What is Burp Suite?
Overview
Burp Suite software is the best toolbox for web security testing. In web security testing, the incursion also protects engineer grace. Used to find and exploit search flaws. Burp Suite is therefore designed to be used by point-and-click. Understanding how systems are attacked is essential for everyone working in security, whether they are developers or security professionals. Burp Suite is a platform and graphical tool that work together to do security testing on online applications. It supports the whole testing process, from the initial mapping and analysis of an application's attack surface through the discovery and exploitation of security flaws.
What is Burp Suite?
Burp Suite is a proxy program that enables us to track, examine, and alter requests made by our browsers before they are forwarded to a distant server.
Burp Suite is a prominent web application security solution. It gives us the ability to manually test for vulnerabilities, intercepts HTTP messages, and change a message's body and header.
It was created by a business with the alias Portswigger, whose creator Dafydd Stuttard also works there. BurpSuite is designed to be an all-in-one toolkit, and BApps are add-ons that may be installed to expand its functionality.
It is the most widely used tool among experts in online app security and bug bounty hunters. It is a better option than free substitutes like OWASP ZAP because of how simple it is to use. The community edition of Burp Suite is accessible for free, whereas the professional edition and the enterprise edition need payment.
Why is Burp Suite Used in Cybersecurity
Burp Suite is a comprehensive framework that may be used to carry out several activities, including:
- Web crawling.
- Web application testing, both manually and automatically.
- Analysis of web applications.
- Vulnerability detection
Burpsuite also has the advantage of being built into the Chrome browser.
Getting Started with Burp Suite
Installing Burp Suite
- Burp Suite is pre-installed if you're using Kali Linux. You must download the community version from ports wigger's website to use it with other Linux distributions like Ubuntu. It also holds for Windows OS.
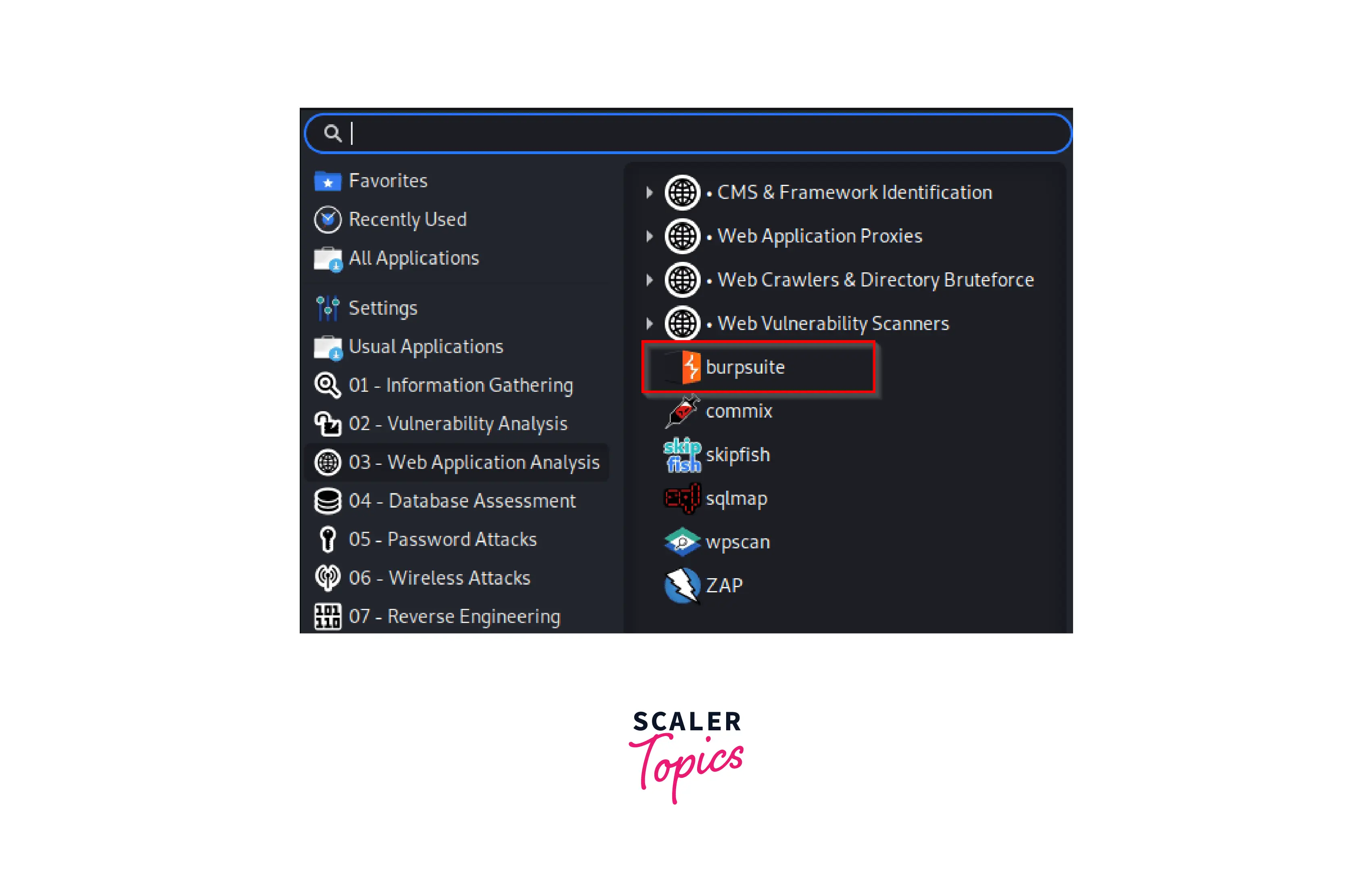
- After that, we launch Burp Suite. On Kali Linux, you may find it under the program's panel.
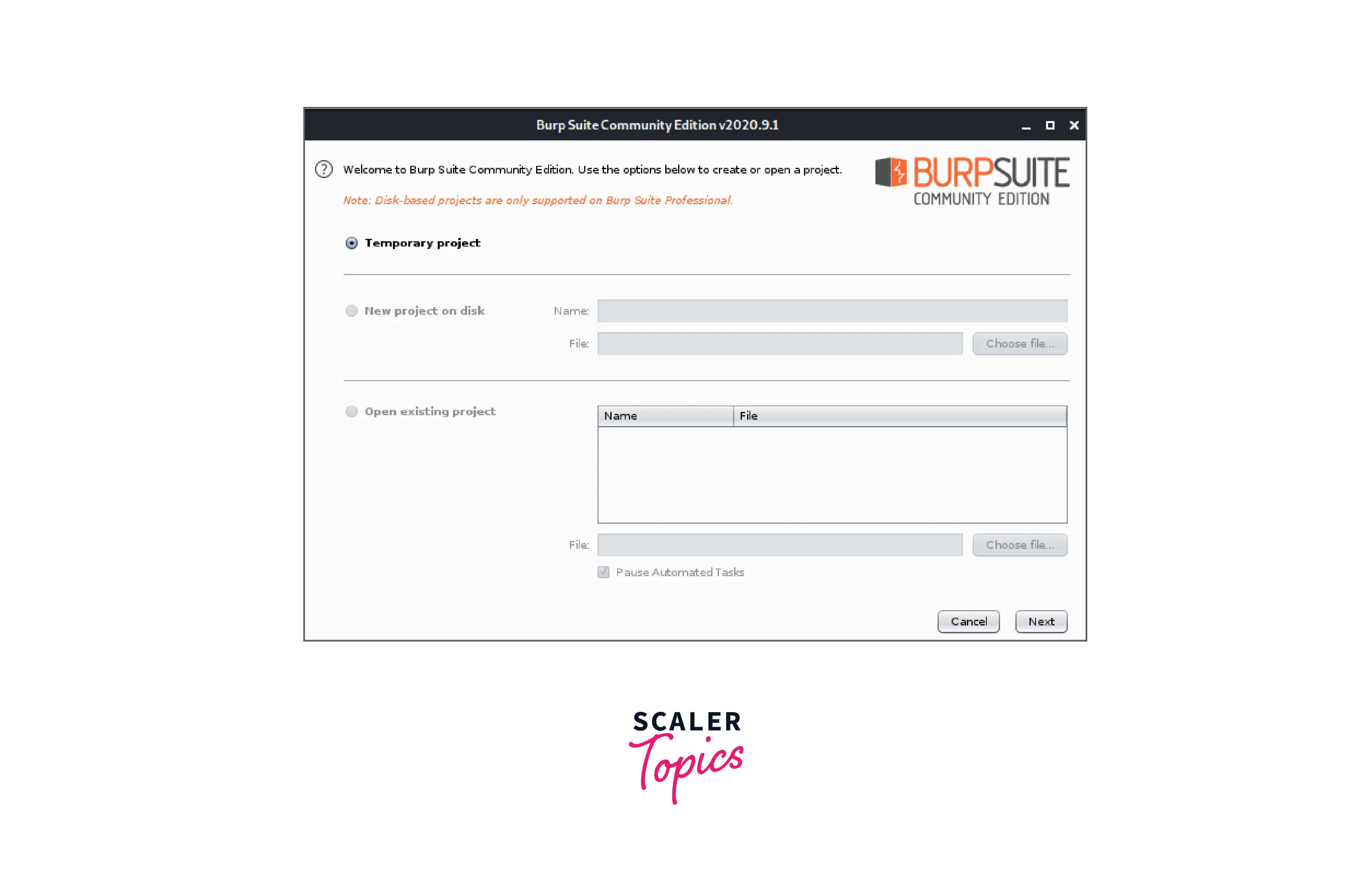
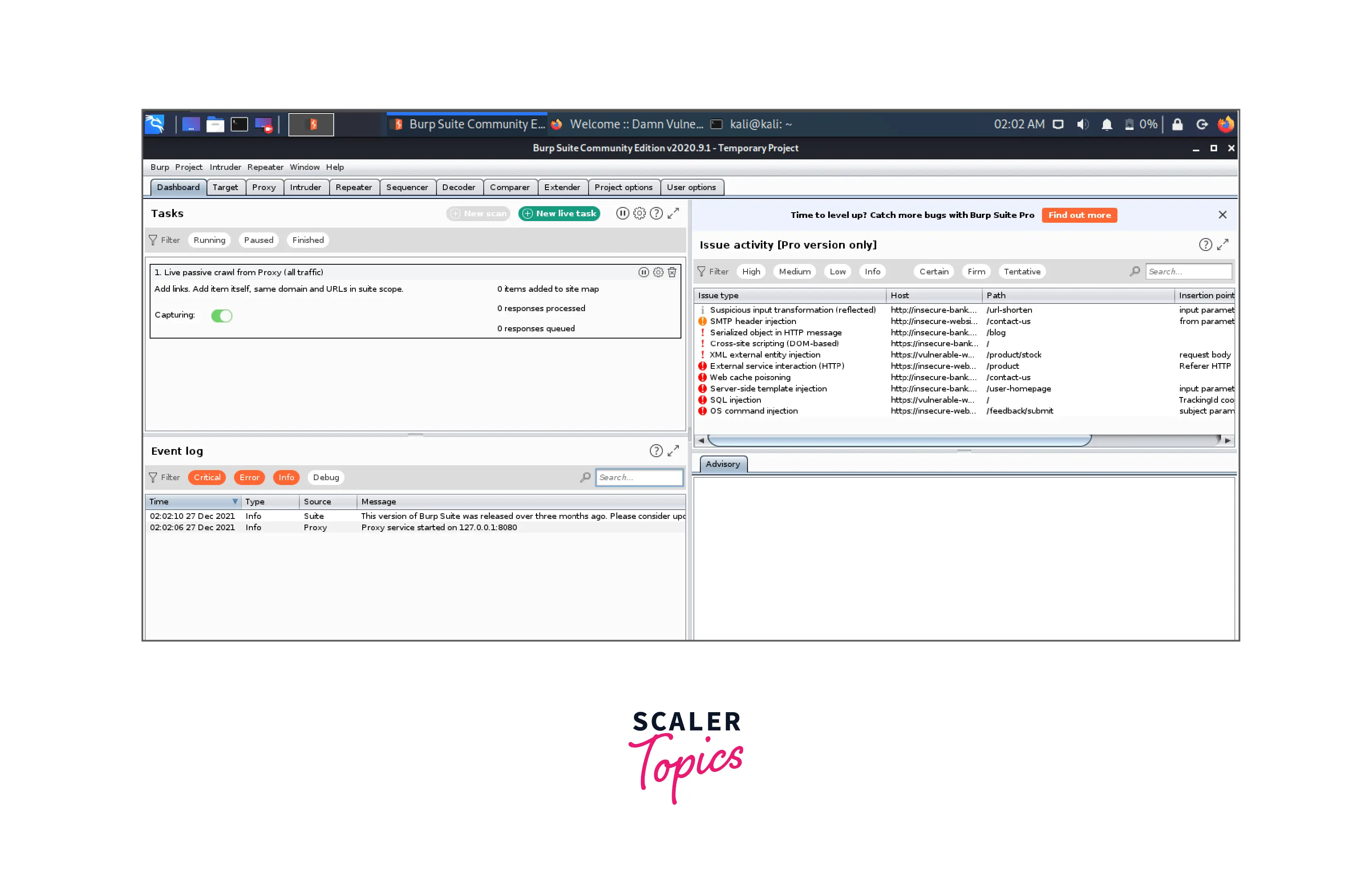
- A window with many choices is displayed to us. Choose Temporary Project, then select Next:
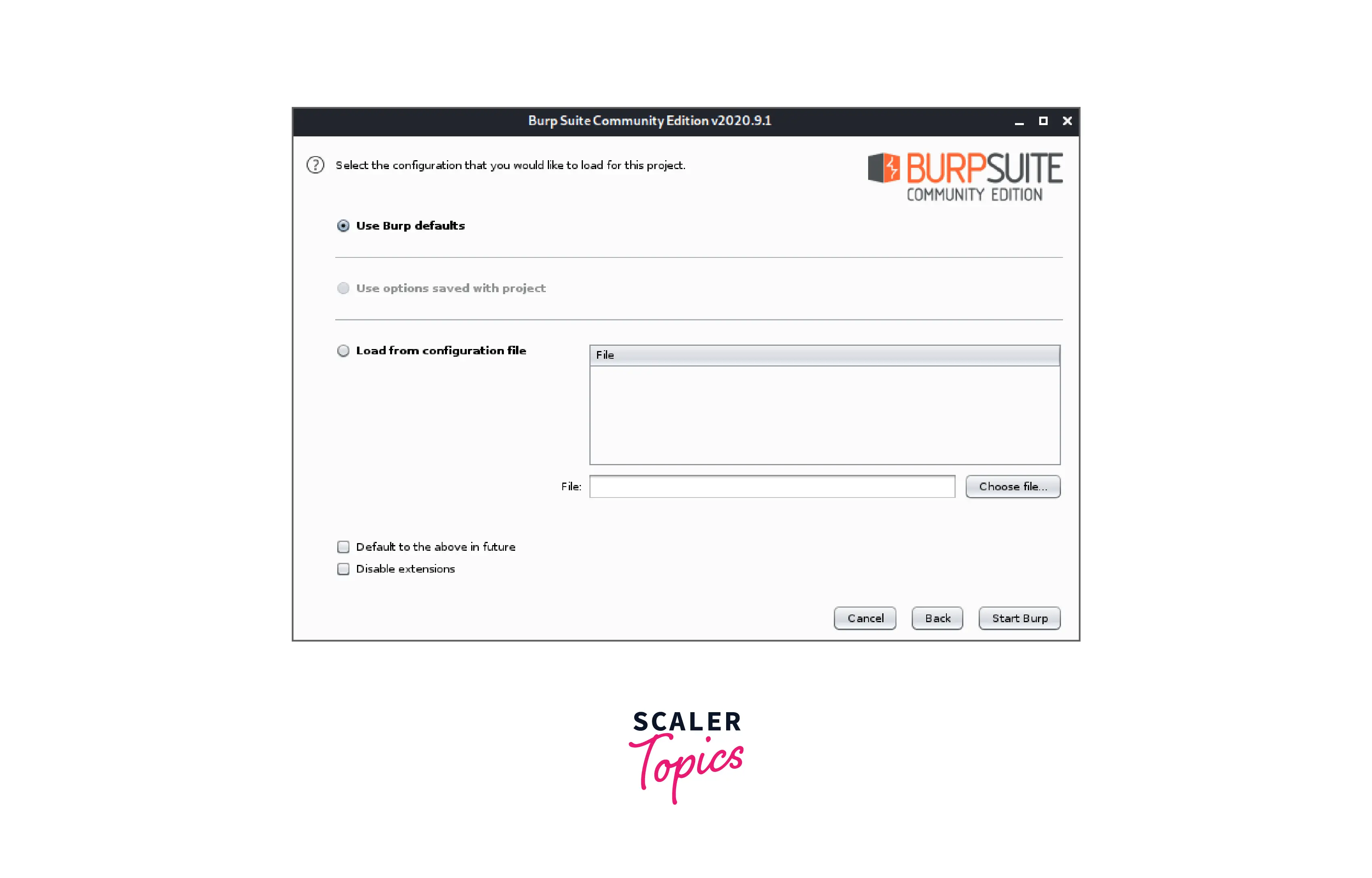
- We'll keep things on the default configuration, so we choose Start burp:
- Burp Suite was successfully launched:
Configuring Burp Suite Proxy
We must now configure the Burp Suite proxy. Using the proxy, we may stop a web request in its tracks and change it.
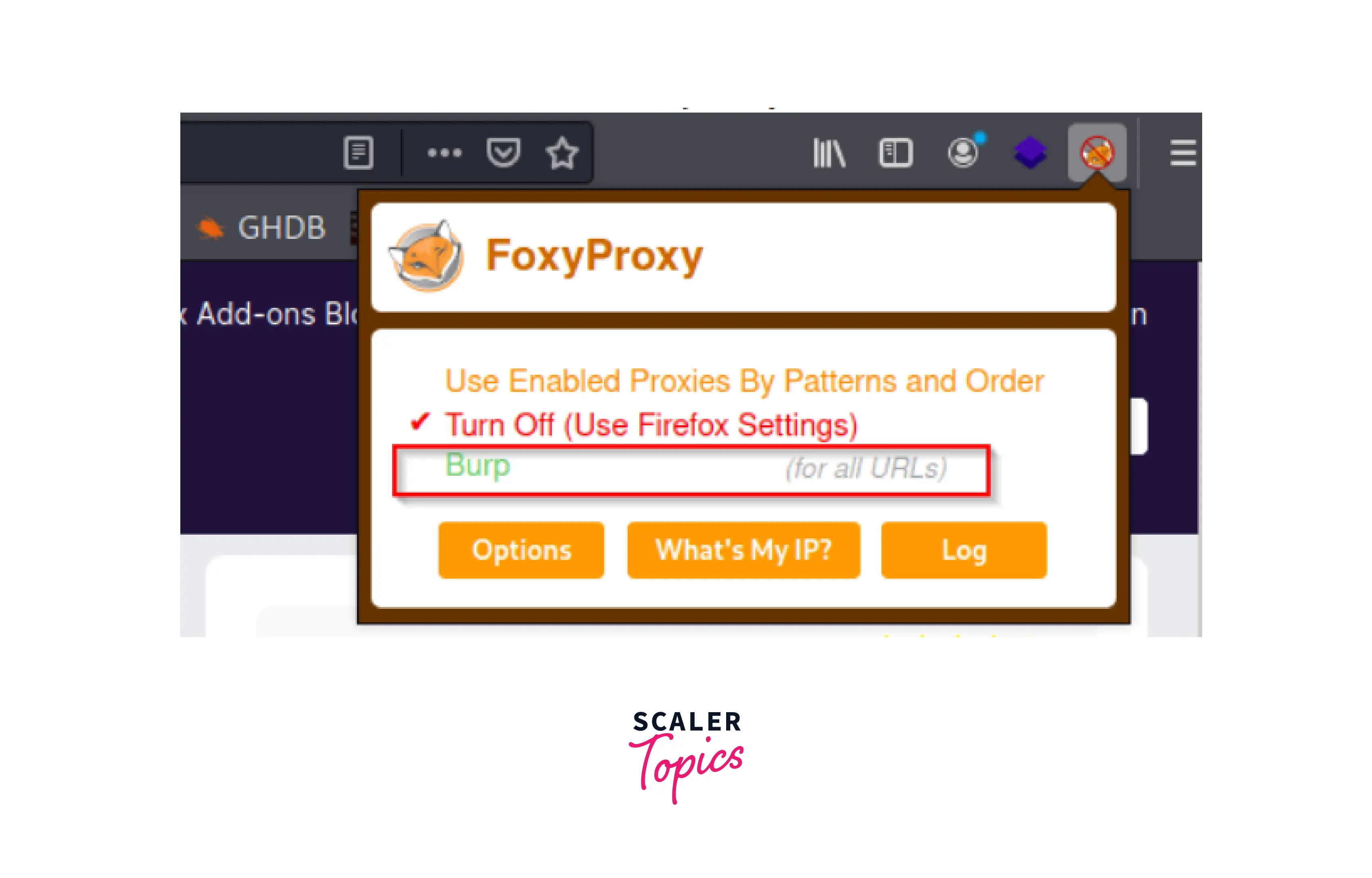
- First, we must add Foxy Proxy to our browser. To add the extension to the browser, click Add.
- After installation, our browser's address bar will display a small fox icon. Click the symbol, then select Options, and then select Add.
- We then see a window with the following input fields:
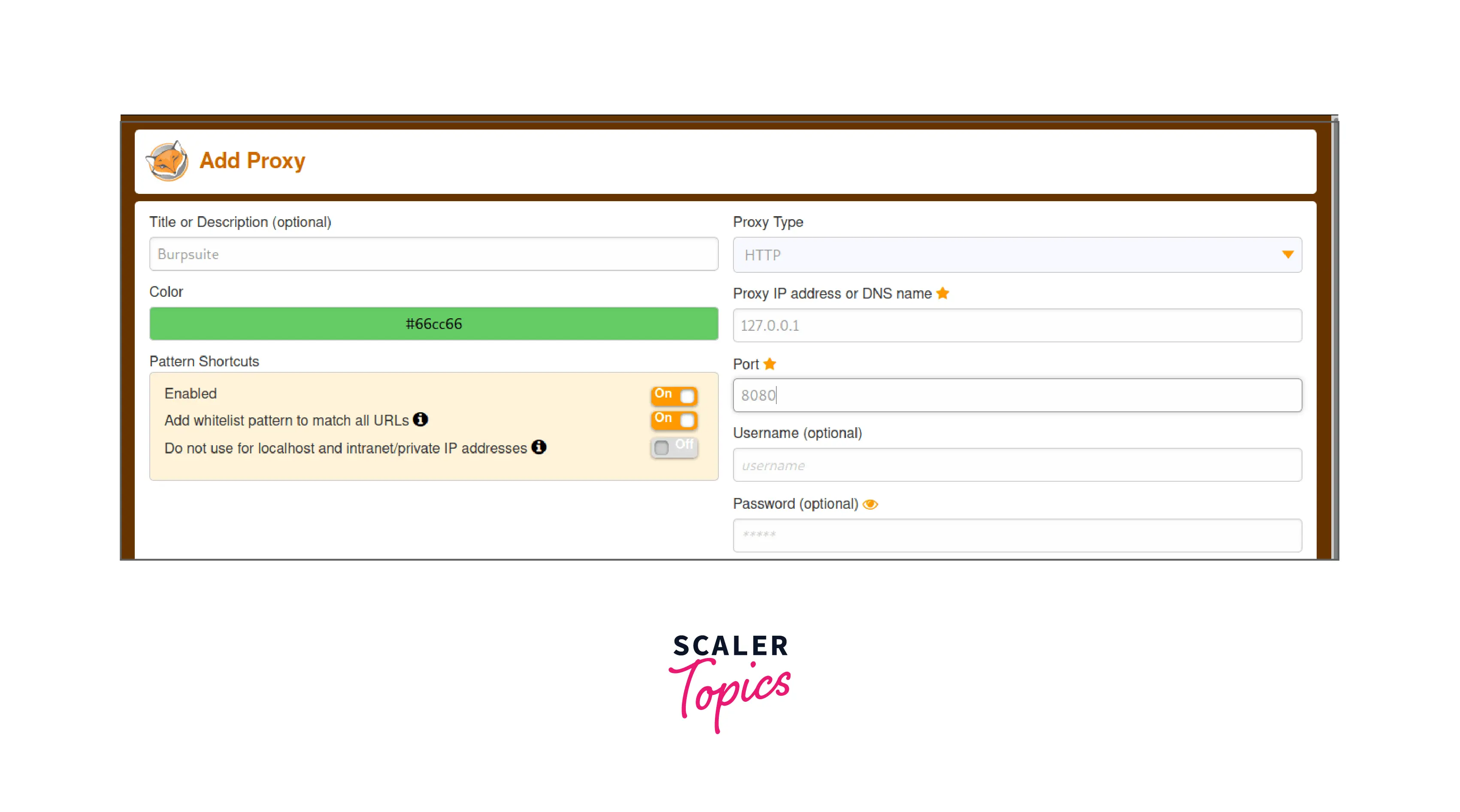
- Title: A label or a brief intro.
- Proxy type: HTTP.
- Proxy IP Address: Your localhost/interface (127.0.0.1).
- Port: The port that Burp Suite should use to execute.
Features and Tools Offered by Burp Suite
BurpSuite provides the following tools:
1. Spider
A web crawler or spider is employed to map the target web application. The mapping's goal is to compile a list of endpoints so that their capabilities may be examined and possible vulnerabilities can be discovered. Spidering is carried out for the straightforward reason that more attack surfaces are available during real testing if you collect more endpoints during recon.
2. Proxy
The intercepting proxy in BurpSuite enables the user to view and change the contents of requests and answers while they are being sent. Additionally, it eliminates the need for copy-and-paste by allowing the user to pass the request or answer that is being monitored to another pertinent BurpSuite tool. The proxy server can be configured to run on a specific loop-back IP address and port. Additionally, the proxy may be set up to block particular kinds of request-response pairings.
3. Intruder
It is a fuzzer that runs a collection of values across an input point. The results are examined for success/failure and content length after the values have been executed. The response code or response's content length changes as a result of an anomaly most frequently. For its payload slot, BurpSuite supports dictionary files, brute-force attacks, and single values. The invader is employed for:
- Brute-force assaults against password forms, pin forms, and other forms of this nature.
- Dictionary attacks on password fields on forms are thought to make them susceptible to XSS or SQL injection.
- Rate limitation on the web app is being tested and attacked.
4. Repeater
A user can submit requests repeatedly with manual adjustments using a repeater. It's employed for:
- Examining if the user-provided values are being examined.
- How successfully is the verification of user-supplied values being carried out?
- What values are expected by the server for an input parameter or request header?
- What happens when the server receives unexpected values?
- Is the server using input sanitization?
- How thoroughly the user-supplied inputs are sanitized by the server?
- What kind of cleanliness practices does the server employ?
- Which cookie is the real session cookie out of the ones that are already there?
- If there is a means to get around CSRF protection and how is it put into practice?
5. Sequencer
The sequencer, an entropy checker, verifies the unpredictability of tokens produced by the webserver. These tokens, like cookies and anti-CSRF tokens, are typically used for authentication in sensitive processes. The ideal way to produce these tokens is completely random, which will distribute the likelihood of each potential character appearing at each location equally. Bitwise and characterwise approaches should be used to accomplish this. This hypothesis' validity is examined with an entropy analyzer.
This is how it works: first, it is thought that the tokens are random. The tokens are then put to the test using specific criteria for certain traits. The definition of a "significance level" is a minimal value of probability that a token will demonstrate for a characteristic, such that the token's randomness hypothesis will be rejected if the token's characteristic probability is below the significance level. This utility may be used to discover weak tokens and show how they are made.
6. Decoder
The decoder provides a list of common encoding techniques such as URL, HTML, Base64, Hex, and so on. When searching for specific data chunks inside the values of parameters or headers, this tool is quite helpful. Additionally, it is employed in the development of payloads for several vulnerability classes. Primary instances of IDOR and session hijacking are also uncovered using it.
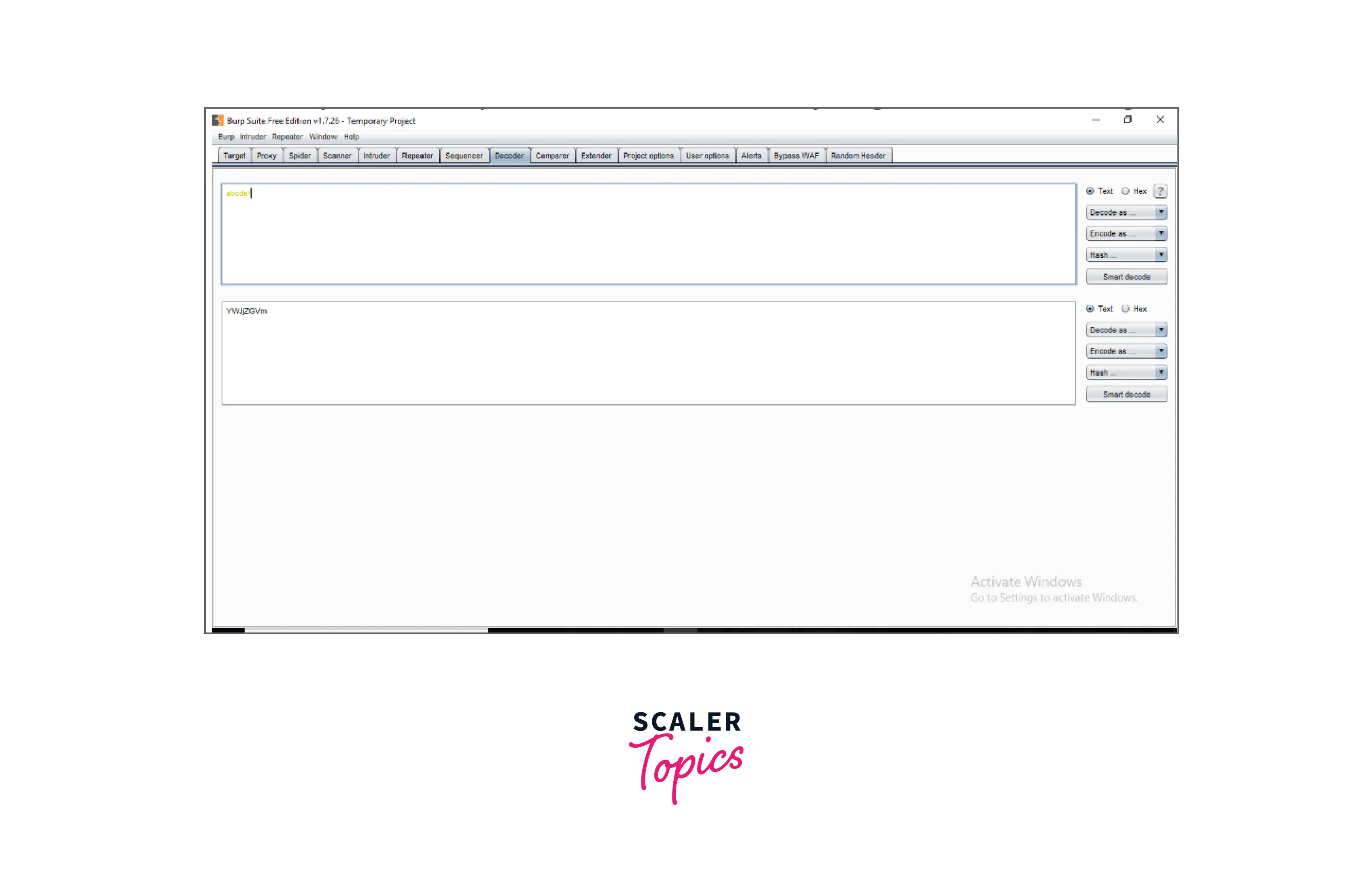
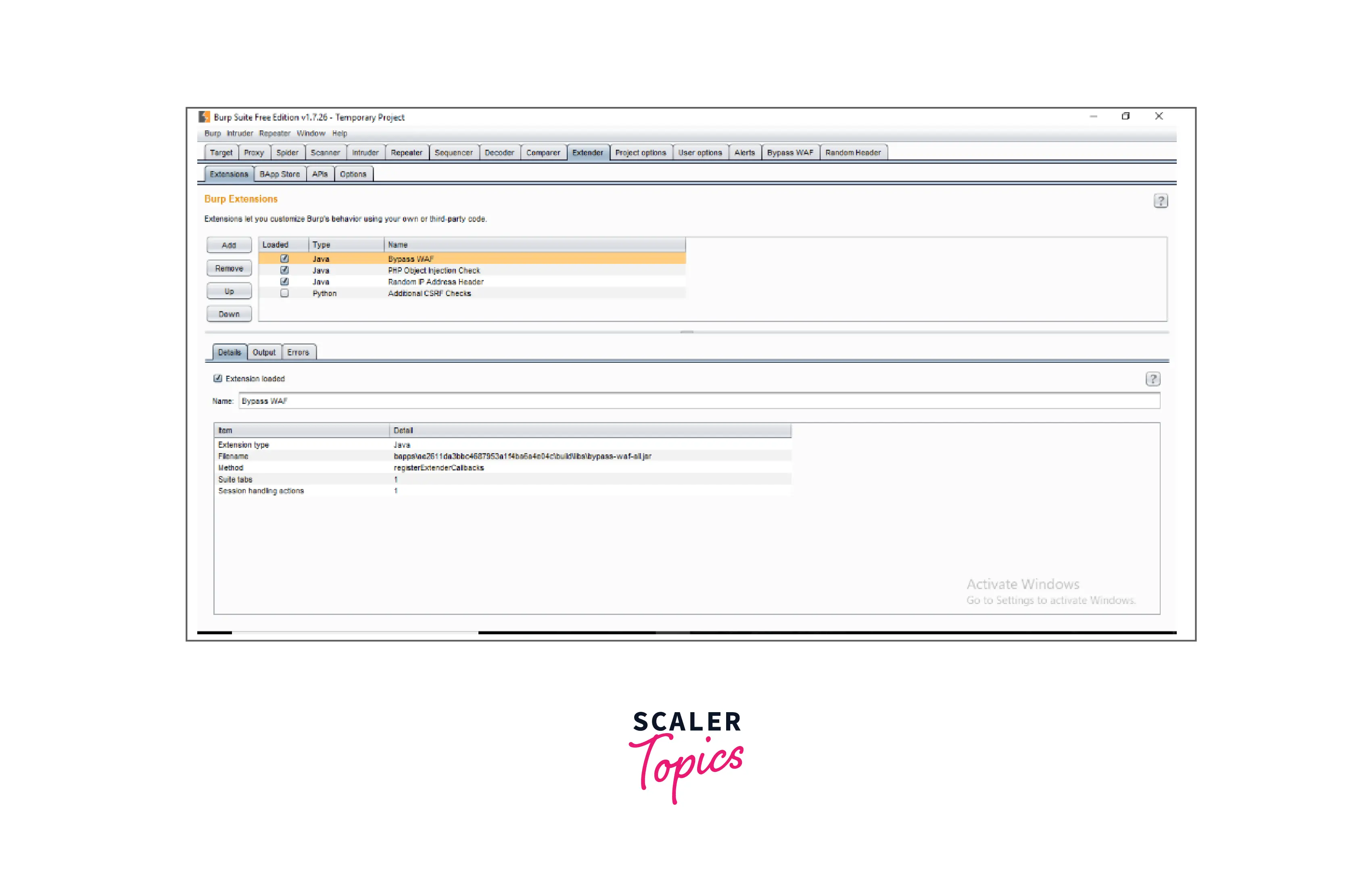
7. Extender
BurpSuite enables the integration of extra components into the toolkit to expand its functionality. These external components are referred to as BApps. These perform the same tasks as browser extensions... The Extender window allows you to examine, modify, install, and remove them. Some of them are supported by the free community version, while others need the professional version, which is a paid upgrade.
8. Scanner
The community edition does not have a scanner. It automatically analyses the website for a variety of common vulnerabilities and provides them together with details on the reliability of each discovery and the difficulty of exploiting them. It is routinely updated to add brand-new, and lesser-known vulnerabilities.
Testing with Burp Suite
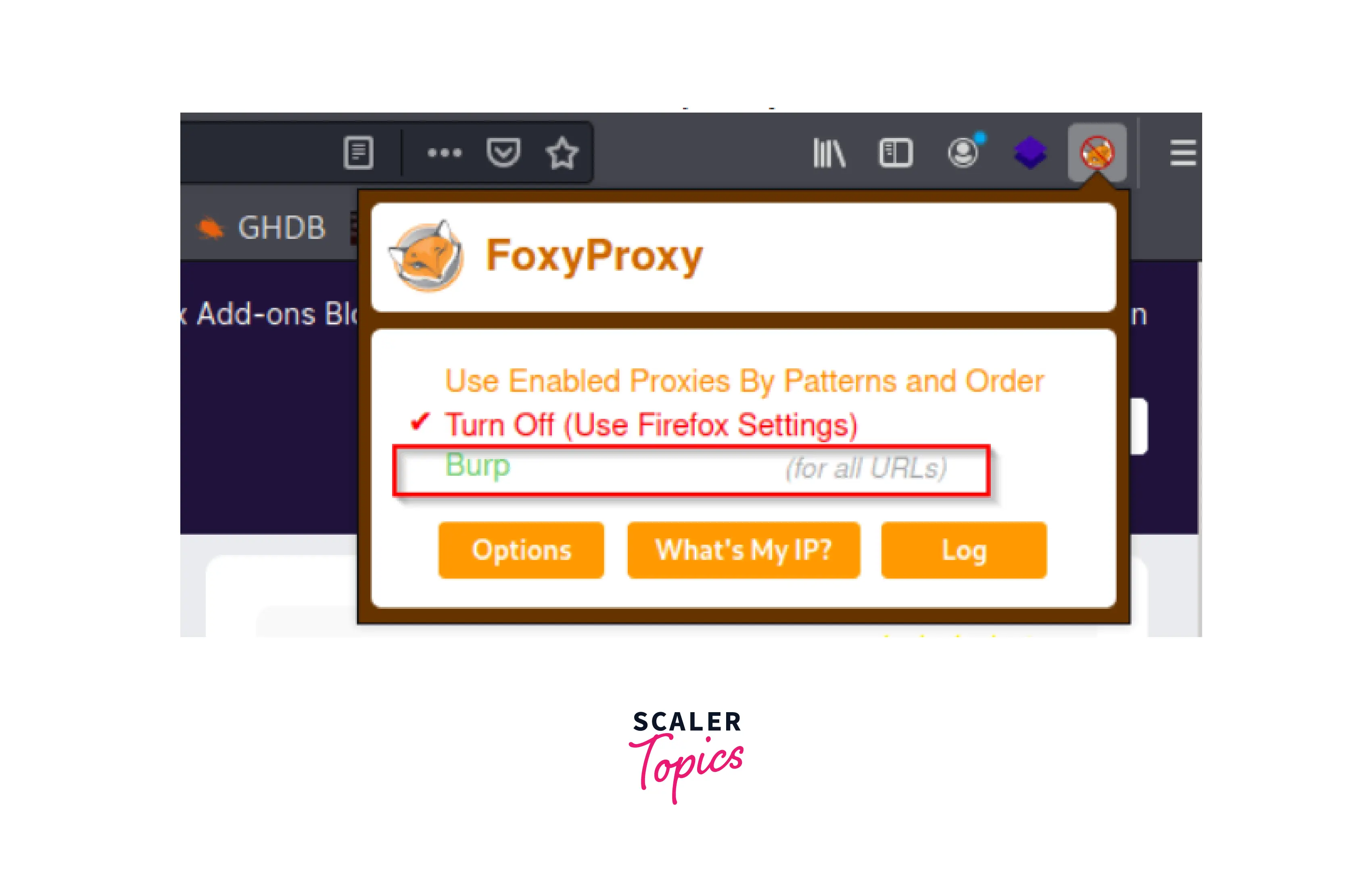
- To start our proxy, we must first ensure that the foxy proxy is running by clicking the fox icon in our browser, followed by Burpsuite:
- Then, in Burp Suite, we choose the proxy tab and select the intercept is off button to activate it.
- Now, if we go back to our browser and try to reload our DVWA page or visit another website, it will freeze. This means that Burp Suite has interrupted or paused our request so that we may influence it.
- In the proxy tab of Burp Suite, we can observe that the HTTP request was intercepted:
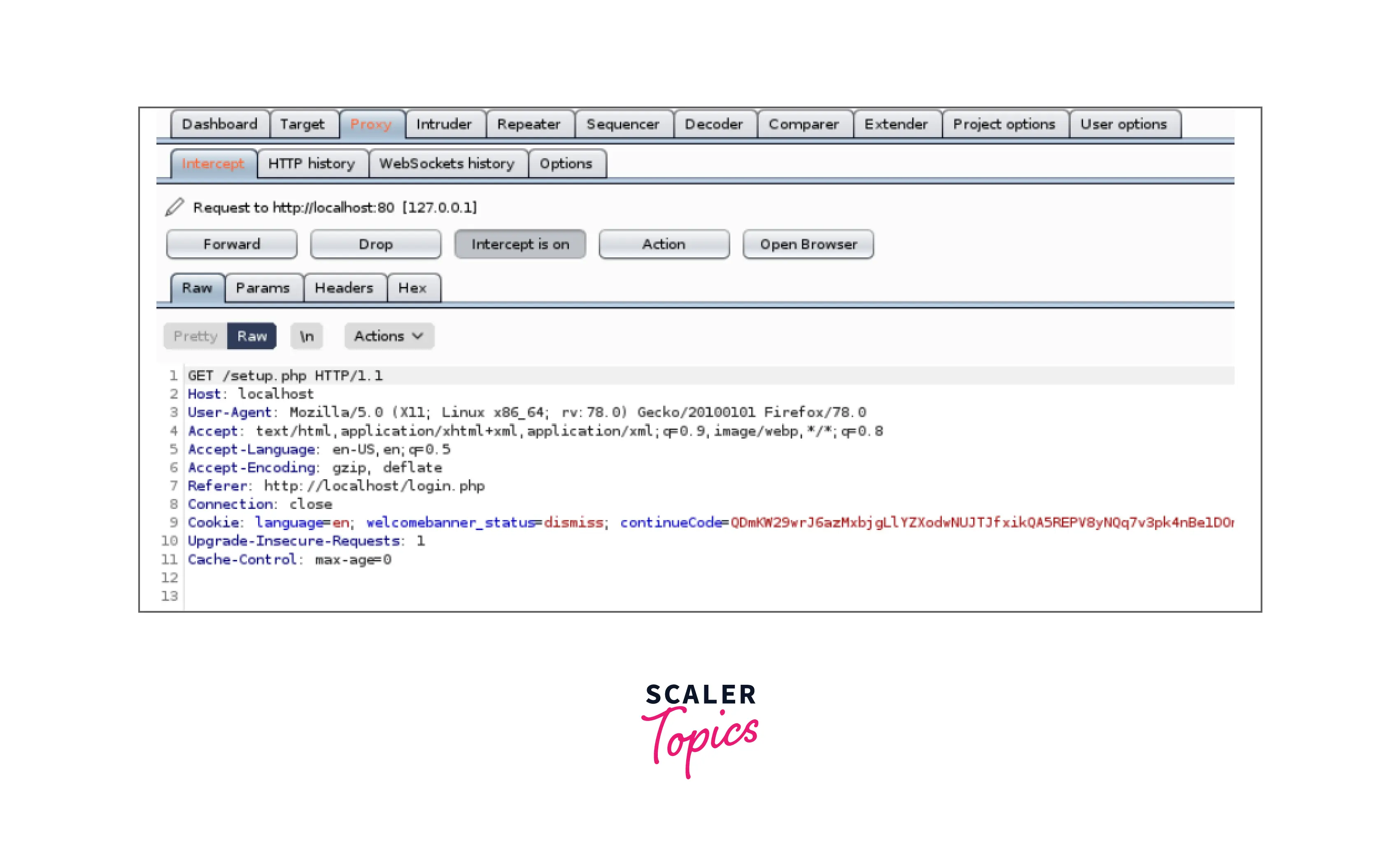
- All we have to do is press the Forward button to send the request.
- When we return to our browser, we'll notice that our page has been refreshed. Several tools in Burp Suite may be used to manipulate our request. They consist of:
- Target: Provides a summary of the functionality and content we are aiming for.
- Proxy: Enables us to intercept, examine, and alter communications between the browser and the desired web application.
- Spider: Facilitates automated web application crawling for us.
- Repeater: This allows us to modify and reissue HTTP requests to automatically review application replies. This is helpful if we want to repeatedly request the same page with different parameters to see how an application responds.
How to Use Burp Suite for Penetration Testing?
Burp's browser may be used for penetration testing and needs no further settings.
- Navigate to the Proxy > Intercept tab and choose Open Browser to start Burp's browser. This will launch a fresh browser session where Burp will automatically proxy all traffic. This may even be used to test HTTPS.
- Once Burp is operating and the Burp browser is open, go to the Proxy > Intercept tab and make sure interception is enabled. Next, open a browser window and navigate to any URL.
- The Intercept tab in the browser displays each HTTP request that is performed. Each communication is available for viewing and editing as necessary. After finishing your edits, click the Forward button to submit the request to the target web server. If there are any outstanding intercepted messages, you must forward them all for the browser to finish loading the pages it is waiting for.
- If necessary, you may turn the Intercept on/off button so that you can browse regularly without being tracked.
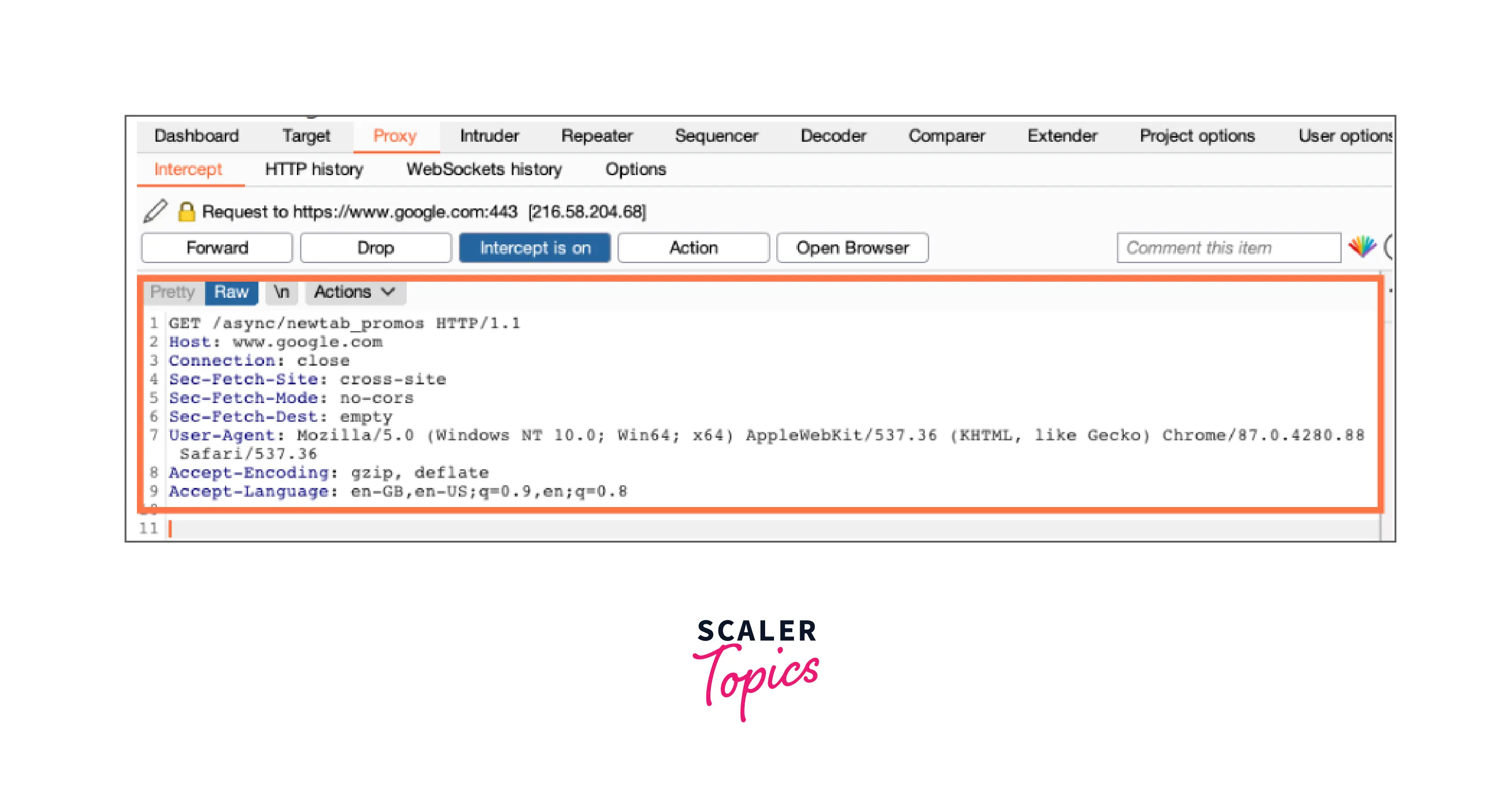
- Burp retains track of all requests and responses as you navigate around an application while it is running, even when the intercept capability is off. This information is kept under the Proxy > HTTP history tab. You may go over the list of requests you've made from this tab.
To view the whole request and answer in the message editor window, select a row in the table.
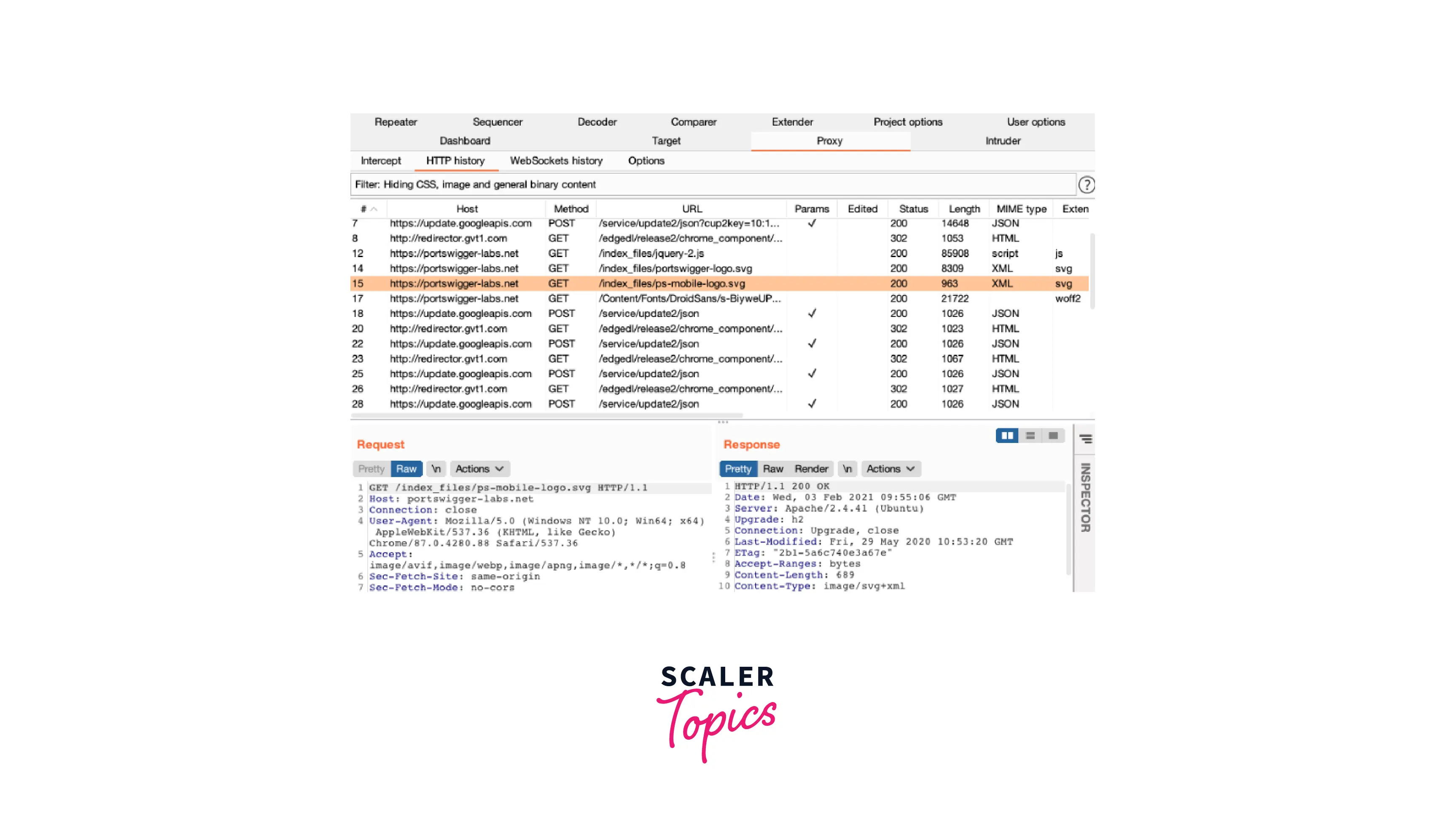
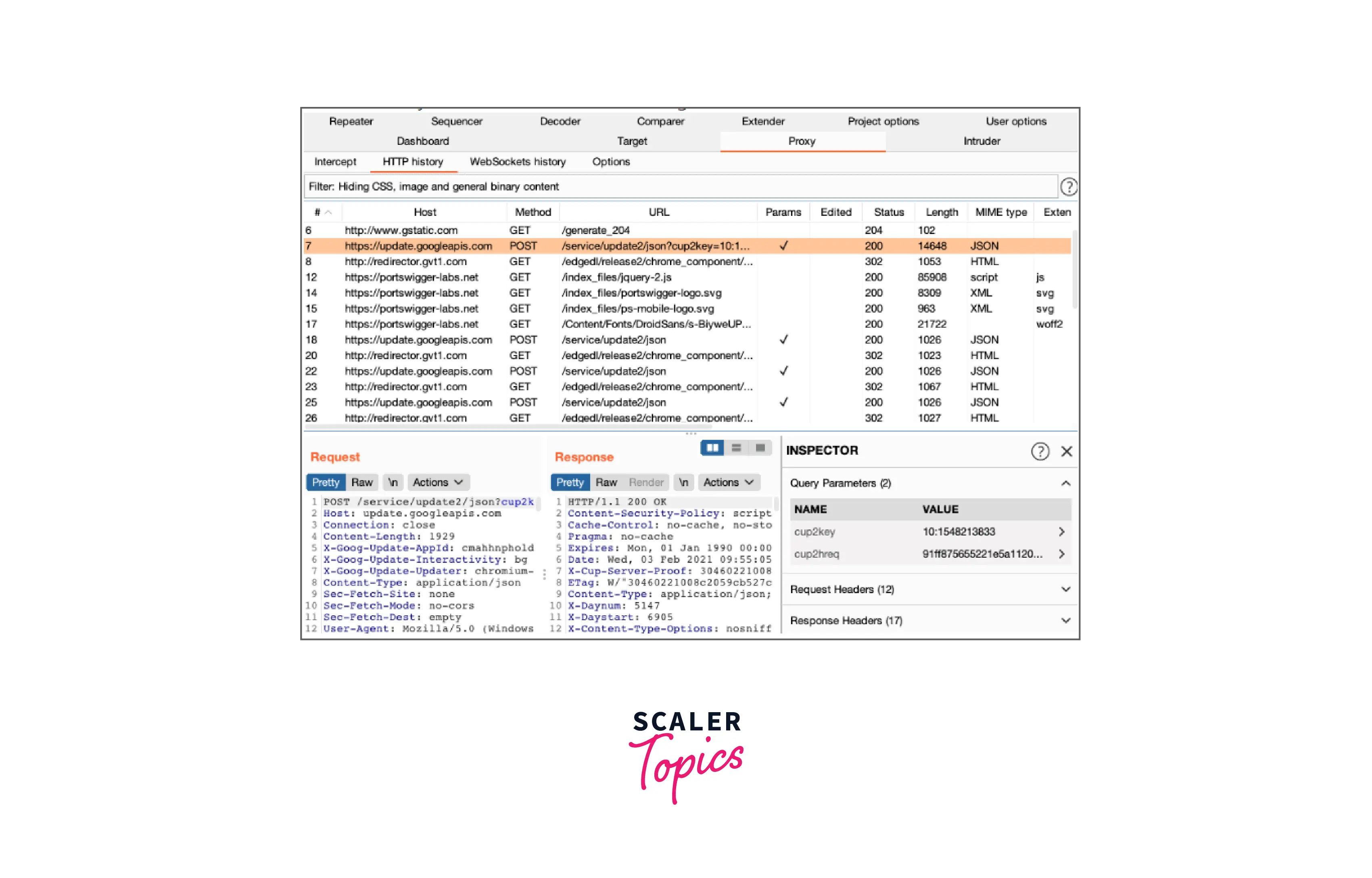
- You may rapidly access several features that assist you in analyzing potentially interesting elements discovered in messages by using the Inspector. For instance, when you go deeper into an encoded item in the inspector, the correct decoding steps will be applied so that you may analyze the value in a more comprehensible manner.
You may also modify this decoded value in the Inspector for editable messages, such as those in Burp Repeater. As you enter, the appropriate encodings are automatically added to the value once again.
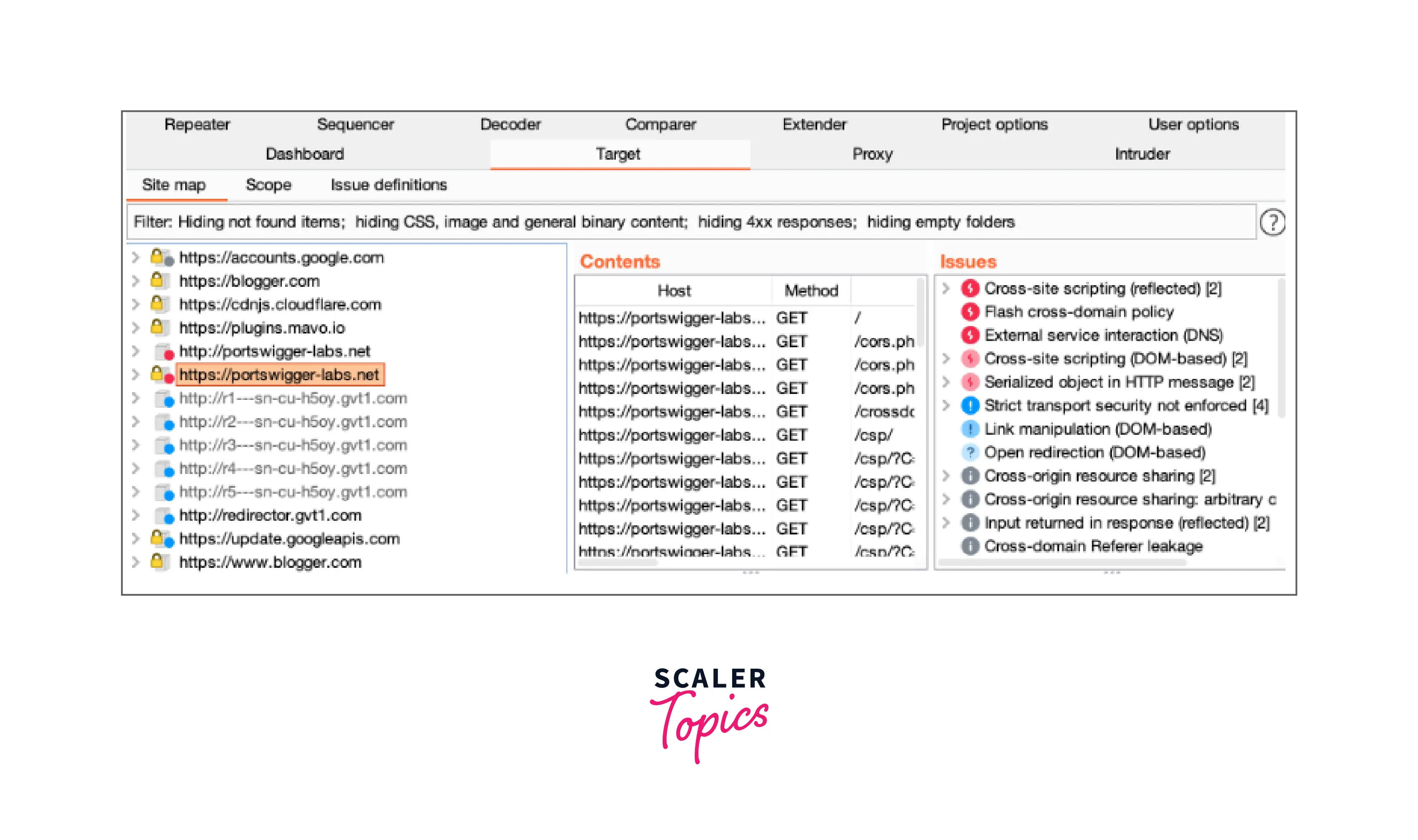
- Burp automatically generates a site map for the target application as you explore. This is shown under the Target > Site map tab.
Both the content that Burp has deduced from replies to your queries and all of the URLs you have visited in the browser are included in the site map. Requested things are displayed in black, while all other items are displayed in grey. The tree's branches may be expanded, things can be chosen, and the entire requests and answers can be shown (where available).
Visit Using the Target tool for further information. By setting up an appropriate live task, you may decide which material is updated on the site map as you navigate.
- With Burp Suite, the user has complete control over how activities are carried out. The ability to transfer HTTP requests across the Burp tools to complete specific tasks is the foundation of Burp's penetration testing methodology.
Sending messages is possible from the Proxy > Intercept, HTTP history, and Site Map tabs as well as from wherever else in Burp where HTTP messages are shown. To accomplish this, choose one or more messages, and then transmit the request to another tool using the context menu.
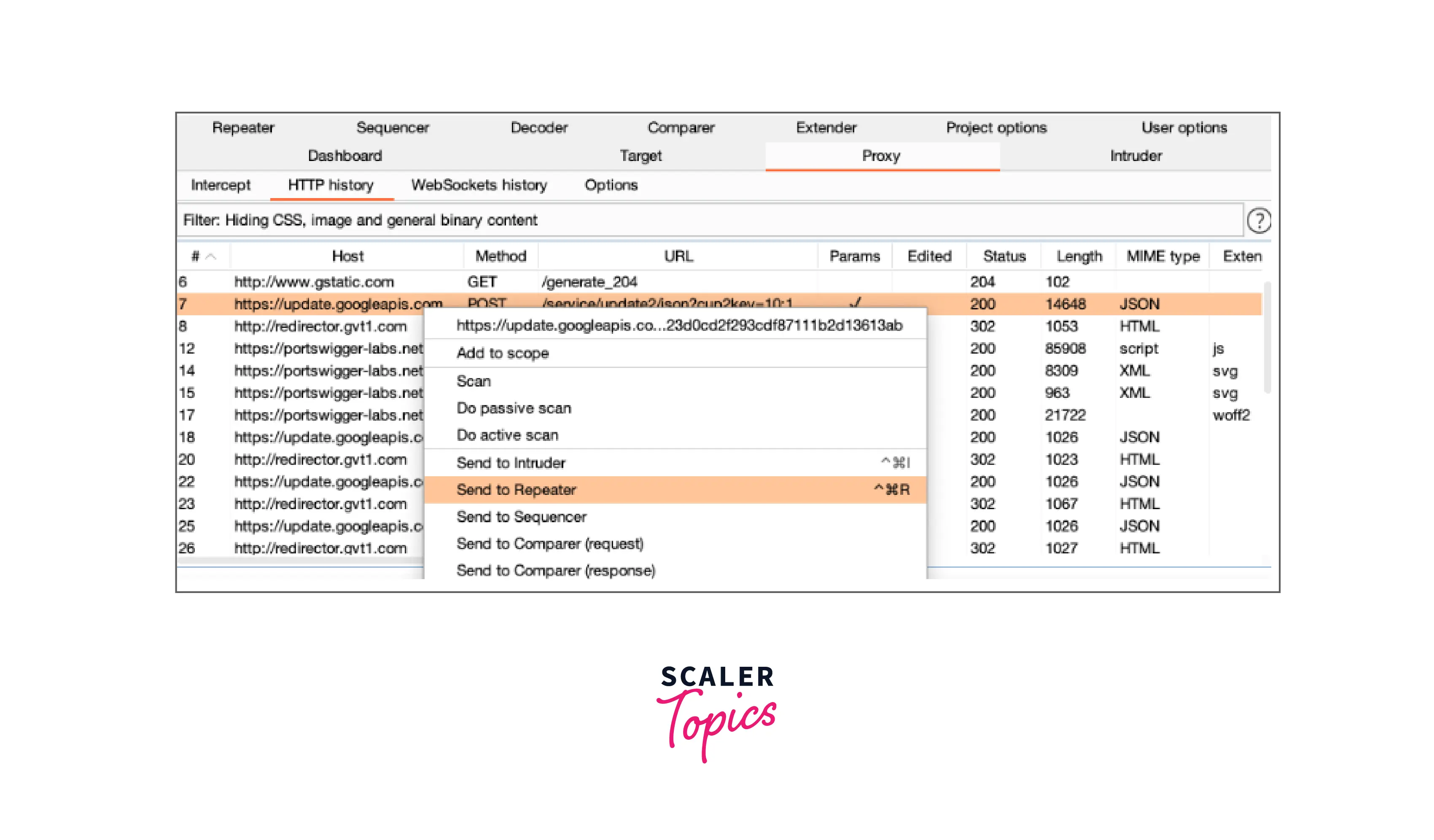
How to Use Burp Suite for Web Application Security Testing?
We'll be utilizing DVWA as our practice site for this. It is intended to aid developers in understanding the procedures they need to use to protect online applications, assist security experts in testing their knowledge and tools in a legal setting, and serve as a teaching tool for web application security.
For this training, the DVWA ISO should be loaded into our local machine.

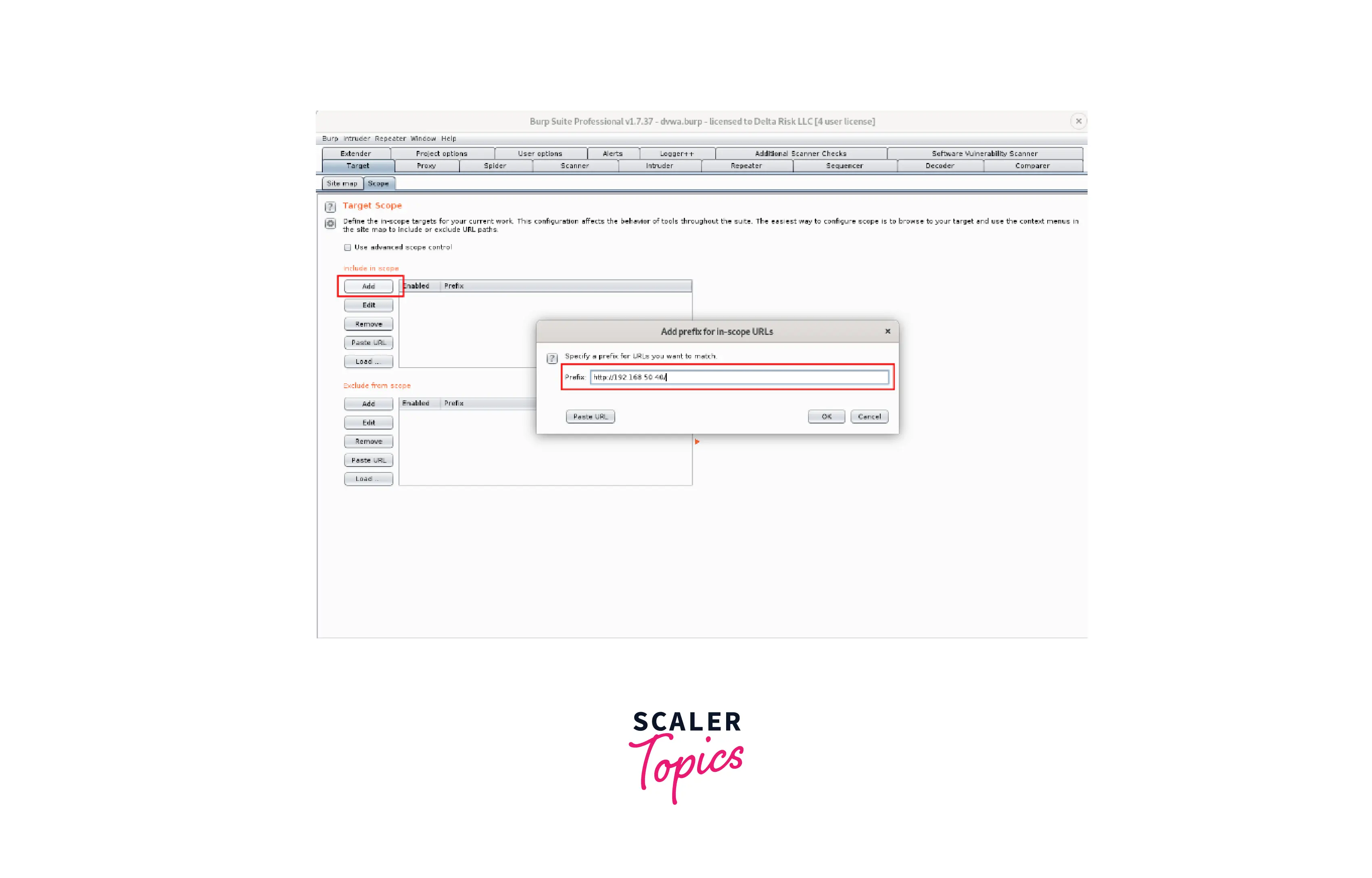
- Burp requires the website to be added to the target scope before any web application testing can begin. Get this DVWA included in our scope. You may accomplish the following by going under the Target tab: Target -> Scope -> Add.
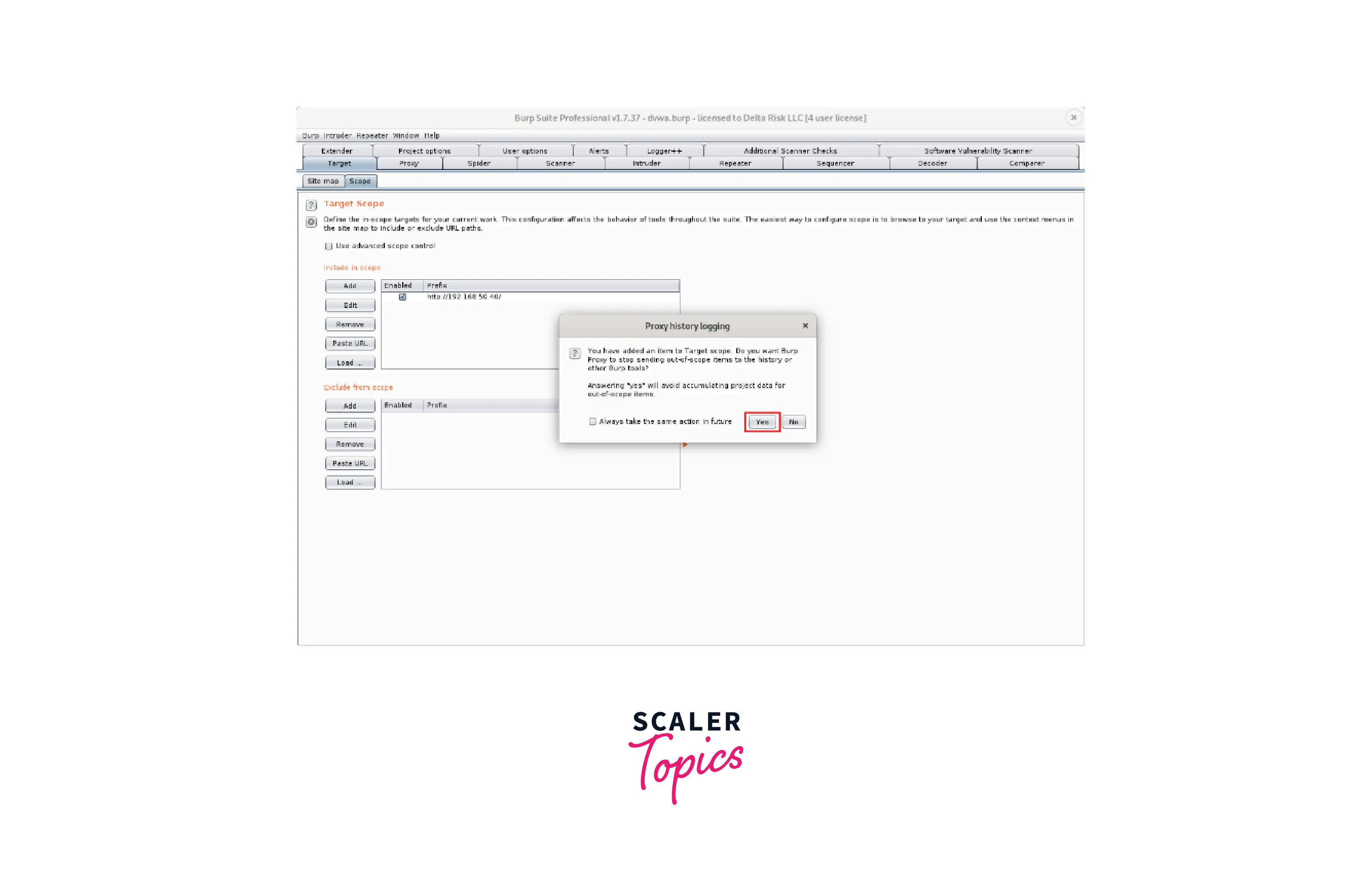
- Burp will ask you if you want to cease transmitting items that are beyond the scope of the target once you have added it successfully to history or other Burp tools. By choosing "Yes" on this question, you may keep your Burp project within reasonable bounds and prevent any out-of-scope requests from being carried out automatically.
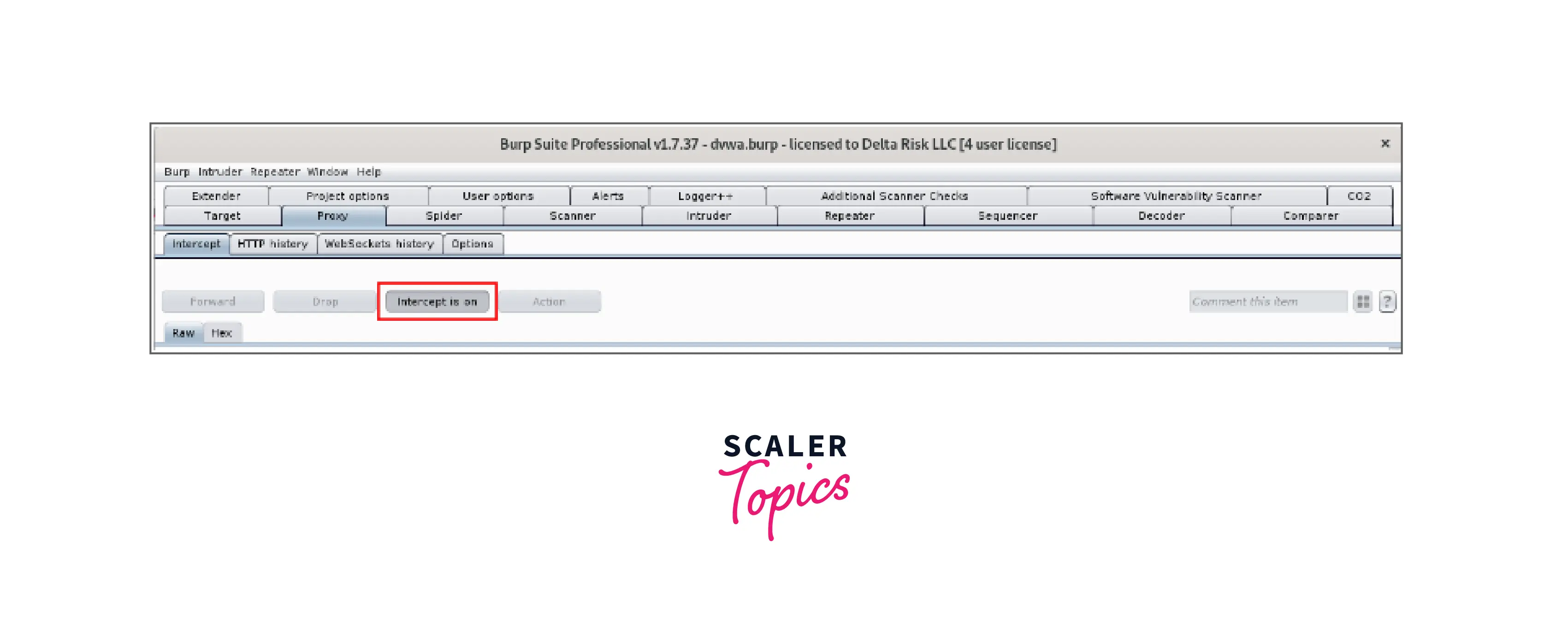
- We are now prepared to use Burp to record our first web request. The first thing to do is to make sure the "Burp" option is chosen in your FoxyProxy selection. Once there, make sure "Intercept" is turned on by going to the Proxy -> Intercept tab.
 The next web request made through Firefox will be captured and held by Burp if the "intercept" setting is enabled. Here, we'll spider and record the "login.php" request that was made from the DVWA main page. Refreshing the Firefox browser when FoxyProxy's Burp feature is enabled and the "intercept" switch is turned on records the following:
The next web request made through Firefox will be captured and held by Burp if the "intercept" setting is enabled. Here, we'll spider and record the "login.php" request that was made from the DVWA main page. Refreshing the Firefox browser when FoxyProxy's Burp feature is enabled and the "intercept" switch is turned on records the following:
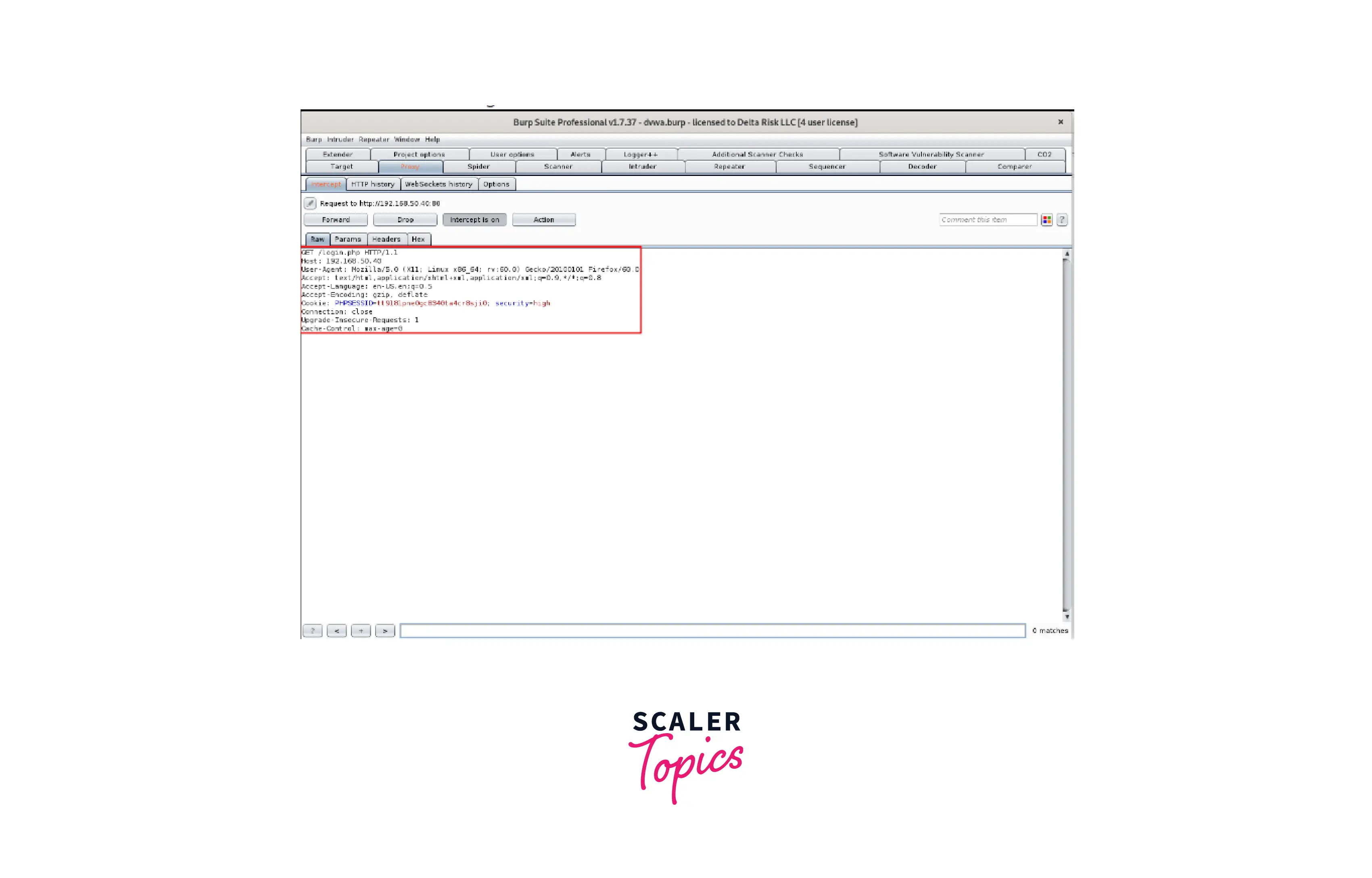
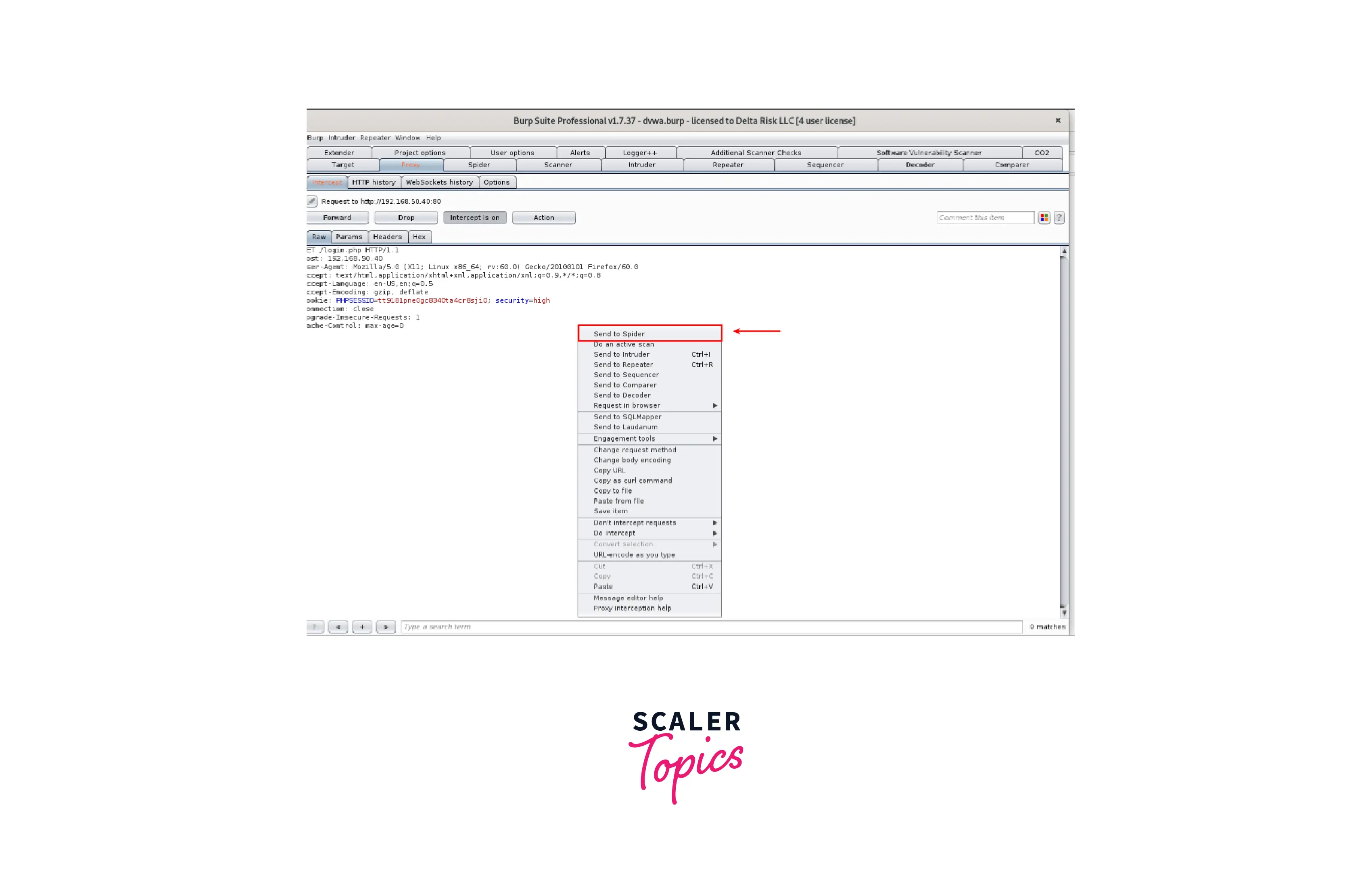
- The request has now been effectively recorded. From here, we may take on a variety of various activities. We're going to right-click on the "Intercept" screen and choose to send to Spider with the application already selected as our target scope.
- After submitting the request to the "Spider," we can view the DVWA's site map in the site map:
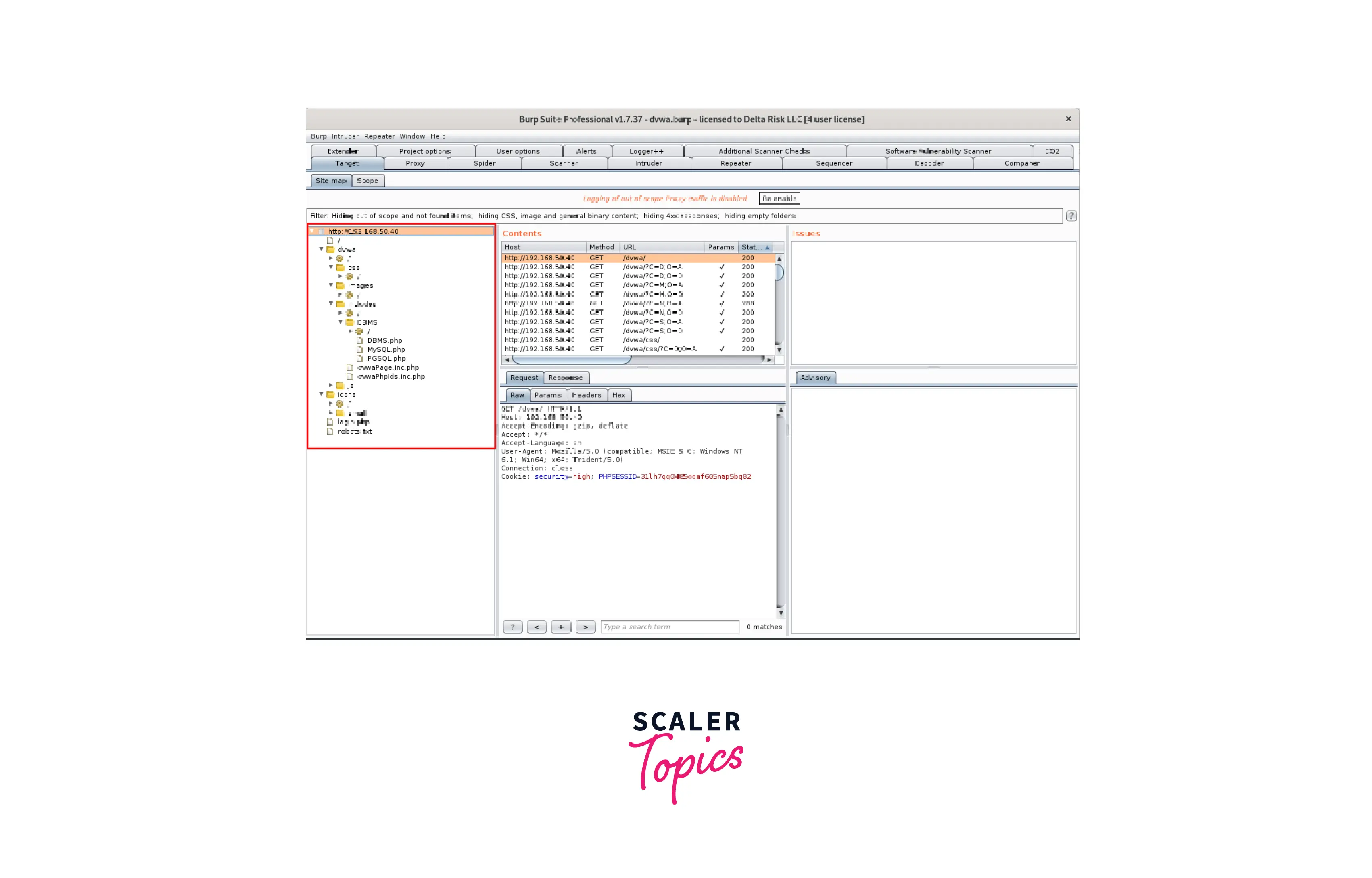 You may use this page to manually navigate through the pages and features that were found during the spidering process. You may browse the pages to see the GET and POST information as well as the requests and answers delivered through Burp.
You may use this page to manually navigate through the pages and features that were found during the spidering process. You may browse the pages to see the GET and POST information as well as the requests and answers delivered through Burp. - The final step will be to actively scan the sitemap that Burp indicated. This will look for potential flaws and exploits in the chosen application using the fantastic Burp scanning engine as well as the enhancements we've provided. To achieve this, choose "Actively scan this host" from the context menu when you right-click the sitemap's root.
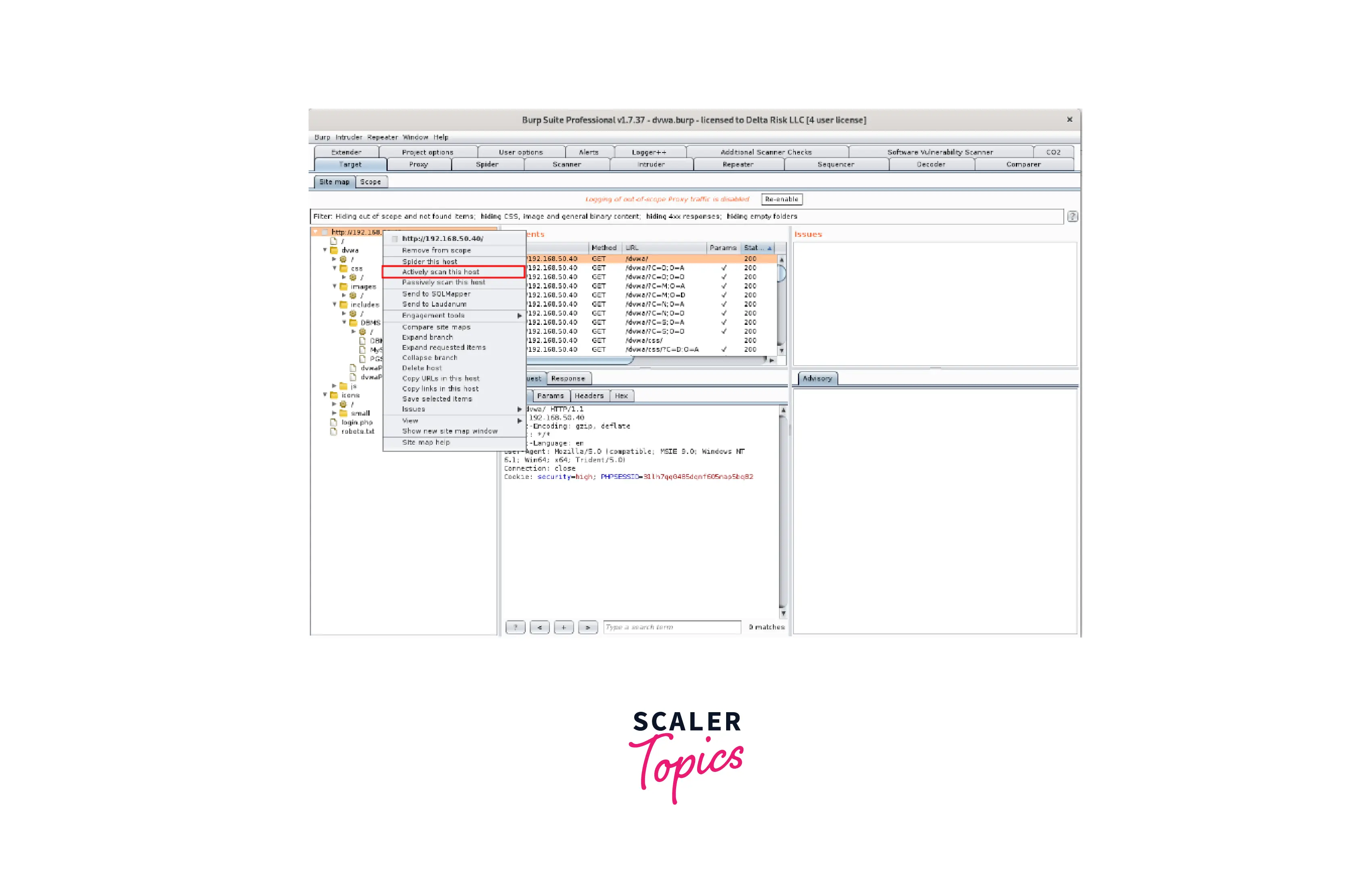
- The "Active Scanning Wizard" will show before starting any scans, providing information on the number of objects being scanned as well as some extra choices for you to tick or uncheck. For the time being, we'll keep everything at default.
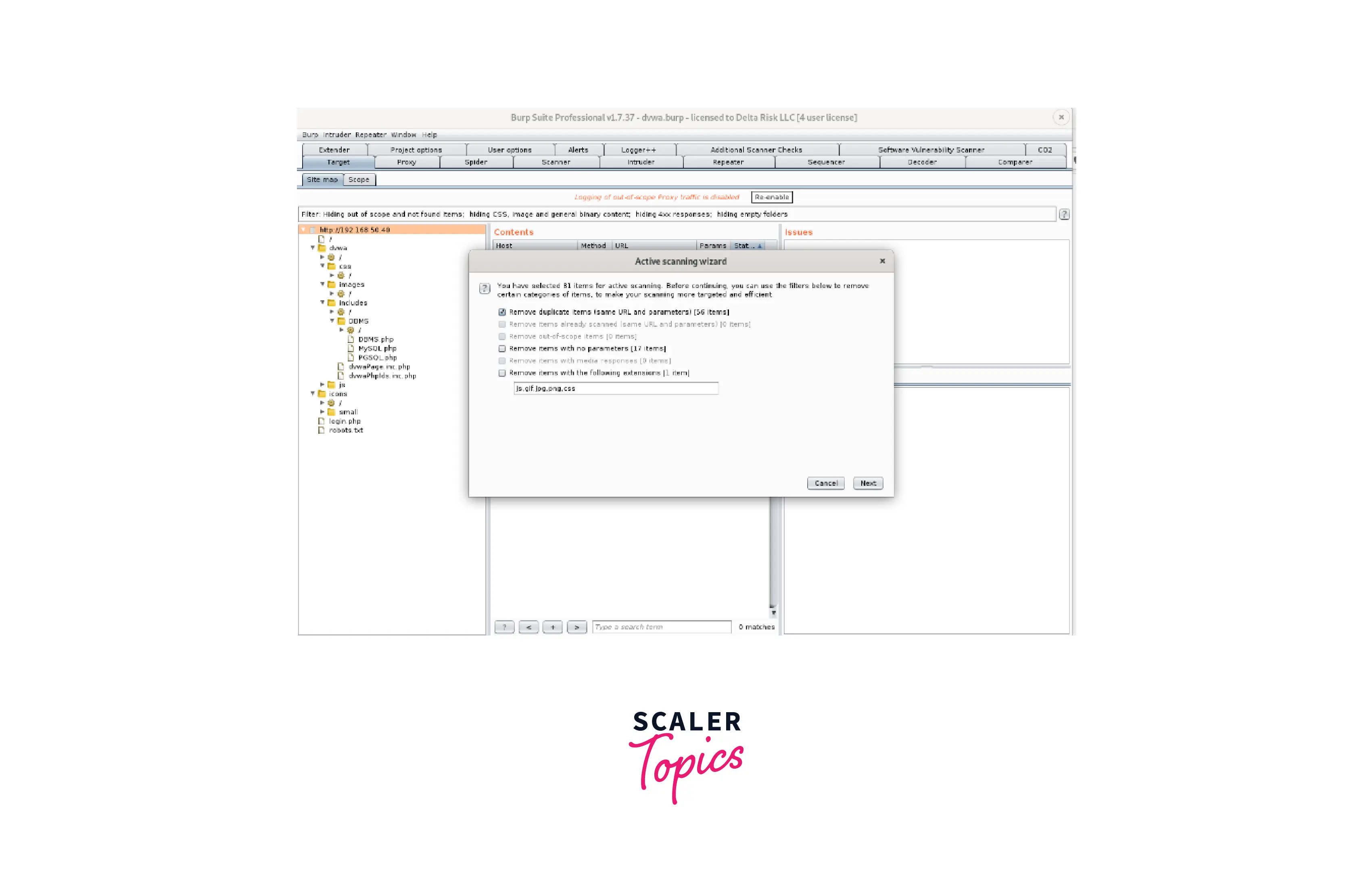
- Following the execution of the scans, you may view the status (Scanner > Scan Queue) and the most recent outcomes as displayed below. The things being scanned are broken down by "Scan Queue" into Host, URL, Status, Issues, and timestamp.
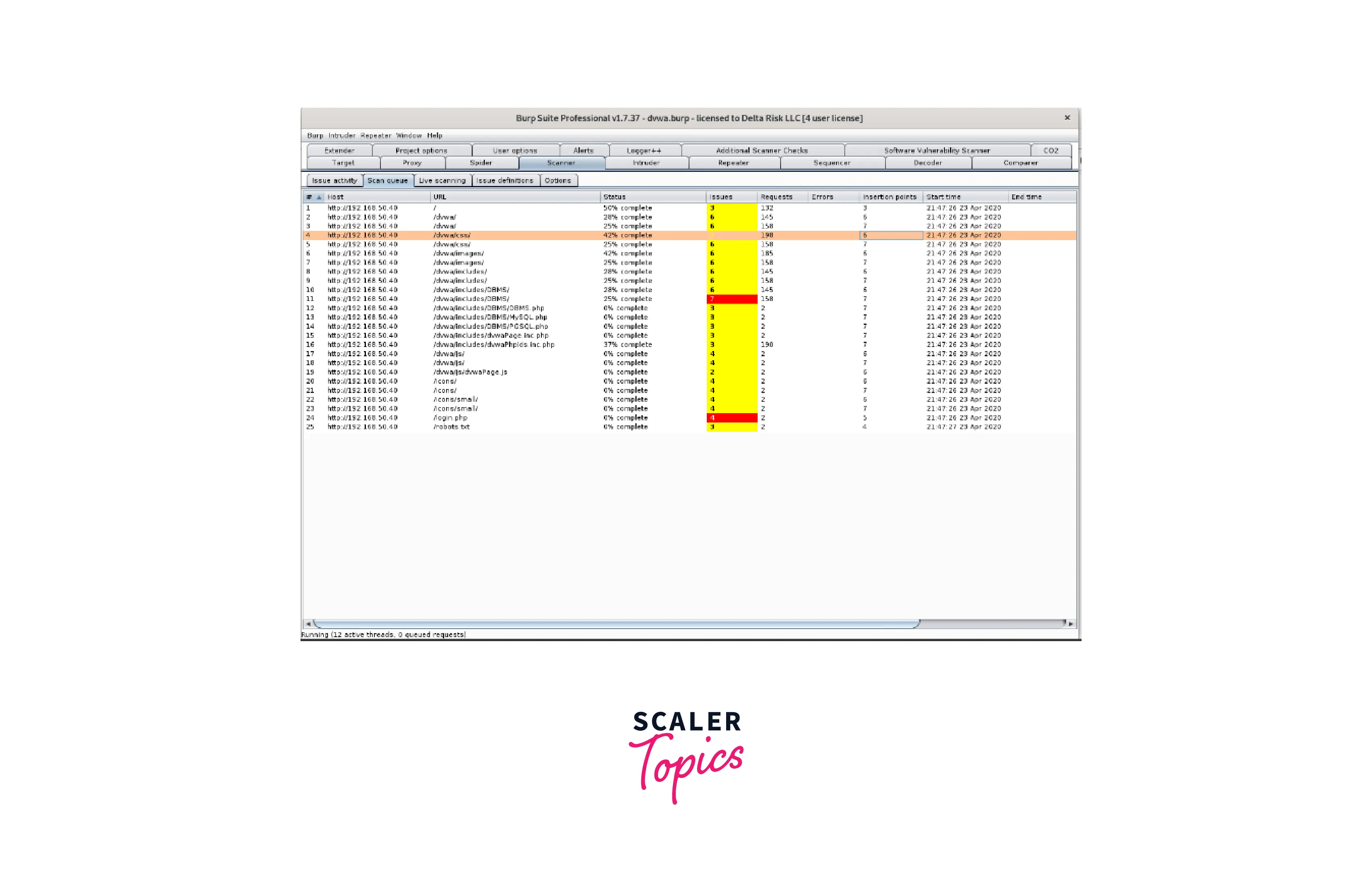
- By selecting the URL's root in the sitemap, you can always see the current status of the scans that is being done. You may browse through the discovered vulnerabilities, learn about the issue's history, and view the requests and replies communicated in the "Issues" and "Advisory" boxes, as shown below.
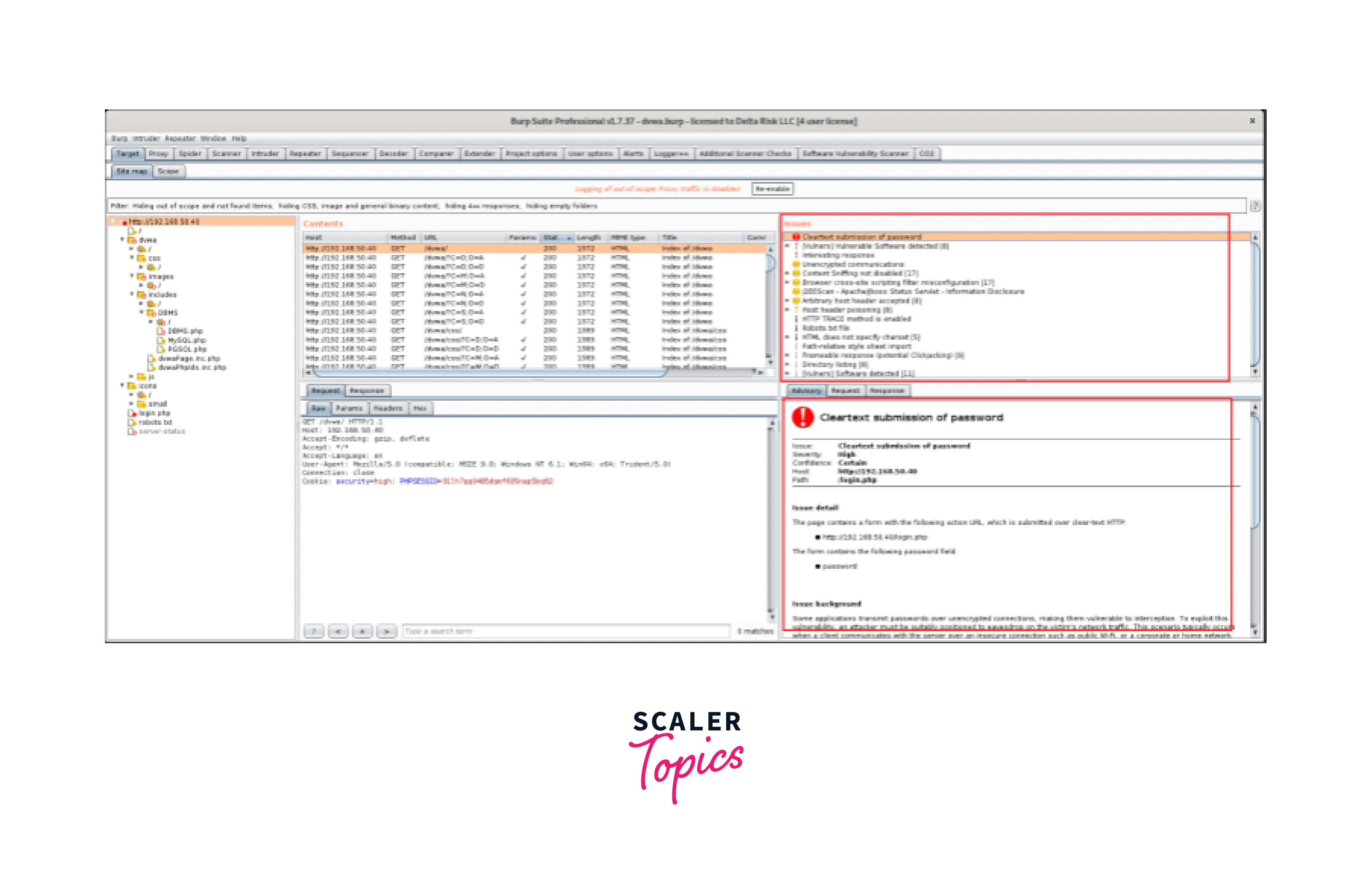 Here, the color of the alert next to the issues indicates the severity of the concerns, which may be seen. In this instance, the "cleartext submission of password" is rated as "high." During the scanning phase, Burp can frequently produce a large number of false positives, therefore manual confirmation of important discoveries is required.
Here, the color of the alert next to the issues indicates the severity of the concerns, which may be seen. In this instance, the "cleartext submission of password" is rated as "high." During the scanning phase, Burp can frequently produce a large number of false positives, therefore manual confirmation of important discoveries is required.
Conclusion
- Burp Suite Professionals is a well-known vulnerability testing tool. It is a comprehensive platform for evaluating the security of online applications.
- Along with penetration testing, Burp Suite can be used to brute-force credentials.
- Its numerous tools integrate well with one another to enable the full testing process, from the initial mapping and analysis of an application's attack surface through the discovery and exploitation of security flaws.
- We employ a variety of Burp Suite tools, including spider, intruder, repeater, etc., to do our security duty.
- Burp gives you complete control, allowing you to combine cutting-edge manual methods with cutting-edge automation to make your work quicker, more fruitful, and more enjoyable.
