Metasploit Framework
Overview
Due to the countless instances of cyber-insecurity, businesses frequently employ hackers and security experts to analyse their systems for flaws. As a result, ethical hackers employ a variety of tools to run a penetration test on the systems. One such tool is the Metasploit Framework, which is frequently used.
Cybercriminals and ethical hackers alike utilise the robust penetration-testing tool known as the Metasploit Framework to check a system's vulnerability.
What is Metasploit?
Metasploit is an open-source project that provides the general public with resources for developing code and researching security vulnerabilities. It enables network administrators to identify security threats on their network and to note which vulnerability needs to be defined first.
Pen (Penetration) testing software is made easier by this kind of project. Additionally, it provides resources for automating the contrast between a program's vulnerability and its patched (repaired) version. Furthermore, it offers sophisticated evasion and anti-forensic tools.
Using Metasploit, the pen testing team may insert pre-written or bespoke code into a network to scan for vulnerabilities. Once problems are discovered and recorded, a different approach to threat hunting is possible, systemic defects may be addressed and fixes can be given priority.
A Typical Metasploit Architecture Diagram.
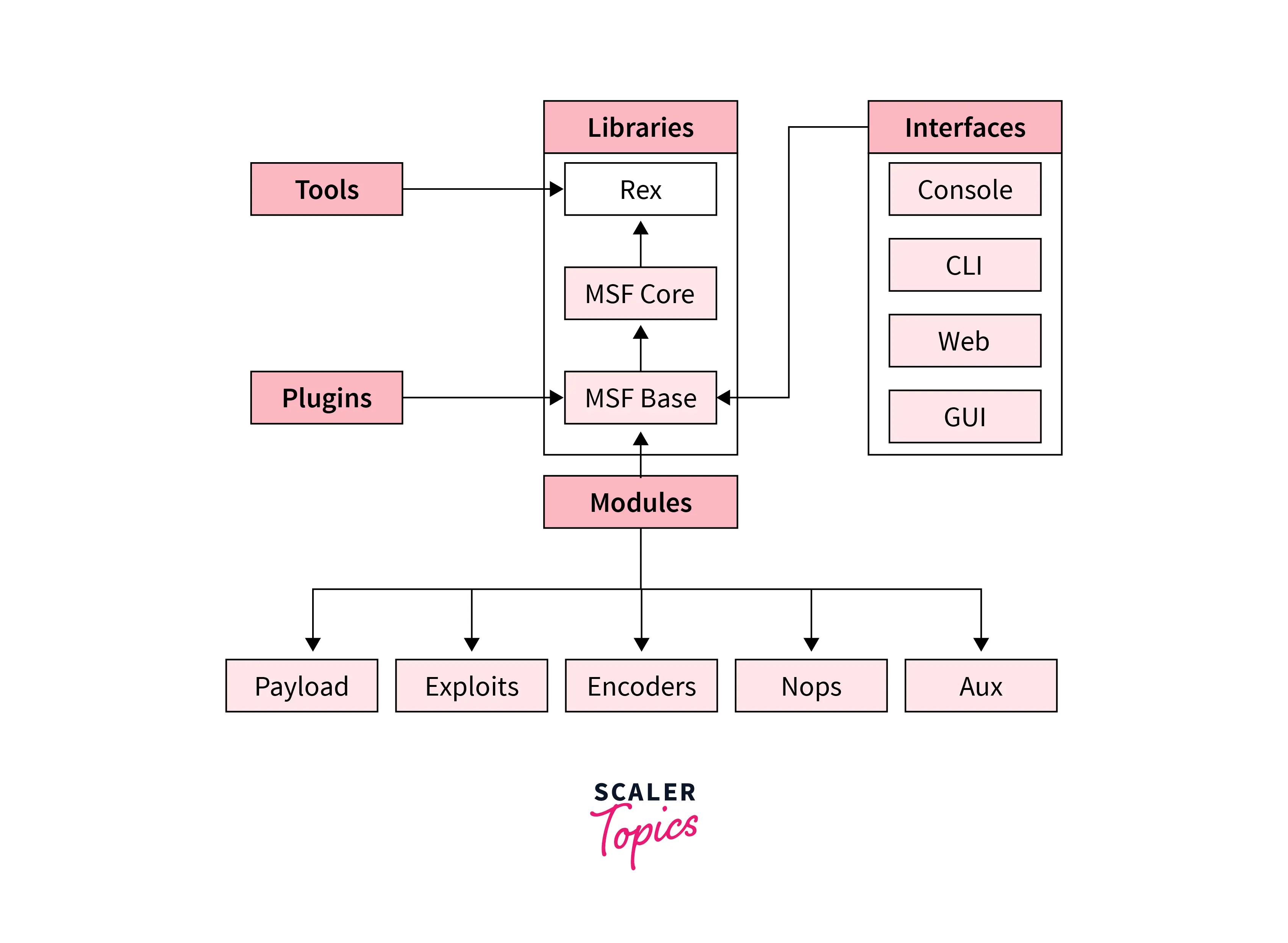
What is Meterpeter?
Meterpreter is a Metasploit attack payload that offers an interactive shell from which an attacker may investigate and execute code on the target system. In-memory DLL injection is used to deploy Meterpreter. Meterpreter doesn't write anything to disc because it only exists in memory. Injecting Meterpreter into the compromised process, from which it can move to other active processes, does not result in the creation of any additional processes. As a result, an attack's forensic footprint is relatively small.
The purpose of Meterpreter is to enable command writing and encrypted communication while avoiding the limitations of employing particular payloads. The drawback of employing particular payloads is that alarms could be set off when a new process begins in the target system.
How is Metasploit Framework Used?
Depending on your Ruby proficiency, Metasploit use may be learned quite quickly. However, switching to working with Metasploit shouldn't be too challenging to get up to speed with if you are already comfortable with other scripting and programming languages like Python. Otherwise, it's a naturally occurring language that can be picked up with enough effort.
You should be aware of the possible hazards involved since this programme needs you to disable your own systemic defences and allows the creation of harmful code. If at all feasible, keep this software installed on a different computer than your own or any other computer that has access to or contains potentially sensitive data. When doing Metasploit pen tests, you should use a specific work device.
A Brief History of Metasploit
H.D. Moore began the Metasploit Project in 2003 as a Perl-based portable network tool, with cooperation from core developer Matt Miller. By 2007, it had been entirely converted to Ruby, and Rapid7 purchased the licence in 2009. The Boston-based business continues to use it as part of its toolkit for developing targeted remote exploits, fuzzing, anti-forensic techniques, and IDS signatures.
Rapid7 purchased the Metasploit project in 2009, and the framework quickly became well-known as a cutting-edge information security tool for assessing the susceptibility of computer systems. Along with exploits for known issues, Metasploit 4.0, which was published in August 2011, provides tools that find software vulnerabilities.
Metasploit Uses and Benefits
You may use Metasploit for a variety of purposes, and it offers the following advantages:
- Actively Developed and Open Source - Metasploit is recommended over other high-priced penetration testing programmes because it offers access to its source code and the addition of particular custom modules.
- Utilization -When doing a broad network penetration test, Metasploit is simple to employ. For the purpose of exploiting the vulnerability, Metasploit runs automated testing on all computers.
- Quick Payload Switching - It is simple and quick to switch payloads with the set payload command. The ability to convert meterpreter or shell-based access into a particular action is made simple.
- Enhanced Exits - Metasploit offers a clean escape from the compromised target system.
- User-Friendly Graphical Environment - The penetration testing effort is made easier by a user-friendly GUI and third-party APIs.
Starting Metasploit Framework on Kali Linux
The following are the steps to get started with the Metasploit:
Step 1 - Obtain Root Access
On Linux, a specific user account known as root has access to all commands, files, and services. It has total access to everything and is the most powerful account. On any Linux system, we can use the sudo su command to take the root or superuser role.
Step 2 - System Update and Upgrade
We resynchronize the Linux package index files from their sources online using the apt-get update command. To update all of the packages that are currently installed on the Linux system, we are currently running apt-get upgrade. The following syntax allows us to perform this in one line:
Step 3 - Setting Up Necessary Dependencies
A large number of dependencies that are necessary for Metasploit to function must be installed. We will use the command listed below to install the dependencies.
Step 4 - Metasploit Repository Cloning
The Metasploit GitHub repository has to be cloned. To do this, we must use the git clone command, and the repository URL, and return to the terminal to paste and run the command, which will download the repository into our home directory. Due to the size of the repository and the volume of items within, it will take some time.
The following screen will appear after performing the aforementioned command:
If the "Command git not found" message appears on the output screen, installing git is required before running the aforementioned command. Use: to install git.
Step 5 - Ruby's Bundler Package Manager Installation
The next step is to install Ruby's bundler package management after we have finished copying the Metasploit GitHub repository into our home directory. To do this, adhere to the following guidelines:
Step 6 - Installing Metasploit Ruby Packages.
Installing the Metasploit ruby packages is the next step. We use the cd command that we just cloned into that directory to first navigate to the Metasploit framework directory.
We must go to and complete installing the remaining packages for Metasploit inside of this directory. Follow these steps to accomplish this:
This output screen will appear once the installation is complete.
 When it's finished, we can simply type ./msfconsole to launch the Metasploit framework.
When it's finished, we can simply type ./msfconsole to launch the Metasploit framework.
Major Keywords in Metasploit
The following are the main modules of the Metasploit framework:
Exploit
Metasploit's Exploit module is used to build and access systems by exploiting the target system's vulnerabilities. The module executes a sequence of commands to focus on a particular area of vulnerability found in a system or application. Buffer overflows, web application exploits, and code injection are a few examples of exploit modules.
Payloads
The module known as the "payload" contains a collection of harmful codes that are executed after successfully infiltrating the target's system. This module contains a list of commands that the hacked target system might follow. In addition, the payload module gives the user control over how to connect to the shell and create the system's motivation, which is the end goal after that system has been taken under one's control.
The payload module offers a variety of functions, such as tiny programmes or even a little application. The payload module can launch meterpreter or a command shell. A really creative payload called a meterpreter enables us to create DLL files that strategically create new structures as needed.
Auxiliaries
Auxiliary functions are a collection of supplemental tools and instructions that do not require payloads to work. Random functions that don't need to be coupled with exploitation can be run using this module. Scanners, sniffers, and denial-of-service assaults (DoS). Some applications of the Auxiliary function include fuzzers and SQL injection tools.
Encoders
Encoders are a group of tools used to change information or codes. The shellcodes' encoding is crucial for exploitation. Encoders are a particular class of sensing apparatus that generates feedback for identifying digital signals.
Evasions.
The evasion module contributes to the creation of a Windows executable, EXE, that bypasses Windows Defender antivirus. This is accomplished through the use of a variety of techniques such as metasm, anti-emulation, shellcode encryption, and source code obfuscation.
Nops
No operation, sometimes known as NOP, is a sort of command that guards against the payload crashing. The NOP generates a random sequence of bytes that are used to get around the traditional IPS/IDS NOP sled signatures.
Post
With the help of this component, Metasploit may execute a broad range of post-exploitation modules that are accessible with Metasploit and can be used to gather evidence, pivot further into a target network, and many other things on compromised targets.
Important Commands in Metasploit
The most often used commands while exploding in Metasploit are:
1. Help
To begin, enter the help keyword to view the many commands you will probably use.
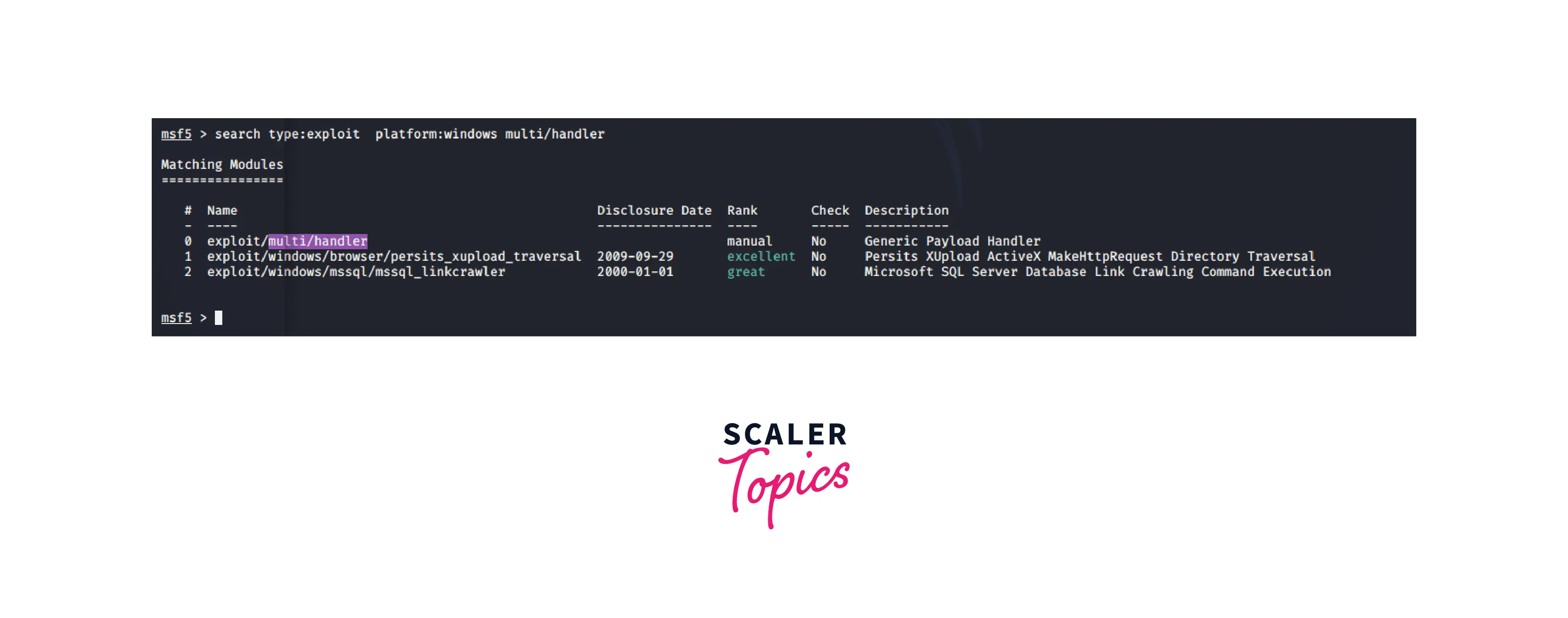
2. Search
The search command could be the most helpful for new users. Finding a certain module might be difficult because there are hundreds of accessible modules; however, the search function can help.
As suggested below, choose a specific term to focus your search:
Type: Specify the kind of module you're looking for. It can be a post, encoder, payload, or exploit.
Platform: It lists the operating system that the module is compatible with.. Depending on the platform you plan to exploit, you are permitted to search for a module.
Name: To find a module, you may also input its name directly.
Syntax Enter the search term, followed by a colon, and then the exact keyword as seen below.
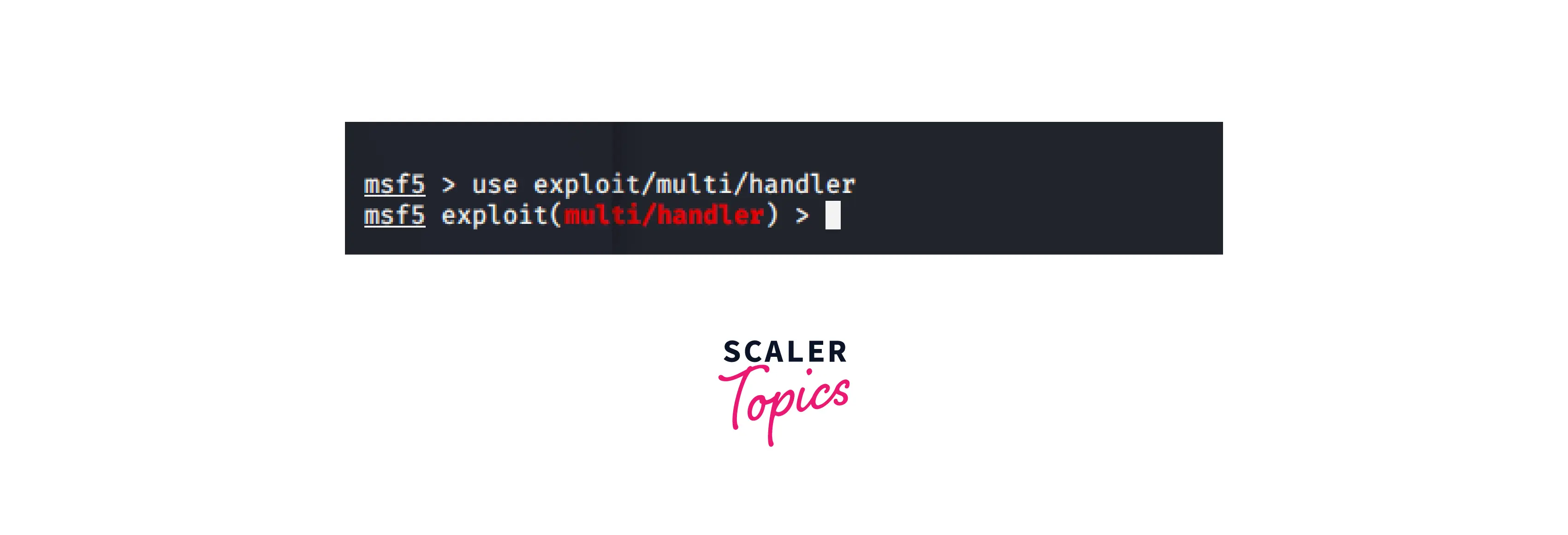
3. Use
When an exploit is executed, the use command makes an exploit available and stages it. The example below demonstrates how to stage an exploit:
If the module is staged successfully, Metasploit will reply by displaying the kind of exploit and abbreviating it in red, as seen below.
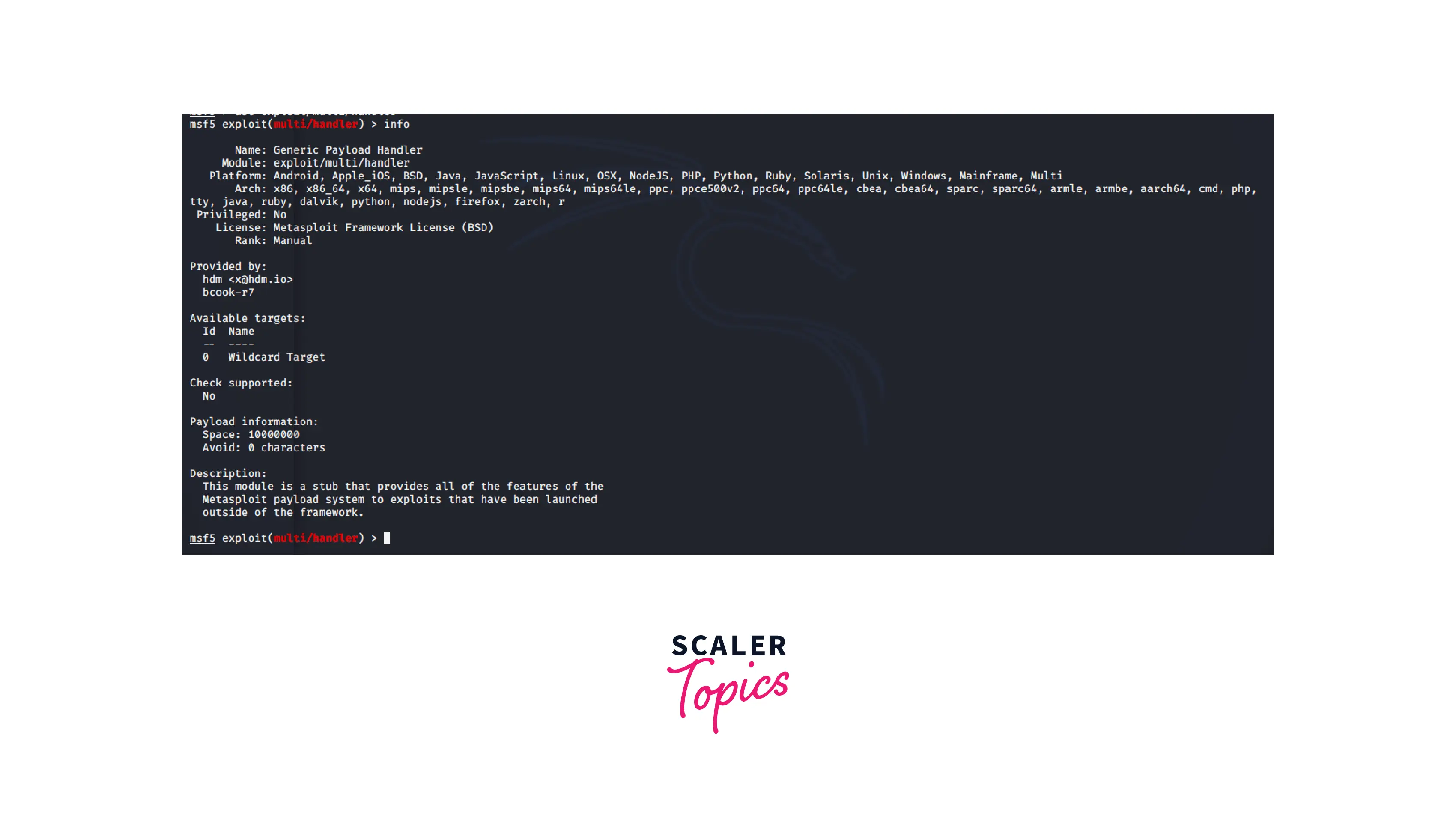
4. Info
Once an exploit has been staged, you may use the info command to find out details about it, including its name, creator, and platform.
Implement the command as indicated below:
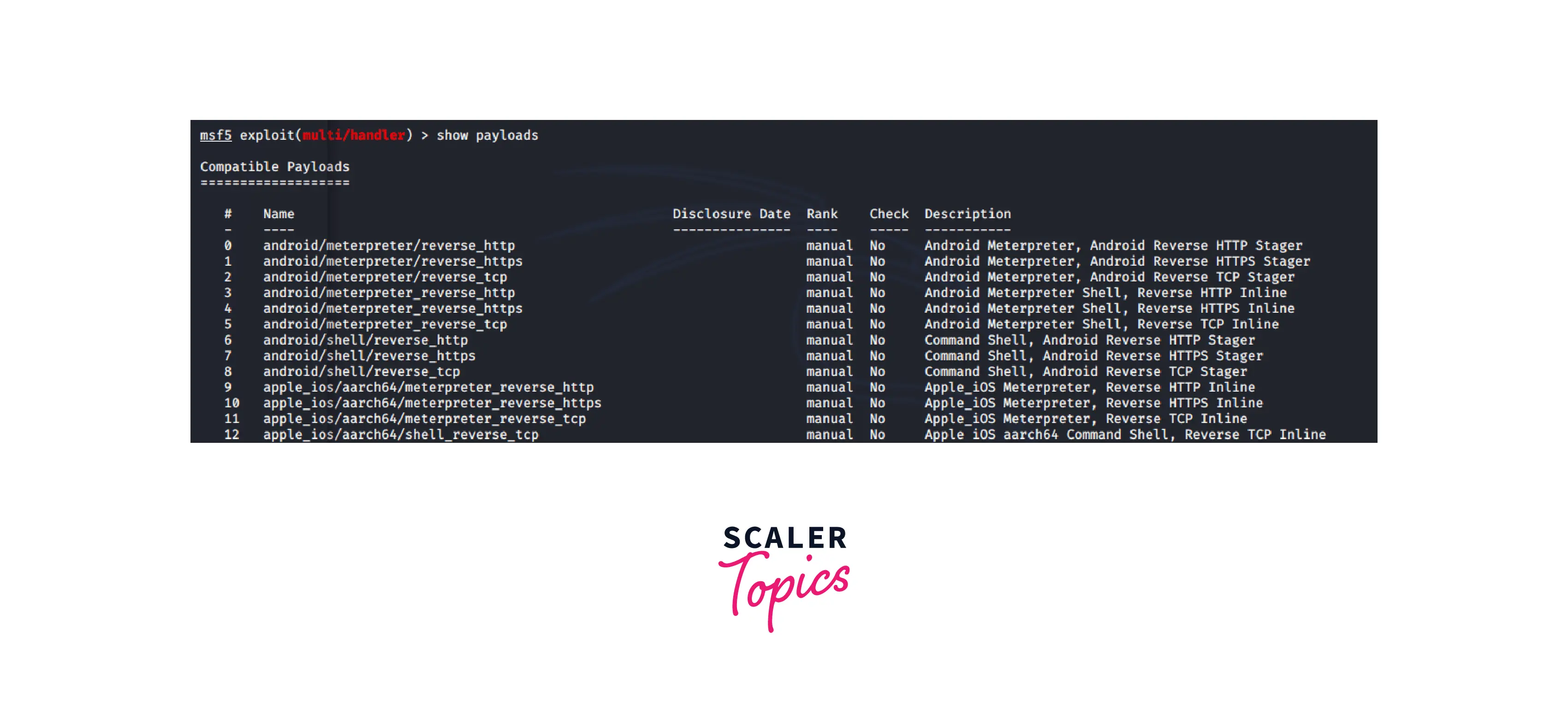
5. Show
Once an exploit has been successfully staged, you can view the payloads, targets, or options associated with the staged attack by using the show command
The top three show commands are:
Show Payloads This command returns a list of all payloads that are suitable with the staged exploit. It will offer a list of all the payloads, which is typically a big list, if the command is executed prior to staging the exploit.
Use the command listed below:
Show Targets The command "show targets" displays a list of all the targets that are susceptible to the staged exploit. The vulnerability of a target might change according on the operating system, update, language, and other factors.
Implement the command as indicated below:
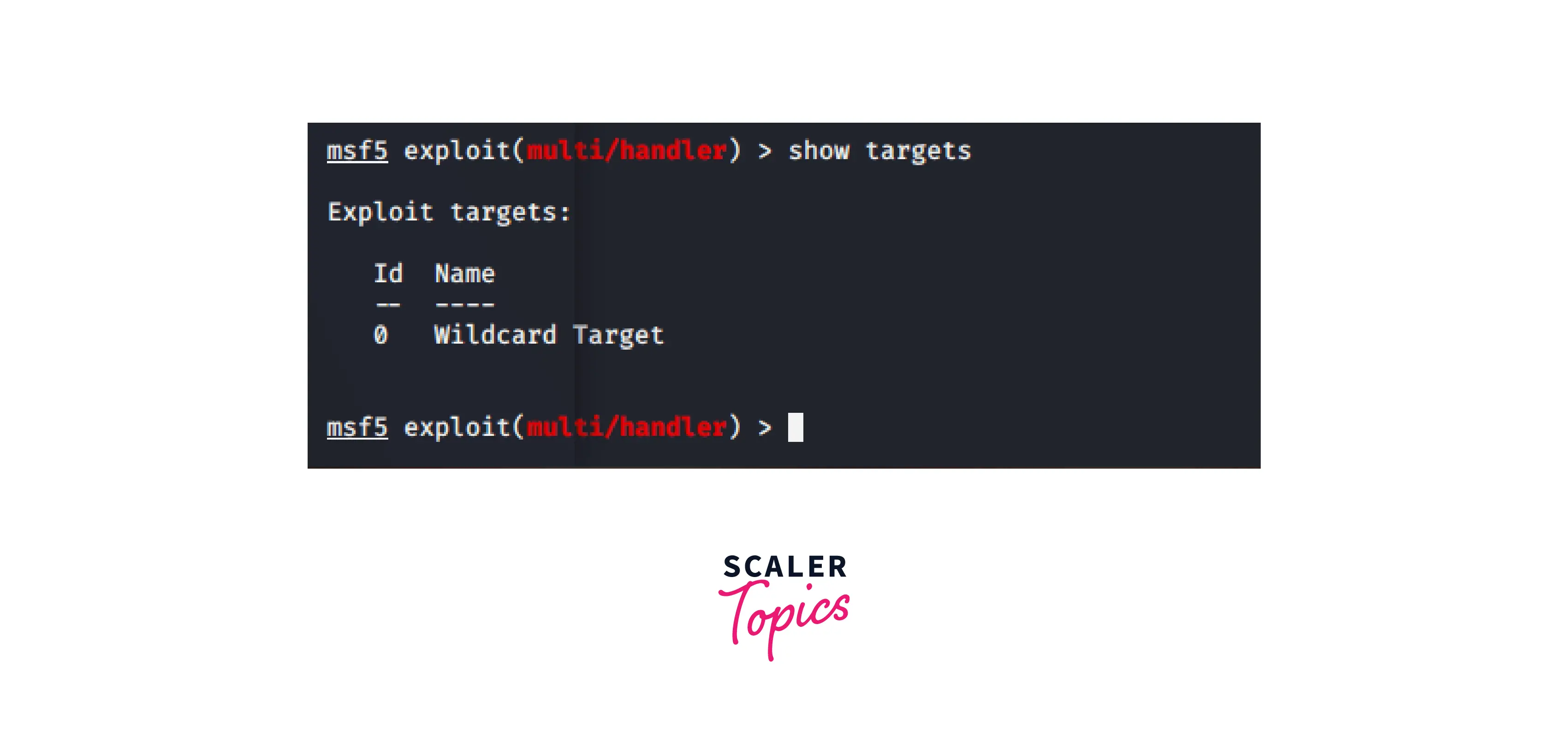 From the aforementioned example, it is clear that our target is open to the attack we employed.
From the aforementioned example, it is clear that our target is open to the attack we employed.
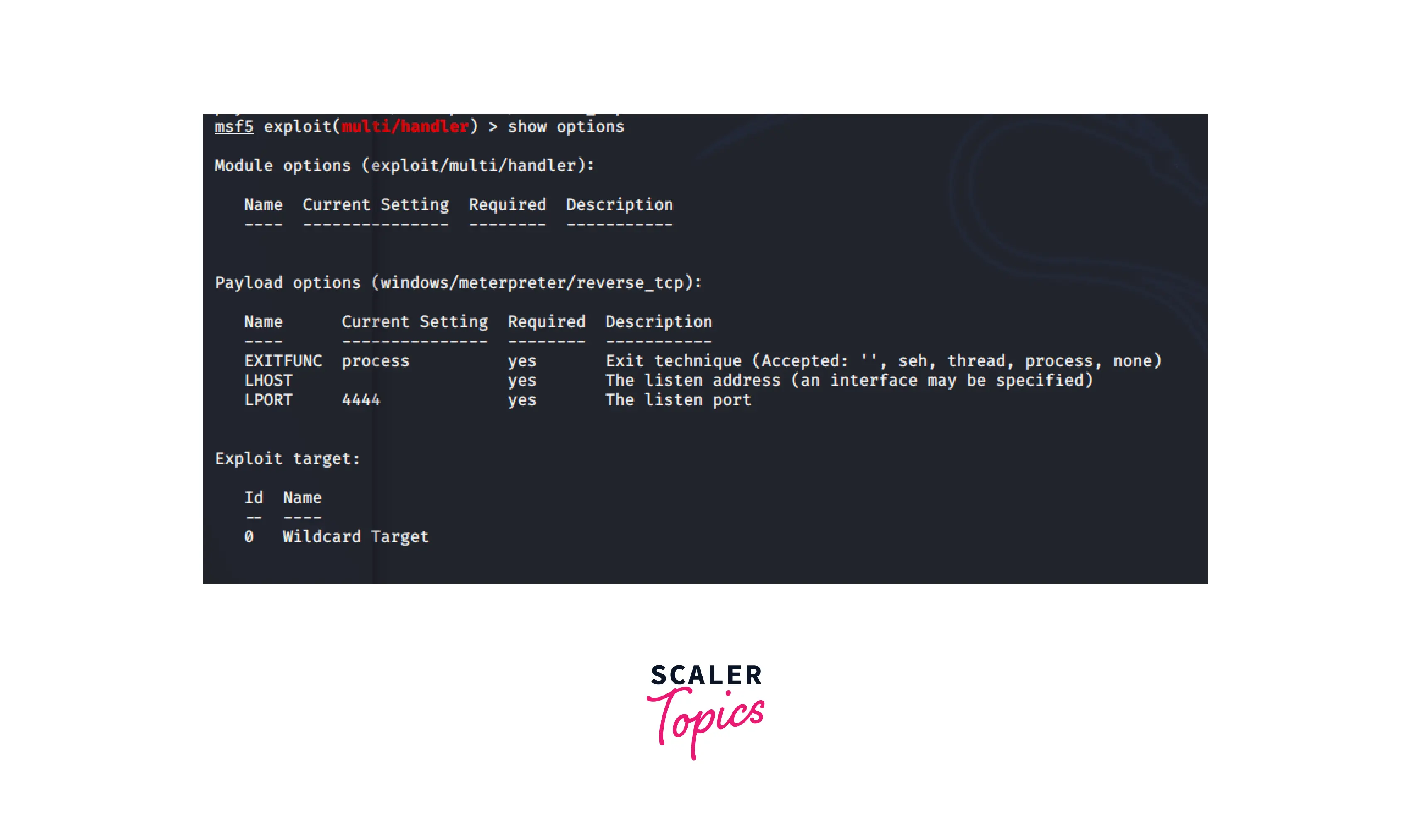
Show Options The options that need to be configured before launching the exploit are shown by this command, which is frequently helpful. Among the options that may be configured are RHOST, LHOST, PATH, LPORT, and others.
As illustrated below, the command is executed:
6. Set
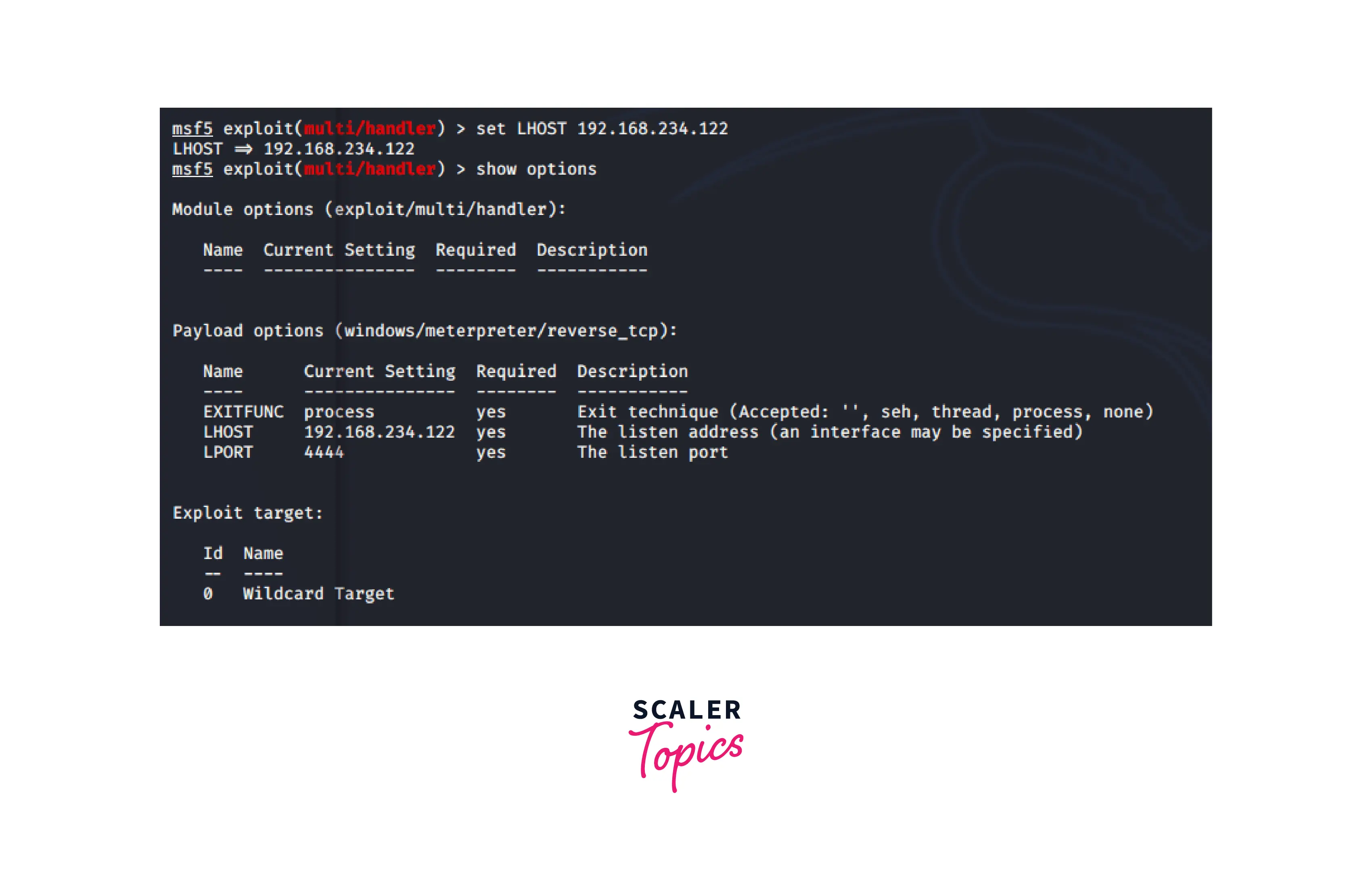
This command overrides a desired option or establishes a new one. The staged module determines which options need to be configured. RHOST, LHOST, PATH, and other options may need to be configured.
Syntax for setting the option is as follows:
7. Exploit
You are now ready to launch the assault once the exploit has been setup and all of the settings have been set.
As seen below, you may launch the attack by using the exploit or run keyword.
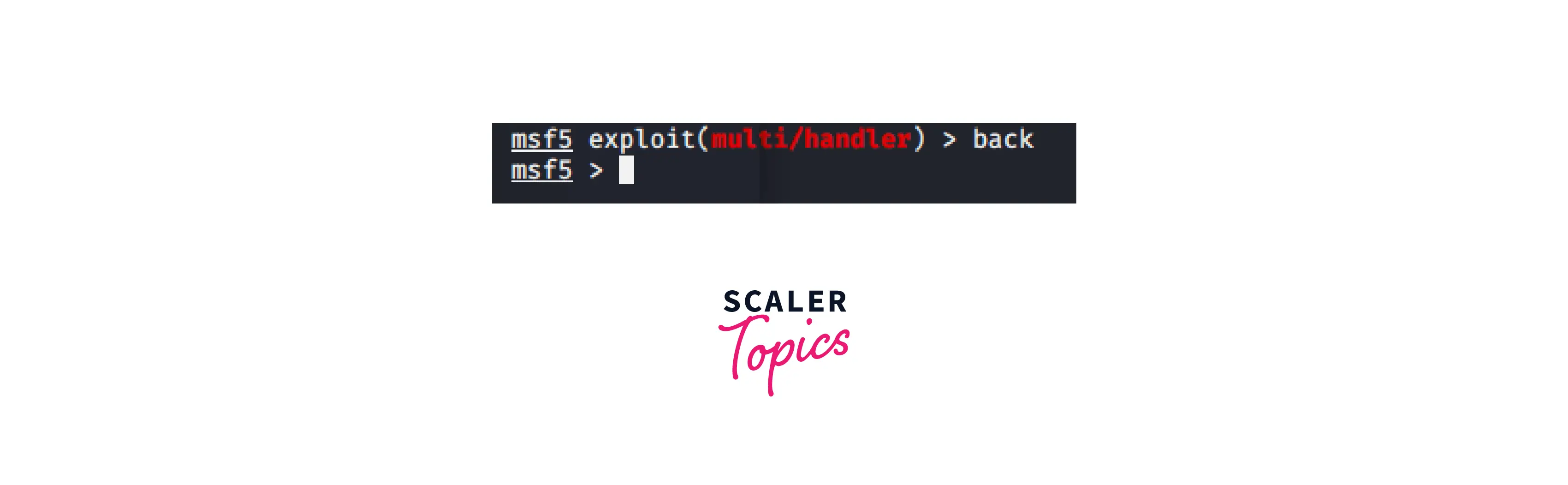
8. Back
This order moves us backwards a step. It is appropriate when you wish to modify the alternatives available.
Implement the command as indicated below:
9. Exit
The following command returns us to the terminal and closes the msfconsole:
Reasons to Learn Metasploit
Cyberattacks and cybercrime are both fairly widespread these days. Hackers are constantly seeking for methods to compromise a network or engage in other illegal actions. Once they discover a weakness in a server or network, hackers attack and steal important data, posing a threat to the organisation, the government, or the entire nation. Metasploit is a framework used to address these problems.
The Metasploit framework makes it simple to locate a server's or network's weak points. Once it has been identified, it is simple to record, and once that is done, the company or the agency may move to address any vulnerabilities and strengthen them before an attack occurs. For businesses, organisations, or governments, this paradigm is very helpful for protecting your sensitive data.
Also, anyone who works as a security analyst or pen-tester needs to have this framework package. It is a crucial tool for locating concealed vulnerabilities utilising a range of instruments and utilities. Through Metasploit, you may adopt a hacker's perspective and employ their techniques for exploring and exploiting servers and networks.
Conclusion
- To practice your exploits, I advise using Metasploitable 2 since it offers a safe environment for doing penetration testing and security analysis.
- Despite having a tonne of tools for finding vulnerabilities, analyzing them, and developing exploits, Metasploit is not without its limitations and flaws.
- Some of them consist of - limited GUI support, the vast bulk of jobs ought to be finished using CLI,
- Should be handled properly, or else your own system might crash.
- A computer running an antivirus or a firewall makes it difficult to install Metasploit.
