Networking for DevOps
Overview
DevOps networking is a critical component of modern IT infrastructures. This article will delve into DevOps networking.
We will cover the following topics OSI model, TCP/IP, the difference between TCP and UDP protocols, IP subnetting and CIDR, Routing, an overview of the DNS, its various record types, domains, zones, and delegation, HTTP and its methods, response codes, and headers and network troubleshooting tools alongside some tips for assembling a toolbox for network management.
The article ends with multiple-choice questions to help you test your knowledge in DevOps networking.
OSI Model
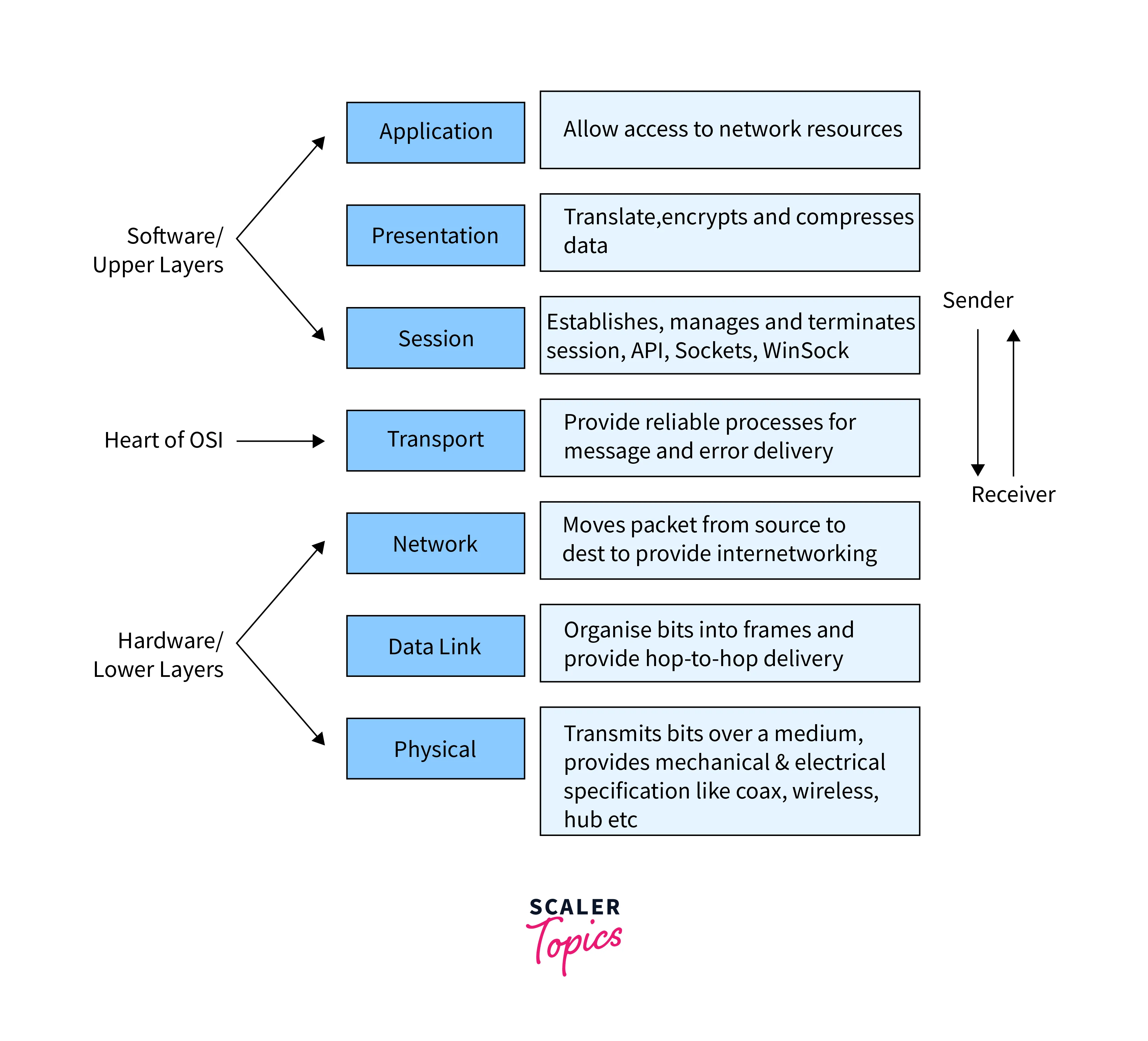
The Open Systems Interconnection (OSI) model is a conceptual framework that describes how data moves through a network. OSI is a layered approach that defines seven layers, each with a specific function in the communication process.
The OSI model is crucial in DevOps networking because it provides a common reference point for network architects, engineers, and administrators to design, implement, and troubleshoot networks.
Now we will take a closer look at each of the seven layers in the OSI model:
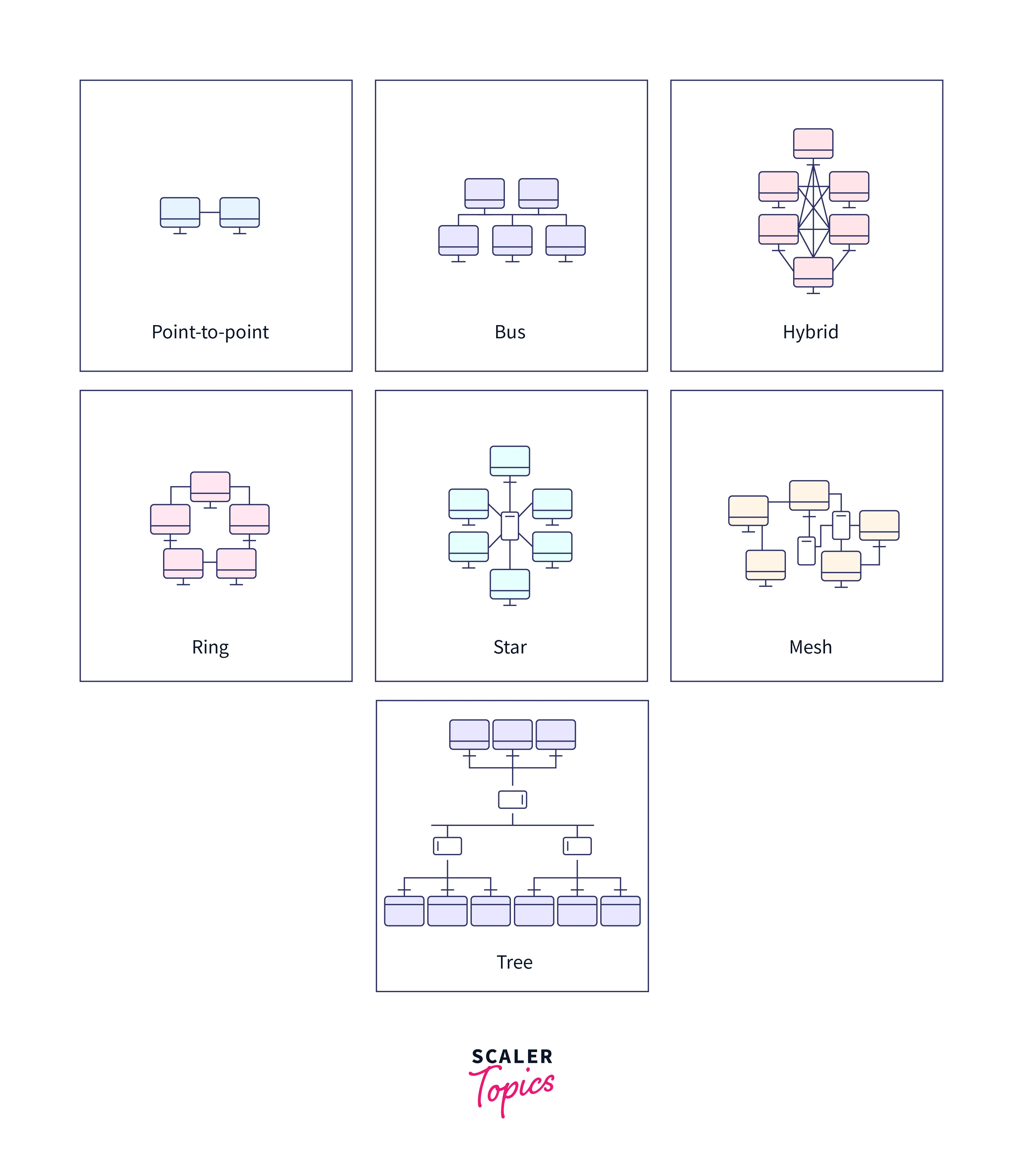
a. Layer 1: Physical
- The Physical layer is the first and bottom layer of the OSI model.
- It converts data into a stream of bits and transmits them over the physical network medium.
- It defines the physical characteristics of the network, such as the type of cable, connectors, and signaling methods used to transmit data.
- This layer establishes, maintains, and terminates physical connections between network devices.
- This layer in DevOps networking uses various communication channels, including copper wires, Wi-Fi, Bluetooth, and fiber optic cables.
- Topologies used at this layer include point-to-point, bus, star, mesh, and ring.
- This layer uses techniques such as encoding, modulation, and error detection and correction, to minimize the effects of interference and noise.
- Some protocols used in the layer include Ethernet, Wi-Fi, Bluetooth, USB, and HDMI.
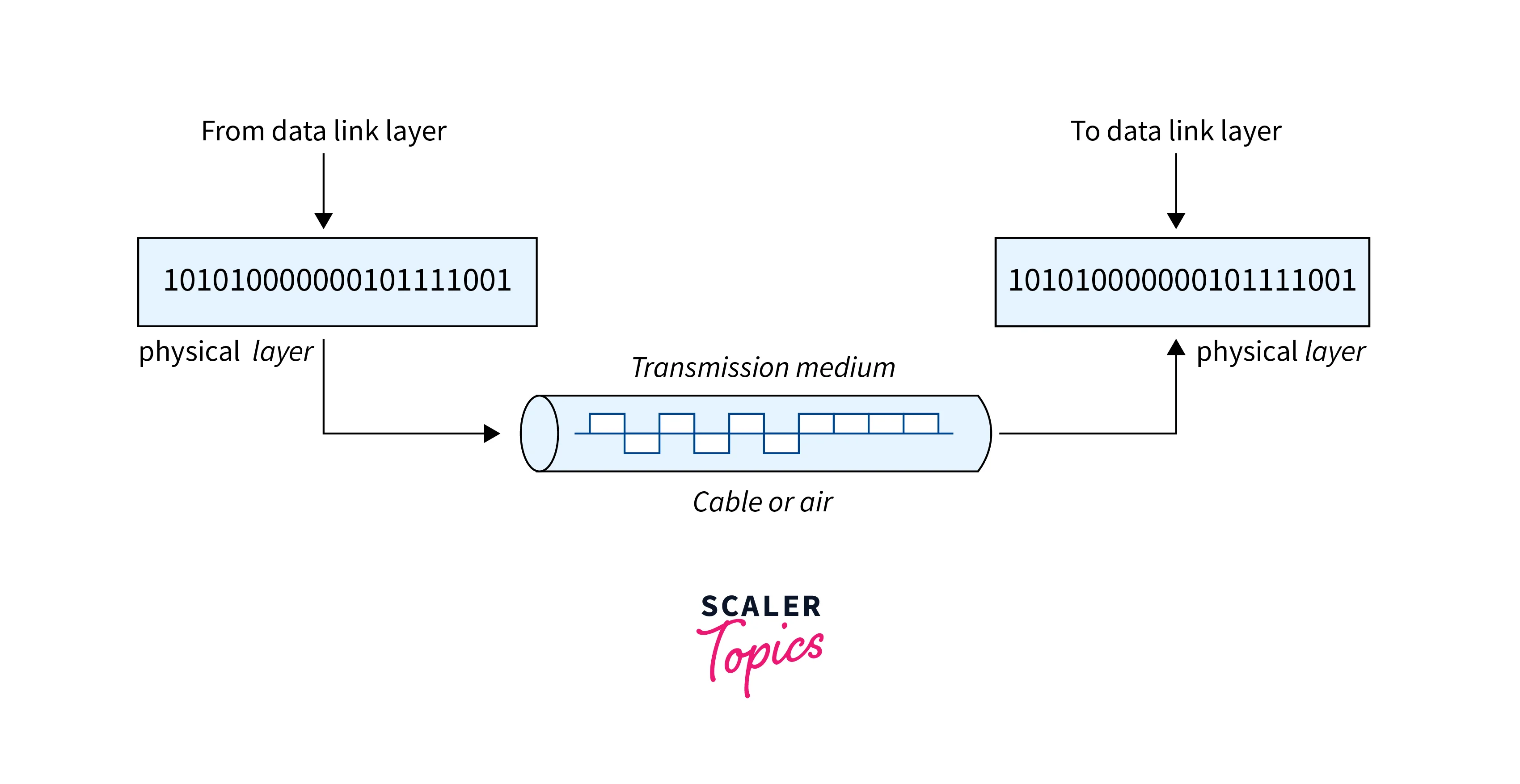
b. Layer 2: Data Link
- The Data Link layer is the second layer in the OSI model.
- It is responsible for providing error-free transfer of data frames between devices on the same network segment.
- It layer breaks down the data received from the Network layer into frames and adds a header and trailer to each frame, which contains control and addressing information.
- The Data Link layer transmits data over a local network and uses physical addresses (MAC addresses) to identify devices on the same network segment.
- This layer in DevOps networking provides services such as framing, error detection, and flow control to ensure the reliable transmission of data frames.
- Topologies used at this layer include point-to-point and broadcast.
- The protocols used in the layer include Ethernet, Token Ring, and FDDI.
- The medium used in this layer includes twisted pair copper wire, coaxial cable, and fiber optic cable.
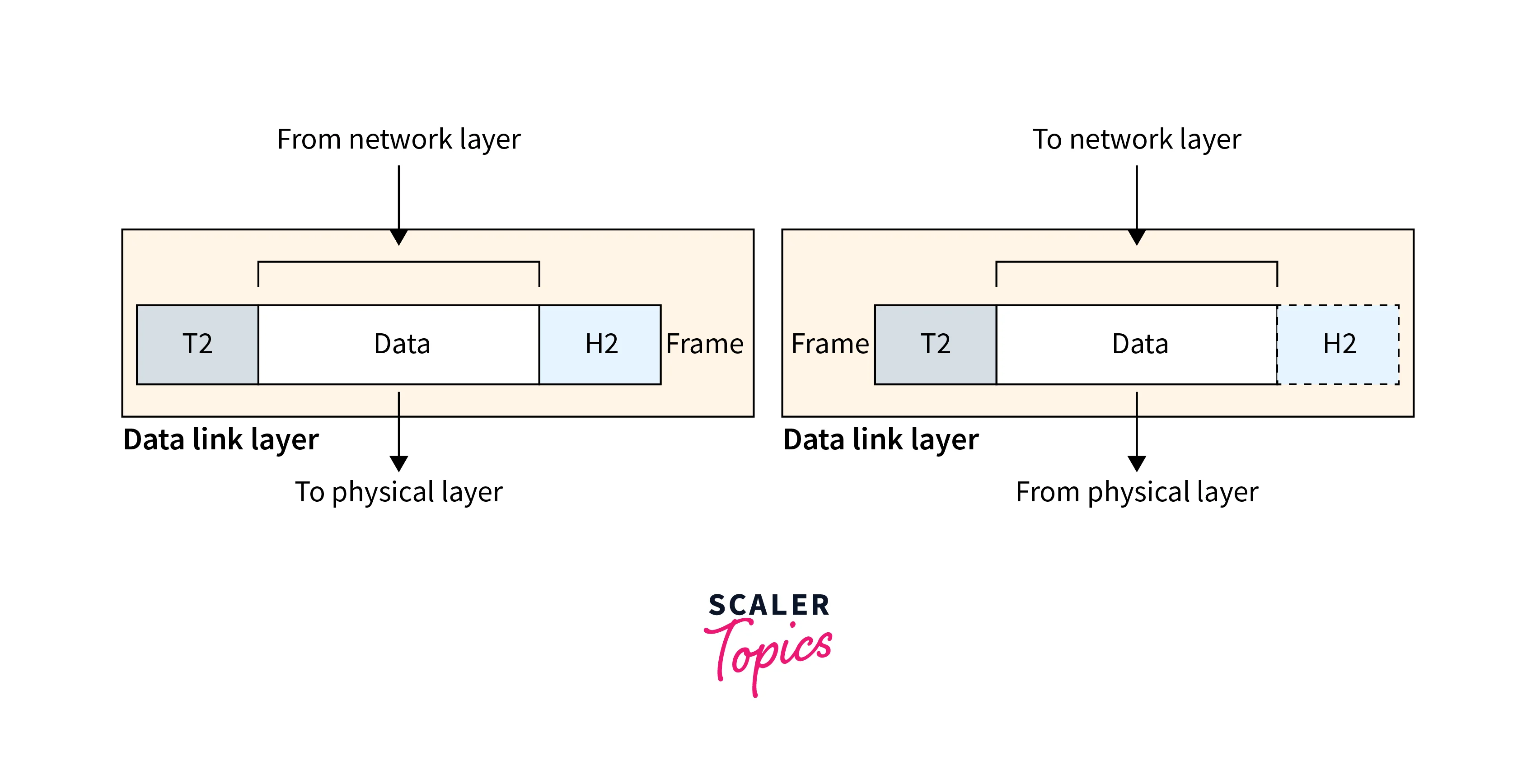
c. Layer 3: Network
- The Network layer is the third layer in the OSI model.
- It is responsible for logically addressing and routing the data between different networks. Logical addressing is a method to identify a device or network node on a network.
- The function of this layer is to provide end-to-end communication between two hosts on different networks.
- This layer in DevOps networking receives data from the upper layers and adds a header that contains logical addressing information, such as IP addresses.
- The protocols used at this layer include Internet Protocol (IP), Internet Control Message Protocol (ICMP), and Internet Group Management Protocol (IGMP).
- The medium used at this layer includes routers and switches.
- The primary task of this layer is to provide routing services and enable data packets to travel across different networks using various routing algorithms.
- This layer helps manage congestion control by monitoring the network and managing the flow of data packets.
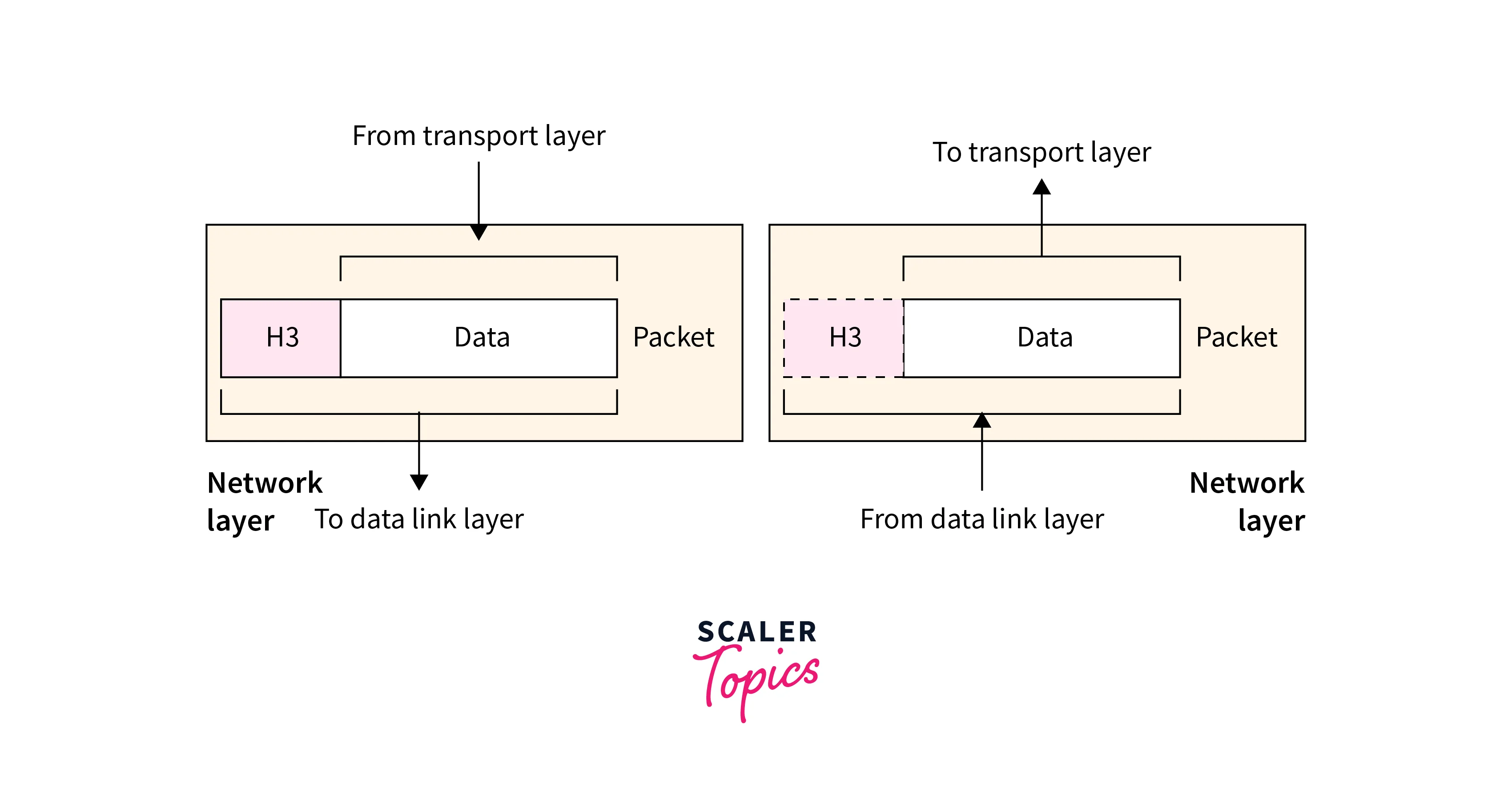
d. Layer 4: Transport
- The Transport layer is the fourth layer in the OSI Model.
- The function of this layer is to provide reliable end-to-end delivery of data between applications or hosts on different networks.
- This layer in DevOps networking takes the data segments received from the Session layer and breaks them down into smaller units, called packets, for transmission over the network.
- The layer is responsible for regulating the flow of data and controlling congestion, thereby preventing network overload.
- The medium used in this layer can be copper cables, fiber optic cables, or wireless communication.
- Some of the commonly used protocols in this layer are Transmission Control Protocol (TCP), User Datagram Protocol (UDP), and Stream Control Transmission Protocol (SCTP).
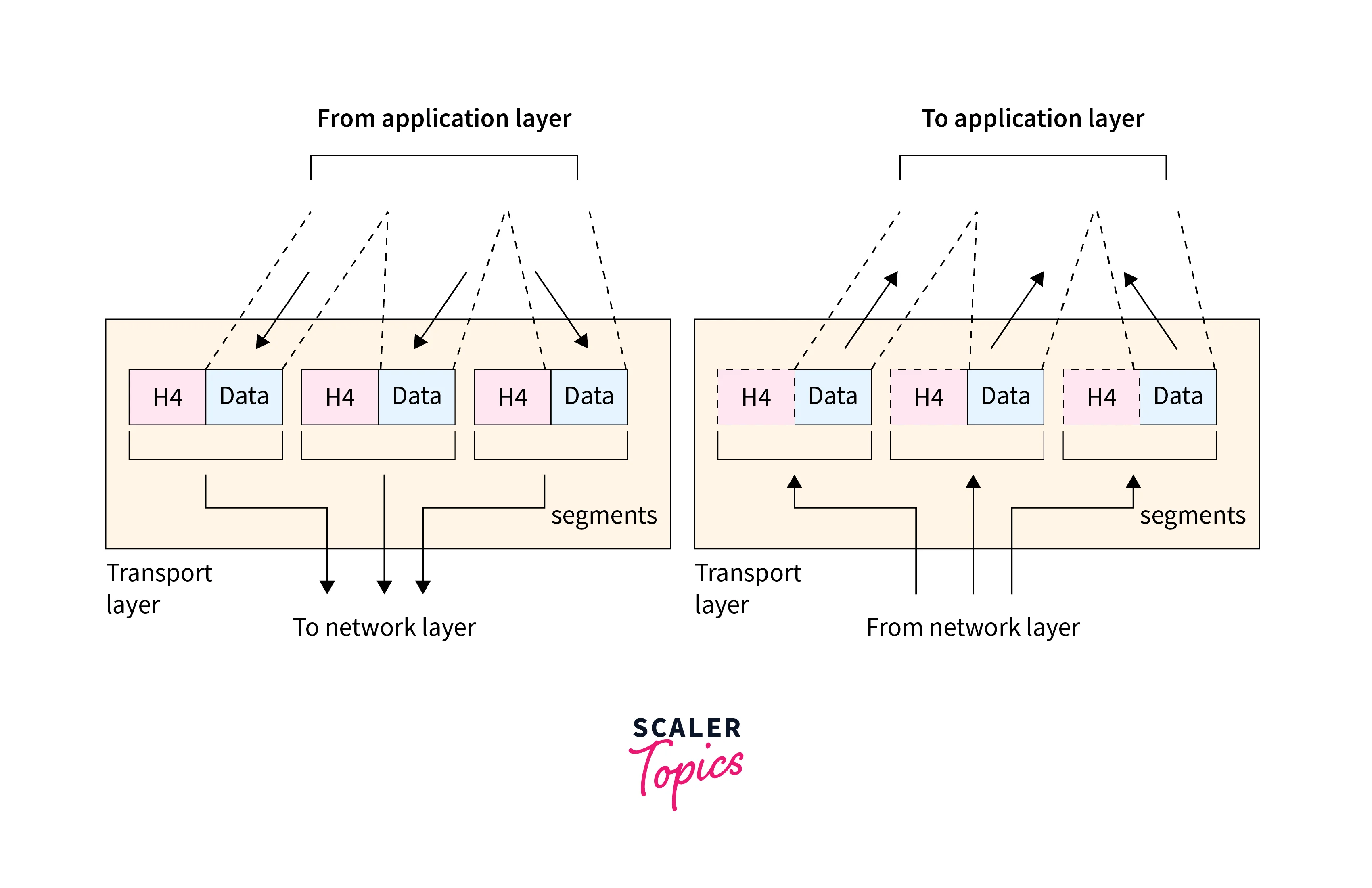
e. Layer 5: Session
- The Session layer is the fifth layer of the OSI model.
- It establishes and manages sessions between applications on different devices.
- The Session layer in DevOps networking maintains the session state, keeping track of the conversation and data exchange.
- It allows for synchronized data exchange and recovery from communication failures.
- It may provide encryption, compression, and checkpoints to ensure the integrity of session data.
- It interacts with the Presentation and Transport layers.
- Protocols used in this layer are NetBIOS, RPC, and SQL.
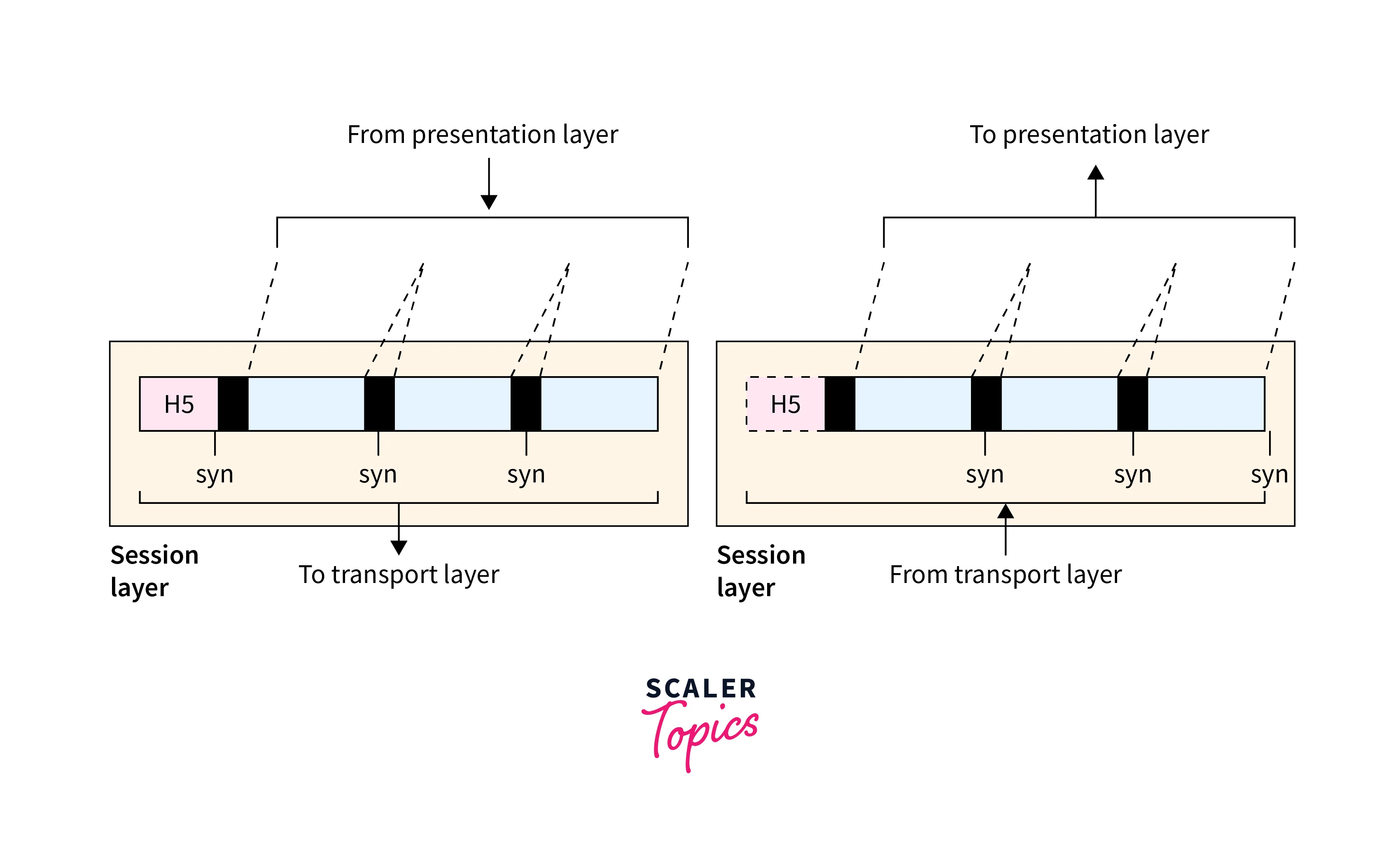
f. Layer 6: Presentation
- The Presentation layer is the sixth layer of the OSI model, located between the Session and Application layers.
- Its primary function is to ensure that data exchanged between applications is presented in a standardized format, regardless of the underlying data format used by the applications.
- This layer performs data transformation, converting data from one format to another to ensure compatibility between applications.
- This layer in DevOps networking also performs encryption and decryption of data, thereby enabling secure data transmission over unsecured networks.
- Compression and decompression of data is another function of this layer, reducing the size of data to be transmitted and saving network bandwidth.
- Protocols used in this layer are JPEG, GIF, MPEG, ASCII, and EBCDIC.
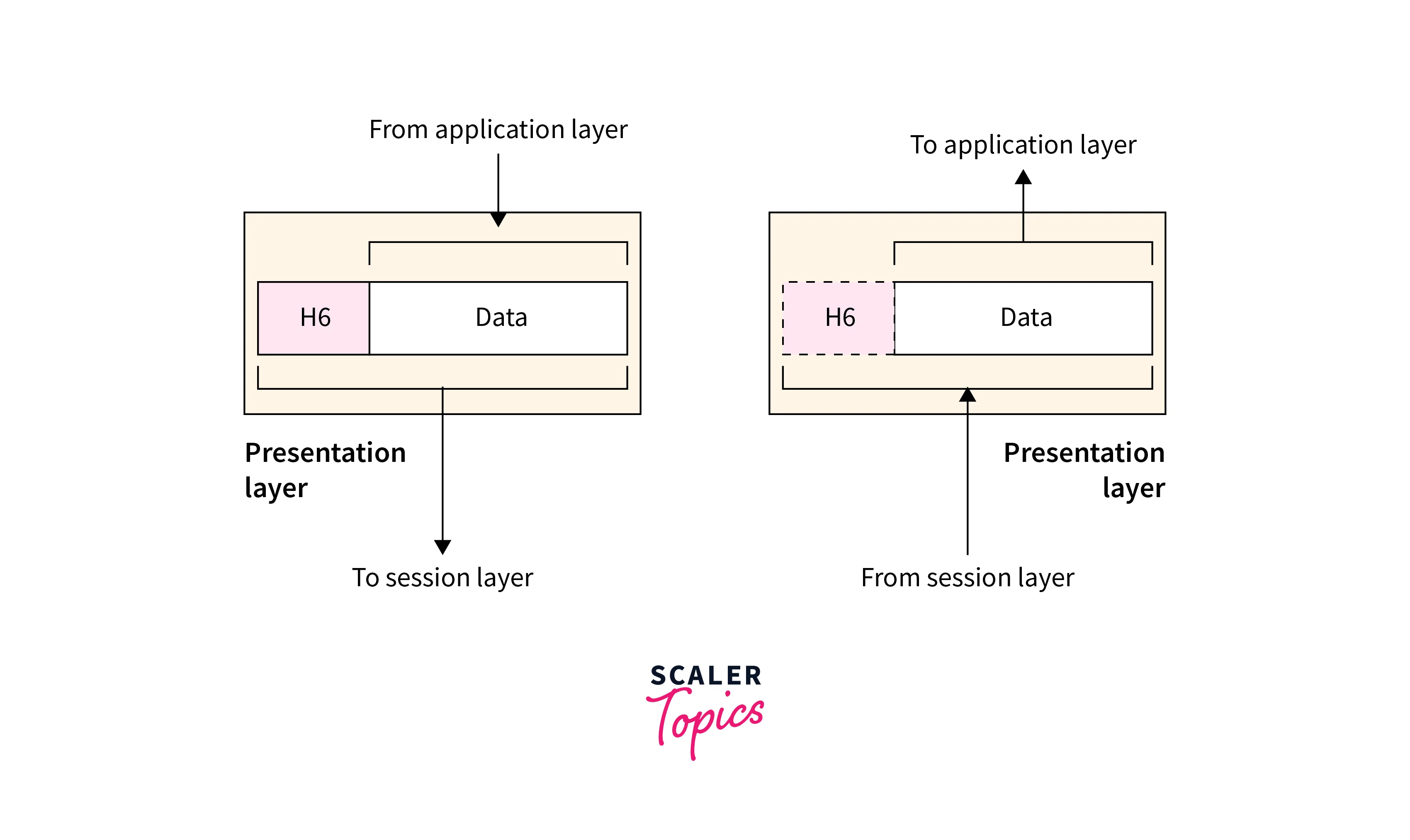
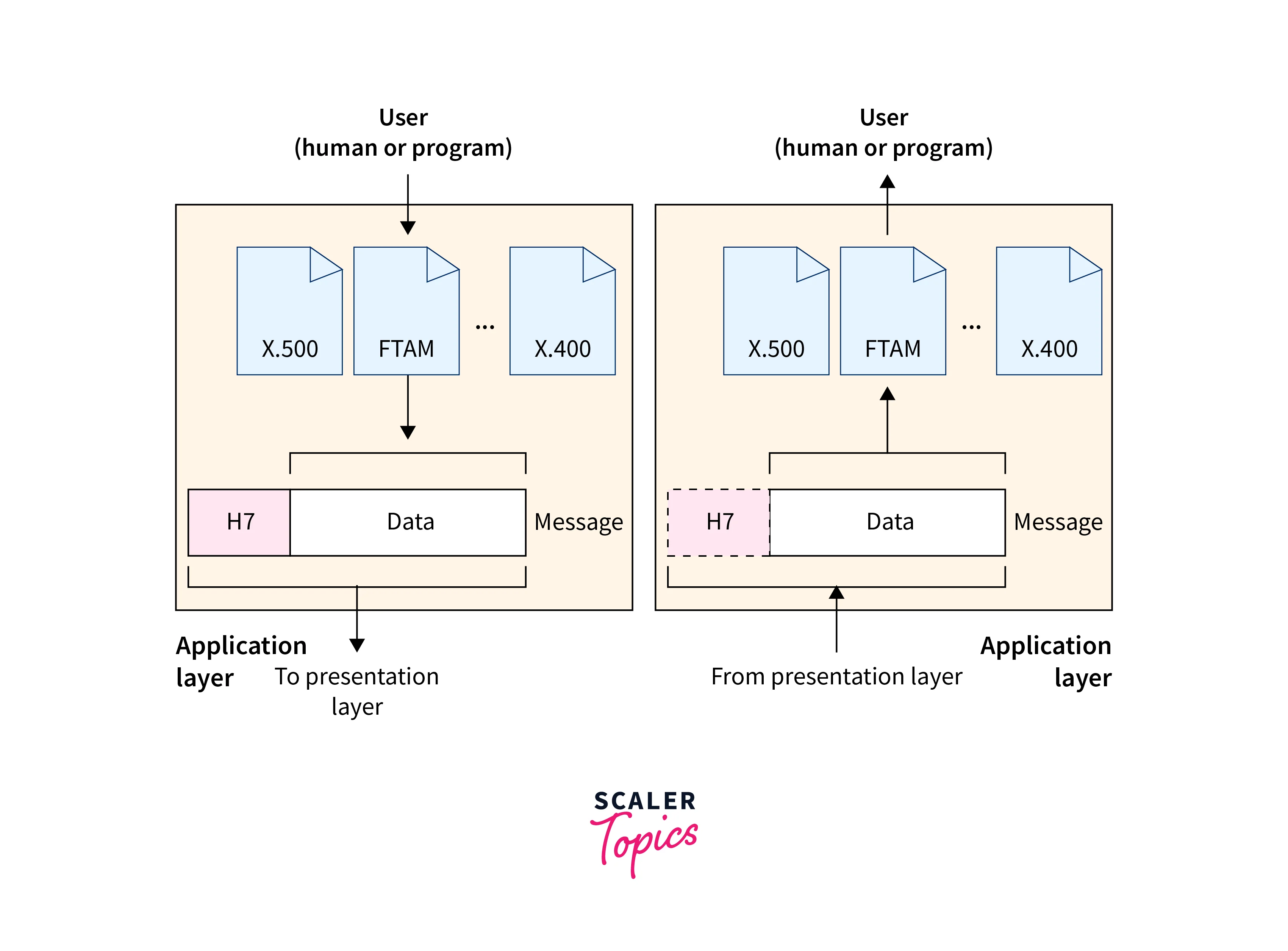
g. Layer 7: Application
- The Application layer is the top layer in the OSI model.
- In this layer, user applications interact with the network.
- Its primary function is to provide a user interface and services that allow applications to exchange information with other devices on the network.
- This layer in DevOps networking supports a range of network applications, including email, web browsing, file transfer, and remote access.
- Applications at the top layer use standardized protocols such as HTTP, FTP, SMTP, and Telnet to communicate with each other.
- This layer handles application-specific functions like message formatting, file compression, and user authentication.
- It interacts with all the lower layers to transmit data across the network.
Understanding the OSI model and its seven layers is essential for a professional working in DevOps networking. Here is an image for a better understanding:
TCP/IP
TCP/IP is a set of communication protocols that allow computers to communicate over the internet.
a. What is TCP/IP, and How is it Different from OSI?
TCP/IP
TCP/IP is the most widely used networking protocol suite in DevOps networking. It provides a reliable, connection-oriented communication model for transmitting data between devices.
Here are some salient points about TCP/IP:
- TCP/IP is a combination of two protocols:
- TCP, which provides reliable and ordered delivery of data, and
- IP that provides routing and addressing capabilities.
- TCP/IP is responsible for breaking data into packets, routing those packets to their destination, and reassembling them into their original form.
- It is a four-layered model, and the four layers are:
- Network Interface Layer:
This layer transmits data over a physical network, including hardware addressing, error detection, and media access control. - Internet Layer:
The responsibility of this layer is to address and route data packets among devices situated on distinct networks. - Transport Layer:
Provides end-to-end data transport services, including error detection, flow control, and congestion control. - Application Layer:
This layer deals with the protocols and processes that applications use to communicate with each other over the internet.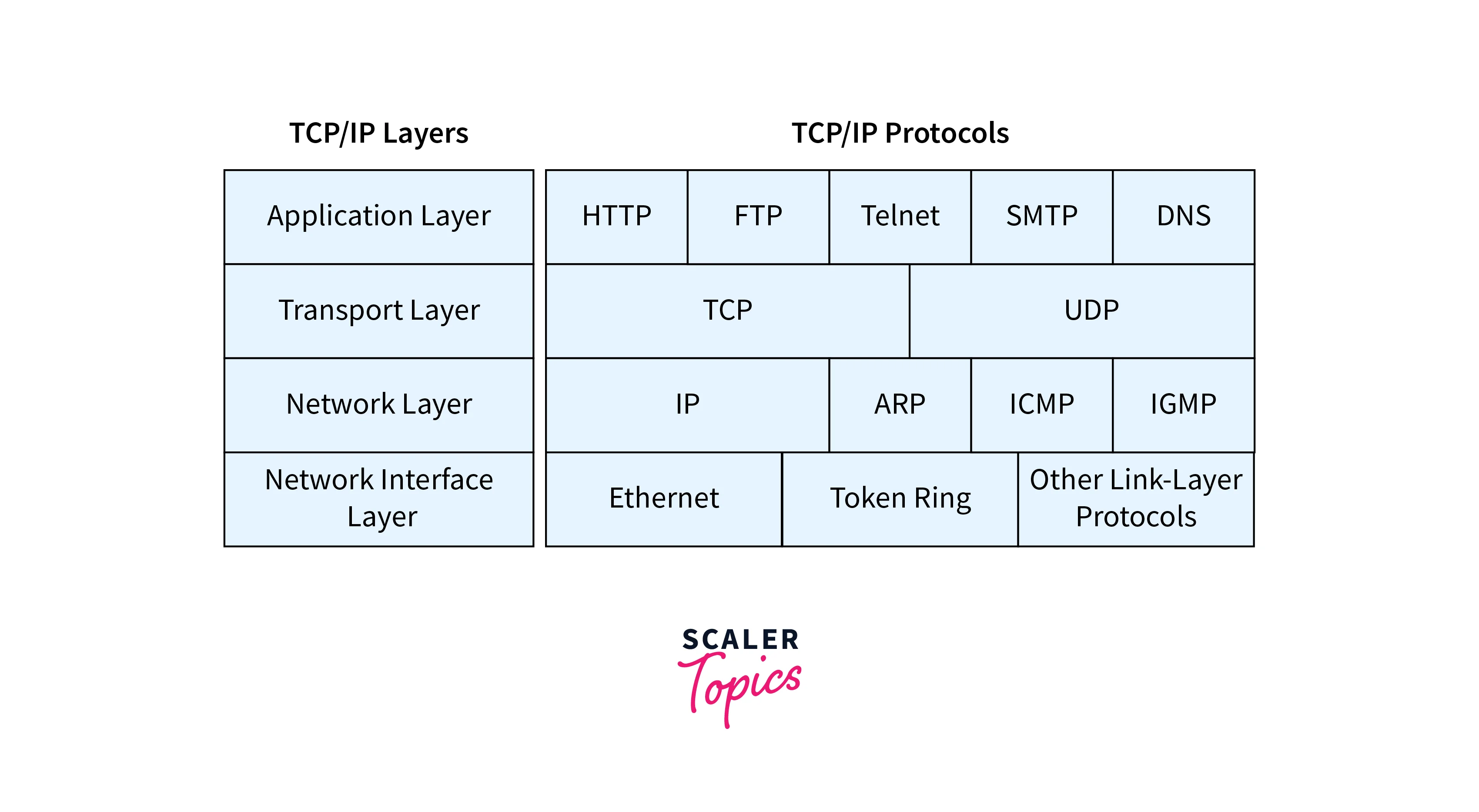
- Network Interface Layer:
Difference between TCP/IP and OSI Model:
In DevOps networking, while both TCP/IP and OSI are used to facilitate communication between computer systems, there are differences between the two models.
- Number of Layers:
- TCP/IP has four layers, while OSI has seven layers.
- Functionality:
- The layers in TCP/IP are more focused on specific tasks, while the layers in OSI are more generalized.
- Implementation:
- TCP/IP is a practical implementation of networking protocols, while OSI is more of a theoretical framework.
- Widely Used:
- TCP/IP is a suite of protocols used for communication over the internet, while OSI is a conceptual model that describes the communication between different systems in a network.
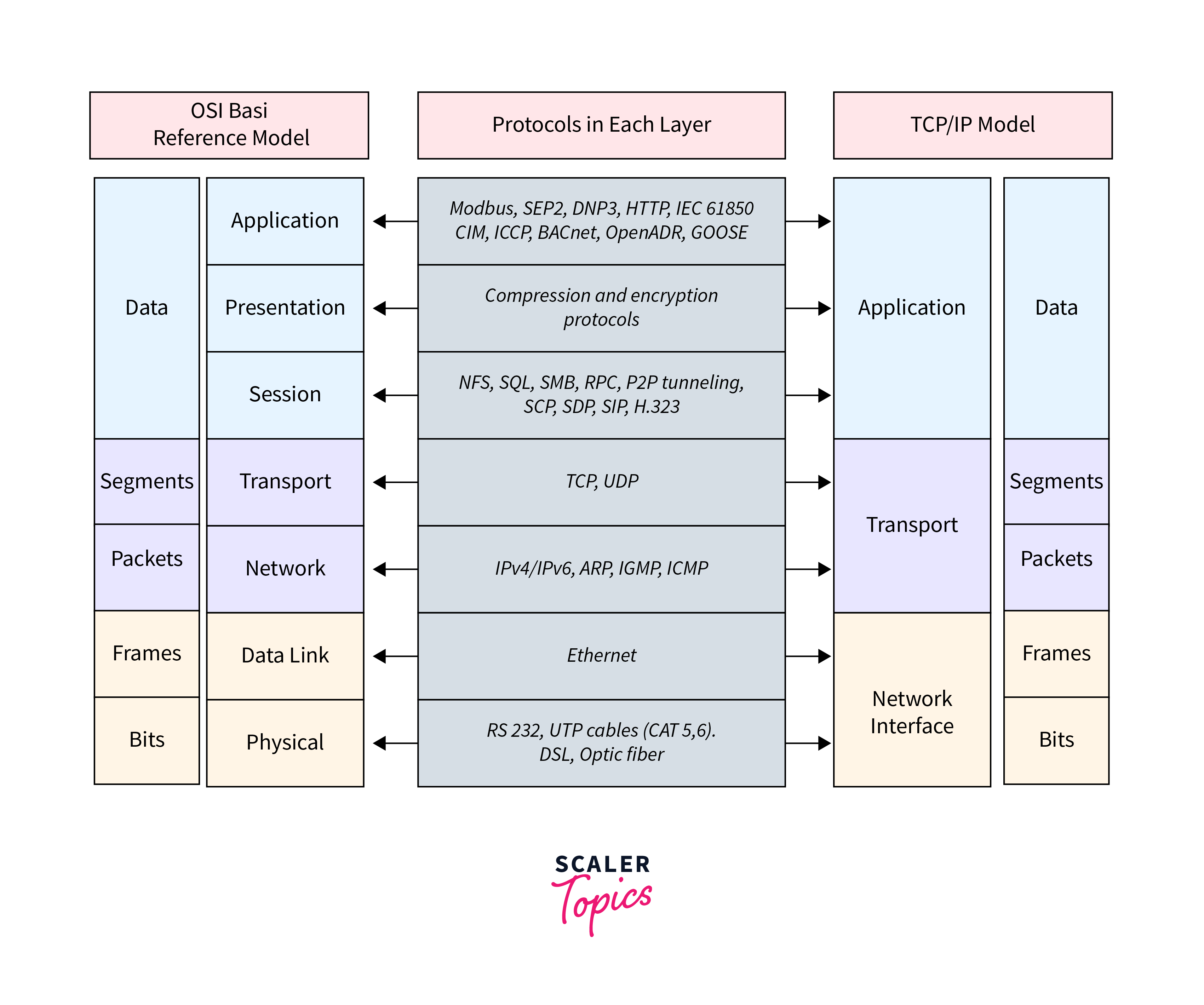
- TCP/IP is a suite of protocols used for communication over the internet, while OSI is a conceptual model that describes the communication between different systems in a network.
b. TCP versus UDP
TCP and UDP are two widely used transport layer protocols in DevOps networking. While both are responsible for delivering data between applications, they differ significantly in how they operate. Here are some of the main differences between TCP and UDP:
- Connection-Oriented vs. Connectionless
- TCP is a connection-oriented protocol. It establishes a reliable and secure connection between two endpoints before exchanging data. It ensures that data is transmitted without errors and in the correct order.
- In contrast, UDP is a connectionless protocol. It does not establish a dedicated connection before sending data. Rather than ensuring the delivery of data packets to the recipient, UDP transmits them without any guarantees about their successful delivery.
- Reliability vs. Speed
- TCP ensures reliable data delivery through mechanisms like error detection, flow control, and retransmission, but this can slow down transmission.
- UDP prioritizes speed over reliability, lacking mechanisms for error detection or retransmission, resulting in lost or out-of-order packets, but enabling faster data transmission than TCP.
- Suitability for Connection and Data Size
- TCP is suited for long-lived connections with a small amount of data sent in single bursts.
- UDP, for short-lived connections with a huge amount of data sent in a single burst.
- Acknowledgment and Retransmission
- The receiver acknowledges TCP segments and requests their retransmission if not received.
- UDP does not guarantee packet delivery or retransmission.
- Flow and Congestion Control
- In DevOps networking, TCP uses flow and congestion control mechanisms to prevent network congestion and ensure reliable data transmission, while UDP does not.
- Usage Scenarios:
- TCP, for applications that require reliable and ordered delivery of packets, such as email, file transfer, and web browsing.
- UDP, for applications that can tolerate packet loss, such as video streaming and online gaming.
c. Ports and Protocols
In DevOps networking, ports and protocols identify different applications and services on a network.
Ports
A port is a communication endpoint for identifying specific applications and services running on a device by network protocols.
In DevOps networking, this is what you need to know about ports:
-
Ports can be blocked or opened using firewall rules to control network traffic and improve security.
-
Port scanning is a technique to identify open ports on a device or network.
-
The numbering of ports ranges from 0 to 65535. There is a division of ports into three ranges:
- Well-known ports (0-1023)
- Registered ports (1024-49151)
- Dynamic or private ports (49152-65535)
-
Well-known ports are typically associated with services or applications, while, for temporary purposes, we use dynamic or private ports.
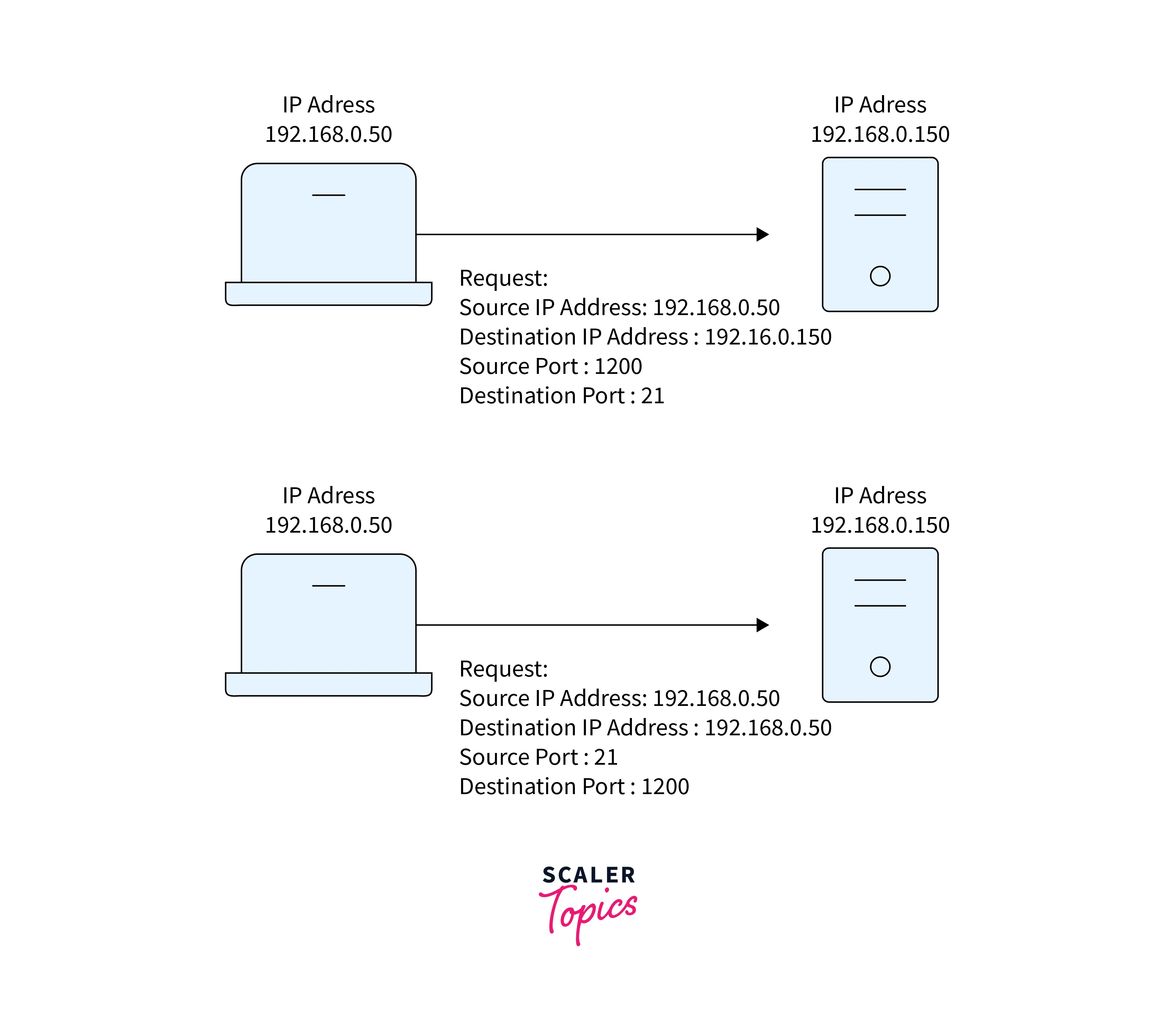
-
Well-known ports and protocols used in DevOps networking include:
Protocols Ports HTTP 80 HTTPS 443 SSH 22 FTP 20/21 SMTP 25 DNS 53 DHCP 67/68 MySQL Database 3306
Protocols:
-
A protocol is a set of rules governing the communication between devices on a network.
-
Some commonly used protocols in DevOps networking include:
Protocol Description HTTP Hypertext Transfer Protocol is used for transmitting data between a client and a server. It is the foundation of data communication on the World Wide Web. HTTPS Hypertext Transfer Protocol Secure is a more secure version of HTTP that uses SSL/TLS encryption to protect data in transit. TCP TCP is a reliable, connection-oriented protocol that provides error detection and recovery mechanisms. UDP UDP is a connectionless protocol that provides fast and unreliable data transmission. DNS Domain Name System is a protocol for resolving domain names into IP addresses. It enables users to access websites using easy-to-remember domain names instead of numeric IP addresses. SMTP SMTP is a protocol for sending email messages between servers. SSH Secure Shell is a protocol for secure remote server access. It provides encrypted communication between a client and a server, preventing eavesdropping and tampering.
In summary, ports and protocols are crucial components of DevOps networking that facilitate communication between devices.
IP Subnetting, CIDR
IP Subnetting:
Subnetting means dividing a relatively large network into smaller subnetworks, or subnets. It involves creating subnets with their unique network addresses and configuring them to work together as a single network.
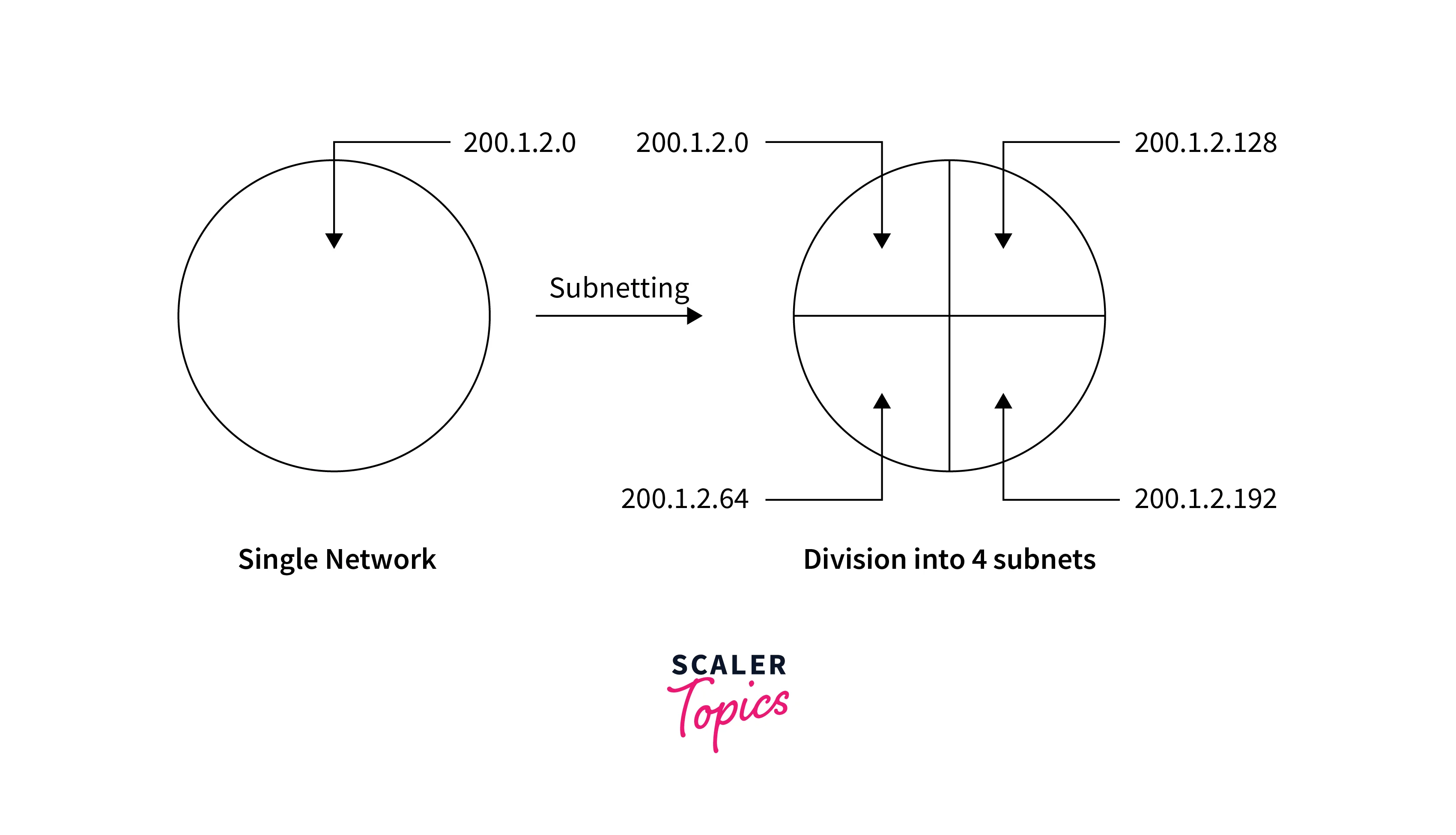
Subnetting is essential in DevOps networking because it helps in the following ways:
- Allocating IP addresses efficiently
- Dividing a network into smaller subnets enables more efficient assignment of IP addresses, reducing the wastage of addresses.
- Enhancing network security
- Subnetting can help improve network security by isolating sensitive resources and limiting access.
- Improving network performance
- Dividing a network into smaller subnets enables more efficient traffic management. Thus, reducing network congestion and enhancing network performance.
In IP addressing, the host portion refers to the part of the IP address used to identify a specific device within a network. The network portion of an IP address identifies the network to which the device is connected.
Here are some key concepts related to IP subnetting in DevOps networking:
- Subnet mask:
- The subnet mask is a numerical value that identifies network and host portions of an IP address. It consists of 32 bits and establishes the boundaries of the network and the devices that belong to it.
- The representation of a subnet mask is similar to that of an IP address.
- For example, a subnet mask of 255.255.255.0 indicates that the first three octets represent the network portion of the address, while the last octet represents the host portion.
- Network ID:
- The network ID is part of an IP address that identifies the network to which the host belongs.
- Applying the subnet mask to the IP address gives us the network address.
- For example, for the IP address 192.168.1.10 and the subnet mask 255.255.255.0, the network ID is 192.168.1.0.
- Host ID:
- The host ID portion of an IP address specifies the particular device on a network.
- To obtain it, take the IP address and apply a mask to remove the network ID.
- E.g., the host ID is 0.0.0.10 for the IP address 192.168.1.10 and the subnet mask 255.255.255.0.
- CIDR notation:
- CIDR (Classless Inter-Domain Routing) notation is a shorthand method of representing the subnet mask.
- It consists of the IP address followed by a slash (/) and the number of bits in the subnet mask.
- E.g., 192.168.1.0/24 represents a network with a subnet mask of 255.255.255.0.
CIDR:
In DevOps networking, CIDR is a method used to allocate and manage IP addresses more efficiently. Below is a brief explanation:
- CIDR enables variable-length subnet masks to create subnets of different sizes within a network.
- CIDR, denoted by a slash followed by a number, determines the network portion of an IP address using the subnet mask. For example, a subnet mask of /24 would create a network with 256 addresses, while a subnet mask of /25 would result in a network with 128 IP addresses.
- CIDR helps to conserve IP addresses by allowing organizations to create smaller subnets, which can be allocated to devices only as needed, rather than assigning larger blocks of IP addresses that may go unused.
- CIDR also enables easier route summarization, thus reducing the size of routing tables and improving network performance.
- CIDR calculates the number of hosts and networks available in a subnet.
The following table shows some common CIDR notations and their corresponding subnet masks:
| CIDR Notation | Subnet Mask | Total Hosts | Usable Hosts | Networks |
|---|---|---|---|---|
| /24 | 255.255.255.0 | 256 | 254 | 1 |
| /20 | 255.255.240.0 | 4,096 | 4,094 | 16 |
| /16 | 255.255.0.0 | 65,536 | 65,534 | 256 |
| /8 | 255.0.0.0 | 16,777,216 | 16,777,214 | 256 |
In DevOps networking, CIDR is used with IP subnetting to create efficient and scalable network architectures.
Routing
Routing is a crucial aspect of networking that sends data packets from one network to another.
In a DevOps networking context, routing ensures network traffic is routed efficiently between different networks. Below are some key points to understand routing:
- Routers are the devices that perform routing in a network.
- Routers use routing tables to determine the best path for a packet.
- A routing table has network prefixes and their associated next-hop addresses. The next-hop address is the IP address of the next router on the path to the destination network.
- Routing also helps load balancing, where network traffic is distributed across multiple paths to avoid congestion and ensure smooth network operation.
- Another aspect of routing in DevOps networking is static and dynamic routing.
- In static routing, routes are manually configured and do not change unless explicitly modified.
- In dynamic routing, routing protocols automatically determine the routes based on network topology and traffic conditions, unlike static routing, where we manually configure routes.
- Routing has two types: interior routing and exterior routing.
- Interior routing protocols include OSPF, EIGRP, and RIP.
- While BGP is an example of an exterior routing protocol.
- Internet service providers use Border Gateway Protocol (BGP) to exchange routing information between various networks. BGP allows for dynamic routing.
In summary, routing is a critical component of DevOps networking, as it helps determine the best path for network traffic, load balancing, and dynamic routing.
Domain Name System (DNS)
DNS is a hierarchical and decentralized naming system for computers, services, or other resources connected to the internet or a private network.
It is like a phonebook, converting human-readable domain names like google.com into IP addresses like 172.217.6.14, which computers use to identify each other.
a. DNS Overview
DNS is responsible for translating domain names into IP addresses, which computers can understand and use to communicate with each other.
Here are some crucial points to know about DNS:
- DNS is a distributed database that contains information about domain names and their associated IP addresses.
- When a user types a domain name into their web browser, the browser requests a DNS resolver to find the corresponding IP address.
- The DNS resolver then checks its cache for the IP address. If it does not have the IP address, it sends a request to a root server.
- The root server responds with the address of a top-level domain (TLD) server, which the DNS resolver then queries for the IP address of the domain name you entered.
- In DevOps networking, DNS operates at the application layer of the OSI model and uses the client-server model.
In summary, DNS is a critical component in DevOps networking. DNS can also be a target for cyber attacks, and DevOps networking teams must implement appropriate security measures to protect against DNS-based attacks.
b. Domains, Zones, and Delegation
Domains, Zones, and Delegation are significant concepts in DevOps networking, particularly in the Domain Name System (DNS). Below we have a detailed overview of each of these concepts:
-
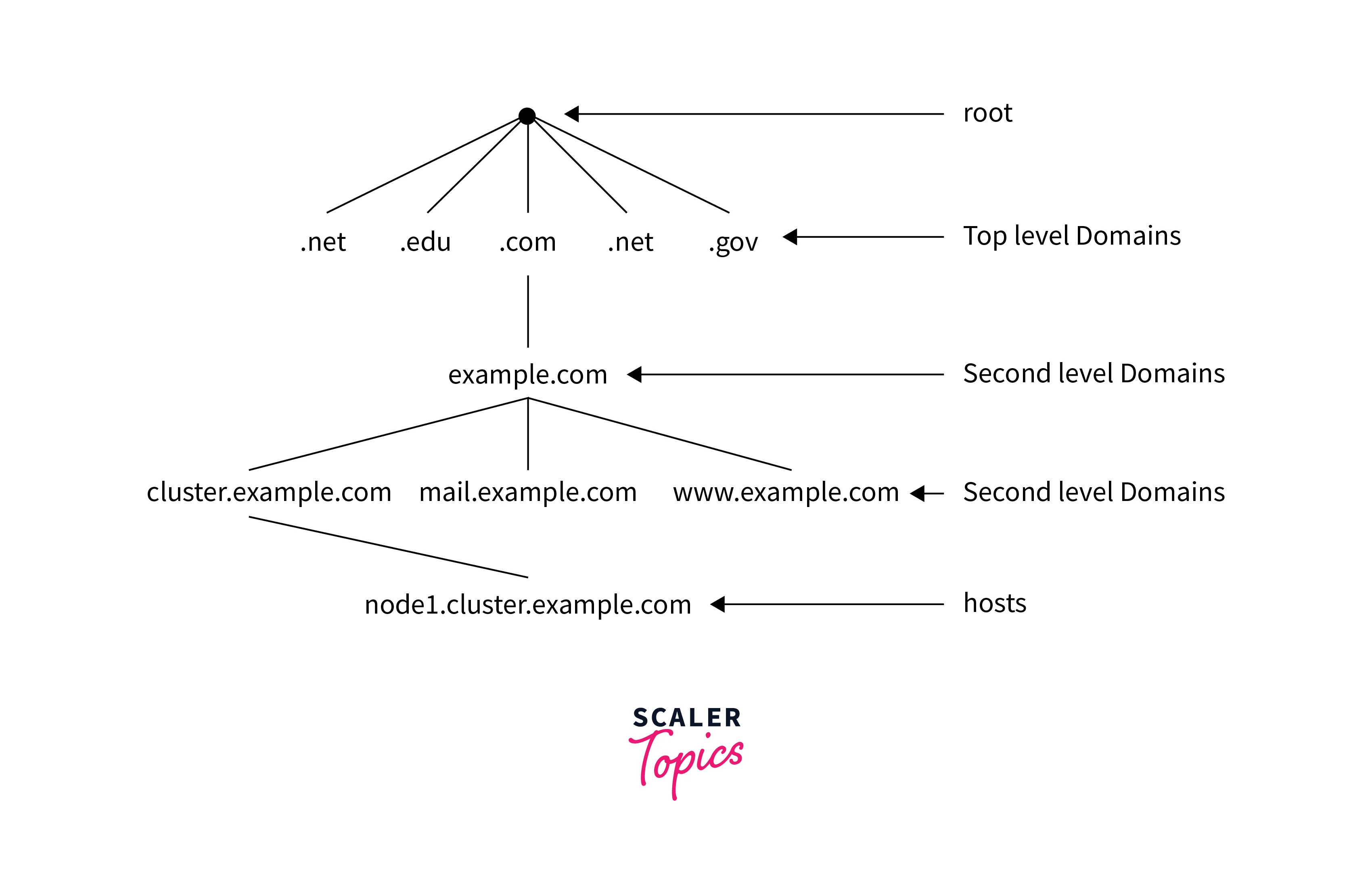
Domains:
- Domains are a hierarchical way of organizing resources in a network.
- A domain name, such as example.com, represents a website or online service and can be subdivided into subdomains like blog.example.com or store.example.com to categorize or specify the services provided by the domain.
- DNS maps domains to IP addresses.
-
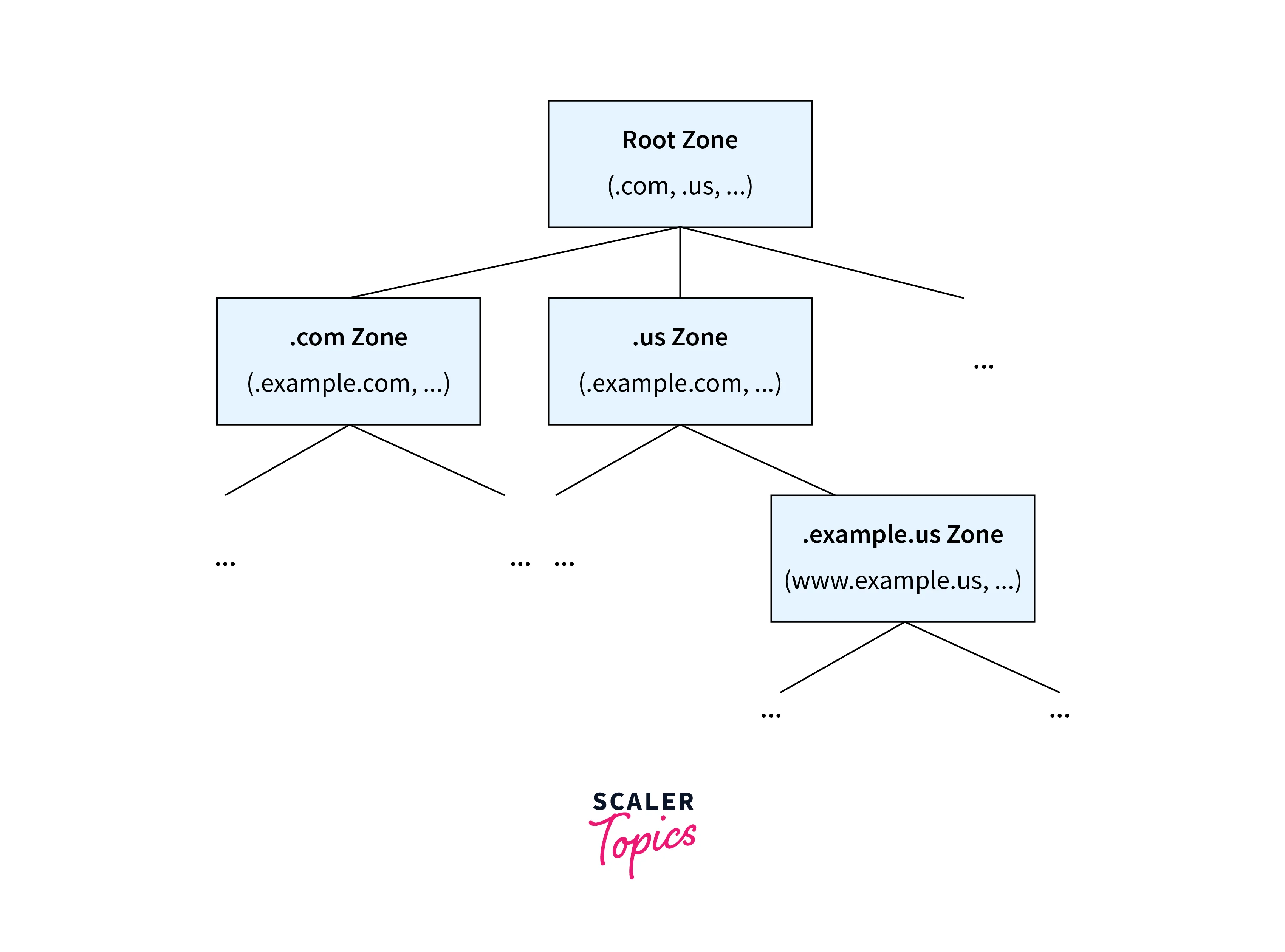
Zones:
- Zones are a contiguous portion of the DNS namespace managed by a single entity, such as an organization or a DNS server.
- In DevOps networking, a domain name identifies each zone that stores information about the domain, including its authoritative name servers, mail servers, and other details.
- A zone can contain multiple domain names.
-
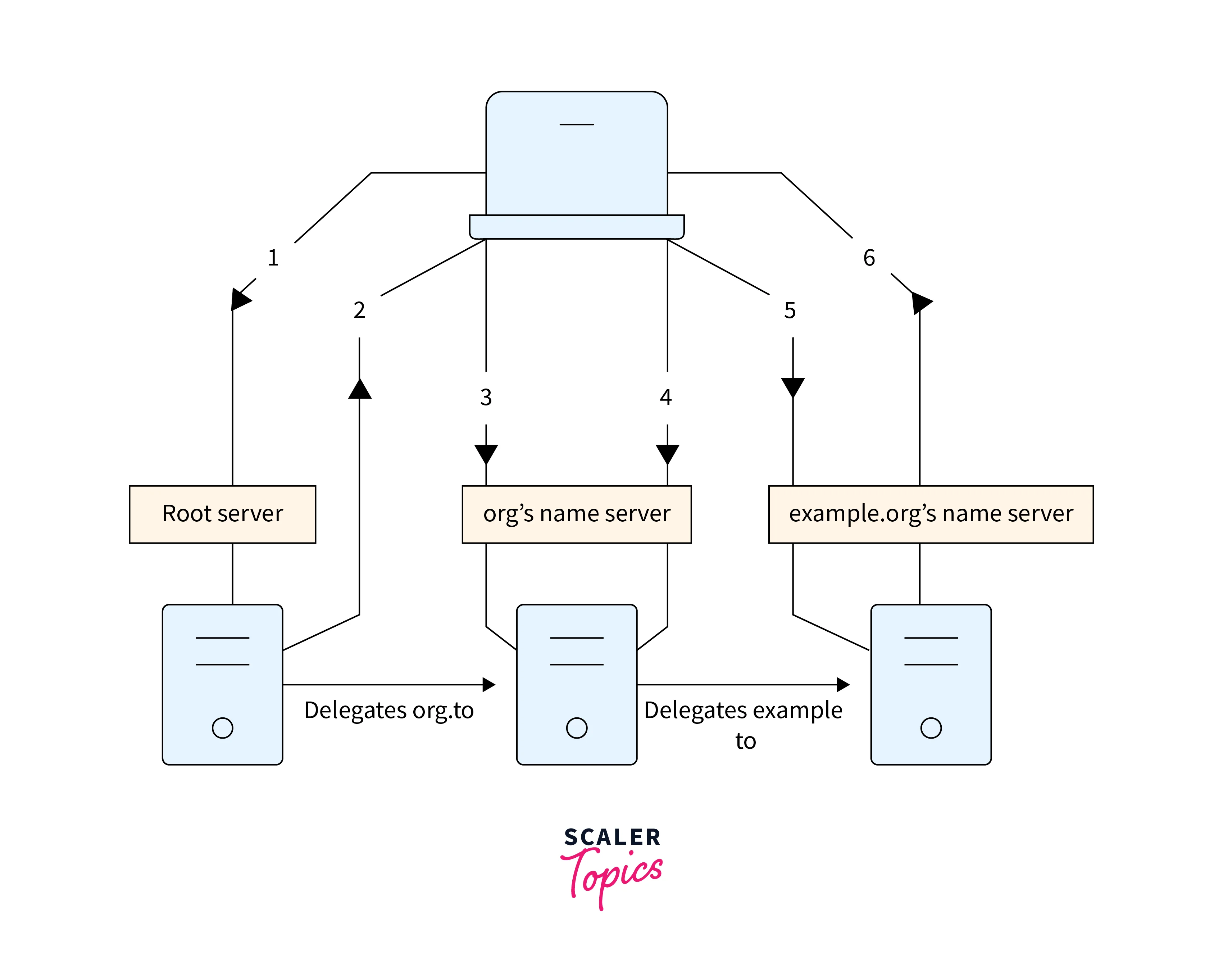
Delegation:
- Delegation means transferring the responsibility for managing a subdomain to another DNS server.
- It is done when a domain owner wants to manage a subdomain on a separate server or delegate responsibility to a third-party provider.
In summary, domains, zones, and delegation are vital concepts in DNS and play a key role in organizing and managing resources on a network. Understanding these concepts is essential for effective DevOps networking.
c. DNS Record Types
DNS uses record types to store information about domain names and their associated IP addresses. The most common record types are:
| Record Type | Description |
|---|---|
| A | Maps a domain name to an IPv4 address |
| AAAA | Maps a domain name to an IPv6 address |
| CNAME | Maps an alias name to a canonical name (another domain name) |
| MX | Maps a domain name to a mail exchange server |
| NS | Specifies the authoritative DNS server for the domain |
| SOA | Specifies authoritative information about a DNS zone, including the primary name server, the email of the domain administrator, the domain serial number, and several timers |
| TXT | Stores text-based information associated with a domain name |
| PTR | Maps an IP address to a domain name (reverse lookup) |
Consult the DNS server documentation and configuration guides to ensure specific applications use the correct record types,
In summary, DNS is a critical part of the internet infrastructure, providing a way to translate human-readable domain names into machine-readable IP addresses. Understanding DNS is essential for DevOps networking professionals as it plays a vital role in network communication and application delivery.
HTTP
In DevOps networking, HTTP (Hypertext Transfer Protocol) is a communication protocol that transmits data over the internet. It is the foundation of the World Wide Web and is responsible for how we interact with web pages.
a. HTTP Methods
In DevOps networking, HTTP Methods are the actions or operations performed on resources identified by URLs in the HTTP protocol. These HTTP methods specify how a client can interact with a web server to retrieve or manipulate information.
i. HTTP Request Methods
HTTP methods are a set of requests used to communicate with a web server. The methods specify what action to perform on a resource. The most common HTTP methods are the following:
- GET:
retrieves a resource from the server - POST:
submits data to be processed to a specific resource - PUT:
updates a resource on the server - DELETE:
removes a resource from the server - PATCH:
partially updates a resource on the server
b. HTTP Response Codes
HTTP response codes are a set of standardized codes that a web server returns to the client to indicate the success or failure of an HTTP request.
i. Categories of HTTP responses
In DevOps networking, One can group the response codes into categories that describe the type of response.
- 1xx: Informational responses
- These codes convey the request status. They indicate the server has received the request and is currently processing it.
- E.g., 100 Continue, 101 Switching Protocols
- 2xx: Success responses
- These codes signify the server has successfully received, understood and accepted the request.
- E.g., 200 OK, 201 Created, 204 No Content.
- 3xx: Redirection responses
- These codes tell the client she needs to take further action to complete the request.
- E.g., 301 Moved Permanently, 302 Found, 307 Temporary Redirect.
- 4xx: Client error responses
- Indicate client-side errors, such as a missing or incorrect parameter.
- E.g., 400 Bad Request, 401 Unauthorized,403 Forbidden, 404 Not Found.
- 5xx: Server error responses
- Indicate server-side errors, such as a server overload or internal server error.
- E.g., 500 Internal Server Error, 503 Service Unavailable.
These codes are often used for background communication between the client and server and are not as critical for users to be aware of. However, the browser displays error codes because they are vital for users to understand when something has gone wrong with their request.
The below image shows what an error 403 Forbidden looks like to the user:

c. HTTP Headers
In DevOps networking, HTTP headers are a critical component of the HTTP protocol for exchanging data between clients and servers. They provide important information about the client, server, and content transmitted, which is essential for handling the HTTP request and response messages.
Here are some rudimentary things to know about HTTP headers:
- An HTTP header is a piece of information that accompanies an HTTP request or response.
- It has a name-value pair separated by a colon (:), with one or more headers separated by a line break.
- There are four types of HTTP headers. Each of these headers serves a specific purpose in the HTTP protocol.
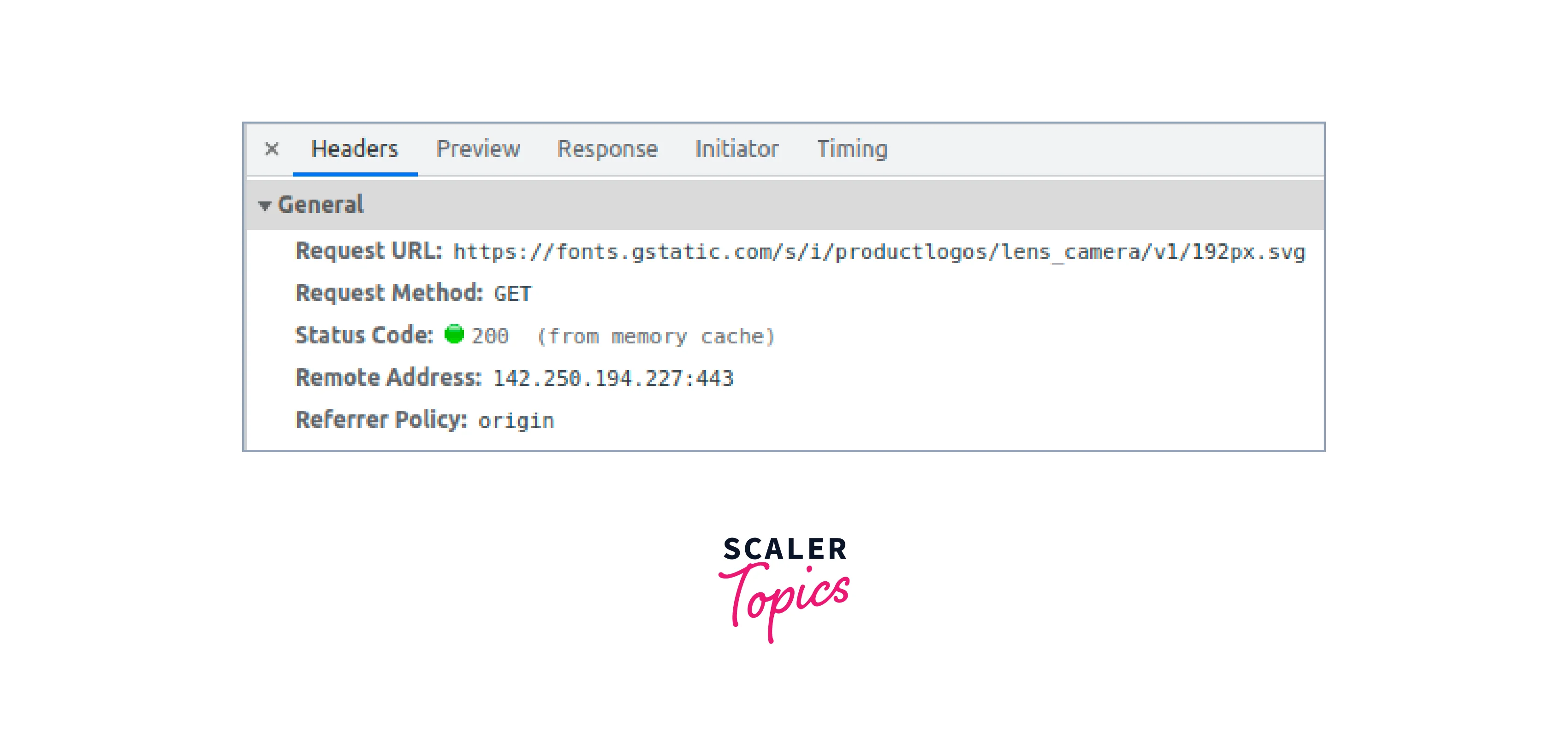
- General headers:
- These headers in HTTP provide general information about the message, such as the date and time of the sent message, and apply to both requests and responses.
- Examples include Request URL, Request Method, and Status Code.
- Request headers:
- These headers provide information about the client or the requested resource.
- Examples include User-Agent, Accept, and Authorization.
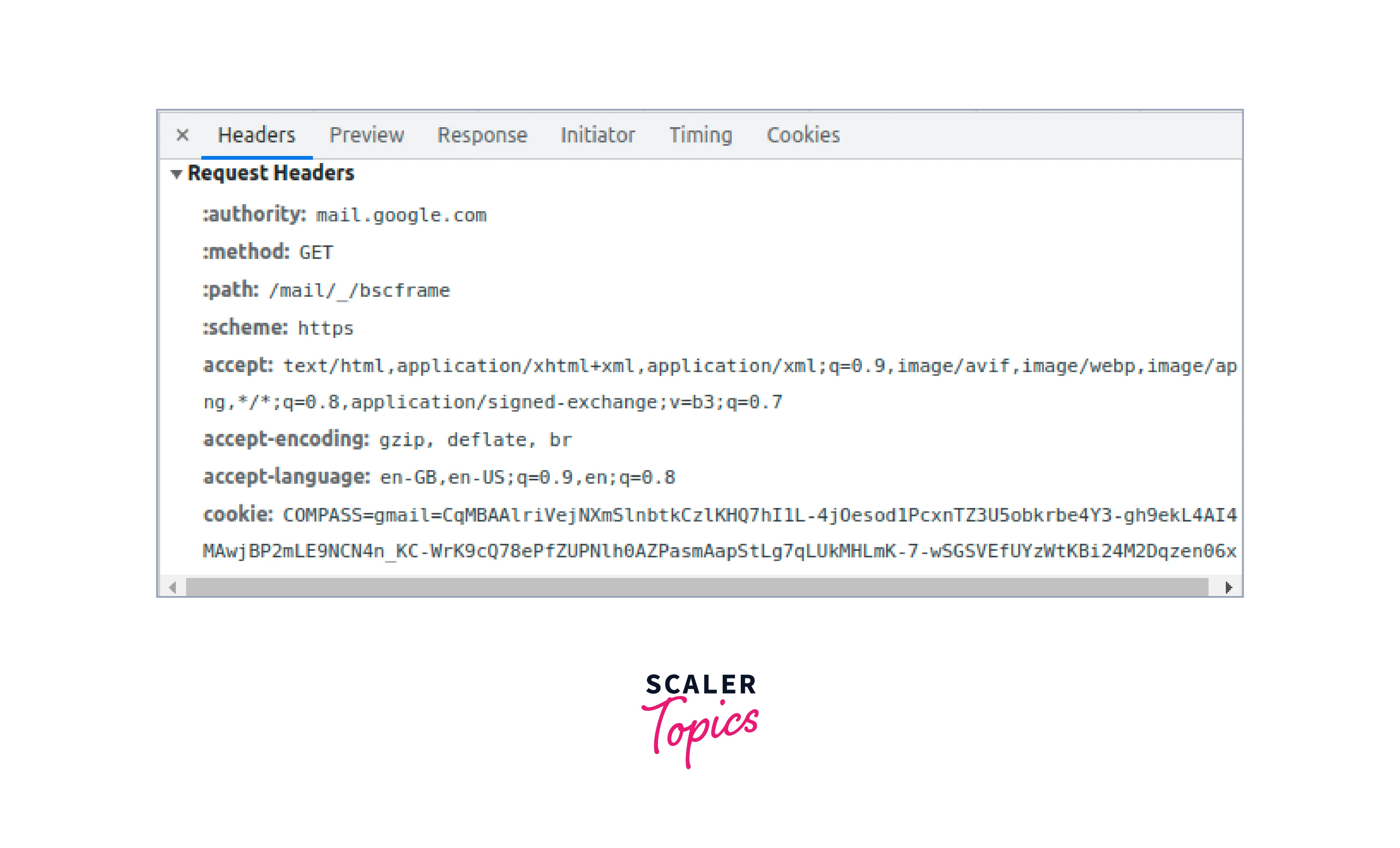
- Response headers:
- In DevOps networking, response headers provide information about the server response or the returned resource.
- Examples of response headers include Content-Type, Content-Length, and Server.
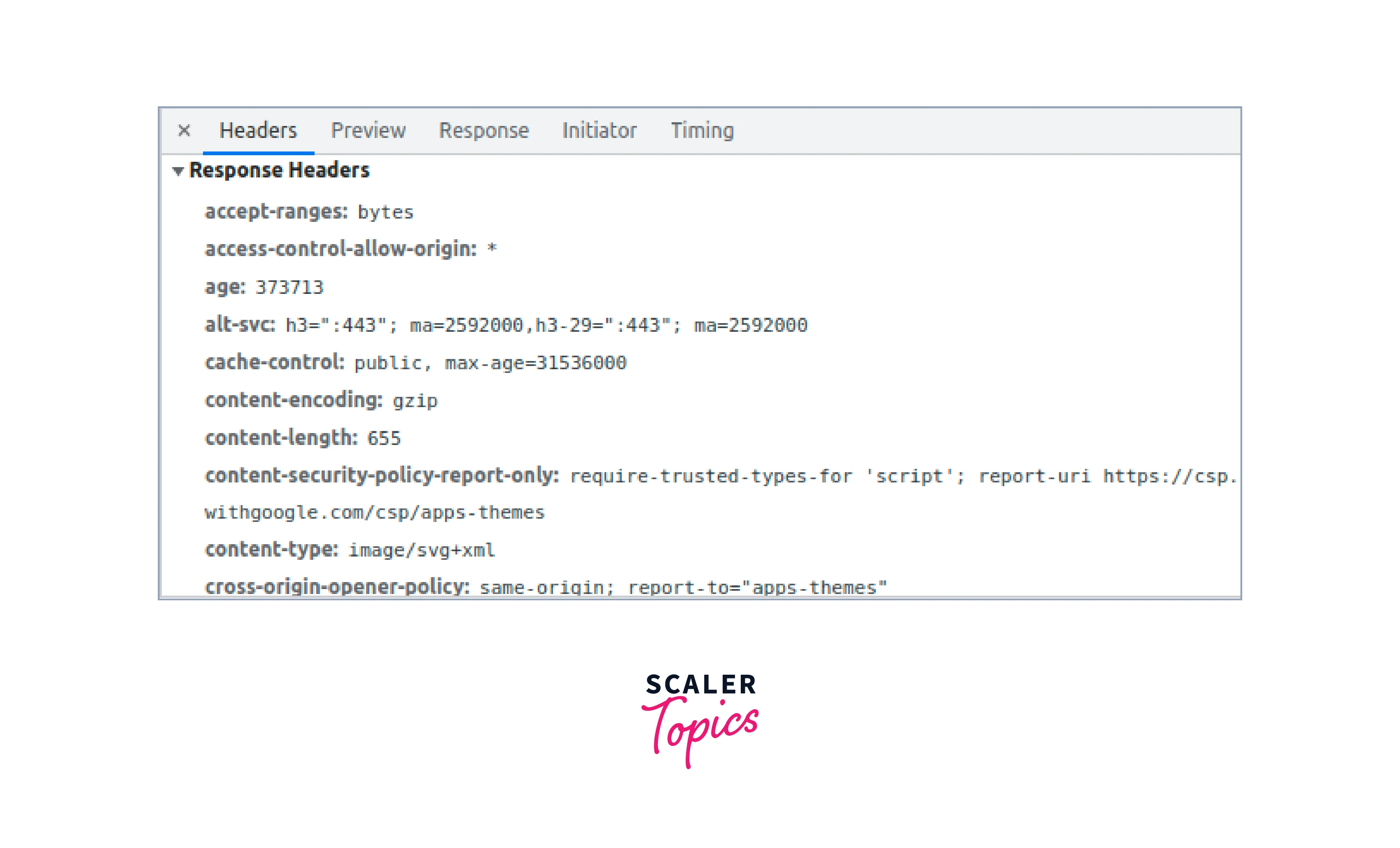
- Entity headers:
- These headers describe the content of the message body.
- Examples include Content-Encoding, Content-Language, and Content-Disposition.
- General headers:
HTTP headers are a crucial aspect of DevOps networking. They enable developers and network administrators enable better understand network traffic and optimize network performance.
Network Troubleshooting Tools
In DevOps networking, network troubleshooting tools are essential for detecting and resolving issues on a network. Here are some of the most important ones:
-
Ping:
- Ping tests network connectivity between two devices.
- Ping sends a request packet to the destination device, and if it receives a reply, it confirms that the two devices are connected.
- To use Ping, open a terminal window and type ping [IP address or hostname] for example, ping google.com
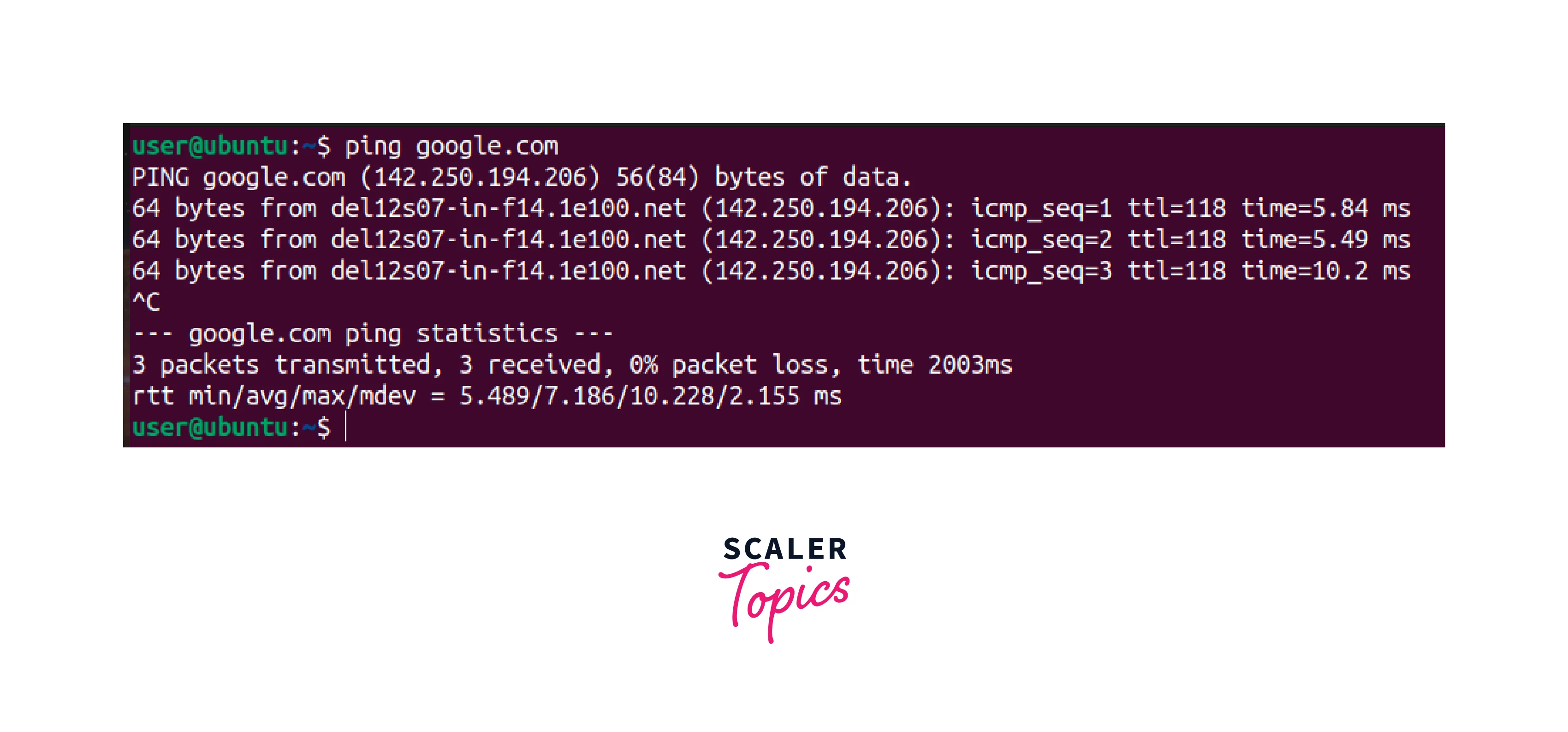
-
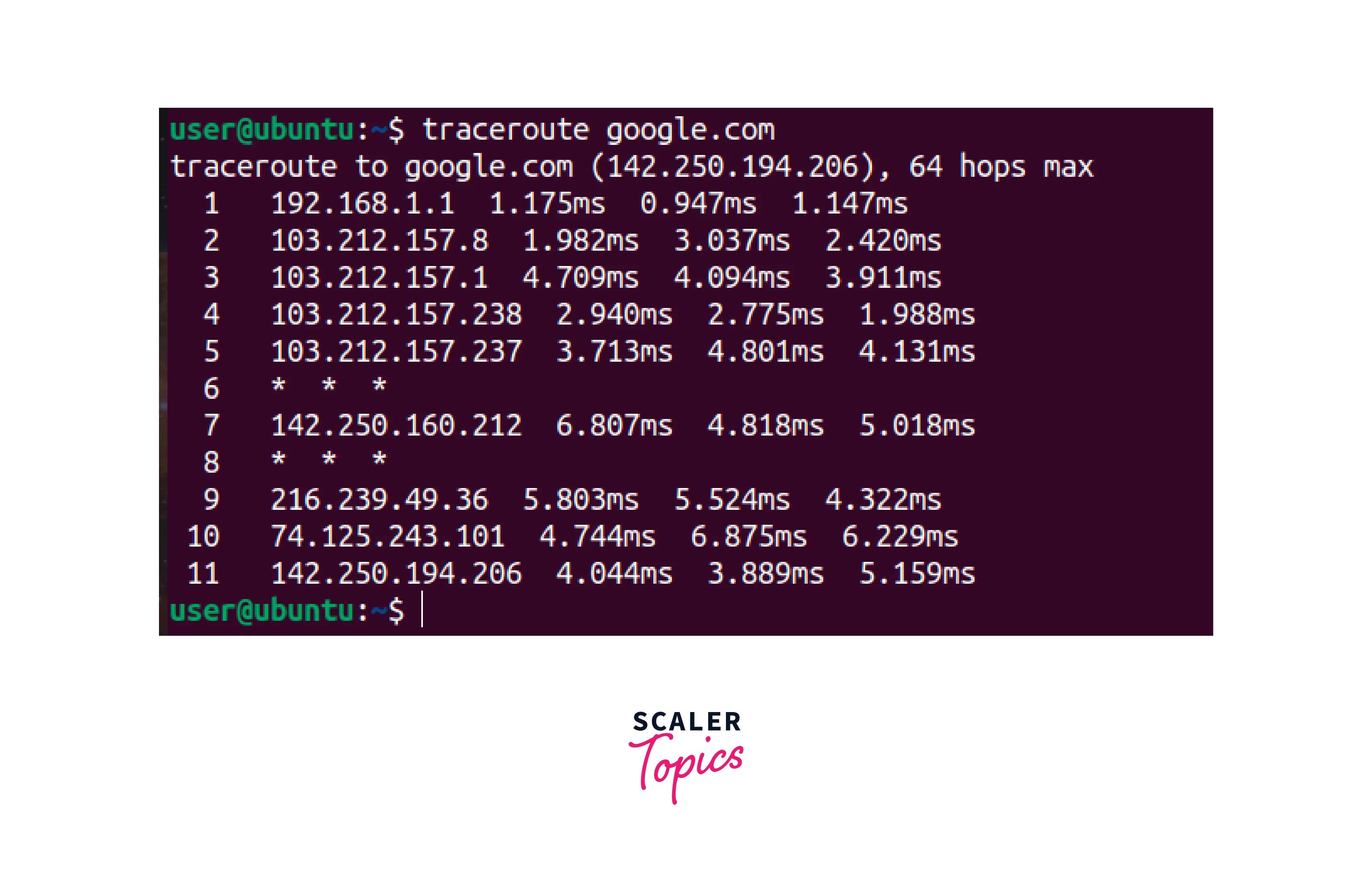
Traceroute:
- Traceroute is used to identify the path taken by packets to a destination host.
- Traceroute displays the IP addresses of all the hops in a route and provides information about response times. This information helps identify and troubleshoot network latency and routing problems in DevOps networking.
- To use Traceroute, run the traceroute [IP address or hostname] command in the command prompt. For example, traceroute google.com
-
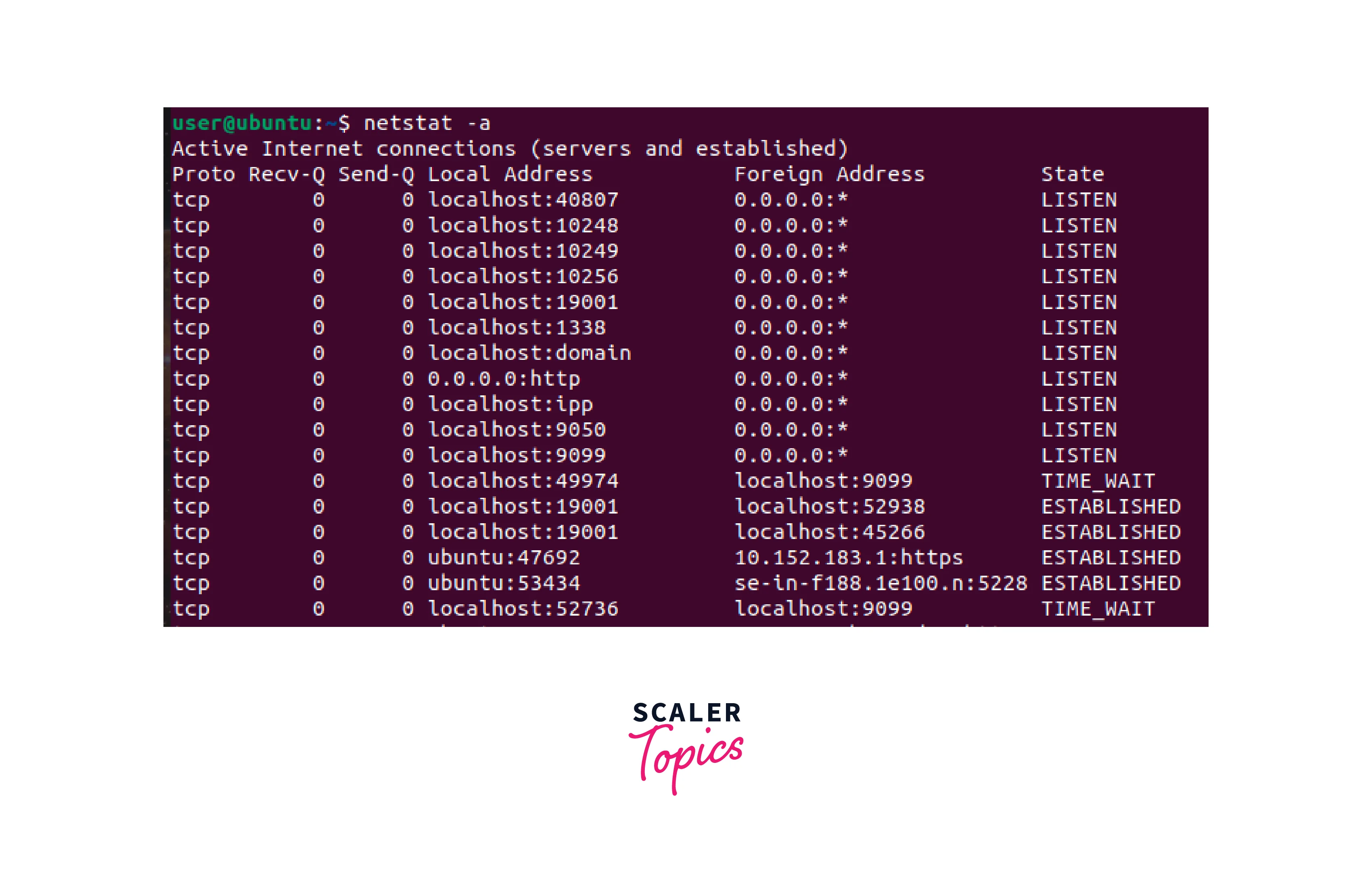
Netstat:
- Netstat shows network statistics for active connections.
- It displays the status of TCP and UDP ports and the IP addresses and ports of established connections.
- Netstat can be used to identify unauthorized connections and network usage.
- To use Netstat in DevOps networking, execute the netstat -a command in your terminal.
-
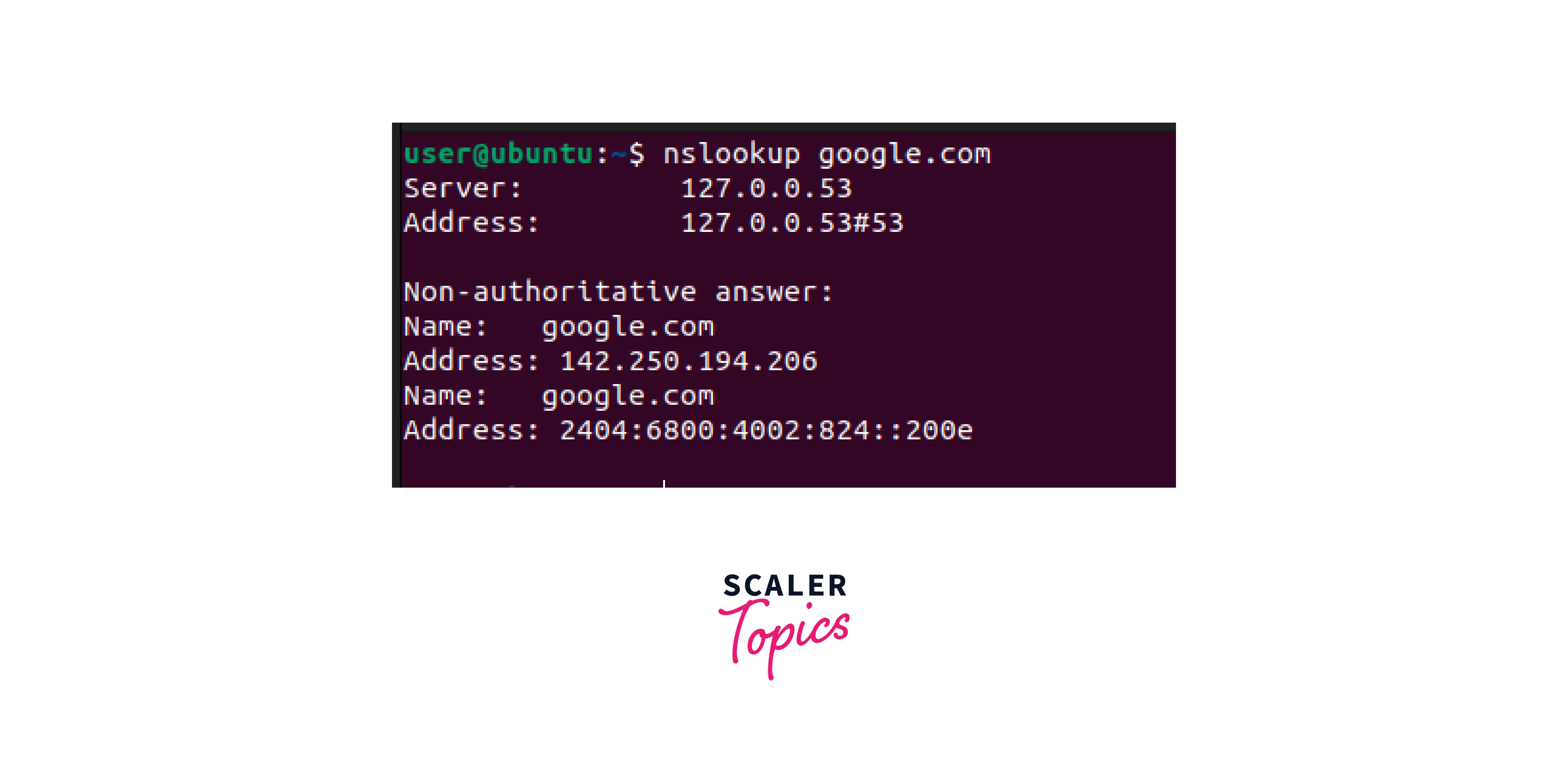
Nslookup:
- Nslookup is a command-line tool for querying DNS servers.
- In DevOps networking, this tool troubleshoots DNS problems by checking the IP address of a domain name and verifying the DNS records.
- It displays the IP address associated with the hostname and the hostname associated with the IP address.
- To use Nslookup, open a command prompt or terminal window and type nslookup [hostname or IP address] for example, nslookup google.com
-
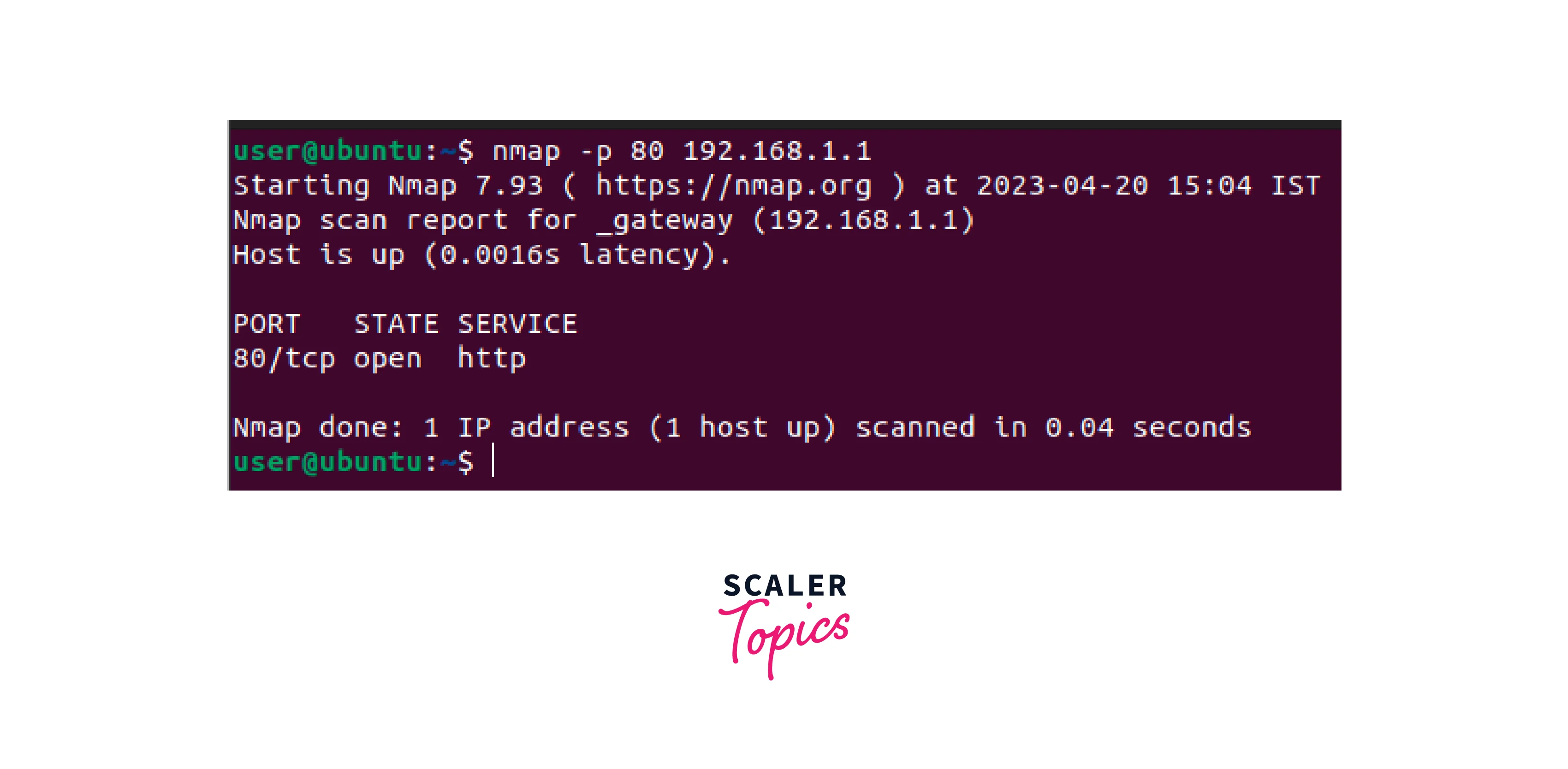
Nmap:
- Nmap is a network scanner to identify hosts and services on a network.
- It can detect open ports, operating systems, and other network characteristics.
- Nmap is for network mapping and security auditing.
- To use Nmap, open a terminal window and type, for example, to scan port 80 on a single host 192.168.1.1, execute the following command: nmap -p 80 192.168.1.1.
These are just some of the DevOps networking troubleshooting tools. Using these tools, network administrators can diagnose and resolve network problems, ranging from connectivity issues to security vulnerabilities.
Putting the Toolbox Together
Putting the toolbox together is all about utilizing the knowledge of DevOps networking concepts and applying it to real-world scenarios. The following are the key points to consider while putting the toolbox together:
-
Understanding the network topology of your infrastructure:
- It includes identifying the devices on the network, their roles, and how they are connected.
- It is essential to have a good understanding of the network topology to troubleshoot issues effectively.
-
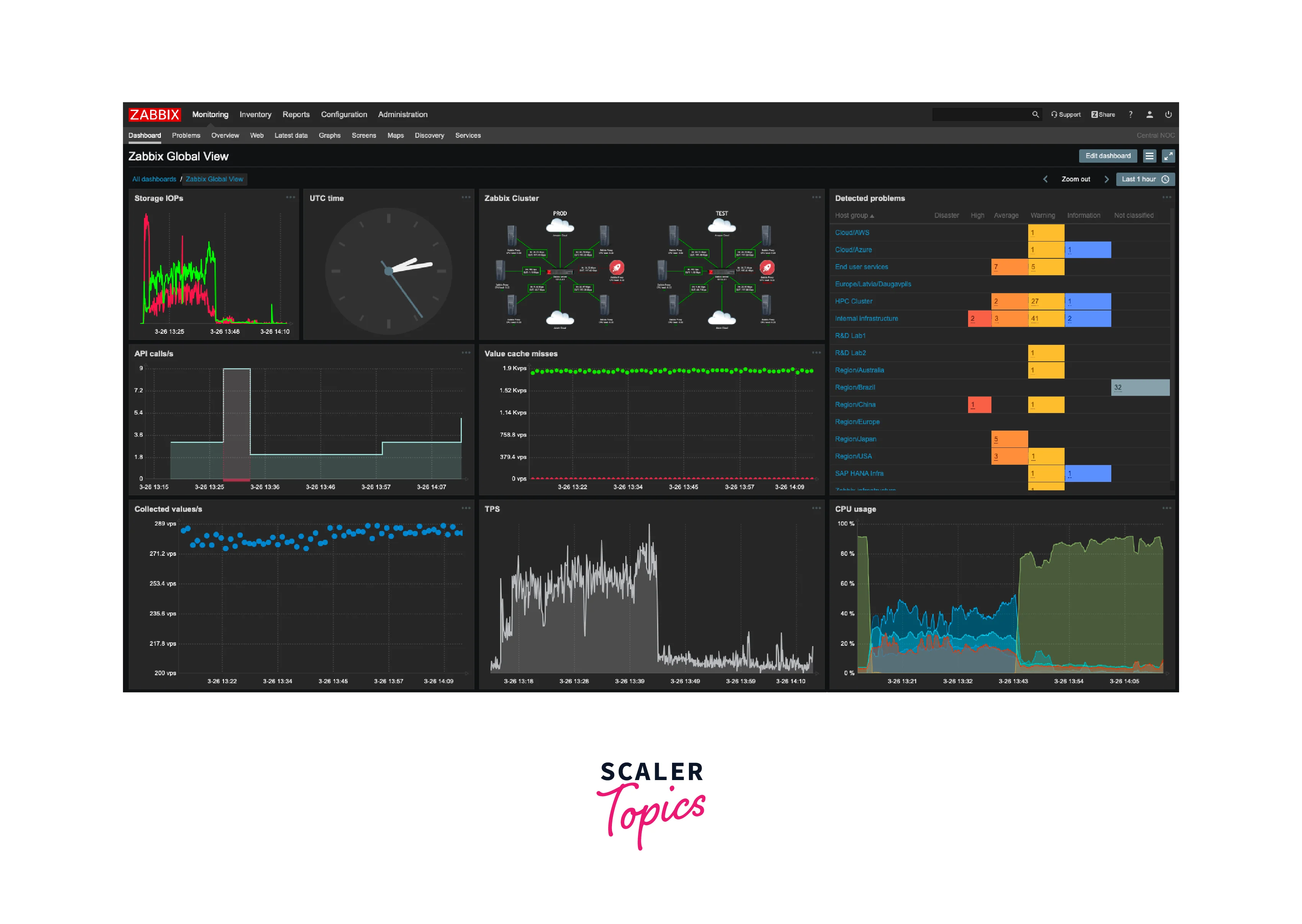
Utilizing network monitoring tools:
- In DevOps networking, monitoring tools can provide visibility into network traffic and detect anomalies, such as traffic spikes, unusual traffic patterns, and potential security threats.
- Use tools like Nagios, Zabbix, and Cacti to monitor network performance, availability, and uptime.
-
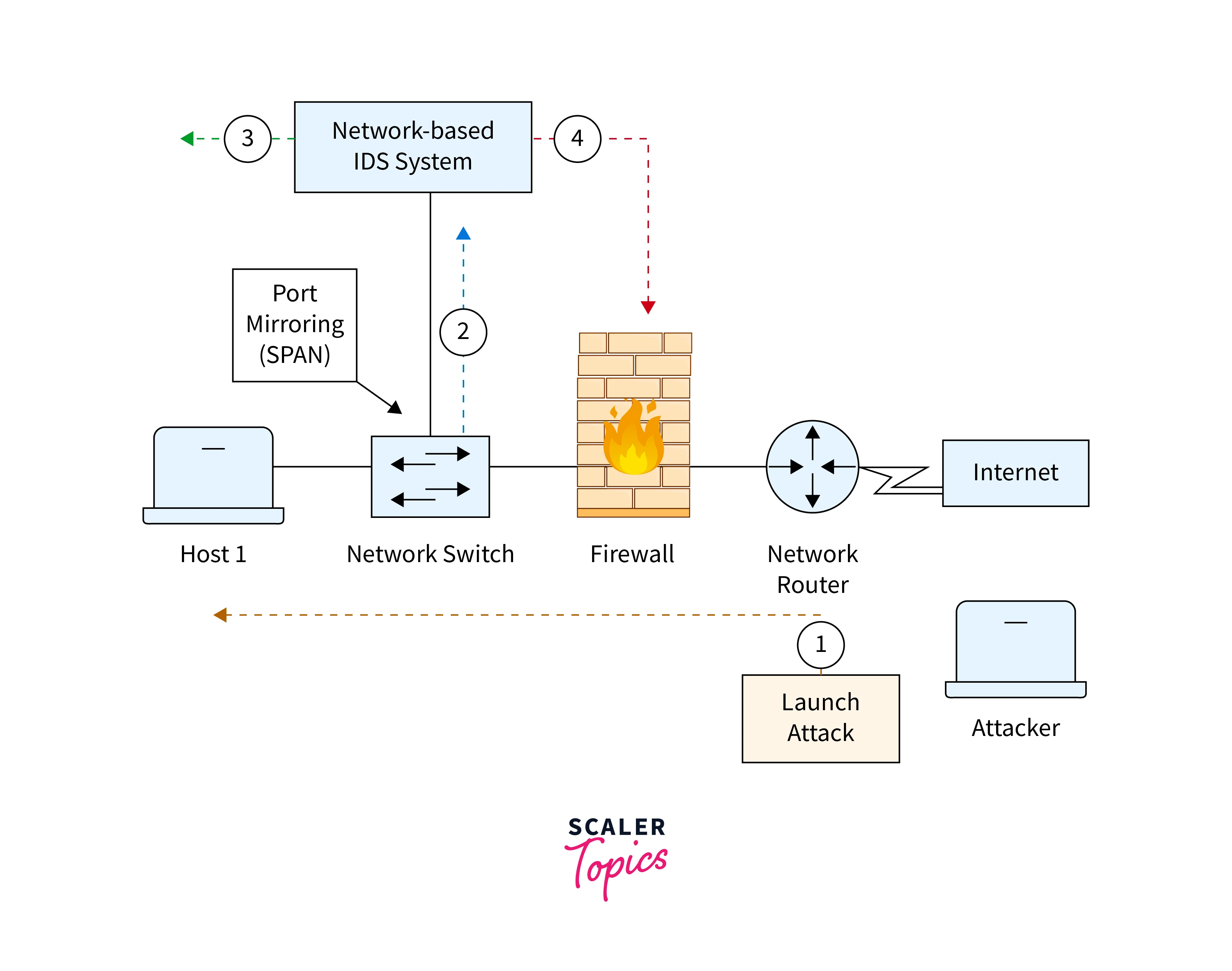
Implementing network security measures:
- DevOps networking requires implementing security measures to ensure that network resources are confidential, have integrity, and are available.
- It includes implementing firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs).
-
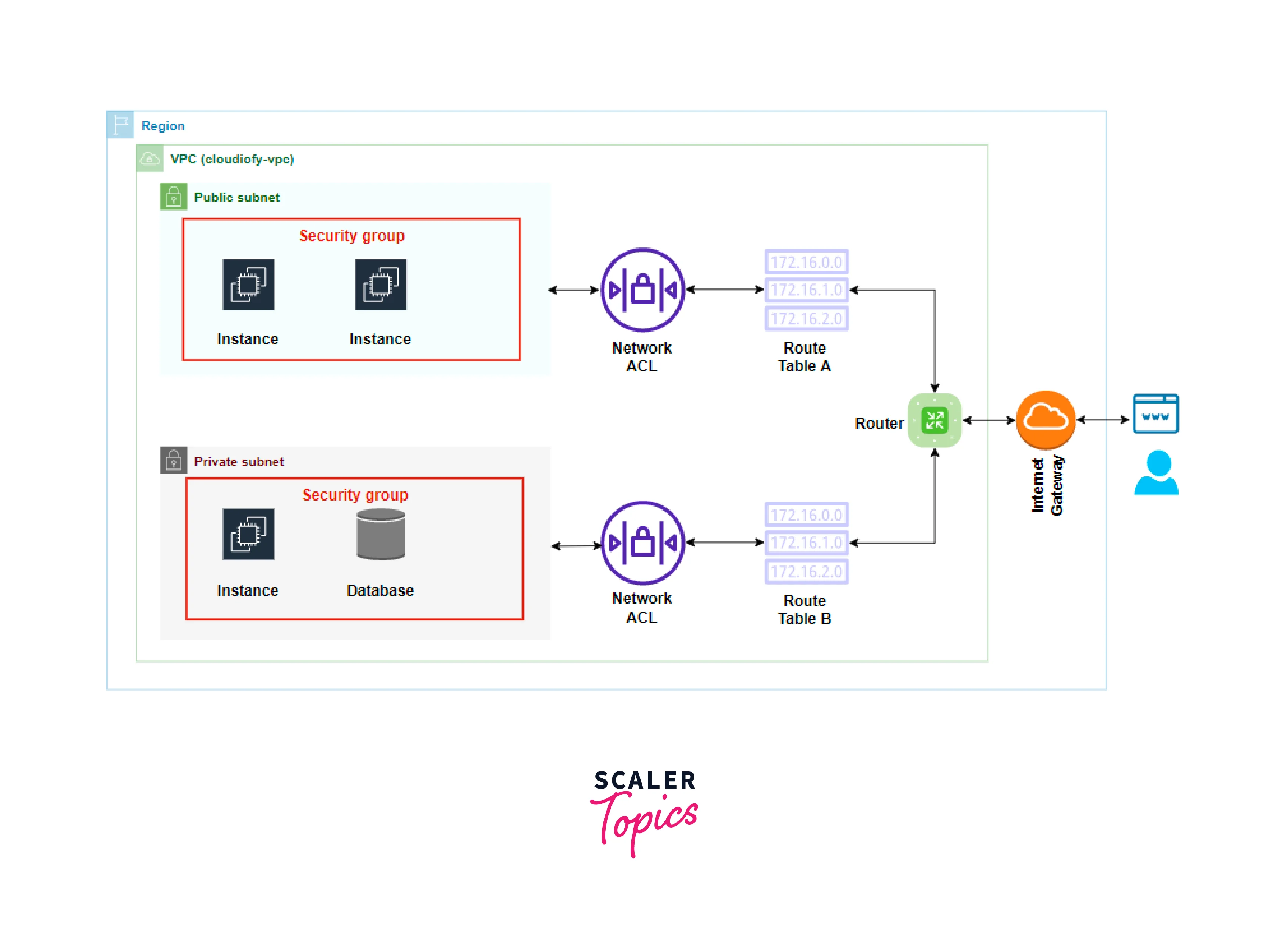
Configuring network devices:
- In DevOps networking, devices, like routers and switches, should be configured correctly for proper functioning.
- It includes setting up VLANs, routing protocols, and access control lists (ACLs).
-
Documenting the network:
- Documenting the network topology, IP addressing scheme and device configurations can help troubleshoot issues and maintain the network.
- You can use Visio, Lucidchart, and Draw.io to create DevOps network diagrams.
-
Keeping up-to-date with industry developments:
- Attending conferences, reading industry publications, and joining online communities can help stay relevant to industry developments in DevOps networking.

In summary, putting the toolbox together can resolve troubleshooting issues and help maintain a robust and secure network infrastructure for DevOps networking.
Conclusion
We have explored topics ranging from the fundamentals to advanced level in DevOps networking.
Let us summarize the key takeaways from this blog:
- The OSI model breaks down network communication into seven distinct layers.
- TCP/IP is a widely used networking protocol stack today and differs from the OSI model in several ways.
- IP subnetting and CIDR are critical concepts in network design and are used to divide a network into smaller, more manageable subnets.
- Routing forward packets to different networks.
- DNS is the system used to translate domain names into IP addresses.
- The HTTP protocol is used for transmitting data over the World Wide Web and is critical for building modern web applications.
- Network troubleshooting tools can help DevOps engineers diagnose and resolve issues quickly.
This article should be considered a reference to keep DevOps networking skills and knowledge up-to-date.
