What are Open Redirects?
Overview
Open Redirects are a type of security vulnerability that can be found in web applications. They occur when an attacker can manipulate a URL parameter to redirect a user to a different, often malicious, website. This type of attack can be particularly dangerous because it can trick users into visiting a fraudulent site, leading to the theft of sensitive information or installation of malware.
This article provides an in-depth explanation of what open redirects are, how they work, and the risks they pose to users and organizations. It also explores the standard methods used by attackers to exploit this vulnerability and offers prevention measures that web developers can implement to mitigate the risk.
By understanding the nature of open redirects and the techniques used by attackers to exploit them, organizations can take the necessary steps to protect their users and secure their web applications against potential threats.
Introduction
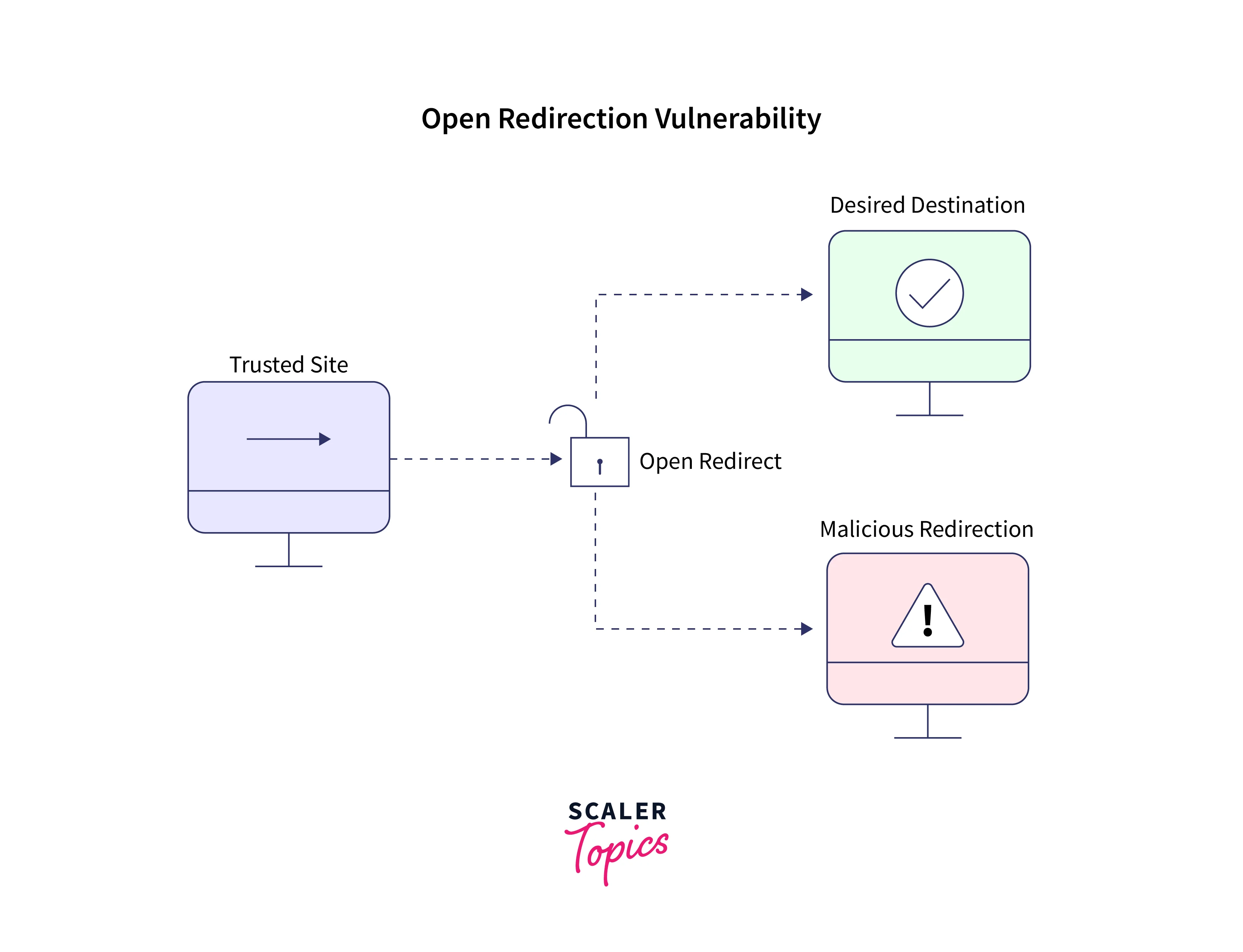
Open redirects are a security vulnerability that affects many web applications, allowing attackers to redirect users to a malicious website. This type of attack can be difficult to detect, and it can be used to steal sensitive information or distribute malware. As a result, understanding what open redirects are and how to prevent them is essential for protecting both users and web applications.
Open redirects occur when a web application allows an attacker to control a parameter in a URL, which is used to redirect the user to another website. For example, a legitimate website may use a URL parameter to redirect users to a login page after they click on a link. However, an attacker can manipulate this parameter to redirect the user to a malicious website, such as a phishing site or a site hosting malware.
Open redirects can be particularly dangerous because they can bypass security measures, such as firewalls and antivirus software. This is because the user is redirected to a legitimate website first, which may not be flagged as a potential threat. The user is then redirected to the malicious site, which can be used to steal sensitive information or install malware on the user's device.
Open redirects are a serious security vulnerability that can result in the theft of sensitive information or the installation of malware on a user's device. Understanding what open redirects are and how to prevent them is essential for protecting both users and web applications. By implementing preventive measures and educating users about the risks of clicking on untrusted links, organizations can mitigate the risk of open redirect attacks and safeguard their online assets.
What are Open Redirects?
Open redirects are a type of web vulnerability where an attacker can redirect a user from a legitimate website to a malicious website by manipulating a URL parameter.
An open redirect occurs when a website allows an external parameter to specify the destination of a redirect. For example, a website might have a URL that looks like this:
http://www.safe.com/redirect?url=http://www.safetoo.com
In this case, the website is using the URL parameter to determine where to redirect the user. An attacker could modify the URL parameter to point to a malicious website, like this:
http://www.example.com/redirect?url=http://www.malicious.com
When the user clicks on the link, they will be redirected to the malicious website, which could be used for phishing attacks or to deliver malware.
Open redirects are a common vulnerability in web applications and can be prevented by validating the redirect destination and limiting the use of external parameters to specify the redirect location. Web developers must be aware of this vulnerability and take steps to prevent it in their applications.
How Does Open Redirect Work?
Open redirect works using a URL parameter to redirect users to a specified website. This parameter is often named "URL" or "redirect_url" and is used in web applications to allow users to be redirected to other pages on the same website or to external websites.
However, if the URL parameter is not properly validated, an attacker can manipulate it to redirect the user to a malicious website instead of the intended destination.
For example, suppose a web application has a URL like this:
http://www.example.com/redirect?url=http://www.example.com/home
The URL parameter is used to specify the destination of the redirect. If an attacker can modify the URL parameter, they can redirect the user to a malicious website.
Here's an example of an open redirect vulnerability:
http://www.example.com/redirect?url=http://www.attacker.com
In this case, the user will be redirected to the attacker's website instead of the intended destination.
Open redirects are a security risk because they can be used to trick users into visiting malicious websites. For example, an attacker could send a phishing email with a link that looks like it goes to a legitimate website but redirects to a fake login page that steals the user's login credentials. To prevent open redirect vulnerabilities, web developers should validate the redirect URL to ensure it's a trusted website, and should avoid using user-controlled input to determine the destination of a redirect.
What Causes Open Redirect Vulnerability?
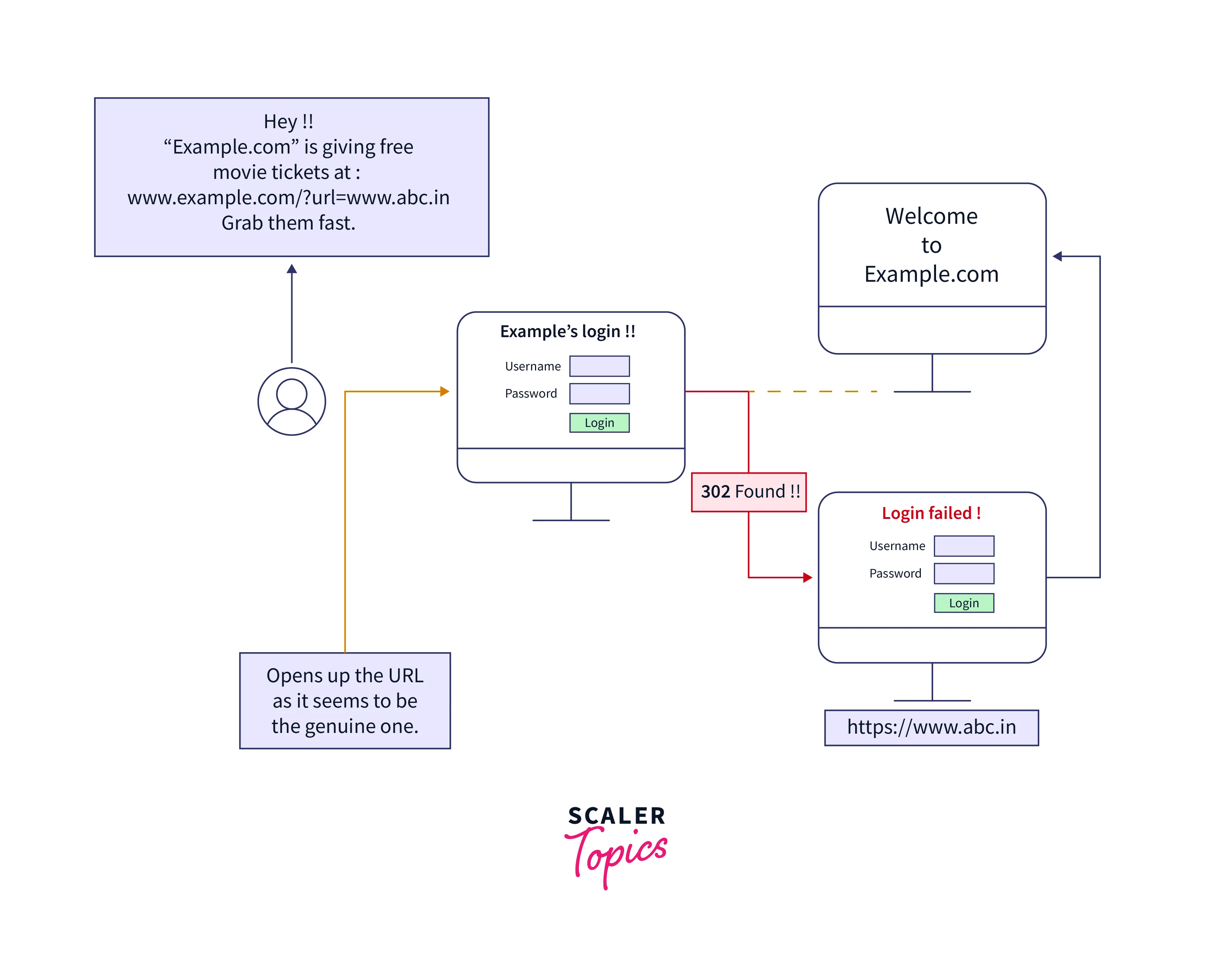
Open redirect vulnerabilities are caused by a lack of input validation or filtering in web applications that use URL redirection. These vulnerabilities arise when an attacker can control a parameter in a URL that is used for redirection.
In web applications, URL redirection is a common feature used to direct users to a different page or site. For example, a login page might redirect users to their account dashboard after successful login. The URL redirection process relies on parameters passed in the URL that tell the web application which page to redirect the user to.
An open redirect vulnerability occurs when a web application allows an attacker to modify the URL parameters used for redirection. This allows the attacker to redirect the user to a malicious website instead of the intended destination.
This can steal sensitive information or install malware on the user's device.
Open redirect vulnerabilities can also be used in phishing attacks. An attacker can send an email with a link to a legitimate website that includes an open redirect. When the user clicks on the link, they are redirected to the legitimate site first, which can help to gain their trust. The user is then redirected to a fake login page or another malicious site, where their information is stolen.
Types of Open Redirects
Several types of open redirects can be used by attackers to redirect users to malicious websites. Understanding the different types of open redirects is important for web developers and security professionals to protect against these types of attacks.
-
Reflected open redirect:
Reflected open redirects occur when an application takes a URL parameter and reflects it to the user in the response. An attacker can use this vulnerability to craft a URL that includes a redirect to a malicious website. When the user clicks on the link, they are redirected to the malicious site. -
Stored open redirect:
Stored open redirects occur when an application stores a URL parameter in a database or file, and then uses it to redirect the user. An attacker can manipulate the stored value of the parameter to redirect the user to a malicious website. -
DOM-based open redirect:
DOM-based open redirects occur when an attacker can manipulate the Document Object Model (DOM) of a web page to cause a redirect. This can be done by injecting JavaScript into the page, which modifies the URL used for redirection. -
Client-side open redirect:
Client-side open redirects occur when a user is redirected to a different website by clicking on a link that is not properly validated on the client side. This can be caused by a lack of validation or filtering of input in client-side scripts. -
Header-based open redirect:
Header-based open redirects occur when an attacker can modify the HTTP headers sent by the server in response to a user request. This can be used to modify the URL used for redirection, which can be used to redirect the user to a malicious website.
Impact of Open Redirects
Open redirects can have a significant impact on both users and organizations. The impact of open redirects varies depending on the nature of the attack and the intent of the attacker. Here are some of the ways that open redirects can affect users and organizations:
-
Phishing attacks:
Open redirects can be used in phishing attacks to trick users into clicking on links that redirect them to fake login pages or other malicious sites. The attacker can then steal the user's login credentials, and personal information, or install malware on their device. -
Malware infections:
Open redirects can be used to redirect users to websites that contain malware, such as viruses, spyware, or ransomware. When the user visits the site, the malware is downloaded onto their device, which can compromise the security of their system and data. -
Reputation damage:
If an attacker can redirect users to a malicious website from a legitimate website, this can damage the reputation of the legitimate website. This can lead to a loss of customer trust and business, especially if the website is associated with sensitive information or financial transactions. -
SEO spamming:
Attackers can use open redirects to redirect users to spammy or fraudulent websites that are designed to manipulate search engine rankings. This can negatively impact the search engine optimization (SEO) of legitimate websites, as search engines may associate the redirecting website with spammy or fraudulent content. -
Brand impersonation:
Open redirects can be used to impersonate legitimate brands or organizations. Attackers can create URLs that appear to be from a legitimate source but redirect users to a fake website. This can be used to steal personal information, money, or login credentials. -
Legal and financial liabilities:
Organizations that are found to have open redirect vulnerabilities may be held legally or financially liable for damages caused by the attacks. There are strict laws related to the protection of personal information such as GDPR, SOC2, HIPAA and many others. The Indian government is also planning to come up with strict laws for this. This can include compensation for users who have been impacted by the attack, fines, or legal fees.
How Hackers Exploit Open Redirects?
A hacker can exploit open redirects to redirect users to malicious websites or steal sensitive information. Here are some of the ways that a hacker can exploit open redirects:
-
Phishing attacks:
A hacker can use open redirects to redirect users to a phishing site that looks like a legitimate website. The hacker can then steal the user's login credentials, credit card numbers, or other sensitive information. -
Session hijacking:
A hacker can use open redirects to steal user sessions. When a user is logged in, the session is usually maintained through a session ID. A hacker can use open redirects to send the session ID to a third-party website that they control, allowing them to hijack the user's session. -
Watering hole attacks:
A watering hole attack involves the hacker identifying a website that is commonly visited by the target audience and then injecting malicious code into the website via an open redirect vulnerability. When users visit the site, they are redirected to a malicious website or served malware. -
Cross-site scripting (XSS) attacks:
A hacker can use an open redirect vulnerability to execute a cross-site scripting (XSS) attack. The hacker can inject malicious code into the redirect URL, which is then executed on the user's browser. This can be used to steal sensitive information or take control of the user's system. -
Advanced persistent threats (APTs):
A hacker can use open redirect vulnerabilities as part of a larger APT campaign. The hacker may use the vulnerability to gain access to the target organization's network, steal sensitive data, or conduct other types of attacks. -
Malvertising:
A hacker can use an open redirect vulnerability to redirect users to a malicious advertisement (malvertisement). The malvertisement may contain malware or may be designed to trick users into divulging personal information.
To exploit open redirects, a hacker needs to find a vulnerable URL parameter that can be manipulated. They can then craft a URL that includes a redirect to a malicious website. When the user clicks on the link, they are redirected to the malicious site.
How to Prevent Open Redirection Vulnerability?
Open redirection vulnerabilities can be prevented by following a few best practices. Here are some guidelines that can help prevent open redirection vulnerabilities:
-
Validate all user input:
Ensure all user input is properly validated and filtered. This can include using a whitelist of trusted URLs or restricting redirection to specific domains. -
Use server-side redirect scripts:
Use server-side redirect scripts to handle redirection, rather than client-side scripts. Server-side scripts are more secure because they cannot be manipulated by the client. -
Limit the use of URL parameters:
Limit the use of URL parameters for redirection, and avoid using them to store sensitive information. -
Use HTTPS:
Use HTTPS to encrypt all data transmitted between the server and the client. This can prevent attackers from intercepting or tampering with the data. -
Implement access controls:
Implement access controls to restrict access to sensitive resources. This can help prevent attackers from accessing sensitive data or applications. -
Implement user awareness programs:
Educate users about the risks of clicking on links from untrusted sources. This can help prevent users from falling victim to phishing attacks or other types of open redirection attacks. -
Regularly update and patch software:
Ensure that all software is up-to-date and regularly patched. This can help prevent attackers from exploiting known vulnerabilities in the software. -
Implement security controls:
Using security measures such as firewalls, antivirus software, and intrusion detection systems, to detect and prevent open redirect attacks. -
Follow secure coding practices:
Follow secure coding practices, such as input validation, output encoding, and session management, to prevent security vulnerabilities. Implementing SAST automation can help in detecting open redirection vulnerabilities in the initial development stage. -
Test for vulnerabilities:
Regularly test for vulnerabilities in web applications and websites, including open, and redirect vulnerabilities. This can help identify and address vulnerabilities before they can be exploited by attackers.
Conclusion
-
Open redirects are a type of security vulnerability that can be exploited by hackers to redirect users to malicious websites or steal sensitive information.
-
Open redirects can be caused by a lack of input validation or filtering in URL parameters, which allows attackers to inject malicious code into the redirect URL.
-
The impact of open redirects can be significant, including phishing attacks, malware infections, SEO spamming, brand impersonation, and session hijacking.
-
To prevent open redirect attacks, web developers should implement secure coding practices, input validation and filtering, server-side redirect scripts, and access controls, among other measures.
-
Organizations should also implement user awareness programs to educate users about the risks of open redirects and use security measures such as firewalls, antivirus software, and intrusion detection systems to detect and prevent attacks.
-
By following these guidelines, organizations can protect their users and data from the risks of open redirect vulnerabilities and help prevent attackers from exploiting these vulnerabilities.
