Enumerating HTTP and HTTPS with Nmap
Overview
The article Enumerating HTTP and HTTPS with Nmap covers the various techniques and methods that can be used to enumerate web services using the popular open-source tool Nmap. The article starts with an introduction to Nmap and its basic commands and options for enumerating HTTP and HTTPS, and then goes on to explain how to use Nmap to perform basic and advanced enumeration of these web services. The article also covers techniques for customizing and automating HTTP and HTTPS enumeration using Nmap and for identifying vulnerabilities in web services.
Introduction
Nmap (Network Mapper) is an open-source tool used for network exploration, management, and security auditing. It can be used to discover hosts and services on a computer network, thus creating a map of the network. Nmap can be used to identify hosts and services on a computer network and can also be used to identify open ports, operating systems, and devices.
Enumeration is the process of collecting information about a network or system. Nmap can be used for enumeration to identify hosts, services, and open ports on a network. It can also be used to gather information about the operating system and version of the host, as well as the software and version running on a particular port. This information can be used to identify potential vulnerabilities and security weaknesses.
Nmap can also be used for penetration testing, which is the process of attempting to gain unauthorized access to a computer system or network. By identifying open ports and services, a penetration tester can determine which attack vectors may be successful and should be used. Nmap can also be used to conduct vulnerability scans, which can identify known vulnerabilities in systems and applications.
Basic Enumeration with Nmap
In this section, we will discuss basic commands and options for enumerating HTTP and HTTPS with Nmap, as well as explain how to use Nmap to perform basic HTTP and HTTPS enumeration.
Basic Commands and Options for Enumerating HTTP and HTTPS with Nmap
The first step in performing basic enumeration with Nmap is to check for open ports on the target IP address or hostname. This can be done using the nmap -p80 [target IP address or hostname] command to check if port 80 is open on the target, and return information about the service running on that port if it is. Similarly, the nmap -p443 [target IP address or hostname] command can be used to check for open ports on port 443, which is the default port for HTTPS.
Another useful command for enumeration is nmap --script http-enum [target IP address or hostname]. This command runs a built-in Nmap script that attempts to identify the web server and version, as well as any virtual hosts or directories on the server.
In addition to these basic commands, Nmap offers several options that can be used to customize the scan and gather more detailed information. For example, the -sV option can be used to determine the version of the service running on an open port. The -A option can be used to enable OS detection, version detection, script scanning, and traceroute. Additionally, --script-args http.useragent=[User-Agent string] option can be used to specify the user-agent string that will be used when connecting to the HTTP service. An example of the above would be: nmap -p80 --script http-sqli-finder --script-args http.useragent="Mozilla 42" scanme.nmap.org
Explanation of How to Use Nmap to Perform Basic HTTP and HTTPS Enumeration
Once you have a general understanding of the basic commands and options for enumerating HTTP and HTTPS with Nmap, you can begin to use them to perform basic enumeration.
The first step is to check for open ports on the target IP address or hostname using the nmap -p 80 [target IP address or hostname] and nmap -p 443 [target IP address or hostname] commands. This will return information about any services running on those ports, including the service name, version, and any open ports.
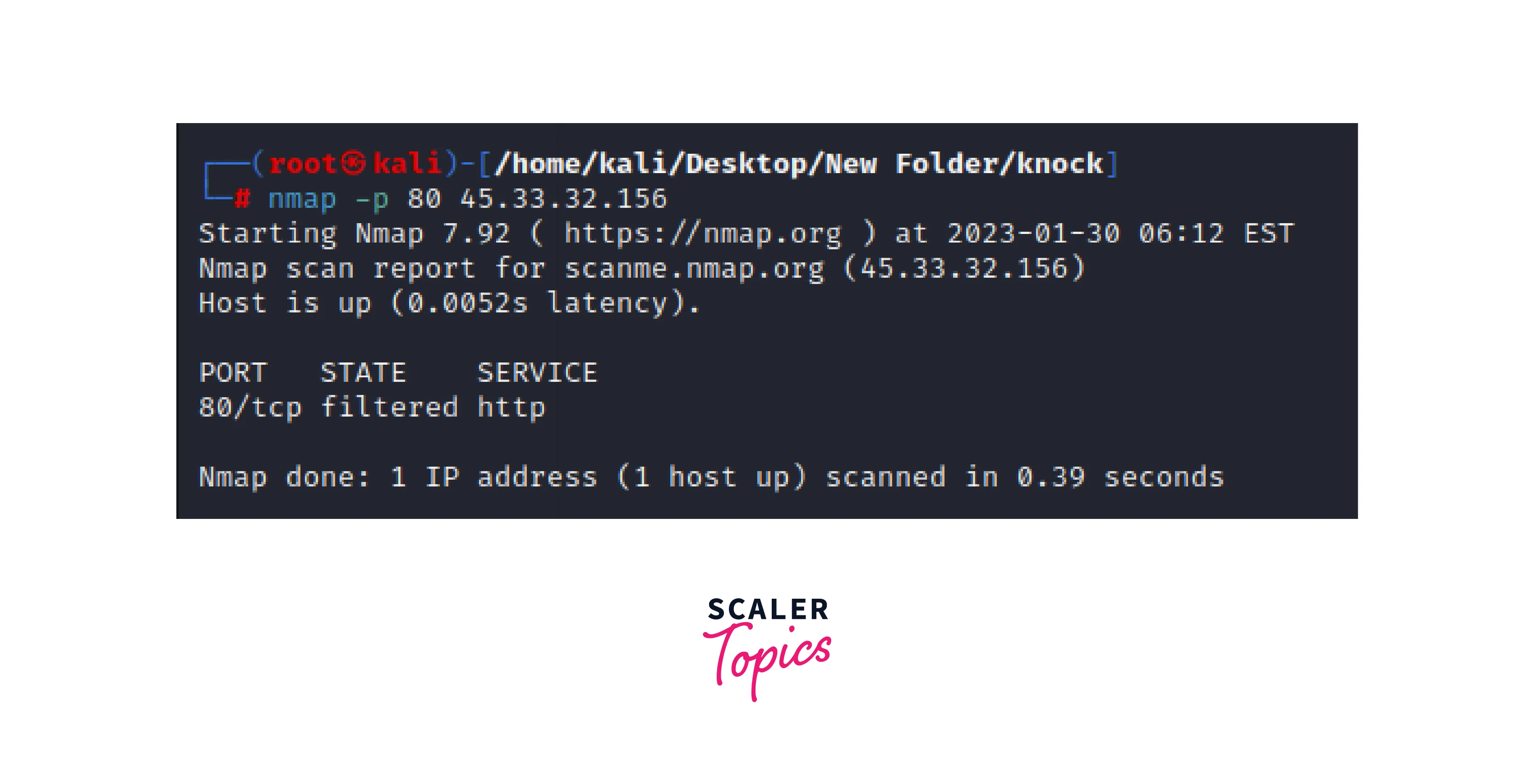
Using Nmap to scan port 80 on IP 45.33.32.156 or Scanme.Nmap.Org which returns the result that the port is filtered and service is HTTP
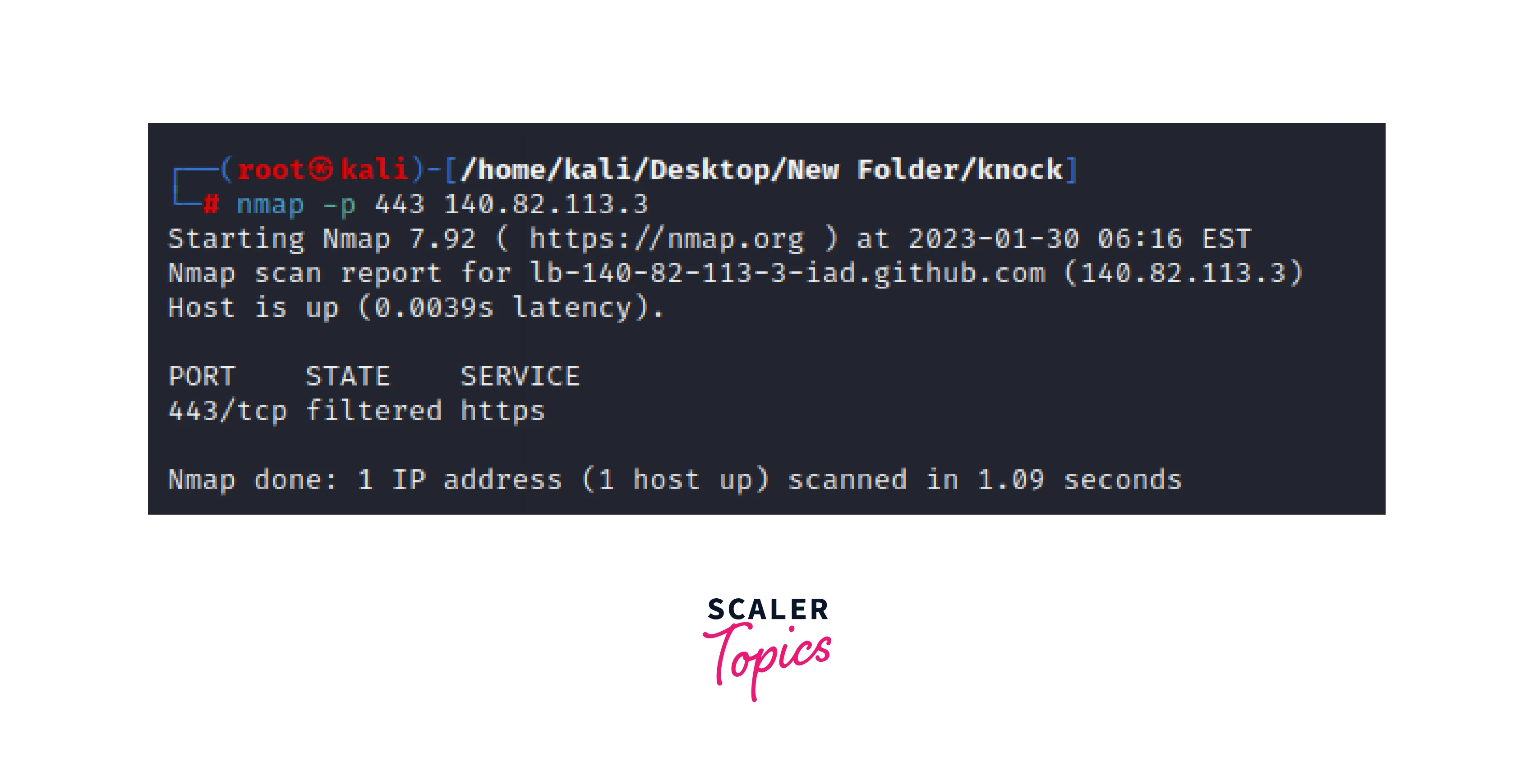
Using Nmap to scan port 443 on IP 140.82.113.3 or github.com which returns the result that the port is filtered and the service is HTTPS
Next, you can use the nmap --script http-enum [target IP address or hostname] command to run a built-in Nmap script that attempts to identify the web server and version, as well as any virtual hosts or directories on the server.
Finally, we can use the options discussed earlier to customize the scan and gather more detailed information. For example, the -sV option can be used to determine the version of the service running on an open port, and the "-A" option can be used to enable OS detection, version detection, script scanning, and traceroute. Additionally, --script-args http.useragent=[User-Agent string] option can be used to specify the user-agent string that will be used when connecting to the HTTP service.
Examples of Common Usage Scenarios for Basic HTTP and HTTPS Enumeration
Basic HTTP and HTTPS enumeration can be used in a variety of scenarios, such as performing reconnaissance on a network before an attack, identifying misconfigured web services, and monitoring network services for changes.
-
An attacker might use basic HTTP and HTTPS enumeration to identify web services running on a target network. They can use this information to determine the version of the web server software and the operating system running on the target, as well as identify any potential vulnerabilities in the web services that can be exploited. Additionally, attackers may use the information gathered during HTTP and HTTPS enumeration to identify misconfigurations, such as open directories or default credentials, that can be used to gain unauthorized access to the web services.
-
A network administrator might use basic HTTP and HTTPS enumeration to identify and fix misconfigured web services on their network. For example, they can use Nmap to scan their network and identify any services that are running outdated software or have open directories, and then take steps to update the software or close the directories to improve the security of their network. Additionally, an administrator can use Nmap to identify web services that are running on non-standard ports, which can be a sign of a potential compromise.
-
An organization may also use basic HTTP and HTTPS enumeration to regularly monitor the services running on their network for changes. This can help to detect and respond to potential security threats, such as new web services that have been added to the network without authorization, or changes to existing web services that may indicate an attempted compromise. Additionally, an organization can use Nmap to scan the network for services that are running on non-standard ports, which can be a sign of a potential compromise.
Advanced Enumeration with Nmap
In this section, we will discuss Advanced commands and options for enumerating HTTP and HTTPS with Nmap, as well as explain how to use Nmap to perform advanced HTTP and HTTPS enumeration.
Advanced Options and Commands for Enumerating HTTP and HTTPS With Nmap
When performing advanced HTTP and HTTPS enumeration with Nmap, there are a variety of options and commands that can be used to gather more detailed information about web services running on a network. Some of the advanced options include:
- -sV: This option is used to probe for the version of the web server software running on the target.
- -sC: This option is used to run a script scan, which can be used to perform additional reconnaissance, such as identifying the type of web server software or checking for common vulnerabilities.
- -A: This option is used to enable OS detection, version detection, script scanning, and traceroute. This option can be useful when performing a full-scale reconnaissance of a target network.
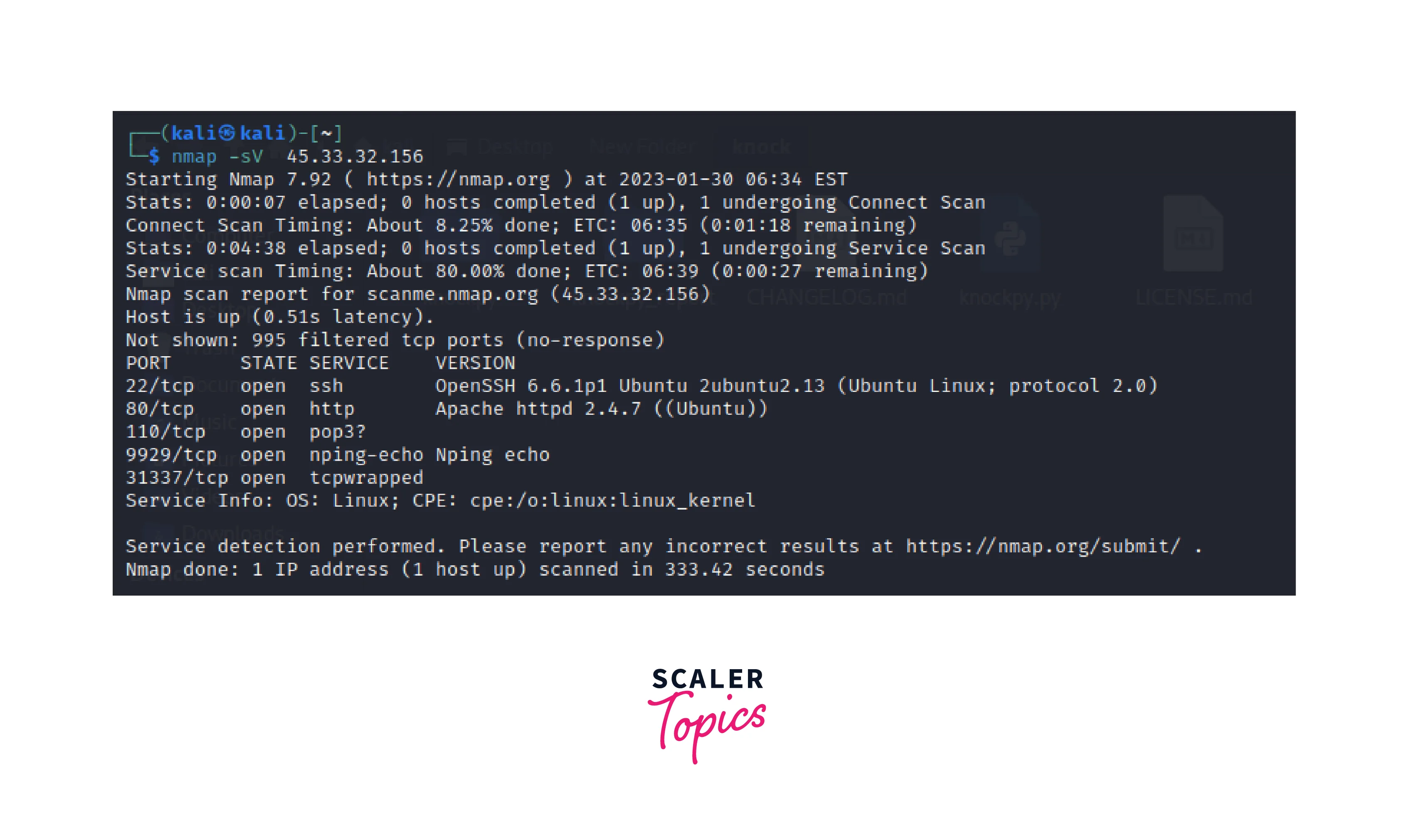
Using Nmap to scan IP 45.33.32.156 or Scanme.Nmap.Org The image depicts the scan result which includes version info, service info, etc.
Additionally, advanced commands can be used to perform a more detailed enumeration of HTTP and HTTPS services. For example, the http-enum command can be used to enumerate the directories and files on a web server, and the http-methods command can be used to identify the allowed HTTP methods on a web server.
Explanation of How to Use Nmap to Perform Advanced HTTP and HTTPS Enumeration
When performing advanced HTTP and HTTPS enumeration with Nmap, one can use the advanced options and commands mentioned above to gather more detailed information about web services running on a network.
For example, using the -sV option can be useful in identifying the version of the web server software running on a target, which can help to identify potential vulnerabilities that can be exploited. The -sC option can be useful in running a script scan, which can be used to perform additional reconnaissance, such as identifying the type of web server software or checking for common vulnerabilities. The -A option can be useful when performing a full-scale reconnaissance of a target network, it enables OS detection, version detection, script scanning, and traceroute.
Additionally, advanced commands such as http-enum can be used to enumerate the directories and files on a web server, and the http-methods command can be used to identify the allowed HTTP methods on a web server, this can help to identify potential misconfigurations in the web services that can be exploited.
Techniques for Customizing and Automating HTTP and HTTPS Enumeration Using Nmap
Nmap can be easily customized and automated to perform HTTP and HTTPS enumeration. One way to customize Nmap is by creating and using custom scripts. For example, a custom script could be created to check for specific vulnerabilities or misconfigurations in web services. This can be done by using the --script option followed by the path to the custom script.
Another way to automate Nmap is by using a command line interface (CLI) or a graphical user interface (GUI) front-end. For example, the Zenmap GUI is a popular front-end for Nmap that provides a user-friendly interface for configuring and running scans. Additionally, Nmap can be integrated with other tools, such as Nessus and Metasploit, to automate the process of identifying vulnerabilities in web services.
Nmap can be easily customized and automated to perform advanced HTTP and HTTPS enumeration, this can help to gather more detailed information about web services, identify potential vulnerabilities and misconfigurations, and automate the process of identifying vulnerabilities in web services.
Examples of Advanced Usage Scenarios for Enumerating HTTP and HTTPS With Nmap
There are many advanced usage scenarios for enumerating HTTP and HTTPS with Nmap. One example is using Nmap to enumerate a large network of web services. This can be done by using Nmap's ability to perform a ping sweep and identify all live hosts on a network, and then running a full-scale reconnaissance scan on all identified web services. This can be useful for identifying all web services running on a network, including those that may not be publicly advertised.
Another example is using Nmap's scripting engine to perform a vulnerability scan on all web services identified on a network. This can be done by using the --script option followed by a set of predefined or custom scripts that check for specific vulnerabilities or misconfigurations in web services. This can be useful for identifying and prioritizing vulnerabilities that need to be addressed.
Another example is using Nmap to automate the process of identifying vulnerabilities in web services. This can be done by integrating Nmap with other tools, such as Nessus and Metasploit, to automatically run scans, identify vulnerabilities, and generate reports. This can be useful for large-scale assessments and for regular monitoring of web services.
Nmap can be used to perform reconnaissance on a specific web application. This can be done by using Nmap's ability to perform a version scan and identify the specific version of the web application and its plugins, then using the -sC option to run a script scan to gather more information and identify specific vulnerabilities of the web application.
Techniques for Identifying Vulnerabilities
Identifying vulnerabilities is an important step in securing a network or web service. There are several techniques that can be used to identify vulnerabilities using Nmap. Some of these techniques include:
-
Script Scanning: Nmap has a built-in scripting engine that allows you to run predefined or custom scripts that check for specific vulnerabilities or misconfigurations. This can be done by using the --script option followed by a set of predefined or custom scripts that check for specific vulnerabilities or misconfigurations in web services. This feature is particularly useful as it allows you to scan for vulnerabilities that are not covered by Nmap's default scan options. Additionally, it also allows you to perform more advanced checks, such as checking for specific configurations or misconfigurations that could lead to a security vulnerability.
-
Version Scanning: Nmap can be used to identify the specific version of a web service, including its plugins and operating system, by using the -sV option. This can be useful for identifying known vulnerabilities that are specific to a particular version of the web service. Knowing the version of the web service can help you to narrow down the potential vulnerabilities that might exist and improve the overall security posture. Additionally, it also allows you to compare it with the latest version and check if there are any updates or patches that need to be applied.
-
OS Fingerprinting: Nmap can be used to identify the operating system of a host by using the -O option. This can be useful for identifying known vulnerabilities that are specific to a particular operating system. OS Fingerprinting is an essential step in network reconnaissance and helps to identify the underlying technology and operating system of the target system. This information can be used to further configure Nmap scans and run more targeted tests for vulnerabilities that are specific to that operating system. Additionally, it also allows you to check if the host is running the latest version of the operating system, and if not, if there are any updates or patches that need to be applied.
-
Integrating with other tools: Nmap can be integrated with other vulnerability scanning tools, such as Nessus and Metasploit, to automatically run scans, identify vulnerabilities, and generate reports. This can be useful for large-scale assessments and for regular monitoring of web services. Integrating Nmap with other tools can also provide additional functionality, such as vulnerability exploitation, which can aid in identifying and exploiting known vulnerabilities. Additionally, integrating Nmap with other tools can help to automate the enumeration process, which can save time and resources.
-
Vulnerability databases: In addition to the above techniques, you can use vulnerability databases such as the National Vulnerability Database (NVD), Common Vulnerabilities and Exposures (CVE) and OpenVAS NVT feed to cross-reference the version and plugins of the web service with known vulnerabilities. These databases are regularly updated and provide a wealth of information on known vulnerabilities and their associated risks. By cross-referencing the version and plugins of a web service with the information in these databases, you can quickly identify known vulnerabilities and assess the risk they pose to your organization. This can aid in prioritizing vulnerabilities and implementing appropriate mitigation strategies. Additionally, many vulnerability management and security software can directly query these databases for vulnerabilities in your systems.
Conclusion
- Nmap is a powerful tool for enumerating web services, particularly HTTP and HTTPS.
- Basic enumeration using Nmap can include things like port scanning, version detection, and OS fingerprinting.
- Advanced enumeration with Nmap can include things like script scanning, customizing and automating scans, and integrating with other tools.
- Identifying vulnerabilities is an important step in web service security, and Nmap can be used to assist in this process through techniques like script scanning, version scanning, OS fingerprinting, and using vulnerability databases.
- Nmap is a versatile tool that can be used for both basic and advanced enumeration of web services, as well as identifying vulnerabilities, making it an essential tool for network and web service administrators.
