Database Security in DBMS

Data is a valuable resource that must be handled and managed with care, just like any other economic resource. As a result, some or all of the commercial data may be tactically important to their specific company and hence must be kept protected and confidential. In this article, you will get to learn about the extent of database security. As countermeasures to these threats, a variety of computer-based controls are available.
What is Database Security in DBMS?
Database security in DBMS is a technique for protecting and securing a database from intentional or accidental threats. Security considerations will apply not only to the data stored in an organization's database: a breach of security may impact other aspects of the system, which may ultimately affect the database structure. As a result, database security encompasses hardware parts, software parts, human resources, and data.
To use the security efficiently, appropriate controls are required, which are separated into a specific goal and purpose for the system. The demand for effective security, which was frequently neglected or overlooked in the past, is now being rigorously verified by many businesses.
We consider database security in the following scenarios:
- Theft and fraudulent.
- Loss of Data privacy.
- Loss of Data integrity.
- Loss of confidentiality or secrecy
- Loss of availability of data.
These above-stated conditions generally represent the areas where the organization should focus on lowering the risk, which is the possibility of data loss or destruction within a database. Since all of the data inside an organization is interrelated, an activity that results in a loss in one area may also lead to a loss in another.
Why Database Security is Important?
Security is an important concern in database management because the information stored in a database is a very valuable and, at times, quite sensitive commodity. As a result, data in a database management system must be protected from abuse and illegal access and updates.
- Compromise of intellectual property: Our intellectual property—trade secrets, inventions, or unique methods—could be essential for our ability to sustain an advantage in our industry. If our intellectual property is stolen or leaked, then we will lose our competitive advantage and it may be difficult to maintain or recover.
- The reputational harm is done to our brand: Customers or partners may refuse to buy goods or services from us (or do business with us) if they do not believe they can trust our company to protect their data or their own.
- The concept of business continuity (or lack of it): Some businesses are unable to operate until a breach has been resolved.
- Penalties or fines to be paid for failure: The cost of failing to comply with international regulations such as the Sarbanes-Oxley Act (SAO) or Payment Card Industry Data Security Standard (PCI DSS) specific to industry regulations on data privacy, such as HIPAA, or regional privacy laws like the European Union's General Data Protection Regulation (GDPR) could be significant, with fines exceeding many millions of dollars in the worst-case scenario.
- Costs of correcting breaches and notifying consumers about them: Along with notifying customers of a breach, the organization that was breached must fund the investigation and forensic services such as crisis management, triage repairs to the affected systems, and much more.
Database Security Threats
Many software vulnerabilities, misconfigurations, or practices of misuse or carelessness could lead to breaches. The following are some of the most well-known causes and types of database security cyber threats.
1) SQL/NoSQL Injection Attacks
It is a type of attack that occurs when a malicious code is injected into frontend (web) apps and then transmitted to the backend database. SQL injections provide hackers with unrestricted access to any data saved in a database. There are two types of such computer attacks: SQL injection attacks on traditional databases and NoSQL injection attacks on large data databases. Typically, these are queries generated as an extension of online application forms or received via HTTP requests. Any database system is vulnerable to these attacks if developers do not follow secure coding practices and the organization does not conduct regular vulnerability testing.
Countermeasures:
- Direct queries should be replaced with stored procedures.
- The MVC Architecture must be implemented.
2) Malware
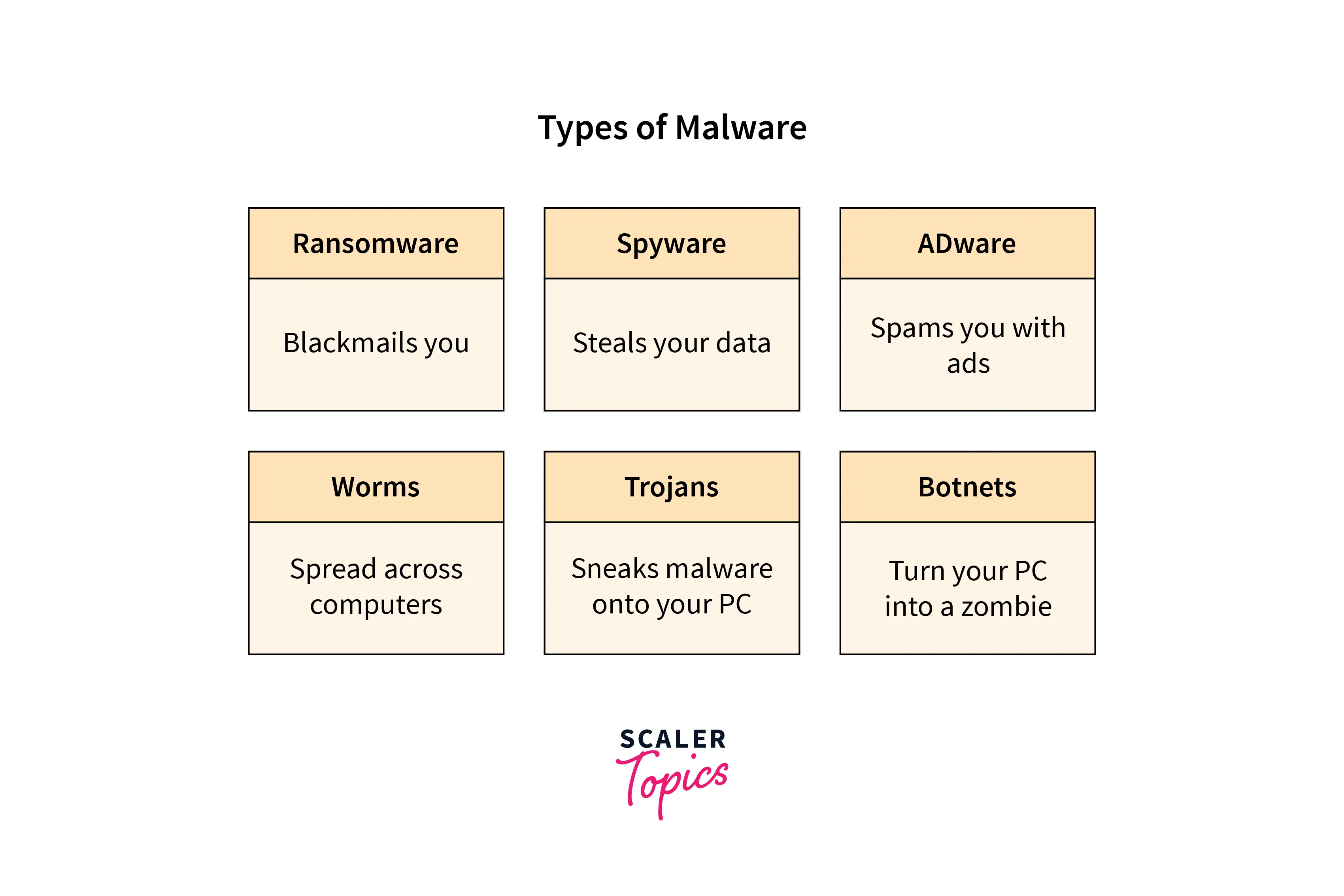
Malware is software designed to corrupt data or harm a database. Malware could enter your system via any endpoint device connected to the database's network and exploit vulnerabilities in your system. Malware protection is important on any endpoint, but it is particularly necessary on database servers due to their high value and sensitivity. Examples of common malware include spyware, Trojan viruses, viruses, worms, adware, and ransomware.
Countermeasures:
- Safeguard any endpoints on your databases. Install specialized malware protection software and spread awareness among users on risk and preventative measures.
3) Lack of Security Expertise and Education
Databases are breached and leaked due to insufficient level of IT security expertise and education of non-technical employees, who may violate basic database security standards and endanger databases. IT security employees may also lack the necessary expertise to create security controls, enforce rules, or execute incident response processes.
Countermeasures:
- Database users must be trained in database security.
- IT security professionals will be encouraged to advance their professional level and qualifications.
4) Denial of Service (DoS/DDoS) Attacks
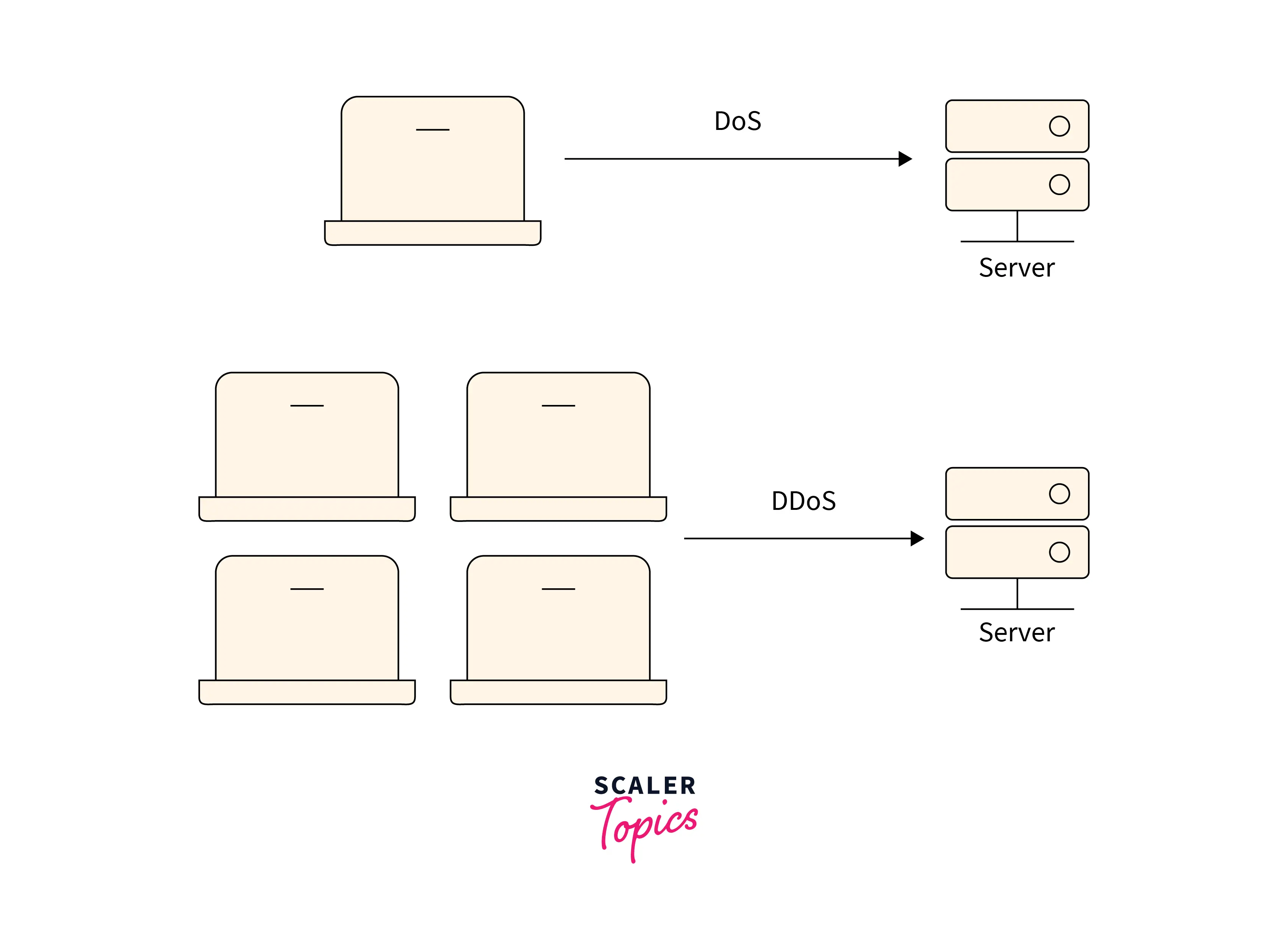
In a denial of service (DoS) attack, the cybercriminal uses a huge number of fake requests to overwhelm the target service—in this case, the database server. As a result, the server cannot handle legitimate requests from actual users and frequently crashes or becomes unstable.
A DoS (Denial of Service) attack causes a database server to slow down and may render it unavailable to all users. Even though a DoS attack does not reveal the contents of a database, it can cost victims a significant amount of time and money. Moreover, what is the use of having a database if you can't use or access it?
In a distributed denial of service (DDoS) attack, fake traffic is generated by a large number of computers that are part of an attacker-controlled botnet. This results in extremely high traffic volumes, which are difficult to stop without a highly scalable defensive architecture. Cloud-based DDoS prevention services can dynamically scale up to deal with massive DDoS attacks.
Countermeasures:
- Harden the TCP/IP stack by increasing the size of the TCP connection queue with the appropriate registry settings.
- Reduce the time it takes to establish a connection.
- Use dynamic backlog methods to ensure that the connection queue is never full.
- Use an Intrusion Detection System (IDS) on your network.
5) Exploitation of Database Software Vulnerabilities
Attackers are continuously attempting to isolate and target software vulnerabilities, and database management software is a particularly desirable target. New vulnerabilities are identified on a daily basis, and security updates are issued regularly by all open-source database management platforms and commercial database software manufacturers. However, if you do not apply these changes immediately, your database may be vulnerable to attack.
Even if you deploy patches on time, there is always the risk of zero-day attacks, which occur when attackers find a vulnerability that the database vendor has not yet found and patched.
Countermeasures:
- Encrypt any sensitive information in your database (s).
- Apply the necessary database controls and permissions.
- Conduct a regular search for new sensitive data in your databases. You may accomplish this very successfully with the Periodic Data Discovery tool and Compliance Manager, which will automatically discover and secure newly uploaded sensitive data.
6) Excessive Database Privileges
Database users in DBMS may have varying levels of access. However, users may abuse them, and the three basic categories of privilege abuse are as follows: excessive privilege abuse, legitimate privilege abuse, and unused privilege abuse. Excessive privileges always introduce unnecessary risks. According to statistics, 80% of attacks on company databases are carried out by current or former workers.
Countermeasures:
- It is recommended that a strict access and privileges control policy be implemented and enforced.
- Don't give staff too many privileges, and revoke outdated privileges as soon as possible.
7) Weak Audit Trail
If a database is not audited, it represents a risk of noncompliance with sensitive data protection rules at the national and international levels. All database events must be automatically logged and registered, and automatic auditing solutions must be used. Failure or unwillingness to do so represents a major risk on multiple levels.
Countermeasures:
- Use automatic auditing solutions that have no impact on database performance.
Control Measures for the Security of Data in Databases
The following are the key control measures used to ensure data security in databases:
Authentication
- Authentication is the process of confirming whether a user logs in only with the rights granted to him to undertake database operations. A certain user can only log in up to his privilege level, but he cannot access any other sensitive data.
- The ability to access sensitive data is restricted by the use of authentication. For example, a mobile phone performs authentication by requesting a PIN, fingerprint, or by face recognition. Similarly, a computer verifies a username by requesting the appropriate password.
- However, in the context of databases, authentication takes on a new dimension because it can occur at multiple levels. It can be done by the database itself, or the configuration can be adjusted to allow the operating system or another external means to authenticate users.
- For example, when creating a database in Microsoft's SQL Server a user must specify whether to use database authentication, operating system authentication, or both (the so-called mixed-mode authentication). Other databases that prioritize security use near-foolproof authentication methods such as fingerprint recognition and retinal scanning.
- By using various authentication technologies such as biometrics for retina and fingerprints, you can protect your data from unauthorized/malicious users.
Access Control
- Database access control is a means of restricting access to sensitive company data to only those people (database users) who are authorized to access such data and permitting access to unauthorized persons. It is a key security concept that reduces risk to the business or organization.
- Physical and logical access control are the two types of access control. Access to campuses, buildings, rooms, and physical IT assets is restricted through physical access control. Connections to computer networks, system files, and data are restricted through logical access control.
- To safeguard a facility, corporations use electronic access control systems to track employee access to restricted company locations and private regions, such as data centers, using user credentials, access card readers, auditing, and reports. Some of these systems include access control panels to restrict access to rooms and buildings, as well as alarms and lockdown features to prevent unauthorized access or operations.
- Logical access control systems execute user and entity identification, authentication, and authorization by evaluating needed login credentials, which can include passwords, personal identification numbers, biometric scans, security tokens, or other authentication factors. Multifactor authentication (MFA), which needs two or more authentication factors, is frequently used as part of a layered defense to safeguard access control systems.
- The most well-known Database Access Control examples are:
- Discretionary Access Control (DAC)
- Mandatory Access Control (MAC)
- Role-Based Access Control (RBAC)
- Attribute-Based Access Control (ABAC)
Inference Control
- Inference control in databases, also known as Statistical Disclosure Control (SDC), is a discipline that aims to secure data so that it can be published without disclosing sensitive information associated with specific individuals among those to whom the data corresponds.
- It prevents the user from completing any inference channel. This strategy prevents sensitive information from indirect disclosure. There are two kinds of inferences: identity disclosure and attribute disclosure.
- SDC is used to protect the privacy of respondents in fields such as government statistics, health statistics, e-commerce (sharing of customer data), etc. Since data modification ultimately implies data protection, SDC aims to achieve protection with the minimum amount of accuracy loss for database users.
Flow Control
- Distributed systems involve a large amount of data flow from one site to another as well as within a site. Flow control prohibits data from being transferred in such a way that unauthorized agents cannot access it.
- A flow policy specifies the channels through which data can flow. It also defines security classes for data as well as transactions. Convert channels are the pathways for information to flow implicitly in ways that violate a company's privacy policy.
Database Security Applying Statistical Method
- Statistical database security focuses on the protection of sensitive individual values stored in so-called statistical databases and used for statistical purposes, as well as retrieving summaries of values based on categories. They do not allow the retrieval of individual information.
- Examples include patient records utilized by medical researchers and extensive phone call records statistically examined by phone companies to improve their services.
- It provides access to the database to obtain statistical information about the number of employees in the company but not to obtain detailed confidential/personal information about a specific individual employee.
- The techniques used to prevent statistical database compromise are classified into two types: noise addition, in which all data and/or statistics are available but are only approximate rather than exact, and restriction, in which the system only delivers statistics and/or data that are deemed safe.
Encryption
- Data encryption protects data confidentiality by converting it to encoded information known as ciphertext, which can only be decoded with a unique decryption key generated either during or before encryption.
- Data encryption can be used during data storage or transfer, and it is usually used in conjunction with authentication services to ensure that keys are only given to or used by authorized users.
- Data is more accessible and desirable to attackers than ever before, increasing the need for security. Additionally, many firms must comply with data protection regulations, many of which specifically require the use of encryption.
- Aside from the clear advantages of enhanced security, privacy protection, and the avoidance of illegal access, encryption also helps to assure data integrity. Encryption protects content against unauthorized change and can be used to validate the origin and authenticity of data.
Data Protection Tools and Platforms
Several companies now offer data protection platforms and tools. A comprehensive approach should include the following features:
-
Discovery: The ability to discover is often required to meet regulatory compliance requirements. Look for a solution that can discover and classify vulnerabilities in our databases, whether they're in the cloud or on-premises. It will also offer recommendations to address any discovered vulnerabilities.
-
Data Activity Monitoring: The solution should be capable of monitoring and analyzing all data activity in all databases, regardless of whether our application is on-premises, in the cloud, or inside a container. It will notify us of suspicious activities in real-time, allowing us to respond to threats more rapidly. It also provides visibility into the current state of our data via an integrated and comprehensive user interface. It is also important to select a system that enforces regulations, procedures, and the division of roles. Be sure that the solution we select can generate the reports we require to comply with the rules.
-
Data Tokenization and Encryption: In the case of an incident, encryption serves as an additional line of protection against any breach. Any software we deploy must be capable of protecting data in the cloud, on-premises hybrid, or multi-cloud environments. Find a tool that has volume, file, and application encryption features that meet our company's compliance requirements. Tokenization (data concealment) or advanced key management of security keys may be required.
-
Data Security and Risk Analysis Optimization: An application that provides contextual insights by combining security data with advanced analytics will allow the user to perform optimizing, risk assessment, and reporting a breeze. Select a technology that can store and combine vast amounts of recent and historical data regarding the security and health of your databases. Also, choose a solution that allows for data analysis, auditing, and reporting capabilities via a comprehensive but user-friendly self-service interface.
Conclusion
- Database security is the protection of a database against both intentional and unintentional threats, which might be computer-based or non-computer-based.
- As the volume of data kept in business databases expands and individuals rely increasingly on corporate data for decision-making, customer service management, supply chain management, and other purposes, there is a higher emphasis on database security than in the past.
- Database security is the responsibility of the entire organization because all individuals rely on the data stored in the organization's database.
- Any loss or unavailability of corporate data will cripple today's organization and hurt its performance. Now, even a few minutes of database downtime can result in significant costs for the organization and people's performance.
- Therefore, database security involves the hardware, software, infrastructure, employees, and data of the organization.
