Introduction to Network Auditing with Nmap
Overview
Nmap is arguably the most well-known surveillance tool among pen testers and hackers. It is primarily a port scanner that assists you in scanning networks and identifying the different ports and services that are present in the network in addition to giving further information about targets, such as reverse DNS names, operating system predictions, device kinds, and MAC addresses. Additionally, it is useful while auditing a network.
Introduction
The Nmap ( or Network Mapper ) is an open-source program created by Gordon Lyon for network scanning and security auditing. Its architecture makes it capable of quickly diagnosing problems on both a single host and big networks. Typically, it is used by network administrators to identify the devices that are especially live on the system, the port number that each device is linked to, and any available open ports.
Nmap is useful for doing a network penetration test. It helps identify system security flaws in addition to providing network information. Nmap may be used on a variety of common operating systems, including Linux, Windows, macOS, and BSD, as it is platform-independent. It is simple to use and comes with both a command-line interface (CLI) and a graphical user interface (GUI).
Among the activities that Nmap may perform are:
- Finding hosts that are linked to a network
- Examining the target host's available open ports and exposed vulnerabilities.
- Identifying active services and their version numbers on a system
- Identifying system weaknesses and network flaws
What Is Nmap?
Nmap may be broadly characterized as a tool that can identify or analyze the services that are active on a system that is connected to the Internet. Network administrators frequently utilize this technique to find possible security holes in their network systems. Additionally, it may be used to automate a variety of duplicate duties, such as keeping track of service update schedules.
Functions of Nmap
Nmap is a powerful tool that, when used correctly, may be used to safeguard and improve networks and data. The application gathers and compiles every piece of return data supplied by ports that have been scanned using Nmap. According to that data, there are several important tasks that the majority of users of the application utilize to assist with. They consist of:
Network Mapping
Nmap was developed primarily for this purpose, and it is now among its most popular applications. Nmap's host discovery feature will show you the different kinds of equipment that are actively using the detected ports. Servers, routers, switches, and other equipment fall under this category. Additionally, users may view the connections between those components and how they come together to produce a network map.
Port Rules Discovery
Nmap can quickly determine if a port is open or closed by anything like a firewall, even with a basic scan. In reality, a lot of IT specialists utilize Nmap to validate their work when developing firewalls. They can monitor the performance of their firewalls and determine whether their settings are achieving the desired impact.
Shadow IT Hunting
Nmap's ability to identify the kind and position of devices on a network makes it useful for identifying objects that shouldn't be there at all. Because they are not formally permitted to be present on a network or are occasionally purposefully disguised, these devices are known as shadow IT. Shadow IT is a risk since such systems are not covered by security audits or programs. For instance, if an Xbox game server is covertly installed on a company network, it may not only use bandwidth but also serve as a launchpad for an assault, especially if it is not kept up to date with the most recent security updates.
Operating System Detection
Through a procedure known as OS fingerprinting, Nmap can identify the kinds of operating systems that are present on found devices. In most cases, this provides details about the operating system and the name of the device's manufacturer (Dell, HP, etc.). Even more information, such as the OS patch level and the device's anticipated uptime, may be found with a more thorough Nmap scan.
Service Discovery
Nmap rises above the status of a standard mapping tool because of its ability to find services. Users can start a deeper scan to learn more about the functions that newly found devices are playing rather than just learning that they exist. Knowing whether they are serving as a mail server, web server, database repository, storage device, or nearly anything else is part of this. Nmap may also report on which individual apps are running and what version of those applications is being utilized, depending on the scan.
Vulnerability Scanning
Since Nmap lacks any type of artificial intelligence or a database of known vulnerabilities, it cannot be considered a specialized vulnerability scanning tool. However, companies may utilize Nmap to determine their sensitivity to certain threats provided they frequently consume security information from threat feeds or other sources.
Nmap may be used to determine whether any applications presently running on network assets satisfy the requirements of a recently discovered vulnerability, for instance, if it only impacts a specific application or service using an earlier version of the software. If anything is discovered, it seems to reason that IT teams would make it a priority to patch any affected systems as soon as possible to close any security holes before an attacker does.
How Does NMap Work?
Nmap works by searching for hosts and services on a network. When a host or service is discovered, the software platform transmits information to that host or service, which then responds. Nmap analyses and deciphers the returned answer before using the data to build a network map. A thorough description of each port's function, who (or what) is using it, how hosts are connecting, what gets through the firewall and what doesn't, as well as a summary of any security vulnerabilities that are discovered, are all included in the map that is produced.
Nmap uses port scanning to find open communication channels on computer systems. Since services operating on open ports could be attacked-prone, this is the initial step for an attacker to learn about the target's network and find a suitable entry point. Nmap requires four main processes to function: host discovery, port scanning, service discovery, and vulnerability testing.
Host Discovery
Nmap by default utilizes requests to find a live IP. The subsequent packets are transmitted to find any accessible hosts:
- ICMP echo command
- SYN packet from TCP to port 443
- ACK packet for TCP on port 80
- A request for an ICMP timestamp
It is advised to initially identify hosts if the target is unknown and vast. At this point, scanning the ports would cause too much traffic, require too much time and resources, and probably result in security alerts.
ARP scanning, ICMP scanning, and TCP scanning are a few techniques to find active IPs.
The following step, locating open ports, might be skipped if there is already a list of active IP addresses.
Scanning for Open Port
Based on the answer to an SYN request, Nmap determines the state of ports.
- Open: Nmap flags a port is open if it receives "syn-ack" as the probe response.
- Close: If Nmap receives an "RST" as a probe response, the flags the port as closed.
- Filtered: Nmap doesn't get a response, which could be because of firewall filtering, it flags the port as open | filtered.
You may utilize a variety of methods for port scanning, including TCP Connect, Stealth Scan, and UDP Scan.
Discovering Services
Nmap can recognize services by monitoring open communication ports for the welcome banner. A lot of popular services, including SSH, Telnet, FTP, and SMTP, use this to identify themselves.
Nmap launches a probe and waits for a response if a banner is not shown. The information obtained is contrasted with thousands of signatures that Nmap has stored in its database file specifically for service fingerprinting.
Testing for Vulnerabilities
Nmap uses the Nmap Script Engine (NSE), a versatile tool that enables users to create scripts for job automation, to identify vulnerabilities in the network.
NSE includes a wide range of scripts that may assist with network discovery, vulnerability exploitation, and backdoor detection. On Linux, the database may be found at "/user/share/nmap/scripts/," whereas on Windows, it is located at "C:Program Files (x86)Nmapscripts."
Modes of Operation
Nmap can carry out a wide range of scans. The many scan kinds are listed below:
1. Ping Sweep
A fast Nmap scan to see which IP addresses respond to ICMP (Internet Control Message Protocol) by pinging all reachable IP addresses. Anyone who needs to know the number of IP addresses might benefit greatly from using this Ping Sweep.
2. SYN Scan
To all target ports, an SYN message is transmitted through TCP. A port has been opened if the system receives a response acknowledging it. If there is no response, the port is closed or unavailable.
3. TCP Scan
It is similar to SYN scan, it sends packets to all ports using the TCP layer. The difference is that the connection is ended by the acknowledgment packets. The TCP scan could be easily seen in the logs, resulting in more processing resources.
4. Idle Scan
This scan is designed to determine whether any malicious attacks are planned on a network. To search for malware, Nmap scans are moved away from a port. But an IP address and a port ought to be sent to the remote host.
5. RPC Scan
Remote Procedure Calls (RPC) are a technique used by hackers to make systems susceptible to viral attacks. To prevent RPC instructions from running on the system and gathering data, it is advised to frequently scan a network for them.
6. Windows Scan
The software looks for acknowledgment packets on the ports after sending SYN packets. This check looks for any anomalies in the ACK packets that have been received and identify any broken ports.
7. Bounce Scan
The security of the File Transfer Protocol layer is examined by this scan. FTP tiers seldom ever receive packets, and when they do, they could send them to an internal layer so that computers can access them inside. The same fault is evaluated by a bounce scan, which detects whether your FTP layer is exposed.
8. UDP Scan
The main use of this scan in Windows is to check for the UDP layer is susceptible. While getting a response from the UDP layer is not always necessary, it is useful to know whether any Trojan attacks are currently underway.
9. FIN Scan
Similar to SYN Scan, the system that transmits the packets receives a significant portion of TCP FIN packet responses. There is no need for consumers to be alarmed because the system is not sending an RST packet.
10. NULL Scan
Systems other than Windows that can quickly identify packet kinds and respond with TCP or NULL responses may benefit from using this scan. NULL scans are not supported by Windows since they do not always work.
Scanning a Network with Nmap
We will utilize Kali Linux, a Debian-based Linux distribution created especially for penetration testers, in our demonstration of what is Nmap. All necessary hacking tools are pre-installed on it.
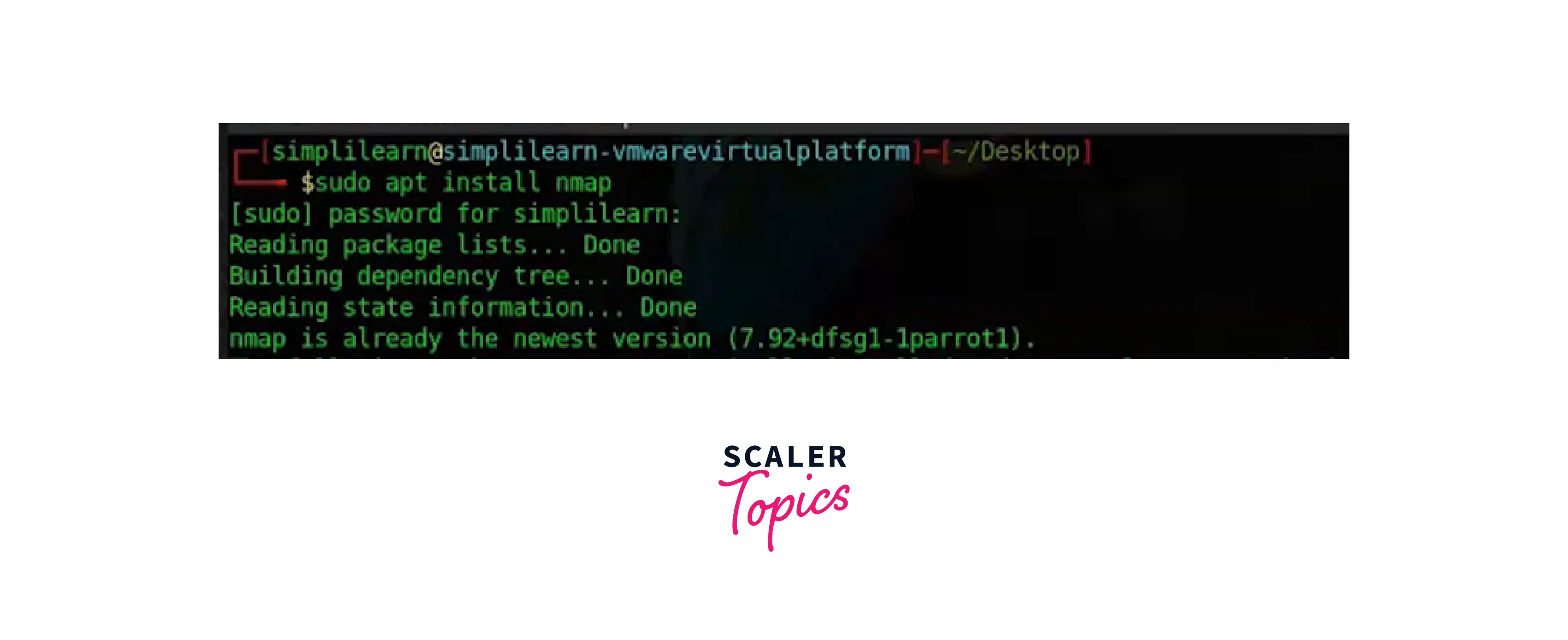
Installing Nmap on Kali Linux
On Linux distributions based on Debian, you may install Nmap by using the following command if you want to reinstall the program.
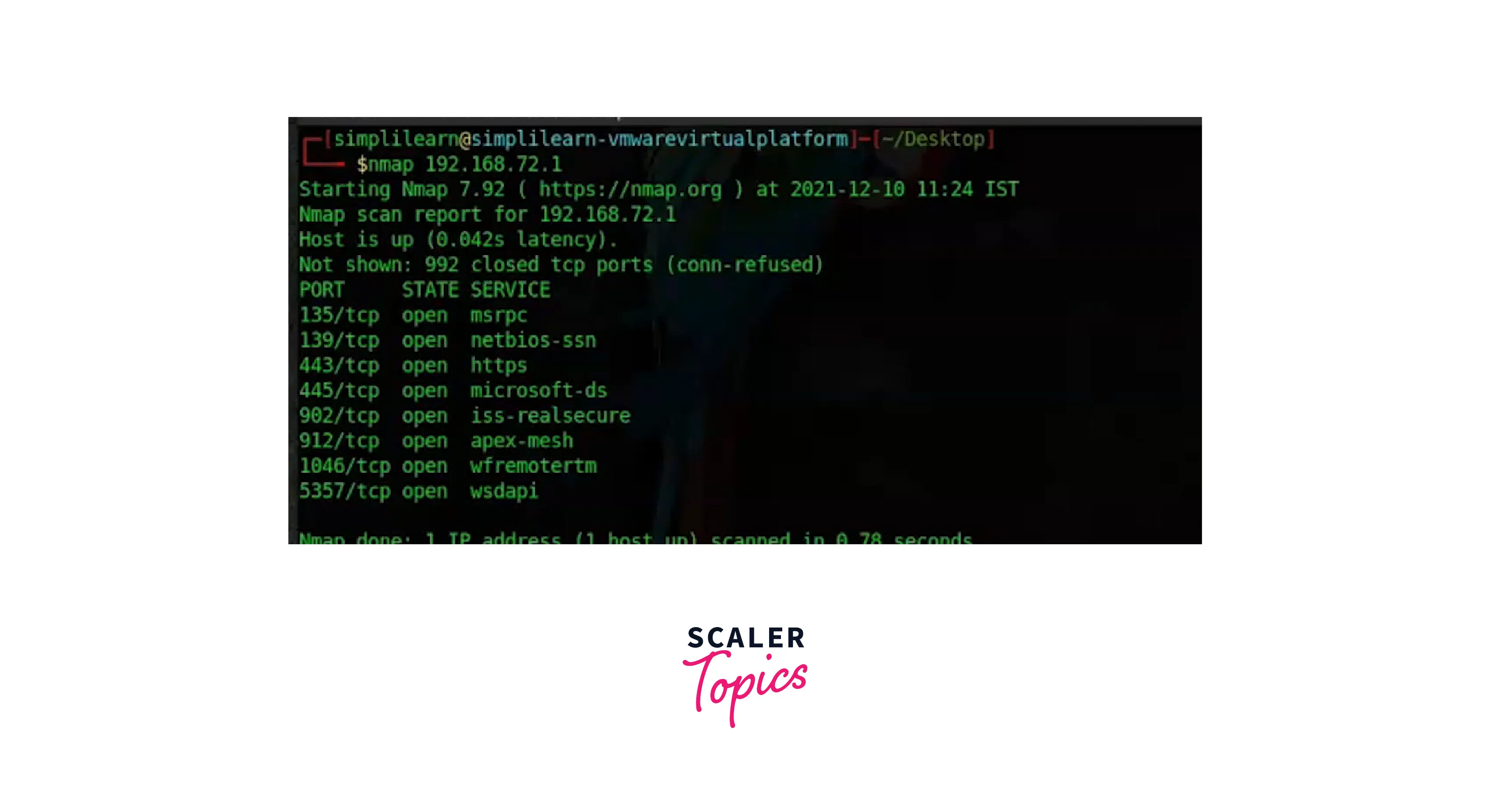
Scanning a Specific IP Addresses or Host-Name
The command nmap <target_IP_address> or nmap www.scaler.com may be used to do an easy port scan to find services that are running.
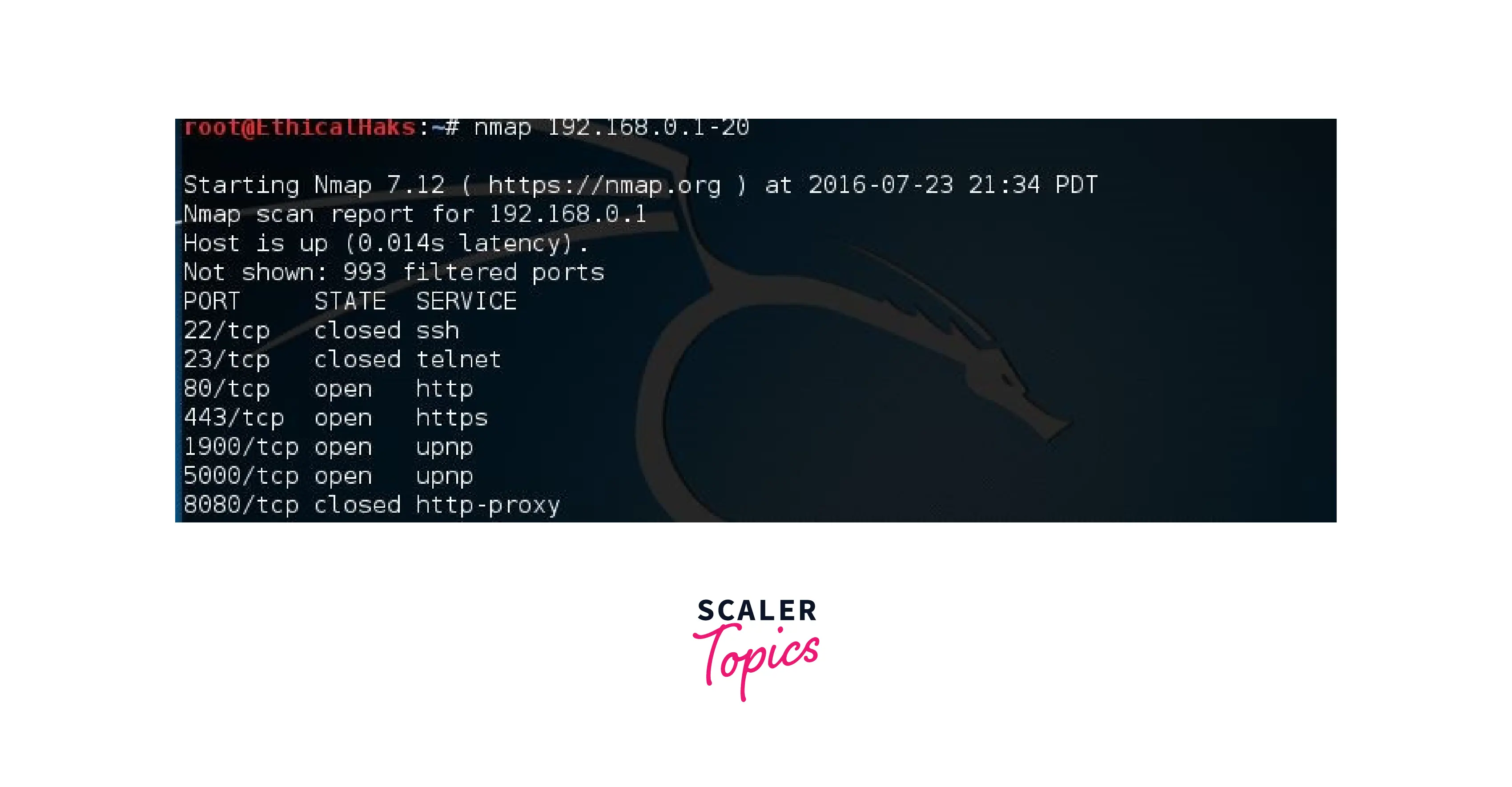
Scanning a Range of IP-Address
This is the command to scan several IP addresses. When attempting to pinpoint the location of a potential network assault, scanning a variety of IPs is helpful. It also saves time while tracking a network assault to be able to scan numerous IPs: nmap 192.168.0.<range r1-r2>
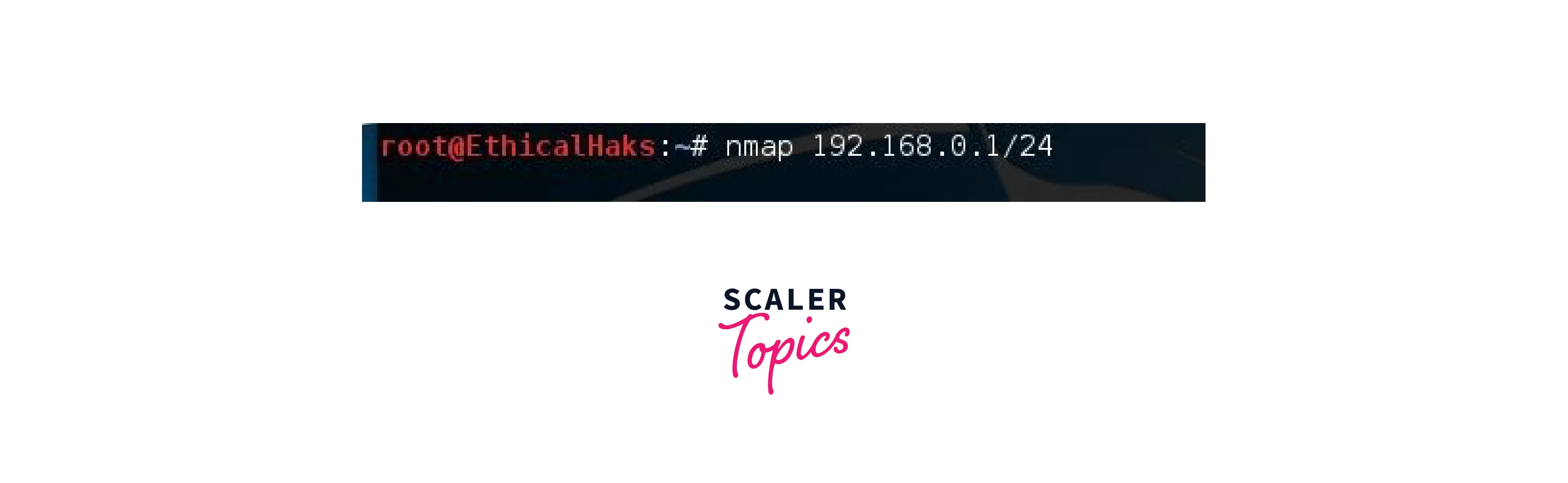
Scanning a Subnet
A subnet is scanned by this command. A subnet scan enables the scan to keep track of many hosts. Using this command to check on various networks is also helpful:
nmap 192.168.0.1/24
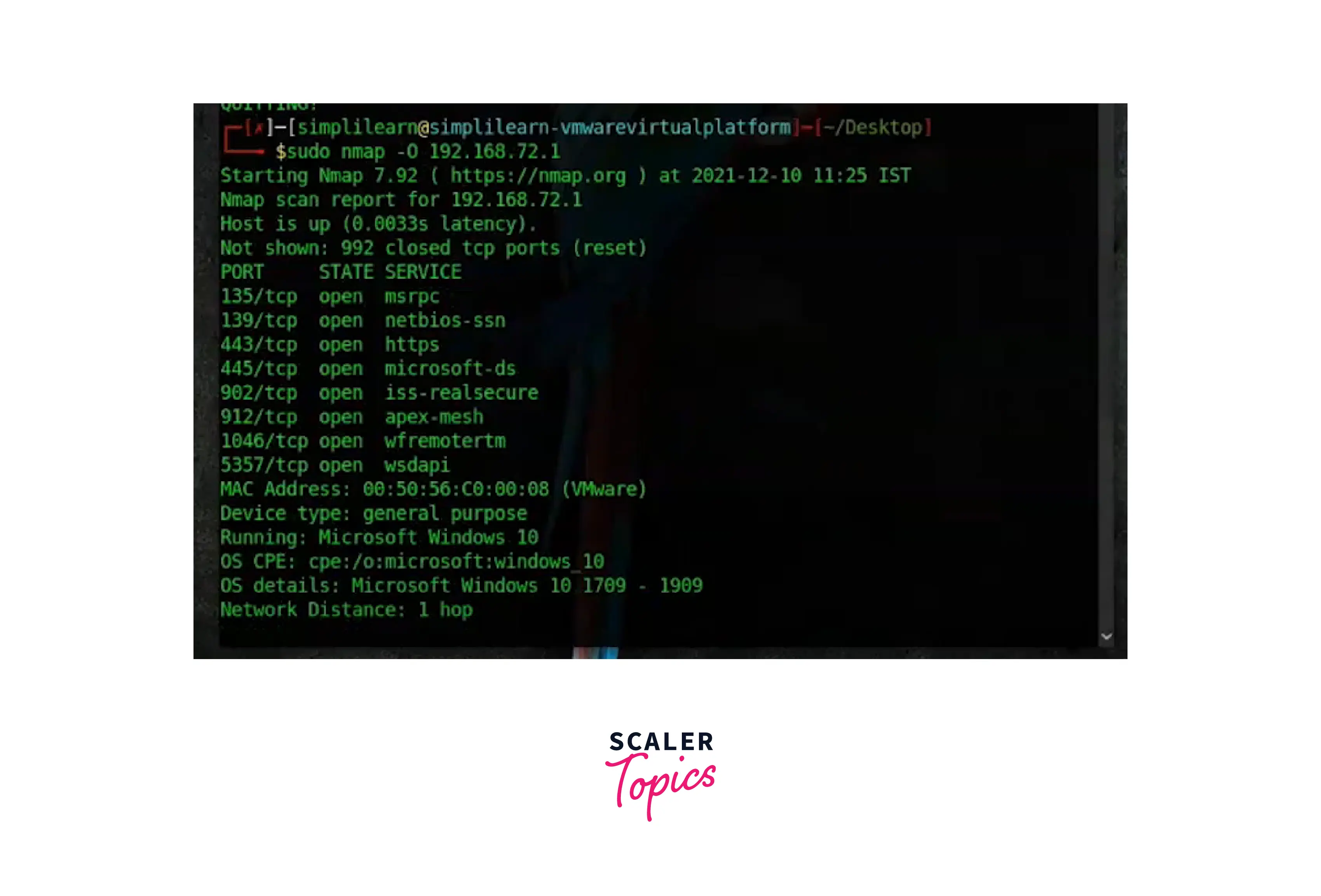
OS Detection
The '-O' flag can also be used to determine the type of operating system the target machine is using. This, however, does TCP/IP fingerprinting, which requires root or sudo access to run.
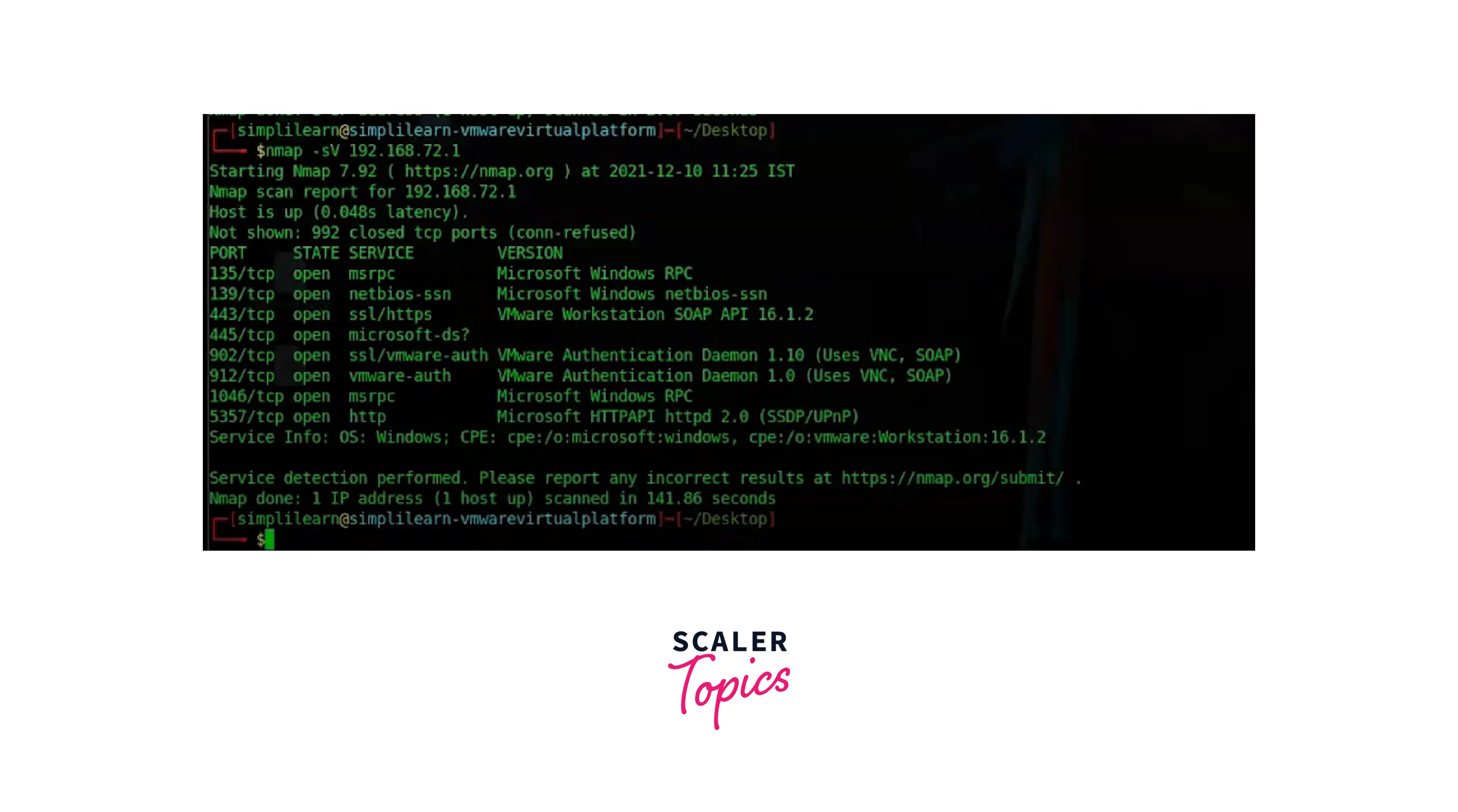
Determining Service/Version Info
You must use the '-sV' switch to acquire the version number of the services being used on the target. Some software, especially older versions, frequently include flaws that, when found, can be used against the user.
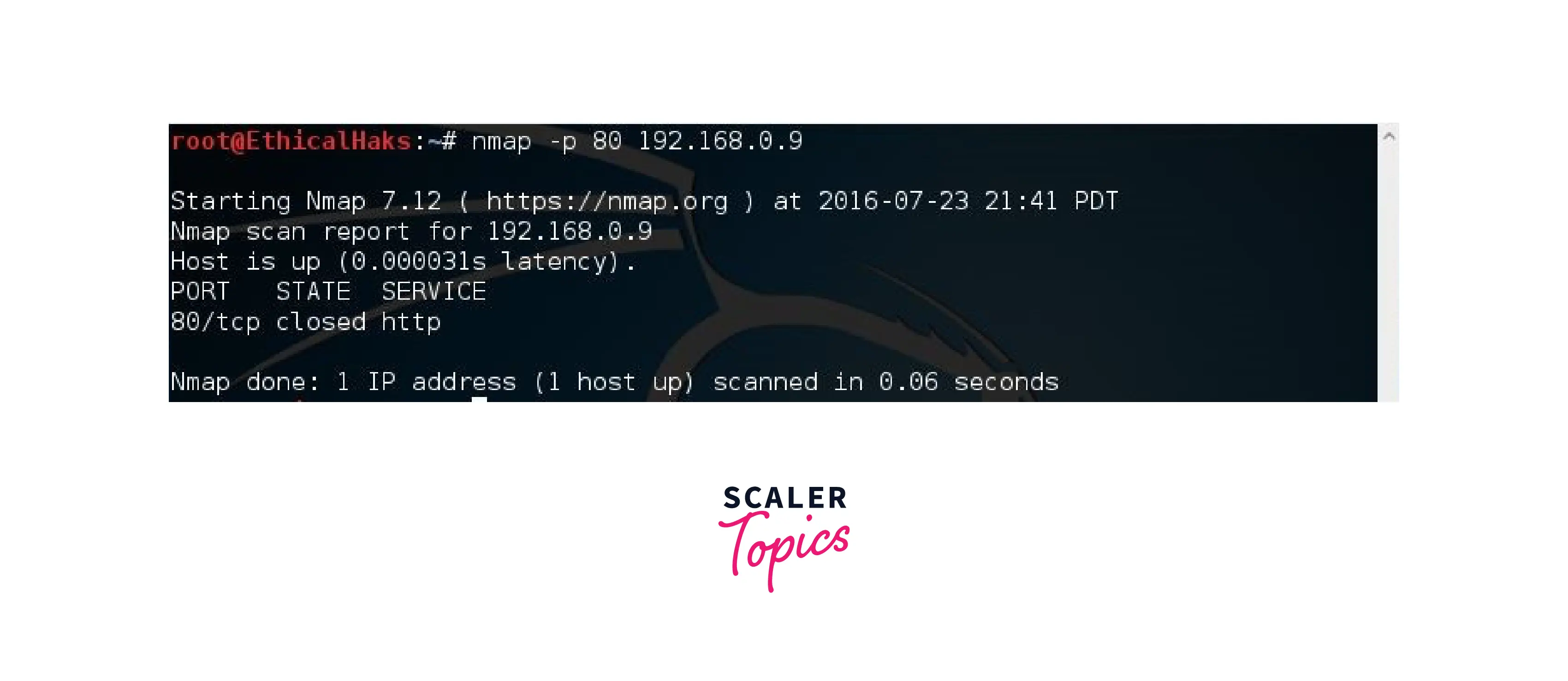
Scanning a Single Port
This command is used to scan a single port. On each host it infects, certain malware will dependably run on a particular port. Knowing these ports might occasionally help you identify the type of virus you are coping with rapidly. In this circumstance, a single port scan is helpful: nmap -p <port_no> 192.168.0.9
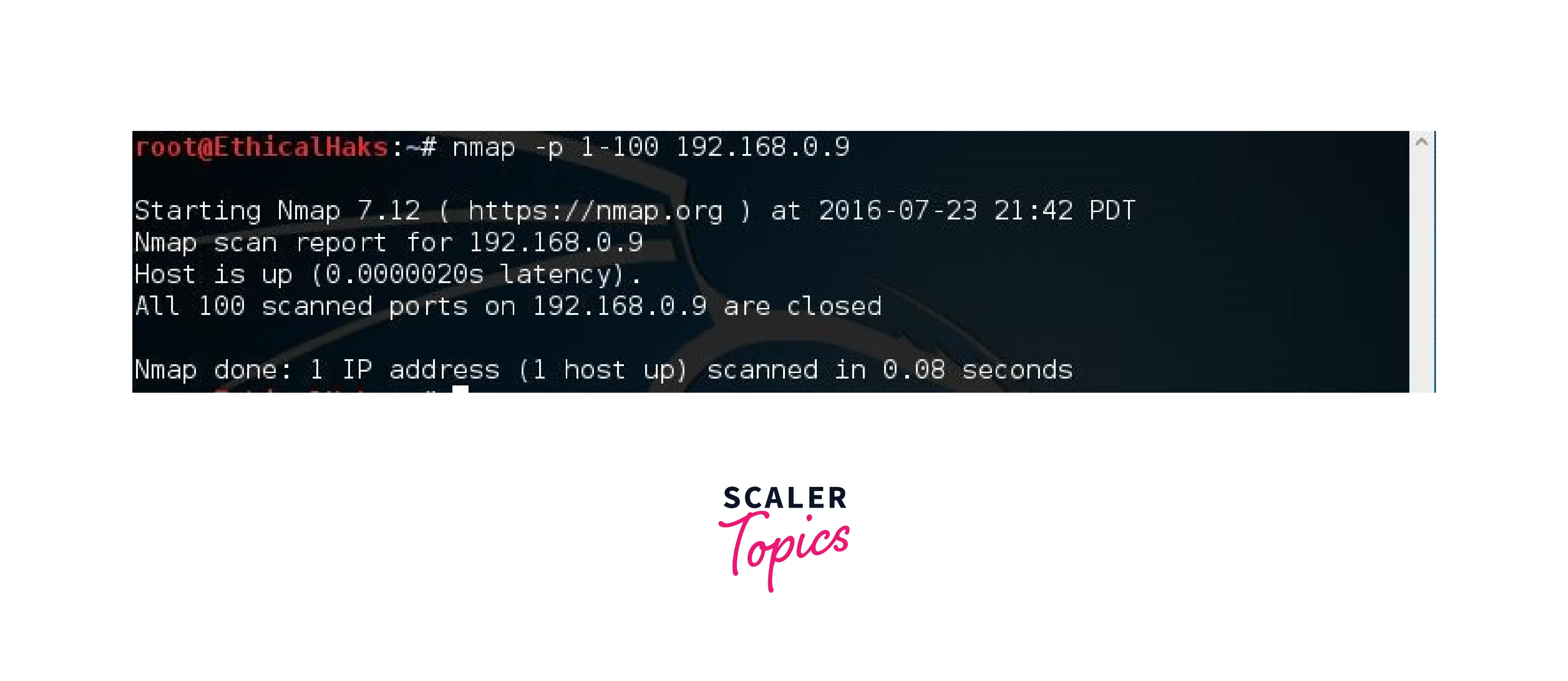
Scanning a Range of Ports
This command will search ports 1-100 in the specified range. You can concentrate on certain port ranges thanks to the adaptability of this command: nmap -p <range1-range2> 192.168.0.9
Use the -p- option to check all ports from 1 to 65535: nmap -p- 172.162.110.123
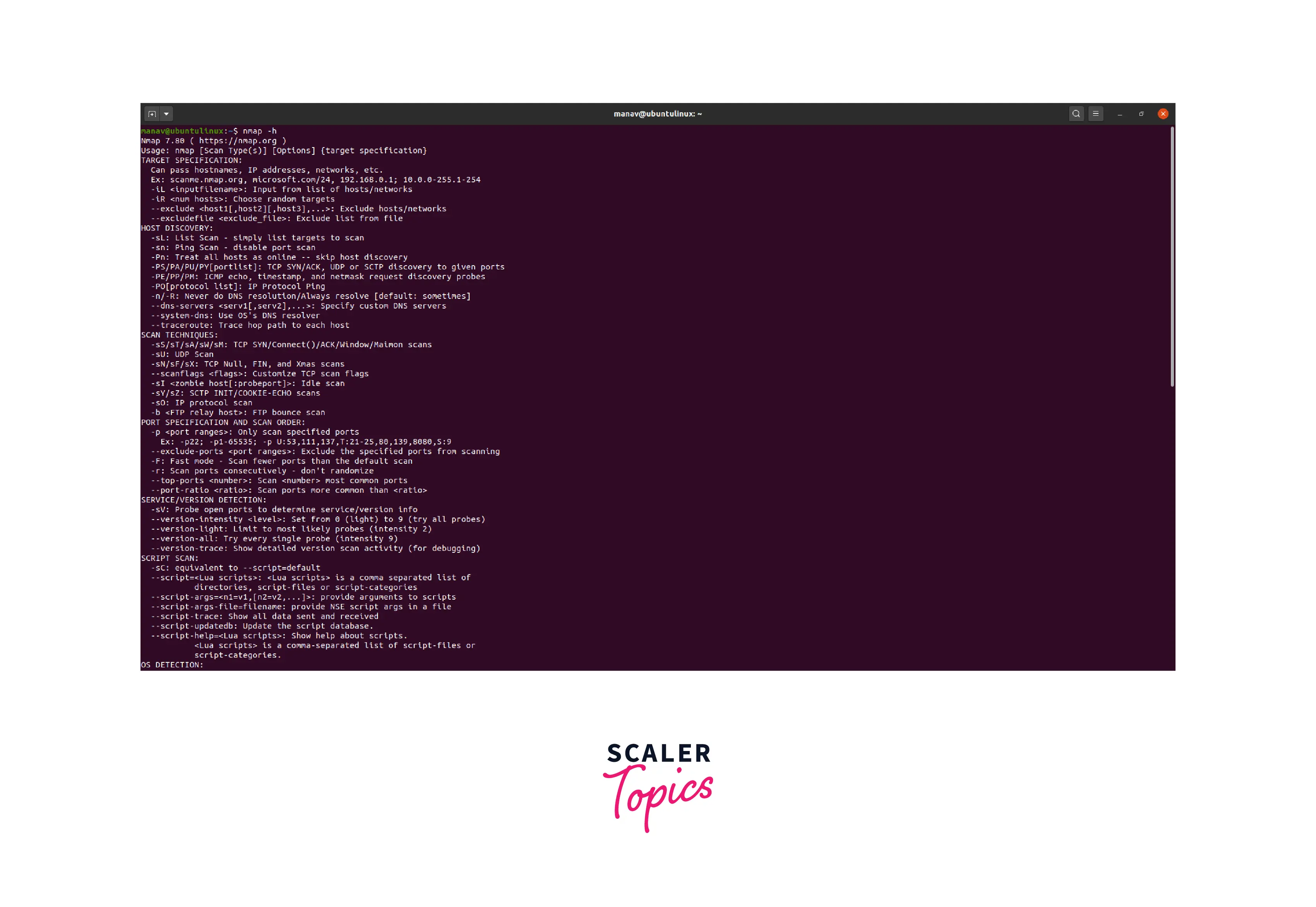
For Help
If you have any queries concerning Nmap or any of the commands that are provided, you utilize the "-h" option. It displays the Nmap command's help page, which includes information about the possible flags.
Conclusion
- Nmap is a solution for security scanning that is widely used in business. Commonly used by network managers to identify the target host connected to the network. It can conduct extensive network scans with ease and is simple to use.
- When anything goes wrong or someone tries to breach your system, Nmap can offer the degree of information and proactive planning necessary to keep your data safe.
- In this post, we learned how network mappers operate and the several ways that they are used in the penetration testing sector. While making sure that workable alternatives and actual demonstrations are taken into account, you covered the range of scans that can be done.
- Nmap is only one tool, though, and ethical hacking groups are built on a variety of similar ideas.
- It now has even more improvements, with only a few clicks, users can easily set up targets and arrange desired scans via Zenmap's graphical user interface. That will aid Nmap in gaining more users.
