Using Nmap to Scan the Network
Overview
The article provides an overview of the Nmap tool and its capabilities for network scanning and security analysis. It explains how Nmap can be used to identify open ports, running services, and potential vulnerabilities on a network and how it can be used to detect possible intrusions. The article also covers some advanced usage of Nmap, such as firewall/IDS evasion and spoofing, and running NSE scripts. It emphasizes the importance of interpreting the results of a Nmap scan and the need to use Nmap results to identify and fix vulnerabilities and detect potential intrusions.
Introduction
Nmap, short for "Network Mapper", is a powerful and widely-used tool for network exploration and management. It allows users to scan networks and gather information about the hosts and services that are running on them. One of the most common tasks that Nmap can carry out is host discovery, where it finds all active hosts on a network by sending various types of packets to the target IP address or range of IP addresses. Another common task is port scanning, which allows users to identify which services are running on a particular host, which is useful for identifying vulnerabilities and troubleshooting network issues.
Nmap can also be used to identify the specific version of a service running on a particular port through version detection and the operating system of a host through OS detection. The scripting engine in Nmap allows users to write custom scripts to automate tasks and gather additional information about the hosts and services on a network.
In addition to these, Nmap can also be used to create an inventory of all the devices and services running on a network, including hardware and software details, and evade firewalls and intrusion detection systems by sending packets with different flags and options. These are just some of the many tasks that Nmap can carry out, and with its powerful scripting engine, users can create custom scripts to perform even more complex tasks.
Basic Usage
The Basic Usage of Nmap includes the synopsis of the Nmap tool. The basic command to use the tool is:
Nmap offers several types of scans that can be used to gather different types of information about the hosts and services on a network. Some of the most common scan types in Nmap include:
- Ping scan:
A ping scan is used to determine whether a host is online or not. It sends an ICMP echo request packet to the target host and waits for a response. If a response is received, the host is considered online. To perform a ping scan we use the flags “-sP” and “-sn”. An example of the command used to perform a ping scan is: - TCP connect scan:
A TCP connect scan establishes a full TCP connection to the target port to determine if it is open. This is the most basic and most reliable scan type, but it is also the slowest and most easily detected. To perform a connect scan we use the flag “-sT”. An example of the command used to perform a TCP connect scan is: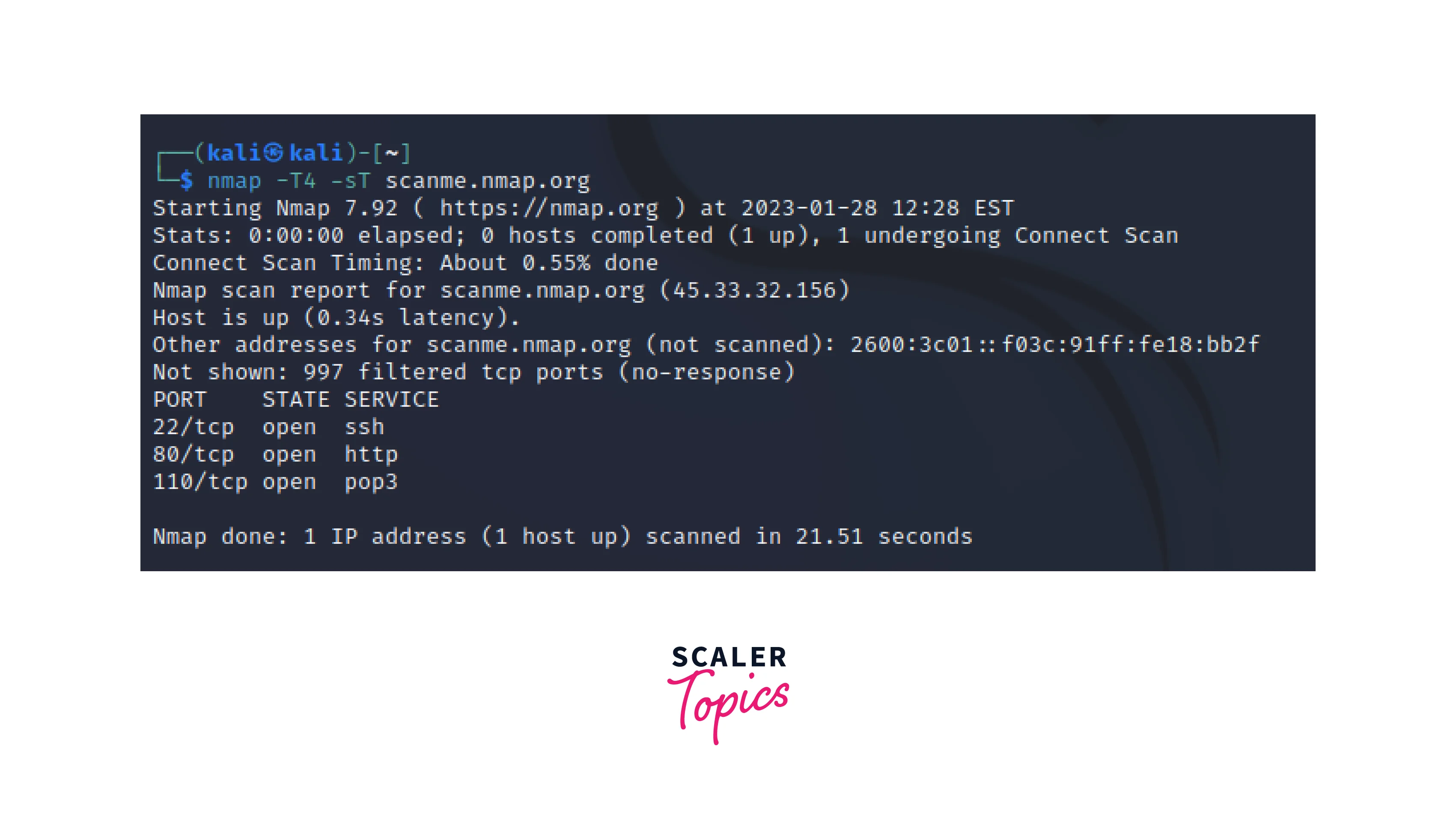 // The above image depicts the TCP connect scan results of scanme.nmap.org, it shows that three ports are open which include ssh, http, and pop3.
// The above image depicts the TCP connect scan results of scanme.nmap.org, it shows that three ports are open which include ssh, http, and pop3.
-
TCP SYN scan:
A TCP SYN scan, also known as a "half-open" scan, sends an SYN packet to the target port and waits for an SYN-ACK or RST packet in response. If an SYN-ACK packet is received, the port is considered open. To perform a TCP SYN scan we use the flag “-sS”. An example of the command used to perform a TCP connect scan is: -
TCP FIN, Xmas, and Null scan:
These scans use different combinations of TCP flags to determine if a port is open. They can be useful for evading firewalls and intrusion detection systems. We use the following flags “-sF”,”-sX”,”-sN” for TCP FIN, XMAS, and Null Scans respectively -
UDP scan:
A UDP scan sends a UDP packet to the target port and waits for an ICMP "port unreachable" error message in response. If no error message is received, the port is considered open. To perform a UDP scan we use the flag “-sU”. An example of the command used to perform the UDP scan is: -
OS detection scan:
An OS detection scan uses a variety of techniques to identify the operating system of a host. This can be useful for understanding the network environment and for identifying potential vulnerabilities. To enable OS detection, we use the flag “-o”. An example of the command used to perform the OS detection is: -
Version detection scan:
A version detection scan attempts to identify the specific version of a service running on a particular port. This information can be used to identify vulnerabilities and to ensure that software is up-to-date. To enable version detection scan, we use the flag “-sV”. An example of the command used to perform the version detection scan is: -
Script scan:
A script scan allows you to run Nmap Scripting Engine (NSE) scripts on the target host, which can be used to gather additional information about the hosts and services on the network.
Advanced Usage
NMap is a powerful tool for network exploration and management, and it offers many advanced features that can be used to gather more detailed information about the hosts and services on a network. Here are some examples of advanced usage of Nmap:
The below example shows a full scan using the -A option that enables OS detection, version detection, script scanning, and traceroute.
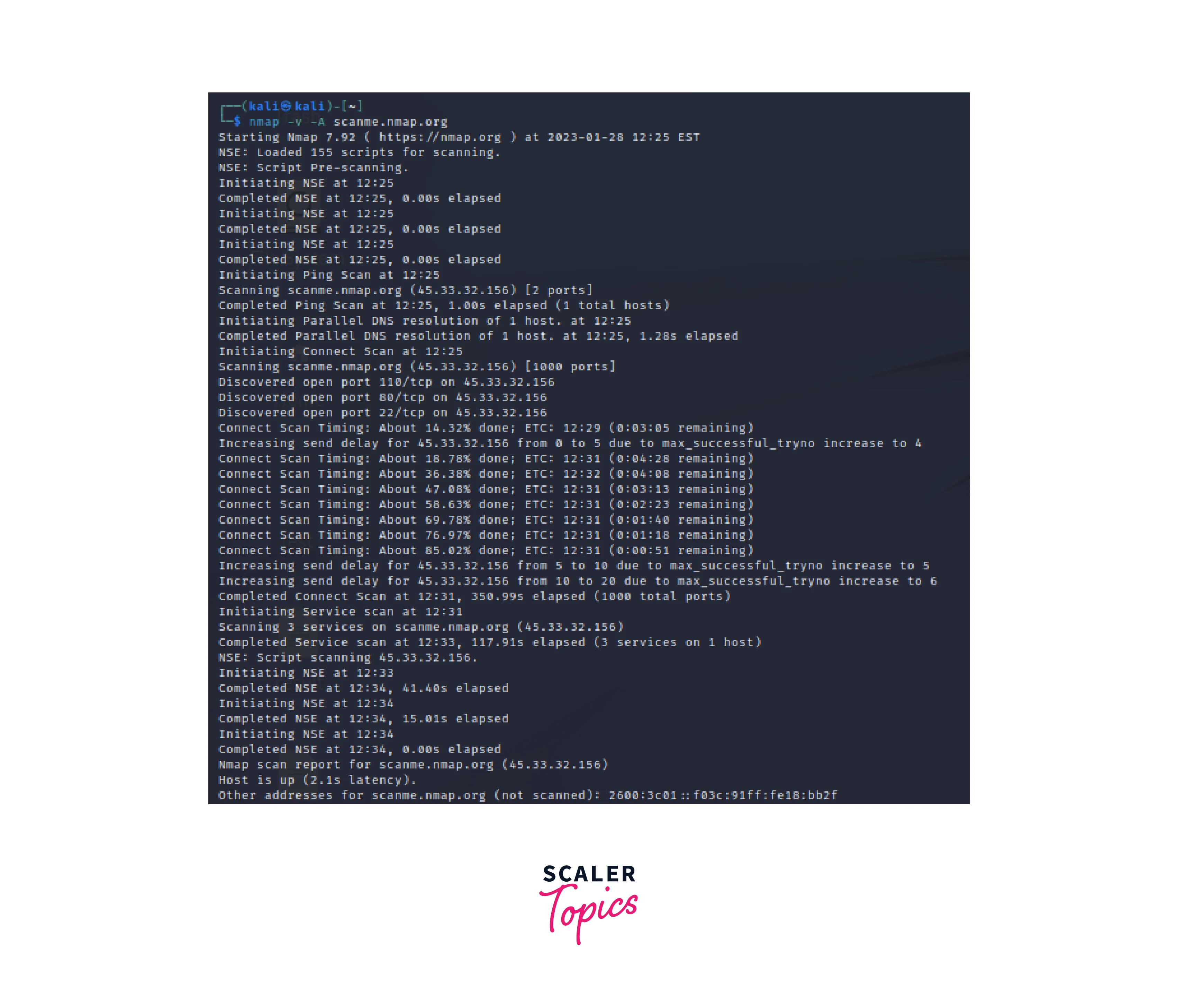 // This image depicts the scan process on our target.
// This image depicts the scan process on our target.
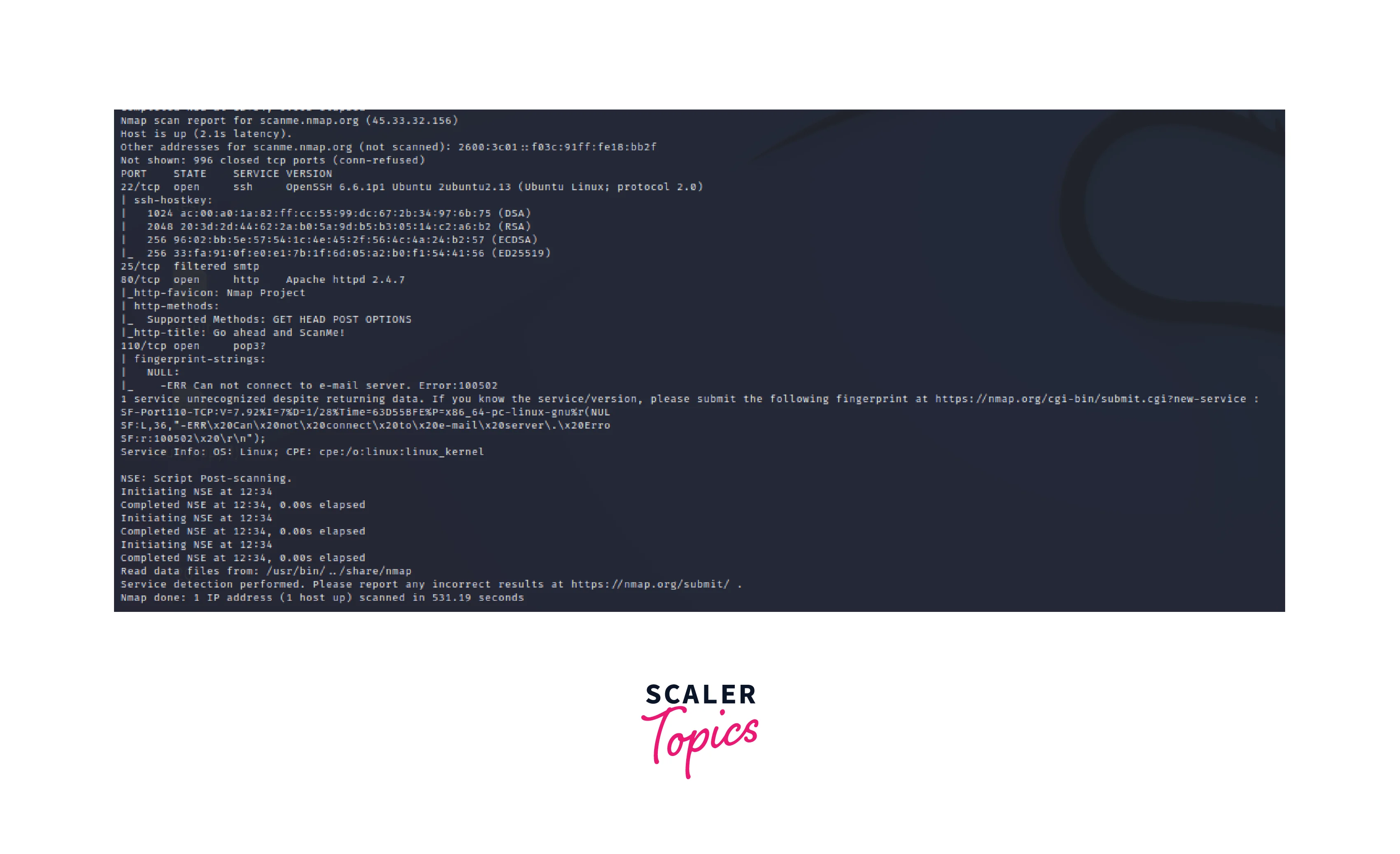 // This image depicts the Scan report for our scan performed.
// This image depicts the Scan report for our scan performed.
- To perform a stealth scan, you can use the "-sS" option. A stealth scan, also known as an SYN scan, sends an SYN packet to the target port and waits for an SYN-ACK or RST packet in response. This type of scan is less likely to be detected by firewalls and intrusion detection systems, making it a useful option for penetration testing and vulnerability assessments.
- To perform a version detection scan on all open ports, you can use the "-A" option. This option enables OS detection, version detection, script scanning, and traceroute all at once. This can provide a comprehensive overview of the target host, including the version of the operating system, the version of the services running, and potential vulnerabilities.
- To perform a service and version detection scan, you can use the "-sV --version-all" option. This option attempts to identify the specific version of a service running on a particular port, even if the service is filtered or closed. This can provide valuable information for identifying vulnerabilities, and troubleshooting network issues.
- To perform a script scan on all ports, you can use the "-sC --script=default" option. This option runs a default set of NSE scripts on all open and closed ports. This can be useful for discovering additional information about the host or identifying vulnerabilities.
- To perform a scan on multiple hosts, you can use the "-iL" option followed by a text file containing the list of IP addresses or hostnames of the devices you want to scan. This can save time and effort if you need to scan a large number of hosts.
- To perform a scan on a specific operating system, you can use the "--osscan-guess" option. This option attempts to identify the operating system of the target host, which can be useful for identifying vulnerabilities that are specific to certain operating systems.
- The top ports are the most commonly used ports on a host or network, and they are often the first ports that are targeted by attackers. By default, Nmap scans the top 1000 most common ports, but this can be customized by using the "--top-ports" option followed by a number. For example, "nmap --top-ports 100 192.168.1.1" will scan the top 100 ports on the device at IP address 192.168.1.1. This is a fast and efficient way to identify open ports and running services on a target host, and it can be useful for identifying vulnerabilities and potential attack vectors.
Interpretation of Results
The results of a Nmap scan provide a wealth of information about the hosts and services on a network, including open ports, running services, and potential vulnerabilities.
One of the most important things to look for in the results of a Nmap scan is the list of open ports. This list will show you which ports on the target host or network are open and accepting connections. This information can be used to identify running services and potential vulnerabilities. For example, if port 80 is open, that means that the host is running a web server, and if port 22 is open, that means that the host is running SSH. By identifying open ports, you can determine which services are running on the target host and what potential vulnerabilities may exist.
Another important aspect of interpreting the results of a Nmap scan is identifying the services that are running on open ports. Nmap can identify the specific version of a service and can also identify version information even if the service is filtered or closed. This information can be used to identify vulnerabilities and ensure that software is up-to-date. By identifying the specific version of a service, you can determine if the version is vulnerable to known exploits and take appropriate action.
It is also important to look for any potential vulnerabilities that may be present on the network. Nmap can identify a wide range of vulnerabilities, including those that are specific to certain operating systems. Additionally, Nmap can also run NSE scripts to identify additional vulnerabilities. By identifying potential vulnerabilities, you can take appropriate action to fix or mitigate the issue.
In addition to the above, you can use Nmap results to identify possible intrusions in the network. By keeping track of open ports and services on the network, you can identify when new ports or services appear, which may indicate that an attacker has gained access to the network. This can be done by regularly scanning the network and comparing the results to previous scans.
Overall, interpreting the results of a Nmap scan is an essential step in understanding the security of a network. It requires a thorough understanding of network security and the ability to analyze and understand large amounts of data. It is important to regularly scan your network, and interpret the results to identify and fix vulnerabilities and detect potential intrusions.
Conclusion
- Nmap is a powerful tool for network scanning and security analysis.
- It can be used to identify open ports, running services, and potential vulnerabilities on a network.
- The results of a Nmap scan can be complex and require a deep understanding of network security to properly interpret.
- Some of the advanced uses of Nmap include firewall/IDS evasion and spoofing, and running NSE scripts.
- It is important to use Nmap results to identify potential intrusions and take appropriate action to fix or mitigate vulnerabilities.
- Nmap should only be used in authorized and legal network testing environments.
- Regularly scanning the network and interpreting the results is an important step in understanding the security of a network.
