Segmentation in Operating System
Segmentation divides processes into smaller subparts known as modules. The divided segments need not be placed in contiguous memory. Since there is no contiguous memory allocation, internal fragmentation does not take place. The length of the segments of the program and memory is decided by the purpose of the segment in the user program.
We can say that logical address space or the main memory is a collection of segments.
Types of Segmentation
Segmentation can be divided into two types:
- Virtual Memory Segmentation: Virtual Memory Segmentation divides the processes into n number of segments. All the segments are not divided at a time. Virtual Memory Segmentation may or may not take place at the run time of a program.
- Simple Segmentation: Simple Segmentation also divides the processes into n number of segments but the segmentation is done all together at once. Simple segmentation takes place at the run time of a program. Simple segmentation may scatter the segments into the memory such that one segment of the process can be at a different location than the other(in a noncontinuous manner).
Why Segmentation is required?
Segmentation came into existence because of the problems in the paging technique. In the case of the paging technique, a function or piece of code is divided into pages without considering that the relative parts of code can also get divided. Hence, for the process in execution, the CPU must load more than one page into the frames so that the complete related code is there for execution. Paging took more pages for a process to be loaded into the main memory. Hence, segmentation was introduced in which the code is divided into modules so that related code can be combined in one single block.
Other memory management techniques have also an important drawback - the actual view of physical memory is separated from the user's view of physical memory. Segmentation helps in overcoming the problem by dividing the user's program into segments according to the specific need.
Advantages of Segmentation in OS
-
No internal fragmentation is there in segmentation.
-
Segment Table is used to store the records of the segments. The segment table itself consumes small memory as compared to a page table in paging.
-
Segmentation provides better CPU utilization as an entire module is loaded at once.
-
Segmentation is near to the user's view of physical memory. Segmentation allows users to partition the user programs into modules. These modules are nothing but the independent codes of the current process.
-
The Segment size is specified by the user but in Paging, the hardware decides the page size.
-
Segmentation can be used to separate the security procedures and data.
Disadvantages of Segmentation in OS
-
During the swapping of processes the free memory space is broken into small pieces, which is a major problem in the segmentation technique.
-
Time is required to fetch instructions or segments.
-
The swapping of segments of unequal sizes is not easy.
-
There is an overhead of maintaining a segment table for each process as well.
-
When a process is completed, it is removed from the main memory. After the execution of the current process, the unevenly sized segments of the process are removed from the main memory. Since the segments are of uneven length it creates unevenly sized holes in the main memory. These holes in the main memory may remain unused due to their very small size.
Characteristics of Segmentation in OS
Some of the characteristics of segmentation are discussed below:
-
Segmentation partitions the program into variable-sized blocks or segments.
-
Partition size depends upon the type and length of modules.
-
Segmentation is done considering that the relative data should come in a single segment.
-
Segments of the memory may or may not be stored in a continuous manner depending upon the segmentation technique chosen.
-
Operating System maintains a segment table for each process.
Example of Segmentation
Let's take the example of segmentation to understand how it works.
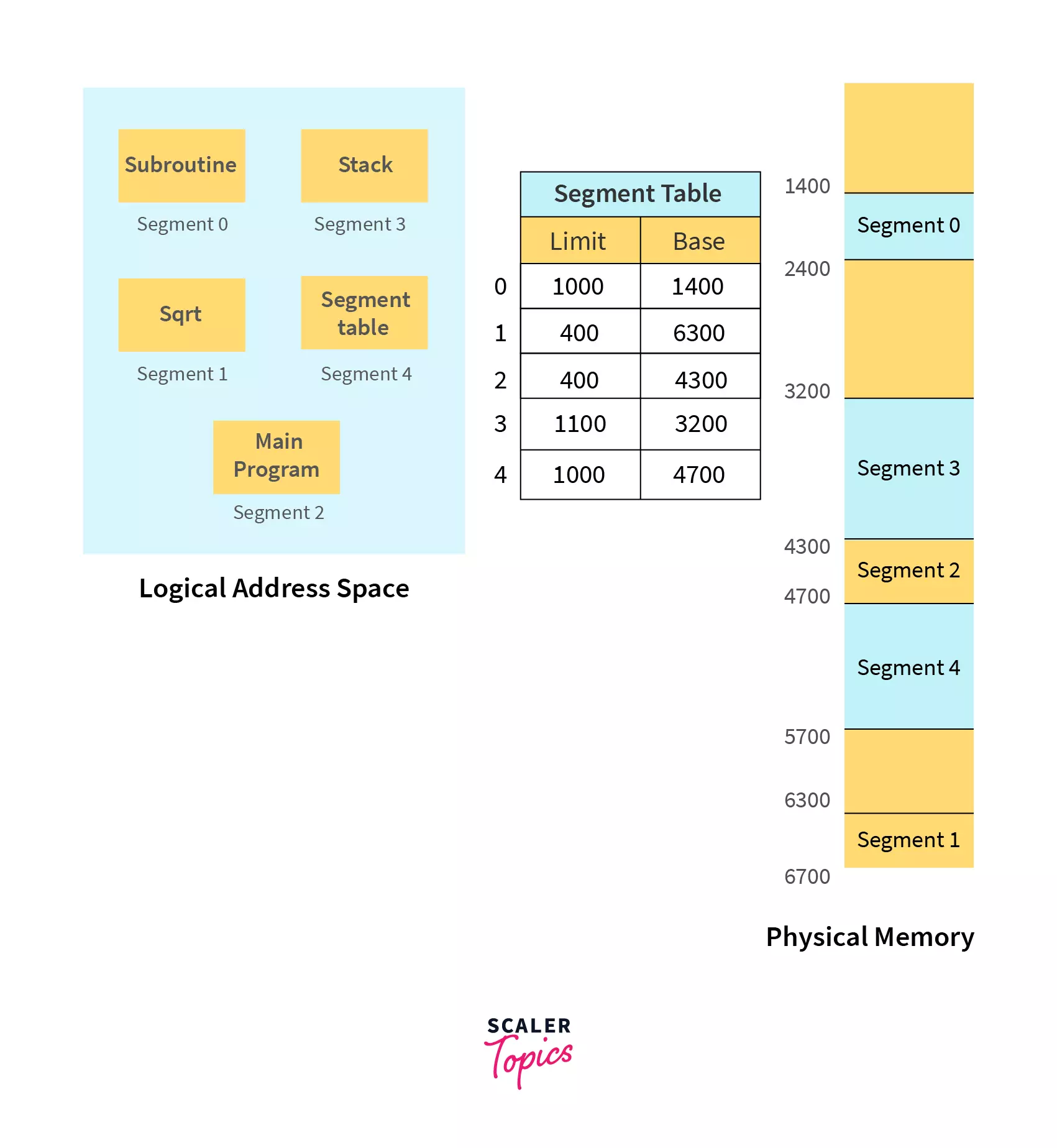
Let us assume we have five segments namely: Segment-0, Segment-1, Segment-2, Segment-3, and Segment-4. Initially, before the execution of the process, all the segments of the process are stored in the physical memory space. We have a segment table as well. The segment table contains the beginning entry address of each segment (denoted by base). The segment table also contains the length of each of the segments (denoted by limit).
As shown in the image below, the base address of Segment-0 is 1400 and its length is 1000, the base address of Segment-1 is 6300 and its length is 400, the base address of Segment-2 is 4300 and its length is 400, and so on.
The pictorial representation of the above segmentation with its segment table is shown below.
Segmentation Architecture
Segmentation architecture refers to the design and structure of a neural network model used for image or video segmentation tasks. Image segmentation is the process of dividing an image into multiple regions or segments, each representing a meaningful object or part of the image. It plays a crucial role in computer vision applications such as object recognition, scene understanding, and autonomous driving.
There are several popular segmentation architectures that have achieved significant success in the field of computer vision. Here are a few notable ones:
-
Fully Convolutional Network (FCN): FCN was one of the pioneering architectures for semantic segmentation. It replaces the fully connected layers of a traditional convolutional neural network (CNN) with convolutional layers to enable dense pixel-wise predictions. FCN utilizes skip connections to combine low-level and high-level features for improved segmentation accuracy.
-
U-Net: U-Net is a popular architecture known for its effectiveness in biomedical image segmentation tasks. It consists of a contracting path (encoder) and an expanding path (decoder). The encoder captures contextual information and reduces the spatial resolution, while the decoder recovers the spatial information and generates segmentation masks. U-Net also utilizes skip connections to preserve fine-grained details.
-
DeepLab: DeepLab is a family of segmentation architectures that have been widely used for various segmentation tasks. The original DeepLab model employs dilated convolutions, atrous spatial pyramid pooling (ASPP), and a fully connected conditional random field (CRF) for refining the segmentation maps. DeepLabv3 and DeepLabv3+ further improve the model with more advanced components like encoder-decoder structures and feature pyramid networks.
-
Mask R-CNN: Mask R-CNN combines object detection and instance segmentation in a single architecture. It extends the popular Faster R-CNN object detection framework by adding a parallel branch that generates segmentation masks for each detected object. Mask R-CNN is widely used for instance-level segmentation tasks, where the goal is to precisely segment each object instance within an image.
Problem of Fragmentation
Segmentation has one major disadvantage. During the swapping of processes, processes are loaded and removed from the main memory. The swapping of processes sometimes results in breaking the free memory space into small pieces according to the segments. This breaking of free space into pieces is called External Fragmentation which is also a major problem in the segmentation technique.
One thing to note here is that there is no internal fragmentation in the case of Segmentation. Each process is loaded by bringing all its associated segments into the main memory. As every segment of the process is loaded into the main memory by creating partitions of the size of each segment. Thus, each segment can fit exactly in the dynamically created partitions of the main memory. Thus, segmentation is free of internal fragmentation.
Common Segments of a Process
The current process (or the program in execution) has text, data and system data segments. Let us learn more about these segments.
-
Text Segment: The text segment contains the code of the program. Text Segment is also known as Instruction Segment, and it is a read-only code located in the address space segment of a program. Text Segments are initialized from the executable file of the program.
-
Data or User Data Segment: The data segment contains four areas of data namely - initialized data, non-initialized data, heap area, and stack area. a. The initialized section of data contains strings that are initialized from the program executable file. b. The non-initialized section of data contains global variables. c. The heap area is an area created by the process to store the global variables. The heap area is also known as Malloc Area. d. The stack area contains local variables, function parameters, and function calls. The stack area grows and shrinks as per function calls. If a function is called, stack area is increased and when a function returns, stack area is decreased.
-
System Data Segment: System Data Segment contains details of a segment like - current directory of the process, user id (UID) of the process, group ids of the process (GIDs), size of text, data and stack, etc. One thing to note here is that the data segment part is maintained by the system and is accessible by the process only via system calls.
Intel x86 Address Translation
To derive the actual address from the logical address, the x86 system uses a 16-bit segment register. The x86 is a series of microprocessors that were developed by Intel Corporation. Intel-compatible x86 computers instruction set architecture uses memory segmentation. Initially, programmers can have an address of a maximum of 64KB. Intel introduced segmentation to allow programs to have an address of more than 64 KB. But there was no memory protection available. Any running program can access any segment without any restriction. A segment is only identified by its starting location without the need for segment length. After some years, the Intel 80286 processor introduced the second version of segmentation that added support for virtual memory and memory protection. In the protected mode, a running program can only access specified segments. Or we can say that a running program can only access the segments that belong to the currently executing process.
The original x86 Intel model without memory protection was then renamed as real mode. In real mode, the size of a segment can range from 1 byte to 64 KB. The newer x86 Intel version was renamed as protected mode and it can support an address of more than 64 KB in size.
The x86-64 architecture does not use segmentation in long mode. Instead, they handle programs and their data by utilizing memory-paging. Paging (which divides memory into equal-sized pages) is more efficient because it also serves as a way of memory protection as only specified pages of a process can be accessed by the running program.
Global Descriptor Table and Segmentation Using of x86 System
Global Descriptor Table is used from the starting of the Intel 80286 processor. The Intel x86 processor uses a binary data structure known as Global Descriptor Table or GDT. The GDT simply tells the CPU about the segments of the memory. It also maintains the various segments of the currently executing process. GDT also maintains the size, base address, and access privileges (like writing or reading, or executing rights) of a segment.
The GDT is pointed by a register known as GDTR or Global Descriptor Table Register. The entries in the Global Descriptor Table are accessed by Segment Selectors(discussed below), which are loaded into Segmentation registers.
There is also a Local Descriptor Table or LDT. Multiple LDTs can be defined inside the GDT. The LDT is used to store the memory segments which are private to a specific program, on the other hand, GDT contains global segments.
The basic overview of address conversion is shown below.
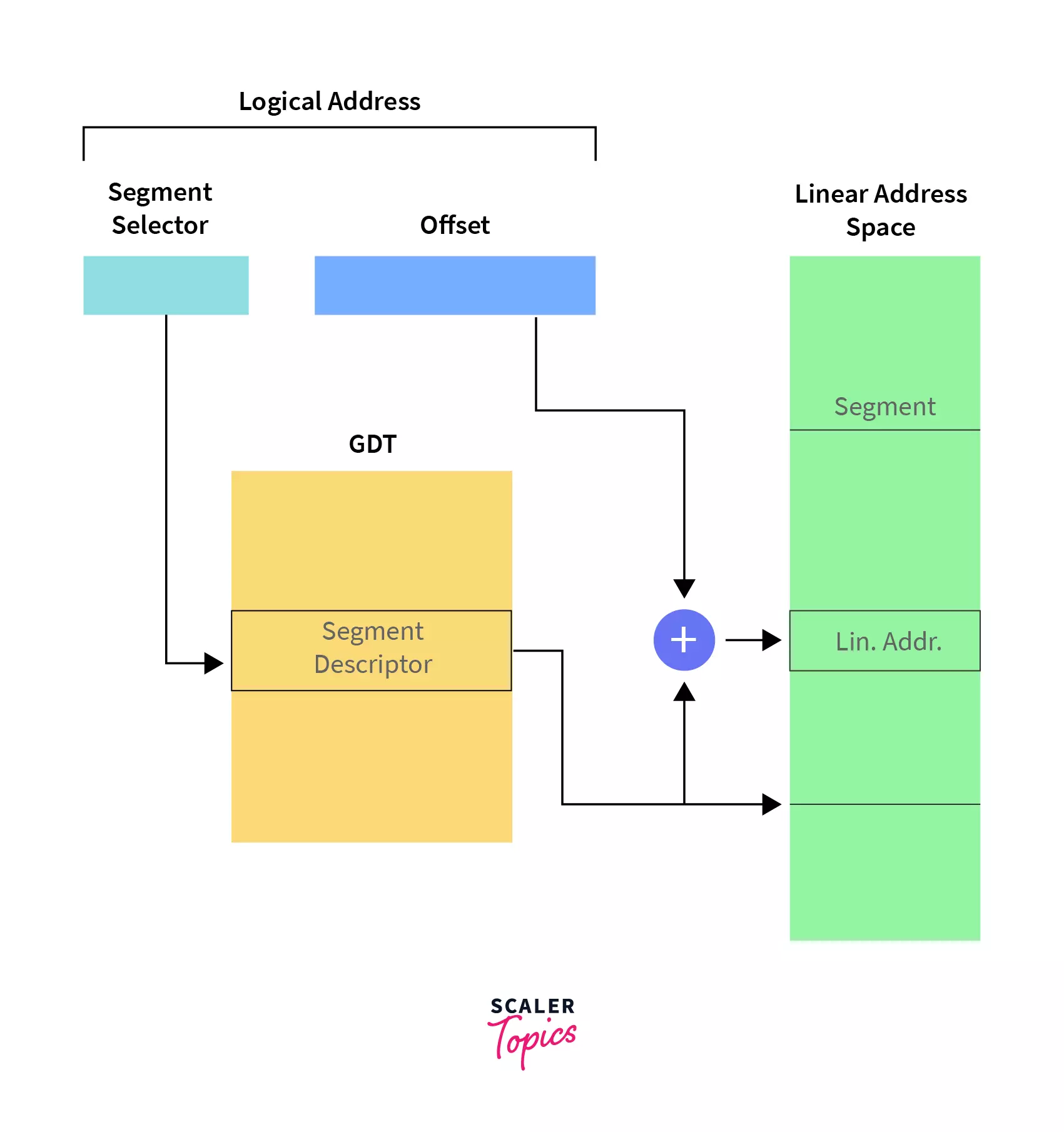
Segment Descriptor Inside Global Descriptor Table
Segment Descriptor is identified with segment selectors. The Segment Selector (or simply selector) is an index inside the LDT or GDT that is used to point or reference a segment. The selectors are then loaded into the segment register for further use. When a sector or index is loaded into the segment register, it automatically reads the GDT or LDT and stores the properties of the segment inside the processor itself.
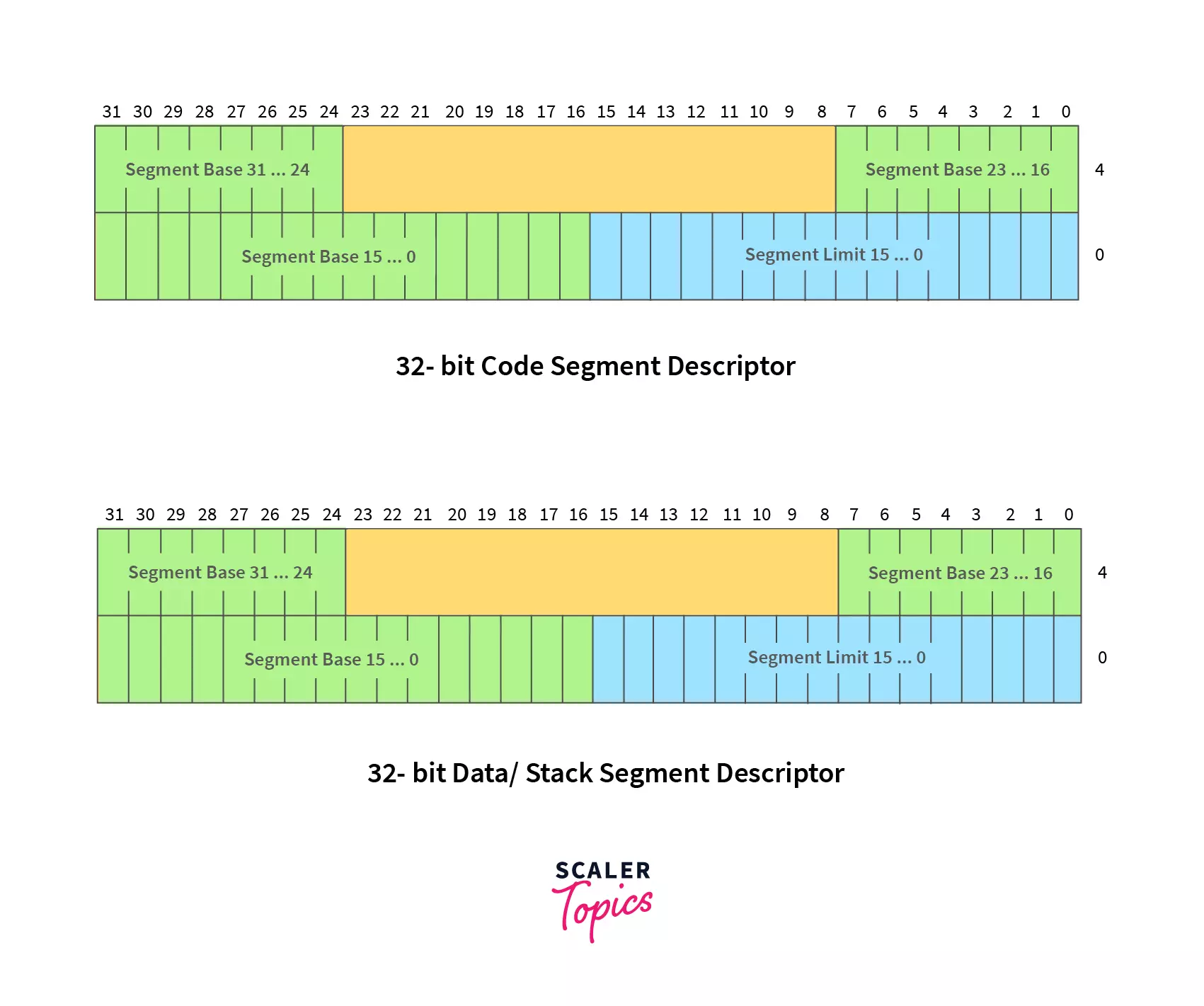
Segment Descriptor contains one memory segment that holds the segment base address, segment limit, and segment access rights (like writing reading, or executing rights).
Size of Segment Descriptor and its components:
- Segment Descriptor: 8 bytes
- Base Address size: 32 bits, which defines the base address of a segment in the linear address space.
- Segment Limit size: 20 bits, which defines the largest offset of a segment.
The basic overview of Segment Descriptor is shown below.
Segment and Offset Registers
To know about the segment and offset register, we should first know what is segment number and offset number are. An offset generally denotes the number of address locations that need to be added to the base address to get to the specified absolute physical address. The segment registers to store the starting addresses of a segment.
To reference any memory location in a segment, the processor combines the segment address in the segment register with the offset value of the location.
So, we use segment number (found using segment register) and offset number (using offset register) for the address translation.
Embrace the challenge of operating systems with our free Operating System course. Enroll now and unlock the secrets to building efficient and responsive computing environments!
Conclusion
-
Segmentation divides the secondary memory into uneven-sized blocks known as segments. Segmentation divides processes into smaller sub-parts known as modules.
-
Segmentation is done considering that the relative data should come in a single segment.
-
Partition size depends upon the type and length of modules.
-
Segmentation can be divided into two types namely - Virtual Memory Segmentation and Simple Segmentation.
-
Operating System maintains a segment table for each process.
-
Segment Table is used to store the records of the segments. The segment table itself consumes small memory as compared to a page table in paging.
-
Intel-compatible x86 computers instruction set architecture introduced memory segmentation.
-
A binary data structure known as Global Descriptor Table (GDT) is used which tells the CPU about the memory segments.
-
GDT contains Segment Selector which is used to point or reference a segment.
-
Segmentation provides better CPU utilization as an entire module is loaded at once.
-
Segmentation allows user to partition their programs into modules that operate independently.
-
The swapping of processes results in the breaking of the free memory space into small pieces. This breaking of free space into pieces is called External Fragmentation.
-
When a process is completed, it is removed from the main memory. Since the segment of the process is of uneven length it creates uneven-sized holes in the main memory.
-
There is an overhead of maintaining a segment table for each process as well.
