What are Shells?
Overview
The article provides a comprehensive overview of the topic of shells including reverse and bind shells. It starts by defining what shells are and their importance as a command-line interface. The article then explains the differences between Reverse shells and Bind shells, including their use cases and when to use them.
Additionally, we will cover step-by-step explanations for creating both Reverse and Bind shells, including the necessary commands and tools required. The article also covers important aspects of detecting and preventing these shells from being used for malicious purposes, including regular monitoring of network traffic, log analysis, firewall configuration, patch management, and user education.
Introduction
A shell is a user interface that provides access to an operating system's services and allows users to execute commands, run scripts, and perform various tasks. Shells are the primary way for users to interact with the underlying system and execute programs, control processes, and manage files. There are many different types of shells available, including the Bourne shell (sh), the C shell (csh), and the Korn shell (ksh).
In addition, to reverse shells and bind shells, other types of shells serve different purposes. For example, there are login shells, which are used to authenticate users and provide them with a user interface, and non-login shells, which are used to execute commands and run scripts without requiring a user to log in.
The shell provides users with a rich environment, including variables, functions, pipes, redirection, and job control. The shell also provides a scripting language that allows users to automate tasks, such as system administration and data processing. Scripts written in shell languages can be used to automate complex tasks, such as setting up a network, managing software installations, and backing up files.
In a networking context, shells can be used to remotely manage servers and other networked devices. This is done by establishing a shell connection over the network, either through a reverse shell or a bind shell. Network administrators can use shells to perform tasks such as monitoring system performance, updating software, and managing configurations.
Reverse Shells
A reverse shell is a type of shell that establishes a connection from a remote machine to a target machine. The remote machine sends a request to connect to the target machine, and when the connection is established, the remote machine has control over the target system. Reverse shells are often used by attackers for malicious purposes, such as gaining unauthorized access to a target system.
In a reverse shell, the attacker creates a shell on the remote machine and sends a request to connect to the target machine. When the connection is established, the attacker has control over the target system and can execute commands, run scripts, and perform various tasks. This allows the attacker to take control of the target system without the need for physical access.
Reverse shells are typically used in combination with other types of attacks, such as malware infections or vulnerabilities in web applications. The attacker may use a reverse shell to gain access to sensitive information, such as passwords and confidential data, or to perform actions that compromise the security of the target system, such as installing malware or modifying system configurations.
To prevent reverse shell attacks, it is important to implement secure network practices, such as firewalls, intrusion detection systems, and anti-malware solutions. Additionally, it is important to keep software and systems up to date with the latest security patches and to educate users about the dangers of reverse shell attacks. With the proper precautions in place, it is possible to reduce the risk of reverse shell attacks and protect sensitive information and systems from unauthorized access.
Bind Shells
A bind shell is a type of shell that listens on a specific port and waits for incoming connections. When a connection is established, the bind shell provides a shell interface to the remote machine, allowing the user to execute commands on the target system. This type of shell is commonly used for legitimate purposes, such as remote administration. The user can connect to the target machine from a remote location and perform tasks, just as if they were sitting at the console.
Bind shells are often used by system administrators to manage servers, networked devices, and other systems from a remote location. By connecting to the bind shell, the administrator can access the target system's shell and perform tasks, such as monitoring system performance, updating software, and managing configurations.
Bind shells can be set up using a variety of methods, including network protocols such as Telnet or SSH. To set up a bind shell, the administrator must specify the port to listen on and configure the firewall to allow incoming connections. Once the bind shell is set up, the administrator can connect to the target system from a remote location and perform tasks as if they were sitting at the console.
While bind shells can be useful for remote administration, they also present a security risk. If the bind shell is not properly secured, an attacker could gain unauthorized access to the target system. To prevent this, it is important to secure the bind shell with strong authentication methods, such as passwords or public key authentication, and to limit access to the bind shell to trusted users.
Comparison of Reverse and Bind Shells
| Reverse Shell | Bind Shell |
|---|---|
| A type of shell where the remote machine initiates a connection to the target machine, allowing the attacker to control the target system. | A type of shell that listens on a specific port and waits for incoming connections, allowing the user to execute commands on the target system from a remote location. |
| Reverse shells are often used by attackers for malicious purposes, such as gaining unauthorized access to target systems, stealing confidential information, or installing malware. | Bind shells are often used for legitimate purposes, such as remote administration, monitoring system performance, updating software, and managing configurations. |
| In a reverse shell, the remote machine initiates the connection and sends a request to connect to the target machine. | In a bind shell, the target machine listens for incoming connections and provides a shell interface when a connection is established. |
| The remote machine establishes a connection with the target machine and has control over the target system. | The remote machine establishes a connection with the target machine and has access to the target system's shell. |
| Reverse shells can present a significant security risk if not properly secured, as attackers can gain unauthorized access to the target system. | Bind shells can also present a security risk if not properly secured, as unauthorized users may be able to connect and execute commands on the target system. |
| To prevent reverse shell attacks, it is important to implement secure network practices, such as firewalls, intrusion detection systems, and anti-malware solutions. It is also important to keep software and systems up to date and educate users about the dangers of reverse shells. | To prevent unauthorized access to bind shells, it is important to secure the bind shell with strong authentication methods, such as passwords or public key authentication, and limit access to trusted users. Additionally, it is important to regularly monitor the bind shell for unauthorized activity. |
When to Use Reverse Shell When to use Bind Shell?
In this section let us discuss when to use the reverse shell and when to use the bind shell:
When to Use Reverse Shell?
-
Remote Access: Reverse shells are useful when remote access is required to a system that is behind a firewall or network security device. This type of shell allows the attacker to bypass firewalls and access the target system from a remote location.
-
Penetration Testing : Reverse shells can be used as a tool in penetration testing to simulate an attack scenario and assess the security of a system. This type of shell allows the tester to evaluate the security of a system and identify vulnerabilities that need to be addressed.
-
Malicious Purposes : Unfortunately, reverse shells are also used for malicious purposes, such as unauthorized access to target systems, stealing confidential information, or installing malware. It is important to understand the potential security risks associated with reverse shells and take steps to prevent unauthorized access.
When to Use Bind Shell?
-
Remote Administration : Bind shells are useful for remote administration, allowing system administrators to manage servers, networked devices, and other systems from a remote location. By connecting to the bind shell, the administrator can access the target system's shell and perform tasks, such as monitoring system performance, updating software, and managing configurations.
-
Testing and Debugging : Bind shells can be used as a tool in testing and debugging to diagnose issues and resolve problems. This type of shell allows the tester or debugger to access the target system and execute commands to gather information or perform tasks.
-
Convenient Access : Bind shells provide a convenient way for system administrators to access systems from a remote location, without having to set up VPNs or other remote access solutions. This type of shell can simplify remote administration and improve efficiency.
How to Create a Bind Shell?
A bind shell is a type of shell that allows a remote user to execute commands on a target system by connecting to a specified port. Netcat is a versatile networking tool that can be used to create a bind shell. In this section of the article, we'll walk you through the process of creating a bind shell, including the installation of Netcat, choosing a port, and executing the commands.
- Install Netcat : To get started, you need to install Netcat on your system. There are several ways to do this, including using a package manager like apt or yum, or downloading the source code and compiling it yourself.
-
Choose a Port : The next step is to choose a port to listen on. To minimize the risk of conflicts with other services, it's recommended to choose a high-numbered, unprivileged port, such as 1024 or higher.
-
Start Netcat in Listen Mode : With Netcat installed and the port chosen, you can start Netcat in Listen mode. To do this, run the following command in your terminal:
Replace the [port_number] with the port number you have chosen to listen on.
- -l (Listen): The -l option is used to tell netcat to listen for incoming connections.
- -v (Verbose): The -v option is for verbose mode, which displays information about the connections.
- -p (Port): The -p option is used to specify the port number that netcat should listen on.
- [Port Number]: This is the port number chosen in step 2, which netcat should listen on.
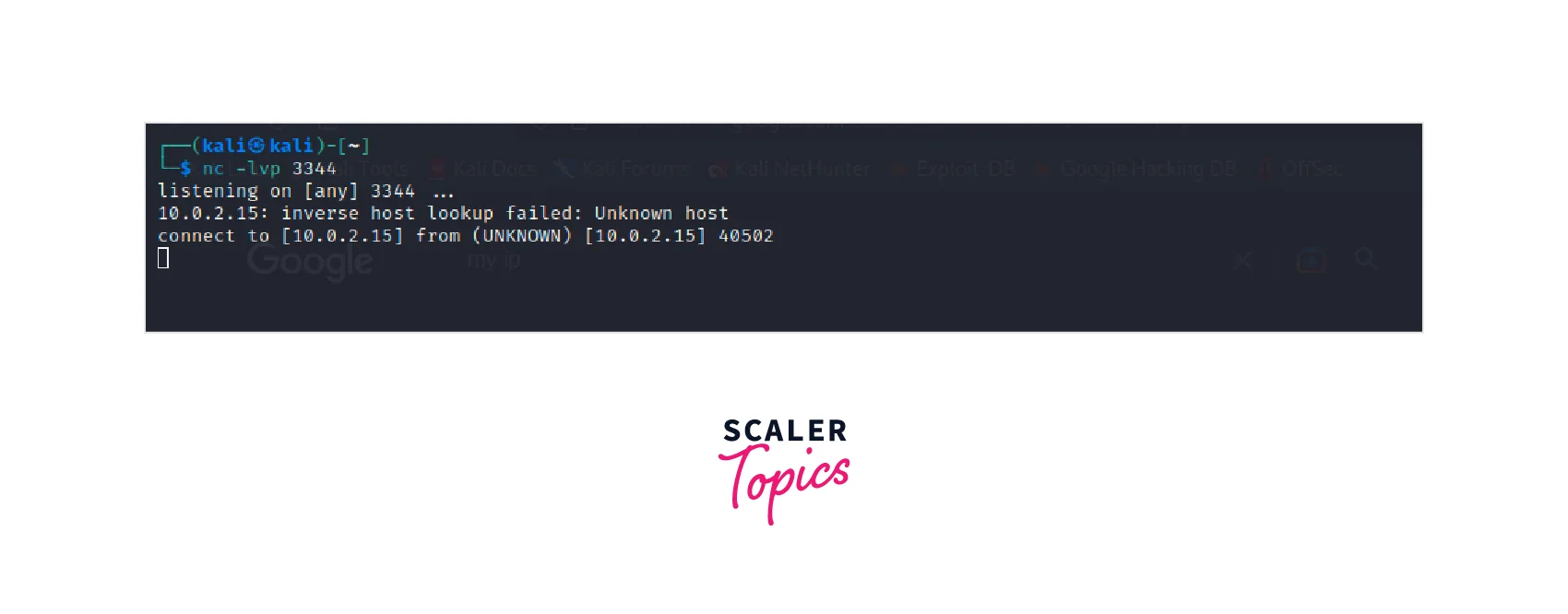
-
Connect to the Bind Shell: Now that Netcat is listening on the specified port, you can connect to the bind shell. You can use another instance of Netcat or a similar tool, such as Telnet or PuTTY, and connect to the specified port on the target system.
Replace the target machine IP and the port number
- [Target Machine IP]: This is the IP address of the machine running the netcat listener.
- [Port Number]: This is the port number chosen in step 1, which netcat should listen on.

In this image, we can observe that the connection has been successfully established.
- With these steps, you now have a functional bind shell! It's important to keep in mind the security risks associated with bind shells and take steps to prevent unauthorized access and maintain system security.
Note : It's not legal to test a website/server/device for a vulnerability without permission from the owner This example is performed on a test environment.
How to Create a Reverse Shell?
A reverse shell is a type of shell that allows a remote user to execute commands on a target system by connecting to the target system from a remote host. Netcat is a versatile networking tool that can be used to create a reverse shell. In this article, we'll walk you through the process of creating a reverse shell, including the installation of Netcat, choosing a port, and executing the commands.
- Install Netcat : To get started, you need to install Netcat on the target system. There are several ways to do this, including using a package manager like apt or yum, or downloading the source code and compiling it yourself.
-
Choose a Port : The next step is to choose a port to use for the reverse shell. To minimize the risk of conflicts with other services, it's recommended to choose a high-numbered, unprivileged port, such as 1024 or higher.
-
Start Netcat on the Target System : With Netcat installed and the port is chosen, you can start Netcat on the target system. To do this, run the following command in your terminal:
Replace <port> with the port number you have chosen to use. The -e option specifies the shell to use, in this case, /bin/bash.
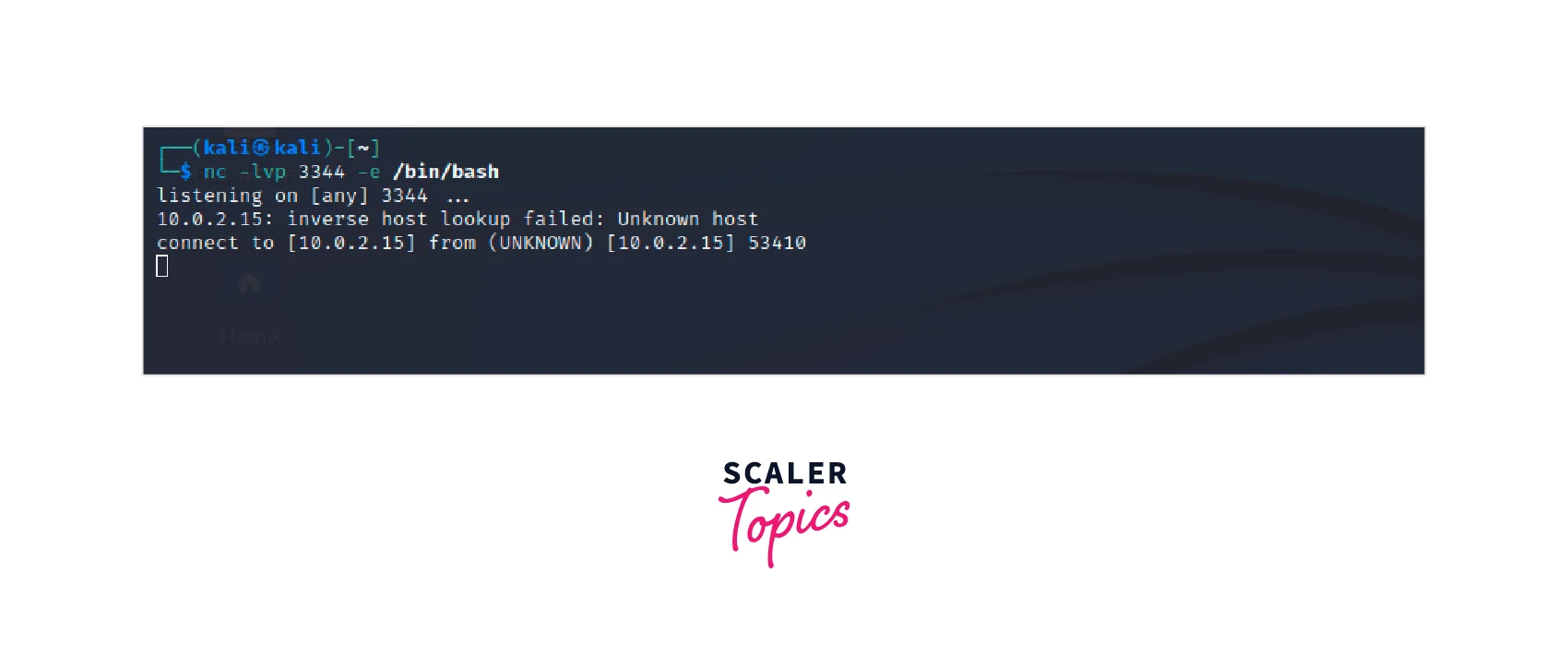
In this image, we can observe that we have set up the target system to listen on port 3344 and initiate a bash shell for the execution of commands once connected.
- Connect to the Reverse Shell : Now that Netcat is listening on the specified port on the target system, you can connect to the reverse shell from the remote host. You can use another instance of Netcat or a similar tool, such as Telnet or PuTTY, and connect to the specified port on the target system.
Replace <target_ip> with the IP address of the target system and <port> with the port number you have chosen to use.
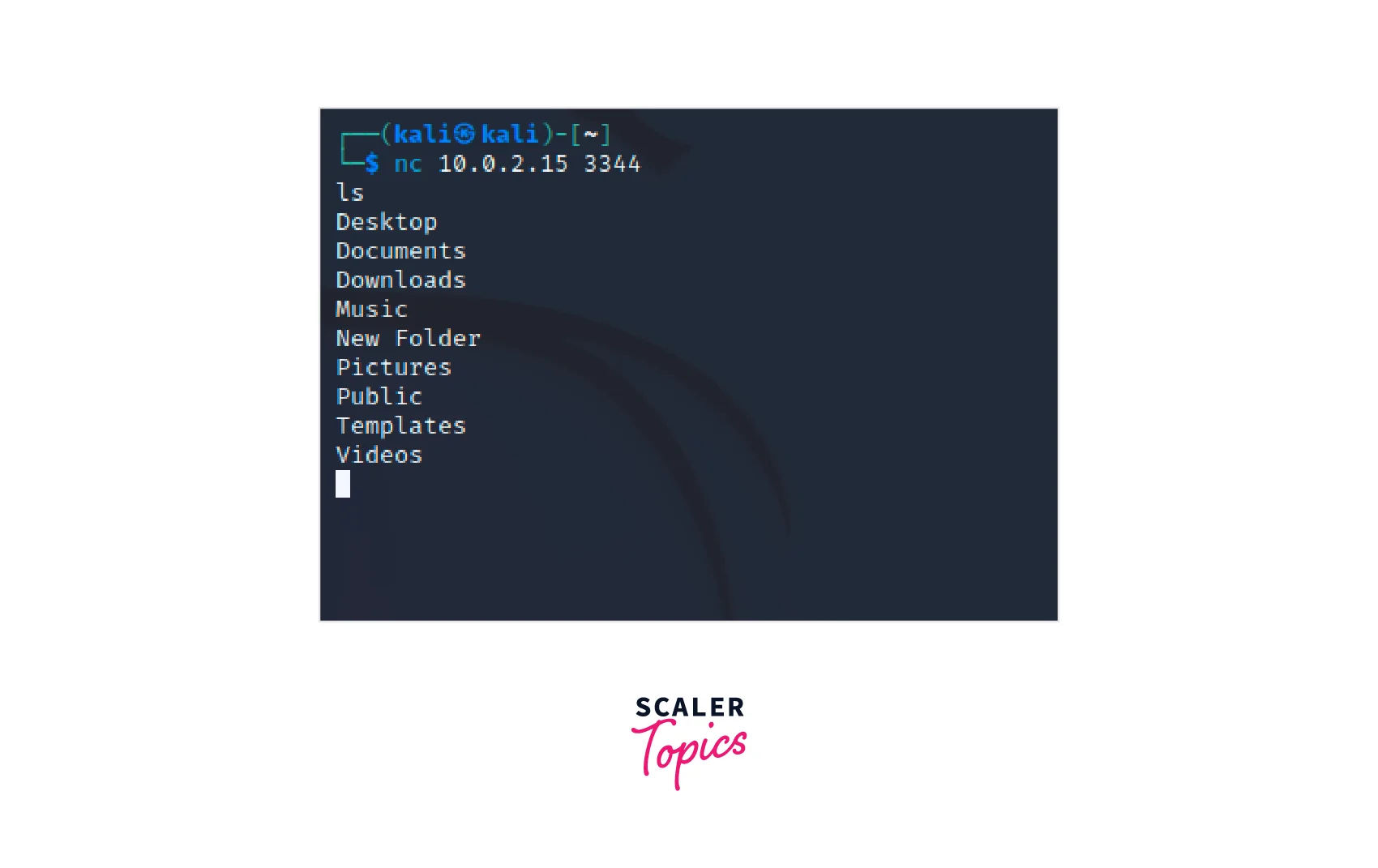
In this image, we can see the execution of the ls command after the reverse shell was set up
- With these steps, you now have a functional reverse shell! It's important to keep in mind the security risks associated with reverse shells and take steps to prevent unauthorized access and maintain system security.
Important: It's not legal to test a website/server/device for a vulnerability without permission from the owner This example is performed on a test environment.
Detection and Prevention
As reverse and bind shells can be used for malicious purposes, it's important to be aware of the steps you can take to detect and prevent them.
Detection
-
Monitoring Network Traffic : One of the most important steps in detecting reverse and bind shells is monitoring network traffic. By regularly monitoring the flow of data on your network, you can identify unusual activity that may indicate the presence of a reverse or bind shell.
Some examples of unusual activity that you should be aware of include:
- Incoming connections from unexpected IP addresses: If you notice that your system is receiving connections from IP addresses that are not normally associated with your network, it may be an indication that someone is attempting to establish a reverse shell.
- Excessive data transfer: If you notice that large amounts of data are being transferred to or from your system, it may be an indication that someone is using a reverse or bind shell to transfer sensitive data out of your network.
- Unusual network traffic patterns: If you notice unusual network traffic patterns, such as an increase in traffic from a specific IP address or port, it may be an indication that someone is attempting to establish a reverse or bind shell.
-
Log Analysis : Log analysis is another important step in detecting reverse and bind shells. System logs and application logs contain valuable information that can be used to identify the presence of these malicious tools on your network.
When a reverse or bind shell is established, it typically generates log entries that record the connection and any data transferred. By analysing these logs, you can determine whether a reverse or bind shell is present on your network and what actions were taken using the shell.
- System and application logs provide valuable information on reverse and bind shells.
- Logs generated by shells typically record the connection and data transferred.
- Log analysis helps determine the presence of shells and the actions taken using the shell.
- System logs may show the IP address, port number, and time of connection establishment.
- Application logs may contain information on commands executed and data transferred.
- Understanding your network and log entries are important for effective log analysis.
- Specialized tools such as log analyzers or intrusion detection systems may be needed.
-
Intrusion Detection Systems (IDS) : Intrusion Detection Systems (IDS) are a crucial tool in detecting and preventing reverse and bind shells from compromising your network. IDS monitors network traffic in real time and uses algorithms and signatures to identify suspicious activity, such as unusual network traffic or shell code execution.
- When a reverse or bind shell is established, it generates network traffic that is likely to be unusual or out of the ordinary. An IDS can detect this unusual activity and trigger an alert, allowing you to take appropriate action.
- In addition to detecting network traffic, an IDS can also detect shell code execution. This is particularly important for detecting bind shells, as they often rely on shell code to establish a listening socket on a target machine.
- There are several different types of IDS available, including network-based IDS, host-based IDS, and hybrid IDS. The type of IDS you choose will depend on the specific requirements of your network and the types of threats you are trying to detect.
Prevention
-
Firewall Configuration : Configuring your firewall to block incoming connections from untrusted IP addresses is an important step in preventing reverse shells. By only allowing connections from trusted IP addresses, you can minimize the risk of reverse shells establishing a connection to your network.
It's important to note that while firewalls can help prevent reverse shells, they are not a guarantee. Reverse shells can still penetrate firewalls if they can exploit a vulnerability in your firewall configuration or use a technique such as port forwarding to bypass the firewall.
-
Patch Management : One of the most effective ways to prevent reverse and bind shells is to keep your systems up to date with the latest security patches and software updates. Vulnerabilities in software and operating systems can be exploited to install reverse or bind shells, so it's essential to keep your systems secure by applying the latest security patches.
Regular patch management can help you ensure that your systems are protected from known vulnerabilities, and it's important to prioritize the installation of security-related updates to reduce the risk of exploitation. By keeping your systems up to date, you can prevent reverse and bind shells and other security threats from compromising your network.
-
Application Security : Applications are a common target for attackers who want to install reverse or bind shells, so it's important to ensure that your applications are secure and free from vulnerabilities. By implementing strong application security measures, such as input validation, error handling, and secure coding practices, you can help prevent reverse and bind shells from compromising your applications.
Regularly testing your applications for vulnerabilities and implementing security updates can help you stay ahead of security threats, and it's essential to keep your applications up to date to prevent reverse and bind shells and other security threats from compromising your network.
-
User Education : Educating users about the dangers of reverse and bind shells and how to avoid them can help prevent their use in your organization. By raising awareness about the risks associated with reverse and bind shells, you can help users understand how to avoid using them, and how to identify and report suspicious activity.
In addition to raising awareness about the risks of reverse and bind shells, it's important to educate users about general security practices, such as avoiding suspicious links and attachments, using strong passwords, and reporting suspicious activity. By working together to create a culture of security, you can help prevent reverse and bind shells and other security threats from compromising your network.
Conclusion
- Shells are programs that provide a command-line interface to control a computer system.
- Reverse shells and bind shells are two types of shells that are used for malicious purposes.
- Reverse shells are initiated by the attacker and allow them to control a compromised system from a remote location.
- Bind shells are installed on a system by an attacker and allow them to connect to the system directly and execute commands.
- To prevent the misuse of reverse and bind shells, organizations should implement a combination of network security measures, such as firewalls, intrusion detection systems, and patch management.
- Regular monitoring of network traffic and system logs can also help detect unusual activity and prevent the misuse of reverse and bind shells.
- It is estimated that approximately 50% of cyber-attacks involve the use of reverse or bind shells.
