Linux Privilege Escalation
Overview
Linux Privilege Escalation is an important step in getting complete access to a victim’s computer. In this article, we will see what are privileges and how permissions are controlled so that access is given to different users for access to different levels of information and their ability to read and write this information. When an attacker gets access to a computer that can be either a normal user or a root user. The attacker will always try to get complete control of the system by getting access to the root user. This happens through privilege escalation.
Introduction
Privilege, in terms of cybersecurity, can be defined as allowing different users to access different levels of information and their ability to read and write this data. Not all users can be allowed to access system information and similarly not each user should be able to make changes to others' data. This is controlled through the Privilege system. In computer systems generally, the user with general read and write permission is called a normal user or regular user and the user with complete access to all system-wide resources is known as a Root user or administrative account. It has the highest privilege in the system and is used for system administration.
What is Privilege Escalation?
When a user obtains rights, they are not authorized to, it is known as privilege escalation. These rights may be used to remove files, access confidential information, or put computer viruses such as malware, ransomware, etc. on the computer. These privilege escalations occur when a software program, operating system, or configuration flaw is used to acquire elevated access to resources that are typically secured by an application or user. As a consequence, a program that was given access to higher privileges than the system administrator or developer had anticipated ends up carrying out malicious actions. It can be of two types Horizontal privilege level escalation and vertical privilege level escalation. The horizontal level is when the attacker gains access to another user with a similar level of administrative access. Weak security policies result in such escalations. Vertical level escalation is when the attacker gains access to administrative or root access and can now control all most all systems.
Linux Privilege Escalation
Privilege escalation is used when an attacker has access to a regular user account and uses that account to gain access to the root user account. Enumeration is described as an important step in Linux privilege escalation. The act of methodically searching a target for data is known as enumeration. By locating open ports, users, and passwords, enumeration may provide hackers with a step-by-step guide for breaking into a system.
While performing the act of enumeration we need to find various details, to begin with, we start looking for the file named passwd which is present in /etc/passwd. This file can be very informative as it provides the list of all users in the system which will be used further.
To check the file, we may use the following command: cat /etc/passwd // this command displays all the users in the system. Each value in the output denotes something, the first value indicates the username of the user, then each value is separated by the use of “:”. The next value indicates that is “x” which indicates that the password is stored in encrypted format in the /etc/shadow file. The next value indicates the user id, the next value indicates the group id, followed by the Full name of the user, then the user's home directory and the login shell.
We will talk a bit more about the permission model in Linux further in the article. But before that let us see what happens in the /etc/shadow file. It contains the system user's passwords and the permission level assigned to it by default is 640 which signifies the owner or superuser has read and written permission. The group has read permission and all the other user cannot access the file. Mostly our field of interest is passwords. The encrypted passwords are saved in the following format type_of_hash:salt_used:hashed_value. The type is the type of hash function used; salt is the extra random data that is added to the passwords to make them more securely encrypted. And the hashed value is the resultant of the hash function of the password and the salt. The types of hashes used are MD5, Blowfish, Eksblowfish, SHA-256, and SHA-512.
How Privileges Are Created and Delegated in Linux Systems
Linux manages different users at once by creating groups and permissions for each user based on which the user can or cannot access or modify the content. Linux ensures that the user with adequate permissions is only able to access and the user with modify permission can only modify this creating a secure environment for multi-user functionality. User Accounts can be further divided into three types known as a Root user account, a regular user account, and a service account.
To Create New User Accounts
- To open the terminal Press Ctrl + Alt + T
- Enter into administrative mode using sudo su command.
- To create a user account, use the following command: useradd user_name Or adduser user_name // this command creates a user with the specified username, but it also creates a new group with the same user name and adds the user to the given group.
- To give admin privilege to the added user use the following command: usermod -aG sudo user_name Or adduser user_name sudo // This command adds the user user_name to the sudo group, which is the group with administrative permissions. To understand delegation we need to see the permission model of the Linux
Permission Model in Linux
As we have seen earlier, each file has a set of permissions that defines the access level of the owner, group, and others regarding the read, write and execute status of the file. To check the specific permission of a file, we can use the following command: ls -l file_name
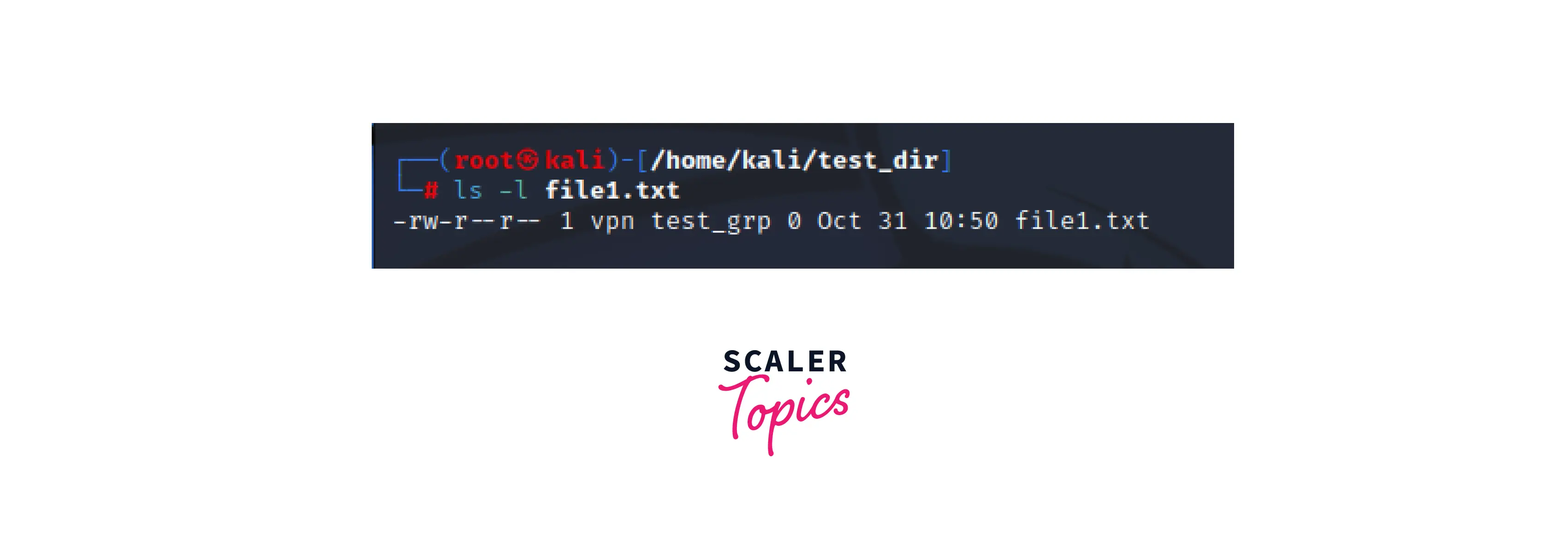
These permissions can be modified depending on the requirement. For this, we can use the "chmod" command, which enables us to change the file permissions.
Only the Root user or the owner of the file/directory can change its permission.
Permissions can be set in two modes, either Absolute mode or Symbolic mode.
- Symbolic Mode – In symbolic mode, we grant or remove permissions by combining letters and symbols.
- Absolute Mode - For adding or removing permissions in absolute mode, we use a number to represent file permissions.
Manage Permissions Using Absolute Mode
The following Table depicts the permissions representation and their corresponding permissions
| Octal Value | Binary | Permission Representation | Permission Description |
|---|---|---|---|
| 0 | 000 | - - - | No Permission |
| 1 | 001 | - - x | Execute Only Permission |
| 2 | 010 | - w - | Write Only Permission |
| 3 | 011 | - w x | Write and Execute Permissions |
| 4 | 100 | r - - | Read Only Permission |
| 5 | 101 | r - x | Read and Execute Permissions |
| 6 | 110 | r w - | Read and Write Permissions |
| 7 | 111 | r w x | Read, Write, and Execute Permissions |
Now we can directly use either the combination of octal values or rwx notation to set file permissions, for example.
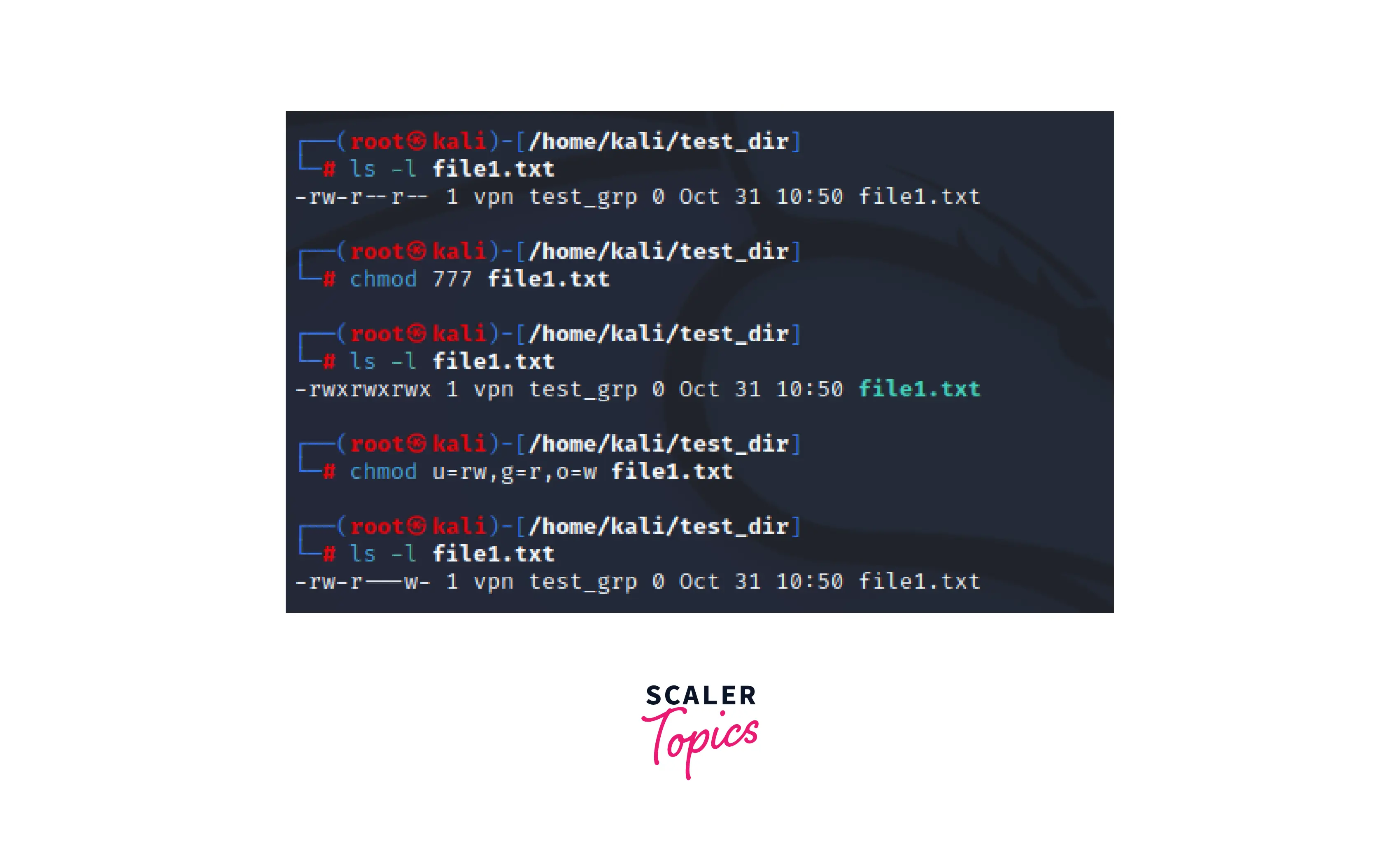
This example depicts permissions using the octal values and setting individual permission of users, groups, and others using the rwx notations.
Manage Permissions Using Symbolic Mode
In symbolic mode, mathematical symbols are used to change the permissions:
| Symbol | Description |
|---|---|
| + | This Symbol denotes the addition of permission to a file or directory |
| - | This Symbol denotes the removal of permission from a file or directory |
| = | This Symbol is used to apply and overwrite any previous permissions set on a file or directory |
| Also, | |
| "u" denotes the user, "g" denotes the group, "o" denotes others, and "a" denotes all. |
The following example denotes changing permissions using symbolic mode.
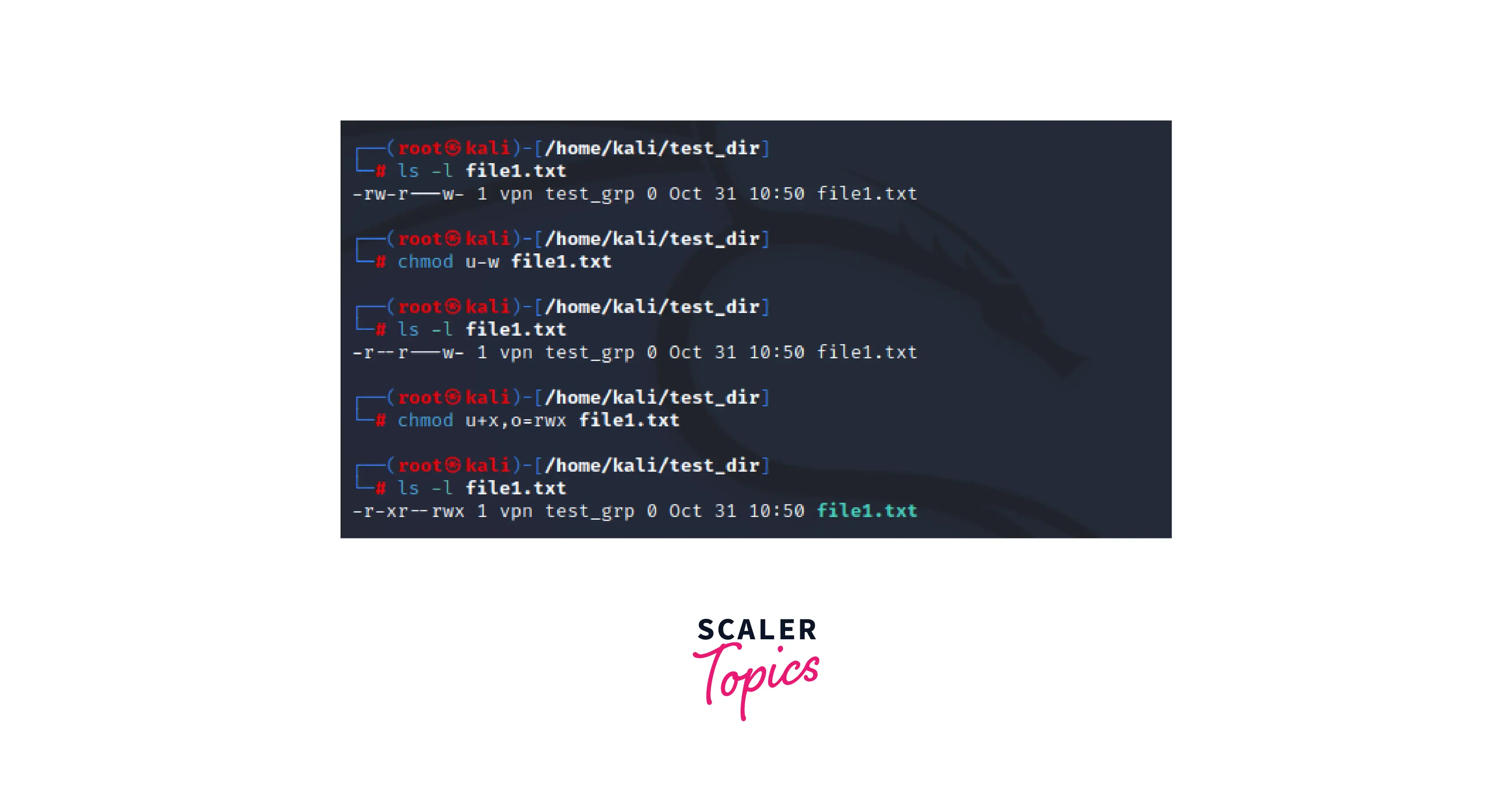
In this example, we modified and assigned the permission of the file using symbolic mode.
Special Permissions and Access Control Lists and Modifying Permissions
Apart from reading, writing, and executing, we also have some other permissions that are less commonly used but essential to know; they are known as special permissions. It allows additional privileges over the standard permission sets. These include SUID, SGID, and sticky bit.
SUID
SUID, which is short for Set User ID is special permission. This special permission enables the execution of the file with the permission and privilege of the owner of the file. When the set user id bit is enabled, it ensures that whoever executes the file will always run with the privileges the owner of the file had. To set up this SUID, we can use the following command:
If you observe that "S" is present in the file permissions, it indicates that the user does not execute permission. When execute permission is available, "s" will be appended in the file permissions. Also, to add SUID using the absolute method, we can per-append a 4 to the numerical permissions.
SGID
SGID, which is short for Set Group ID, is also special permission. When this permission is enabled, the GID of the user becomes the same as that of the group owner. That is, any user can access a file with the permissions provided to the group owner. To set up this SGID, we can use the following command:
Also, to add SGID using the absolute method, we can pre-append a 2 to the numerical set of permissions.
Sticky Bit
Sticky bit, as the name suggests, is used to prevent files from being deleted by authorizing only the root user, owner of the file, or owner of the directory to delete the file. To set up this sticky bit, we can use the following command:
Also, to add SGID using the absolute method, we can pre-append a 1 to the numerical permissions set.
Why Do We Need to Perform Linux Privilege Escalation?
Considering the attacker is successful in creating a privilege escalation, why did they struggle so much to gain administrative access? What would the attacker do with the administrative access?
The answer to the question is pretty simple the attacker aims to gain access to sensitive data and information which they can use to extort money. The data and information locked for the normal user will be available to the root user. Hence the attacker needs privilege escalation.
Sometimes the attacker only gains access to the shell until the system restarts as that would break off any existing connections as soon as the system shuts down and the attacker might need to repeat the same process which may or may not be successful this time.
So, the attacker might also create a permanent backdoor in the victim's machine. So that even if the user shuts down the system or changes his credentials still the machine will be accessible to the attacker because of the presence of a backdoor.
Techniques Used for Linux Privilege Escalation
We talked about how a user can check all the users in the system, also how to create new users, change the permissions of the file. We also discussed what an attacker can do once he gets access to the admin account. But we did not discuss how can he get access to the admin account.
Kernel Exploits
Sometimes the version of kernel used leads to exploits. If the kernel is not updated to the latest version with the latest security patches, then the system might be considered vulnerable.
You may use Metasploit or any other vulnerability database to search and use any openly available exploits. These exploits may lead to the attacker getting root access to the system. One of the most famous exploits of all time is the “DirtyCow” exploit which resulted in unauthorized users being able to write into read-only memory mappings.
For example, searching Metasploit for privilege escalation exploits availability.
These exploits may be used depending on the kernel version of the victim’s system. For more information on how to use Metasploit msfconsole, you may refer to the following article
Exploiting Services that Are Running as Root
When a service is already running with administrative privileges and these services are exploitable. We might find a service that is active but only available and can only be accessed from the host. Any service such as a database, development server, or any other service which can be vulnerable and these services are running as root can be exploited to gain root privileges. We may use the following command to check the service running inside using the netstat and can be compared with nmap scan results to find services that are not accessible only from inside.
Exploiting SUID Executables
SUID refers to the set user id and is considered as special file permission. When this is set to true, it allows the user with a normal privilege level to be able to execute the file as the file owner. This is used when some applications or services require temporary root privileges. This allows the attacker to run files on the victim’s machine with root privileges. Similarly, there is another special file permission known as GUID which is the group user id.
For more details about SUID and GUID you may refer link.
Exploiting SUDO Rights
If the current user belongs to the sudo group, they can run commands as root without using the root password. Using the “sudo -l” command one can list all the commands available for the root user. Even if the user has limited admin privilege, that is it can execute some applications or services with root privilege, the attacker may modify these to execute the malicious code.
Exploiting Badly Configured Cron Jobs
Cron jobs are jobs that are tasks scheduled to happen after a fixed amount of time. When these tasks are owned by the root user and are scheduled, but a normal user has the privilege level to edit then it can be exploited by the attacker to run malicious scripts and gain admin access. The following command can be used to check all the cron jobs that are running.
Additional Techniques to Escalate privilege
Other than the primary methodologies mentioned, there are a few ways you can escalate privileges:
Exploiting users with ‘.’ in their PATH
Most Linux users do not use the ‘.’ Notation to run a file. Instead of using the appropriate command, we tend to use the shortcut. But this habit can be used by the attacker to place a malicious program with the same name as that of the command will result in the execution of the malicious program instead.
When using programs that make system(), execvp(), or execlp() calls to programs, the attacker may benefit from having “.” in their PATH by putting a program into a directory in the PATH so that the malicious program is run instead.
The other commonly used techniques include:
- NFS share if enabled and misconfigured, it can be used to escalate privilege.
- Usage of Weak Passwords Hashes of weak passwords are easily cracked.
- Capability' It is similar to SUID and commands to check it “setcap” and “getcap”
Enumeration Techniques to Automate Privileged Escalation on Linux
As seen above enumeration is a very important step in the privilege escalation in Linux. Instead of trying out all these above steps which included checking users, their privileges, users with no password, checking vulnerabilities in the version of the kernel or any software used.
To Reduce the manual efforts, we may use some enumeration scripts. But they provide a lot of unusable output, making it possible to overlook vulnerabilities. Some of the tools include:
- LinEnum - LinEnum is a simple shell script that automatically checks for privilege escalation opportunities. The various options available are:-
- -k This parameter is used to enter the keyword
- -e This parameter is used to enter the export location
- -t// This parameter is used to include in-depth tests
- -s //This parameter is used to enter the current user password to check sudo permissions
- -r // This parameter is used to enter the name of the report
- -h // This parameter is used to display help
- Unix-privesc-check - Unix-privesc-check is a script for Unix machines. The command to use the following script is ./unix-privesc-check > output.txt
- LinPEAS - LinPEAS is also a shell script that checks for privilege escalation opportunities.
- Linux Exploit Suggester 2 - This script is extremely useful for quickly finding privilege escalation vulnerabilities.
Conclusion
- Through the system of privileges the users and their access levels are managed. Not every user should have access to system information, nor should every user have the ability to edit the data of another user.
- Linux operating systems are used as web servers and they are the most common targets of Linux privilege escalation attacks.
- Permissions can be set in two modes, either Absolute mode or Symbolic mode.
- Various Techniques of privilege escalation are: Kernel exploits, Exploiting services that are running as root, exploiting SUID Executables, exploiting SUDO rights/user, exploiting badly configured cron jobs, exploiting users with ‘.’ in their PATH, NFS share, Capability, cracked weak passwords.
- Some of the automation Scripts include LinEnum, LinPEAS, Linux Exploit Suggester 2, and Unix-privesc-check.
