Enumeration and Scanning
Overview
Cybersecurity is an important aspect for organizations trying to secure their networks and systems from security breaches. To make sure the networks and systems are secure companies hire penetration testers who hack through the system and search for exploitable vulnerabilities to fix them. This process in a nutshell is called penetration testing. Scanning and enumeration are two significant phases of a penetration test as it aims to search and identify vulnerabilities throughout the network or system using various tools and techniques. In this article, we are going to deep dive into the scanning and enumeration aspect of a penetration test.
Scanning and Enumeration in Cybersecurity
Scanning and enumeration are two critical activities in cybersecurity that help identify potential security threats and vulnerabilities in a computer network. Scanning is the process of sending requests to a target system to gather information about its network topology, open ports, and running services.
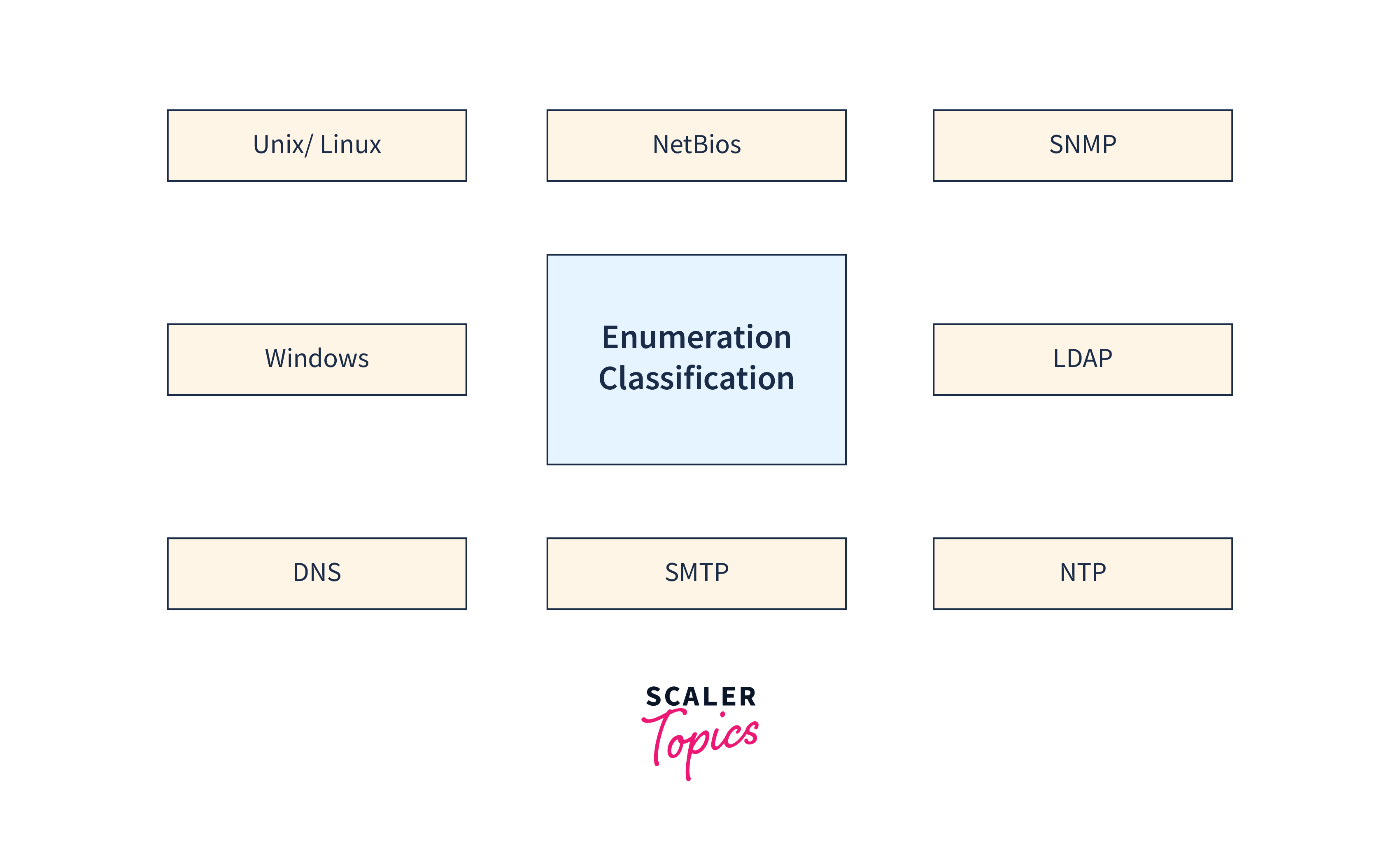
Enumeration is the process of using the information gathered during scanning to identify specific details about a target system, such as its operating system, applications, and user accounts. By combining the information gathered from scanning and enumeration, testers can build a comprehensive profile of a target system, and use this information to develop a strategy for attacking it.
Types of Scans and Enumerations
Several types of scans and enumerations can be performed during the scanning and enumeration phase of a penetration test. Some of the most common types include:
-
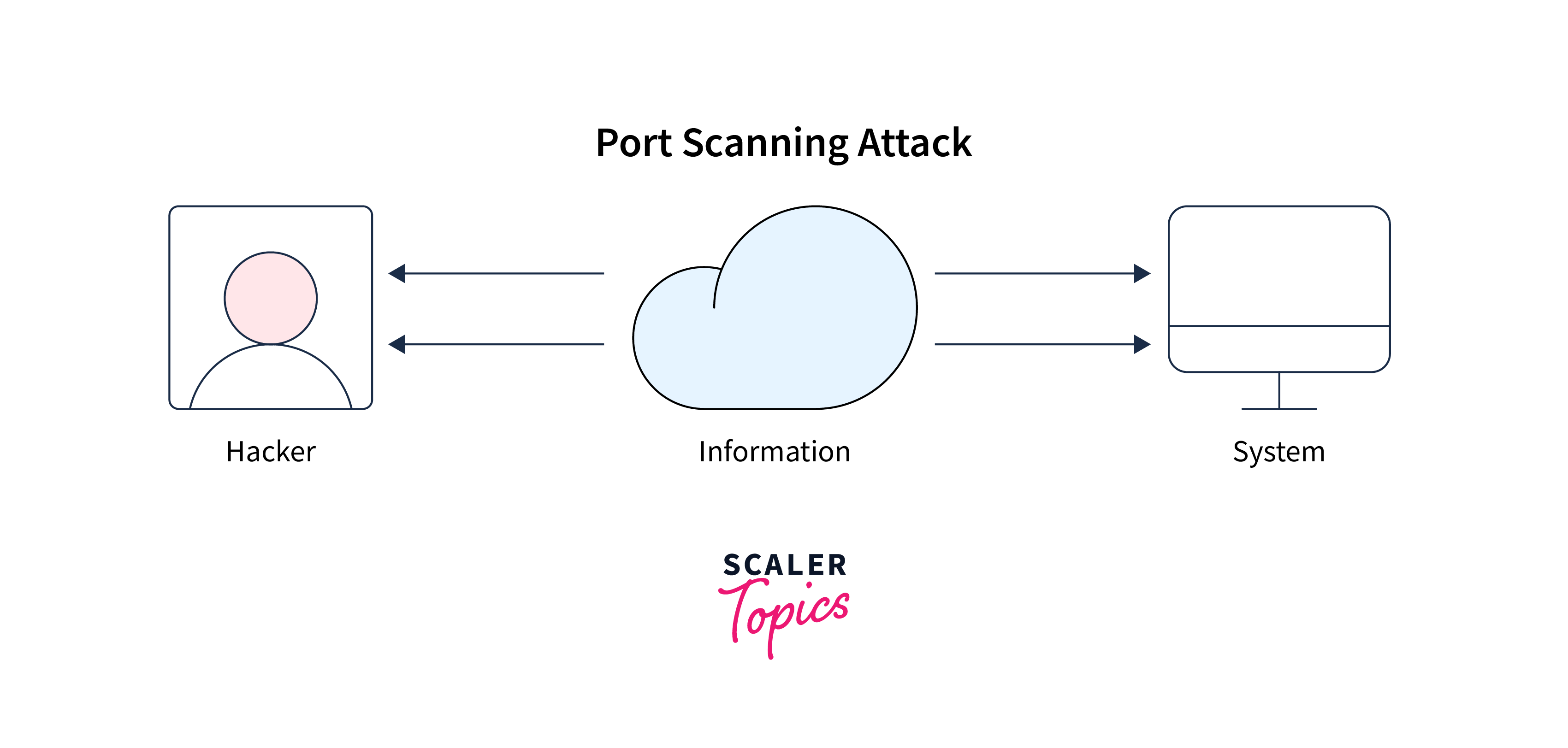
Port Scans:
A port scan is a type of scan that is used to determine which network services and ports are open and available on a target system. This type of scan helps to identify the types of services that are running on the target system and to determine the state of the ports on the target system (open, closed, or filtered). There are several types of port scans, including TCP connect scans, SYN scans, FIN scans, Xmas scans, and Null scans. -
Version Scans:
A version scan is used to determine the version of software that is running on a target system. This type of scan is useful for identifying known vulnerabilities in the software, as well as for determining which types of exploits are likely to be successful. -
OS Detection Scans:
An OS detection scan is used to determine the type of operating system that is running on a target system. This type of scan is useful for identifying known vulnerabilities in the operating system, as well as for determining which types of exploits are likely to be successful. -
Vulnerability Scans:
A vulnerability scan is used to identify known vulnerabilities in software and operating systems that are running on a target system. This type of scan is useful for identifying the potential impact of a vulnerability, as well as for determining the priority for remediation efforts. -
Banner Grabbing:
Banner grabbing is a technique used to gather information about a target system by connecting to it and examining the banner that is returned. This type of scan can be used to identify the type of operating system, web server, and application server that is running on the target system. -
Network Mapping:
Network mapping is a technique used to create a map of the target system's network, including the systems and services that are running on the network. This type of scan is useful for identifying potential attack vectors, as well as for developing a comprehensive understanding of the target system's network infrastructure. -
User Enumeration:
User enumeration is a technique used to determine the names of valid users on a target system. This information can be used to mount targeted attacks against specific users or to perform social engineering attacks. -
System Enumeration:
This involves actively trying to gather information about the target system, such as its operating system, version, and other details. -
Service Enumeration:
In service enumeration, the attacker actively tries to gather information about the services running on a target system, network, or device, such as the services offered, the versions being used, and other details.
Scanning and Enumeration Tools

There are various scanning and enumeration tools available in the market that can help organizations implement these techniques in their cybersecurity strategy. Some popular tools include:
- Nmap:
Nmap is a popular open-source tool that is used for network exploration, administration, and security auditing. Nmap can be used for a variety of tasks, including port scanning, version detection, OS detection, and vulnerability scanning. - Nessus:
Nessus is a commercial vulnerability scanning tool that is used to identify vulnerabilities in systems and applications. Nessus can be used to perform a variety of scans, including port scans, version scans, OS detection scans, and vulnerability scans. - OpenVAS:
OpenVAS is an open-source vulnerability scanning tool that is used to identify vulnerabilities in systems and applications. OpenVAS can be used to perform a variety of scans, including port scans, version scans, OS detection scans, and vulnerability scans.
Vulnerability Identification
Vulnerability identification is a critical component of the scanning and enumeration phase of penetration testing. The goal of vulnerability identification is to identify, evaluate, and assess the potential security weaknesses and vulnerabilities in the target system, network, or device that can be exploited by an attacker. After identification of the potential security weaknesses and vulnerabilities, the next step is to verify the existence of these vulnerabilities and evaluate their impact on the target system, network, or device. This can be done using various techniques, such as manual testing, exploitation, and automated testing tools.
The identification and assessment process typically involves evaluating the impact of a vulnerability on the target system, network, or device. This can include determining the potential consequences of a successful attack, such as unauthorized access, data theft, or system downtime. The assessment process may also involve determining the likelihood of an attack, such as the ease of exploiting a vulnerability or the availability of exploits in the public domain.
Importance of Scanning and Enumeration in Penetration Testing
Scanning and enumeration are essential steps in a penetration test as they provide valuable information about the target system, network, or device and help identify potential security weaknesses and vulnerabilities. Some of the key reasons why scanning and enumeration are important in penetration testing are:
-
Information Gathering:
Scanning and enumeration provide a wealth of information about the target system, network, or device, including open ports and services, operating systems, network configurations, and user accounts. This information can be used to identify potential attack vectors and security weaknesses. -
Vulnerability Identification:
Scanning and enumeration tools can identify known vulnerabilities in the target system, network, or device, which can be used to prioritize and address the most critical vulnerabilities first. -
Threat Intelligence:
Scanning and enumeration can also provide valuable intelligence about the threat landscape, including the types of threats and attack methods that are being used in the target environment. -
Evidence Collection:
Scanning and enumeration can also provide valuable evidence that can be used to support the findings of a penetration test, including proof of vulnerabilities and attack methods.
Conclusion
- Scanning and enumeration are critical components of penetration testing, which helps identify security vulnerabilities and weaknesses in a system, network, or device.
- There are several types of scans and enumeration techniques, including network and port scans, vulnerability scans, version scans, user enumeration, system enumeration, and OS detection scans.
- Several scanning and enumeration tools such as Nmap, Nessus, and OpenVas are used to gather information about a target.
- Vulnerability identification is the process of discovering security weaknesses and vulnerabilities in a system, network, or device. Various techniques such as manual testing, exploitation, and automated testing tools are used to identify and assess these vulnerabilities.
- Scanning and enumeration are important aspects of an organization's security measures, as they help identify and prioritize security weaknesses and vulnerabilities in a system, network, or device.
