Staged vs Non-staged Payloads in Cybersecurity
Overview
As we all know, Metasploit has a wide range of payloads. Those payloads are available in several varieties and vary according to the platform. There are two main "categories" of those sorts, each with a significant distinction that is frequently misunderstood. They have staged payloads and stageless payloads.
The objective of this article is to discuss how these two and other types of payloads differ from one another. To determine when each type should be used, let's quickly go over the available various payload types.
Introduction
Knowing about malware payloads and how to stop them may make your company safer. An executable or program that talks back to a cyber attacker over a communication channel is referred to as a payload. payload management is the cornerstone of the threat actor's malevolent campaign, in their eyes. A threat actor can enter your network directly through a payload, keep that line of communication open, and use it to carry out their illegal goals and objectives, depending on the type and functionality of the payload.
The majority of cyber attacks employ payloads, however, others employ payload-less attacks, such as phishing campaigns that do not contain dangerous links or malware but instead depend on more advanced deception like spoofing to deceive their targets.
What are Payloads?
The payload, in terms of computer security, is the portion of the private user text that could also include malware, such as worms or viruses, which carry out destructive activity, such as deleting data, sending spam, or encrypting data. Along with the payload, such malware frequently contains overhead code intended to spread itself or prevent detection.
In other terms, a payload is a program that runs when hackers take advantage of a vulnerability. Typically, it contains a small number of commands that will be executed on the targeted operating system to steal data and perform other destructive activities (such as key-loggers).
Types of Payloads
Metasploit has a wide range of payloads, each of which serves a specific purpose inside the framework. Let's quickly review the different payload categories to get a sense of when each category should be applied.
Inline (Non-Staged) Payloads
a single payload that includes the exploit and complete shell code necessary to complete the chosen task. Due to their all-encompassing nature, inline payloads are by definition more stable than their alternatives. Some exploits, however, are unable to handle the increased size of these payloads.
Staged Payloads
Stage payloads collaborate with stager payloads to carry out a particular task. To execute the staged payload on the remote host, a stager creates a communication channel between the attacker and the target.
Meterpreter Payloads
Meterpreter, the abbreviation for Meta-Interpreter, is a sophisticated, multifaceted payload that functions by injecting dll filFinding the Meterpreter using traditional forensic methods is very challenging ods because it only exists in the remote host's memory and leaves no traces on the hard drive. The development of Meterpreter is very strong, and it is constantly changing. Scripts and plugins can be loaded and unloaded dynamically as needed.
PassiveX Payload
PassiveX is a payload that can assist in getting around restrictive outbound firewalls. It accomplishes this by creating a hidden instance of Internet Explorer using an ActiveX control. It communicates with the attacker by sending and receiving HTTP requests and responses using the new ActiveX control.
NoNX
The NX (No eXecute) bit is a CPU feature that prevents code from executing in specific areas of memory. NX is implemented in Windows as Data Execution Prevention (DEP). The Metasploit NoNX payloads are made to bypass DEP.
Ord Payloads
Ordinal payloads are based on the Windows stager and have specific benefits and drawbacks. The advantages include the fact that it functions without the explicit definition of a return address on every version and language of Windows going back to Windows 9x. They are also remarkably tiny in size. However, they are not the standard option due to two very specific drawbacks. The first is that it depends on the loaded state of ws2_32.dll in the target process before exploitation. The second is that compared to the other stages, it is a little less stable.
IPv6 Payloads
As the name suggests, the Metasploit IPv6 payloads are designed to operate over IPv6 networks. An IPv6 packet consists of user data as the payload and control data for addressing and routing. The payload of an IPv6 packet normally consists of a datagram or segment of the transport layer protocol, but it can also contain information for the internet layer (such as ICMPv6) or link layer (such as OSPF).
Reflective DLL Injection
Reflective DLL Injection is a method that involves injecting a staged payload into a compromised host process that is running in memory and never making contact with the host hard drive. Reflective DLL injection is used by the Meterpreter and VNC payloads, respectively. More information is available from Stephen Fewer, the inventor of the reflective DLL injection method.
Staged vs Non-staged Payloads
The easiest payload type to comprehend is a stageless/Non-staged payload since it comes complete with all the information required to obtain a reverse shell callback. As a result, in comparison to a staged, the file size is often significantly higher and the software is more complicated. You may catch this payload by keeping an eye on a raw socket. A listener may be made using Netcat, Python, Socat, etc. Windows/meterpreter_reverse_tcp serves as the stageless version of the staged payload.
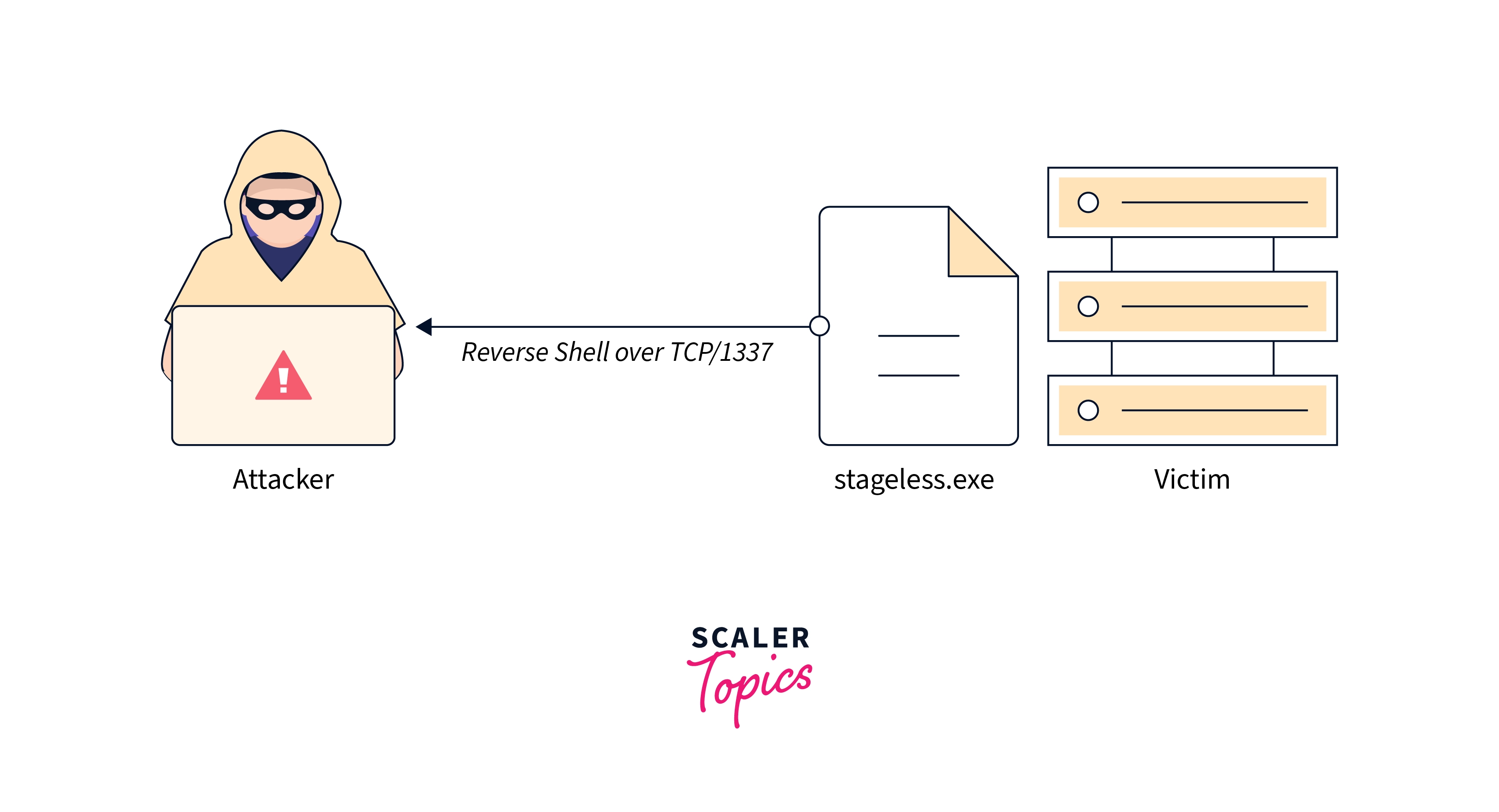
In the diagram, our aforementioned victim is duped into starting stageless.exe, and an attacker receives a callback to their Netcat listener through TCP/1337.
A staged payload is a little more challenging since it must go out to another device (the original executable is commonly referred to as a "Dropper") to obtain a second "Stage," which includes a more comprehensive and full application. This might occasionally just be a shellcode or it could occasionally be another module, like Mimikatz. It needs a "Hander" because of the more complicated contact. This is handled by the exploit/multi/handler module of the Metasploit Framework. Metasploit's standard staged payload is windows/meterpreter/reverse_tcp.

In the illustration above, our victim is persuaded to run the dropper, which then beacons out to our C2 server to get a second stage. This second stage is then injected and performed in memory, which causes a reverse shell callback to be triggered.
Creating and Using Payloads
Msfvenom is a payload-generating and encoding system. On June 8, 2015, it took the place of msfpayload and msfencode.
To begin using msfvenom, please review the parameters it supports:
Generating Payload
There are two flags (-p and -f) that you must specify to construct a payload:
-
The -p parameter: indicates the payload to produce.
You may perform the following to find out what payloads Framework offers:
The "-" character can also be used with the -p flag to accept a special payload:
-
The -f parameter: specifies the payload's format.
Example of Syntax:
You can look at the following information to discover whether formats are supported:
Typically, you will generally utilize msfvenom in the following manner:
Encoding Payload
When you use the -b flag (the bad char flag), the encoding functionality will be enabled by default. In other circumstances, you must employ the -e flag as in:
Use the -l flag to see what encoders are supported:
Using the -i flag, the payload can also be encoded several times. Though encoding isn't intended to be utilized as a true AV evasion method, sometimes extra iterations may aid in escaping antivirus:
Avoiding Bad Characters
The -b flag can be used to exclude certain characters from the payload. When this option is selected, msfvenom will automatically locate an appropriate encoder to encode the payload:
Using Custom Template
The msf/data/templates directory contains templates that are used by default by msfvenom. You may use the -x flag to select your own by doing something like this:
Chaining msfvenom Output
To layer on numerous encodings, the primitive msfpayload and msfencode tools were frequently chained together. Msfvenom may also accomplish this:
Executing Payloads
Attackers must devise a method of delivering the malicious DDoS payload to the target PC. They spread the payload virus using two major methods: social engineering attacks and DNS hijacking. A payload that is placed behind your system is likely to remain inactive until it is activated. Attackers have a variety of options for carrying out the payload and weakening a system's security.
The following are a few typical ways to execute a payload.
- Using deception to launch an executable file: For example, a person could download an installation setup file from a website that they think contains some software that is being sold illegally, but when they run the file for installation, it turns out to be malicious and introduces an infected payload into their system.
- Setting up certain behavioral conditions: This strategy works by putting some logical requirements in place. For instance, a worker might insert a malicious payload into his company's network with the intent that it will run while he is not on the clock. Therefore, there are a few requirements that must be satisfied before such payloads may access the network.
- Launching particular non-executable files: Some non-executable files may even have a payload hidden inside of them. For example, an image file with the.png extension might include a payload that is executed when the image is launched.
Evasion Techniques
You may use all the crucial security hygiene advice, which naturally includes staying away from mindlessly clicking email attachments and links. Regular vulnerability patches and penetration testing are also important.
Additionally, there are a wide variety of distribution and execution methods and approaches for these payloads, and no particular mitigation strategy exists.
When downloading files or receiving any data over the air, security safeguards should be implemented in addition to being cautious of phishing scams and other social engineering and amplifying attacks. Installing trustworthy and legitimate anti-virus software on your PC and doing routine file system checks are two of the finest ways for consumers to stop an attack from starting on their system.
Users must take care to avoid disclosing or transferring sensitive information over their network connection since doing so opens the door for hackers to breach network security.
It is crucial for your company you keep your APIs safe. It means that programmers shouldn't utilize fad-driven frameworks that might cause security problems if misconfigured or improperly implemented, but rather stick to proven technologies they are familiar with.
Conclusion
- Simply said, a harmful payload is a component of the attack that harms the target.
- Malware payload may be found in all attack vectors, including worms, viruses, and malware.
- These malicious payloads may be discovered in email attachments, URLs, and other types of transmission methods.
- Here are some instances of how these payloads may be employed in cyberattacks and the harm they can do to users: data theft, activity tracking, advertising display, changing or deleting files, running background processes, and downloading fresh files.
