Exploitation and Gaining Access
Overview
Exploitation and gaining access are crucial stages in the penetration testing methodology. These stages involve actively attempting to breach the security of a target system or network to identify vulnerabilities and evaluate the organization's overall security posture. The primary objective of exploitation and access-gaining is to simulate a real-world attack scenario and assess the target's ability to defend against it.
Exploitation and Gaining Access in the Pentester Methodology
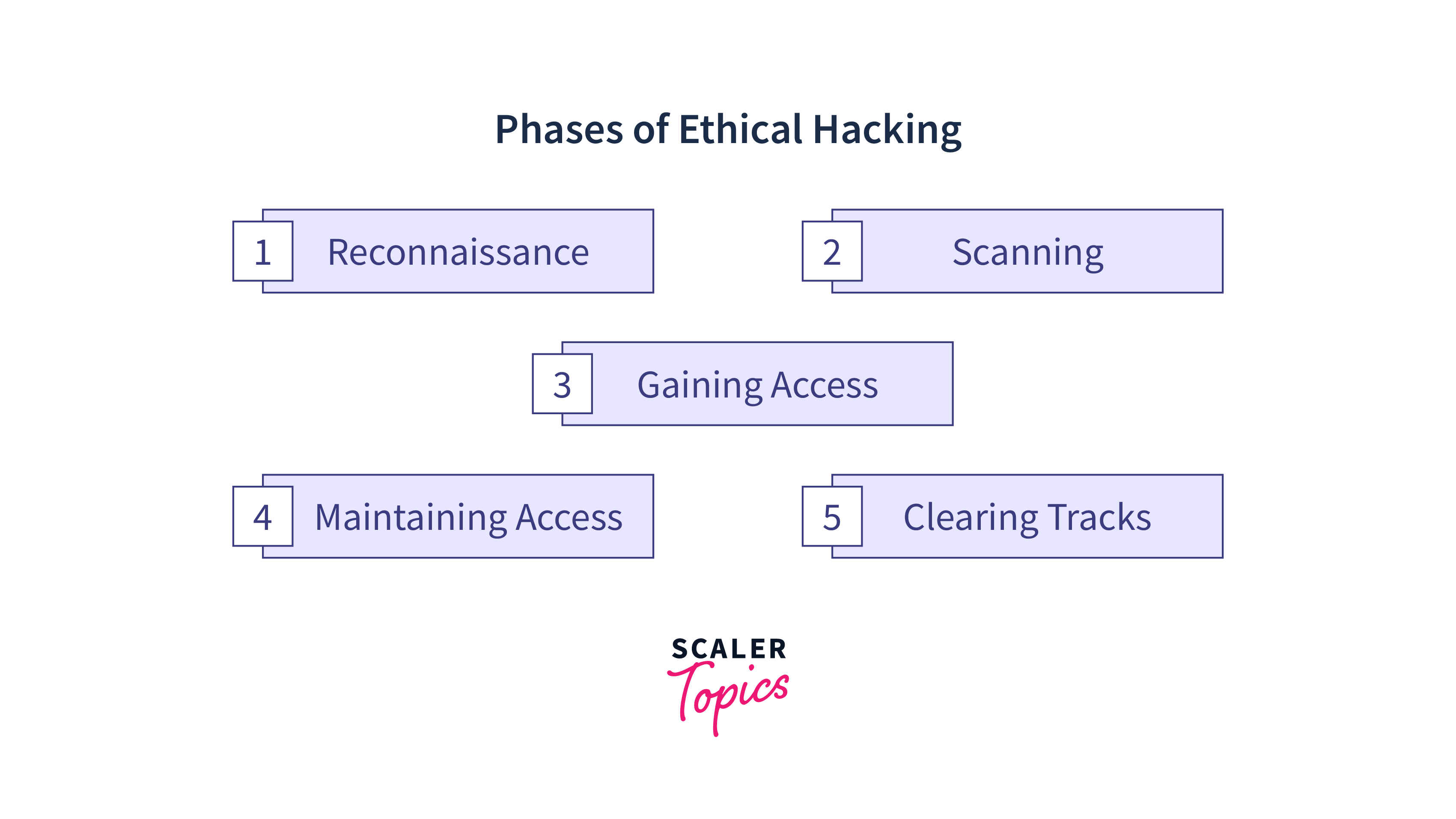
The exploitation and gaining access phase of penetration testing is a critical step in the overall penetration testing process. In this phase, the pentester attempts to use the vulnerabilities identified in the previous phases to gain access to the target system, escalate privileges, and gather information about the target. This phase typically follows the information gathering vulnerability scanning and assessment phase of a penetration test.
The goal of the exploitation and gaining access phase is to identify and exploit any security weaknesses that exist in the target system, to gain unauthorized access to the target’s system or network, as well as to gain a deeper understanding of the system's architecture and security posture. This phase requires a significant amount of technical expertise, thus the success of the exploitation phase depends on the tester’s knowledge of security exploits, hacking techniques, and the ability to use the right tools for the job.
Understanding Exploitation
With the information gained during the reconnaissance and scanning phases of pen-testing, the pentester maps the possible vulnerabilities and entry points in a target system. The aim of the pentester or ethical hacker is to get to the farthest depth into the target organization’s system or network environment and identify probable targets without getting detected. This involves bypassing security restrictions and countermeasures set by the organization. These countermeasures could be intrusion prevention systems, web application firewalls, system guards, or other measures that could hinder the ability of a pentester to complete an exploit.
To get past these countermeasures stealthily, and to gain access to the target’s system, various types of exploits and techniques are used.
What are Exploits?
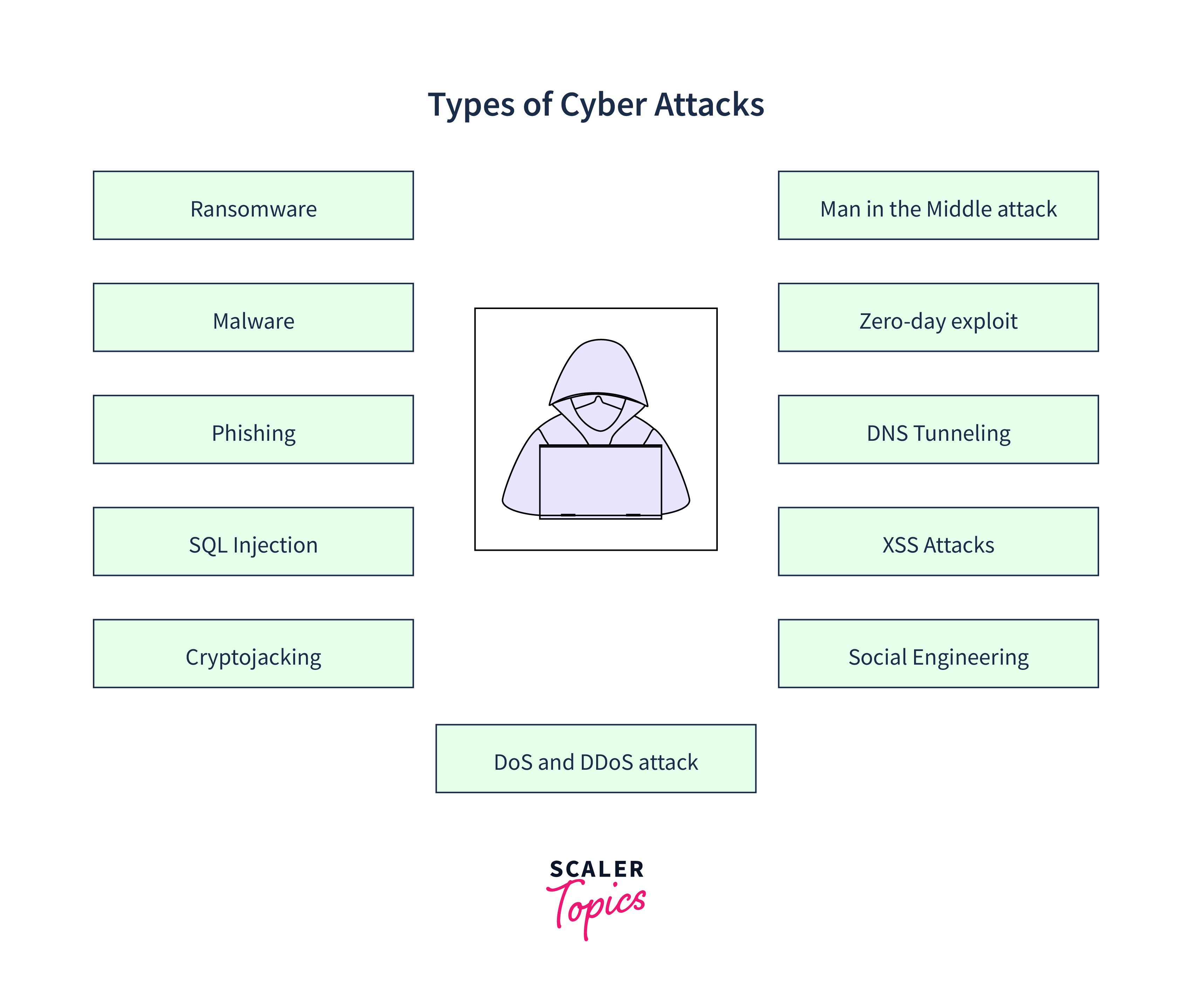
Exploits in penetration testing refer to the tools and techniques used to take advantage of vulnerabilities in a system or application to gain unauthorized access, escalate privileges, or execute malicious code. It can be described as a piece of code that exploits a vulnerability to make the software behave inadvertently.
Types of Exploits
There are several types of exploits, and these can be classified based on functionality, method of attack, and target systems. Some of the common types of exploits are:
- Remote Exploits:
Remote exploits are attacks that are executed over a network and target a remote system. They are typically used to take control of a target system or steal sensitive information. - Local Exploits:
Local exploits are attacks that are executed on a target system that has already been compromised. They are typically used to escalate privileges or gain additional access to the target system. - Client-Side Exploits:
Client-side exploits target a client device, such as a desktop computer, laptop, or mobile device. They typically exploit vulnerabilities in applications, such as web browsers or email clients, to steal sensitive information or execute malicious actions. - Server-Side Exploits:
Server-side exploits target servers, such as web servers, email servers, or database servers. They typically exploit vulnerabilities in server-side applications, such as web applications or databases, to compromise the target system or steal sensitive information. - Zero-Day Exploits:
Zero-day exploits are attacks that take advantage of previously unknown vulnerabilities. They are particularly dangerous because they are not yet known to the vendor or security community, making them more likely to be successful. - Social Engineering Exploits:
Social engineering exploits use human manipulation techniques to trick victims into revealing sensitive information or performing malicious actions. They can take the form of phishing scams, baiting, or other forms of deception. - Application-Level Exploits:
Application-level exploits target specific applications, such as web browsers, email clients, or productivity software. They typically exploit vulnerabilities in the application code to steal sensitive information or execute malicious actions. - Network-Level Exploits:
Network-level exploits target network devices, such as routers, switches, or firewalls. They typically exploit vulnerabilities in network protocols or configurations to gain unauthorized access to a target network.
Common Exploits Used in Pentesting
Various exploits can be included in the above categories. Some of the most commonly used ones are:
- Buffer Overflow:
A buffer overflow exploit takes advantage of a vulnerability in software that occurs when a program tries to store more data in a buffer than it can hold, causing the data to overflow into adjacent memory locations. This can result in the execution of arbitrary code, which can be used to compromise the target system. - Code Injection:
Code injection exploits involve injecting malicious code into an application or operating system, which can be executed when the application or system runs. This type of exploit can be used to take control of a target system or to steal sensitive information. - Privilege Escalation:
Privilege escalation exploits are used to gain elevated privileges on a target system, allowing the attacker to bypass security controls and access sensitive data or execute malicious actions. This type of exploit can be used to compromise the target system or to gain access to resources that are otherwise restricted. - Cross-Site Scripting (XSS):
XSS exploits take advantage of vulnerabilities in web applications, which allow attackers to inject malicious code into web pages that are visited by unsuspecting users. This can result in the theft of sensitive information, such as passwords, or the execution of malicious actions, such as spreading malware. - Remote Code Execution (RCE):
RCE exploits allow an attacker to execute code remotely on a target system, which can be used to compromise the target or to steal sensitive information. This type of exploit can be used to bypass security controls and gain access to resources that are otherwise restricted. - SQL Injection:
SQL injection exploits take advantage of vulnerabilities in database applications, which allow attackers to inject malicious SQL code into a database, compromising the target system and accessing sensitive data. - Directory Traversal:
Directory traversal exploits allow attackers to bypass security controls and access files and directories on a target system that are normally restricted. This type of exploit can be used to steal sensitive information or execute malicious actions. - Man-in-the-Middle (MitM):
MitM exploits allow attackers to intercept communications between two parties, allowing them to modify or steal sensitive information being transmitted. This type of exploit can be used to compromise the target system or to steal sensitive information, such as passwords or credit card numbers. - Rootkit:
A rootkit exploit is a type of malware that allows an attacker to gain access to a target system and hide their presence, making it difficult to detect and remove the infection. Rootkits can be used to steal sensitive information, launch attacks against other systems, or execute malicious actions.
Techniques and Tactics of Gaining Access
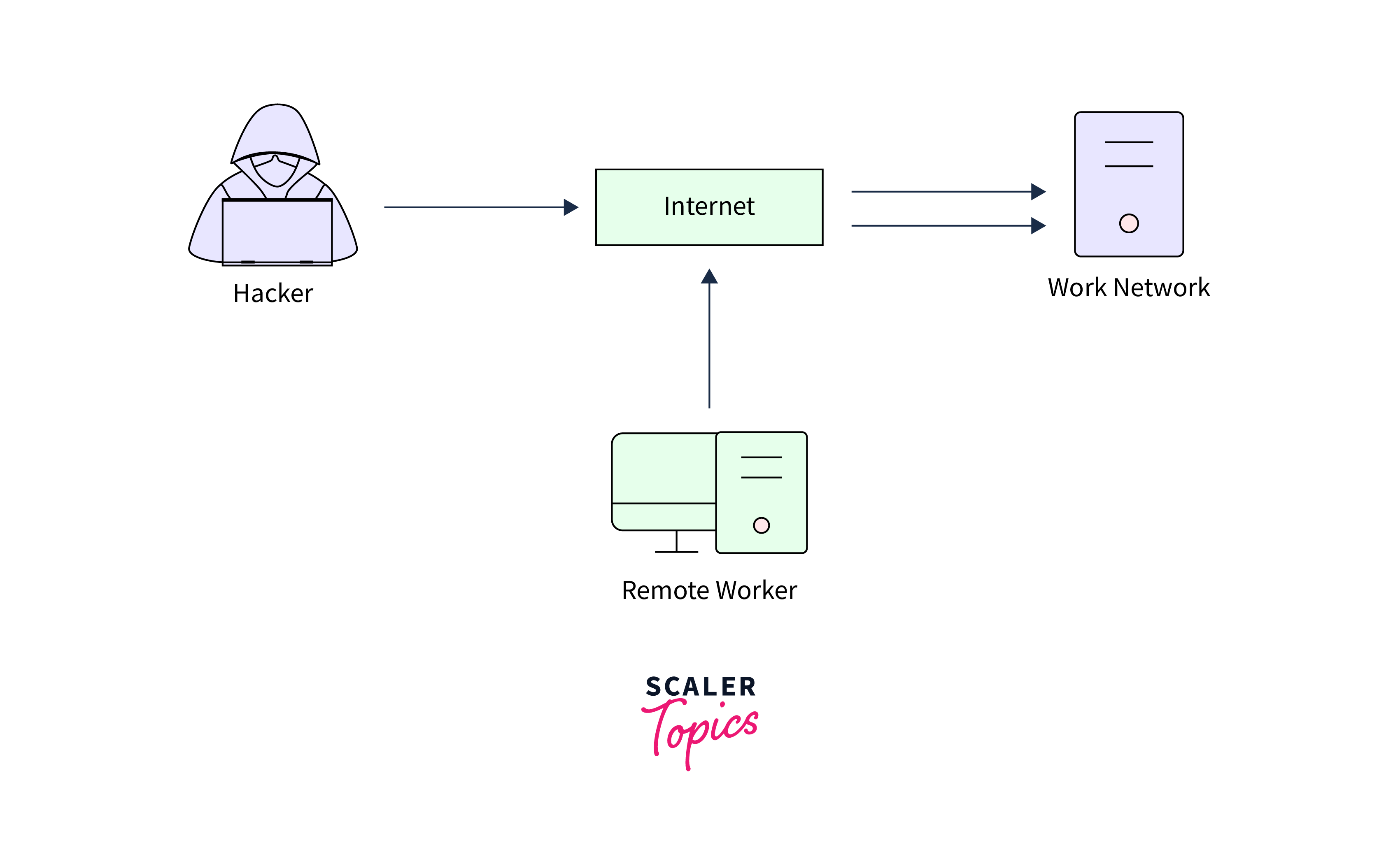
There are various techniques and tactics used by penetration testers that are designed to bypass security controls, such as firewalls, intrusion detection systems, and intrusion prevention systems, and to exploit vulnerabilities in the target system.
Here are some common techniques and tactics for gaining access:
- Social Engineering:
Social engineering is the use of deception and manipulation to trick individuals into revealing sensitive information or performing actions that compromise the target system. This can include phishing attacks, impersonation attacks, or pretexting, among others. - Password Attacks:
Password attacks are used to crack or obtain passwords, which can then be used to gain access to the target system. This can include brute force attacks, dictionary attacks, or password-cracking tools, among others. - Remote Access Trojans (RATs):
RATs are malicious programs that allow an attacker to remotely control a target system, allowing them to bypass security controls and gain access to sensitive data or execute malicious actions. - Exploit Kits:
Exploit kits are collections of exploits that can be used to compromise target systems by exploiting vulnerabilities in software, such as web browsers or operating systems. - Backdoor Access:
Backdoor access refers to the use of hidden or secret entry points into a target system, which can be used to bypass security controls and gain unauthorized access. This can include the use of rootkits or other forms of malware. - Web Application Attacks:
Web application attacks are designed to exploit vulnerabilities in web applications, such as cross-site scripting (XSS), SQL injection, or directory traversal, among others. These attacks can result in the theft of sensitive information or the execution of malicious actions. - Network Attacks:
Network attacks are designed to exploit vulnerabilities in network protocols or infrastructure, such as man-in-the-middle (MitM) attacks or denial of service (DoS) attacks, among others. These attacks can result in the disruption of network services or the theft of sensitive information. - Physical Attacks:
Physical attacks are designed to exploit vulnerabilities in physical security, such as the theft of sensitive information or the execution of malicious actions by compromising physical access to a target system or network.
Conclusion
- Exploitation and gaining access are critical phases in penetration testing that involve identifying and exploiting vulnerabilities in the target system or application.
- Penetration testers use various techniques and tactics to gain unauthorized access, escalate privileges, and execute malicious code to demonstrate the potential impact of vulnerabilities.
- The goal of using exploits in penetration testing is to identify and demonstrate the potential impact of vulnerabilities and help organizations improve their security posture.
- Some of the common types of exploits include buffer overflow exploits, SQL injection exploits, cross-site scripting (XSS) exploits, and directory traversal exploits.
- Countermeasures are intrusion prevention systems used by organizations. To get passed these pentesters use various techniques and tactics to gain access such as social engineering, password attacks, remote access trojans, and exploit kits.
