Vulnerabilities in Cyber Security
Overview
Vulnerabilities in cyber security have become a threat to the protective measures of systems and networks leaving them susceptible to exploitation by cybercriminals. The impact of these vulnerabilities can be far-reaching, encompassing financial losses, reputational damage, and potential legal effects on individuals, businesses, and governments alike. Let us explore into the world of vulnerabilities, exploring their effects on day-to-day operations and the digital security to mitigate them.
Introduction to Vulnerabilities in Cyber Security
Vulnerabilities in cyber security refer to weaknesses or flaws in a system's defenses that can be exploited by malicious actors. These vulnerabilities can exist in various forms, from software bugs and misconfigurations to human error and social engineering tactics. For companies, the impact of these vulnerabilities can be significant and multifaceted. Financial losses due to data breaches, theft of intellectual property, or disruptions in business operations can have immediate and lasting consequences.
The Ever-Evolving Landscape of Vulnerabilities:
The landscape of vulnerabilities in cyber security is dynamic and diverse, with a wide range of threats constantly evolving to exploit weaknesses in digital defenses. The rapid pace of innovation often outpaces security measures, leaving systems exposed to unforeseen risks. Understanding these various vulnerabilities is crucial for implementing effective security measures. Here are some of the prominent vulnerabilities:
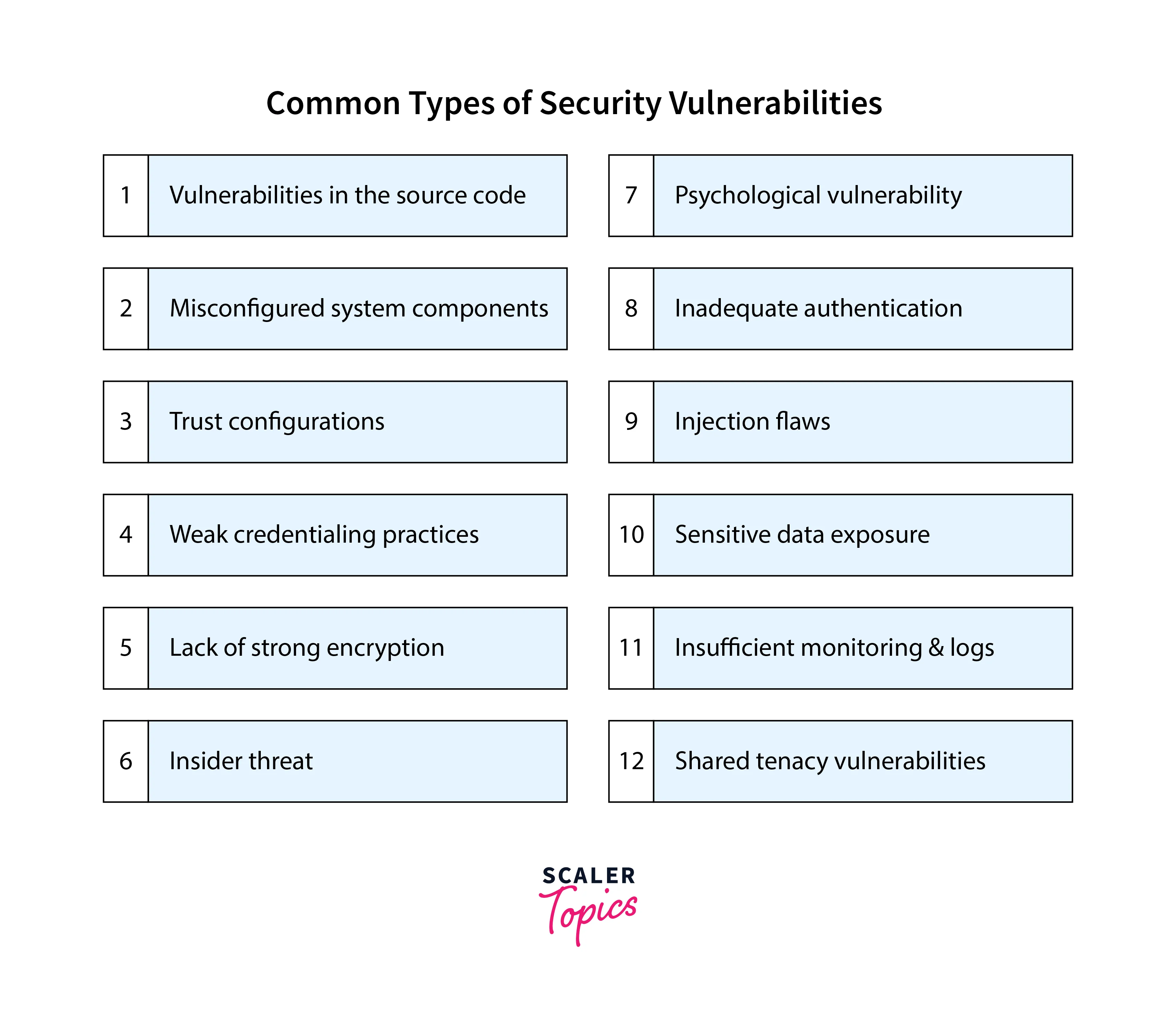
- Phishing Attacks include deceptive emails that trick individuals into revealing sensitive information.
- Ransomware is malicious software that encrypts files or systems, demanding a ransom for access, potentially causing severe data loss and operational disruption.
- Supply Chain Attacks exploits vulnerabilities in a company's network of suppliers and service providers, gaining unauthorized access.
- Artificial Intelligence and Machine Learning Attacks involve attempts to manipulate or deceive AI algorithms, potentially leading to biased outcomes or compromised decision-making.
- Nation-State Cyber Warfare are government-backed cyber operations for intelligence gathering or infrastructure disruption, with significant geopolitical implications.
- Insider Threats are threats from within an organization, where individuals misuse their access or privileges, stemming from malicious intent, negligence, or mistakes.
- Zero-Day Vulnerabilities are undisclosed and unpatched software vulnerabilities exploited by attackers, with no immediate defense available.
- Social Engineering Attacks rely on psychological manipulation to trick individuals into divulging sensitive information, employing tactics like pretexting and baiting.
- Malware Attacks include various malicious software, designed to infiltrate and compromise systems, often for data theft or causing damage.
How Vulnerabilities Are Assessed
Vulnerability assessment involves systematically identifying, classifying, and prioritizing potential weaknesses in a system or network. Let us explore some common tools and methodologies used to conduct vulnerability assessments:

Nmap
Nmap is an open-source network scanner that is widely used for vulnerability assessment. It helps in discovering hosts and services on a network, as well as finding open ports and their associated services.
Usage:
A basic nmap scan for vulnerabilities might involve running the following command:
This command scans all 65,535 ports on the target host, using aggressive scanning and verbose output options.
OpenVAS (Open Vulnerability Assessment System)
A comprehensive vulnerability scanning tool that provides a database of known vulnerabilities, allowing for effective assessment and management of security risks.
Usage:
OpenVAS can be accessed via a web interface. After setting up the tool, users can initiate scans on target hosts and receive detailed reports outlining identified vulnerabilities.
Nexpose
Nexpose, now known as InsightVM, is a vulnerability management solution that provides a centralized platform for vulnerability assessment and risk prioritization.
Usage:
Users can configure Nexpose to perform scheduled scans on target networks. The tool then generates reports that categorize vulnerabilities based on severity, allowing organizations to focus on high-priority issues.
Burp Suite
Burp Suite is a popular web vulnerability scanner used for assessing the security of web applications. It identifies common web application vulnerabilities such as SQL injection, cross-site scripting (XSS), and more.
Usage:
Burp Suite is an interactive tool. Security professionals use it to manually test web applications by sending various types of requests and analyzing the responses for potential vulnerabilities.
Metasploit
Metasploit is a widely-used penetration testing framework that includes a robust vulnerability scanner. It aids in identifying vulnerabilities and provides tools to exploit them for testing purposes.
Usage:
Metasploit provides a range of modules for vulnerability scanning. Users can select the appropriate module based on the target system and initiate scans to identify potential weaknesses.
OWASP ZAP (Zed Attack Proxy)
OWASP ZAP is a free and open-source security testing tool used for finding vulnerabilities in web applications. It's particularly adept at identifying common vulnerabilities like injection attacks, broken authentication, and cross-site request forgery (CSRF).
Usage:
Users can set up OWASP ZAP as a proxy server and configure their web browser to route traffic through it. ZAP intercepts and analyzes web requests and responses, flagging potential vulnerabilities.
Mitigating Vulnerabilities
Mitigation refers to the proactive measures and strategies put in place to reduce the likelihood of a security breach or the potential impact of a security incident. Mitigating vulnerabilities requires a combination of technical measures, user awareness, and a proactive security posture. Here are some key strategies to effectively address vulnerabilities:
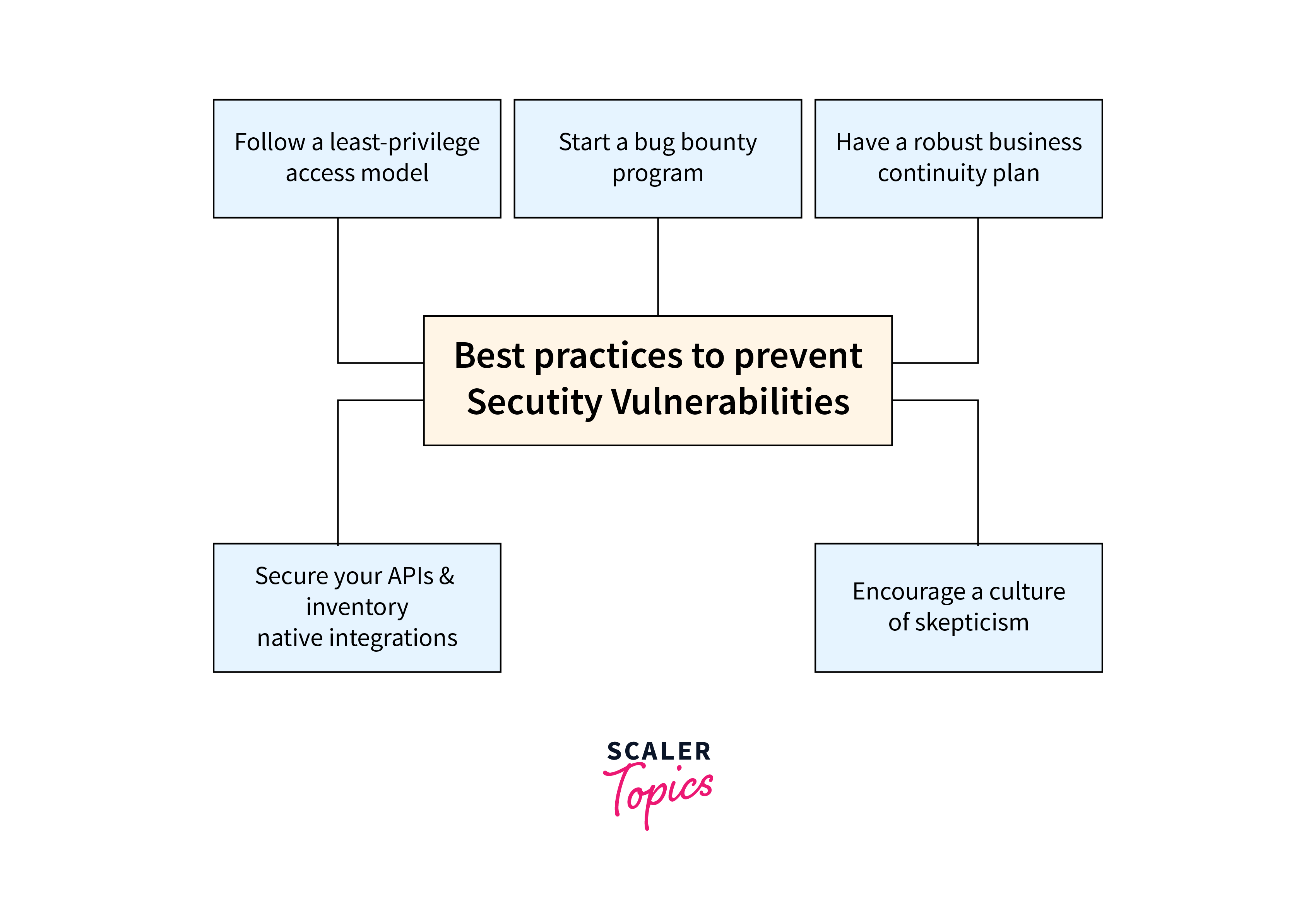
- Patch Management:
Regularly updating software with the latest security patches is crucial to fix known vulnerabilities. Automated systems streamline this process for timely updates. - Vulnerability Scanning:
Regular scans and assessment tools help identify and prioritize weaknesses, allowing organizations to strengthen their defenses. - Security Awareness Training:
Educating employees on cyber threats, best practices, and strong passwords reduces the risk of falling victim to social engineering attacks. - Access Control:
Implementing strict access controls and least privilege principles limits exposure to sensitive information, ensuring it's only accessible to those who need it. - Incident Response Planning:
Having a well-defined incident response plan enables organizations to react immediatly and effectively in the event of a security breach, minimizing potential damage. - Endpoint Security Defenses:
Safeguarding individual devices such as laptops, desktops, and mobile with up-to-date security measures creates a critical layer of defense against threats. - Security Controls:
Measures and safeguards like access controls, encryption protocols, and intrusion detection systems protect information systems from unauthorized access or alterations, significantly reducing vulnerability risks.
Conclusion
- Vulnerabilities in cyber security are weaknesses in a system's defenses that can be exploited by malicious actors, containing software bugs, misconfigurations, and human error.
- The ever-evolving landscape of vulnerabilities makes it necessary for a proactive and vigilant approach to security, as cyber threats continue to adapt and evolve.
- Vulnerability assessment involves systematically identifying, evaluating, and prioritizing potential weaknesses in a system or network, employing tools like Nmap scans for vulnerabilities.
- Common vulnerabilities include phishing attacks, ransomware, supply chain attacks, IoT vulnerabilities, AI/ML attacks, and nation-state cyber warfare, alongside others like insider threats and zero-day vulnerabilities.
- Mitigation involves proactive measures to reduce the likelihood of a security breach. Mitigating vulnerabilities requires a multifaceted approach, including patch management, regular vulnerability scanning, and the deployment of endpoint security defenses.
- Implementing security controls, access controls, and incident response planning are crucial components of a comprehensive security strategy. Security awareness training and data encryption add layers of protection to maintain a strong security posture.
