Cracking the Captured Handshake
Overview
Cracking the Captured Handshake is a process aimed at exploiting vulnerabilities in Wi-Fi security protocols to gain unauthorized access to secured networks. It involves capturing the 'handshake,' a crucial authentication step during device connection. This captured data is then subjected to brute-force or dictionary attacks using specialized software and hardware to guess the correct password. It's important to emphasize that attempting handshake cracking without proper authorization is both ethically and legally prohibited, as it constitutes unauthorized access to computer systems, potentially leading to severe consequences.
Setting Up the Environment
In order to proceed with handshake cracking, it's crucial to establish the necessary environment and tools. This section will guide you through the steps to gather captured handshakes and install/configure the required software.
Gathering Captured Handshakes
Capturing handshakes is a fundamental step in the process of cracking secured Wi-Fi networks. Airodump-ng, part of the Aircrack-ng suite, is a versatile command-line tool for monitoring wireless networks and capturing data packets. Here's a detailed breakdown of the process:
- Launching Airodump-ng:
Begin by opening a terminal window and initiating Airodump-ng. Specify the wireless interface to monitor and the channel on which the target network is operating.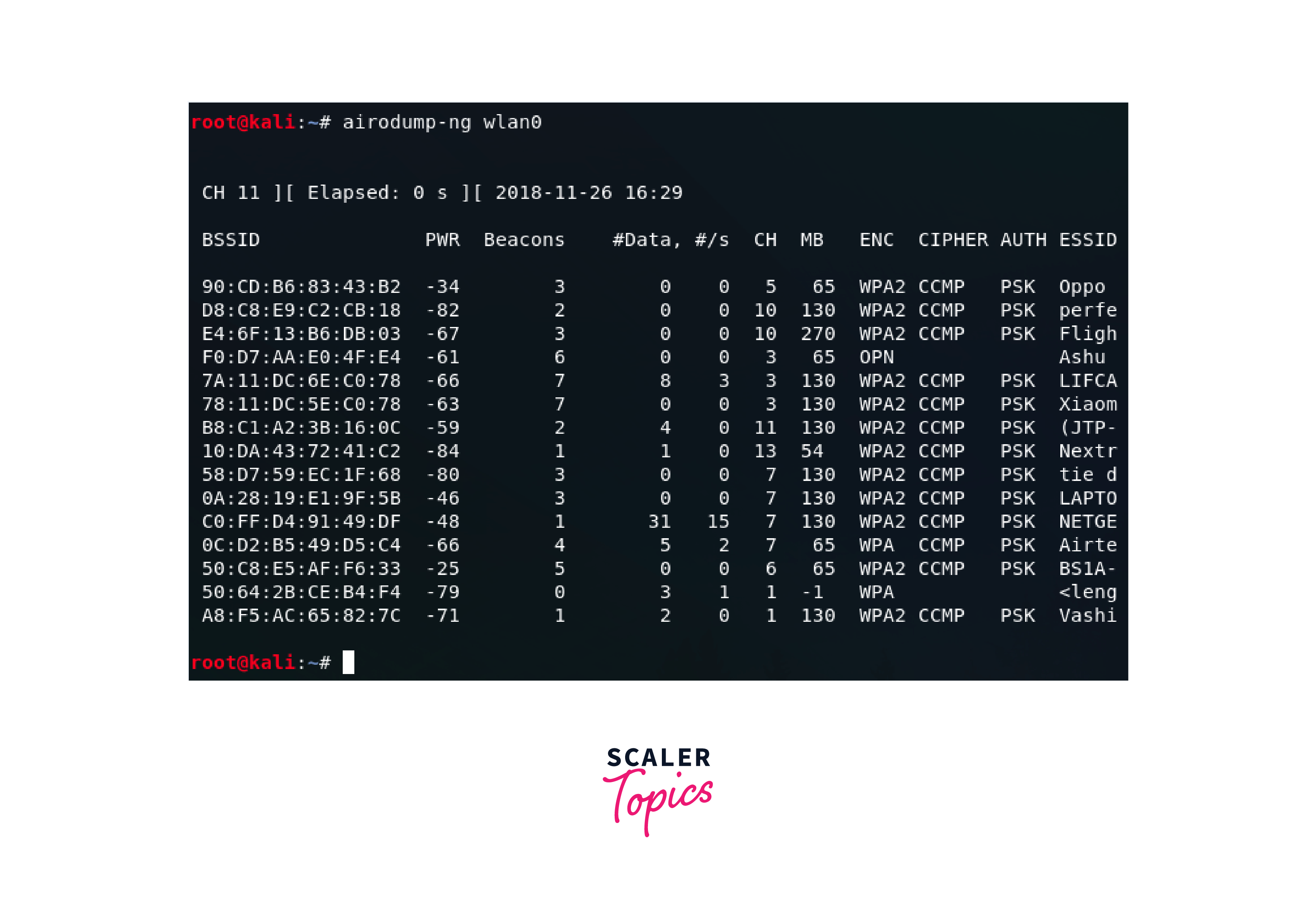
- Monitoring Nearby Networks:
Airodump-ng will display a list of nearby Wi-Fi networks, along with essential information like BSSID (MAC address of the access point), ESSID (network name), and the number of clients connected. - Capturing Handshake:
Identify the target network's BSSID and channel. Airodump-ng can be set to focus specifically on this network, capturing all relevant packets, including the handshake. - Waiting for a Handshake:
Patiently monitor the output until a successful handshake is captured. This may take some time, as it depends on network activity and the number of connected clients. - Saving Captured Data:
Once the handshake is obtained, it will be saved in a file for later use. This file will be crucial in the subsequent cracking process.
Installing and Configuring Necessary Tools
To efficiently crack captured handshakes, specific software and hardware tools are essential. Hashcat is a potent password recovery tool with support for a wide range of hashing algorithms and optimization for GPU acceleration. Here's an in-depth guide on installing and configuring Hashcat:
- Downloading and Installing Hashcat:
Visit the official Hashcat website and download the appropriate version for your operating system. Installation is typically straightforward, but be sure to follow any provided instructions. Here is the link: GitHub or HashCat
- Configuring Hashcat:
Before using Hashcat, it's crucial to set up the right options. This includes specifying the hashing algorithm used in the captured handshake, as well as selecting the attack mode (dictionary, brute-force, etc.) based on available information about the target network's security. - Choosing the Right Wordlist or Mask:
Depending on the chosen attack mode, selecting an appropriate wordlist or creating a custom mask might significantly influence the success of the cracking process. - Executing the Attack:
Once Hashcat is configured, initiate the attack using the captured handshake file and chosen parameters. Hashcat will apply the specified attack mode and attempt to find the correct password. - Monitoring Progress:
Hashcat will provide real-time feedback on its progress, including the number of password guesses per second. The time required for a successful crack depends on factors like the complexity of the password and the chosen attack mode.
Choosing an Effective Wordlist
Selecting the right wordlist is a critical aspect of the handshake cracking process. A wordlist contains a collection of potential passwords that Hashcat will systematically try against the captured handshake until a match is found. Here's a detailed guide on how to choose an effective wordlist:
- Wordlist Sources:
- Common Wordlists:
These include lists of commonly used passwords, which are a good starting point. Examples include "rockyou.txt", a widely used wordlist compiled from various data breaches. - Specialized Wordlists:
Depending on the target, specialized wordlists tailored to specific industries, interests, or regions can be highly effective. For instance, a list of popular sports teams for a sports-related network. - Custom Wordlists:
Crafting a custom wordlist based on specific knowledge about the target (e.g., favourite sports teams, pet names, significant dates) can significantly improve the chances of success.
- Wordlist Size and Complexity:
- Balancing Size and Efficiency:
Larger wordlists may contain more potential passwords but can also increase the time needed for the cracking process. Consider the trade-off between comprehensiveness and speed. - Adding Variants and Leetspeak:
Supplementing a basic wordlist with variants (e.g., "password123" and "p@ssw0rd") and common leetspeak substitutions (e.g., replacing 'e' with '3') can greatly expand the coverage.
- Hybrid Attacks and Rules:
- Combining Wordlists:
Applying hybrid attacks involves combining multiple wordlists or applying rules to generate variations. This approach can be highly effective, especially when the target password may be a combination of common words. - Rulesets for Transformation:
Hashcat allows the application of rulesets that perform transformations on words in the wordlist (e.g., capitalization, appending numbers). These rules can significantly increase the chances of a successful crack.
- Updating and Fine-Tuning:
- Regular Updates:
Wordlists should be periodically updated to incorporate new trends and data breaches. Communities and forums dedicated to security often share updated and curated wordlists. - Fine-tuning for Specific Targets:
When specific information about the target is available (e.g., known preferences or affiliations), customizing the wordlist accordingly can significantly enhance success rates.
Using Hashcat for Handshake Cracking
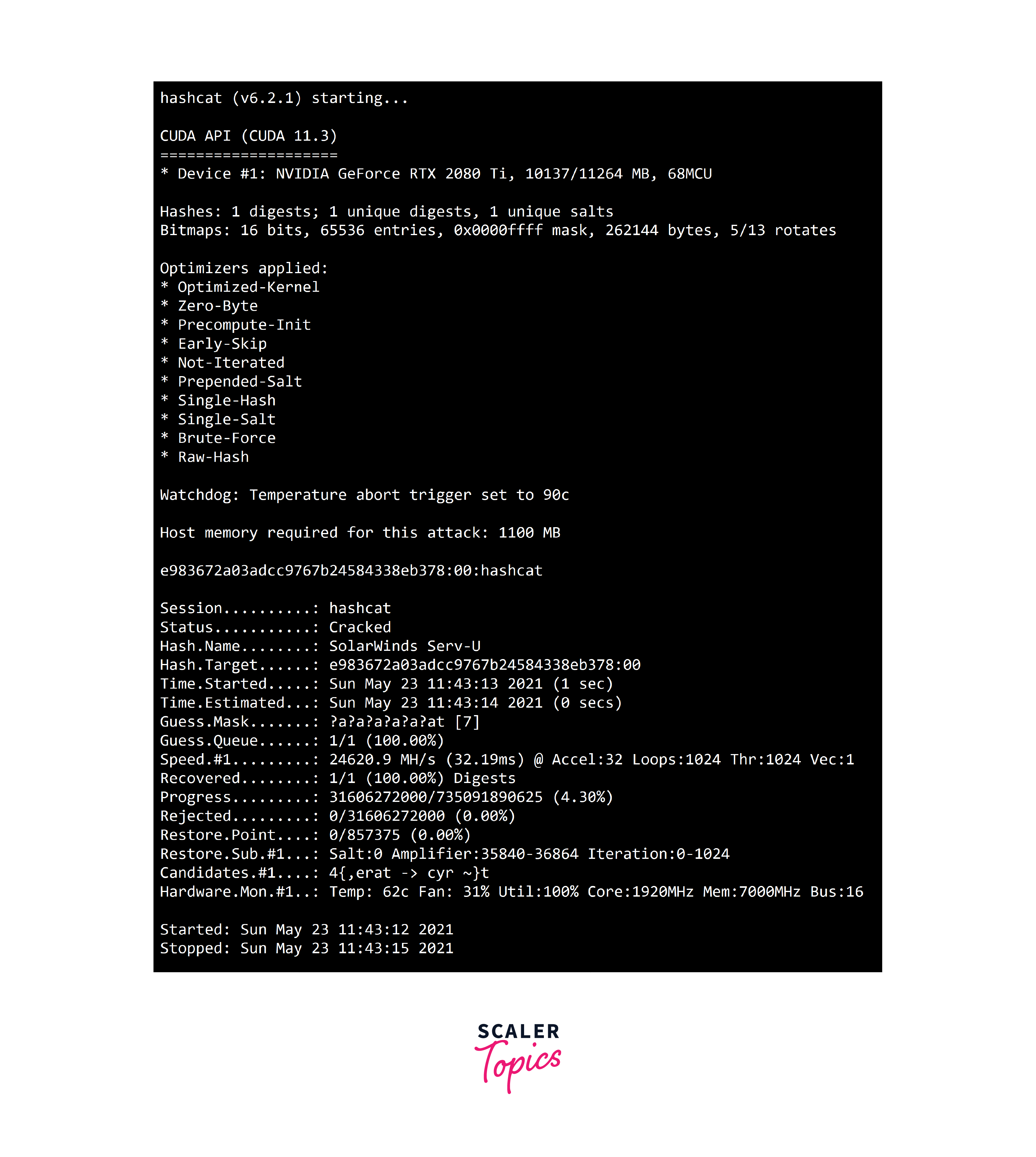
Hashcat is a powerful password recovery tool that excels in efficiently cracking captured handshakes. Here are the steps to utilize Hashcat effectively for this purpose:
-
Choosing the Correct Attack Mode:
- Dictionary Attack:
This mode uses a predefined list of potential passwords (the wordlist) to attempt a match. It's highly effective if the actual password is in the list. - Brute-Force Attack:
This method systematically tries every possible combination of characters until the correct password is found. It's exhaustive but can be time-consuming for complex passwords. - Rule-Based Attack:
This mode combines dictionary words with predefined rules to generate variations. It's effective for passwords with common patterns or substitutions. - Mask Attack:
This approach is useful when you have specific information about the password's structure (e.g., length, character types).
- Dictionary Attack:
-
Specifying Hashing Algorithm and Mode:
- -m Flag:
Use the -m flag to specify the hashing algorithm used in the captured handshake file (e.g., WPA/WPA2 hashes are typically identified with mode 2500). - Choosing Hashcat Modes:
Depending on the targeted network's security, select the appropriate mode to ensure Hashcat interprets the captured handshake correctly.
- -m Flag:
-
Loading Handshake Data:
Use the -m flag to specify the hash type followed by the path to the captured handshake file. Hashcat will then use this file as the input for the cracking process. -
Selecting Wordlists and Rules:
- Use the -a flag followed by the attack mode number to specify the chosen mode (e.g., -a 0 for dictionary attack).
- Specify the wordlist to be used with the -w flag followed by the path to the wordlist file.
- For rule-based attacks, apply rules using the --rule-file flag followed by the path to the ruleset.
-
Executing the Attack:
Once all parameters are set, initiate the attack by running Hashcat. It will begin the process of trying passwords against the captured handshake. -
Monitoring Progress and Results:
- Hashcat provides real-time feedback on its progress, including the number of password guesses per second. Monitor this information to estimate the time required for a successful crack.
- Upon success, Hashcat will display the cracked password, allowing access to the secured network.
-
Handling Unsuccessful Attempts:
If the cracking process is unsuccessful, consider adjusting parameters like attack mode, wordlist, or rules. Additionally, trying a different attack mode may yield better results.
Conclusion
- Selecting the right wordlist is crucial for successful handshake cracking, with options ranging from common, specialized, to custom wordlists.
- Balancing size and complexity is important to optimize efficiency, taking into consideration the trade-off between comprehensiveness and speed.
- Hashcat is a versatile password recovery tool with various attack modes, and choosing the correct mode depends on available information about the target password.
- Specifying the hashing algorithm and loading handshake data are crucial steps in the process, ensuring Hashcat interprets the captured handshake correctly.
- Initiating the attack in Hashcat starts the process of trying passwords against the captured handshake, and real-time feedback on progress helps estimate the time required for a successful crack.
- Adjusting parameters like attack mode, wordlist, or rules may improve the chances of success, offering a troubleshooting approach when initial attempts are unsuccessful.
