OWASP Juice Shop
OWASP Juice Shop serves as a crucial training ground for web application penetration testers and ethical hackers. As a sophisticated insecure web app, it offers a hands-on experience to identify and fix vulnerabilities. With a focus on challenge hunting, its architecture provides a realistic simulation for honing skills in a secure environment, enhancing expertise.
What is OWASP Juice Shop?
OWASP Juice Shop is a leading, intentionally vulnerable web app ideal for security training, CTFs, and testing security tools. It simulates the OWASP Top Ten vulnerabilities and real-world application flaws. This application aids cybersecurity professionals in understanding and mitigating risks by providing a practical environment to test and enhance their skills.
Features of OWASP Juice Shop
OWASP Juice Shop is an intentionally created insecure web application written in JavaScript that features a range of web application vulnerabilities that comes under OWASP and other known vulnerabilities. This vulnerable application comes with numerous hacking challenges of contrasting difficulty. The user (usually a security professional or penetration tester) is supposed to exploit the underlying vulnerabilities. Finding its scoreboard is one of the most painless challenges. OWASP Juice Shop acts as a guinea pig that security professionals can use to learn web application penetration testing. Some other notable features of this vulnerable application are:
- It is an open-source web application licensed under the MIT license. It does not incur hidden costs or caveats.
- The application is easy to install and use. You can choose between Node.js, Docker, and Vagrant to operate on various platforms like Windows, Mac, and Linux. We can also run it in all major cloud providers.
- It is an excellent tool for newcomers as it contains hacking instructor scripts with an optional tutorial mode guide. It also features several challenges with an explanation of the underlying vulnerabilities.
- The entire OWASP Juice Shop is gamified in nature. The app will notify the user to solve challenges. It also comes with a scoreboard where users can track the various security challenges they have completed or are yet to go.
- The application is self-contained, meaning it can automatically download new &additional dependencies or pre-packages as per requirement.
- The OWASP Juice Shop is self-healing, meaning it cleans all data and cache and repopulates it from scratch on every server startup. It can store all user progress in the browser or the local backup.
- This application is customizable, and businesses can set the app as per look & feel, vulnerabilities needed, or customer requirements.
- It features Capture the Flag (CTF) and has more than 20 hacking challenges. It also comes with additional coding challenges that help users find and fix responsible code flaws.
- It supports interoperability. It means OWASP juice Shop allows us to integrate OWASP Juice Shop with training systems via WebHook, use API or file import and monitor the extensive metrics.
Why OWASP Juice Shop Exists?
To those who aren't aware of the application vulnerabilities this app intentionally keeps, it will look like a small online shop that sells fruits and vegetable juice. Apart from the overrated payment system and delivery aspect, all other operations of this app are fully functional. It is the tip or upper side of the iceberg. What lies below it is the giant collection of web app vulnerabilities, comprising 85 different challenges with varying difficulty levels. These intentionally planned vulnerabilities exist to help security professionals and penetration testers get a hands-on idea about how to exploit different web application vulnerabilities.
Its development started on September 2014 & uses various server-side development platforms like ASP/JSP/Servlet. Over the past few years, other modern and newly detected vulnerabilities got added to this web app. OWASP Juice Shop exists to highlight all possible web application vulnerabilities that one can learn to identify or exploit. It uses a gamification approach to teach security professionals and penetration testers how to make software security visible to developers and cybersecurity professionals. In other words, OWASP Juice Shop delivers a unique web app to provide impartial, practical details about Web app security to cybersecurity aspirants, universities, business firms, government agencies, and other associations worldwide.
OWASP Juice Shop Architecture
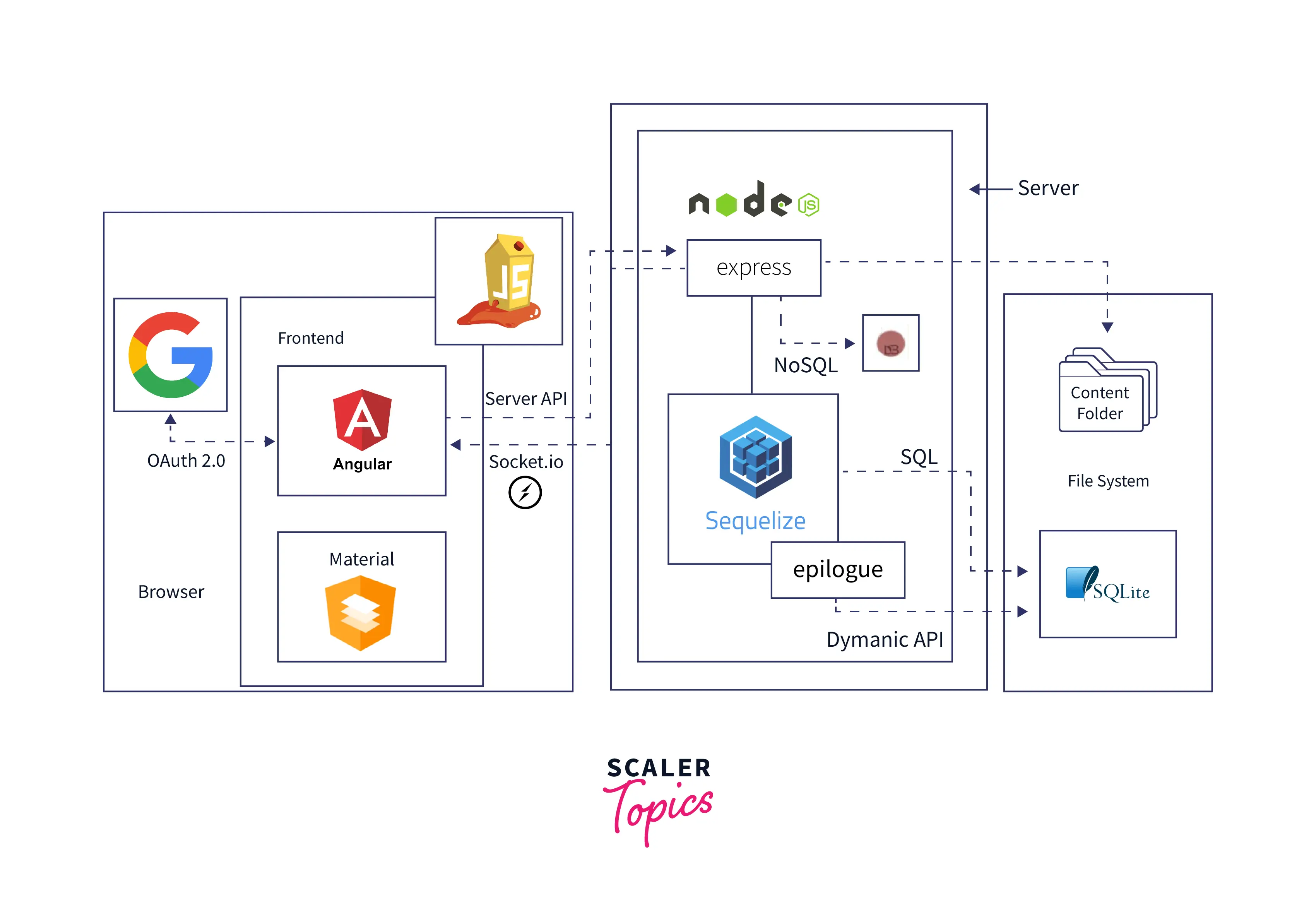
This vulnerable web application is a pure web app that uses JavaScript (JS) & TypeScript (TS) along with front-end libraries and frameworks like Angular. It acts as a Single Page Application (SPA). Its architecture got its exceptional design interface layout from Angular Material components & Google's Material Design. The backend uses SQLite, an Express app hosted in a Node.js server. Its functionality to the client resides through the RESTful API.
It also leverages a data storage system through MarsDB as part of the vulnerable web app. It derivates from the widely used MongoDB NoSQL database. It is compatible with most query/modifies operations. It comes with various push notification that pops up when any challenge gets successfully hacked. These notifications use the Web Socket protocol. This vulnerable app also offers convenient user registration by implementing OAuth 2.0 so that penetration testers and aspirants using it can sign in through their Google accounts.
Here is the overall architecture diagram of the OPWAS Juice Shop. The block diagram shows how the app performs high-level communication between the client, server, and data layers.
Part I - Hacking Preparations
There are different ways to use the OWASP Juice Shop application. The chances are high that you can deploy and use this vulnerable web application on any system or platform. While installing or running the application, if you encounter any challenge or issue where your application is not running, you can ask for help on the community chat by opening the GitHub issue. Also, you may flip through the troubleshooting guide that comes along.
Without further ado, let's jump into how to set up & use the vulnerable web application.
One-click Cloud-based Setup
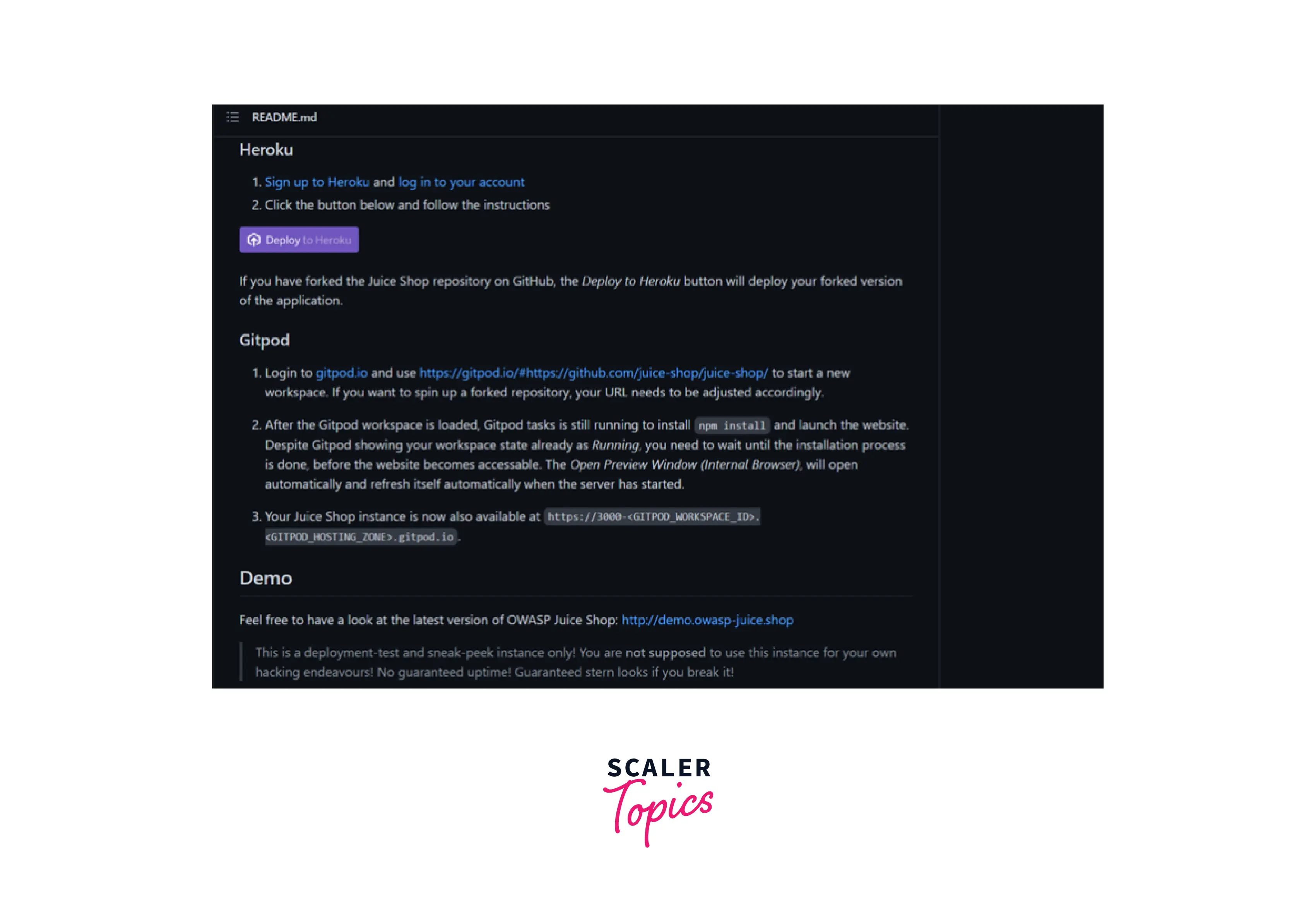
The fastest way to use the instance of this vulnerable web app is by clicking the "Deploy to Heroku" button that comes within the README.md file. You have to log in to the Heroku account, & it will redirect you to a single instance that hosts the application. In case you fork the repository on GitHub and then click the "Deploy to Heroku" button, it will deploy the forked version (customizable) version of OWASP Juice Shop.
Local Installation/Setup
To execute the OWASP Juice Shop web application locally on your computer (as a local setup), you need to install Node.js on your system. The Juice Shop runs officially on different versions like 8.x, 10.x, and 11.x. During the deployment and continuous integration of the application as a part of the local setup, it will automatically test the compatible version of Node.js. For long-term support, Juice Shop recommends installing version 10.x of Node.js. The steps are: a. Install Node.js from its official site. b. Next, on the command-line tool like Command Prompt, Git bash, or Terminal, run git clone https://github.com/bkimminich/juice-shop.git c. Navigate to the cloned folder with the command: cd juice-shop d. Run npm install. You have to perform this step before first initiating or if you change the source code. e. Run npm start to start the application. f. In your browser, browse to http://localhost:3000
Setup from Pre-packaged Distribution
- To run the OWASP Juice Shop pre-packaged distribution, first install the 64bit Node.js on your Linux or Windows system.
- Then, download juice-shop-<version>_<node-version>_<os>_x64.zip (or .tgz - if Linux). You will find it attached to the GitHub repository as per the latest release.
- Unpack the archive. Run the command: "npm start" in an unpacked folder to launch the Juice Shop web application.
- Once it gets fully unpacked, browse to http://localhost:3000.
Part II - Challenge Hunting
There are various challenge categories and tags that security professionals and aspirant hackers can try exploiting. There are six different levels of vulnerability-hunting challenges that OWASP Juice Shop provides. You can look at the hints in case you get stuck in any particular challenge. Without further delay, let's jump into the list of challenges OWASP Juice Shop offers in various categories.
Trivial Challenge
It has the easiest of challenges with 1 star.
- Confidential Document: Her have to access a confidential document.
- Error Handling: We have to irritate an error that is not very gracefully handled.
- Privacy Policy: In this challenge, we have to read Juice Shop's privacy policy.
- Redirects Tier 1: In this challenge, we have to redirect to a donation site that went out of business.
- Repetitive Registration: Follow the DRY principle while registering a user.
- Score Board: Find the carefully hidden 'Score Board' page.
- XSS Tier 0: We have to execute a reflected XSS attack with <iframe src = "javascript:alert(`xss`)"> .
- XSS Tier 1: We have to execute a DOM XSS attack with <iframe src = "javascript:alert(xss)"> .
- Zero Stars: We have to provide devastating zero-star feedback to the store.
Easy Challenges
- It has easy challenges with 2 stars for beginners.
- Admin Section: In this challenge, we have to access the administration section of the store.
- Basket Access Tier 1: Here, we have to view another user's shopping basket.
- Deprecated Interface: In this challenge, we have to utilize a deprecated B2B interface not properly shut down.
- Five-Star Feedback: Here we have to get rid of all 5 star customer feedback.
- Login Admin: In this challenge, we have to log in with the administrator's user account.
- Login MC SafeSearch: In this challenge, we have to log in with MC SafeSearch's original user credentials without using SQL Injection.
- Password Strength: In this challenge, we have to log in with the administrator's user credentials without using SQL injection or previously altering them.
- Security Policy: We have to behave like any "white hat" hacker.
- Weird Crypto: In this challenge, we have to inform the shop about an algorithm or library not use the way it does.
- XSS Tier 1.5: Here we carry out an XSS attack with <script> alert(xss) </script> on a legacy page within the application.
Medium Challenge
As the name suggests, it has medium-level challenges with a rating of 3 stars.
- Admin Registration: Registering you as an admin user.
- Basket Access Tier 2: In this challenge, we have to place an additional product into another user's shopping basket.
- CAPTCHA Bypass Tier 1: This challenge is about submitting 10 or more customer feedback within 10 seconds.
- Forged Feedback: We have to post some feedback in another user's name.
- Forged Review: We have to post a product review as another user or edit any user's existing
- review.
- Login Amy: In this challenge, we have to log in with Amy's original user credentials
- Login Bender: We have to log in with Bender's user account in this challenge.
- Login Jim: In this challenge, we have to log in with Jim's user account.
- Payback Time: Here we have to place an order that makes you rich.
- Privacy Policy Tier 2: Here we have to prove that you read our privacy policy.
- Product Tampering: In this challenge, we have to alter the href of the link within the O-Saft product description.
- Reset Bjoern's Password Tier 1: We have to reset the password of Bjoern's OWASP account via the Forgot Password mechanism through the security question.
- Reset Jim's Password: We have to reset Jim's password via the Forgot Password mechanism with a truthful answer to his security question.
- Upload Size: Here we have to upload a file larger than 100 kB.
- XSS Tier 2: In this challenge, we have to carry out a persisted XSS attack with <iframe src = "javascript:alert(xss)"> bypassing a client-side security mechanism.
- XSS Tier 3: In this challenge, we have to carry out a persisted XSS attack with <iframe src = "javascript:alert(xss)"> without using the frontend application at all.
- XXE Tier 1: In this challenge, we will be retrieving the content of C:\Windows\system.ini or /etc/passwd from the server.
Hard Challenge
This challenging level has increased difficulty, and OWASP rated it as 4 stars.
- Access Log: We have to take access to any access log file of the server.
- Christmas Special: In this challenge, we have to order the Christmas special offer of 2014.
- DLP Failure Tier 1: Here we must identify an unsafe product that was removed from the shop and inform the shop which ingredients are dangerous.
- Easter Egg Tier 1: In this challenge, we have to identify the hidden easter egg.
- Easter Egg Tier 2: In this challenge, we have to apply some advanced cryptanalysis for finding the real easter egg.
- Expired Coupon: Here, the challenge is to successfully redeem an expired campaign coupon code.
- Forgotten Developer Backup: In this challenge, we have to access a developer's forgotten backup file.
- Forgotten Sales Backup: In this challenge, we have to access a salesman's forgotten backup file.
- Login Bjoern: Here, the challenge is to successfully log in with Bjoern's Gmail account without previously changing his password.
- Lost in Recycling: Here we have to uncover an old Recycle request and inform the shop about its unusual address.
- Misplaced Signature File: In this challenge, we have to access a misplaced SIEM file having a signature.
- NoSQL Injection Tier 1: This challenge allows the server to sleep for some time.
- NoSQL Injection Tier 2: In this challenge, we have to revise multiple product reviews at the same time.
- Reset Bender's Password: In this challenge, we have reset Bender's password via the Forgot Password mechanism.
- Steganography: In this challenge, we have to find out a notorious character hiding in plain sight in the shop.
- Typosquatting Tier 1: In this challenge, we have to inform the shop about a typosquatting trick that is there within it.
- User Credentials: In this challenge, we have to retrieve a list of all user credentials via SQL Injection.
- Vulnerable Library: We must inform the shop about a vulnerable library it uses.
- XSS Tier 4: In this challenge, we have to perform a persisted XSS attack with <iframe src = "javascript:alert(xss)"> and bypass a server-side security mechanism.
- XSS Tier 5: Here we have to perform a persisted XSS attack with <iframe src = "javascript:alert(xss)"> using the HTTP header.
Dreadful Challenge
This set of challenges is even harder, and OWASP tagged it with 5 stars. It is for expert hackers and penetration testers.
- Blockchain Tier 1: In this challenge, we have to learn about the Token Sale before its official announcement.
- Change Bender's Password: Here we have to change Bender's password without using SQLi.
- DLP Failure Tier 2: Here, the challenge is dumpster dive the internet for a leaked password.
- Email Leak: Here we have to disclose unwanted information by accessing data cross-domain.
- Extra Language: Here, the challenge is to retrieve the language file that never made it into production.
- JWT Issues Tier 1: Here, the challenge is to counterfeit an essentially unsigned JWT token.
- Login CISO: Here we have to exploit OAuth 2.0 to log in with the CISO's user account.
- NoSQL Injection Tier 3: Here, the challenge is to perform a NoSQL injection to all the orders belonging to us.
- RCE Tier 1: In this challenge, we have to perform a Remote Code Execution that would keep a less hardened application busy forever.
- Reset Bjoern's Password Tier 2: In this challenge, we have to reset the password of Bjoern's internal account via the Forgot Password.
- Reset Morty's Password: Reset Morty's account password via the Forgot Password, obfuscating the answer to his security question.
- Supply Chain Attack: In this, we have to inform the dev team about a hazard/risk to some of their CVE/vulnerability.
- Typosquatting Tier 2: Here, the challenge is to inform the shop about a sneakier instance of typosquatting.
Diabolic Challenges
These are the hardest of all challenges. Once you complete these challenges, you will gain superior expertise in vulnerability analysis. OWASP rated it with 6 stars.
- Arbitrary File Write: Here, the challenge is to overwrite the Legal Information file.
- Forged Coupon: Here we have to forge a coupon code that gives a discount of at least 80 percent.
- Imaginary Challenge: Solve challenge #999 which does not exist.
- JWT Issues Tier 2: In this challenge, we have to forge an almost properly RSA-signed JWT token.
- Multiple Likes: Here we have to like any review at least three times under the name of the same user.
- Login Support Team: In this challenge, we have to log in with the support team's original user credentials without using an SQLi attack.
- Premium Paywall: Here we have to unlock Premium Challenge to access limited content.
- RCE Tier 2: In this challenge, we have to perform a Remote Code Execution (RCE) using infinite loops to keep your server occupied.
- SSRF: In this challenge, we have to ask for a hidden resource on the server.
- SSTi: In this challenge, we have to infect the server with malware.
- XSS (last tier): To solve this challenge, we have to embed an XSS payload </script> <script> alert(xss) </script> in the marketing collaterals.
Part III - Getting Involved:
After you have enjoyed completing all the challenges, of hacking the OWASP Juice Shop, you might want OWASP to inform you about its upcoming releases, challenges, fixes, and other updates. For that, you can stay tuned through various platforms.
OWASP Juice Shop Challenges
There are different challenge categories, tags, and coding challenges that OWASP Juice Shop hackers can solve. Let us discuss each of them one by one.
Challenge Categories
We can categorize the Juice Shop's vulnerabilities into multiple classes.
- Broken Access Control
- Broken Anti Automation
- Broken Authentication
- Cryptographic Issues
- Improper Input Validation
- Injection
- Insecure Deserialization
- Miscellaneous Challenges
- Security Misconfiguration
- Security through Obscurity
- Sensitive Data Exposure
- Invalidated Redirects
- Vulnerable Components
- XSS
- XXE
Challenge Tags
Tags are not for determining vulnerability categories but provide additional meta-information about the different challenges. They help cluster particular challenge types - like those that need some scripting or automation, lack seriousness, is good for practicing, etc.
- Brute Force
- Code Analysis
- Contraption
- Danger Zone
- Good Practice
- Good for Demos
- OSINT
- Prerequisite
- Shenanigans
- Tutorial-based
Coding Challenges
It is another code-based set of challenges that started with OWASP Juice Shop version 12.9.0. Here the vulnerable application offers developer-focused coding challenges for some of its existing hacking. Juice Shop allows associating vulnerable code as per various hacking challenges. Each coding challenge will have two phases:
- Find It: It is where the user has to identify and pick vulnerable code statements in an actual code snippet from Juice Shop.
- Fix It: In this phase, the user has to offer 3 to 4 options to determine to improve that vulnerability. We have to decide which solution will best fit.
Conclusion
- We hope this article has given a comprehensive idea of the various features of OWASP juice shop and why it exists.
- Next, we came across the OWASP juice shop architecture, hacking preparations, various challenges, and how to stay involved even after using it.
- Lastly, the article listed the different challenge categories, challenge tags, and types of coding challenges as part of the OWASP juice shop.
