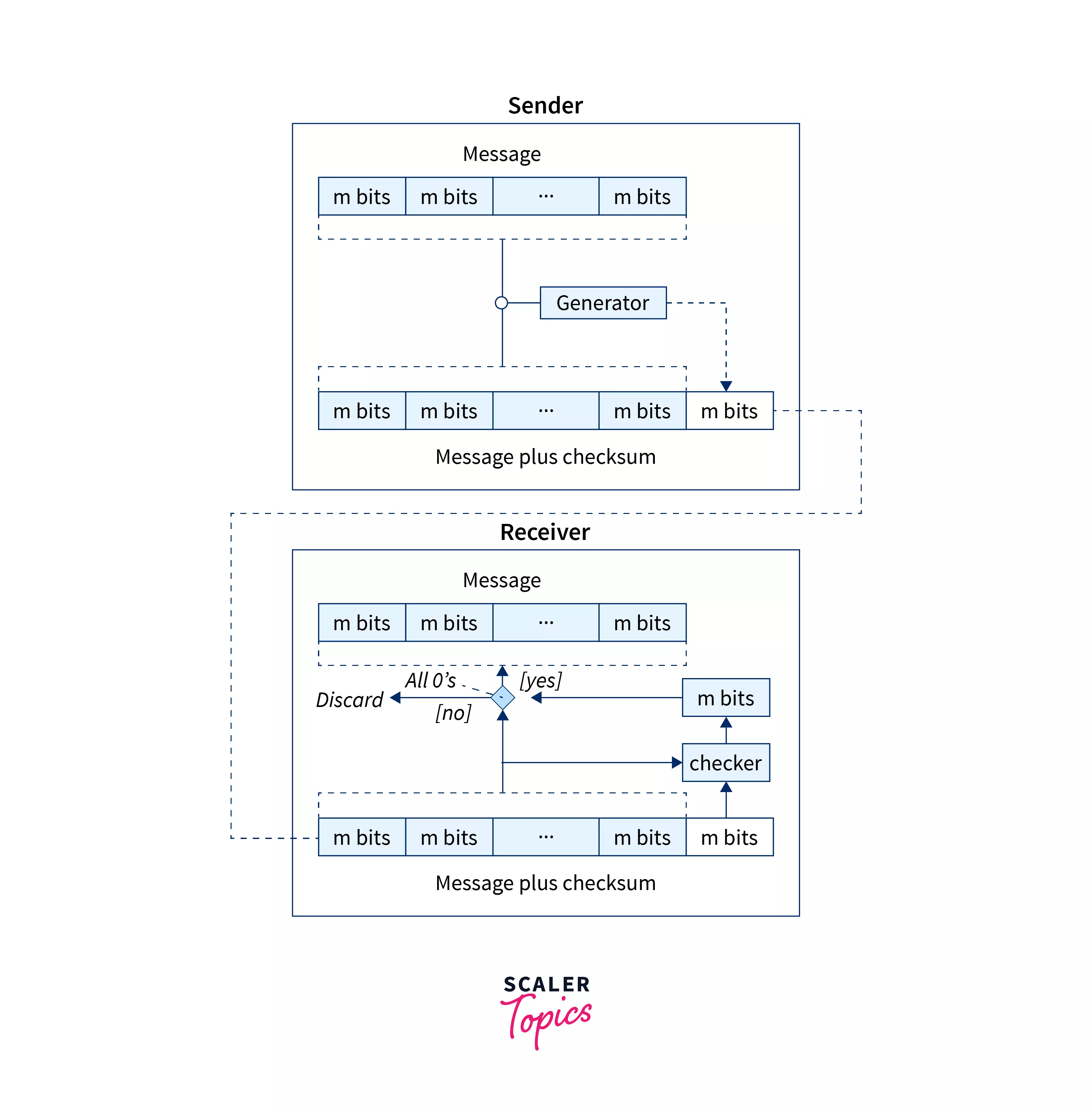
Checksum at Sender Side
The sender divides data into blocks of equal size and then adds the data of every block using 1’s complement arithmetic to get the sum. It then complements the sum to get the Checksum and sends it along with the data frames. At sender side steps of generation of the Checksum are given below :
- Step 1 :
First of all, break the given data into “k” an equal number of blocks, i.e., “N” bits in all the “K” blocks of the message. - Step 2 :
Perform addition of all the “k” divisions - Step 3 :
If there is a carry bit, add it. - Step 4 :
Now find the 1’s complement of the sum. For finding 1's complement of any binary number, just replace every zero with one and replace everyone with zero(e.g., 10001 - 1's Complement 01110) This complemented sum is known as Checksum. - Step 5 :
Checksum is appended to the message to be sent to the receiver.
Now the data appended with Checksum is ready to send.
Checksum at Receiver Side
The receiver receives data Checksum and passes it to the checksum validator. The following steps are used to validate the Checksum at the receiver end.
- Step 1 :
Perform addition on all “K” data blocks - Step 2 :
If there is a carry bit, add it. - Step 3 :
Find the 1’s complement of the sum. - Step 4 :
If we got a result that contains only 0, then ACCEPT the data, otherwise, REJECT the data.
Example of Checksum Error Detection
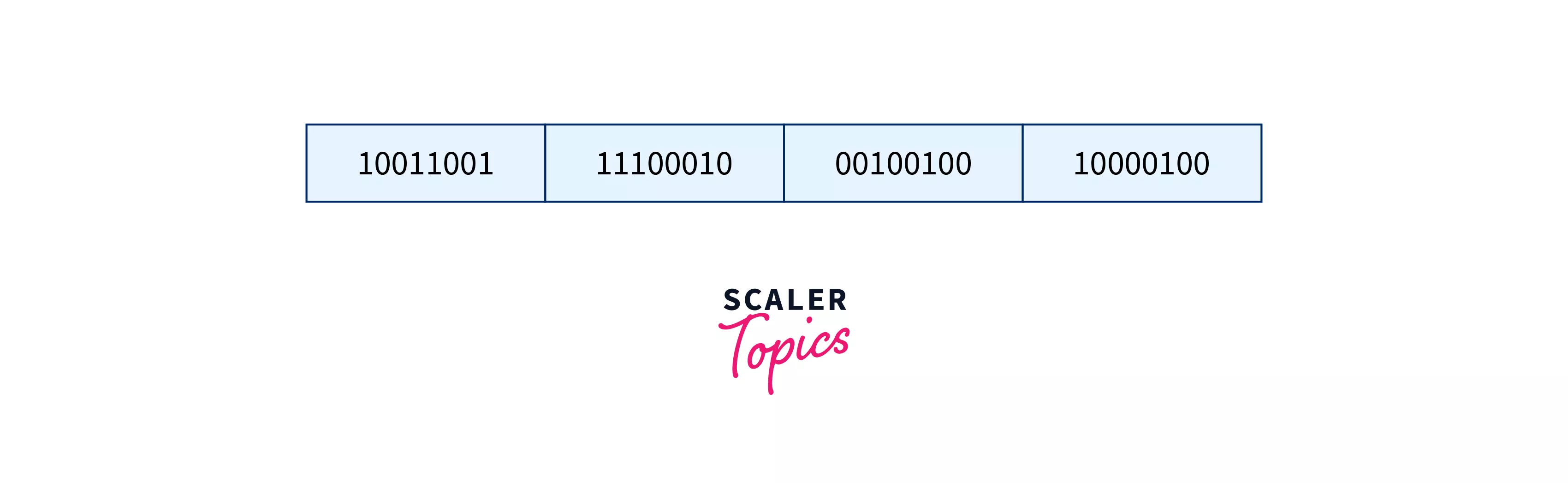
Suppose that the data 10011001111000100010010010000100 is to be sent to the receiver.
Sender Side
-
Step 1 :
Break the message into four equal size blocksBelow is an image to show the division of the message into k parts.
-
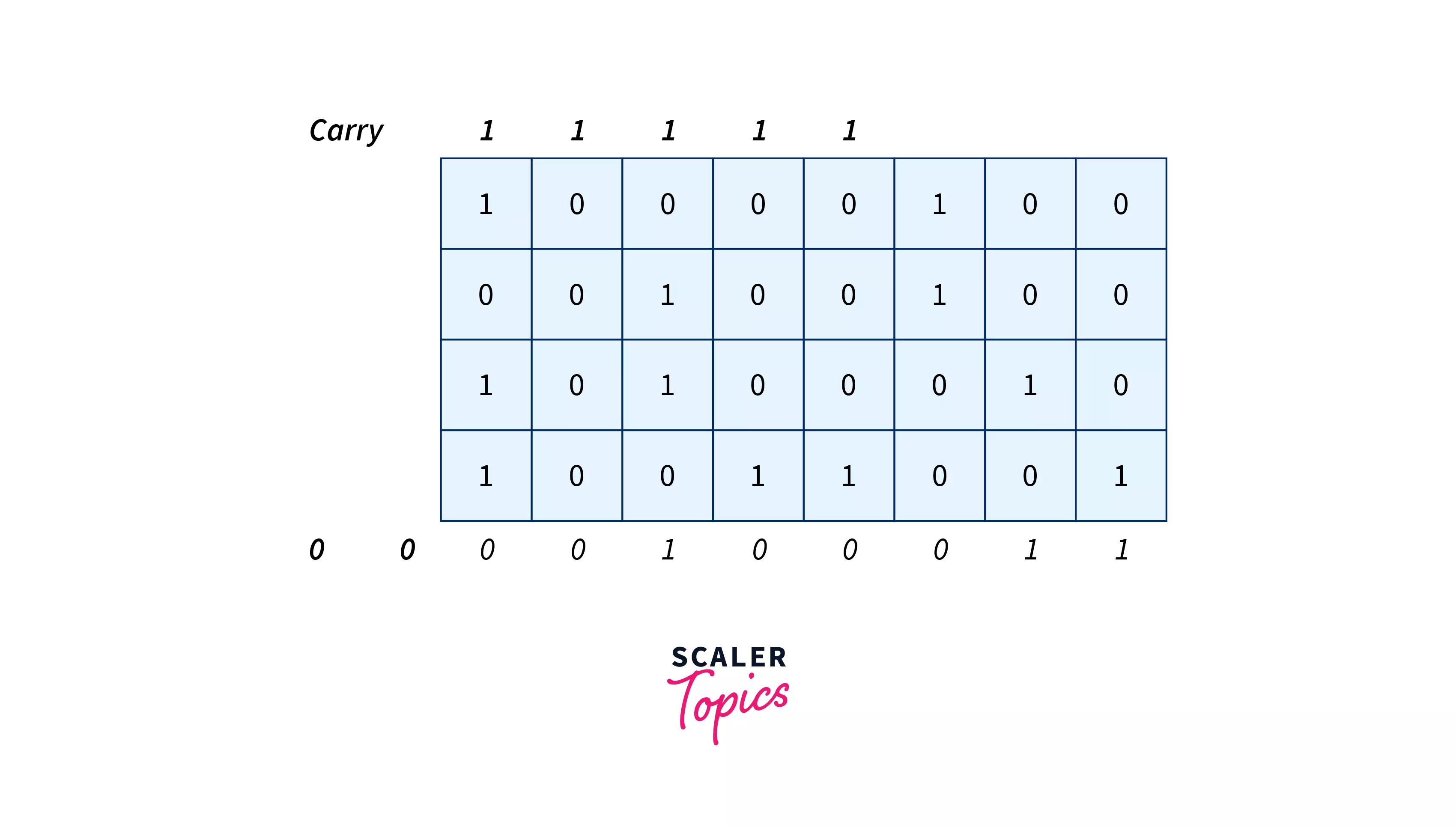
Step 2 :
Perform addition on all k blocks.Below is an image to add data of k parts.
-
Step 3 :
If any carry is generated, simply add it in sum.Below is an image to add carry to the sum.
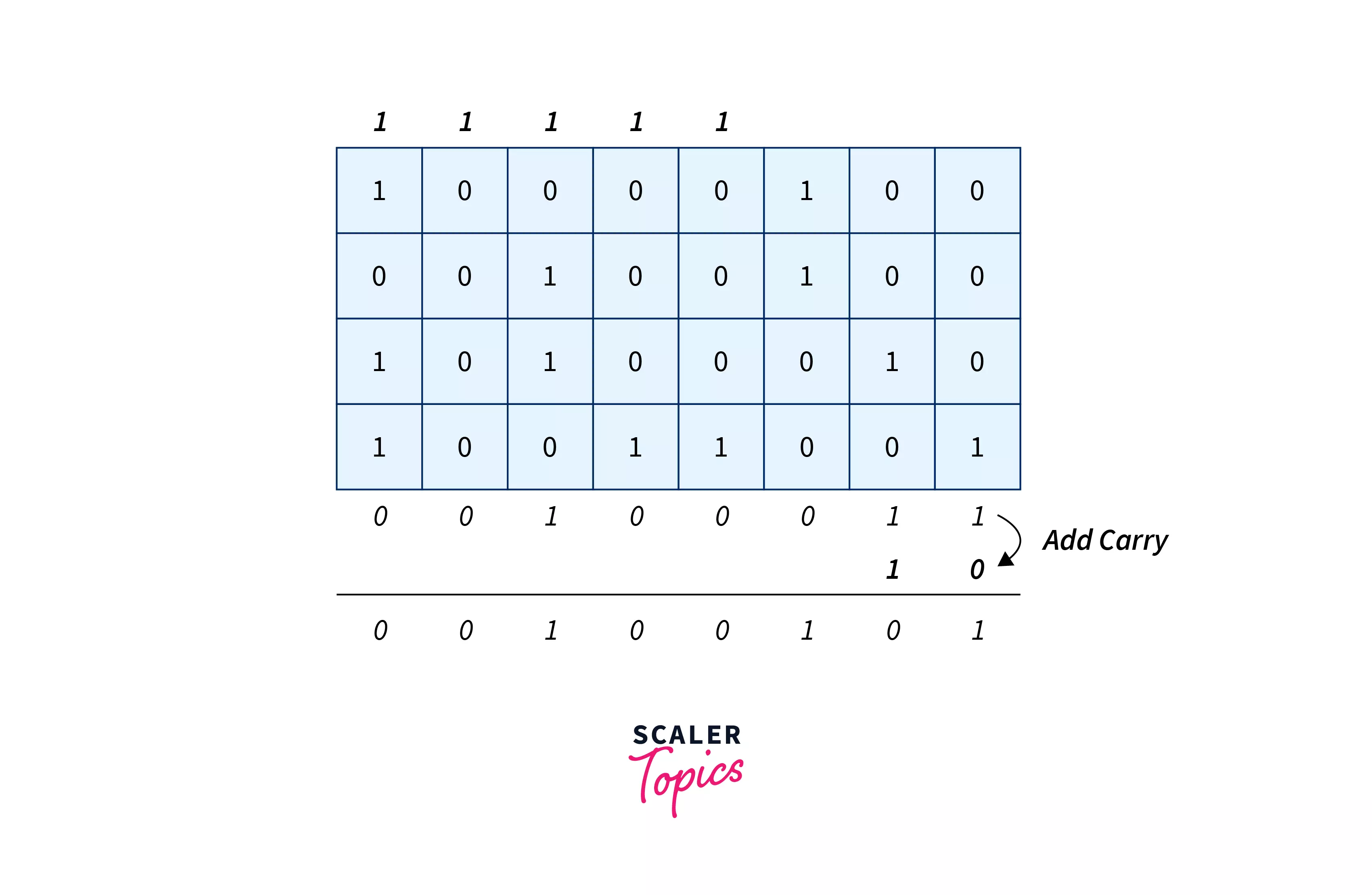
-
Step 4 :
Find the 1’s complement of the result of the sum, this is known as Checksum.Below is an image to show the 1's complement of the result.
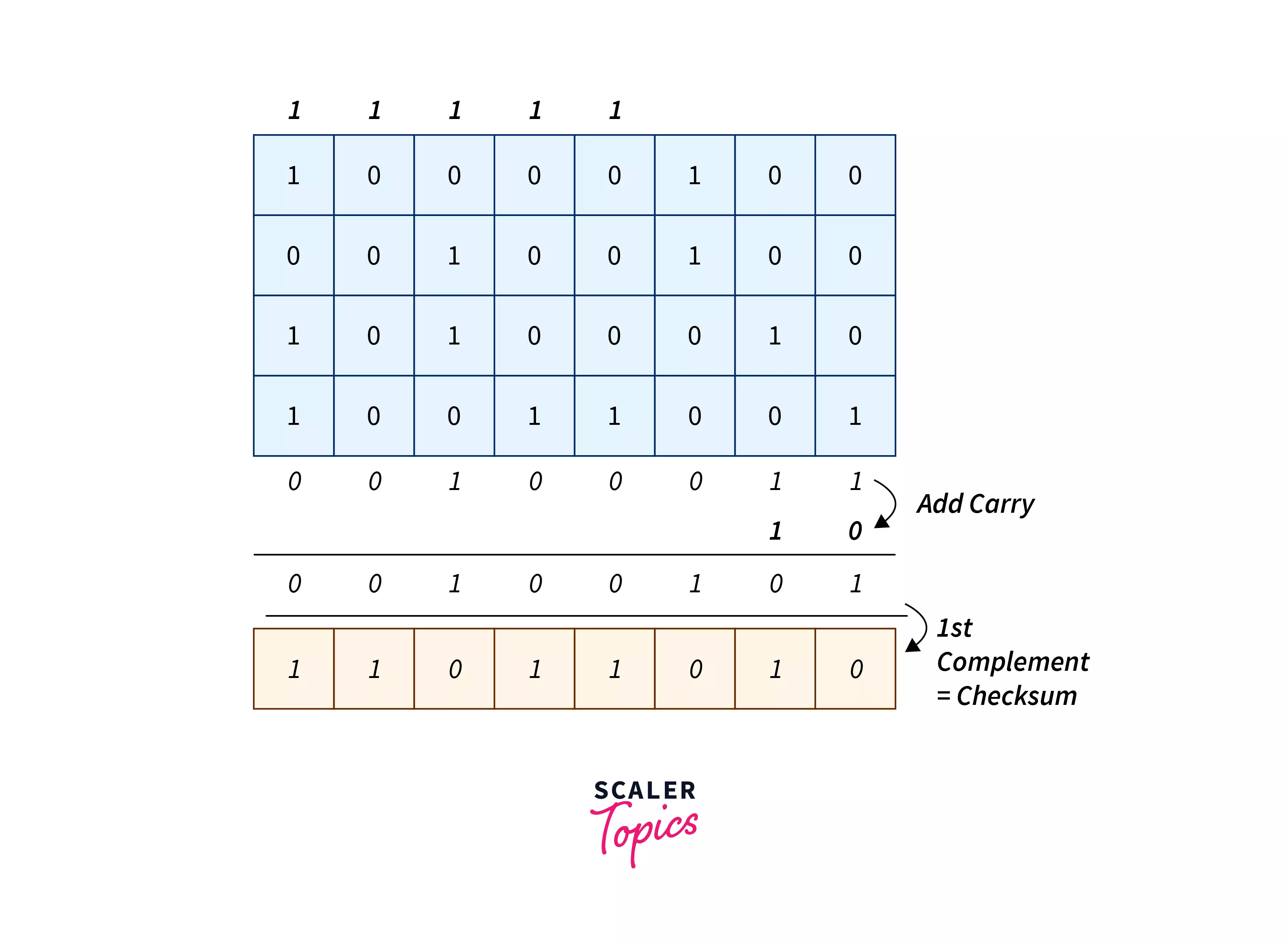
-
Step 5 :
Append Checksum in the message to send it to the receiver.
Receiver Side
-
Step 1 :
Perform the addition on all the k's-size blocks.Below is an image to show an addition of blocks on the receiver side.
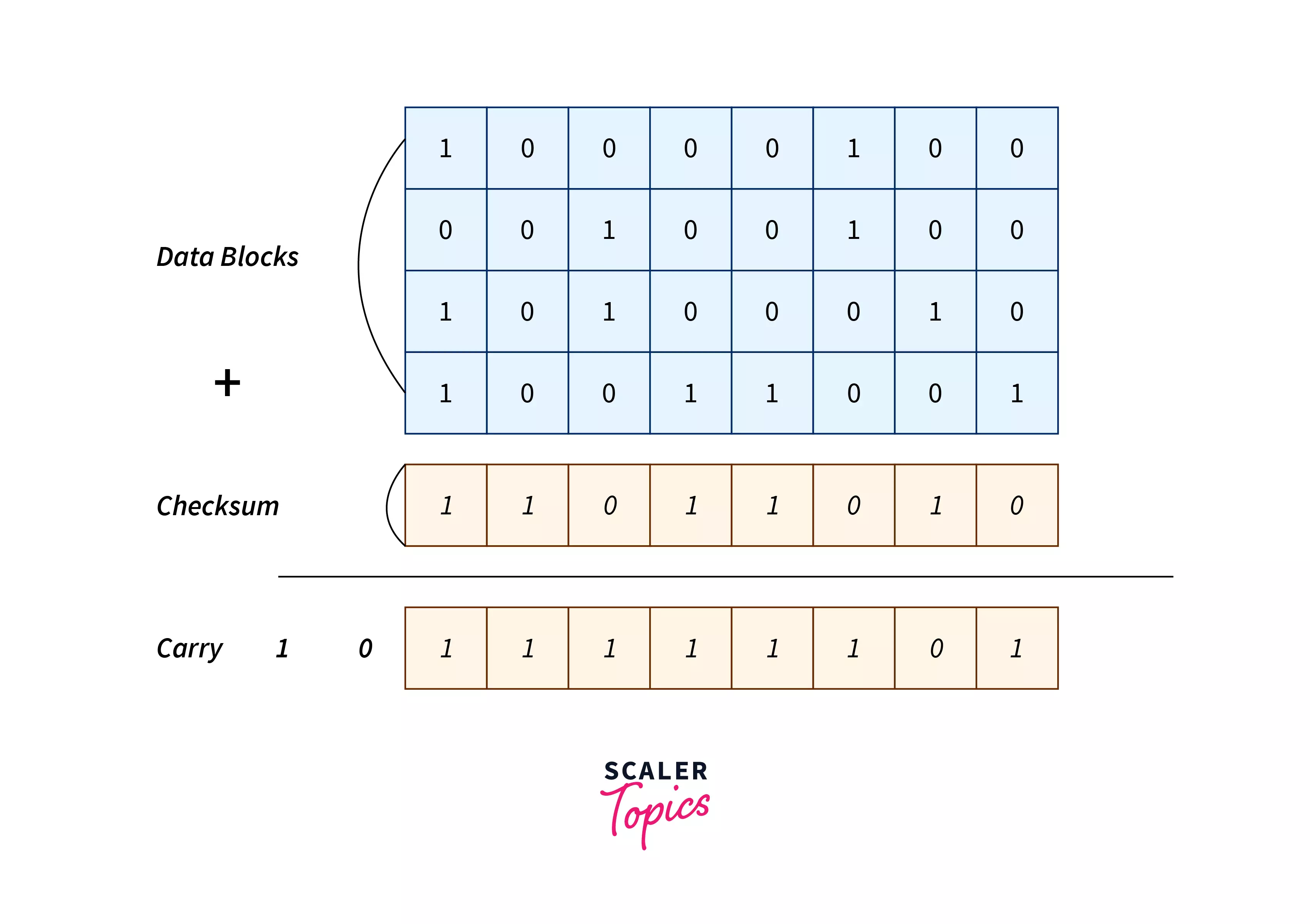
-
Step 2 :
If any carry is generated in performing an addition, then sum it with the step 1 result.Below is an image to show the addition of carrying to the sum.

-
Step 3 :
Find the 1’s complement of a sum. If all bits are zero in the result, then simply ACCEPT that message, otherwise, REJECTS the data. Below is an image to show the 1's complement of the sum.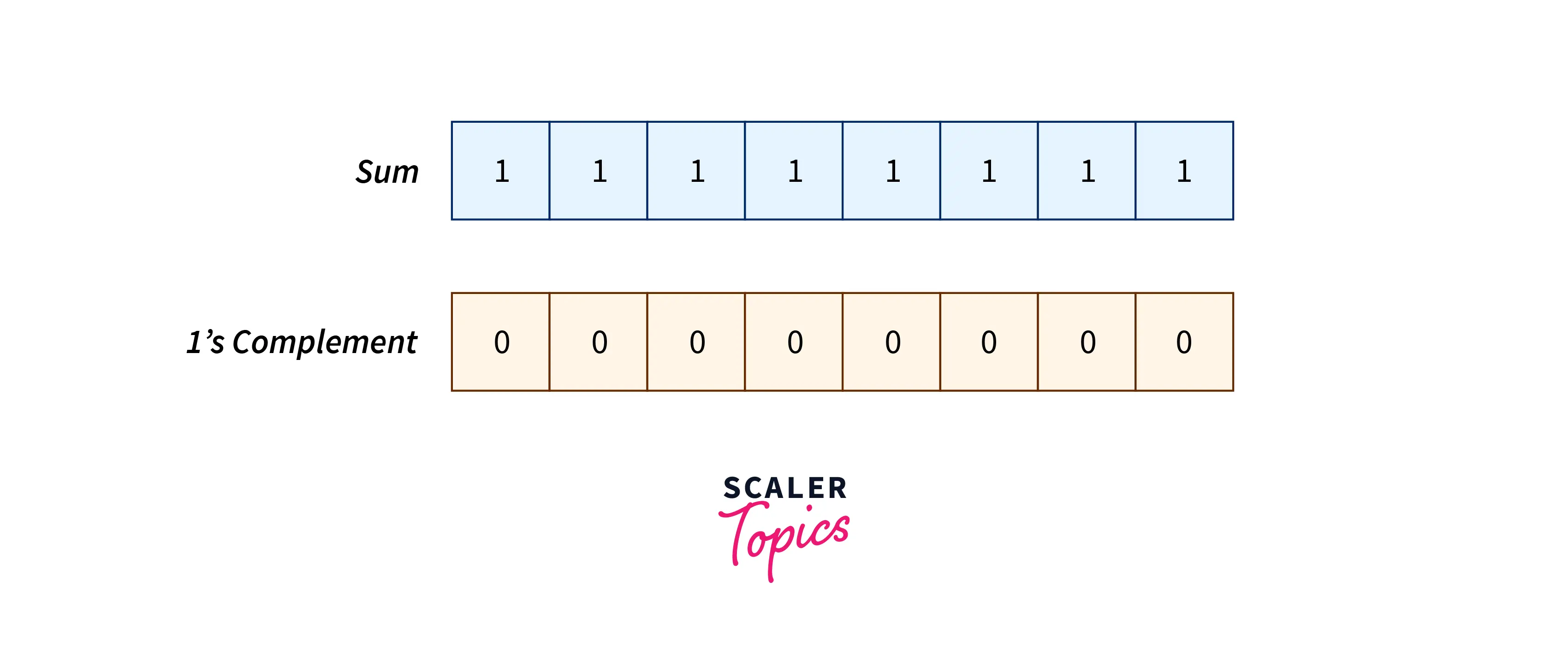
In our example, we get all 0's in the answer after finding the 1's complement of the sum, so the data is ACCEPTED.
Conclusion
- Checksum is an error detection technique that works with any length message.
- Checksum uses checksum generator at sender side and checksum validator at the receiver end.
- SHA, MD-5, etc., are some checksum error detection algorithms.
- Checksum error detection detects both odd and even number of bits error.
