Enumerating SSH with Nmap
Overview
This article aims to provide an in-depth understanding of how to use the Nmap tool to enumerate Secure Shell (SSH) services. The article will cover the basics of SSH and how it works, as well as the various options and commands available in Nmap for enumerating SSH protocol. The article will also provide examples and step-by-step instructions for using Nmap to enumerate SSH protocol on a target network.
Introduction
In this article, we will explore how to use Nmap to enumerate SSH servers on a network. We will cover the basics of SSH and what is Nmap, and provide examples of uses of Nmap to perform basic and advanced enumeration tasks on SSH servers, including version detection, user account enumeration, and brute-force password attacks. We will also discuss best practices for securing SSH configurations and protecting against SSH enumeration and brute-force attacks.
SSH Protocol
The Secure Shell (SSH) protocol is a widely used protocol for secure communication over an unsecured network. It provides encrypted communication for authentication and data transmission, making it an essential tool for remote access to servers. SSH is typically used to log into a remote machine and execute commands, but it also supports tunnelling, forwarding TCP ports, and transferring files.
The SSH protocol uses public-key cryptography for authentication and symmetric key cryptography for data encryption. When a client connects to an SSH server, the server provides its public key, which the client then uses to verify the authenticity of the server. If the client is satisfied that the server is authentic, it generates a symmetric key that is used to encrypt all subsequent communication between the client and server. This process provides a secure and encrypted communication channel, protecting the data and authentication credentials transmitted over the network.
Basic Enumeration with Nmap
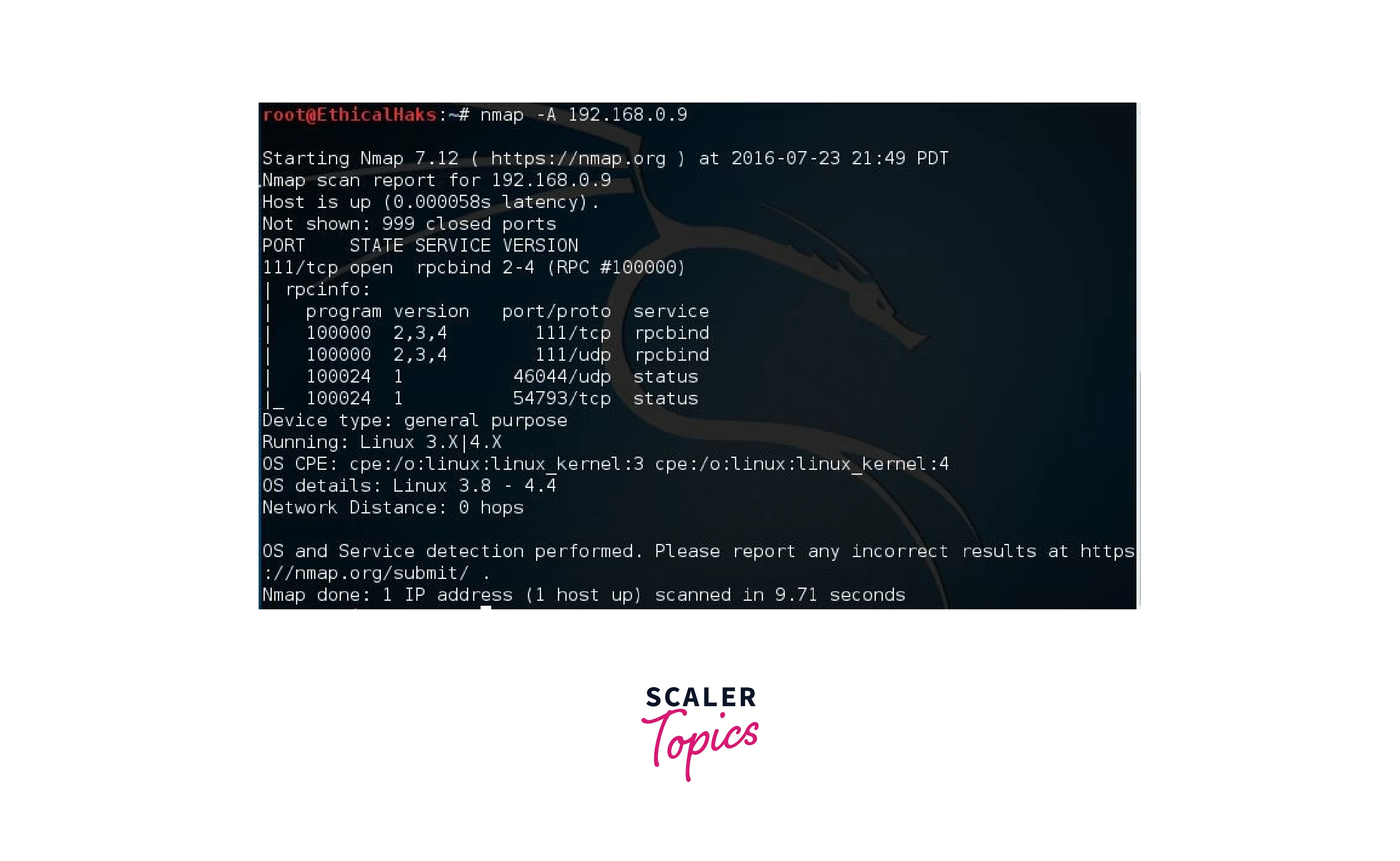
Basic enumeration with Nmap refers to the process of using Nmap to gather information about a target network or host. This process can include identifying the operating system, open ports, and running services on a target host. To perform basic enumeration, Nmap uses a variety of techniques such as sending packets to specific ports and analyzing the response. These techniques allow Nmap to determine the operating system, version, and patch level of the target host, as well as the type of services running on open ports.
Basic Commands and Options for Enumerating
Basic enumeration can be performed by running a simple command, such as "nmap [target IP address]". This command will perform a basic scan of the target IP address and return information such as open ports and the operating system.
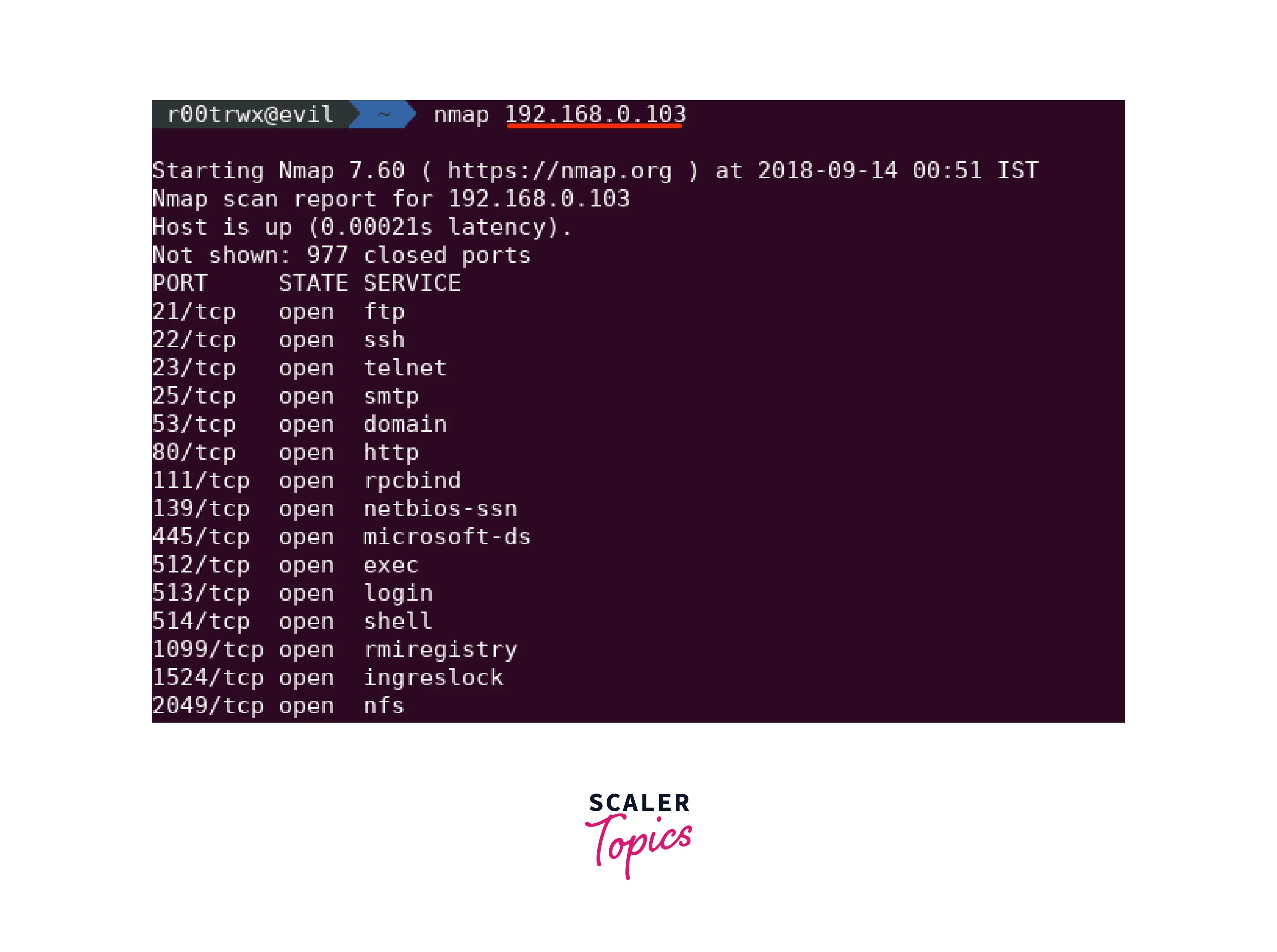
Additionally, Nmap offers a variety of options and flags that can be used to customize and fine-tune the information gathered during basic enumeration. For example, the "-sV" flag can be used to enable version detection, which can provide more detailed information about the services running on open ports.
Explanation of How to Use Nmap to Perform Basic SSH Enumeration
SSH enumeration is the process of identifying and gathering information about an SSH server on a target network. Nmap, a powerful network exploration and security auditing tool, can be used to perform this task.
The basic command for performing an SSH enumeration with Nmap is:
nmap -sV -p 22 [target host]
This command tells Nmap to perform a version scan (-sV) on port 22, which is the default port for SSH. The [target host] can be a hostname or IP address.
Another useful option for SSH enumeration is the -A option, which enables OS detection, version detection, script scanning, and traceroute. This option can provide more detailed information about the target host and its SSH service:
nmap -sV -p 22 -A [target host]
Additionally, Nmap also allows users to specify a specific SSH script to run during the enumeration process. To run a specific script, the -sC option can be used. For example, to run the ssh-brute script, which checks for brute force attacks on SSH, the following command can be used:
nmap -sV -p 22 --script ssh-brute [target host]
These are just a few examples of the basic commands and options that can be used for SSH enumeration with Nmap. There are many other options and scripts available that can provide even more information about the target SSH service. By using Nmap, a cybersecurity professional can quickly and easily gather information about SSH services on a target network and identify any potential vulnerabilities.
Examples of Common Usage Scenarios for Basic SSH Enumeration
Examples of common usage scenarios for basic SSH enumeration with Nmap include:
- Identifying open SSH services on a target network: This can be done by running a basic port scan (nmap -sV -p 22 [target]) on the target network, which will identify all hosts that have an open TCP port 22 (SSH).
- Checking for brute force attacks on SSH: By running the nmap --script=ssh-brute [target] command, one can check if the target SSH servers are being targeted by brute force attacks.
- Identifying vulnerable SSH servers: By running the nmap -sV --script=ssh-vuln-cve* [target] command, one can identify if the target servers are vulnerable to any known SSH-related vulnerabilities.
- Exporting the results of the scan: By using the -oX or -oN options, one can export the results of the scan to an XML or normal text file respectively.
Advanced Enumeration with Nmap for SSH
Advanced enumeration with Nmap for SSH involves using advanced options and commands to gather more detailed information about the target SSH server. This can include using Nmap's scripting engine to run specific scripts that are designed to enumerate SSH servers. Some examples of advanced enumeration techniques include:
Using Nmap's version detection feature to fingerprint the specific version of the SSH server software in use. This can help identify vulnerabilities that are specific to that version of the software.
nmap -sV <target IP or hostname> -p 22
Using Nmap's script engine to run scripts that are designed to enumerate specific information about the SSH server, such as the directory listing of the server or the users that are currently logged in.
nmap -sV --script ssh2-enum-algos.nse <target-IP>
Using Nmap's OS detection feature to fingerprint the operating system of the target machine. This can help identify potential vulnerabilities that are specific to that operating system.
nmap -O [target IP address]
Using Nmap's service version detection feature to fingerprint the version of the SSH service running on the target machine. This can help identify vulnerabilities that are specific to that version of the service.
nmap -sV -p 22 target_ip
Using Nmap's script engine to run other scripts that are designed to enumerate other services running on the target machine, such as HTTP or SMB.
nmap -sV --script=http-enum.nse,smb-enum-users.nse TARGET_IP
Examples of Advanced Usage Scenarios for Enumerating SSH with Nmap
Here are a few examples of advanced usage scenarios for enumerating SSH with Nmap:
1. Detecting and Fingerprinting SSH Servers
Nmap can be used to scan a network for open SSH ports and fingerprint the server software in use, allowing security professionals to identify potential vulnerabilities and misconfigurations. When performing an enumeration of SSH servers with Nmap, one of the first steps is to detect and fingerprint the servers. This is done by sending a series of probes and analyzing the responses to determine the type and version of the server software.
2. Brute-forcing SSH Login Credentials
Nmap can also be used in conjunction with other tools, such as Hydra, to perform a brute-force attack against SSH servers to identify weak login credentials. Brute-forcing SSH login credentials involve attempting to log in to an SSH server using a list of commonly used username and password combinations. This can be done using specialized tools such as "Hydra" or "Medusa" which automates the process of trying different combinations of credentials.
3. Detecting SSH Servers Behind Firewalls
SSH servers can be hidden behind firewalls, making them harder to detect. However, several techniques can be used to detect SSH servers that are behind firewalls. The common method is to use Nmap's " -sV" option to perform a version scan of the target network. This option sends probes to the target host to determine the version of the services running on the host. It can also identify open ports and the services running on them.
4. Checking for Weak SSH Configuration
Nmap can be used to scan a network for SSH servers and check their configuration for weak settings. This can include checking for the use of outdated or vulnerable encryption algorithms, weak authentication methods, and the absence of proper hardening measures, such as disabling root login or limiting the use of password-based authentication.
Techniques for Identifying Vulnerabilities in SSH
There are several techniques for identifying vulnerabilities in a system or network using SSH. Some of the most common techniques include:
- Vulnerability scanning: This technique involves using automated tools to scan a system or network for known vulnerabilities related to SSH. These tools typically check for missing patches, misconfigurations, and other issues that could be exploited by an attacker.
- Penetration testing: This technique involves simulating an attack on a system or network using SSH to identify vulnerabilities and assess the effectiveness of security controls. Penetration testing can be performed manually or with the use of automated tools.
- Source code analysis: This technique involves reviewing the source code of a software application that uses SSH to identify vulnerabilities that could be exploited by an attacker. This can be done manually or with the use of automated tools.
- Social engineering: This technique involves tricking individuals into revealing sensitive information or performing actions that could compromise security related to SSH. Social engineering can be performed through phishing emails, phone calls, or in-person interactions.
- Network traffic analysis: This technique involves monitoring network traffic related to SSH to identify unusual activity that could indicate a security incident. This can be done with the use of network security monitoring tools.
- Physical security assessment: This technique involves evaluating the physical security controls of a facility to identify vulnerabilities that could be exploited by an attacker related to SSH. This can include evaluating access controls, cameras, and other physical security measures.
Conclusion
- SSH is a widely used network protocol for secure communication between computers on a network.
- There are various techniques that can be used to identify vulnerabilities in a system or network using SSH, such as vulnerability scanning, penetration testing, source code analysis, social engineering, network traffic analysis, and physical security assessment.
- By using these techniques, one can assess the security of a system or network that uses SSH and take appropriate measures to mitigate any identified vulnerabilities.
